Robust Image Embedded Watermarking Using DCT and Listless SPIHT
Abstract
:1. Introduction
2. Related Work
3. Proposed Scheme
3.1. Embedding Procedure
- Randomly select an 8 × 8 block from host image and apply DCT to the block.
- Randomly select a watermark bit from the watermark image in order to embed into the block.
- Randomly select a DCT coefficient (DC or one of the AC components) to embed the watermark bit. Let its value be denoted as .
- Let P1 and P2 be the pair-wise co-prime numbers used in CRT (say, P1 = 38 and P2 = 107) for the DC coefficient. For an AC coefficient, let the values of P1 = 38 and P2 = 55.
- Find E1 and E2 by applying the inverse CRT to . Let the absolute difference between E1 and E2 value be .
- Determine the value D = max(P1,P2) – 1.
- The required condition for embedding watermark bit ‘1’, iswhere if is DC coefficient, otherwise, . Apply CRT to modify . If the condition is not satisfied, then is modified in step of 8 until the required condition in Equation (2) is satisfied.
- The required condition for embedding watermark bit ‘0’ is
- Apply CRT to modify . If the condition in Equation (3) is not satisfied, then is modified in step 8 until the required condition is satisfied.
- Reconstruct DCT block with the modified DCT coefficient and apply inverse DCT to the block to construct the watermarked image block.
- Repeat the steps (represented in bullet form) 1–9 for all the remaining blocks until all the watermark bits are embedded.
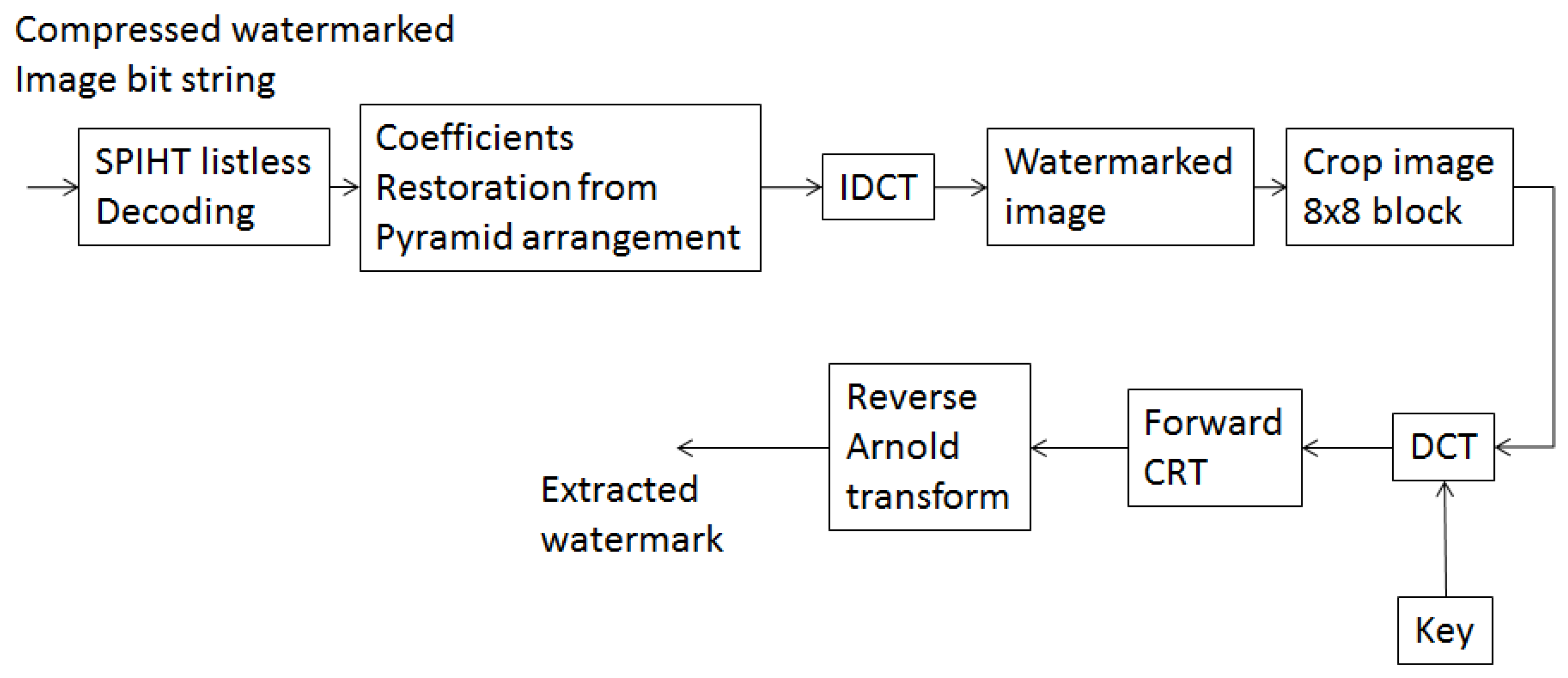
3.2. Extraction Procedure
3.3. Secret Keys
- The parameters for Torus automorphism permutation: The disarrangement parameters and obtained in Equation (1) are necessary when reconstructing the watermark pattern.
