An ISM Modeling of Barriers for Blockchain/Distributed Ledger Technology Adoption in Supply Chains towards Cybersecurity
Abstract
1. Introduction
- What are the challenges of BDLT adoption for cyber supply chain risk management?
- What hierarchical relationships exist among identified challenges?
- Which challenges have more driving power and which challenges have more dependency power on the adoption of BDLT technologies in CSCRM?
2. Literature Review
2.1. Supply Chain Risk Management
2.2. Cyber Supply Chain Risk Management
2.3. Blockchain and Distributed Ledger Technologies
2.4. BDLTs Key Capabilities for Cybersecurity
- Decentralization: Unlike a traditional centralized transaction system where transactions are verified by a trusted centralized agency, such as a central bank or a government, in a decentralized infrastructure, two parties can access the database without the need for a third party to keep records or perform authorization. Within traditional systems, risks related to human error or criminal activity remain unidentified. Furthermore, such centralization can have several downsides, including more charges, lower overall performance, and various failures in the systems on the part of service providers [61,62]. Distributed ledgers record transactions without the association of a third party, which is helpful in the reduction of service costs, the improvement of the efficiency of the chain, and mitigation of the risk of system failures [63].
- Availability: The National Institute of Standards and Technology (NIST) defines availability as “ensuring timely and reliable access to and use of information” [64]. Cyberattacks start to impact availability of technology services with vulnerabilities, such as counterfeiting, theft, fraud, data manipulation, or falsification [65]. The DLT solution based on its decentralization and peer-to-peer characteristics makes it more difficult for criminals to disrupt. However, one of the most common attacks, known as distributed denial-of-service (DDoS) attacks, can target internet services and networks with more traffic than the server or network can handle and, hence, some disruptions to blockchain solutions. As a result, with the availability of information in decentralized platforms of DLTs, a rise in DDoS attacks could be observed [66].
- Data Access and Disclosure: According to reference [67], blockchain is a “secure public ledger platform shared by all parties through the Internet or an alternative distributed network of computers”. Blocks with sets of information are shared between participants. The participants have the ability to share records and have limited access to their relevant transactions whenever they need them [68]. The decentralized nature of blockchain technology contributes to information sharing among relevant parties, helping transactions with high security from potentially targeted attacks or complex incidents [69].
- Traceability: BDLTs provide a wide range of capabilities, including traceable and tamper-resistant records, a high level of traceability with trusted information, accessibility, and the visibility of data provenance [70,71]. All blockchain transactions are given an exact timestamp when the transactions are added to the chain [46]. Such an inherited characteristic of blockchain enhances traceability and authenticity for the transaction of products, data, and interactions [72].
- Transparency: Current centralized systems in the supply chain deal with issues such as fraudulent activities, privacy and security errors, lack of transparency and trust [73]. Blockchain technologies are potential enablers of a trusted and efficient supply chain and can improve transparency and bring high visibility, authenticity, and availability to all the stakeholders in the network [74,75]. The secure and tamper-resistant mechanism of blockchain paves the way for greater transparency, increasing the trustworthiness of transactions through interaction and access to the network among users [76].
- Privacy and Security: Blockchains or cryptographic-based distributed ledgers allow more integrity and information security than traditional databases because blockchain connects devices to the networks and members to devices, and encrypted transactions are added to the chain with the authorization of all participants without the need for data disclosure [23]. So, given the abovementioned advantage of the BDLTs, it is very difficult to hack this impenetrable technology.
- Immutability: Immutability in the blockchain refers to the high ability of technology to remain censorship-resistant and indelible [77]. Immutability enables the transformation of each new transaction into the chain and approval by a consensus mechanism. In addition, all the historical registered operations are immutable; therefore, any manipulation and forgery of data records would need a cyber-attacker to break most of a network’s nodes [74].
- Reduced Overall Cost: Blockchain technologies help reduce the overall cost because of the direct transfer of transactions without the need for a bank or other third party. Costs related to documentation, tax services, auditing, and governance can potentially be reduced. Subsequently, the reduction of transaction costs that can be supported by blockchain technology would lead to eliminating cybersecurity incidents [78,79].
- Data Quality: BDLT does not ensure the quality of data but any blocks that contain low accuracy and quality of data will not be allowed to add to the chain. Blockchain guarantees transformation of accurate and impenetrable data faster than any other system, and facilitates entities in exchanging information in a protected way [66].
- Distributed: The validated transactions and updated records are synchronized into blocks for processing and protocols and supporting infrastructures allow every node or participant in different locations to receive a real-time transaction [80].
2.5. Applications of BDLTs Adoption in CSCRM
3. Challenges for Blockchain/BDLT Adoption in CSCRM
3.1. Immature, Early Stage of Development
3.2. Scalability and Bandwidth Issues
3.3. Wasted Resources or High Energy Consumption
3.4. Throughput and Low Performance
3.5. Lack of Standardization and Interoperability
3.6. Privacy and Information Disclosure Issues
3.7. Criminal Activity, Malicious Attacks
3.8. Dependent on Input Information from External Oracles
3.9. Poor User Experience
3.10. Suitability of Blockchain
3.11. Cryptocurrency Volatility
3.12. Smart Contract Issues
3.13. Quantum Resilience
3.14. Lack of Trust
3.15. Users’ Credential Loss
3.16. Poor Clarity Regulatory Provisions
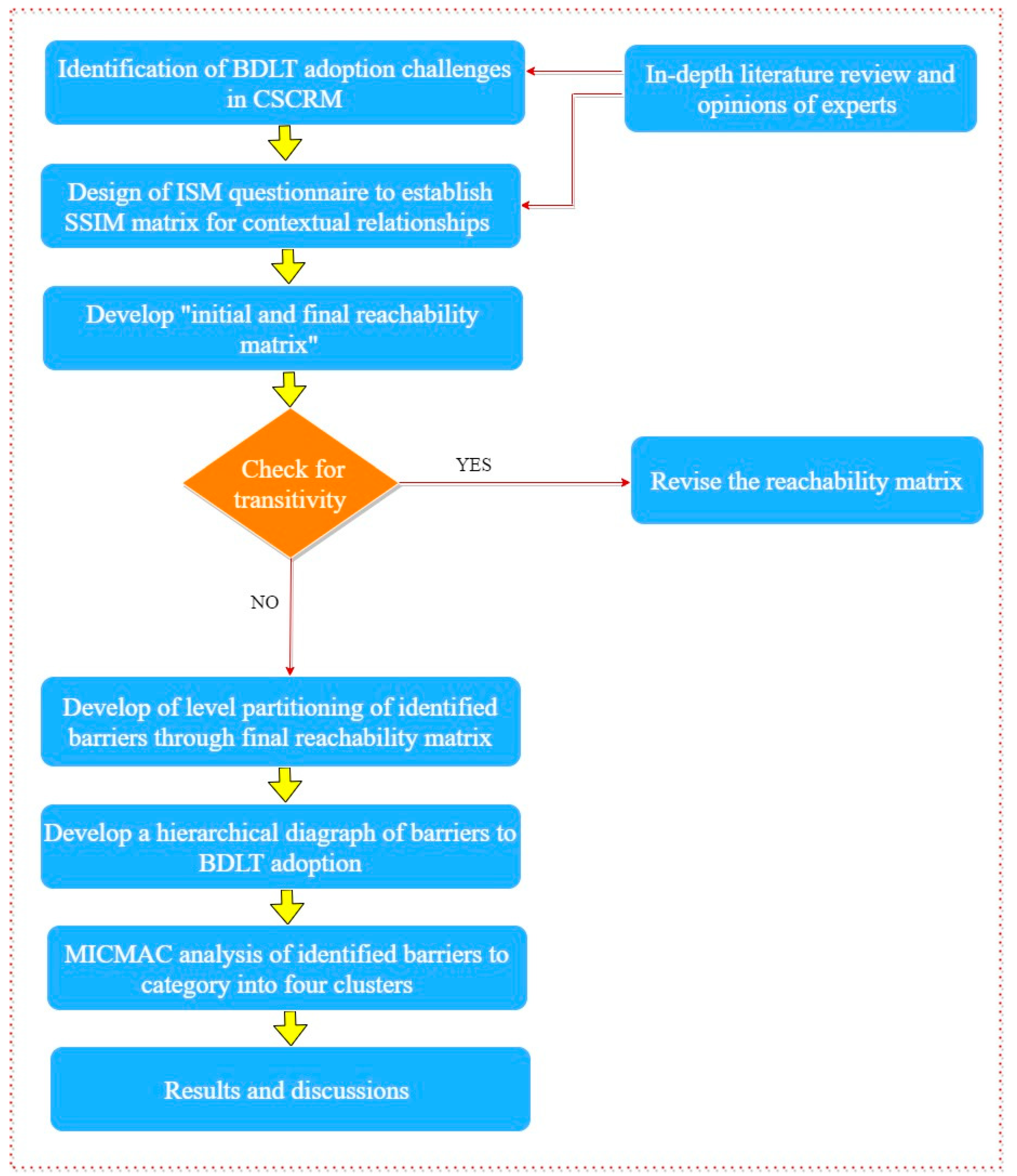
4. Methodology and Research Design
4.1. Data Collection
4.2. ISM Methodology
5. Results
5.1. Structural Self-Interaction Matrix (SSIM)
5.2. Reachability Matrix
- i.
- If the symbol of V is shown in the cell of (i, j) in the SSIM matrix, then in the IRM, the value of cell (i, j) will become 1, and the corresponding cell (j, i) is replaced with the value ‘0’.
