1. Introduction
The Internet of Things (IoT) influences the advancement of modern industries and smart cities, particularly through the concept of intelligent industry [
1]. A core component of this transformation is the Industrial Internet of Things (IIoT), which enables the collection and analysis of vast amounts of data from IoT devices and industrial machinery. IIoT facilitates seamless connectivity among distributed devices—including industrial sensors, machines, and controllers—to optimize operations through real-time data-driven decision-making [
2]. With the integration of edge computing and cloud-based infrastructures, IIoT enables advanced services such as system optimization, predictive analytics, and remote monitoring.
Despite these technological advancements, the lack of standardized security frameworks renders IIoT networks highly vulnerable to sophisticated cyber threats. The growing volume and complexity of data intensify the need for effective cybersecurity mechanisms. Traditional rule-based and signature-based detection systems are insufficient for identifying advanced, evolving threats [
3]. Consequently, cyber threat intelligence (CTI) has emerged as a proactive strategy for identifying, analyzing, and mitigating threats by leveraging real-time data on Indicators of Compromise (IOCs), adversarial tactics, and zero-day vulnerabilities. CTI enables organizations to make informed, evidence-based security decisions to protect critical infrastructure [
4].
However, centralized CTI systems often struggle with latency, scalability, and privacy issues, particularly in distributed and heterogeneous IIoT environments. To overcome these limitations, artificial intelligence (AI)—especially machine learning (ML)—is increasingly integrated into CTI to support threat detection, analysis, and prediction in real time [
5]. Nonetheless, centralized ML architectures introduce concerns around data privacy and communication overhead, making them unsuitable for IIoT’s distributed nature.
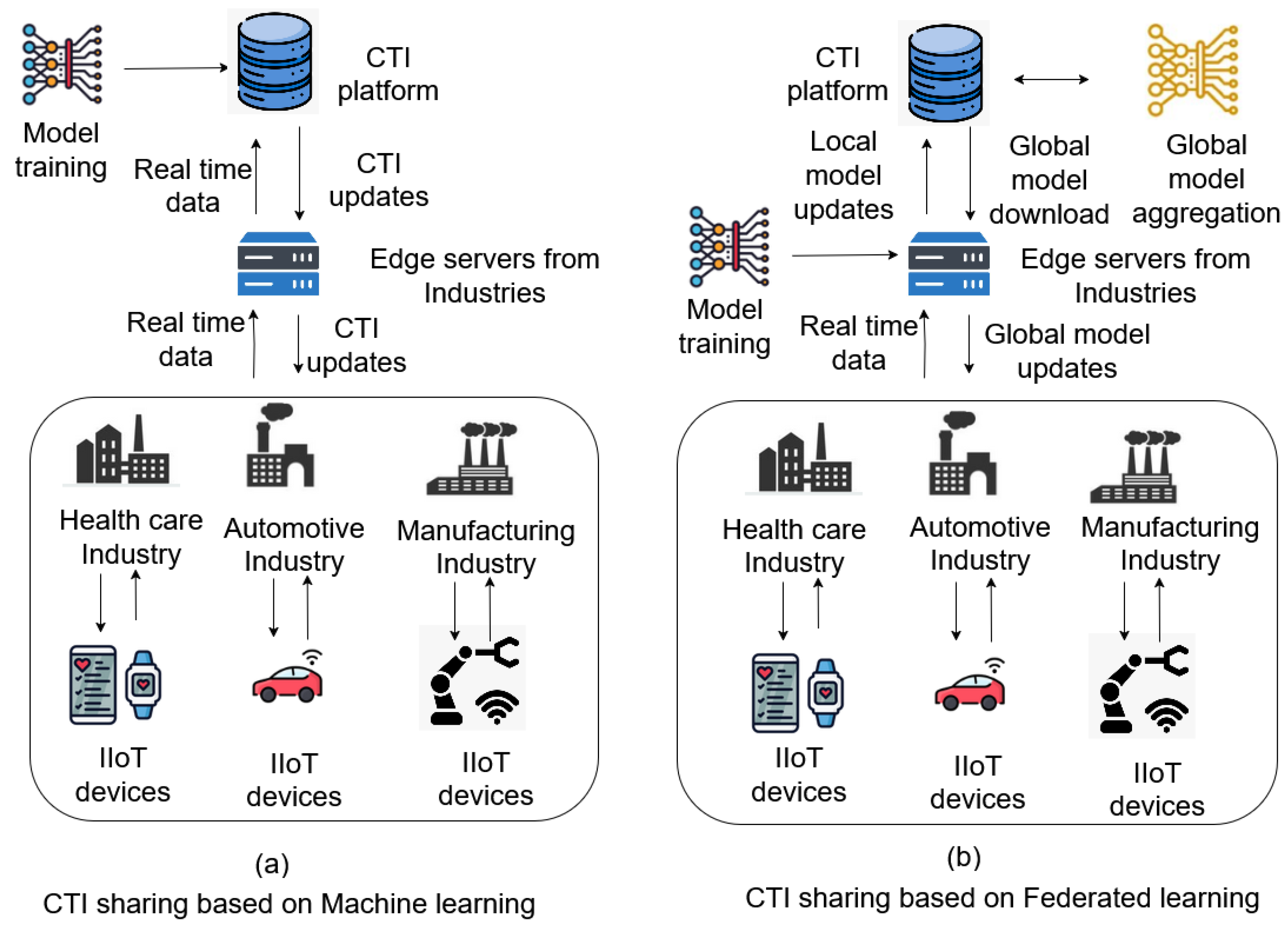
To address these challenges, federated learning (FL) offers a promising solution. It enables collaborative model training across IIoT devices without sharing raw data, thereby preserving data privacy and reducing the risk of breaches [
6]. In FL-based CTI frameworks, only model updates are exchanged, allowing organizations to build shared threat intelligence while complying with privacy constraints. This makes FL especially suited for CTI in IIoT settings where data sensitivity is important.
Several surveys, such as those by [
7,
8,
9], have thoroughly investigated AI-driven threat detection in IIoT environments. However, they do not address the use of CTI with federated learning in full, which is increasingly crucial for privacy-aware collaborative defense systems.
Table 1 provides a comparative overview of recent surveys related to cybersecurity, CTI, and federated learning in IIoT.
