Analyzing the Impact of Cyber Security Related Attributes for Intrusion Detection Systems
Abstract
:1. Introduction
2. Review of Existing Relevant Studies
- S. Bekesiene and colleagues (2021) organized a research endeavor to evaluate distance learning modules through integrated AHP TOPSIS approach under the fuzzy based environment [17]. In this study, three distance learning courses have been evaluated at three level stage assessment namely course structure, quality of information tools, and student opinion. The fuzzy TOPSIS technique was found to be a practical method that delivered an excellent value analysis and ranking, according to the survey data.
- Almotiri (2021) proposed a study to assess the effectiveness of malicious traffic detention systems. In this study, he used AHP-TOPSIS under fuzzy environment to evaluate six malicious traffic detention systems [18]. The Host-based malicious traffic detection strategy (MTD4) was shown to be the most successful and long-lasting malicious traffic detection mechanism among the six alternatives in this investigation.
- Sahu and Colleagues (2020) presented a novel framework for software durability assessment using AHP-TOPOSIS under the hesitant fuzzy conditions [15]. They discovered that trustworthiness and maintainability are two essential and vital qualities for preserving the software durability.
- Agarwal and Colleagues (2020) used well-known patterns, sometimes known as design strategies, to create a fuzzy ANP-TOPSIS evaluation of the university’s various software systems [8]. To analyze the university’s software security, a unique set of security qualities in terms of security techniques was identified and selected.
- Alharbe (2020) conducted a research study for usable-security evaluation of information software systems [12]. For that, he used the MCDM approaches and enunciated guidelines that would help the practitioners in recognizing and prioritizing usable-security attributes while designing and developing the software.
- Kaur and colleagues (2020) worked on the detection and assessment of security risk-factors during web application development; the suggested study employs an adaptive neural fuzzy inference system [19]. This study offers practitioners suggestions for analyzing and prioritizing security concerns in healthcare web apps throughout the early phases of development in order to create safe software solutions.
- Solangi and colleagues (2019) created a system for evaluating the best renewable energy resource for electricity production [10]. Fuzzy-based TOPSIS and Delphi-AHP algorithms were used to conduct this experiment. In this study, wind energy was considered to be the greatest option for generating electricity in Pakistan.
- Goutam and colleagues (2019) proposed a tactic for calculating the vulnerability of online applications [20]. Penetration testing is a technique for identifying software flaws. To establish their security, financial web apps have been submitted to both manual and automated testing. Throughout the study, the results of both vulnerability assessment approaches are nearly identical.
- Sengul and colleagues (2015) developed a fuzzy-TOPSIS-based model to assess Turkey’s renewable energy systems [13]. Shannon’s entropy approach was used to compute the weights of the qualities. In this study, the hydro-power plant was found to be the best renewable energy supply system.
- The significance of hesitant fuzzy sets in MCDM systems was investigated by Qian and colleagues (2013) [14]. According to the findings, generalised HF sets are the best fit for cases when decision makers are confused which membership to choose due to a number of possible memberships with unknown probability.
- Buyukozkan and colleagues (2012) the authors used the integrated AHP-TOPSIS approach under fuzzy conditions to conduct an analytical research on healthcare electronic service quality [21]. Specialization, interactivity, service correctness, dependability, and responsiveness were determined to be the most important characteristics in providing satisfying and effective healthcare web services, according to the study.
3. Machine Learning in Cybersecurity
- (1)
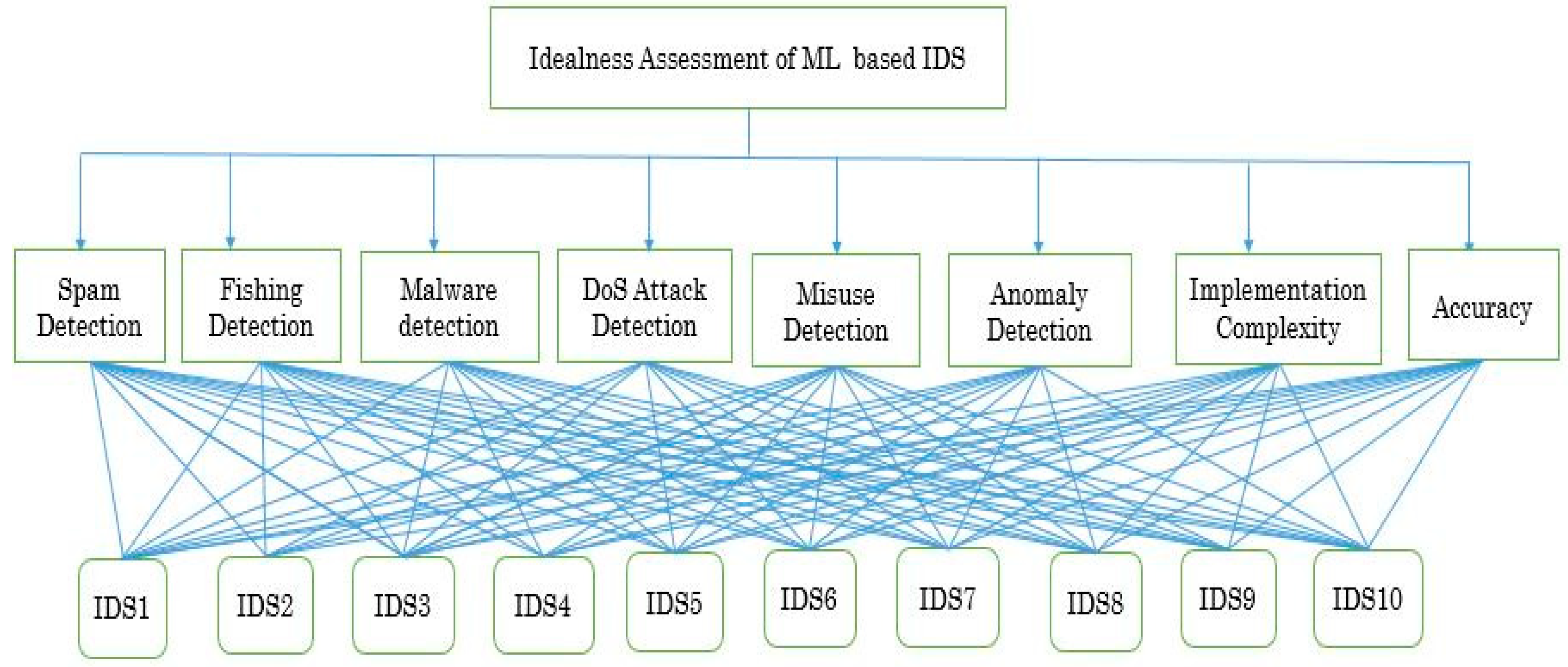
- Spam Detection: Spam detection is a significant feature of ML-based intrusion detection systems that are used to identify spams. Spam, as a technical term, is mostly related to electronic mails and is known by some other names, such as junk mail or unsolicited bulk mail. It is unwanted and unwelcomed digital content that is used by spammers through different messaging systems [25]. Mostly, it comes in the form of unwanted and unnecessary mails through internet. Most of the times spams are used for commercial purposes and are just unpleasant in nature. However, sometimes, spam messages can be catastrophic for the system and system’s user. In this scenario, the intention of spammers is to send malicious codes, execute phishing scams, and to earn money.