- ii.
- If the symbol of A is shown in the cell of (i, j) in the SSIM matrix, then in the IRM, the value of cell (i, j) will become 0, and the corresponding cell (j, i) is replaced with the value ‘1’.
- iii.
- If the symbol of X is shown in the cell of (i, j) in the SSIM matrix, then in the IRM, the value of cell (i, j) will become 1, and the corresponding cell (j, i) is replaced with the value ‘1’.
- iv.
- If the symbol of O is shown in the cell of (i, j) in the SSIM matrix, then in the IRM, the value of cell (i, j) will become 0, and the corresponding cell (j, i) is replaced with the value ‘0’.
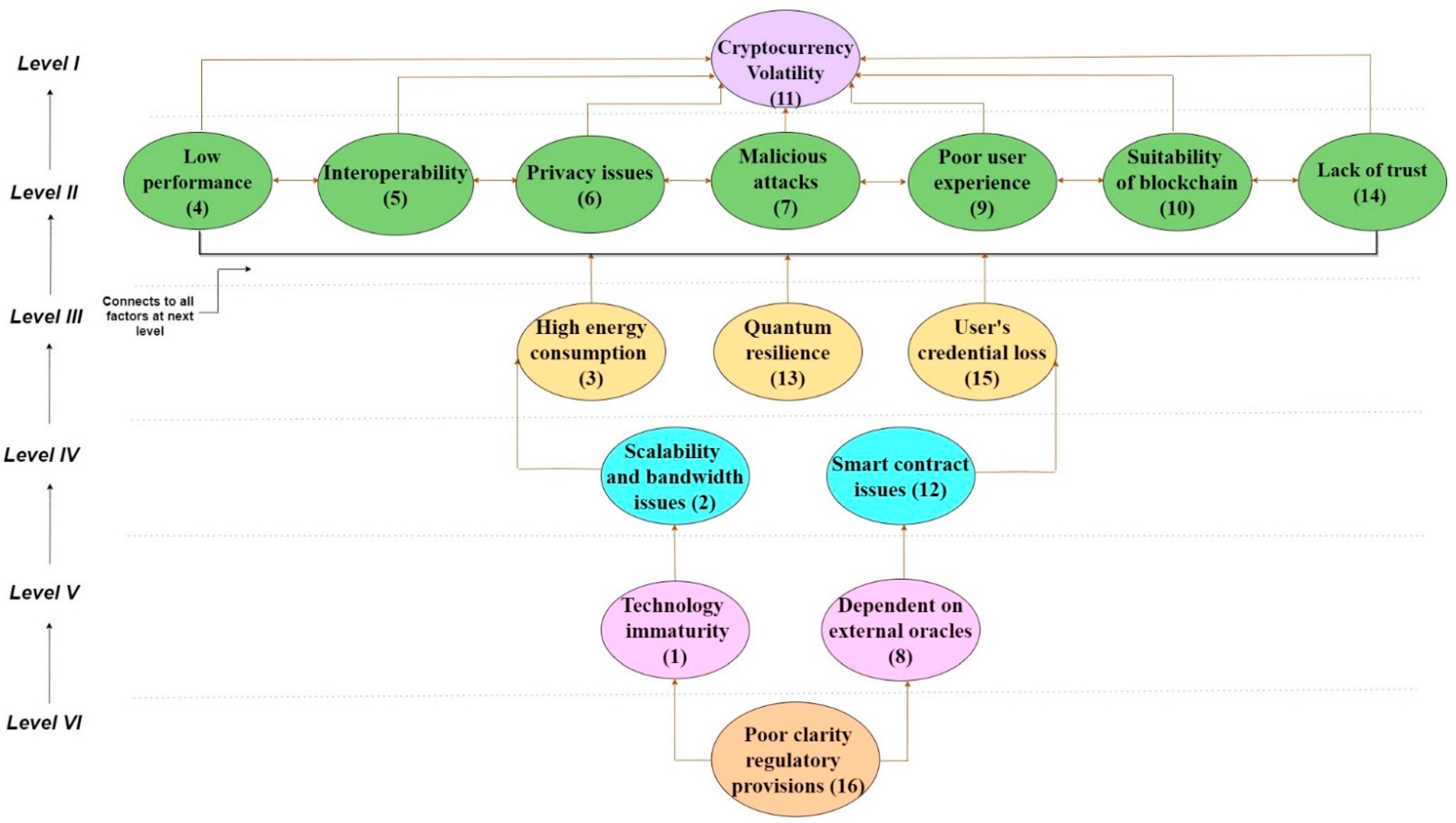
5.3. Level Partitions
5.4. Building an ISM Model
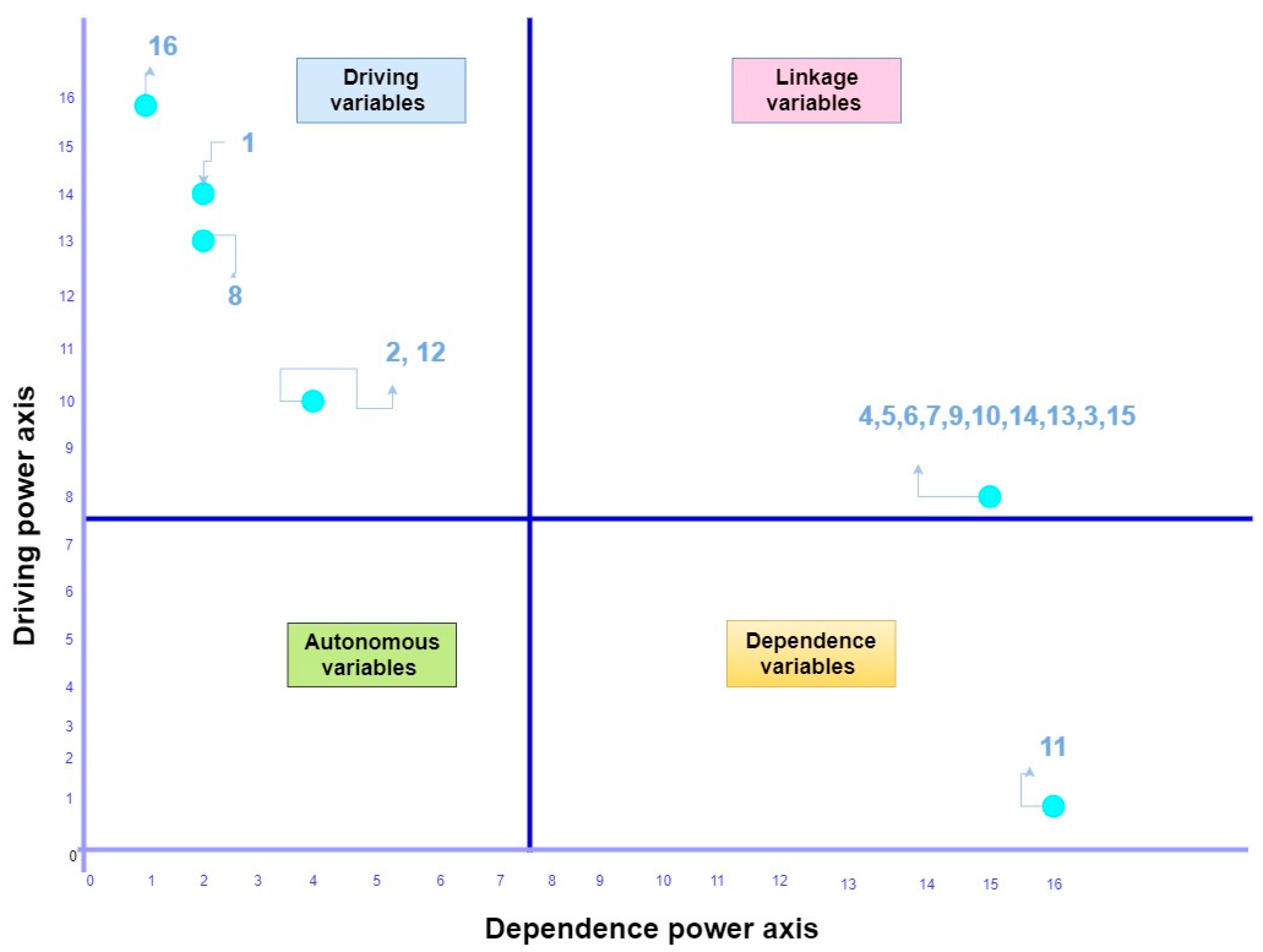
5.5. MICMAC Analysis
6. Discussion on Theoretical and Managerial Implications
6.1. Implications for Theory
6.2. Implications for Practice
7. Conclusions, Discussion of Findings, and Scope for Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Chen, T.M.; Abu-Nimeh, S. Lessons from Stuxnet. Computer 2011, 44, 91–93. [Google Scholar] [CrossRef]
- Burton, M.; Cho Walsgard, J. Cyber Attack Puts a Spotlight on Fragile Global Supply Chain—Bloomberg. Available online: https://www.bloomberg.com/news/articles/2019-03-19/cyber-attackputs-a-spotlight-on-fragile-global-supply-chains (accessed on 2 February 2021).
- Boyes, H. Cybersecurity and Cyber-Resilient Supply Chains. Technol. Innov. Manag. Rev. 2015, 5, 28–34. [Google Scholar] [CrossRef]
- ResilienceFrom Ports to Distribution: Insights into Supply Chain Cyber Threats. Available online: https://www.resilience360.dhl.com/resilienceinsights/fro-mports-to-production-insights-into-supply-chain-cyberthreats/?utm_source=GoogleAdwords&utm_medium=PaidSearch&utm_Capaign=cyber-crime-2018&utm_term=CyberSecurity&utm_content=Thought-Leadership&g (accessed on 26 February 2020).