- The record number of the selected block has to be preserved.
- The embedding position of the watermark bits, i.e., the DCT coefficients and their positions have to be preserved.
- Co-prime numbers used in CRT.
4. Simulation Results and Analysis
- Quality of the watermarked images.
- Robustness of the scheme against common attacks such as compression, crop, histogram manipulation, auto contrast, noise, inversion and filtering.
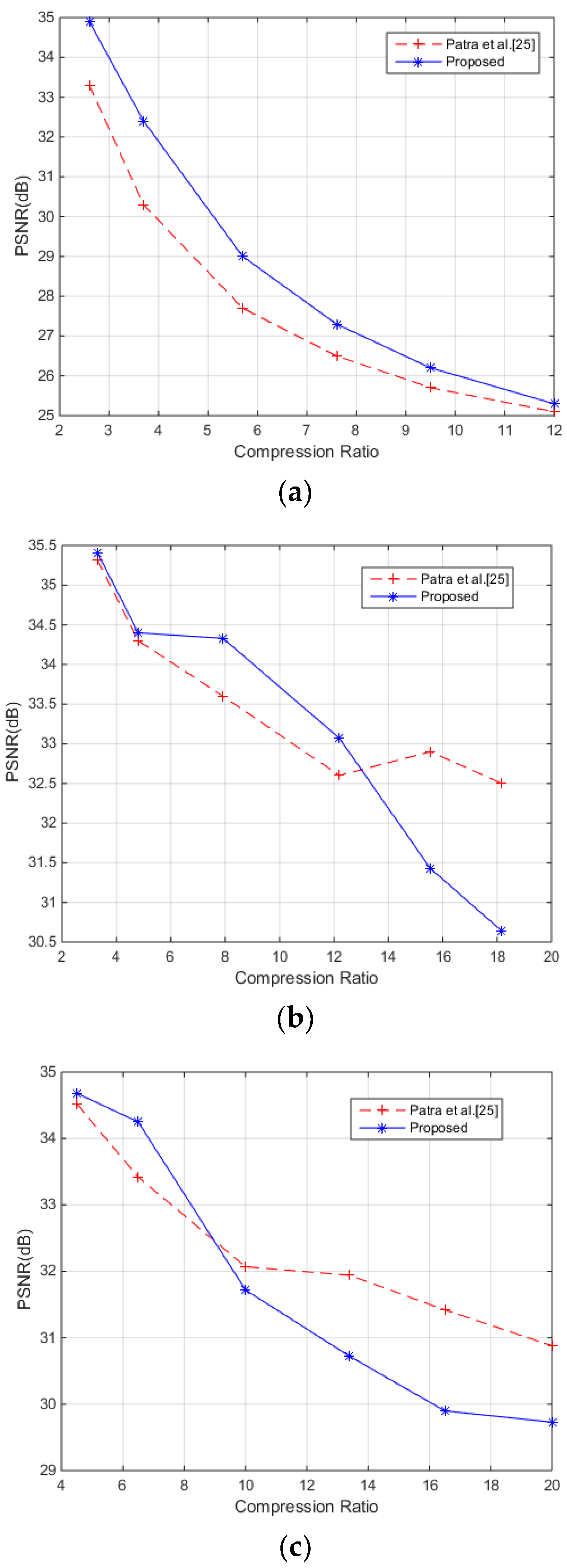
4.1. Quality of the Watermarked Images
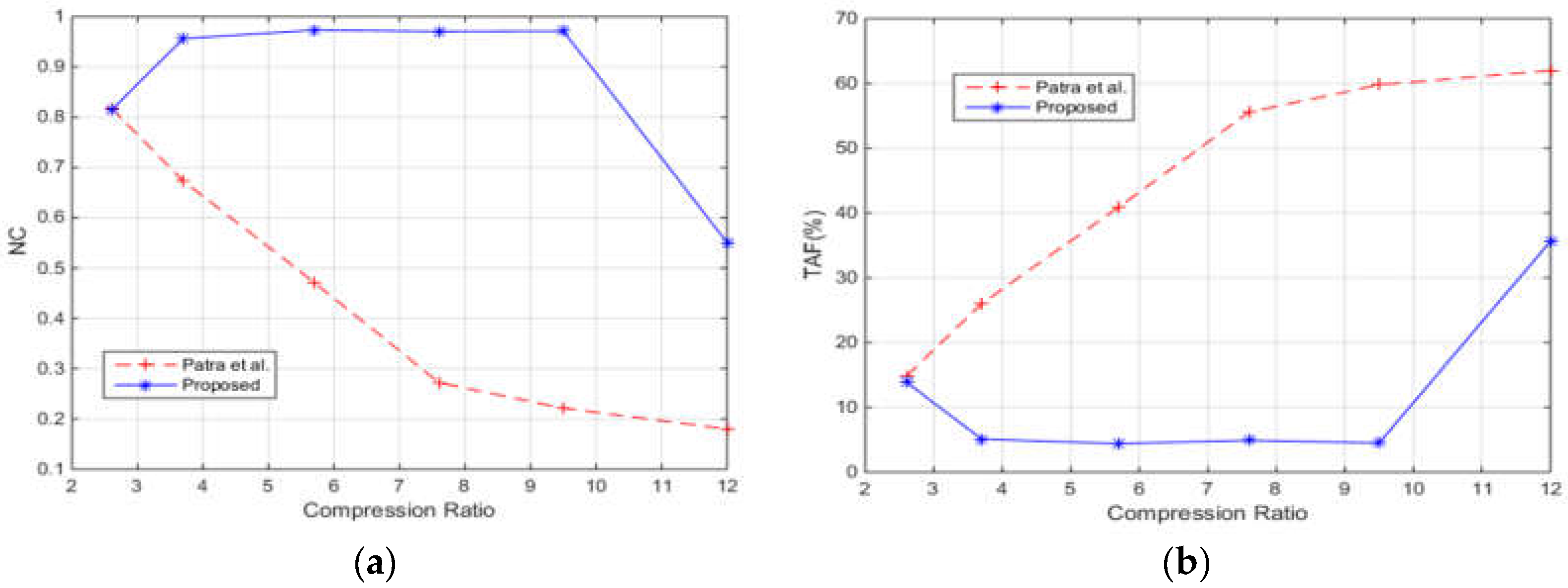
4.2. Robustness after Different Attacks
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Vleeschouwer, C.D.; Delaigle, J.F.; Marq, B. Invisibility and application functionalities in perceptual watermarking an overview. Proc. IEEE 2002, 90, 64–77. [Google Scholar] [CrossRef]
- Nikolaidis, N.; Pitas, I. Robust image watermarking in the spatial domain. Signal Process. 1997, 66, 385–403. [Google Scholar] [CrossRef]
- Cox, I.J.; Kilian, J.; Leighton, F.T.; Shamoon, T. Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Process. 1997, 6, 1673–1687. [Google Scholar] [CrossRef] [PubMed]
- Chen, T.H.; Tsai, D.S. Owner—Customer right protection mechanism using a watermarking scheme and a watermarking protocol. Pattern Recognit. 2006, 39, 1530–1541. [Google Scholar] [CrossRef]
- Lin, C.Y.; Chang, S.F. A robust image authentication method distinguishing JPEG compression from malicious manipulation. IEEE Trans. Circuits Syst. Video Technol. 2001, 11, 153–168. [Google Scholar] [CrossRef]
- Hsu, C.T.; Wu, J.L. Hidden digital watermarks in images. IEEE Trans. Image Process. 1999, 8, 58–68. [Google Scholar] [CrossRef] [PubMed]
- Barni, M.; Bartolini, F.; Cappellini, V.; Piva, A. A DCT-domain system for robust image watermarking. Signal Process. 1977, 66, 357–372. [Google Scholar] [CrossRef]