- (2)
- Phishing Identification: Cyber intrusions are very common at present, and there has been a rampant increase in their occurrence. Phishing is one of the common and interesting social engineering attacks used by intruders to steal confidential data. The targeted data often include credit card details and login credentials. In phishing, cyber criminals use the concept of spoofing, which helps them to masquerade as a legitimate and known source to the victim [24]. Mostly, they use it to spoof the websites of reputed organizations so that the victims can easily trust and share their confidential data. In addition, phishing attacks are also used to spread malware for system cookie stealing and keystroke capturing. Thus, detection of phishing attacks has become one of the significant features of ML-based intrusion detection systems.
- (3)
- Malware Identification: Malware, as a collective suit of various malicious software mainly, compromises viruses, spyware, key loggers, and ransomware. Malware is a code designed by cyber-attackers with the intention to cause severe damage in the victim’s system or to acquire illegitimate network access. Generally, it is a coded file that is spread by cyber-attackers through different messaging systems such as e-mail and requires the victim to execute the malware. Different types of malware programs are designed for different purposes by the intruders and are often used to compromise the financial data of organizations and enterprises [24]. Machine learning algorithms have been produced by researchers for both malware detection and malware classification into different classes or families. Hence, detection of malware is also one of the key characteristics of ML-based intrusion detection systems.
- (4)
- DoS Attacks Detection: The three main components of security or cyber-security are confidentiality, integrity, and availability (CIA). These are commonly known as CIA triad and are considered the basic components for the security of any system or network. Among the three, one of the vital components is availability. Availability literally defines the character that is to be used or obtained, but in information security, it ensures that, whenever information and other resources are needed by the authentic users, there should be timely and reliable access to them [26]. To interrupt the functioning of the system and system resource access for its users, the cyber intruders use the DOS attacks. Denial of service (DoS) attacks are used to make online system resources unavailable to its users by flooding a server with traffic. The different types of DoS attack are teardrop attack, flooding attack, IP fragmentation attack, protocol attack, and application-based attack [24]. Researchers have practiced different ML algorithms to detect DoS attacks. Thus, detection of these attacks is also a key characteristic of ML-based intrusion detection models.
- (5)
- Misuse Detection: Misuse detection is a significant characteristic of ML-based intrusion detection systems. Misuse detection ensures the identification of those cybersecurity attacks that are familiar to an intrusion detection system [27]. The intrusion detection system already knows the nature of these attacks and has signatures of these attacks in their supporting database. Analysis and detection of new attacks are based on these existing signatures. Therefore, detection systems merely having this characteristic are very poor in detecting the unknown attacks whose signatures are not present in the supporting database.
- (6)
- Anomaly Detection: Identification or detection of zero-day attacks (unknown attacks) is a challenging issue and one of the important characteristics addressed by the ML-based approaches. The behavior of zero-day attack types is not recorded in the model’s supporting database. An intelligent model based on machine learning analyzes these types of attacks and attempts to forecast their class based on its knowledge and experience [27]. Thus, identification of zero-day attacks is an essential attribute for an ML-based intrusion detection system. It plays a crucial role in making an ML-based intrusion detection model ideal for installation environment.
- (7)
- Implementation Complexity: As the name implies, it specifies all those complications that are considered during the whole implementation process of a system. Here, it defines all those complexity parameters that are considered by researchers, scientists, and other stockholders to build an ML-based intrusion detection system. It includes processing power, amount of training data, working complexity of model, implementation complexity of an algorithm, overall cost of model and other required resources, etc. Thus, implementation complexity is also an essential attribute for evaluating an ML-based intrusion detection system and has been considered for this assessment.
