1. Introduction
The public sector has confronted service revolution since the mid-1980s. In the 1990s, the public sector’s service revolution has gathered momentum [
1] and satisfactory service delivery for users and citizens with efficiency and effectiveness have led to e-government [
2]. E-government, primarily facilitating communications between the government and its stakeholders including citizens, other governments, government agencies and employees via internet and web-enabled computer technologies, becomes a prevalent and useful public service tool for the public sector and an international phenomenon [
3].
E-government has established new public governance on the premise of e-government’s economic, political and practical values including citizenry satisfaction, resource efficiency, democratic responsiveness, accountability and fluent communications between governments and their stakeholders [
4]. Though increasing practical and research attention to e-government, e-government is a nascent research field, due to its relatively short history that begun in the middle of 1990s [
5]. The e-government literature has focused on e-service, e-democracy, conceptual modeling [
6] and the diffusion of e-government including influencing factors on e-government diffusion, organizational factors in the e-government diffusion, systems and applications for e-government and technology diffusion [
7]. Joseph’s (2013) analysis of the e-government research trend suggests the importance of studies using primary data and the opportunities of diverse topics which can expand the e-government literature [
4].
With the advent of information technologies such as e-government in public sectors, the information systems security (ISS) becomes one of the prevalent problems. This study analyzed the primary data collected from the Korean public sector concerning ISS. As ISS has been identified both as a success factor [
8]) and a barrier to e-government, e-government should reduce ISS threats and continuously improve ISS. ISS issues in e-government include protecting citizens’ personal data, cyber-attacks and terrors [
7], system security for cloud computing [
9] and transaction security [
8].
Although ISS violation harms private organizations in terms of financial loss and reputational damage [
10], for the public sector it causes more serious reputational damage and a complex web of financial, political and economic loss. Although technology-based solutions have been applied as the main solution for information threats and attacks, they have been only modestly effective [
11]. The heavy reliance on technology-based solutions stems from the limited understanding of the complicated characteristics intertwined with technical, institutional, sociocultural and organizational aspects of ISS [
12]. Consequently, it is natural that the focus of ISS has shifted from technical approaches toward social-organizational approaches and individual employee behavior.
In fact, numerous studies (e.g., [
10,
13,
14]) have identified insider threats (i.e., information violation by employees) as one of the most serious threats to ISS. Employees’ ISS compliance and behavior have been identified to be among key elements to successful ISS from a socio-organizational and behavioral perspective [
15].
Therefore, employees’ ISS-compliant or ISS-noncompliant behavior in organizations has received growing attention in ISS literature [
16]. Deterrence theory is the primary theoretical framework that has been used to understand and predict employees’ misuse and violation of information systems [
17]. However, the inconclusive findings with regard to the effectiveness of formal deterrence systems suggest that each individual’s different level of perceived deterrence threat determines the effectiveness of ISS deterrence [
18].
Therefore, this study investigates the factors that influence individuals’ perceptions of formal and informal deterrence threats by analyzing the ISS compliance intentions of employees working in the Korean public sector.
Although Korean government agencies have been implementing and imitating ISS systems for effective information security, problems including a lack of manpower and ill-defined roles that cause performance-assessment problems, poor information security documentation and information security monitoring and inspection (Hwang & Choi, 2017). Government employees are required active cooperation and ISS behaviors for effective ISS performance; however, ISS is not considered as their priority when ISS behaviors are not included in their individual performance evaluations in the Korean government. Thus, it is vital to understand what drives employees’ ISS compliance intentions [
19].
Nye’s four types of social controls [
20] are integrated with Hirschi’s social bonding theory [
21], which provides useful insights for understanding employees’ motivations for ISS compliance or violation and their different levels of perceived deterrence threat. Moreover, public sector employees’ ISS compliance intentions are investigated in the presence of formal deterrence and shame as self-imposed punishment. An empirical study of this under-researched ISS topic can make a valuable contribution in the field of public administration and e-government and has several practical implications:
ISS policies for e-government should embrace employees’ motivations for compliance or noncompliance and the individual differences of their responses to sanction-based approaches.