- Mohanty, S.P.; Ranganathan, N.; Namballa, R.K. VLSI implementation of invisible digital watermarking algorithms towards the development of a secure JPEG encoder. In Proceedings of the IEEE Workshop on Signal Processing Systems, Seoul, Korea, 27–29 August 2003; pp. 183–188. [Google Scholar]
- Lu, Z.M.; Zheng, H.Y.; Huang, J. A digital watermarking scheme based on DCT and SVD. In Proceedings of the Third International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kaohsiung, Taiwan, 26–28 November 2007; pp. 241–244. [Google Scholar] [CrossRef]
- Qi, H.; Zheng, D.; Zhao, J. Human visual system based adaptive digital image watermarking. Signal Process. 2007, 88, 174–188. [Google Scholar] [CrossRef]
- Liu, K.-C. Wavelet-based watermarking for color images through visual masking. AEU Int. J. Electron. Commun. 2010, 64, 112–124. [Google Scholar] [CrossRef]
- Nguyen, T.V.; Patra, J.C. A simple ICA-based watermarking scheme. Digital Signal Process. 2008, 18, 762–776. [Google Scholar] [CrossRef]
- Xin, Y.; Liao, S.; Pawlak, M. Circularly orthogonal moments for geometrically robust image watermarking. Pattern Recognit. 2007, 40, 3740–3752. [Google Scholar] [CrossRef]
- Ahmed, A.M.; Day, D.D. Applications of the naturalness preserving transform to image watermarking and data hiding. Digit. Signal Process. 2004, 14, 531–549. [Google Scholar] [CrossRef]
- Deng, C.; Gao, X.; Li, X.; Tao, D. A local Tchebichef moments-based robust image watermarking. Signal Process. 2009, 89, 1531–1539. [Google Scholar] [CrossRef]
- Liu, R.; Tan, T. An SVD-based watermarking scheme for protecting rightful ownership. IEEE Trans. Multimed. 2002, 4, 121–128. [Google Scholar] [CrossRef]
- Mohammad, A.A.; Alhaj, A.; Shaltaf, S. An improved SVD-based watermarking scheme for protecting rightful ownership. Signal Process. 2008, 88, 2158–2180. [Google Scholar] [CrossRef]
- Shieh, J.M.; Lou, D.C.; Chang, M.C. A semi-blind digital watermarking scheme based on singular value decomposition. Comput. Stand. Interface 2006, 28, 428–440. [Google Scholar] [CrossRef]