- (8)
- Accuracy: This defines the measure of degree of correctness and precision of any computation or process corresponding to the right standard. It is one of the most notable features of ML algorithms. In machine learning, accuracy is determined by how well the proposed ML-based models generate the required results [27]. It is measured using precision, sensitivity, specificity, area under the curve, and other measures. It describes how accurate a machine learning-based model is when compared to the other models or techniques.
4. Adopted Methodology
5. Numerical Calculations and Results
6. Discussion
- In this research experiment, the ML-based cybersecurity attributes are prioritized in this sequential order: accuracy, anomaly detection, misuse detection, DoS attack detection, malware detection, implementation complexity, spam detection, and phishing detection, having the global normalized weights 0.273937, 0.222015, 0.127306, 0.122505, 0.10973, 0.053217, 0.052354, and 0.038937, respectively.
- After IDS-6, the following competing alternatives are ranked in order based on their produced performance scores: IDS-8, IDS-9, IDS-7, IDS-5, IDS-4, IDS-3, IDS-10, IDS-1, and IDS-2 in terms of identified weighted ML-based cybersecurity attributes.
- ML-based cybersecurity provided by intrusion detection systems is a challenging issue, and in this league, our study offers accurate recommendations for developing ideal and effective machine learning-based intrusion detection systems.
- This study was performed specifically for the intrusion detection systems deployed in healthcare environments. However, it may be used as a guideline for building any sort of ideal and effective intrusion detection systems, because the assessment attributes are identified on the basis of generalization.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Samuel, A.L. Some Studies in Machine Learning Using the Game of Checkers. IBM J. Res. Dev. 1959, 3, 210–229. [Google Scholar] [CrossRef]
- Mitchell, T.M. Machine Learning; McGraw-Hill: New York, NY, USA, 1997; pp. 386–387. [Google Scholar]
- Jordan, M.I.; Mitchell, T.M. Machine learning: Trends, perspectives, and prospects. Science 2015, 349, 255–260. [Google Scholar] [CrossRef] [PubMed]
- Harrington, P. Machine Learning in Action; Simon and Schuster: New York, NY, USA, 2012. [Google Scholar]
- Dua, S.; Du, X. Data Mining and Machine Learning in Cybersecurity; CRC Press: New York, NY, USA, 2016. [Google Scholar]
- Tsai, C.-F.; Hsu, Y.-F.; Lin, C.-Y.; Lin, W.-Y. Intrusion detection by machine learning: A review. Expert Syst. Appl. 2009, 36, 11994–12000. [Google Scholar] [CrossRef]
- Belavagi, M.C.; Muniyal, B. Performance Evaluation of Supervised Machine Learning Algorithms for Intrusion Detection. Procedia Comput. Sci. 2016, 89, 117–123. [Google Scholar] [CrossRef] [Green Version]
- Agrawal, A.; Seh, A.H.; Baz, A.; AlHakami, H.; AlHakami, W.; Baz, M.; Kumar, R.; Khan, R.A. Software Security Estimation Using the Hybrid Fuzzy ANP-TOPSIS Approach: Design Tactics Perspective. Symmetry 2020, 12, 598. [Google Scholar] [CrossRef] [Green Version]
- Kumar, R.; Khan, A.I.; Abushark, Y.B.; ALAM, M.; Agrawal, A.; Khan, R.A. An Integrated Approach of Fuzzy Logic, AHP and TOPSIS for Estimating Usable-Security of Web Applications. IEEE Access 2020, 8, 50944–50957. [Google Scholar] [CrossRef]
- Solangi, Y.A.; Tan, Q.; Mirjat, N.H.; Das Valasai, G.; Khan, M.W.A.; Ikram, M. An integrated Delphi-AHP and fuzzy TOPSIS approach toward ranking and selection of renewable energy resources in Pakistan. Processes 2019, 7, 118. [Google Scholar] [CrossRef] [Green Version]