- NIST. Best Practices in Cyber Supply Chain Risk Management. Available online: https://www.nist.gov/system/files/documents/itl/csd/Workshop-Brief-on-Cyber-Supply-Chain-Best-Practices.pdf (accessed on 15 February 2021).
- Hinde, S. Life Was Simple Then. Comput. Secur. 2000, 19, 222–229. [Google Scholar] [CrossRef]
- Williams, P. Why Latin Port, Shipping and Supply Chain Security is Getting more Complex—And What it Means for Training. Available online: https://www.linkedin.com/pulse/why-latin-port-shipping-supply-chain-security-getting-rachael-white/?trackingId=Rzjy0I5pF8Dy7YG3Vsm5Rg%3D%3D (accessed on 25 January 2021).
- Radanliev, P.; De Roure, D.C.; Nicolescu, R.; Huth, M.; Montalvo, R.M.; Cannady, S.; Burnap, P. Future developments in cyber risk assessment for the internet of things. Comput. Ind. 2018, 102, 14–22. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Das Bit, S. A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Aceto, B. Blockchain e Dintorini. 2019. Retrieved 7 March 2021. Available online: http://tendenzeonline.info/articoli/2019/05/08/blockchain-edintorini (accessed on 18 August 2020).
- Kshetri, N. Blockchain’s roles in strengthening cybersecurity and protecting privacy. Telecommun. Policy 2017, 41, 1027–1038. [Google Scholar] [CrossRef]
- Wensley, J.H.; Lamport, L.; Goldberg, J.; Green, M.W.; Levitt, K.N.; Milliar-Smith, P.M.; Shostak, R.E.; Weinstock, C.B. SIFT: Design and analysis of a fault-tolerant computer for aircraft control. Proc. IEEE 1978, 66, 1240–1255. [Google Scholar] [CrossRef]
- Rauchs, M.; Glidden, A.; Gordon, B.; Pieters, G.C.; Recanatini, M.; Rostand, F.; Vagneur, K.; Zhang, B.Z. Distributed Ledger Technology Systems: A Conceptual Framework. SSRN Electron. J. 2018. [Google Scholar] [CrossRef]
- Saur, K.; Bowman, M.; Miele, A.; Held, J.P. Technology for Secure Partitioning and Updating of a Distributed Digital Ledger. U.S. Patent US20180145836A1, 18 November 2016. [Google Scholar]
- Ølnes, S.; Ubacht, J.; Janssen, M. Blockchain in government: Benefits and implications of distributed ledger technology for information sharing. Gov. Inf. Q. 2017, 34, 355–364. [Google Scholar] [CrossRef]
- Siyal, A.A.; Junejo, A.Z.; Zawish, M.; Ahmed, K.; Khalil, A.; Soursou, G. Applications of Blockchain Technology in Medicine and Healthcare: Challenges and Future Perspectives. Cryptography 2019, 3, 3. [Google Scholar] [CrossRef]
- Chod, J.; Trichakis, N.; Tsoukalas, G.; Aspegren, H.; Weber, M. On the Financing Benefits of Supply Chain Transparency and Blockchain Adoption. Manag. Sci. 2020, 66. [Google Scholar] [CrossRef]
- Zhao, G.; Liu, S.; Lopez, C.; Lu, H.; Elgueta, S.; Chen, H.; Boshkoska, B.M. Blockchain technology in agri-food value chain management: A synthesis of applications, challenges and future research directions. Comput. Ind. 2019, 109, 83–99. [Google Scholar] [CrossRef]
- Chen, S.; Liu, X.; Yan, J.; Hu, G.; Shi, Y. Processes, benefits, and challenges for adoption of blockchain technologies in food supply chains: A thematic analysis. Inf. Syst. e-Bus. Manag. 2020, 1–27. [Google Scholar] [CrossRef]
- Treiblmaier, H.; Rejeb, A.; Strebinger, A. Blockchain as a Driver for Smart City Development: Application Fields and a Comprehensive Research Agenda. Smart Cities 2020, 3, 853–872. [Google Scholar] [CrossRef]
- Mathew, A.R. Cyber Security through Blockchain Technology. Int. J. Eng. Adv. Technol. 2019, 9, 3821–3824. [Google Scholar] [CrossRef]
- Srivastava, S.S.; Dwivedi, R.; Gunda, A.; Meena, D.K.; Negi, R.; Vasita, N.; Singh, A. Blockchain and Its Application in Cybersecurity. In Cyber Security in India; IITK Directions; Shukla, S., Agrawal, M., Eds.; Springer: Singapore, 2020; Volume 4. [Google Scholar] [CrossRef]
- Taylor, P.J.; Dargahi, T.; Dehghantanha, A.; Parizi, R.M.; Choo, K.-K.R. A systematic literature review of blockchain cyber security. Digit. Commun. Netw. 2020, 6, 147–156. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernandez-Carames, T.M. A Review on Blockchain Technologies for an Advanced and Cyber-Resilient Automotive Industry. IEEE Access 2019, 7, 17578–17598. [Google Scholar] [CrossRef]
- Azzi, R.; Chamoun, R.K.; Sokhn, M. The power of a blockchain-based supply chain. Comput. Ind. Eng. 2019, 135, 582–592. [Google Scholar] [CrossRef]
- Ivanov, D.; Dolgui, A.; Das, A.; Sokolov, B. Digital Supply Chain Twins: Managing the Ripple Effect, Resilience, and Disruption Risks by Data-Driven Optimization, Simulation, and Visibility. In Handbook of Ripple Effects in the Supply Chain; International Series in Operations Research & Management Science; Ivanov, D., Dolgui, A., Sokolov, B., Eds.; Springer: Cham, Switzerland, 2019; Volume 276. [Google Scholar] [CrossRef]
- Zhang, H.; Nakamura, T.; Sakurai, K. Security and Trust Issues on Digital Supply Chain. In Proceedings of the 2019 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Fukuoka, Japan, 5–8 August 2019; Institute of Electrical and Electronics Engineers (IEEE), 2019. [Google Scholar]
- Hajric, V. Blockchain is Dead? Crypto Geeks Debate Merits of Once Dear Tech-Bloomberg. 2019. Available online: https://www.bloomberg.com/news/articles/2019-11-12/blockchain-is-deadcrypto-geeks-debate-merits-of-once-dear-tech (accessed on 28 February 2021).
- Hofmann, E.; Rüsch, M. Industry 4.0 and the current status as well as future prospects on logistics. Comput. Ind. 2017, 89, 23–34. [Google Scholar] [CrossRef]
- Dias, G.C.; Hernandez, C.T.; De Oliveira, U.R. Supply chain risk management and risk ranking in the automotive industry. Gestão Produção 2020, 27. [Google Scholar] [CrossRef]
- Juttner, U.; Peck, H.; Christopher, M. Supply chain risk management: Outlin ing an agenda for future re-search. Int. J. Logist. Res. Appl. 2003, 6, 197–210. [Google Scholar] [CrossRef]
- Ivanov, D.; Sokolov, B.; Solovyeva, I.; Dolgui, A.; Jie, F. Dynamic recovery policies for time-critical supply chains under conditions of ripple effect. Int. J. Prod. Res. 2016, 54, 7245–7258. [Google Scholar] [CrossRef]
- Ivanov, D. Revealing interfaces of supply chain resilience and sustainability: A simulation study. Int. J. Prod. Res. 2018, 56, 3507–3523. [Google Scholar] [CrossRef]
- Ghadge, A.; Weiß, M.; Caldwell, N.D.; Wilding, R. Managing cyber risk in supply chains: A review and research agenda. Supply Chain Manag. Int. J. 2019, 25, 223–240. [Google Scholar] [CrossRef]
- Chand, M.; Raj, T.; Shankar, R. Analysing the operational risks in supply chain by using weighted interpretive structure modelling technique. Int. J. Serv. Oper. Manag. 2014, 18, 378. [Google Scholar] [CrossRef]
- Venkatesan, S.P.; Kumanan, S. Supply chain risk prioritisation using a hybrid AHP and PROMETHEE approach. Int. J. Serv. Oper. Manag. 2012, 13, 19. [Google Scholar] [CrossRef]
- Ho, W.; Zheng, T.; Yildiz, H.; Talluri, S. Supply chain risk management: A literature review. Int. J. Prod. Res. 2015, 53, 5031–5069. [Google Scholar] [CrossRef]
- Moustafa, N.; Adi, E.; Turnbull, B.; Hu, J. A New Threat Intelligence Scheme for Safeguarding Industry 4.0 Systems. IEEE Access 2018, 6, 32910–32924. [Google Scholar] [CrossRef]
- Boyson, S. Cyber supply chain risk management: Revolutionizing the strategic control of critical IT systems. Technovation 2014, 34, 342–353. [Google Scholar] [CrossRef]
- Sindhuja, P.N.; Kunnathur, A.S. Information security in supply chains: A management control perspective. Inf. Comput. Secur. 2015, 23, 476–496. [Google Scholar] [CrossRef]
- Bartol, N. Cyber supply chain security practices DNA—Filling in the puzzle using a diverse set of disciplines. Technovation 2014, 34, 354–361. [Google Scholar] [CrossRef]
- Windelberg, M. Objectives for managing cyber supply chain risk. Int. J. Crit. Infrastruct. Prot. 2016, 12, 4–11. [Google Scholar] [CrossRef]
- Bode, C.; Wagner, S.M. Structural drivers of upstream supply chain complexity and the frequency of supply chain disruptions. J. Oper. Manag. 2015, 36, 215–228. [Google Scholar] [CrossRef]
- Boyens, J.M.; Paulsen, C.; Bartol, N.; Winkler, K.; Gimbi, J. Case Studies in Cyber Supply Chain Risk Management: Summary of Findings and Recommendations; Technology Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020. [Google Scholar]
- Davis, A. Building Cyber-Resilience into Supply Chains. Technol. Innov. Manag. Rev. 2015, 5, 19–27. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Luecking, M. The convergence of IoT and distributed ledger technologies (DLT): Opportunities, challenges, and solutions. J. Netw. Comput. Appl. 2021, 177, 102936. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 11 February 2012).
