Sustainable Implementation of Access Control
Abstract
:1. Introduction
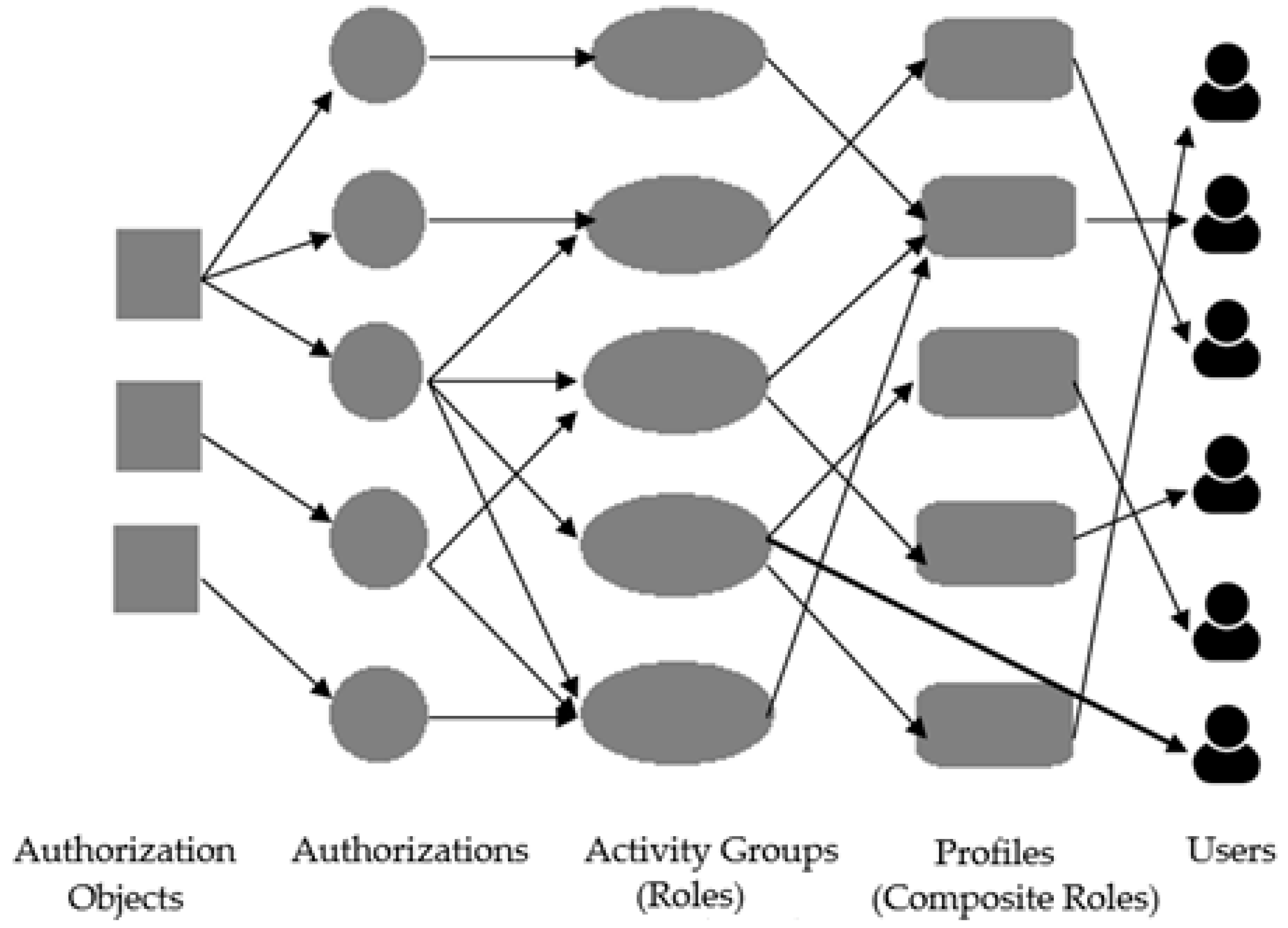
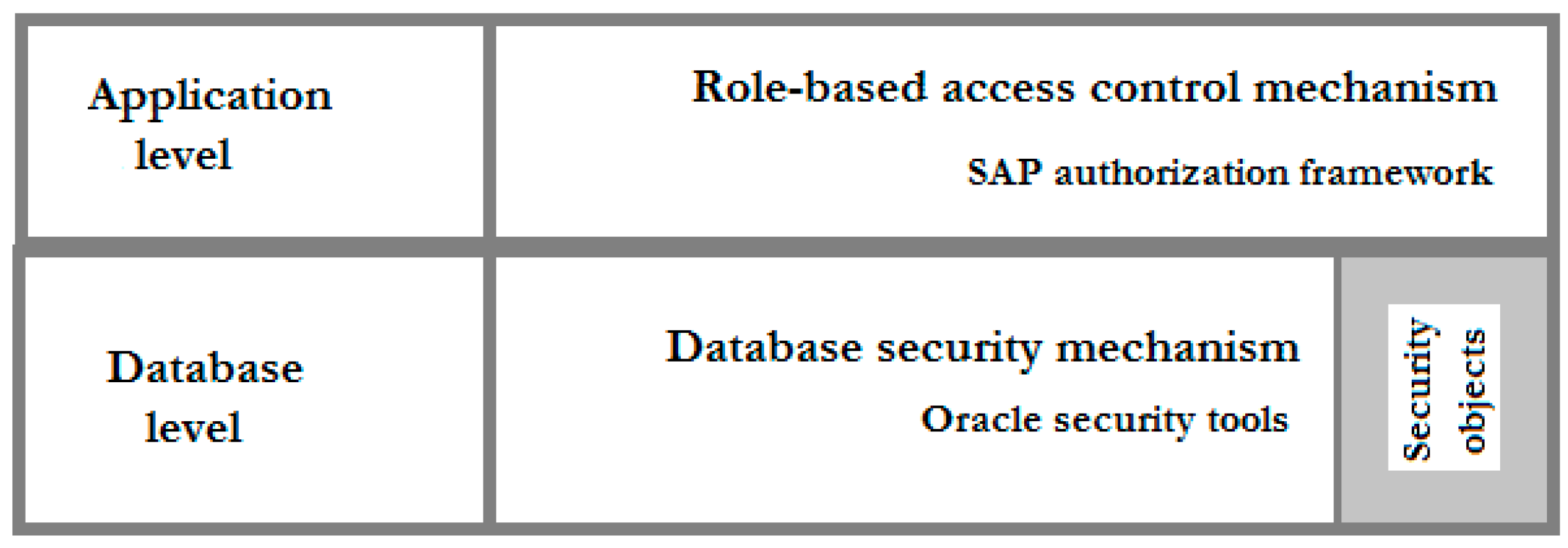
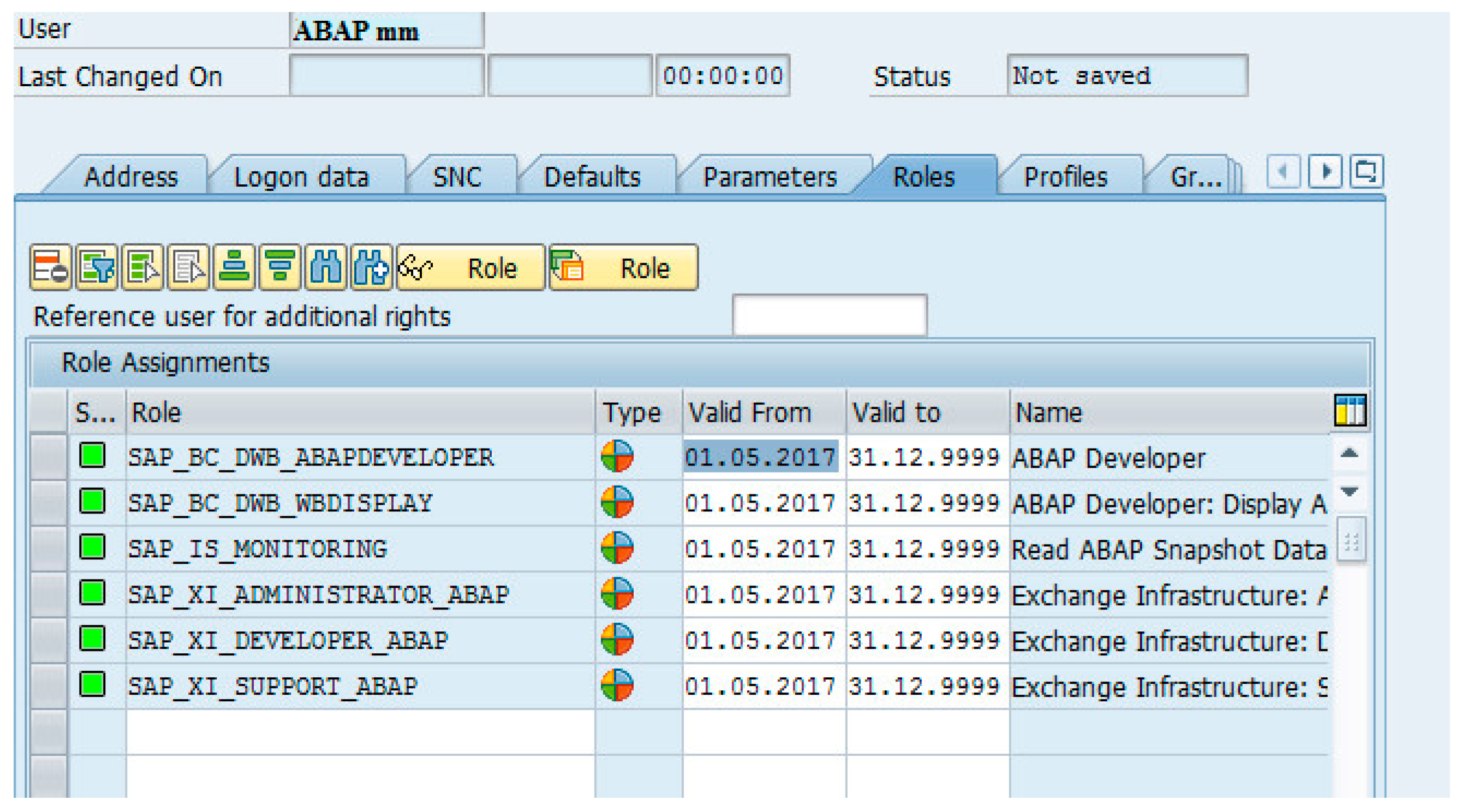
2. Authorization and Access Control
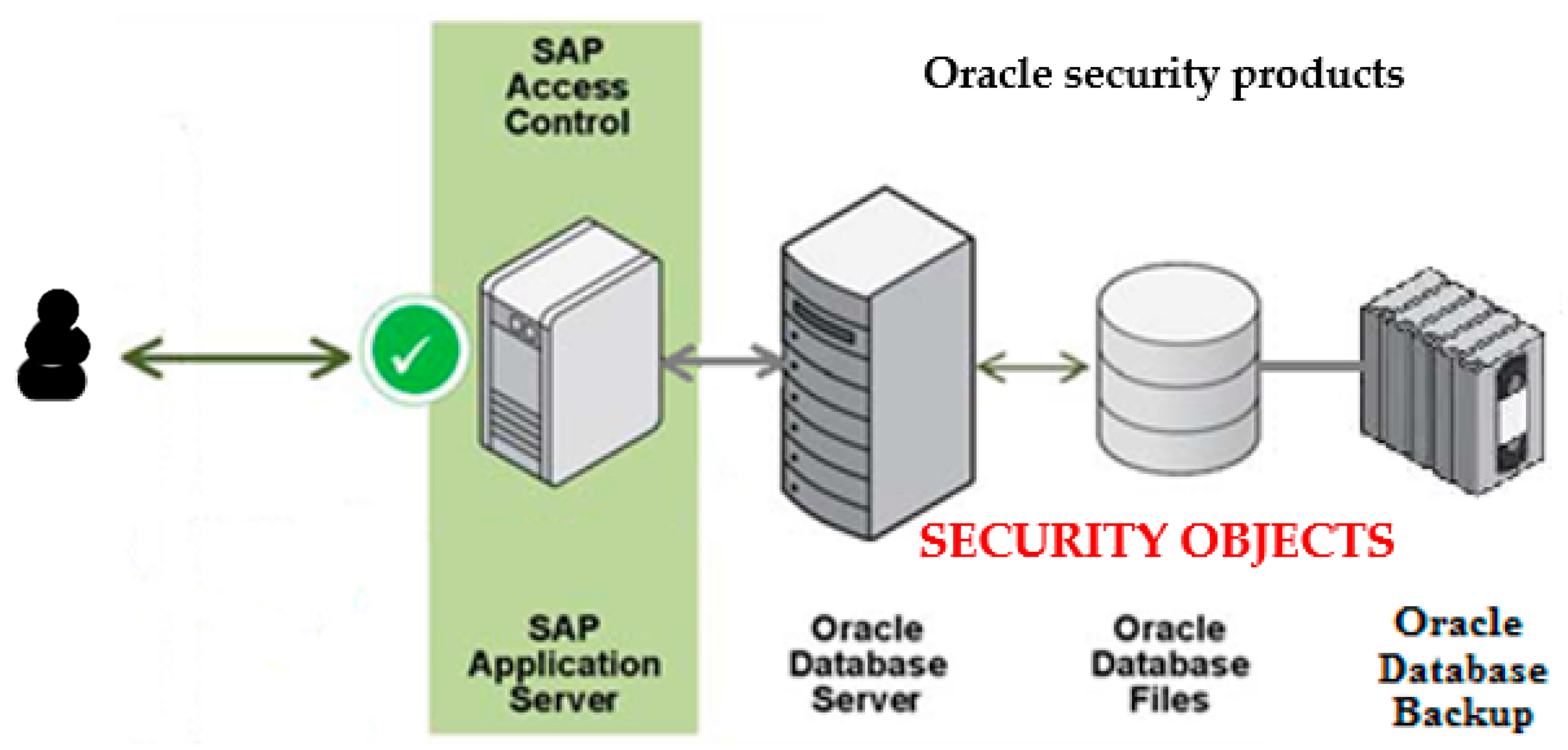
3. Sustainable Implementation of Access Control
| CREATE TABLE UflagHistory (id NUMBER(12) CONSTRAINT pk_iduflag PRIMARY KEY, |
| mandt VARCHAR2(3), bname VARCHAR2(36), uflag NUMBER(3), (1) |
| datac VARCHAR2(36), user_modif VARCHAR2(20) DEFAULT USER NOT NULL), |
| CREATE OR REPLACE TRIGGER Changes_Lock_Unlock |
| BEFORE UPDATE ON SAPSR3.usr02 |
| FOR EACH ROW |