- Lee, S.; Jang, D.; Yoo, C.D. An SVD-based watermarking method for image content authentication with improved security. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Philadelphia, PA, USA, 22–27 April 2005; Volume 2, pp. 525–528. [Google Scholar] [CrossRef]
- Chung, K.L.; Yang, W.N.; Huang, Y.H.; Wu, S.T.; Hsu, Y.C. On SVD-based watermarking algorithm. Appl. Math. Comput. 2007, 188, 54–57. [Google Scholar] [CrossRef]
- Chang, C.-C.; Tsai, P.; Lin, C.-C. SVD-based digital image watermarking scheme. Pattern Recognit. Lett. 2005, 26, 1577–1586. [Google Scholar] [CrossRef]
- Patra, J.C.; Soh, W.; Ang, E.L.; Meher, P.K. An improved SVD-based watermarking technique for image and document authentication. In Proceedings of the IEEE Asia Pacific Conference on Circuits and Systems, Singapore, 4–7 December 2006; pp. 1984–1987. [Google Scholar] [CrossRef]
- Kalantari, N.K.; Ahadi, S.M.; Vafadust, M. A robust image watermarking in the Ridgelet domain using universally optimum decoder. IEEE Trans. Circuits Syst. Video Technol. 2010, 20, 396–406. [Google Scholar] [CrossRef]
- Sadreazami, H.; Amini, M. A robust spread spectrum based image watermarking in ridgelet domain. AEU Int. J. Electron. Commun. 2002, 66, 364–371. [Google Scholar] [CrossRef]
- Patra, J.C.; Phua, J.E.; Bornand, C. A novel DCT domain CRT-based watermarking scheme for image authentication surviving JPEG compression. Digital Signal Process. 2010, 20, 1597–1611. [Google Scholar] [CrossRef]
- Patra, J.C.; Karthik, A.; Barnand, C. A novel CRT based watermarking techniques for authentication of multimedia content. Digital Signal Process. 2010, 20, 442–453. [Google Scholar] [CrossRef]
- Suhail, M.A.; Obaidat, M.S. Digital watermarking-based DCT and JPEG model. IEEE Trans. Instrum. Meas. 2003, 52, 1640–1677. [Google Scholar] [CrossRef]
- Rawat, S.; Raman, B. A publicly verifiable lossless watermarking scheme for copyright protection and ownership assertion. AEU Int. J. Electron. Commun. 2012, 66, 955–962. [Google Scholar] [CrossRef]