- Buterin, V. Bitcoin Network Shaken by Blockchain Fork. Bitcoinmagazine. 2013. Available online: https://bitcoinmagazine.com/articles/bitcoin-network-shaken-by-blockchain-fork1363144448/ (accessed on 15 January 2020).
- Buterin, V. DAOs, DACs, DAs and More: An Incomplete Terminology Guide. Ethereum Blog. 2014. Available online: https://blog.ethereum.org/2014/05/06/daos-dacs-das-and-more-an-incomplete-terminologyguide/ (accessed on 2 March 2021).
- Ackermann, J.; Meier, M. Blockchain 3.0—The next generation of blockchain systems. In Proceedings of the Advanced Seminar Blockchain Technologies, Munich, Germany, September 2018; pp. 1–7. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Futur. Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
- Pajooh, H.H.; Rashid, M.; Alam, F.; Demidenko, S. Hyperledger Fabric Blockchain for Securing the Edge Internet of Things. Sensors 2021, 21, 359. [Google Scholar] [CrossRef]
- Swan, M. Climate Change 2013—The Physical Science Basis. In Blockchain: Blueprint for a New Economy; O’Reilly Media, Inc.: Newton, MA, USA, 2015. [Google Scholar]
- Kamble, S.; Gunasekaran, A.; Arha, H. Understanding the Blockchain technology adoption in supply chains-Indian context. Int. J. Prod. Res. 2019, 57, 2009–2033. [Google Scholar] [CrossRef]
- Liu, X.; Farahani, B.; Firouzi, F. Distributed Ledger Technology. In Intelligent Internet of Things; Springer: Berlin/Heidelberg, Germany, 2020; pp. 393–431. [Google Scholar]
- Van Engelenburg, S.; Janssen, M.; Klievink, B. Design of a software architecture supporting business-to-government information sharing to improve public safety and security. J. Intell. Inf. Syst. 2017, 52, 595–618. [Google Scholar] [CrossRef]
- Merkle, R.C. A digital signature based on a conventional encryption function. In Advances in Cryptology—CRYPT0 87, Lecture Notes in Computer Science; Pomerance, C., Ed.; Springer: Berlin/Heidelberg, Germany, 1987; Volume 369. [Google Scholar] [CrossRef]
- Luu, L.; Narayanan, V.; Baweja, K.; Zheng, C.; Gilbert, S.; Saxena, P. SCP: A Computationally-Scalable Byzantine Consensus Protocol for Blockchains. IACR Cryptol. ePrint Arch. 2015, 20, 1168. [Google Scholar]
- Dinh, T.T.A.; Wang, J.; Chen, G.; Liu, R.; Ooi, B.C.; Tan, K.-L. BLOCKBENCH. In Proceedings of the 2017 ACM International Conference on Interactive Experiences for TV and Online Video, Hilversum, The Netherlands, 14–16 June 2017; ACM: New York, NY, USA, 2017. [Google Scholar]
- Anderberg, A.; Andonova, E.; Bellia, M.; Calès, L.; Inamorato Dos Santos, A.; Kounelis, I.; Nai Fovino, I.; Petracco Giudici, M.; Papanagiotou, E.; Sobolewski, M.; et al. Blockchain Now And Tomorrow; EUR 29813 EN; Publications Office of the European Union: Luxembourg, 2019; ISBN 978-92-76-08977-3. [Google Scholar]
- Tapscott, A.; Tapscott, D. How Blockchain is changing finance. Harvard Business Review. 1 March 2017. Available online: https://hbr.org/2017/03/howBlockchain-is-changing-finance (accessed on 5 April 2020).
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352. [Google Scholar] [CrossRef]
- Yadav, S.; Singh, S.P. An integrated fuzzy-ANP and fuzzy-ISM approach using blockchain for sustainable supply chain. J. Enterp. Inf. Manag. 2020, 34, 54–78. [Google Scholar] [CrossRef]
- Kissel, R. Glossary of Key Information Security Terms, NIST Interagency/Internal Report (NISTIR)–7298rev2. 5 June 2013. [Google Scholar]
- Etemadi, N.; Borbon-Galvez, Y.; Strozzi, F.; Etemadi, T. Supply Chain Disruption Risk Management with Blockchain: A Dynamic Literature Review. Information 2021, 12, 70. [Google Scholar] [CrossRef]
- Piscini, E.D.D. Blockchain & cyber security. Let’s Discuss. Available online: https://www2.deloitte.com/content/dam/Deloitte/ie/Documents/Technology/IE_C_BlockchainandCyberPOV_0417.pdf (accessed on 3 March 2021).
- Pilkington, M. Blockchain technology: Principles and applications. In Re-search Handbook on Digital Transformations; Edward Elgar Publishing: Cheltenham, UK, 2016. [Google Scholar]
- IBM. Blockchain. 2017. Available online: https://www.ibm.com/blockchain/what-is-blockchain.html (accessed on 9 February 2021).
- Zeng, Z.; Li, Y.; Cao, Y.; Zhao, Y.; Zhong, J.; Sidorov, D.; Zeng, X. Blockchain Technology for Information Security of the Energy Internet: Fundamentals, Features, Strategy and Application. Energies 2020, 13, 881. [Google Scholar] [CrossRef]
- Tian, F. A supply chain traceability system for food safety based on HACCP, blockchain & Internet of things. In Proceedings of the 2017 International Conference on Service Systems and Service Management, Dalian, China, 16–18 June 2017; pp. 1–6. [Google Scholar]
- Galvez, J.F.; Mejuto, J.; Simal-Gandara, J. Future challenges on the use of blockchain for food traceability analysis. TrAC Trends Anal. Chem. 2018, 107, 222–232. [Google Scholar] [CrossRef]
- Abeyratne, S.A.; Monfared, R.P. Blockchain Ready Manufacturing Supply Chain Using Distributed Ledger. Int. J. Res. Eng. Technol. 2016, 5, 1–10. [Google Scholar]
- Etemadi, N.; Borbon, Y.G.; Strozzi, F. Blockchain technology for cybersecurity applications in the food supply chain: A systematic literature review. In Proceedings of the XXIV Summer School “Francesco Turco”—Industrial Systems Engi-neering, Bergamo, Italy, 9–11 September 2020. [Google Scholar]
- Kshetri, N. Will blockchain emerge as a tool to break the poverty chain in the Global South? Third World Q. 2016, 38, 1710–1732. [Google Scholar] [CrossRef]
- Feng, H.; Wang, X.; Duan, Y.; Zhang, J.; Zhang, X. Applying blockchain technology to improve agri-food traceability: A review of development methods, benefits and challenges. J. Clean. Prod. 2020, 260, 121031. [Google Scholar] [CrossRef]
- Ge, L.; Brewster, C.; Spek, J.; Smeenk, A.; Top, J.; Van Diepen, F.; Klaase, B.; Graumans, C.; Wildt, M.D.R.D.; FBR Supply Chain & Information Management. Blockchain for Agriculture and Food: Findings from the Pilot Study; Wageningen University and Research: Wageningen, The Netherlands, 2017. [Google Scholar]
- Politou, E.; Casino, F.; Alepis, E.; Patsakis, C. Blockchain Mutability: Challenges and Proposed Solutions. IEEE Trans. Emerg. Top. Comput. 2019, 1. [Google Scholar] [CrossRef]
- Korpela, K.; Hallikas, J.; Dahlberg, T. Digital Supply Chain Transformation toward Blockchain Integration. In Proceedings of the Proceedings of the 50th Hawaii International Conference on System Sciences (2017), Waikoloa, HI, USA, 4–7 January 2017. [Google Scholar]
- Yadav, S.; Singh, S.P. Blockchain critical success factors for sustainable supply chain. Resour. Conserv. Recycl. 2020, 152, 104505. [Google Scholar] [CrossRef]
- Rathod, N.; Motwani, D. Security Threats on Blockchain and its Countermeasures. Int. Res. J. Eng. Technol 2018, 5, 1636–1642. [Google Scholar]
- Treiblmaier, H. The impact of the blockchain on the supply chain: A theory-based research framework and a call for action. Supply Chain Manag. Int. J. 2018, 23, 545–559. [Google Scholar] [CrossRef]
- Wang, Y.; Han, J.H.; Beynon-Davies, P. Understanding blockchain technology for future supply chains: A systematic literature review and research agenda. Supply Chain Manag. Int. J. 2019, 24, 62–84. [Google Scholar] [CrossRef]
- Sulkowski, A.J. Blockchain, Business Supply Chains, Sustainability, and Law: The Future of Governance, Legal Frameworks, and Lawyers? SSRN Electron. J. 2018. [Google Scholar] [CrossRef]
- Rouhani, S.; Pourheidari, V.; Deters, R. Physical Access Control Management System Based on Permissioned Blockchain. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2018; pp. 1078–1083. [Google Scholar]
- Fernandez-Carames, T.M.; Fraga-Lamas, P. A Review on the Application of Blockchain to the Next Generation of Cybersecure Industry 4.0 Smart Factories. IEEE Access 2019, 7, 45201–45218. [Google Scholar] [CrossRef]
- Sittón-Candanedo, I.; Alonso, R.S.; Corchado, J.M.; Rodríguez-González, S.; Casado-Vara, R. A review of edge computing reference architectures and a new global edge proposal. Futur. Gener. Comput. Syst. 2019, 99, 278–294. [Google Scholar] [CrossRef]
- Kshetri, N. Can Blockchain Strengthen the Internet of Things? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef]
- Gu, J.; Sun, B.; Du, X.; Wang, J.; Zhuang, Y.; Wang, Z. Consortium Blockchain-Based Malware Detection in Mobile Devices. IEEE Access 2018, 6, 12118–12128. [Google Scholar] [CrossRef]
- Huang, J.; Kong, L.; Chen, G.; Wu, M.-Y.; Liu, X.; Zeng, P. Towards Secure Industrial IoT: Blockchain System With Credit-Based Consensus Mechanism. IEEE Trans. Ind. Inform. 2019, 15, 3680–3689. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Abbas, H.; Ni, W. Blockchain’s adoption in IoT: The challenges, and a way forward. J. Netw. Comput. Appl. 2019, 125, 251–279. [Google Scholar] [CrossRef]