| BEGIN (2) |
| INSERT INTO UflagHistory (mandt, bname, uflag, datac) |
| VALUES (:OLD.mandt, :OLD.bname, :NEW.uflag, |
| TO_CHAR (SYSDATE,'MM-DD-YYYY HH24:MI:SS')); |
| END; |
| CREATE OR REPLACE TRIGGER IdHistory |
| BEFORE INSERT ON UflagHistory |
| REFERENCING OLD AS OLD NEW AS NEW |
| FOR EACH ROW (3) |
| BEGIN |
| SELECT NVL(MAX(id),0)+1 INTO :NEW.id FROM UflagHistory; |
| END; |
| CREATE OR REPLACE PROCEDURE lock_unlock_all |
| (p_mandt IN SAPSR3.usr02.mandt%TYPE, p_uflag IN SAPSR3.usr02.uflag%TYPE) AS |
| v_nr NUMBER(2):=0; |
| BEGIN |
| SELECT COUNT(mandt) INTO v_nr FROM SAPSR3.usr02 WHERE mandt = p_mandt; |
| IF v_nr >= 1 THEN |
| UPDATE SAPSR3.usr02 SET uflag = p_uflag WHERE mandt = p_mandt; (4) |
| COMMIT; |
| DBMS_OUTPUT.PUT_LINE ('In table [USR02] the access of all users |
| with mandt ['||p_mandt||'] was changed in ['||p_uflag||']'); |
| ELSE |
| DBMS_OUTPUT.PUT_LINE ('Mandt ['||p_mandt||'] does not exist'); |
| END IF; |
| END; |
4. Discussion
| Resuming, |
| SECURITY OBJECTS = {table UflagHistory, trigger Changes_Lock_Unlock, (5) |
| trigger IdHistory, procedure lock_unlock_all} |
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kayem, A.V.D.M.; Akl, S.G.; Martin, P. Adaptive Cryptographic Access Control; Springer: New York, NY, USA, 2010; ISBN 978-1-4419-6654-4. [Google Scholar]
- Needham, R.; Maybury, R. Security Control—Chapter 4. In Security Engineering: A Guide to Building Dependable Distributed Systems; Wiley Publishing Inc.: Hoboken, NJ, USA, 2008; pp. 93–108. ISBN 978-0-470-06852-6. [Google Scholar]
- Vimercati, S.D.; Foresti, S.; Samarati, P. Authorization and access Control. In Security, Privacy, and Trust in Modern Data Management; Springer: Berlin/Heidelberg, Germany, 2007; pp. 39–53. ISBN 978-3-540-69860-9. Available online: https://link.springer.com/chapter/10.1007/978-3-540-69861-6_4 (accessed on 20 March 2018).