- Kumar, R.; Baz, A.; Alhakami, H.; Alhakami, W.; Baz, M.; Agrawal, A.; Khan, R.A. A Hybrid Model of Hesitant Fuzzy Decision-Making Analysis for Estimating Usable-Security of Software. IEEE Access 2020, 8, 72694–72712. [Google Scholar] [CrossRef]
- Alharbe, N. A fuzzy-Delphi based decision-making process for measuring usable-security of Web based smart hospital management system. ICIC Express Lett. 2020, 14, 15–21. [Google Scholar]
- Şengül, U.; Eren, M.; Shiraz, S.E.; Gezder, V.; Şengül, A.B. Fuzzy TOPSIS method for ranking renewable energy supply systems in Turkey. Renew. Energy 2015, 75, 617–625. [Google Scholar] [CrossRef]
- Qian, G.; Wang, H.; Feng, X. Generalized hesitant fuzzy sets and their application in decision support system. Knowl. Based Syst. 2013, 37, 357–365. [Google Scholar] [CrossRef]
- Sahu, K.; Alzahrani, F.A.; Srivastava, R.K.; Kumar, R. Hesitant Fuzzy Sets Based Symmetrical Model of Decision-Making for Estimating the Durability of Web Application. Symmetry 2020, 12, 1770. [Google Scholar] [CrossRef]
- Torra, V.; Narukawa, Y. On hesitant fuzzy sets and decision. In Proceedings of the 2009 IEEE International Conference on Fuzzy Systems, Jeju, Korea, 20–24 August 2009; pp. 1378–1382. [Google Scholar]
- AlMotiri, S.H. Integrated Fuzzy Based Computational Mechanism for the Selection of Effective Malicious Traffic Detection Approach. IEEE Access 2021, 9, 10751–10764. [Google Scholar] [CrossRef]
- Bekesiene, S.; Vasiliauskas, A.V.; Hošková-Mayerová, Š.; Vasilienė-Vasiliauskienė, V. Comprehensive Assessment of Distance Learning Modules by Fuzzy AHP-TOPSIS Method. Mathematics 2021, 9, 409. [Google Scholar] [CrossRef]
- Kaur, J.; Khan, A.I.; Abushark, Y.B.; Alam, M.; Khan, S.A.; Agrawal, A.; Kumar, R.; Khan, R.A. Security risk assessment of healthcare Web application through adaptive neuro-fuzzy inference system: A design perspec-tive. Risk Manag. Healthc. Policy 2020, 13, 355–371. [Google Scholar] [CrossRef]
- Goutam, A.; Tiwari, V. Vulnerability Assessment and Penetration Testing to Enhance the Security of Web Application. In Proceedings of the 2019 4th International Conference on Information Systems and Computer Networks (ISCON), Mathura, India, 21–22 November 2019; pp. 601–605. [Google Scholar]
- Büyüközkan, G.; Çifçi, G. A combined fuzzy AHP and fuzzy TOPSIS based strategic analysis of electronic service quality in healthcare industry. Expert Syst. Appl. 2012, 39, 2341–2354. [Google Scholar] [CrossRef]
- Handa, A.; Sharma, A.; Shukla, S.K. Machine learning in cybersecurity: A review. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2019, 9, 1306. [Google Scholar] [CrossRef]
- Dasgupta, D.; Akhtar, Z.; Sen, S. Machine learning in cybersecurity: A comprehensive survey. J. Déf. Model. Simul. Appl. Methodol. Technol. 2020, 154, 8. [Google Scholar] [CrossRef]
- Thomas, T.; Vijayaraghavan, A.P.; Emmanuel, S. Machine Learning Approaches in Cyber Security Analytics; Springer: New York, NY, USA, 2020; pp. 37–200. [Google Scholar]
- Crawford, M.; Khoshgoftaar, T.M.; Prusa, J.D.; Richter, A.N.; Al Najada, H. Survey of review spam detection using machine learning techniques. J. Big Data 2015, 2, 23. [Google Scholar] [CrossRef] [Green Version]
- Forouzan, A.B. Data Communications Networking, 3rd ed.; Tata McGraw-Hill Education: New York, NY, USA, 2007. [Google Scholar]
- Seh, A.H.; Al-Amri, J.F.; Subahi, A.F.; Agrawal, A.; Kumar, R.; Khan, R.A. Machine Learning Based Framework for Maintaining Privacy of Healthcare Data. Intell. Autom. Soft Comput. 2021, 29, 697–712. [Google Scholar] [CrossRef]
- Sahu, K.; Alzahrani, F.A.; Srivastava, R.K.; Kumar, R. Evaluating the Impact of Prediction Techniques: Software Reliability Perspective. Comput. Mater. Contin. 2021, 67, 1471–1488. [Google Scholar] [CrossRef]