Because employees in the public sector may respond to both formal and informal deterrence, e-government ISS guidelines and training should emphasize to employees the repercussions of committing ISS violations, highlighting not only the formal sanctions but also the emotional punishment (e.g., shame and guilt) based on peers’ criticism, individual reputational damage and alienation.
Because adult social bond elements, such as job commitment and job stability, are positively associated with perceived deterrence threats, the design of the deterrence system should incorporate them.
4. Methodology Data Analysis and Results
Structural equation modeling is used to validate the research model; enables analysis of the relationship and strength between constructs. Consistent with a growing number of management studies, the partial least squares (PLS) approach to structural equation modeling is used as the estimation procedure. PLS combines factor analysis with linear regression, makes only minimal assumptions with the goal of variance explanation, makes no assumptions regarding the underlying distribution of the data and does not require large sample sizes [
53]. The data analysis is conducted by use of the smart PLS 2.0 and SPSS 18.0 software packages.
The reliability of the data and the convergent validity are analyzed. Before analyzing the data, however, exploratory factor analysis is conducted by using principle component analysis. A varimax orthogonal factor rotation is conducted.
Table 2 shows the results of the exploratory factor analysis.
The Cronbach’s alpha values are greater than 0.7, indicating that the data is reliable. Variables are considered internally valid if their composite reliability value is greater than 0.7 and their average variance extracted (AVE) value is greater than 0.5 [
53]. As shown in
Table 3, the composite reliability and AVE values for all constructs is greater than the required thresholds for validity.
To satisfy discriminant validity, the square roots of the AVE values must be greater than the correlation coefficients between the construct and the other constructs in the model [
53].
Table 4 shows the correlation matrix for the constructs and, on the diagonal, the square roots of the AVE values. The square roots of the AVE values exceeded the correlation coefficients, verifying discriminant validity.