- Mao, D.; Hao, Z.; Wang, F.; Li, H. Novel Automatic Food Trading System Using Consortium Blockchain. Arab. J. Sci. Eng. 2019, 44, 3439–3455. [Google Scholar] [CrossRef]
- Sylim, P.; Liu, F.; Marcelo, A.; Fontelo, P. Blockchain Technology for Detecting Falsified and Substandard Drugs in Distribution: Pharmaceutical Supply Chain Intervention. JMIR Res. Protoc. 2018, 7, e10163. [Google Scholar] [CrossRef] [PubMed]
- Salah, D.; Ahmed, M.H.; ElDahshan, K. Blockchain Applications in Human Resources Management. In Proceedings of the Proceedings of the Evaluation and Assessment in Software Engineering, Trondheim, Norway, 15–17 April 2020; ACM: New York, NY, USA, 2020. [Google Scholar]
- Yi, C.S.S.; Yung, E.; Fong, C.; Tripathi, S. Benefits and Use of Blockchain Technology to Human Resources Management: A Critical Review. Int. J. Hum. Resour. Stud. 2020, 10, 131–140. [Google Scholar] [CrossRef]
- Khan, S.; Khan, R. Multiple Authorities Attribute-Based Verification Mechanism for Blockchain Mircogrid Transactions. Energies 2018, 11, 1154. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of Things—New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Azbeg, K.; Ouchetto, O.; Andaloussi, S.J.; Fetjah, L.; Sekkaki, A. Blockchain and IoT for Security and Privacy: A Platform for Diabetes Self-management. In Proceedings of the 2018 4th International Conference on Cloud Computing Technologies and Applications (Cloudtech), Brussels, Belgium, 26–28 November 2018; pp. 1–5. [Google Scholar]
- Acharjamayum, I.; Patgiri, R.; Devi, D. Blockchain: A Tale of Peer to Peer Security. In Proceedings of the 2018 IEEE Symposium Series on Computational Intelligence (SSCI), Bangalore, India, 18–21 November 2018; Institute of Electrical and Electronics Engineers (IEEE) Symposium Series on Computational Intelligence (SSCI): Piscataway Township, NJ, USA, 2018; pp. 609–617. [Google Scholar]
- Sinha, U.; Hadi, A.A.; Faika, T.; Kim, T. Blockchain-Based Communication and Data Security Framework for IoT-Enabled Micro Solar Inverters. In 2019 IEEE CyberPELS (CyberPELS); Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Big Island, HI, USA, 13–17 March 2017; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2017; pp. 618–623. [Google Scholar]
- Meng, W.; Tischhauser, E.W.; Wang, Q.; Wang, Y.; Han, J. When Intrusion Detection Meets Blockchain Technology: A Review. IEEE Access 2018, 6, 10179–10188. [Google Scholar] [CrossRef]
- Chawathe, S. Monitoring Blockchains with Self-Organizing Maps. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2018; pp. 1870–1875. [Google Scholar]
- Miers, I.; Garman, C.; Green, M.; Rubin, A.D. Zerocoin: Anonymous Distributed E-Cash from Bitcoin. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2013; pp. 397–411. [Google Scholar]
- Ben Sasson, E.; Chiesa, A.; Garman, C.; Green, M.; Miers, I.; Tromer, E.; Virza, M. Zerocash: Decentralized Anonymous Payments from Bitcoin. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2014; pp. 459–474. [Google Scholar]
- Ucci, D.; Aniello, L.; Baldoni, R. Survey of machine learning techniques for malware analysis. Comput. Secur. 2019, 81, 123–147. [Google Scholar] [CrossRef]
- Biryukov, A.; Khovratovich, D.; Pustogarov, I. Deanonymisation of Clients in Bitcoin P2P Network. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; ACM: New York, NY, USA, 2014; pp. 15–29. [Google Scholar]
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 6–10. [Google Scholar]
- Xie, J.; Tang, H.; Huang, T.; Yu, F.R.; Xie, R.; Liu, J.; Liu, Y. A Survey of Blockchain Technology Applied to Smart Cities: Research Issues and Challenges. IEEE Commun. Surv. Tutor. 2019, 21, 2794–2830. [Google Scholar] [CrossRef]
- Yuan, R.; Xia, Y.-B.; Chen, H.-B.; Zang, B.-Y.; Xie, J. ShadowEth: Private Smart Contract on Public Blockchain. J. Comput. Sci. Technol. 2018, 33, 542–556. [Google Scholar] [CrossRef]
- De Haro-Olmo, F.J.; Varela-Vaca, Á.J.; Álvarez-Bermejo, J.A. Blockchain from the Perspective of Privacy and Anonymisation: A Systematic Literature Review. Sensors 2020, 20, 7171. [Google Scholar] [CrossRef] [PubMed]
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The Blockchain Model of Cryptography and Privacy-Preserving Smart Contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Veit, D.J.; Weinhardt, C. Enterprise, applications and services in the finance industry. Inf. Syst. e-Business Manag. 2007, 5, 139–141. [Google Scholar] [CrossRef]
- Comelli, M.; Fenies, P.; Tchernev, N. A combined financial and physical flows evaluation for logistic process and tactical production planning: Application in a company supply chain. Int. J. Prod. Econ. 2008, 112, 77–95. [Google Scholar] [CrossRef]
- Nguyen, Q.K. Blockchain—A Financial Technology for Future Sustainable Development. In Proceedings of the 2016 3rd International Conference on Green Technology and Sustainable Development (GTSD), Kaohsiung, Taiwan, 24–25 November 2016; pp. 51–54. [Google Scholar]
- Augur, The Augur Project. Available online: https://augur.net/ (accessed on 16 May 2020).
- Poon, J.; Buterin, V. Plasma: Scalable Autonomous Smart Contracts. White Pap. 2017, 206, 1–47. [Google Scholar]
- Gnosis.io. Available online: https://gnosis.io/ (accessed on 27 July 2020).
- Hewett, N.; Lehmacher, W.; Wang, Y. Inclusive Deployment of Blockchain for Supply Chains: Part 5—A Framework for Blockchain Cybersecurity; World Economic Forum: Geneva, Switzerland, 2019. [Google Scholar]
- Kshetri, N. 1 Blockchain’s roles in meeting key supply chain management objectives. Int. J. Inf. Manag. 2018, 39, 80–89. [Google Scholar] [CrossRef]
- Wamba, S.F.; Queiroz, M.M.; Trinchera, L. Dynamics between blockchain adoption determinants and supply chain performance: An empirical investigation. Int. J. Prod. Econ. 2020, 229, 107791. [Google Scholar] [CrossRef]
- Kayikci, Y.; Subramanian, N.; Dora, M.; Bhatia, M.S. Food supply chain in the era of Industry 4.0: Blockchain technology implementation opportunities and impediments from the perspective of people, process, performance, and technology. Prod. Plan. Control. 2020, 1–21. [Google Scholar] [CrossRef]
- Hackius, N.; Petersen, M. Blockchain in logistics and supply chain: Trick or treat? In Proceeding of the Hamburg international conference of logistics; HICL: Hamburg, Germany, 2017. [Google Scholar]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Kamble, S.S.; Gunasekaran, A.; Sharma, R. Modeling the blockchain enabled traceability in agriculture supply chain. Int. J. Inf. Manag. 2020, 52, 101967. [Google Scholar] [CrossRef]
- Choi, D.; Chung, C.; Seyha, T.; Young, J. Factors Affecting Organizations’ Resistance to the Adoption of Blockchain Technology in Supply Networks. Sustainability 2020, 12, 8882. [Google Scholar] [CrossRef]
- Sahebi, I.G.; Masoomi, B.; Ghorbani, S. Expert oriented approach for analyzing the blockchain adoption barriers in humanitarian supply chain. Technol. Soc. 2020, 63, 101427. [Google Scholar] [CrossRef]
- Dutta, P.; Choi, T.-M.; Somani, S.; Butala, R. Blockchain technology in supply chain operations: Applications, challenges and research opportunities. Transp. Res. Part E Logist. Transp. Rev. 2020, 142, 102067. [Google Scholar] [CrossRef]
- Yli-Huumo, J.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where is current research on blockchain technology—A systematic review. PLoS ONE 2016, 11, e0163477. [Google Scholar] [CrossRef]
- O’Leary, D.E. Configuring blockchain architectures for transaction information in blockchain consortiums: The case of accounting and supply chain systems. Intell. Syst. Account. Financ. Manag. 2017, 24, 138–147. [Google Scholar] [CrossRef]
- Öztürk, C.; Yildizbaşi, A. Barriers to implementation of blockchain into supply chain management using an integrated multi-criteria decision-making method: A numerical example. Soft Comput. 2020, 24, 14771–14789. [Google Scholar] [CrossRef]
- Cao, B.; Zhang, Z.; Feng, D.; Zhang, S.; Zhang, L.; Peng, M.; Li, Y. Performance analysis and comparison of PoW, PoS and DAG based blockchains. Digit. Commun. Netw. 2020, 6, 480–485. [Google Scholar] [CrossRef]
- Brasil. Decreto—Lei nº 227, de 28 de fevereiro de Dá nova redação ao Decreto-lei nº 1.985, de 29 de janeiro de 1940 (Código de Minas). Brasília. Available online: http://www.planalto.gov.br/ccivil_03/Decreto-Lei/Del0227.htm (accessed on 19 October 2020).