- Agrawal, A.; Alenezi, M.; Khan, S.A.; Kumar, R.; Khan, R.A. Multi-Level Fuzzy system for usable-Security assessment. J. King Saud Univ. Comput. Inf. Sci. 2019, 1–21. [Google Scholar] [CrossRef]

| Rank | Abbreviation | Linguistic Term | Triangular Fuzzy Number |
|---|---|---|---|
| 10 | AHI | Absolutely High Importance | (7.0000, 9.0000, 9.0000) |
| 9 | VHI | Very High Importance | (5.0000, 7.0000, 9.0000) |
| 8 | ESHI | Essentially High Importance | (3.0000, 5.0000, 7.0000) |
| 7 | WHI | Weakly High Importance | (1.0000, 3.0000, 5.0000) |
| 6 | EHI | Equally High Importance | (1.0000, 1.0000, 3.0000) |
| 5 | EE | Exactly Equal | (1.0000, 1.0000, 1.0000) |
| 4 | ELI | Equally Low Importance | (0.3300, 1.0000, 1.0000) |
| 3 | WLI | Weakly Low Important | (0.2000, 0.3300, 1.0000) |
| 2 | ESLI | Essentially Low Importance | (0.1400, 0.2000, 0.3300) |
| 1 | VLI | Very Low Importance | (0.1100, 0.1400, 0.2000) |
| 0 | ALI | Absolutely Low Importance | (0.1100, 0.1100, 0.1400) |
| CSA1 | CSA2 | CSA3 | CSA4 | CSA5 | CSA6 | CSA7 | CSA8 | |
|---|---|---|---|---|---|---|---|---|
| CSA1 | 1.00000, 1.00000, 1.00000, 1.00000 | 0.02440, 0.07540, 0.23620, 0.88810 | 0.01402, 0.04390, 0.12750, 0.46970 | 0.01270, 0.03480, 0.09340, 0.34300 | 0.00930, 0.03480, 0.08710, 0.29360 | 0.00440, 0.01710, 0.06610, 0.21010 | 0.00068, 0.03405, 0.12320, 0.33240 | 0.01009, 0.04701, 0.15506, 0.16903 |
| CSA2 | - | 1.00000, 1.00000, 1.00000, 1.00000 | 0.02607, 0.06102, 0.36090, 0.69100 | 0.30090, 0.41403, 0.89800, 1.54501 | 0.13082, 0.23080, 0.63051, 0.69100 | 0.06600, 0.12400, 0.40300, 0.49010 | 0.1340, 0.2570, 0.5810, 0.8400 | 0.00303, 0.01094, 0.13072, 0.74060 |
| CSA3 | - | - | 1.00000, 1.00000, 1.00000, 1.00000 | 0.20400, 0.29100, 0.53500, 1.00000 | 0.00500, 0.02109, 0.12604, 0.88801 | 0.14100, 0.29100, 0.37100, 0.68700 | 0.00200, 0.01208, 0.04703, 0.32027 | 0.00016, 0.00093, 0.09052, 0.43061 |
| CSA4 | - | - | - | 1.00000, 1.00000, 1.00000, 1.00000 | 0.20040, 0.29010, 0.53500, 1.00000 | 0.00500, 0.02190, 0.12604, 0.88081 | 0.14100, 0.29010, 0.37010, 0.68070 | 0.00200, 0.01208, 0.04703, 0.32207 |
| CSA5 | - | - | - | - | 1.00000, 1.00000, 1.00000, 1.00000 | 0.08030, 0.20100, 0.37100, 0.47600 | 0.00102, 0.00808, 0.04703, 0.22306 | 0.00004, 0.00301, 0.01701, 0.11703 |
| CSA6 | - | - | - | - | - | 1.00000, 1.00000, 1.00000, 1.00000 | 0.03050, 0.08800, 0.18300, 0.34200 | 0.00101, 0.00600, 0.02905, 0.23102 |
| CSA7 | - | - | - | - | - | - | 1.00000, 1.00000, 1.00000, 1.00000 | 0.08600, 0.17200, 0.31060, 0.67040 |
| CSA8 | - | - | - | - | - | - | - | 1.00000, 1.00000, 1.00000, 1.00000 |
| CSA1 | CSA2 | CSA3 | CSA4 | CSA5 | CSA6 | CSA7 | CSA8 | Normalized Weights | |
|---|---|---|---|---|---|---|---|---|---|
| CSA1 | 1.00000 | 0.29255 | 0.98708 | 0.38203 | 0.64130 | 0.24960 | 0.99330 | 0.19990 | 0.052354 |
| CSA2 | 3.41822 | 1.00000 | 0.16210 | 0.16220 | 0.13920 | 0.19340 | 0.19220 | 0.39350 | 0.038937 |
| CSA3 | 1.55933 | 7.18391 | 3.88651 | 1.07949 | 1.00000 | 0.71272 | 0.12028 | 0.91150 | 0.10973 |
| CSA4 | 2.6176 | 6.16523 | 8.96861 | 1.00000 | 0.92636 | 0.10224 | 0.35211 | 0.76270 | 0.122505 |
| CSA5 | 5.0025 | 2.5413 | 2.03004 | 1.31113 | 1.09709 | 0.99949 | 0.81552 | 1.00000 | 0.127306 |
| CSA6 | 1.00675 | 5.20291 | 2.94811 | 2.84002 | 8.31393 | 0.99481 | 1.00000 | 1.22621 | 0.222015 |
| CSA7 | 1.01309 | 6.16903 | 1.00000 | 0.11150 | 0.25730 | 0.11120 | 0.33920 | 0.49260 | 0.053217 |
| CSA8 | 4.00641 | 5.17063 | 8.99281 | 9.78091 | 1.40308 | 1.00000 | 1.00522 | 1.00051 | 0.273937 |
| C.R. = 0.03485540 | |||||||||
| Attributes (SDA/Alternatives) | IDS-1 | IDS-2 | IDS-3 | IDS-4 | IDS-5 | IDS-6 | IDS-7 | IDS-8 | IDS-9 | IDS-10 |
|---|---|---|---|---|---|---|---|---|---|---|