Now that the measures have been validated, the effects proposed in the model and their significance are estimated using PLS.
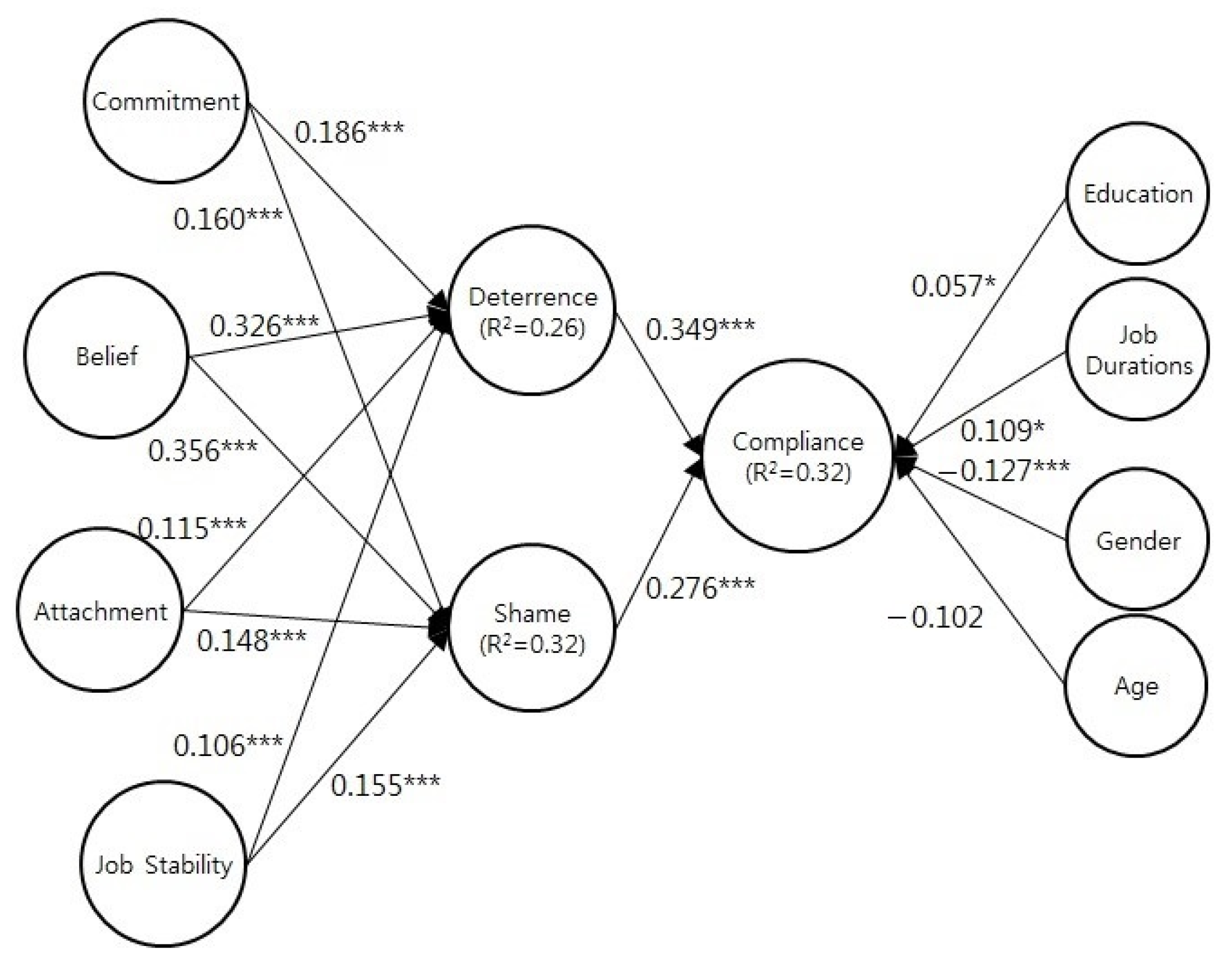
Table 5 shows the results of the structural model PLS regressions. The bootstrap method is used to evaluate the path (bootstrap time = 500). The model explains 32% of the total variance in employee ISS compliance.
Several versions of the research model have been tested. In the first model (
Figure 2), all constructs are included and a direct path and an indirect path to compliance, as well as the effects of the control variable on compliance, are tested. Hypothesis 1, that commitment is positively associated with deterrence, is supported (ß = 0.186,
p < 0.01). This result shows that an increased level of commitment is associated with an improvement in deterrence, meaning that it is associated with improved ISS compliance and inhibition of ISS violations, which supports Bulgurcu et al. [
12] study. Hypothesis 2, that commitment is positively associated with shame, is supported (ß = 0.160,
p < 0.01). This result means that as employees commit further to the organization, their potential shame about violating ISS increases.
Hypothesis 3, that belief is positively associated with deterrence, is also supported (ß = 0.326,
p < 0.01). This result shows that increased belief is associated with an improvement in deterrence, which is consistent with Siponen and Vance [
27]. Hypothesis 4, that belief is positively associated with shame, is supported (ß = 0.356,
p < 0.01). In other words, as employees’ beliefs about what is acceptable versus unacceptable behavior strengthens, their potential shame associated with violating ISS increases.
Hypothesis 5, that attachment is positively associated with deterrence, is also supported (ß = −0.115,
p < 0.01). This result shows that deterrence improves as attachment increases. Hypothesis 6, that attachment is positively associated with shame, is supported (ß = 0.148,
p < 0.01), which supports Hirschi [
30]’s study. This result shows that the more an employee is attached to his or her family the greater the potential shame of violating ISS.