- Baliga, A. Understanding Blockchain Consensus Models. Available online: https://pdfs.semanticschol-ar.org/da8a/37b10bc1521a4d3de925d7ebc44bb606d740.pdf (accessed on 29 June 2017).
- Karame, G. On the Security and Scalability of Bitcoin’s Blockchain. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; ACM: New York, NY, USA, 2016; pp. 1861–1862. [Google Scholar]
- Cho, S.; Park, S.Y.; Lee, S.R. Blockchain Consensus Rule Based Dynamic Blind Voting for Non-Dependency Transaction. Int. J. Grid Distrib. Comput. 2017, 10, 93–106. [Google Scholar] [CrossRef]
- Geraci, A.; Katki, F.; McMonegal, L.; Meyer, B.; Lane, J.; Wilson, P.; Radatz, J.; Yee, M.; Porteous, H.; Springsteel, F. IEEE Standard Computer Dictionary: Compilation of IEEE Standard Computer Glossaries; IEEE Press: Piscataway Township, NJ, USA, 1991. [Google Scholar]
- Scott, C.R. Benefits and Drawbacks of Anonymous Online Communication: Legal Challenges and Communicative Recommendations. Free. Speech Yearb. 2004, 41, 127–141. [Google Scholar] [CrossRef]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the Security and Performance of Proof of Work Blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; Association for Computing Machinery (ACM): New York, NY, USA, 2016; Volume 2016, pp. 3–16. [Google Scholar]
- O’Leary, D.E. Open Information Enterprise Transactions: Business Intelligence and Wash and Spoof Transactions in Blockchain and Social Commerce. Intell. Syst. Account. Financ. Manag. 2018, 25, 148–158. [Google Scholar] [CrossRef]
- Rahouti, M.; Xiong, K.; Ghani, N. Bitcoin Concepts, Threats, and Machine-Learning Security Solutions. IEEE Access 2018, 6, 67189–67205. [Google Scholar] [CrossRef]
- Etemadi, N.v.G.P.; Strozzi, F. An ISM Modelling of Success Factors for Blockchain Adoption in a Cyber Secure Supply Chain. In Proceedings of the 4th International Conference on Computers in Management and Business, ICCMB 2021, Singapore, January 30–February 1 2021; ACM: New York, NY, USA. [Google Scholar] [CrossRef]
- Al-Jaroodi, J.; Mohamed, N. Blockchain in Industries: A Survey. IEEE Access 2019, 7, 36500–36515. [Google Scholar] [CrossRef]
- Khan, F. What is the “Oracle Problem” and How Does Chainlink Solve It? Available online: www.datadriveninves-tor.com/2019/06/15/what-is-the-oracle-problem-how-does-chainlink-solve-it/ (accessed on 23 February 2021).
- Damjan, M. The interface between blockchain and the real world. Ragion Pratica 2018. [Google Scholar] [CrossRef]
- Kamilaris, A.; Fonts, A.; Prenafeta-Boldύ, F.X. The rise of blockchain technology in agriculture and food supply chains. Trends Food Sci. Technol. 2019, 91, 640–652. [Google Scholar] [CrossRef]
- Gonczol, P.; Katsikouli, P.; Herskind, L.; Dragoni, N. Blockchain Implementations and Use Cases for Supply Chains–A Survey. IEEE Access 2020, 8, 11856–11871. [Google Scholar] [CrossRef]
- Kosmarski, A. Blockchain Adoption in Academia: Promises and Challenges. J. Open Innov. Technol. Mark. Complex. 2020, 6, 117. [Google Scholar] [CrossRef]
- Li, J.; Maiti, A.; Springer, M.; Gray, T. Blockchain for supply chain quality management: Challenges and opportunities in context of open manufacturing and industrial internet of things. Int. J. Comput. Integr. Manuf. 2020, 33, 1321–1355. [Google Scholar] [CrossRef]
- Siegfried, N.; Rosenthal, T.; Benlian, A. Blockchain and the Industrial Internet of Things. J. Enterp. Inf. Manag. 2020. [Google Scholar] [CrossRef]
- Zhou, Y.; Soh, Y.S.; Loh, H.S.; Yuen, K.F. The key challenges and critical success factors of blockchain implementation: Policy implications for Singapore’s maritime industry. Mar. Policy 2020, 122, 104265. [Google Scholar] [CrossRef]
- Chang, V.; Baudier, P.; Zhang, H.; Xu, Q.; Zhang, J.; Arami, M. How Blockchain can impact financial services—The overview, challenges and recommendations from expert interviewees. Technol. Forecast. Soc. Chang. 2020, 158, 120166. [Google Scholar] [CrossRef]
- Shardeo, V.; Patil, A.; Madaan, J. Critical Success Factors for Blockchain Technology Adoption in Freight Transportation Using Fuzzy ANP–Modified TISM Approach. Int. J. Inf. Technol. Decis. Mak. 2020, 19, 1549–1580. [Google Scholar] [CrossRef]
- Morkunas, V.J.; Paschen, J.; Boon, E. How blockchain technologies impact your business model. Bus. Horiz. 2019, 62, 295–306. [Google Scholar] [CrossRef]
- Scott, B.; Loonam, J.; Kumar, V. Exploring the rise of blockchain technology: Towards distributed collaborative organizations. Strat. Chang. 2017, 26, 423–428. [Google Scholar] [CrossRef]
- Holotiuk, F.; Pisani, F.; Moormann, J. Radicalness of blockchain: An assessment based on its impact on the payments industry. Technol. Anal. Strat. Manag. 2019, 31, 915–928. [Google Scholar] [CrossRef]
- Abu-Elezz, I.; Hassan, A.; Nazeemudeen, A.; Househ, M.; Abd-Alrazaq, A. The benefits and threats of blockchain technology in healthcare: A scoping review. Int. J. Med Inform. 2020, 142, 104246. [Google Scholar] [CrossRef]
- Ghode, D.; Yadav, V.; Jain, R.; Soni, G. Adoption of blockchain in supply chain: An analysis of influencing factors. J. Enterp. Inf. Manag. 2020, 33, 437–456. [Google Scholar] [CrossRef]
- Upadhyay, A.; Ayodele, J.O.; Kumar, A.; Garza-Reyes, J.A. A review of challenges and opportunities of blockchain adoption for operational excellence in the UK automotive industry. J. Glob. Oper. Strat. Sourc. 2020, 14, 7–60. [Google Scholar] [CrossRef]
- Tanwar, S.; Bhatia, Q.; Patel, P.; Kumari, A.; Singh, P.K.; Hong, W.-C. Machine Learning Adoption in Blockchain-Based Smart Applications: The Challenges, and a Way Forward. IEEE Access 2020, 8, 474–488. [Google Scholar] [CrossRef]
- Kouhizadeh, M.; Saberi, S.; Sarkis, J. Blockchain technology and the sustainable supply chain: Theoretically exploring adoption barriers. Int. J. Prod. Econ. 2021, 231, 107831. [Google Scholar] [CrossRef]
- Chang, S.E.; Chen, Y.-C.; Lu, M.-F. Supply chain re-engineering using blockchain technology: A case of smart contract based tracking process. Technol. Forecast. Soc. Chang. 2019, 144, 1–11. [Google Scholar] [CrossRef]
- Mendling, J.; Weber, I.; Van Der Aalst, W.; Brocke, J.V.; Cabanillas, C.; Daniel, F.; Debois, S.; Di Ciccio, C.; Dumas, M.; Dustdar, S.; et al. Blockchains for Business Process Management—Challenges and Opportunities. ACM Trans. Manag. Inf. Syst. 2018, 9, 1–16. [Google Scholar] [CrossRef]
- Saberi, S.; Kouhizadeh, M.; Sarkis, J. Blockchains and the Supply Chain: Findings from a Broad Study of Practitioners. IEEE Eng. Manag. Rev. 2019, 47, 95–103. [Google Scholar] [CrossRef]
- Alkhater, N.; Walters, R.; Wills, G. An empirical study of factors influencing cloud adoption among private sector organisations. Telemat. Inform. 2018, 35, 38–54. [Google Scholar] [CrossRef]
- Shin, N.; Park, S. Evidence-Based Resilience Management for Supply Chain Sustainability: An Interpretive Structural Modelling Approach. Sustainability 2019, 11, 484. [Google Scholar] [CrossRef]
- Van Alstyne, M. Why Bitcoin has value. Commun. ACM 2014, 57, 30–32. [Google Scholar] [CrossRef]
- Böhme, R. Internet Protocol Adoption: Learning from Bitcoin; IAB Workshop on Internet Technology Adoption and Transition (ITAT): Cambridge, UK, 2018. [Google Scholar]
- Alharby, M.; Van Moorsel, A. Blockchain Based Smart Contracts: A Systematic Mapping Study. arXiv 2017, arXiv:1710.06372. [Google Scholar]
- Chen, G.; Xu, B.; Lu, M.; Chen, N.-S. Exploring blockchain technology and its potential applications for education. Smart Learn. Environ. 2018, 5, 1. [Google Scholar] [CrossRef]
- Dolev, S.; Wang, Z. SodsBC: Stream of Distributed Secrets for Quantum-safe Blockchain. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2020; pp. 247–256. [Google Scholar]
- Singh, A.; Teng, J.T. Enhancing supply chain outcomes through Information Technology and Trust. Comput. Hum. Behav. 2016, 54, 290–300. [Google Scholar] [CrossRef]