| CSA1 | 3.25100, 5.12100, 7.14100, 8.71200 | 3.15400, 5.15400, 6.91400, 7.74200 | 2.82200, 4.62400, 6.64200, 8.72200 | 1.55000, 3.18000, 5.18000, 6.72000 | 1.46500, 3.18500, 5.18200, 7.72400 | 2.54679, 4.26458, 6.22156, 8.64444 | 2.91100, 4.64100, 6.00111, 6.41500 | 1.45000, 3.00000, 4.91500, 5.43500 | 1.18400, 2.84200, 4.84200, 6.45400 | 2.09645, 3.73200, 5.74300, 6.45900 |
| CSA2 | 4.21800, 5.31700, 6.31700, 7.71200 | 2.45400, 4.45400, 6.45400, 7.44500 | 2.91200, 4.64200, 6.00200, 6.42500 | 1.45000, 3.00000, 4.91000, 5.45000 | 1.18100, 2.81200, 4.82200, 6.45200 | 2.15469, 3.75467, 5.73124, 6.45467 | 3.18100, 5.12800, 7.10225, 8.65200 | 1.45400, 3.07200, 4.91400, 5.62500 | 0.82400, 2.27400, 4.27400, 6.65400 | 3.01640, 4.82300, 6.82300, 7.65400 |
| CSA3 | 4.21700, 6.27100, 8.14100, 8.71200 | 2.84200, 4.82400, 5.84200, 6.45400 | 3.18200, 5.18200, 7.10220, 8.65100 | 1.45000, 3.07000, 4.91000, 5.65000 | 0.82200, 2.27300, 4.27300, 6.65300 | 3.31546, 4.82167, 6.83125, 7.69645 | 2.45300, 4.43500, 6.45300, 7.65300 | 0.94100, 2.42500, 4.45100, 5.65200 | 2.45500, 4.27500, 6.27500, 8.65500 | 3.91100, 5.91300, 7.82200, 8.65500 |
| CSA4 | 3.25100, 5.11200, 7.14200, 8.72200 | 3.14500, 5.15400, 6.94100, 7.72400 | 2.82100, 4.61400, 6.64100, 8.71200 | 1.55000, 3.18000, 5.18000, 6.72000 | 1.43500, 3.18300, 5.18300, 7.72300 | 2.91200, 4.64200, 6.00200, 6.42500 | 1.45000, 3.00000, 4.91000, 5.45000 | 1.18100, 2.81200, 4.82200, 6.45200 | 2.15469, 3.75467, 5.73124, 6.45467 | 3.18100, 5.12800, 7.10225, 8.65200 |
| CSA5 | 4.22800, 5.32700, 6.37200, 7.72200 | 2.44500, 4.45400, 6.45400, 7.45400 | 2.91100, 4.64100, 6.00111, 6.41500 | 1.45000, 3.00000, 4.91500, 5.43500 | 1.18400, 2.84200, 4.84200, 6.45400 | 3.18200, 5.18200, 7.10220, 8.65100 | 1.45000, 3.07000, 4.91000, 5.65000 | 0.82200, 2.27300, 4.27300, 6.65300 | 3.31546, 4.82167, 6.83125, 7.69645 | 2.45300, 4.43500, 6.45300, 7.65300 |
| CSA6 | 4.27200, 6.22700, 8.14200, 8.73200 | 2.82400, 4.82300, 5.82300, 6.45300 | 3.18100, 5.12800, 7.10225, 8.65200 | 1.45400, 3.07200, 4.91400, 5.62500 | 0.82400, 2.27400, 4.27400, 6.65400 | 3.01640, 4.82300, 6.82300, 7.65400 | 3.18100, 5.12800, 7.10225, 8.65200 | 1.45400, 3.07200, 4.91400, 5.62500 | 0.82400, 2.27400, 4.27400, 6.65400 | 3.01640, 4.82300, 6.82300, 7.65400 |
| CSA7 | 5.36300, 6.33600, 7.12300, 8.51300 | 3.7300, 5.73300, 7.55300, 8.65300 | 2.45300, 4.43500, 6.45300, 7.65300 | 0.94100, 2.42500, 4.45100, 5.65200 | 2.45500, 4.27500, 6.27500, 8.65500 | 3.91100, 5.91300, 7.82200, 8.65500 | 2.45300, 4.43500, 6.45300, 7.65300 | 0.94100, 2.42500, 4.45100, 5.65200 | 2.45500, 4.27500, 6.27500, 8.65500 | 3.91100, 5.91300, 7.82200, 8.65500 |
| CSA8 | 4.64300, 5.64300, 7.55300, 8.84300 | 3.03000, 5.00300, 7.14300, 7.51300 | 2.18300, 4.09300, 6.14400, 7.51300 | 2.82400, 4.64400, 6.64400, 8.51400 | 1.91500, 3.74300, 5.73500, 7.51200 | 2.55700, 4.45500, 6.45600, 8.51600 | 2.85464, 4.64540, 6.64000, 8.51000 | 1.91000, 3.73000, 5.73000, 7.51000 | 1.45000, 3.00000, 4.91000, 5.45000 | 1.18000, 2.82000, 4.82000, 6.45000 |
| IDS-1 | IDS-2 | IDS-3 | IDS-4 | IDS-5 | IDS-6 | IDS-7 | IDS-8 | IDS-9 | IDS-10 | |
|---|---|---|---|---|---|---|---|---|---|---|
| CSA1 | 0.32450, 0.46580, 0.55250, 0.63470 | 0.60040, 0.81200, 0.85800, 0.96090 | 0.63690, 0.81660, 0.58960, 0.96670 | 0.23210, 0.38210, 0.54280, 0.73262 | 0.35250, 0.55620, 0.62970, 0.84720 | 0.62555, 0.87250, 0.93560, 0.98590 | 0.48350, 0.61599, 0.70350, 0.83950 | 0.34620, 0.55230, 0.66240, 0.81270 | 0.43370, 0.63630, 0.73360, 0.85830 | 0.33540, 0.52540, 0.61580, 0.78050 |
| CSA2 | 0.20040, 0.32200, 0.43700, 0.54700 | 0.55440, 0.84564, 0.85467, 0.96497 | 0.61160, 0.77620, 0.85660, 0.94560 | 0.38020, 0.57240, 0.72220, 0.08220 | 0.42210, 0.65278, 0.75720, 0.91290 | 0.61520, 0.85500, 0.91570, 0.96580 | 0.24520, 0.39570, 0.54750, 0.74530 | 0.45220, 0.66820, 0.76210, 0.89800 | 0.61310, 0.77320, 0.85360, 0.94530 | 0.61250, 0.85500, 0.91570, 0.96850 |