Hypothesis 7, that job stability is positively associated with deterrence, is supported (ß = 0.106,
p < 0.01), demonstrating that increased job stability improves deterrence, which is consistent with Crutchfield’s [
39] study. Hypothesis 8, that job stability is positively associated with shame, is supported (ß = 0.155,
p < 0.01), which indicates that more stable job environments engender more shame from employees who violate ISS policy.
Hypothesis 9, that deterrence is positively associated with ISS compliance, is supported (ß = 0.349,
p < 0.01), which support many ISS studies (e.g., [
18,
28,
42]). In other words, deterrence positively influences employee compliance with ISS. Hypothesis 10, that shame is positively associated with compliance, is supported (ß = 0.276,
p < 0.01).
As
Table 6 shows, gender, education and job duration is associated with ISS compliance. On average, men comply with ISS more than women do. Education also influences compliance with ISS: a high level of education helps in ISS compliance. Longer job duration is also associated with improved ISS compliance.
In additional, the mediation effects of deterrence and shame are statistically tested. Such an analysis of a mediation effect explains how or why relationships between the independent variables and the dependent variable exist. The mediating effects of deterrence and shame are tested using logic from Baron and Kenny [
54], which describes that a variable acts as a mediator when it satisfies the following three conditions:
the correlation between the independent variable and the mediating variable (path a) is significant;
the correlation between the meditating variable and the dependent variable (path b) is significant; and
when path a and path b are controlled (when the mediator is introduced into the regression equation describing path c, from the independent variable to the dependent variable), the correlation in path c is no longer statistically significant and thus can be eliminated.
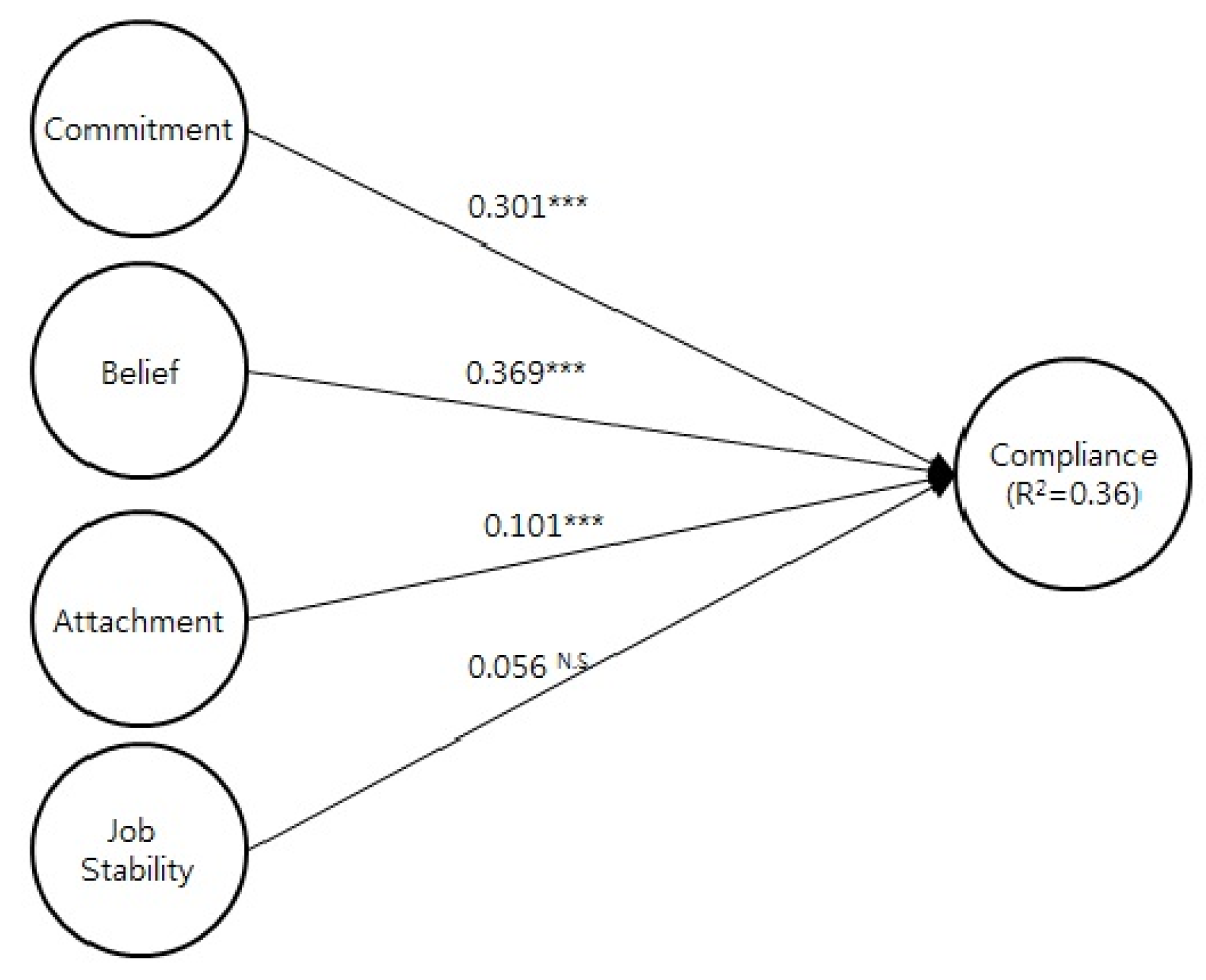
As
Figure 3 shows, the direct paths from commitment, belief and attachment to ISS compliance are significant, but the direct path from job stability to ISS compliance is not significant. Therefore, job stability is excluded from the subsequent mediational analysis.
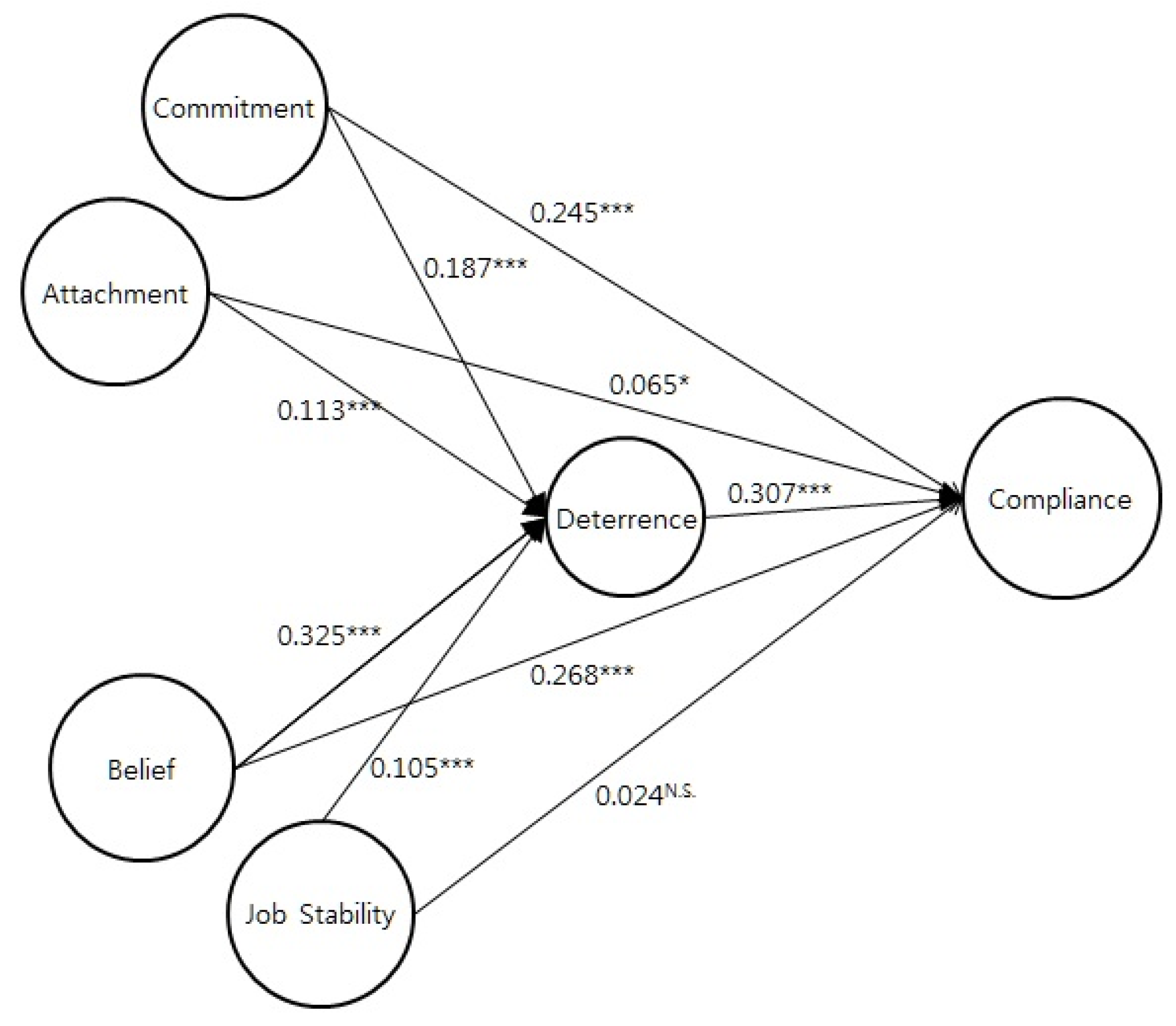
By introducing deterrence as a mediator of the path between the three independent variables and ISS compliance, the strength of the relationships between ISS compliance and each of commitment, belief and attachment is reduced, indicating a partial mediating effect of deterrence on the effects of commitment, attachment and belief on compliance (see