References [
12,
13] focus on CTI frameworks and ML-based intelligence sharing, but they lack consideration of decentralized approaches like FL that mitigate privacy and data governance challenges. While Ref. [
14] includes elements of FL-based CTI, it does not provide a detailed classification, challenges, or taxonomy specific to IIoT systems.
Moreover, refs. [
10,
15] introduce FL in cybersecurity, but without integrating it within CTI frameworks. Lastly, semantic approaches reviewed by [
16] offer promising directions for CTI enrichment but omit the collaborative potential of FL for decentralized threat sharing. Therefore, as shown in the final row of
Table 1, our proposed survey is one of the first to holistically address FL-based CTI within the IIoT context, covering AI integration, privacy preservation, taxonomy development, and future research directions.
1.1. Literature Review Strategies
This work is conducted as a review, following the guidelines of Kitchenham and Charters, and is reported in accordance with PRISMA recommendations. The aim is to comprehensively explore the convergence of federated learning (FL) and cyber threat intelligence (CTI) in the Industrial Internet of Things (IIoT), while ensuring the transparency and reproducibility of the review process.
Databases and Search Strings: We searched multiple leading digital libraries, including ACM Digital Library, IEEE Xplore, SpringerLink, ScienceDirect, and MDPI, to ensure wide coverage. The search was conducted between August 2024 and January 2025. Search queries combined Boolean operators with controlled vocabulary; for example:
“cyber threat intelligence” AND “federated learning”
“IIoT” OR “Industrial Internet of Things” AND “federated learning”
“privacy-preserving learning” AND “threat intelligence”
These terms were iteratively refined to balance recall and precision and expanded to include synonyms such as “distributed security,” “collaborative learning,” and “intrusion detection.”
Timeframe: The review covers publications from 2018 to 2025, encompassing both the early adoption of FL in security contexts and the latest advancements. The extended timeframe is necessary to illustrate the evolution of FL-based CTI frameworks and to include very recent contributions (2024–2025) that reflect state-of-the-art trends.
Inclusion and Exclusion Criteria: Studies were included if they (i) explicitly addressed CTI in conjunction with FL or (ii) proposed IIoT security frameworks in which FL was central to the threat intelligence process. Studies were excluded if they were (i) purely conceptual without technical detail, (ii) not peer-reviewed, or (iii) irrelevant to either CTI or FL in IIoT contexts. Only English-language publications were considered.
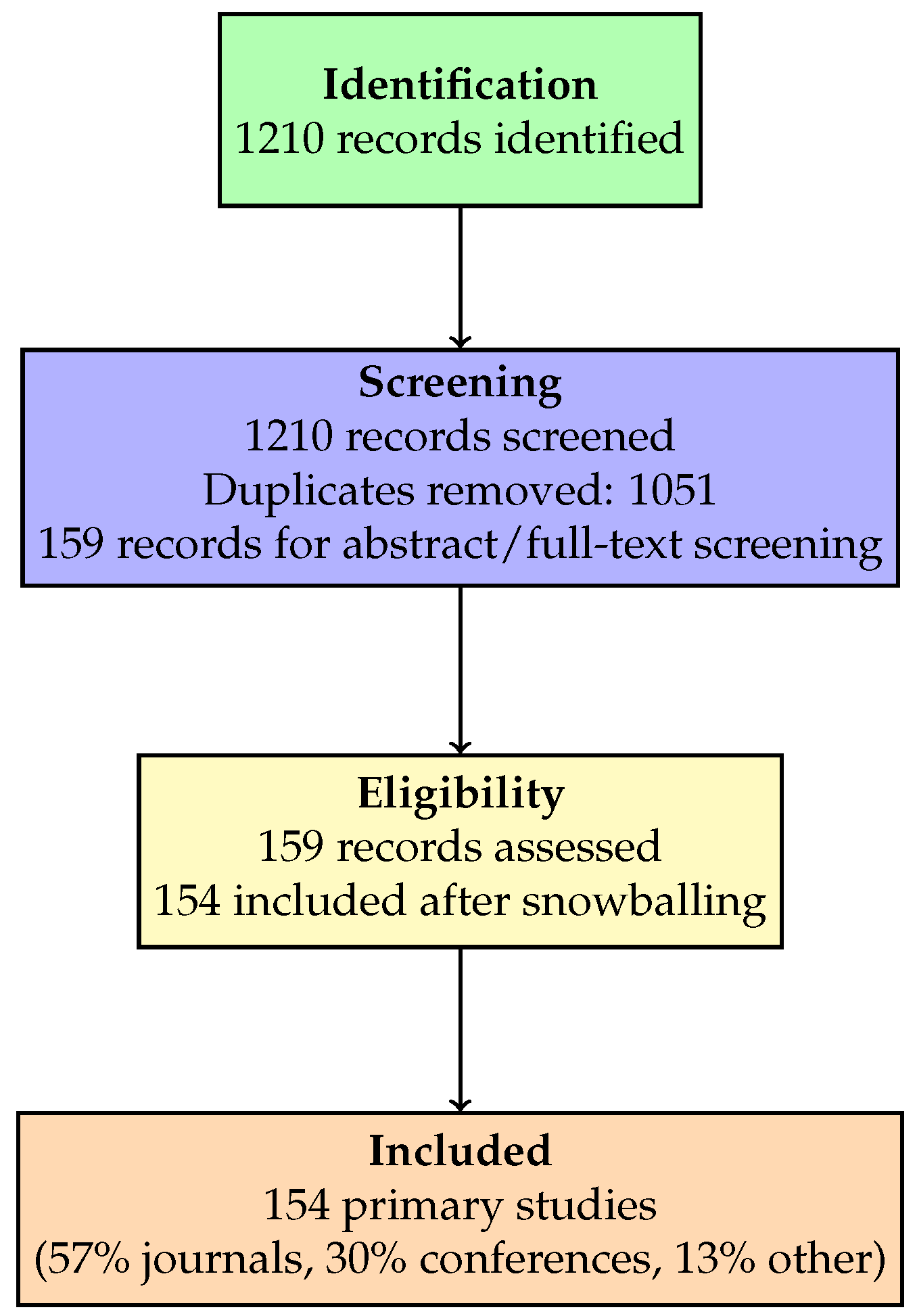
Screening Process: The initial search yielded 1210 records. After removing duplicates and applying the inclusion and exclusion criteria, 159 papers were retained for abstract and full-text screening. Using forward and backward snowballing, the final dataset comprised 154 primary studies: 57% journal articles, 30% conference papers, and 13% other sources. Nearly all (99%) were published after 2019, reflecting the rapid growth of this field.