- Chen, S.; Shi, R.; Ren, Z.; Yan, J.; Shi, Y.; Zhang, J. A Blockchain-Based Supply Chain Quality Management Framework. In Proceedings of the 2017 IEEE 14th International Conference on e-Business Engineering (ICEBE), Shanghai, China, 4–6 November 2017; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2017; Volume 207, pp. 172–176. [Google Scholar]
- Ghode, D.J.; Yadav, V.; Jain, R.; Soni, G. Blockchain adoption in the supply chain: An appraisal on challenges. J. Manuf. Technol. Manag. 2020, 32, 42–62. [Google Scholar] [CrossRef]
- Seebacher, S.; Maleshkova, M. A Model-driven Approach for the Description of Blockchain Business Networks. In Proceedings of the 51th Hawaii International Conference on System Sciences, Waikoloa, HI, USA, 3 January 2018; pp. 3487–3496. [Google Scholar]
- Helo, P.; Hao, Y. Blockchains in operations and supply chains: A model and reference implementation. Comput. Ind. Eng. 2019, 136, 242–251. [Google Scholar] [CrossRef]
- Kurpjuweit, S.; Schmidt, C.G.; Klöckner, M.; Wagner, S.M. Blockchain in Additive Manufacturing and its Impact on Supply Chains. J. Bus. Logist. 2019, 1–25. [Google Scholar] [CrossRef]
- Gökalp, E.; Gökalp, M.O.; Çoban, S. Blockchain-Based Supply Chain Management: Understanding the Determinants of Adoption in the Context of Organizations. Inf. Syst. Manag. 2020, 1–22. [Google Scholar] [CrossRef]
- Kumar, R.; Tahir, M.F.; Kumar, S.; Zia, A.; Memon, H.; Mahmood, W. Challenges in Adoption of Blockchain in Developing Countries. In Proceedings of the 2019 4th International Conference on Emerging Trends in Engineering, Sciences and Technology (ICEEST), Karachi, Pakistan, 10–11 December 2019; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2019; pp. 1–8. [Google Scholar]
- Ramdani, B.; Kawalek, P.; Lorenzo, O. Predicting SMEs’ adoption of enterprise systems. J. Enterp. Inf. Manag. 2009, 22, 10–24. [Google Scholar] [CrossRef]
- Bernik, I.; Prislan, K. Measuring Information Security Performance with 10 by 10 Model for Holistic State Evaluation. PLoS ONE 2016, 11, e0163050. [Google Scholar] [CrossRef] [PubMed]
- Wüst, K.; Gervais, A. Do you need a Blockchain? In Proceedings of the 2018 Crypto Val. Conf. Blockchain Technology, Zug, Switzerland, 20–22 June 2018; pp. 45–54. [Google Scholar] [CrossRef]
- Lo, S.K.; Xu, X.; Chiam, Y.K.; Lu, Q. Evaluating Suitability of Applying Blockchain. In Proceedings of the 2017 22nd International Conference on Engineering of Complex Computer Systems (ICECCS), Fukuoka, Japan, 5–8 November 2017; Institute of Electrical and Electronics Engineers (IEEE): Piscataway Township, NJ, USA, 2017; pp. 158–161. [Google Scholar]
- Mann, S.; Potdar, V.; Gajavilli, R.S.; Chandan, A. Blockchain Technology for Supply Chain Traceability, Transparency and Data Provenance. In Proceedings of the 2018 International Conference on Blockchain Technology and Application—ICBTA 2018, Xi’an, China, 10–12 December 2018; ACM: New York, NY, USA, 2018; pp. 22–26. [Google Scholar]
- Luu, L.; Chu, D.-H.; Olickel, H.; Saxena, P.; Hobor, A. Making Smart Contracts Smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; Association for Computing Machinery (ACM): New York, NY, USA, 2016; pp. 254–269. [Google Scholar]
- NIST’s Second Round Announcement Call for Proposals PostQuantum Cryptosystems. Available online: https://csrc.nist.gov/news/2019/pqc-standardization-process-2nd-roundcandidates (accessed on 3 March 2021).
- Erol, I.; Ar, I.M.; Ozdemir, A.I.; Peker, I.; Asgary, A.; Medeni, I.T.; Medeni, T. Assessing the feasibility of blockchain technology in industries: Evidence from Turkey. J. Enterp. Inf. Manag. 2020. [Google Scholar] [CrossRef]
- Hileman, G.; Rauchs, M. Global Blockchain Benchmarking Study. SSRN Electron. J. 2017. [Google Scholar] [CrossRef]
- Davies, S.; Likens, S. Blockchain is Here: What’s Your Next Move? Pwc.com. 2019. Available online: https://www.pwc.com/gx/en/issues/blockchain/blockchain-in-business.html (accessed on 13 March 2021).
- Govindan, K.; Kannan, G.; Haq, A.N. Analyzing supplier development criteria for an automobile industry. Ind. Manag. Data Syst. 2010, 110, 43–62. [Google Scholar] [CrossRef]
- Toktaş-Palut, P.; Baylav, E.; Teoman, S.; Altunbey, M. The impact of barriers and benefits of e-procurement on its adoption decision: An empirical analysis. Int. J. Prod. Econ. 2014, 158, 77–90. [Google Scholar] [CrossRef]
- Bolaños, R.; Fontela, E.; Nenclares, A.; Pastor, P. Using interpretive structural modelling in strategic decision-making groups. Manag. Decis. 2005, 43, 877–895. [Google Scholar] [CrossRef]
- Govindan, K.; Azevedo, S.G.; Carvalho, H.; Cruz-Machado, V. Lean, green and resilient practices influence on supply chain performance: Interpretive structural modeling approach. Int. J. Environ. Sci. Technol. 2015, 12, 15–34. [Google Scholar] [CrossRef]
- Warfield, J.N. Implication Structures for System Interconnection Matrices. IEEE Trans. Syst. Man Cybern. 1976, SMC-6, 18–24. [Google Scholar] [CrossRef]
- Pandey, V.; Garg, S. Analysis of interaction among the enablers of agility in supply chain. J. Adv. Manag. Res. 2009, 6, 99–114. [Google Scholar] [CrossRef]
- Ruiz-Benítez, R.; López, C.; Real, J.C. The lean and resilient management of the supply chain and its impact on performance. Int. J. Prod. Econ. 2018, 203, 190–202. [Google Scholar] [CrossRef]
- Prasad, S.; Shankar, R.; Gupta, R.; Roy, S. A TISM modeling of critical success factors of blockchain based cloud services. J. Adv. Manag. Res. 2018, 15, 434–456. [Google Scholar] [CrossRef]
- Yadav, V.S.; Singh, A.; Raut, R.D.; Govindarajan, U.H. Blockchain technology adoption barriers in the Indian agricultural supply chain: An integrated approach. Resour. Conserv. Recycl. 2020, 161, 104877. [Google Scholar] [CrossRef]
- Godet, M. From Anticipation to Action: A Handbook of Strategic Prospective; UNESCO Publishing: Paris, France, 1993. [Google Scholar]
| Challenge No. | Challenge Names | References |
|---|---|---|
| 3.1 | Immature, an early stage of development | [78,122,145,146,147] |
| 3.2 | Scalability and bandwidth issues | [108,127,148,149,150] |
| 3.3 | Wasted resources or high energy consumption | [100,130,151,152] |
| 3.4 | Throughput and Low performance | [72,145,146,153] |
| 3.5 | Lack of standardization and interoperability | [139,154,155,156,157,158] |
| 3.6 | Privacy and information disclosure issues | [108,123,125,159,160] |
| 3.7 | Criminal activity, malicious attacks | [129,137,152,154,160,161] |
| 3.8 | Dependent on input information from external oracles | [24,45,96,144] |
| 3.9 | Poor user experience | [19,130,162,163] |
| 3.10 | Suitability of blockchain | [123,125,164,165] |
| 3.11 | Cryptocurrency volatility | [24,118,166,167] |
| 3.12 | Smart contract issues | [51,72,168,169] |
| 3.13 | Quantum Resilience | [123,160,170] |
| 3.14 | Lack of trust | [83,164,171,172,173] |
| 3.15 | Users’ credential loss | [118,174] |
| 3.16 | Poor clarity regulatory provisions | [108,147,163,175,176,177] |
| Sr. No. | Barriers | 16 | 15 | 14 | 13 | 12 | 11 | 10 | 9 | 8 | 7 | 6 | 5 | 4 | 3 | 2 | 1 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | Immature, early stage of development | A | V | V | V | V | 0 | V | 0 | 0 | V | V | V | V | V | V | |
| 2 | Scalability and bandwidth issues | A | 0 | V | 0 | 0 | 0 | 0 | 0 | A | V | V | 0 | V | V | ||
| 3 | Wasted resources or high energy consumption | 0 | 0 | V | 0 | 0 | 0 | 0 | 0 | A | 0 | 0 | 0 | V | |||
| 4 | Throughput and Low performance | A | A | V | 0 | A | 0 | A | 0 | A | A | A | A | ||||
| 5 | Lack of standardization and interoperability | A | 0 | A | 0 | A | 0 | 0 | 0 | 0 | V | V | |||||
| 6 | Privacy and information disclosure issues | A | A | V | A | A | V | V | A | A | V | ||||||
| 7 | Criminal activity, malicious attacks | A | A | V | A | A | V | V | A | A | |||||||
| 8 | Dependent on input information from external oracles | A | 0 | V | 0 | V | V | 0 | 0 | ||||||||
| 9 | Poor user experience | A | A | A | 0 | A | 0 | 0 | |||||||||
| 10 | Suitability of blockchain | A | 0 | V | A | A | 0 | ||||||||||