Figure 4). This result shows that commitment, belief and attachment are related to ISS compliance via deterrence.
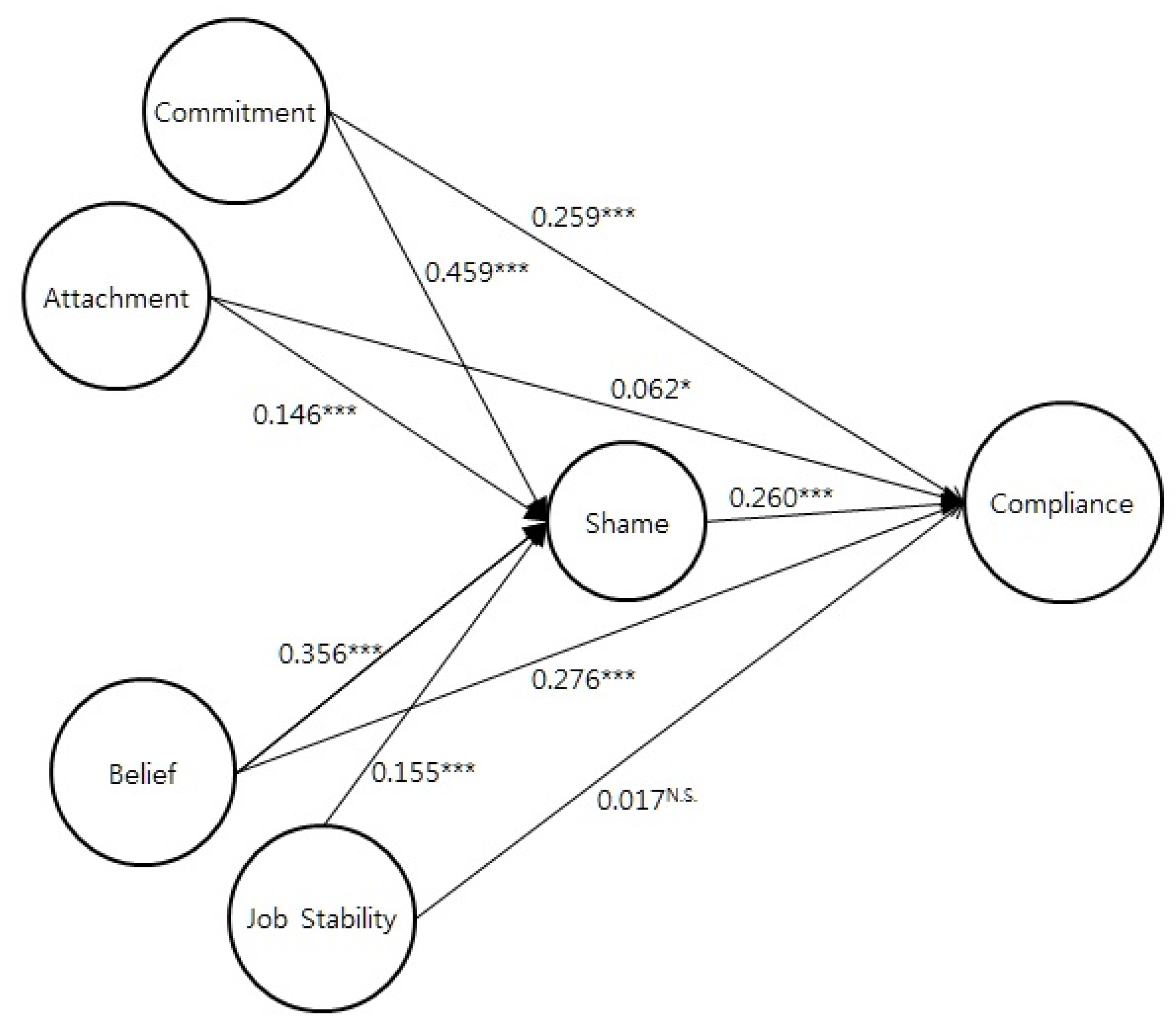
The same procedure is conducted to test the meditating effect of shame on the relationship between ISS compliance and each of commitment, belief and attachment. Shame demonstrates similar mediational effects as deterrence. The strength of the relationships between ISS compliance and each of commitment, belief and attachment is reduced, indicating a partial mediating effect of shame on the effects of commitment, belief and attachment (see
Figure 5). In other words, commitment, belief and attachment are related to ISS compliance via shame. Thus, deterrence and shame contribute to a better explanation of ISS compliance in the context of attachment, belief and commitment.
Lastly, but not least importantly, the effects on ISS compliance of four control variables (gender, age, job duration and education) are tested. Of these, only gender is statistically significant. On average, men comply with ISS more than women do. Education and job duration seem to positively influence ISS compliance, but the relationships are not statistically significant.
Additionally, we conducted a common method bias (CMB) test based on Podsakoff, MacKenzie, Lee and Podsakoff’s CMB method [
55]. The indicators of all constructs were reflectively associated with the method factor; each indicator variance was then computed as explained by the principle constructs and the method factor.
Table 7 notes that most of the method loadings were not significant. Moreover, the common method-based variance for an indicator was only 0.006, whereas the average substantive explained variance was 0.797. Based on the results of these tests, it was determined that CMB was apparently not a significant threat in this study.
5. Discussion
This study investigates the factors that influence individuals’ perceptions of deterrence threats by analyzing the ISS compliance intentions of the Korean government employees. Nye’s social controls and Hirschi’s social bonding theory are integrated in the current study’s research model, which leads us to understand employees’ motivations for ISS compliance or violation and their different levels of perceived deterrence threat. Additionally, the presence of formal deterrence and shame as self-imposed punishment is analyzed to investigate the government employees’ ISS compliance intentions. An empirical study of this under-researched ISS topic can make a valuable contribution in the field of public administration and e-government.