- Kougianos, E.; Mohanty, S.P.; Mahapatra, R.N. Hardware assisted watermarking for multimedia. Comp. Electr. Eng. 2009, 35, 339–358. [Google Scholar] [CrossRef]
- Sun, M.T.; Chen, T.C.; Gouulie, A.M. VLSI implementation of a 16×16 discrete cosine transform. IEEE Trans. Circuits Syst. 1989, 36, 610–617. [Google Scholar] [CrossRef]
- Uramoto, S.; Inoue, Y.; Takabatake, A.; Takeda, J.; Yamashita, Y.; Terane, H.; Yoshimoto, M. A 100 MHz 2-D discrete cosine transform core processor. J. Solid-State Circuits 1992, 27, 492–498. [Google Scholar] [CrossRef]
- Chan, Y.-H.; Siu, W.-C. On the realization of discrete cosine transform using distributed arithmetic. IEEE Trans. Circuits Syst. I: Fundam. Theory Appl. 1992, 39, 705–711. [Google Scholar] [CrossRef]
- Karthanasis, H.C. A low ROM distributed arithmetic implementation of the forward/inverse DCT/DST using rotations. IEEE Trans. Consum. Electron. 1995, 41, 263–272. [Google Scholar] [CrossRef]
- Srinivasan, V.; Liu, K.J.R. VLSI design of high-speed time recursive 2-D DCT/IDCT processor for video applications. IEEE Trans. Circuits Syst. Video Technol. 1996, 6, 87–96. [Google Scholar] [CrossRef]
- Said, A.; Pearlman, W. A. A new fast and efficient image codec based on set partitioning in hierarchical trees. IEEE Trans. Circuits Syst. Video Technol. 1996, 6, 243–250. [Google Scholar] [CrossRef]
- Wheeler, F.; Pearlman, W.A. SPIHT image compression without lists. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Istanbul, Turkey, 5–9 June 2000; Volume 4, pp. 2047–2050. [Google Scholar]
- Pearlman, W.A.; Islam, A.; Nagraj, N.; Said, A. Efficient, low complexity image coding with set partitioning embedded block coder. IEEE Trans. Circuits Syst. Video Technol. 2004, 6, 1219–1235. [Google Scholar] [CrossRef]
- Senapati, R.K.; Pati, U.C.; Mahapatra, K.K. Reduced memory, low complexity embedded image compression algorithm using hierarchical listless DTT. IET Image Process. 2014, 8, 213–238. [Google Scholar] [CrossRef]