A PRISMA flow diagram (
Figure 1) is included to illustrate the selection process. The categorization and taxonomy presented in
Section 3 and
Section 4 are grounded in this systematically identified dataset, ensuring that the classification reflects evidence-based analysis rather than descriptive grouping. This systematic approach provides a transparent foundation for synthesizing developments in FL-driven CTI for IIoT, identifying knowledge gaps, and guiding future research directions.
1.2. Contributions
This paper makes the following key contributions:
We present a comprehensive survey of cyber threat intelligence (CTI) strategies for Industrial IoT (IIoT), emphasizing privacy-preserving federated learning (FL) approaches.
We analyze recent studies summarized in
Table 1 to identify research gaps at the intersection of FL and CTI.
We contribute an empirical synthesis of FL aggregation strategies outlining trade-offs in accuracy, robustness, and efficiency under IIoT-specific constraints— offering a practical decision-support tool for system designers.
We highlight key deployment challenges, including non-IID data, communication overhead, adversarial threats, and resource heterogeneity in IIoT environments.
We propose a taxonomy and research roadmap aligning FL techniques with CTI goals to support scalable, secure, and decentralized intelligence systems for next-generation IIoT.
Unlike previous surveys that addressed AI-based CTI [
12,
13], FL in IoT [
10,
15], or semantic enrichment [
16], this review uniquely integrates a (i) systematic PRISMA-based methodology, (ii) an empirical synthesis of aggregation strategies, and (iii) a deployment-focused taxonomy for IIoT.
The remainder of this paper is organized as follows.
Section 2 outlines the preliminaries of CTI, AI, and FL;
Section 3 offers a detailed review of the FL architecture and its working mechanisms.
Section 4 presents a review of existing threat detection techniques that utilize FL in IIoT.
Section 5 provides suggestions for future research, and
Section 6 concludes the article.
3. Review of Federated Learning
This section categorizes FL based on client type, data partitioning, network architecture, and orchestration strategy for effective IIoT deployment.
3.1. FL by Data Partitioning
FL can be classified by how data are partitioned among clients [
24]:
Horizontal FL (HFL): Clients share the same features but different samples. Suitable for similar IIoT domains across locations.
Vertical FL (VFL): Clients observe the same entities with different features, enabling cross-domain feature fusion.
Federated Transfer Learning (FTL): Supports collaboration with minimal feature or sample overlap by transferring knowledge from trained models.
Table 3 offers more information on their comparison in approaches, benefits, challenges, and basic use cases.
Table 3 summarizes key differences between HFL, VFL, and FTL in terms of their applicable scenarios, methodological approaches, advantages, challenges, and representative use cases within cyber-physical threat intelligence (CTI) for IIoT systems. HFL is effective when data are horizontally partitioned, typically across similar devices or environments. VFL supports vertical partitioning across organizations that share common entities but collect different attributes. FTL provides flexibility in heterogeneous settings where data overlap is limited, enabling collaboration through model transfer. The table helps clarify when and how each FL type can be strategically applied depending on the data distribution and system goals.
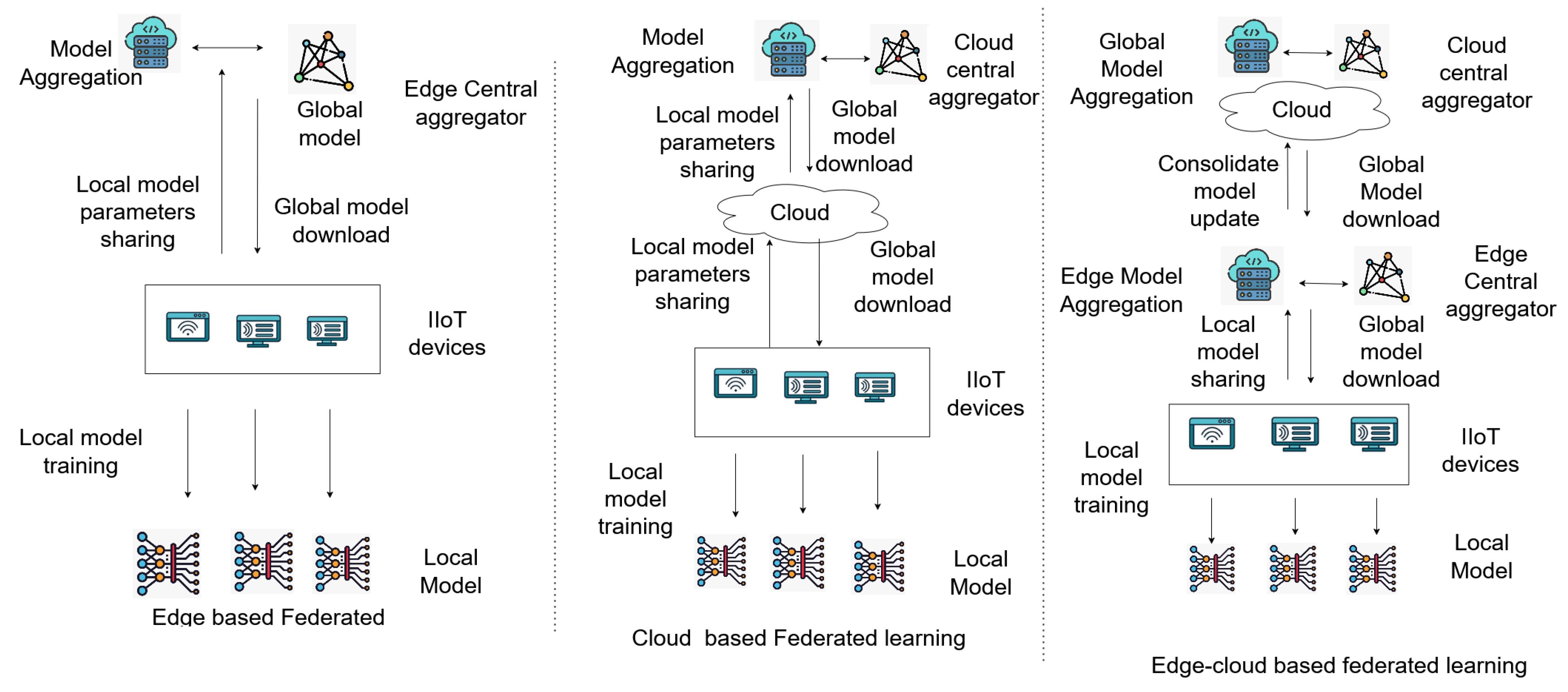
3.2. FL by Network Architecture
FL architectures are generally categorized into centralized, decentralized, and hierarchical models [
24,
31]. In centralized FL, a central server aggregates updates from participating clients. This model can be implemented in different configurations: cloud-based FL is suitable for large-scale CTI systems, edge-based FL reduces latency by aggregating updates closer to data sources, and edge-cloud hybrid FL combines both approaches to support scalable and responsive threat modeling.