| CSA3 | 0.23010, 0.35080, 0.44070, 0.57000 | 0.37320, 0.56350, 0.69330, 0.83350 | 0.57460, 0.72560, 0.79260, 0.89660 | 0.24920, 0.41320, 0.53220, 0.74210 | 0.24220, 0.39270, 0.54270, 0.74230 | 0.45520, 0.66850, 0.76150, 0.89580 | 0.46510, 0.65570, 0.76550, 0.90550 | 0.27250, 0.45620, 0.53320, 0.73230 | 0.57430, 0.72530, 0.73920, 0.89630 | 0.34620, 0.55230, 0.66240, 0.81270 |
| CSA4 | 0.25074, 0.38070, 0.43700, 0.54000 | 0.03730, 0.10350, 0.24320, 0.51030 | 0.03968, 0.10555, 0.19250, 0.38450 | 0.42230, 0.62490, 0.76240, 0.88200 | 0.46310, 0.65370, 0.76350, 0.90350 | 0.27550, 0.45560, 0.53350, 0.73530 | 0.42210, 0.65278, 0.75720, 0.91290 | 0.61520, 0.85500, 0.91570, 0.96580 | 0.24520, 0.39570, 0.54750, 0.74530 | 0.45220, 0.66820, 0.76210, 0.89800 |
| CSA5 | 0.45090, 0.61020, 0.65030, 0.68080 | 0.29430, 0.43840, 0.56330, 0.74203 | 0.48350, 0.61599, 0.70350, 0.83950 | 0.34620, 0.55230, 0.66240, 0.81270 | 0.43370, 0.63630, 0.73360, 0.85830 | 0.33540, 0.52540, 0.61580, 0.78050 | 0.24220, 0.39270, 0.54270, 0.74230 | 0.45520, 0.66850, 0.76150, 0.89580 | 0.46510, 0.65570, 0.76550, 0.90550 | 0.27250, 0.45620, 0.53320, 0.73230 |
| CSA6 | 0.30750, 0.44450, 0.54457, 0.64052 | 0.24390, 0.41330, 0.53320, 0.74310 | 0.24520, 0.39570, 0.54750, 0.74530 | 0.45220, 0.66820, 0.76210, 0.89800 | 0.61310, 0.77320, 0.85360, 0.94530 | 0.42230, 0.62490, 0.76240, 0.88200 | 0.46310, 0.65370, 0.76350, 0.90350 | 0.27550, 0.45560, 0.53350, 0.73530 | 0.42210, 0.65278, 0.75720, 0.91290 | 0.61520, 0.85500, 0.91570, 0.96580 |
| CSA7 | 0.61020, 0.80500, 0.91070, 0.96080 | 0.42330, 0.64390, 0.76340, 0.88044 | 0.46510, 0.65570, 0.76550, 0.90550 | 0.27250, 0.45620, 0.53320, 0.73230 | 0.57430, 0.72530, 0.73920, 0.89630 | 0.34620, 0.55230, 0.66240, 0.81270 | 0.43370, 0.63630, 0.73360, 0.85830 | 0.33540, 0.52540, 0.61580, 0.78050 | 0.24220, 0.39270, 0.54270, 0.74230 | 0.45520, 0.66850, 0.76150, 0.89580 |
| CSA8 | 0.57400, 0.72500, 0.79200, 0.89060 | 0.34560, 0.55350, 0.66450, 0.81570 | 0.43570, 0.63650, 0.73650, 0.85580 | 0.33240, 0.52420, 0.61820, 0.78200 | 0.03980, 0.10022, 0.19220, 0.38420 | 0.45220, 0.66820, 0.76210, 0.89800 | 0.34650, 0.55530, 0.66450, 0.81570 | 0.43750, 0.63650, 0.73560, 0.85580 | 0.33540, 0.52540, 0.61850, 0.78050 | 0.03580, 0.10555, 0.19520, 0.38450 |
| IDS-1 | IDS-2 | IDS-3 | IDS-4 | IDS-5 | IDS-6 | IDS-7 | IDS-8 | IDS-9 | IDS-10 | |
|---|---|---|---|---|---|---|---|---|---|---|
| CSA1 | 0.00080, 0.01020, 0.01600, 0.02100 | 0.11050, 0.16070, 0.18030, 0.19090 | 0.14020, 0.17900, 0.19800, 0.21090 | 0.05070, 0.08500, 0.10800, 0.13010 | 0.05505, 0.08070, 0.10040, 0.12200 | 0.04208, 0.05900, 0.06400, 0.06800 | 0.05800, 0.08050, 0.09500, 0.11800 | 0.02030, 0.03700, 0.04300, 0.05500 | 0.00090, 0.02300, 0.04500, 0.05900 | 0.08070, 0.09040, 0.09400, 0.10100 |
| CSA2 | 0.00807, 0.01035, 0.01700, 0.02100 | 0.07074, 0.11800, 0.14400, 0.17300 | 0.13300, 0.16800, 0.18400, 0.20080 | 0.03701, 0.06106, 0.07900, 0.11000 | 0.03020, 0.05300, 0.07200, 0.09800 | 0.03020, 0.04070, 0.05030, 0.06030 | 0.14800, 0.18091, 0.20060, 0.22040 | 0.03404, 0.05700, 0.08200, 0.11000 | 0.04070, 0.07040, 0.09020, 0.11020 | 0.04304, 0.05010, 0.06060, 0.06090 |
| CSA3 | 0.01200, 0.01800, 0.02100, 0.02040 | 0.12500, 0.16090, 0.18050, 0.20010 | 0.14080, 0.18091, 0.20060, 0.22040 | 0.03404, 0.05700, 0.08200, 0.11000 | 0.04700, 0.07400, 0.09020, 0.11020 | 0.04304, 0.05100, 0.06060, 0.06090 | 0.14200, 0.17090, 0.19800, 0.21090 | 0.05700, 0.08500, 0.10800, 0.13100 | 0.05055, 0.08070, 0.10040, 0.12020 | 0.04028, 0.05900, 0.06400, 0.06800 |