- Engedy, M.; Munaga, V.N.K.; Saxena, A. A robust wavelet based digital watermarking scheme using chaotic mixing. In Proceedings of the First International Conference on Digital Information Management, Bangalore, India, 6–8 December 2006; pp. 36–40. [Google Scholar] [CrossRef]
- Das, C.; Panigrahi, S.; Sharma, V.K.; Mahapatra, K.K. A Novel blind robust image watermarking in DCT domain using inter-block coefficient correlation. AEU Int. J. Electron. Commun. 2014, 68, 244–253. [Google Scholar] [CrossRef]
- Chang, C.C.; Hsiao, J.Y.; Chiang, C.L. An image copyright protection scheme based on torus automorphosim. In Proceedings of the First International Symposium on Cyber Worlds, Tokyo, Japan, 6–8 November 2002; pp. 217–224. [Google Scholar]

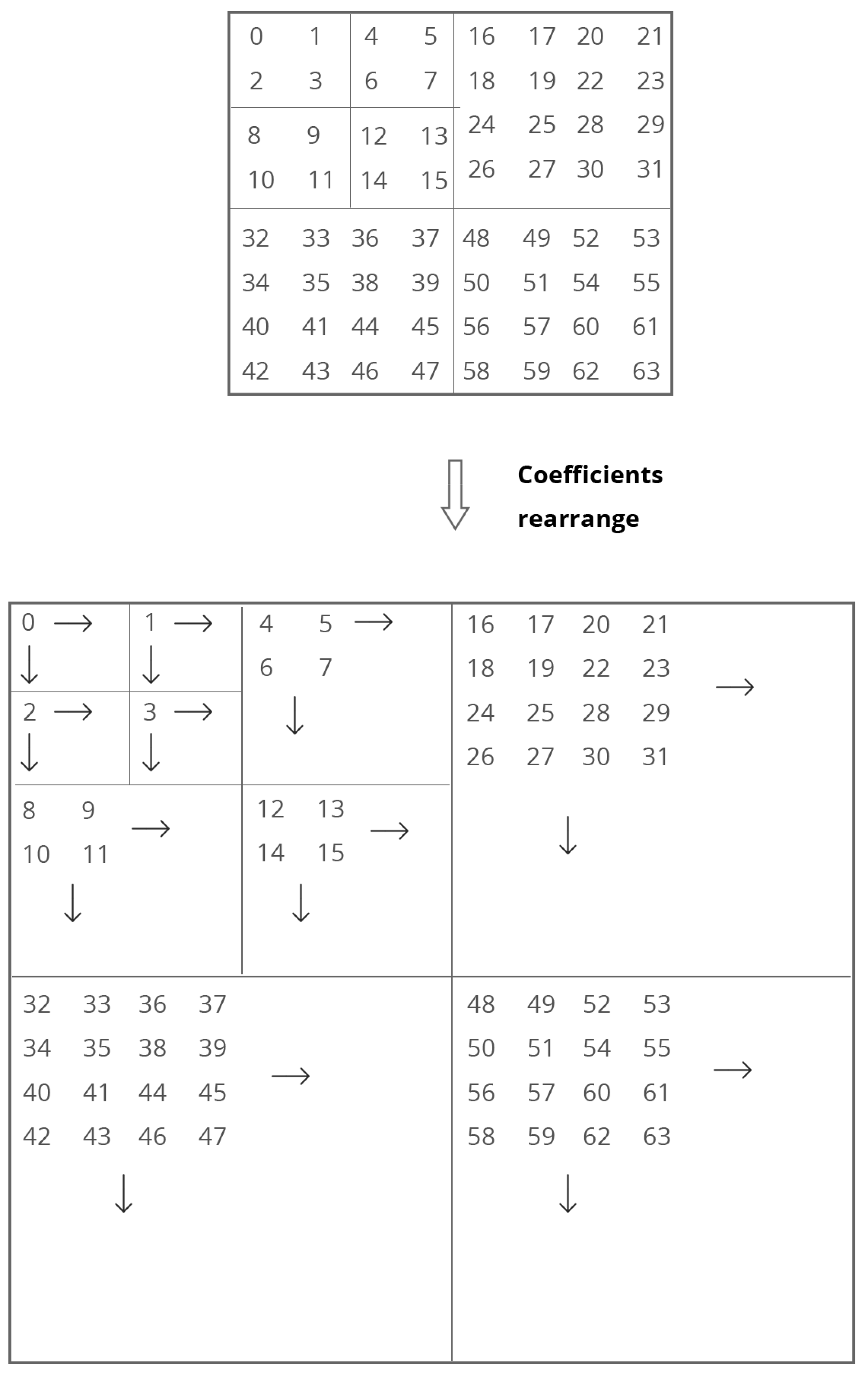


| Image | Bit Rate (bpp) | Algorithm | PSNR (dB) | SSIM | NC | TAF (%) |
|---|---|---|---|---|---|---|
| Lena | 0.25 | SPIHT [35] | 31.24 | 0.9075 | 0.1317 | 65.15 |
| LSK [38] | 30.93 | 0.8974 | 0.3032 | 52.75 | ||
| Proposed | 30.93 | 0.8982 | 0.3201 | 51.61 | ||
| 0.5 | SPIHT | 31.10 | 0.9167 | 0.9848 | 1.71 | |
| LSK | 31.31 | 0.9301 | 0.9828 | 2.04 | ||
| Proposed | 31.36 | 0.9292 | 0.9848 | 1.86 | ||
| 1.0 | SPIHT | 33.87 | 0.9600 | 0.9801 | 1.84 | |
| LSK | 34.02 | 0.9621 | 0.9797 | 1.91 | ||
| Proposed | 34.13 | 0.9617 | 0.9804 | 1.94 | ||
| 1.5 | SPIHT | 34.35 | 0.9658 | 0.9227 | 6.14 | |
| LSK | 34.76 | 0.9677 | 0.9180 | 6.52 | ||
| Proposed | 34.40 | 0.9676 | 0.9149 | 6.32 | ||
| 2.0 | SPIHT | 34.83 | 0.9686 | 0.9298 | 5.56 | |
| LSK | 34.76 | 0.9677 | 0.9180 | 6.52 | ||
| Proposed | 34.90 | 0.9693 | 0.9257 | 5.26 | ||
| 2.5 | SPIHT | 35.41 | 0.9738 | 0.9510 | 4.00 | |
| LSK | 35.33 | 0.9733 | 0.9517 | 4.08 | ||
| Proposed | 35.44 | 0.9740 | 0.9598 | 4.07 | ||
| 3.0 | SPIHT | 35.65 | 0.9724 | 0.9490 | 4.08 | |
| LSK | 35.52 | 0.9744 | 0.9480 | 4.28 | ||
| Proposed | 35.65 | 0.9739 | 0.9558 | 3.27 | ||
| Lossless | SPIHT | 35.83 | 0.9762 | 0.9841 | 1.36 | |