Figure 3 showcases the above three cloud-edge orchestration strategies.
Decentralized FL removes the central aggregator, allowing clients to exchange model updates directly in a peer-to-peer manner. Peer-to-peer FL is well-suited for cooperative IIoT environments, while blockchain-based FL ensures tamper-proof and auditable collaboration, especially in cross-organizational settings.
Hierarchical FL introduces intermediate aggregation layers between local clients and the global model. In two-layer architectures, model updates flow from edge devices to the cloud via edge aggregators, whereas three-layer architectures add a regional layer to facilitate national-scale CTI operations. Each structure offers trade-offs in scalability, efficiency, and trust management, depending on the operational requirements of the IIoT environment.
3.3. FL Training Process in IIoT
This subsection provides a mathematical description of the federated learning (FL) model training process as applied to the Industrial Internet of Things (IIoT) context. It outlines the sequential stages, formalizes model update equations, and highlights key considerations for deploying FL in resource-constrained and heterogeneous IIoT environments.
Let
M denote the set of
n IIoT devices participating in FL. Each client
holds a local dataset
and selects a subset
for training. The typical FL process involves the following stages [
23,
24,
25,
28,
31,
32,
33,
34]:
Client Selection A subset of eligible clients is selected based on data quality, device capability, and diversity. The selection impacts model performance and convergence.
FL Initialization The FL system defines tasks, data sources, and evaluation metrics. The model architecture, optimization strategy, and data partitioning are established. Training begins with the central server distributing initial parameters.
Global Model Initialization: In round
t, each client
receives the current global model
:
Data Preparation: Clients preprocess and clean local data to ensure quality and consistency. Redundant or low-value data are removed before training begins.
Local Model Training: Each client updates the model locally using its data subset
:
where
is the learning rate and
is the local loss function.
Global Aggregation: The server aggregates local updates to produce the global model:
This continues iteratively until convergence or target accuracy is reached.
Model Deployment: The finalized model is deployed for inference across IIoT environments and may be fine-tuned with new data to adapt to changing conditions.
Aggregation Strategies: Various aggregation methods can be used depending on requirements such as convergence speed, privacy, or robustness [
27,
34].
Table 4 provides a comparative overview of twelve aggregation strategies commonly employed in FL. These methods differ in how they weigh client updates, handle statistical heterogeneity, and balance trade-offs among convergence rate, communication cost, and privacy preservation. Strategies such as FedAvg, FedProx, and Scaffold are contrasted alongside more recent approaches designed to enhance robustness or adapt to non-IID data distributions. This comparison helps inform the selection of an appropriate aggregation technique based on specific IIoT deployment requirements and constraints.
3.4. FL Model Evaluation
Federated learning (FL) supports various data types reflecting the distributed and heterogeneous nature of real-world environments. Unlike centralized ML, which assumes IID data, FL often operates on non-IID data due to device variability, user behavior, and context. It also accommodates vertical, horizontal, sparse, sequential, and hybrid data partitions [
53,
54,
55].
Evaluating FL models is more complex than in centralized ML due to data decentralization and privacy constraints. Since servers lack direct access to client data, indirect evaluation strategies are used to assess model quality, guide client selection, detect adversaries, and ensure fairness [
56,
57], as summarized in
Table 5.
3.5. Empirical Comparisons: A Strategic Lens on Aggregation Trade-Offs
A key contribution of this survey is the synthesis of empirical findings that reveal critical trade-offs among federated learning (FL) aggregation methods within the context of cyber threat intelligence (CTI) for Industrial IoT (IIoT) environments. Despite the proliferation of FL strategies in the literature, few works offer a comparative lens that aligns technical performance with IIoT-specific operational constraints. This section consolidates empirical evidence to highlight how different aggregation strategies perform across key metrics, offering actionable insights for practitioners and researchers designing FL-enabled CTI systems.
FedAvg is simple to implement but suffers a 15% performance drop under non-IID data, a common characteristic in IIoT due to device heterogeneity.
Weighted aggregation improves accuracy by 10%, particularly in unbalanced environments, but requires precise tuning of client weights—posing scalability challenges.
Clipped averaging enhances robustness against adversarial updates (+8%) but increases computational overhead by 5%.
Differential privacy strengthens confidentiality but incurs a 7% reduction in model accuracy due to noise injection.
Adversarial aggregation techniques yield up to 12% resilience improvement but are computationally intensive, making them more suitable for high-stakes industrial applications.
FL-based models can reach 90% accuracy in IID settings, but this can drop by 20% under non-IID distributions—an issue highly relevant for CTI in IIoT, where data are often sparse, imbalanced, and decentralized.
As illustrated in
Table 6, robust aggregation strategies such as Krum and ClippedAvg are better suited for adversarial settings but come at the cost of higher computational demand. Krum filters out anomalous or malicious updates, offering high resilience, whereas ClippedAvg mitigates the influence of extreme values, stabilizing the model under noisy conditions.
Conversely, FedAvg is ideal for resource-constrained or latency-sensitive deployments due to its simplicity, but it underperforms in non-IID conditions common in IIoT. FedProx adds regularization to enhance fairness across clients, although this slows convergence. Multi-Krum advances robustness further but requires significant computation, limiting its applicability in lightweight edge systems.
This comparative evaluation not only bridges a gap in current FL-CTI literature but also offers a decision-support framework for choosing aggregation strategies tailored to varying IIoT security, performance, and resource demands. It underscores the central thesis of this paper: designing effective FL-based CTI frameworks for IIoT requires a context-aware balance of accuracy, privacy, robustness, and scalability.