- Bourgeois, D.; Bourgeois, D.T. Information systems security—Chapter 6. In Information Systems for Business and Beyond; The Open Textbook Challenge by the Saylor Academy. 2014. Available online: https://bus206.pressbooks.com/chapter/chapter-6-information-systems-security/ (accessed on 27 January 2018).
- Kostadinov, D. Key Elements of an Information Security Policy. 2014. Available online: https://resources.infosecinstitute.com/key-elements-information-security-policy/#gref (accessed on 12 March 2018).
- Crampton, J. Cryptographic Enforcement of Role-Based Access Control. In International Workshop on Formal Aspects in Security and Trust. 2010; pp. 191–205. Available online: https://link.springer.com/chapter/10.1007/978-3-642-19751-2_13 (accessed on 20 December 2017).
- Sree, P.V.; Babu, G.P. Role-Based Cryptography. Int. J. Comput. Sci. Mob. Comput. 2014, 3, 799–803. [Google Scholar]
- Levitt, J. SAP Security Concepts, Segregation of Duties, Sensitive Access & Mitigations Control; The Institute of Internal Auditors Los Angeles Chapter; PricewaterhouseCoopers LLP. 2015. Available online: https://chapters.theiia.org/los-angeles/Events/Documents/IIA%20%20Los%20Angeles%20%20SAP%20Security%20Presentation%20.pdf (accessed on 23 November 2017).
- Tayeh, G.A.; Myrah, T. Properties of Sustainable Information Systems. In Proceedings of SIGGreen Pre-ICIS 2016 Workshop. 2016. Available online: https://boris.unibe.ch/98846/1/ICIS2016.pdf (accessed on 28 January 2018).
- Junker, H.; Farzad, T. Towards Sustainability Information Systems. Procedia Comput. Sci. 2015, 64, 1130–1139. Available online: https://ac.els-cdn.com/S1877050915027222/1-s2.0-S1877050915027222-main.pdf?_tid=bbacb3a5-0798-4ff0-ac4d-21b6ba037b2f&acdnat=1524206064_5a4ce9aec5a6984ea3eb7dddbf70917f (accessed on 10 September 2017). [CrossRef]
- Muntean, M. Business Intelligence Issues for Sustainability Projects. Sustainability 2018, 10, 335. [Google Scholar] [CrossRef]
- Petrini, M.; Pozzebon, M. Integrating Sustainability into Business Practices. Braz. Adm. Rev. 2010, 7, 362–378. [Google Scholar] [CrossRef]
- Evans, S.; Vladimirova, D.; Holgado, M.; Fossen, K.; Yang, M. Business Model Innovation for Sustainability: Towards a Unified Perspective for Creation of Sustainable Business Models. Bus. Strategy Environ. 2017, 26, 507–608. [Google Scholar] [CrossRef]
- Ahituv, N.; Neumann, S.; Zviran, M. A System Development Methodology for ERP Systems. J. Comput. Inf. Syst. 2016, 42, 56–67. [Google Scholar]
- Kim, D.; Solomon, M.G. Fundamentals of Information Systems Security, 3rd ed.; World Headquarters: Burlington, MA, USA, 2018; pp. 112–135. ISBN 978-1284116458. [Google Scholar]
- Stahl, S.; Pease, K.A. Seven Requirements for Successfully Implementing Information Security Policies and Standards. In A Guide for Executives. 2011. Available online: https://citadel-information.com/wp-content/uploads/2010/12/seven-requirements-for-successfully-implementing-information-security-policies-2012.pdf (accessed on 15 November 2017).
- Labuschagne, L.; Marnewick, C. A Security Framework for an ERP System. In Proceedings of the ISSA 2005 New Knowledge Today Conference. 2005. Available online: https://www.researchgate.net/publication/220803192_A_security_framework_for_an_ERP_system (accessed on 13 January 2018).
- Cram, W.A.; Proudfoot, J.G.; D’Arcy, J. Organizational information security policies: A review and research framework. Eur. J. Inf. Syst. 2017, 26, 605–641. [Google Scholar] [CrossRef]
- SAP BASIS and Security Administration. 2016. Available online: http://www.acc.ncku.edu.tw/chinese/faculty/shulc/courses/cas/SAP_BASIS_and_Security_Administration.pdf (accessed on 16 December 2017).
- SAP BASIS ADMIN Roles & Responsabilities. 2012. Available online: http://goddbstechnologiesltd.blogspot.ro/2012/05/sap-basis-admin-roles-responsibilities.html (accessed on 17 December 2017).