| LSK | 35.68 | 0.9754 | 0.9747 | 2.24 | ||
| Proposed | 36.00 | 0.9750 | 0.9831 | 1.36 |
| Image | Bit Rate (bpp) | Algorithm | PSNR (dB) | SSIM | NC | TAF (%) |
|---|---|---|---|---|---|---|
| Barbara | 0.25 | SPIHT [35] | 26.92 | 0.8454 | 0.0300 | 72.93 |
| LSK [38] | 27.26 | 0.8749 | 0.0527 | 71.27 | ||
| Proposed | 27.25 | 0.8730 | 0.0700 | 70.33 | ||
| 0.5 | SPIHT | 29.42 | 0.9106 | 0.3788 | 47.58 | |
| LSK | 29.03 | 0.9047 | 0.7539 | 19.63 | ||
| Proposed | 28.97 | 0.9034 | 0.7762 | 17.94 | ||
| 1.0 | SPIHT | 31.48 | 0.9474 | 0.9784 | 3.09 | |
| LSK | 32.16 | 0.9572 | 0.9673 | 3.57 | ||
| Proposed | 32.25 | 0.9572 | 0.9737 | 3.27 | ||
| 1.5 | SPIHT | 34.27 | 0.9714 | 0.9737 | 2.84 | |
| LSK | 34.43 | 0.9731 | 0.9689 | 3.25 | ||
| Proposed | 34.50 | 0.9731 | 0.9659 | 3.57 | ||
| 2.0 | SPIHT | 34.77 | 0.9774 | 0.9034 | 7.68 | |
| LSK | 34.78 | 0.9775 | 0.8974 | 8.19 | ||
| Proposed | 34.83 | 0.9784 | 0.9045 | 7.38 | ||
| 2.5 | SPIHT | 35.52 | 0.9801 | 0.9355 | 5.56 | |
| LSK | 35.25 | 0.9800 | 0.9136 | 6.98 | ||
| Proposed | 35.54 | 0.9804 | 0.9416 | 5.26 | ||
| 3.0 | SPIHT | 35.77 | 0.9821 | 0.9521 | 4.15 | |
| LSK | 35.66 | 0.9830 | 0.9477 | 4.41 | ||
| Proposed | 35.86 | 0.9824 | 0.9440 | 4.73 | ||
| Lossless | SPIHT | 36.06 | 0.9822 | 0.9791 | 2.04 | |
| LSK | 35.66 | 0.9814 | 0.9443 | 4.58 | ||
| Proposed | 36.24 | 0.9827 | 0.9770 | 2.19 |
| Image | Bit Rate (bpp) | Algorithm | PSNR (dB) | SSIM | NC | TAF (%) |
|---|---|---|---|---|---|---|
| Boat | 0.25 | SPIHT [35] | 29.34 | 0.9066 | 0.078 | 69.70 |
| LSK [38] | 29.20 | 0.9024 | 0.1425 | 64.76 | ||
| Proposed | 29.21 | 0.9036 | 0.1610 | 63.43 | ||
| 0.5 | SPIHT | 29.61 | 0.9085 | 0.9814 | 2.31 | |
| LSK | 30.04 | 0.9244 | 0.9791 | 2.41 | ||
| Proposed | 30.10 | 0.9241 | 0.9801 | 2.41 | ||
| 1.0 | SPIHT | 33.20 | 0.9599 | 0.9801 | 2.31 | |
| LSK | 33.42 | 0.9660 | 0.9743 | 2.64 | ||
| Proposed | 33.44 | 0.9641 | 0.9757 | 2.36 | ||
| 1.5 | SPIHT | 34.22 | 0.9648 | 0.9119 | 6.95 | |
| LSK | 34.32 | 0.9655 | 0.9088 | 7.15 | ||