4. Real-World FL Applications for CTI in IIoT
Federated learning (FL) is increasingly used in cyber threat intelligence (CTI) systems to secure Industrial IoT (IIoT) environments by enabling collaborative threat detection without centralized data sharing [
58]. This decentralized learning paradigm preserves privacy and improves scalability, which is critical for sensitive and heterogeneous IIoT settings. However, FL models must contend with challenges such as non-IID data distributions, communication overhead, model-poisoning attacks, and hardware limitations [
59].
Deploying FL for CTI in IIoT requires architectures that balance privacy, scalability, and low latency, addressing challenges like resource-constrained devices and non-independent and identically distributed (non-IID) data. We identify three primary deployment models, summarized in
Table 7.
Beyond academic prototypes, several industry-facing deployments illustrate the applicability of FL-CTI in IIoT contexts. For instance, Jithish et al. [
46] demonstrated federated anomaly detection across smart grid substations, while Verma et al. [
47] applied an edge–cloud FLDID framework in smart manufacturing environments. In the healthcare domain, Astillo et al. [
61] deployed FL for privacy-preserving diabetes monitoring across hospital IoT infrastructures. These case studies, together with others summarized in
Table 7 and
Table 8, highlight how deployment choices (edge–cloud, hierarchical, or decentralized) manifest in practical IIoT scenarios with real operational constraints and performance outcomes.
Edge-Cloud Model:
In the edge-cloud model, IIoT devices (e.g., sensors) perform local model training, and a central cloud server aggregates updates to build a global CTI model. This model minimizes latency, making it suitable for real-time threat detection in IIoT applications like smart manufacturing.
Hierarchical Model:
Hierarchical models use intermediate edge servers (e.g., gateways) to perform partial aggregation, with a central server finalizing the global model. This model enhances scalability by reducing communication with the central server, making it ideal for large-scale IIoT deployments like smart grids.
Fully Decentralized Model:
Fully decentralized models eliminate central servers, with IIoT devices collaborating peer-to-peer using protocols like blockchain for trust management. This maximizes privacy, which is critical for sensitive IIoT applications like oil and gas.
As discussed in
Section 3.5, the choice of aggregation strategy significantly influences model accuracy, robustness, and convergence. For example, ClippedAvg and Krum offer higher resilience in adversarial environments, while FedAvg provides efficiency in resource-constrained IIoT deployments. These trade-offs are crucial when applying FL to specific cybersecurity tasks. Complementary defenses—such as differential privacy, secure aggregation, and adversarial training—are often integrated to enhance robustness [
28].
FL-based threat detection has been applied across a range of CTI tasks, including malware detection, anomaly detection, intrusion detection systems (IDS), trust management, botnet identification, and phishing detection. The subsections below offer recommendations for the representative case examples.
4.1. FL-Based Malware Detection
Traditional malware detection approaches struggle with evolving attack vectors and data privacy concerns. FL addresses these limitations by enabling collaborative training across edge devices without exposing raw data. Several frameworks have employed cross-silo learning and task-specific feature extraction to improve detection performance in IIoT networks [
36,
62].
To handle non-IID settings, techniques like associative rule mining and Markov chains [
63] have been used. Lightweight models such as SIM-FED [
64], which employs a 1D CNN, are designed for IIoT scalability and demonstrate robustness against white-box and black-box attacks. Ref. [
65] propose a DNN-based flowchart for distributed traffic classification, while [
66] use graph-based models (Fed-MalGAT, Fed-MalGCN) to leverage function call graphs (FCGs) and capture semantic code structures—improving detection accuracy in complex threat scenarios.
Summary and Challenges. FL-based malware detection frameworks demonstrate strong potential for privacy-preserving, scalable defense in IIoT. However, performance remains highly sensitive to non-IID distributions, adversarial manipulation, and communication overhead. Future work should emphasize adaptive aggregation, lightweight models, and real-world benchmarking on evolving malware datasets.
4.2. FL-Based Intrusion Detection Systems (IDS)
Intrusion detection systems (IDS) benefit significantly from FL’s privacy-preserving capabilities, particularly in IIoT deployments with distributed attack surfaces. Systems such as FELIDS [
29], Fed-ANIDS [
52], and MV-FLID [
51] integrate DNNs and multiview learning for improved anomaly detection. However, the vulnerability of FL to backdoor attacks, as shown in [
37], has prompted research into more robust aggregation strategies and defense mechanisms.
To improve resilience and communication efficiency, several works incorporate advanced aggregation or encryption techniques. Ref. [
30] enable cross-organizational model sharing, while FLDID [
47] uses encryption for secure gradient exchange. DAFL [
31] dynamically adjusts aggregation weights, aligning with empirical insights that weighted or robust aggregation (e.g., ClippedAvg) enhances model performance under heterogeneity. Ref. [
67] emphasize the benefits of local training to reduce latency and enhance scalability. Ref. [
68] further demonstrate that FL outperforms centralized machine learning in both detection accuracy and data confidentiality.
Summary and Challenges. FL-based IDS solutions improve anomaly detection while safeguarding data privacy, yet they remain vulnerable to poisoning and backdoor attacks. Robust aggregation, encryption, and hybrid edge-cloud models are essential directions to balance accuracy, latency, and resilience in IIoT deployments.
4.3. FL-Based Phishing and Spam Detection
Phishing and spam attacks are persistent threats in IIoT environments, often leveraging email, SMS, and messaging protocols to deliver malicious payloads or exfiltrate sensitive information. These attacks frequently involve impersonation, spoofed links, or context-aware social engineering. Due to the sensitive nature of communication data, centralized phishing detection systems raise privacy and regulatory concerns. Federated learning (FL) provides a decentralized, privacy-preserving alternative that enables collaborative detection without exposing raw user data.
Recent FL-based approaches enhance phishing and spam detection by combining secure training with natural language processing (NLP), lightweight model architectures, and robust aggregation methods to address IIoT-specific challenges such as non-IID data and adversarial risks. Insights from the previous
Section 3 highlight that resilient aggregation (e.g., ClippedAvg, Multi-Krum) improves detection reliability under heterogeneous and potentially compromised clients.
Notable systems include:
ConvLSTM-FL: Ref. [
69] apply a ConvLSTM model within an FL framework to detect phishing content across distributed text streams.
SENTINEY: Ref. [
70] integrate Secure Multi-Party Computation (SMPC), unsupervised clustering, and string-matching to build adaptive and privacy-respecting phishing detectors.
DistilBERT-FL: Ref. [
71] implement SMS spam detection using federated DistilBERT, ensuring privacy while leveraging deep semantic representations.