- USH02 SAP Change History for Logon Data Table. Available online: http://www.se80.co.uk/saptables/u/ush0/ush02.htm (accessed on 23 December 2017).
- Gonzales, S.M. Fraud Prevention through Segregation of Duties: Authorization model in SAP GRC Access Control. 2016. Available online: https://e-archivo.uc3m.es/bitstream/handle/10016/ 23673/TFG_Sandra_Morillejo_Gonz%C3%A1lez.pdf (accessed on 20 February 2018).
- Ugur, A.; Sogukpinar, I. Multilayer Authorization Model and Analysis of Authorizations Methods. Turk. J. Electr. Eng. Comput. Sci. 2016, 24, 4915–4934. [Google Scholar] [CrossRef]
- Xu, M.; Qin, Z.; Yan, F.; Fu, S. Trusted Commputing and Information Security. In Proceedings of the 11th Chinese Conference, CTCIS 2017, Changsha, China, 14–17 September 2017; Springer: Berlin, Germany, 2017; pp. 397–408, ISBN 978-981-10-7080-8. [Google Scholar]
- Hernandez, J.; Martinez, F.; Keogh, J. User Management and Security in SAP Environments—Chapter 8. In SAP/R3 Handbook; Mc Graw Hill: New York, NY, USA, 2006; pp. 351–399. Available online: http://cdn.ttgtmedia.com/searchSAP/downloads/chapter-february2.pdf (accessed on 24 March 2018).
- Vacca, J.R. Computer and Inforrmation Security; Morgen Kaufman: Burlington, MA, USA, 2017; pp. 13–33, 391–418, 1041–1044. ISBN 978-0-12-803843-7. [Google Scholar]
- Kagermann, H.; Kinney, W.; Kuting, K.; Weber, K.L. Internal Audit Handbook. Managing with the SAP-Audit Roadmap; Springer: New York, NY, USA, 2008; ISBN 978-3-540-70887-2. [Google Scholar]
- Eric, S.; Noblet, J.P. Integrating ERP into the Organization: Organizational Changes and Side-Effect. Int. Bus. Res. 2012, 5, 51. [Google Scholar]
- Kirchmer, M. Business Process Oriented Implementation of Standard Software: How to Achieve Competitive Advantage Quickly and Efficiently; Springer: New York, NY, USA, 2012; ISBN 978-3642977176. [Google Scholar]
- Oracle Database Security for SAP Applications. 2017. Available online: http://www.oracle.com/us/products/database/nl20-database-security-396167.pdf (accessed on 30 May 2018).
- Oracle Solution Center. Oracle Solution for SAP Environments. White Paper. 2014. Available online: http://www.oracle.com/us/solutions/sap/oracle-security-for-sap-2148703.pdf (accessed on 20 January 2018).
- Kyte, T.; Kuhn, D. Expert Oracle Database Architecture; Kindle, Ed.; APress: New York, NY, USA, 2014; ISBN 978-1430262985. [Google Scholar]
- Gupta, S.K. Advanced Oracle PL/SQL Developer’s Guide; Packt Publishing: Maharashtra, India, 2016; ISBN 978-1785284809. [Google Scholar]
- Designing SAP Application Security. Leveraging SAP Access Monitoring Solution during SAP Implementations; Upgrades or Security Redesign Projects. 2017. Available online: https://www.protiviti.com/sites/default/files/united_states/insights/designing-sap-application-security-protiviti.pdf (accessed on 15 February 2018).
- Wessing, D. A Case Study into the Application of a Good Practice SAP (Access) Security Design Framework. 2015. Available online: http://www.vurore.nl/images/vurore/ downloads/scripties/2046-Def-scriptie--Dennis-Wessing.pdf (accessed on 29 January 2018).
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Muntean, M.; Dijmărescu, L. Sustainable Implementation of Access Control. Sustainability 2018, 10, 1808. https://doi.org/10.3390/su10061808
Muntean M, Dijmărescu L. Sustainable Implementation of Access Control. Sustainability. 2018; 10(6):1808. https://doi.org/10.3390/su10061808
Chicago/Turabian StyleMuntean, Mihaela, and Laurenţiu Dijmărescu. 2018. "Sustainable Implementation of Access Control" Sustainability 10, no. 6: 1808. https://doi.org/10.3390/su10061808
APA StyleMuntean, M., & Dijmărescu, L. (2018). Sustainable Implementation of Access Control. Sustainability, 10(6), 1808. https://doi.org/10.3390/su10061808