| 11 | Cryptocurrency volatility | A | A | A | A | A | |||||||||||
| 12 | Smart contract issues | A | A | V | 0 | ||||||||||||
| 13 | Quantum Resilience | A | 0 | V | |||||||||||||
| 14 | Lack of trust in new technology | A | A | ||||||||||||||
| 15 | Users’ credential loss | A | |||||||||||||||
| 16 | Poor clarity regulatory provisions |
| Sr. No. | Barriers | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | Immature, early stage of development | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 1 | 1 | 1 | 1 | 0 |
| 2 | Scalability and bandwidth issues | 0 | 1 | 1 | 1 | 0 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 |
| 3 | Wasted resources or high energy consumption | 0 | 0 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 |
| 4 | Throughput and low performance | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 |
| 5 | Lack of standardization and interoperability | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 6 | Privacy and information disclosure issues | 0 | 0 | 0 | 1 | 0 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 0 | 1 | 0 | 0 |
| 7 | Criminal activity, malicious attacks | 0 | 0 | 0 | 1 | 0 | 0 | 1 | 0 | 0 | 1 | 1 | 0 | 0 | 1 | 0 | 0 |
| 8 | Dependent on input information from external oracles | 0 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 1 | 0 | 0 |
| 9 | Poor user experience | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 10 | Suitability of blockchain | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 1 | 0 | 0 |
| 11 | Cryptocurrency volatility | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 |
| 12 | Smart contract issues | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 0 |
| 13 | Quantum resilience | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 1 | 1 | 0 | 0 |
| 14 | Lack of trust in new technology | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 1 | 0 | 0 | 1 | 0 | 0 |
| 15 | Users’ credential loss | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 0 | 0 | 0 | 1 | 1 | 0 |
| 16 | Poor clarity regulatory provisions | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
| Sr. No. | Barriers | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | Driving Power |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | Immature, an early stage of development | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | 14 |
| 2 | Scalability and bandwidth issues | 0 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 10 |
| 3 | Wasted resources or high energy consumption | 0 | 0 | 1 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 9 |
| 4 | Throughput and low performance | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 8 |
| 5 | Lack of standardization and interoperability | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 8 |
| 6 | Privacy and information disclosure issues | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 8 |
| 7 | Criminal activity, malicious attacks | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 8 |
| 8 | Dependent on input information from external oracles | 0 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 0 | 13 |
| 9 | Poor user experience | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 8 |
| 10 | Suitability of blockchain | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 8 |
| 11 | Cryptocurrency volatility | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 1 |
| 12 | Smart contract issues | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 0 | 10 |
| 13 | Quantum resilience | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 1 | 1 | 0 | 0 | 9 |
| 14 | Lack of trust in new technology suppliers | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 8 |
| 15 | Users’ credential loss | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 9 |
| 16 | Poor clarity regulatory provisions | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 16 |
| Dependence Power | 2 | 4 | 5 | 15 | 15 | 15 | 15 | 2 | 15 | 15 | 16 | 4 | 3 | 15 | 5 | 1 | ||
| Iteration No. | Reachability Set | Antecedent Set | Intersection Set | Level |
|---|---|---|---|---|
| Iteration 1 | 1, 2, 3, 4, 5, 6, 7, 9, 10, 11, 12, 13, 14, 15 | 1, 16 | 1 | |
| 2, 3, 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 8, 16 | 2 | ||
| 3, 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 3, 8, 16 | 3 | ||
| 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | ||
| 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | ||
| 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | ||
| 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | ||
| 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 14, 15 | 8, 16 | 8 | ||
| 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | ||
| 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | ||
| 11 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16 | 11 | I | |
| 4, 5, 6, 7, 9, 10, 11, 12, 14, 15 | 1, 8, 12, 16 | 12 | ||
| 4, 5, 6, 7, 9, 10, 11, 13, 14 | 1, 13, 16 | 13 | ||
| 4, 5, 6, 7, 9, 10, 11, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | ||
| 4, 5, 6, 7, 9, 10, 11, 14, 15 | 1, 8, 12, 15, 16 | 15 | ||
| 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16 | 16 | 16 | ||
| Iteration 2 | 1, 2, 3, 4, 5, 6, 7, 9, 10, 12, 13, 14, 15 | 1, 16 | 1 | |
| 2, 3, 4, 5, 6, 7, 9, 10, 14 | 1, 2, 8, 16 | 2 | ||
| 3, 4, 5, 6, 7, 9, 10, 14 | 1, 2, 3, 8, 16 | 3 | ||
| 4, 5, 6, 7, 9, 10, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | II | |
| 4, 5, 6, 7, 9, 10, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | II | |
| 4, 5, 6, 7, 9, 10, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | II | |
| 4, 5, 6, 7, 9, 10, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | II | |
| 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 14, 15 | 8, 16 | 8 | ||
| 4, 5, 6, 7, 9, 10, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | II | |
| 4, 5, 6, 7, 9, 10, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | II | |
| 4, 5, 6, 7, 9, 10, 12, 14, 15 | 1, 8, 12, 16 | 12 | ||
| 4, 5, 6, 7, 9, 10, 13, 14 | 1, 13, 16 | 13 | ||
| 4, 5, 6, 7, 9, 10, 14 | 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 4, 5, 6, 7, 9, 10, 14 | II | |
| 4, 5, 6, 7, 9, 10, 14, 15 | 1, 8, 12, 15, 16 | 15 | ||
| 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 12, 13, 14, 15, 16 | 16 | 16 | ||
| Iteration 3 | 1, 2, 3, 12, 13, 15 | 1, 16 | 1 | |
| 2, 3 | 1, 2, 8, 16 | 2 | ||
| 3 | 1, 2, 3, 8, 16 | 3 | III | |
| 2, 3, 8, 12, 15 | 8, 16 | 8 | ||
| 12, 15 | 1, 8, 12, 16 | 12 | ||
| 13 | 1, 13, 16 | 13 | III | |
| 15 | 1, 8, 12, 15, 16 | 15 | III | |
| 1, 2, 3, 8, 12, 13, 15, 16 | 16 | 16 | ||
| Iteration 4 | 1, 2, 12 | 1, 16 | 1 | |
| 2 | 1, 2, 8, 16 | 2 | IV | |
| 2, 8, 12 | 8, 16 | 8 | ||
| 12 | 1, 8, 12, 16 | 12 | IV | |
| 1, 2, 8, 12, 16 | 16 | 16 | ||
| Iteration 5 | 1 | 1, 16 | 1 | V |
| 8 | 8, 16 | 8 | V | |
| 1, 8, 16 | 16 | 16 | ||
| Iteration 6 | 16 | 16 | 16 | VI |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Etemadi, N.; Van Gelder, P.; Strozzi, F. An ISM Modeling of Barriers for Blockchain/Distributed Ledger Technology Adoption in Supply Chains towards Cybersecurity. Sustainability 2021, 13, 4672. https://doi.org/10.3390/su13094672
Etemadi N, Van Gelder P, Strozzi F. An ISM Modeling of Barriers for Blockchain/Distributed Ledger Technology Adoption in Supply Chains towards Cybersecurity. Sustainability. 2021; 13(9):4672. https://doi.org/10.3390/su13094672
Chicago/Turabian StyleEtemadi, Niloofar, Pieter Van Gelder, and Fernanda Strozzi. 2021. "An ISM Modeling of Barriers for Blockchain/Distributed Ledger Technology Adoption in Supply Chains towards Cybersecurity" Sustainability 13, no. 9: 4672. https://doi.org/10.3390/su13094672
APA StyleEtemadi, N., Van Gelder, P., & Strozzi, F. (2021). An ISM Modeling of Barriers for Blockchain/Distributed Ledger Technology Adoption in Supply Chains towards Cybersecurity. Sustainability, 13(9), 4672. https://doi.org/10.3390/su13094672