FLPhish: Ref. [
43] address Byzantine threats through ensemble learning and client reputation scoring, aligning with robust aggregation recommendations from empirical studies.
On-Device Learning: Refs. [
72,
73] implement mobile spam detection entirely on-device, reducing communication overhead and minimizing attack surfaces.
FPF: Ref. [
74] apply federated NLP pipelines for phishing email detection using context-aware local features.
Client Grouping: Ref. [
48] improve personalization by clustering clients with similar behavioral profiles, improving convergence under non-IID settings.
PhoBERT-FL: Ref. [
75] demonstrate the effectiveness of federated PhoBERT in Vietnamese SMS classification, with promising results in multilingual IIoT contexts.
These approaches underscore the practical viability of FL for real-time phishing and spam detection in IIoT, especially when enhanced with behavioral personalization, robust aggregation, and efficient NLP. Selecting aggregation strategies suited to the threat model and system constraints—such as ClippedAvg for robustness or FedAvg for low-resource scenarios—is critical for maintaining performance in real-world deployments.
Summary and Challenges. FL-based phishing and spam detection frameworks leverage NLP, secure multi-party computation, and lightweight deep models to achieve privacy-preserving protection across distributed IIoT communication channels. While these approaches demonstrate strong adaptability to multilingual and context-aware data, challenges remain in handling adversarial clients, non-IID distributions, and high communication costs. Future work should explore personalized federated models, clustering-based client grouping, and robust aggregation mechanisms (e.g., ClippedAvg, Multi-Krum) to maintain accuracy while minimizing resource overhead in real-world deployments.
4.4. FL-Based Botnet Detection
The rise in connected IoT devices has expanded the attack surface for botnets, which leverage device heterogeneity and traffic volume to evade centralized detection. Traditional methods often fall short due to scalability, privacy concerns, and model brittleness under adversarial conditions. Federated learning (FL) offers a distributed and privacy-preserving solution for collaborative botnet detection in IIoT environments.
Refs. [
76,
77] designed FL-based frameworks enabling localized model training with shared aggregation, allowing adaptation to device-specific behavior. Ref. [
78] combined FL with Network and Host IDS systems for early DDoS detection via decentralized correlation of malicious activities.
Ref. [
50] introduced explainable FL with SHAP-based insights from client models to enhance global model interpretability. Ref. [
44] used FedAvg in a deep learning framework for zero-day botnet detection but encountered limitations under non-IID data and adversarial interference—highlighting a need for robust aggregation, such as Krum or ClippedAvg, as discussed in
Section 3.
To improve efficiency and scalability, Ref. [
79] proposed a lightweight FL framework that applies hyperparameter tuning and dimensionality reduction to mitigate data imbalance and memory overhead. Ref. [
80] also optimized aggregation mechanisms, aligning with empirical insights that aggregation strategies directly impact detection accuracy and system robustness in distributed environments.
Summary and Challenges. Botnet detection in IIoT benefits greatly from FL’s distributed collaboration, allowing detection of zero-day attacks and device-specific patterns without centralized data sharing. Recent works show improved interpretability through explainable FL and scalability via lightweight frameworks. Nonetheless, resilience against adversarial manipulation and efficiency under non-IID data remain unresolved. Future research should prioritize adaptive aggregation, efficient communication compression, and cross-domain validation to ensure botnet detection systems remain robust, scalable, and applicable to heterogeneous IIoT environments.
4.5. FL-Based Trust Management
Trust management in IIoT requires accurate assessment of client reliability while preserving data privacy. FL enables decentralized trust inference and collaboration across edge nodes, supporting adaptive defenses in dynamic threat environments.
Ref. [
81] introduced a hybrid CNN–BiLSTM FL model embedded in a zero-trust framework, capturing spatio-temporal threat signatures. Ref. [
42] proposed FedBayes, leveraging Bayesian inference for resilient aggregation—though its vulnerability to adversarial perturbation indicates the need for more robust strategies like Multi-Krum or ClippedAvg for stronger fault tolerance, per
Section 3.5.
Ref. [
82] employed asynchronous FL and reinforcement learning to assign trust scores in vehicular networks, while [
83] combined blockchain and zero-trust FL for decentralized collaboration. Environmental variability and non-IID data remain challenges that can be addressed through adaptive aggregation or client clustering.
Ref. [
84] and SAFL [
85] integrate blockchain and self-attention mechanisms, respectively, to improve traceability and local personalization. These systems illustrate how context-aware aggregation and hybrid FL architectures can improve trust assessment in hostile IIoT settings.
Summary and Challenges. FL-based trust management enhances reliability assessments in IIoT by decentralizing decision-making and integrating zero-trust and blockchain principles. These systems demonstrate improved traceability, personalization, and fault tolerance. However, they face significant challenges in adversarial environments, where malicious clients or poisoned updates can distort trust scores. Developing hybrid trust models that combine Bayesian inference, reinforcement learning, and adaptive aggregation will be critical for strengthening resilience while maintaining low-latency performance suitable for dynamic industrial ecosystems.
4.6. FL-Based Anomaly Detection
Anomaly detection is central to CTI, especially in IIoT, where unusual behaviors often indicate compromise. FL allows edge devices to collaboratively detect anomalies while safeguarding raw data. However, as shown in
Section 3.5, non-IID data and adversarial risks demand careful selection of aggregation strategies to ensure convergence and robustness.
Ref. [
40] used GRU models with ensemble aggregation to enhance accuracy under variable network conditions. Ref. [
46] applied SSL/TLS-based aggregation in smart meters, offering secure and low-latency anomaly detection. To prevent single points of failure, Ref. [
38] introduced blockchain-based asynchronous FL.
In resource-constrained ICS environments, lightweight solutions like [
86] autoencoder-Fourier hybrid achieve efficiency and performance. Ref. [
87] proposed energy-weighted FL using symbolic sensor data to calculate global thresholds. These strategies reflect a need for flexible aggregation—FedProx or weighted FedAvg may balance personalization with generalization.
Ref. [
45] enhanced motion-aware detection with FL-based Flownet-YOLOv8n, reducing latency via edge aggregators. FedeX [
88] integrated VAE and XAI for explainability, while [
61] addressed device-level anomaly detection in healthcare using quantized FL to reduce resource load.