This study makes several theoretical and practical contributions as follows:
An empirical study of this under-researched ISS topic can make a valuable contribution in the field of public administration and e-government. More specifically, most ISS studies have focused on formal deterrence; however, the roles of both formal and informal deterrence and individuals’ differences in perceptions of deterrence threats in increasing employee ISS compliance reflect the complexities of ISS compliance shape intentions of individual ISS compliance. Thus, this study reflects the complexity of employee compliance or noncompliance with ISS which requires a more comprehensive theoretical framework. Our research model integrates Nye’s social control theory with Hirschi’s social bonding theory to understand this complexity, which leads this study to provide novel and valuable insights. This study is one of very few studies that have investigated the role of and the effect of shame on ISS compliance, which provides empirical evidence for shame serving the roles of self-imposed punishment and informal deterrence.
Practically speaking, ISS policies for e-government should embrace employees’ motivations for compliance or noncompliance and the individual differences of their responses to sanction-based approaches. Because employees in the public sector may respond to both formal and informal deterrence, e-government ISS guidelines and training should emphasize to employees the repercussions of committing ISS violations, highlighting not only the formal sanctions but also the emotional punishment (e.g., shame and guilt) based on peers’ criticism, individual reputational damage and alienation. Because adult social bond elements, such as job commitment and job stability, are positively associated with perceived deterrence threats, the design of the deterrence system should incorporate them.
In this study, a research model has been constructed based largely upon Nye’s comprehensive social control theory, which specifies direct and indirect control of socially deviant behavior by an individual’s socially formed control and bond elements [
20]. Despite criminology literature’s emphasis of the importance of informal deterrence, including shame and guilt, most ISS studies have focused on formal deterrence. Moreover, although individuals’ differences in their perceptions of deterrence threats affect their ISS compliance or noncompliance behavior, factors influencing such differences have not been studied sufficiently. The roles of formal and informal deterrence and individuals’ differences in perceptions of deterrence threats in increasing employee ISS compliance—and the relationships among them—reflect the complexities of ISS compliance.
Understanding the complexity of employee compliance or noncompliance with ISS requires a more comprehensive theoretical framework and Nye’s social control theory enables the examination of these complexities in a research model. Adopting constructs from the ASBT, this article has posited a research model in which four social bond constructs (commitment, belief, attachment and job stability) are mediated by deterrence and shame in improving an individual’s ISS-compliant behavior. Analysis of data collected from government employees largely supports the proposed research model, confirming the applicability of ASBT to ISS compliance in the public sector.
As expected, the analysis results show that adult social bonding elements—job commitment, belief, attachment and job stability in the ASBT—are positively associated with deterrence and shame, which in turn are positively associated with the ISS compliance of individual employees. Thus, ASBT is a useful theory for understanding the individual factors that influence employees’ perceptions of formal deterrence and informal shame related to ISS compliance in an e-government context.
Belief seems to have a greater effect on deterrence and shame than do the other three ASBT constructs. It can be inferred that, because belief is a norm compared to the other rather temporary constructs, such as commitment, a strong internal orientation is more important than are fragile punishments or rewards that increase commitment and that indirect social controls, such as attachment and job stability, may have weaker effects.
Very few studies have investigated the role of shame in reducing the incidence of ISS violation and the effect of shame on ISS compliance has rarely been studied. This article has provided empirical evidence for shame serving the roles of self-imposed punishment and informal deterrence and thus increasing ISS compliance. The identification of shame serving such a role can help in designing effective employee training programs.
This article has validated the mediation effects of deterrence and shame, which are elements of social control, on the ISS-compliance effects of elements of SBT. Specifically, through deterrence and shame, commitment, attachment and belief positively influence ISS compliance. The mediation effects show that the research model integrating SBT into social control theory explains well how employees comply with ISS.