| Proposed | 34.34 | 0.9690 | 0.9136 | 6.75 | ||
| 2.0 | SPIHT | 34.87 | 0.9693 | 0.9055 | 7.40 | |
| LSK | 34.80 | 0.9702 | 0.9058 | 7.56 | ||
| Proposed | 34.94 | 0.9709 | 0.9099 | 7.18 | ||
| 2.5 | SPIHT | 35.53 | 0.9732 | 0.9440 | 4.81 | |
| LSK | 35.44 | 0.9745 | 0.9470 | 4.41 | ||
| Proposed | 35.52 | 0.9751 | 0.9456 | 4.51 | ||
| 3.0 | SPIHT | 35.70 | 0.9758 | 0.9564 | 3.48 | |
| LSK | 35.60 | 0.9738 | 0.9396 | 4.88 | ||
| Proposed | 35.75 | 0.9756 | 0.9537 | 3.88 | ||
| Lossless | SPIHT | 35.92 | 0.9758 | 0.9804 | 1.89 | |
| LSK | 35.78 | 0.9747 | 0.9656 | 2.79 | ||
| Proposed | 36.10 | 0.9760 | 0.9811 | 1.73 |
| Attacks | Crop | Noise (Impulse) | Sharpen | Invert | Histogram Equalize |
|---|---|---|---|---|---|
| Attacked Images |  |  |  |  |  |
| PSNR (dB) | 35.8 | 35.9 | 37.9 | 35.9 | 34.9 |
| Extracted Watermark |  |  |  |  |  |
| NC | 0.7158 | 0.7208 | 0.5034 | 0.9771 | 0.5415 |
| Attacks | Crop (top left) | Crop (top right) | Crop (bottom left) | Crop (bottom right) | Auto contrast |
| Attacked Images |  |  |  |  |  |
| PSNR (dB) | 35.8 | 35.8 | 35.84 | 35.86 | 35.82 |
| Extracted Watermark |  |  |  |  |  |
| NC | 0.7316 | 0.7269 | 0.7411 | 0.7316 | 0.9838 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shivani, J.L.D.; Senapati, R.K. Robust Image Embedded Watermarking Using DCT and Listless SPIHT. Future Internet 2017, 9, 33. https://doi.org/10.3390/fi9030033
Shivani JLD, Senapati RK. Robust Image Embedded Watermarking Using DCT and Listless SPIHT. Future Internet. 2017; 9(3):33. https://doi.org/10.3390/fi9030033
Chicago/Turabian StyleShivani, J. L. Divya, and Ranjan K. Senapati. 2017. "Robust Image Embedded Watermarking Using DCT and Listless SPIHT" Future Internet 9, no. 3: 33. https://doi.org/10.3390/fi9030033
APA StyleShivani, J. L. D., & Senapati, R. K. (2017). Robust Image Embedded Watermarking Using DCT and Listless SPIHT. Future Internet, 9(3), 33. https://doi.org/10.3390/fi9030033