Summary and Challenges. Anomaly detection represents a core CTI application for FL in IIoT, addressing threats ranging from industrial control system faults to healthcare monitoring anomalies. Current advances integrate secure aggregation, ensemble learning, and lightweight deep models, improving both detection accuracy and efficiency. However, performance remains constrained by device heterogeneity, scarce benchmark datasets, and vulnerability to adversarial manipulation. Future directions should emphasize benchmark creation, explainable anomaly detection, and adaptive aggregation strategies that can dynamically balance personalization with global generalization in IIoT deployments.
4.7. FL-Based CTI Approaches for IIoT Applications
The taxonomy presented in this section was not developed in a purely descriptive manner but was systematically derived from the 154 primary studies identified in
Section 1.1. Specifically, we classified works according to four evidence-based criteria: (i) data partitioning strategy (e.g., HFL, VFL, FTL), (ii) orchestration approach (edge–cloud, hierarchical, decentralized), (iii) aggregation method (e.g., FedAvg, FedProx, robust aggregation), and (iv) targeted CTI task (e.g., intrusion detection, malware detection, trust management). This multi-criteria classification aligns with clustering-based frameworks in the FL survey literature [
23,
28,
34], ensuring that categories emerge from systematic grouping of shared attributes across studies rather than subjective description. In this way, the taxonomy is both reproducible and grounded in the evidence base of CTI-relevant FL research.
FL-based CTI frameworks in IIoT aim to decentralize intelligence sharing while preserving data privacy and operational latency. Aggregation method selection is critical—robust techniques like ClippedAvg are well-suited for adversarial settings, whereas FedAvg may suffice in cooperative, low-risk environments.
Ref. [
89] proposed SeCTIS, merging swarm learning, blockchain, and zero-knowledge proofs to enable secure and distributed threat collaboration. Ref. [
90] introduced FL-CTIF, combining enriched attack data with a privacy-preserving ANN model. Ref. [
91] designed FedTIU, a lightweight DDoS detection framework using edge-based collaborative FL.
DLTIF [
92] applied distributed learning to maritime CTI, integrating FL with knowledge-driven classification. Ref. [
93] developed a federated forest-based framework for adaptive edge defense, demonstrating robust CTI through hierarchical local-global fusion.
4.8. FL-Based CTI Approaches for Other Applications
FL-based CTI systems are increasingly adopted in domains beyond IIoT, including healthcare, SDN, and financial systems. In such contexts, model robustness, fairness, and privacy remain vital, and empirical findings (
Section 3.5) suggest strategies like FedProx or grouped aggregation can help mitigate heterogeneity.
Refs. [
94,
95] developed FL-enabled IDS in SDNs and IoMTs using PCA-driven feature analysis under non-IID constraints. Ref. [
60] employed encrypted FL with adversarial filtering for smart grid security. Ref. [
96] introduced FedCRI to share mobile cyber-risk intelligence while maintaining privacy.
Ref. [
20] used blockchain-FL for secure CTI sharing in IoT networks, addressing communication latency and integrity. FedCTI [
6,
97] applied federated intelligence to anomaly detection in smart spaces and Open Banking, respectively.
BFLS [
98], CELEST [
99], and FGNN [
100] combined GNNs with FL for global threat pattern recognition with poisoning resistance. Ref. [
101] integrated MISP, SSI, and blockchain into a federated framework for traceable and privacy-respecting CTI exchange.
In revising
Section 4, we moved beyond descriptive reporting and incorporated explicit critical evaluation of the reviewed works. For example, while FedAvg remains widely adopted due to its simplicity and low computational cost, several studies highlight its vulnerability under highly non-IID conditions and susceptibility to poisoning attacks [
29,
44]. By contrast, robust aggregation methods such as Krum and Multi-Krum demonstrate greater resilience to adversarial clients, but at the expense of significantly higher computational overhead and slower convergence [
27,
34]. Similarly, hierarchical FL deployments have been shown to improve scalability and privacy in large IIoT environments, yet they introduce additional latency and coordination complexity [
21,
45]. These trade-offs underscore that no single approach dominates across all dimensions; instead, aggregation and deployment strategies must be carefully matched to the operational constraints and threat models of specific CTI use cases. By foregrounding such contradictions and limitations, the discussion provides a more balanced synthesis of the state of knowledge in FL-based CTI for IIoT.
5. Future Research Directions
Future research in federated learning (FL) for cybersecurity and cyber threat intelligence (CTI) in Industrial Internet of Things (IIoT) environments must address systemic limitations, contextual deployment constraints, and evolving adversarial threats. The following directions build upon empirical insights, including the aggregation strategy trade-offs identified in
Section 3, and highlight key opportunities for both researchers and industry practitioners.
5.1. FL-Based Cybersecurity in IIoT
As IIoT deployments often include legacy systems with limited computational capabilities, future work should focus on lightweight and energy-efficient FL designs. Cryptographic techniques such as elliptic-curve cryptography and lightweight homomorphic encryption must be adapted to the constraints of IIoT nodes, enabling secure participation in collaborative training. Edge-aware model compression, quantization, and sparsification will be critical for reducing communication overhead.
Real-time adaptation is another pressing need. FL frameworks must evolve toward self-learning and context-aware updates that respond dynamically to fast-changing threat landscapes, including device compromise, firmware changes, or network shifts. This may require hybrid architectures that combine FL with edge intelligence, stream reasoning, or reinforcement learning.
Empirical analysis in this paper shows that aggregation strategy selection significantly impacts system robustness, especially under non-IID data and adversarial influence. Future research should develop adaptive aggregation mechanisms that can switch between methods (e.g., FedAvg, ClippedAvg, Krum) based on threat level, device profile, or network health.
Standardization of communication protocols and model exchange formats remains a barrier to interoperability across heterogeneous IIoT environments. Collaborative efforts are needed to align FL training processes with industrial protocols (e.g., OPC UA, MQTT) and to develop domain-specific FL APIs.
Finally, quantum-resilient FL is emerging as a long-term priority. Integrating quantum key distribution, post-quantum cryptography, and verifiable federated learning protocols can future-proof FL deployments against cryptographic degradation.
5.2. FL-Based CTI in IIoT
To support real-time threat intelligence, FL-based CTI systems must become scalable, interoperable, and semantically enriched. Existing CTI standards such as STIX and TAXII must be extended or wrapped in lightweight, federated APIs suitable for constrained IIoT environments. Cross-platform implementations that enable real-time sharing of structured threat indicators between IIoT nodes and enterprise systems are urgently needed.