| CSA4 | 0.00080, 0.01200, 0.01600, 0.02010 | 0.11500, 0.16070, 0.18030, 0.19090 | 0.14200, 0.17090, 0.19080, 0.21900 | 0.05700, 0.08500, 0.10080, 0.13010 | 0.05505, 0.08700, 0.10400, 0.12020 | 0.04208, 0.05900, 0.06400, 0.06080 | 0.13030, 0.16080, 0.18400, 0.20080 | 0.03701, 0.06106, 0.07900, 0.11000 | 0.03200, 0.05300, 0.07200, 0.09800 | 0.03020, 0.04700, 0.05300, 0.06300 |
| CSA5 | 0.00807, 0.01305, 0.01070, 0.02100 | 0.07704, 0.11800, 0.14400, 0.17300 | 0.13300, 0.16800, 0.18400, 0.20080 | 0.03701, 0.06016, 0.07090, 0.11000 | 0.03200, 0.05300, 0.07020, 0.09800 | 0.03200, 0.04700, 0.05300, 0.06300 | 0.00090, 0.02030, 0.04050, 0.05090 | 0.06300, 0.09709, 0.11400, 0.13100 | 0.06010, 0.08700, 0.10100, 0.12000 | 0.01900, 0.03025, 0.03800, 0.05100 |
| CSA6 | 0.01000, 0.01500, 0.01011, 0.02000 | 0.00800, 0.02204, 0.05002, 0.10000 | 0.00900, 0.02300, 0.04500, 0.05090 | 0.06300, 0.09709, 0.11400, 0.13100 | 0.06010, 0.08070, 0.10010, 0.12000 | 0.01900, 0.03205, 0.03800, 0.05010 | 0.11200, 0.14040, 0.16030, 0.19050 | 0.05160, 0.08200, 0.09900, 0.12200 | 0.05800, 0.08050, 0.09500, 0.11080 | 0.02300, 0.03700, 0.04300, 0.05500 |
| CSA7 | 0.01073, 0.02033, 0.02500, 0.02700 | 0.06101, 0.10100, 0.11070, 0.15400 | 0.11020, 0.14040, 0.16030, 0.19050 | 0.05016, 0.08020, 0.09900, 0.12200 | 0.05080, 0.08050, 0.09050, 0.11800 | 0.02300, 0.03700, 0.04300, 0.05500 | 0.14200, 0.17090, 0.19080, 0.21090 | 0.05700, 0.08500, 0.10800, 0.13100 | 0.05505, 0.08070, 0.10400, 0.12200 | 0.04208, 0.05900, 0.06400, 0.06800 |
| CSA8 | 0.08504, 0.09030, 0.09300, 0.09086 | 0.03701, 0.06016, 0.07090, 0.11000 | 0.03200, 0.05030, 0.07200, 0.09080 | 0.03020, 0.04700, 0.05030, 0.06030 | 0.14020, 0.17090, 0.19080, 0.21900 | 0.03200, 0.04700, 0.05300, 0.06300 | 0.13300, 0.16800, 0.18400, 0.20080 | 0.03701, 0.06106, 0.07900, 0.11000 | 0.03200, 0.05300, 0.07200, 0.09800 | 0.03200, 0.04700, 0.05300, 0.06300 |
| Alternatives | Dist+ | Dist− | Gaps Degree of CC +i | Satisfaction Degree of CC −i | Alternative Ranks |
|---|---|---|---|---|---|
| IDS-1 | 0.338458 | 0.589857 | 0.655256 | 0.358566 | 9 |
| IDS-2 | 0.035659 | 0.047455 | 0.640454 | 0.355475 | 10 |
| IDS-3 | 0.035659 | 0.043458 | 0.535425 | 0.464597 | 7 |
| IDS-4 | 0.039457 | 0.046855 | 0.535635 | 0.465465 | 6 |
| IDS-5 | 0.035459 | 0.042857 | 0.583459 | 0.484545 | 5 |
| IDS-6 | 0.045566 | 0.025855 | 0.366855 | 0.635660 | 1 |
| IDS-7 | 0.035485 | 0.035555 | 0.469457 | 0.525646 | 4 |
| IDS-8 | 0.044455 | 0.026460 | 0.394564 | 0.615453 | 2 |
| IDS-9 | 0.035549 | 0.026457 | 0.483546 | 0.575626 | 3 |
| IDS-10 | 0.298855 | 0.445685 | 0.586599 | 0.455696 | 8 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alharbi, A.; Seh, A.H.; Alosaimi, W.; Alyami, H.; Agrawal, A.; Kumar, R.; Khan, R.A. Analyzing the Impact of Cyber Security Related Attributes for Intrusion Detection Systems. Sustainability 2021, 13, 12337. https://doi.org/10.3390/su132212337
Alharbi A, Seh AH, Alosaimi W, Alyami H, Agrawal A, Kumar R, Khan RA. Analyzing the Impact of Cyber Security Related Attributes for Intrusion Detection Systems. Sustainability. 2021; 13(22):12337. https://doi.org/10.3390/su132212337
Chicago/Turabian StyleAlharbi, Abdullah, Adil Hussain Seh, Wael Alosaimi, Hashem Alyami, Alka Agrawal, Rajeev Kumar, and Raees Ahmad Khan. 2021. "Analyzing the Impact of Cyber Security Related Attributes for Intrusion Detection Systems" Sustainability 13, no. 22: 12337. https://doi.org/10.3390/su132212337
APA StyleAlharbi, A., Seh, A. H., Alosaimi, W., Alyami, H., Agrawal, A., Kumar, R., & Khan, R. A. (2021). Analyzing the Impact of Cyber Security Related Attributes for Intrusion Detection Systems. Sustainability, 13(22), 12337. https://doi.org/10.3390/su132212337