As shown in
Section 4, FL-based CTI systems vary in their sensitivity to aggregation choices, data imbalance, and adversarial clients. Future research should develop intelligent orchestration layers that dynamically assign clients to aggregation groups (e.g., as seen in [
48]) based on behavior similarity or trust metrics. These grouping strategies can improve convergence and accuracy under non-IID conditions.
Benchmarking is also critical. Publicly available FL-CTI datasets for IIoT remain scarce. New benchmarks should include multi-source threat logs, communication traces, and enriched annotations to facilitate evaluation of detection accuracy, model resilience, privacy preservation, and scalability.
Semantic enrichment tools—including text mining, NLP, named-entity recognition, and diachronic linguistics—can enhance CTI extraction from unstructured data. The adoption of ontologies, particularly OWL-based models, can support reasoning across device types, threat vectors, and anomaly signatures. This also enables cross-system semantic interoperability.
At the organizational level, governance models must align CTI sharing with privacy and accountability mandates. Zero-trust principles, secure multiparty computation (SMPC), and blockchain integration can support trustworthy participation across entities. Multilevel governance frameworks—from local operators to national CERTs—can help operationalize FL-based CTI and provide adaptive responses to threats across jurisdictions.
Lastly, future research must focus on optimizing FL for large-scale CTI environments. Efficient filtering, threat prioritization, and contextual alert scoring can reduce analyst burden while maintaining detection accuracy. Combining FL with federated analytics, explainable AI (XAI), and secure auditability will be essential for fostering adoption in safety-critical industrial ecosystems.
5.3. Security Risks and Defenses in FL-CTI
While federated learning provides privacy-preserving collaboration, FL-CTI systems remain vulnerable to a spectrum of adversarial risks that can compromise trustworthiness and scalability in IIoT environments. We categorize these threats into three major classes and summarize corresponding defense strategies.
1. Poisoning Attacks. Malicious clients may inject poisoned gradients or manipulated local updates to degrade the performance of the global model or introduce targeted misclassifications. Empirical studies show that FL methods such as FedAvg are highly vulnerable under non-IID distributions [
37,
44]. Defenses include robust aggregation algorithms (e.g., Krum, Multi-Krum, ClippedAvg) [
27,
34], anomaly detection on client updates, and secure multi-party computation to filter malicious contributions.
2. Backdoor Attacks. Adversaries may implant hidden triggers in local updates, enabling specific malicious behaviors in the global model without significantly affecting aggregate accuracy. Such attacks have been demonstrated in FL-based IDS and malware detection [
29,
52]. Countermeasures include gradient clipping, differential privacy [
22], model inspection, and defense-aware training that selectively removes suspicious update patterns.
3. Adaptive Adversaries. Attackers capable of dynamically adjusting strategies (e.g., combining data poisoning with inference or evasion tactics) pose a significant challenge in IIoT contexts where data are non-IID and devices are resource-constrained. Mitigation requires adaptive aggregation methods, ensemble defenses, blockchain-enabled trust management [
20,
21], and continuous monitoring of aggregation dynamics. We categorize these threats into three major classes and summarize corresponding defense strategies, as shown in
Table 9.
By systematizing adversarial risks and linking them to concrete defenses, FL-CTI research can move beyond acknowledging threats to providing reproducible, evidence-based strategies. This structured synthesis addresses gaps in prior surveys, where adversarial issues were often only briefly noted.
5.4. Prioritized Research Roadmap
To provide clearer prioritization and actionable guidance, we restructure the research roadmap into short-term, medium-term, and long-term challenges for FL-CTI in IIoT:
Short-Term (1–2 years).
Development of lightweight FL models and efficient aggregation methods that can operate under strict IIoT resource constraints [
29,
44].
Creation and open sharing of standardized benchmark datasets (e.g., CTI-relevant subsets of CICIDS2017, Bot-IoT, IoT-23) to improve reproducibility and comparability [
36,
52].
Deployment of privacy-preserving FL prototypes in industrial testbeds (smart grids, smart manufacturing) to demonstrate near-term feasibility [
46,
47].
Medium-Term (3–5 years).
Adaptive aggregation strategies that dynamically adjust to adversarial conditions, non-IID distributions, and client heterogeneity [
27,
34].
Integration of CTI standards (e.g., STIX, TAXII, OpenIOC) with FL pipelines to ensure semantic interoperability across organizations [
20,
21].
Establishment of governance frameworks and regulatory guidelines for cross-organizational FL-CTI deployments, addressing trust, liability, and compliance [
22].
Long-Term (5+ years).
Exploration of post-quantum cryptography and quantum-resilient FL frameworks to safeguard CTI sharing in next-generation IIoT systems [
28].
Fully decentralized CTI exchange models leveraging blockchain and swarm learning to eliminate single points of failure while preserving scalability [
45,
60].
Development of self-healing, autonomous FL-CTI systems capable of real-time defense against adaptive adversaries through continual learning [
37].
This structured roadmap ensures that near-term research addresses immediate practical gaps (lightweight models, benchmarks, testbeds), while medium-term efforts focus on interoperability and resilience, and long-term priorities target quantum-era security and fully autonomous FL-CTI ecosystems.
6. Conclusions
This survey provided a comprehensive examination of how federated learning (FL) can enhance cyber threat intelligence (CTI) across Industrial Internet of Things (IIoT) environments. By analyzing a wide range of threat detection methods, privacy-preserving architectures, and FL-based CTI applications, the study underscores the transformative potential of FL in enabling decentralized, secure, and scalable threat intelligence.
A key contribution of this work is the integration of an empirical synthesis that evaluates leading FL aggregation strategies under IIoT-specific constraints. This analysis offers practical insights into the trade-offs between accuracy, robustness, convergence speed, and computational cost—guiding system designers in selecting appropriate techniques based on deployment requirements. The taxonomy of real-world use cases and the detailed discussion of CTI integration further establish this work as a foundational reference for future research.
The future directions outlined in this survey highlight the need for adaptive, trustworthy, and interoperable FL frameworks that can operate under diverse IIoT conditions. As IIoT networks continue to grow in complexity and scale, developing FL-based CTI systems that are resilient to non-IID data, adversarial threats, and real-time constraints will be essential.
Ultimately, this work lays the groundwork for advancing FL-driven CTI research and supports the design of next-generation security solutions that align with the privacy, scalability, and trust requirements of emerging industrial ecosystems.