A Bibliometric Analysis and Visualization of In-Vehicle Communication Protocols
Abstract
1. Introduction
- To identify the most influential publications, authors, and journals in the domain of in-vehicle communication protocols, including CAN, LIN, FlexRay, MOST, and Automotive Ethernet.
- To map and analyze co-authorship, institutional collaborations, and country-level contributions within the field.
- To uncover key thematic areas, keyword trends, and emerging research directions using co-occurrence and co-citation analysis.
- To explore the integration of modern technologies such as AI and cybersecurity into vehicular networks based on publication trends and citation metrics.
2. Materials and Methods
2.1. Search Strategy and Scope
2.2. Inclusion and Exclusion Criteria
2.3. Sources of Information
2.4. Study Design
- Clustering layout: LinLog modularity-based layout to enhance the visibility of thematic clusters.
- Minimum threshold for inclusion: At least 10 occurrences for keywords and 10 citations for co-cited references to focus on the most significant patterns while reducing noise from sparsely cited items.
- Counting method:
- ○
- Full counting was used for co-authorship networks to give equal weight to all contributors.
- ○
- Fractional counting was applied to co-citation analysis to normalize influence across highly connected items.
3. Results
3.1. Current Status of In-Vehicle Communication Protocol
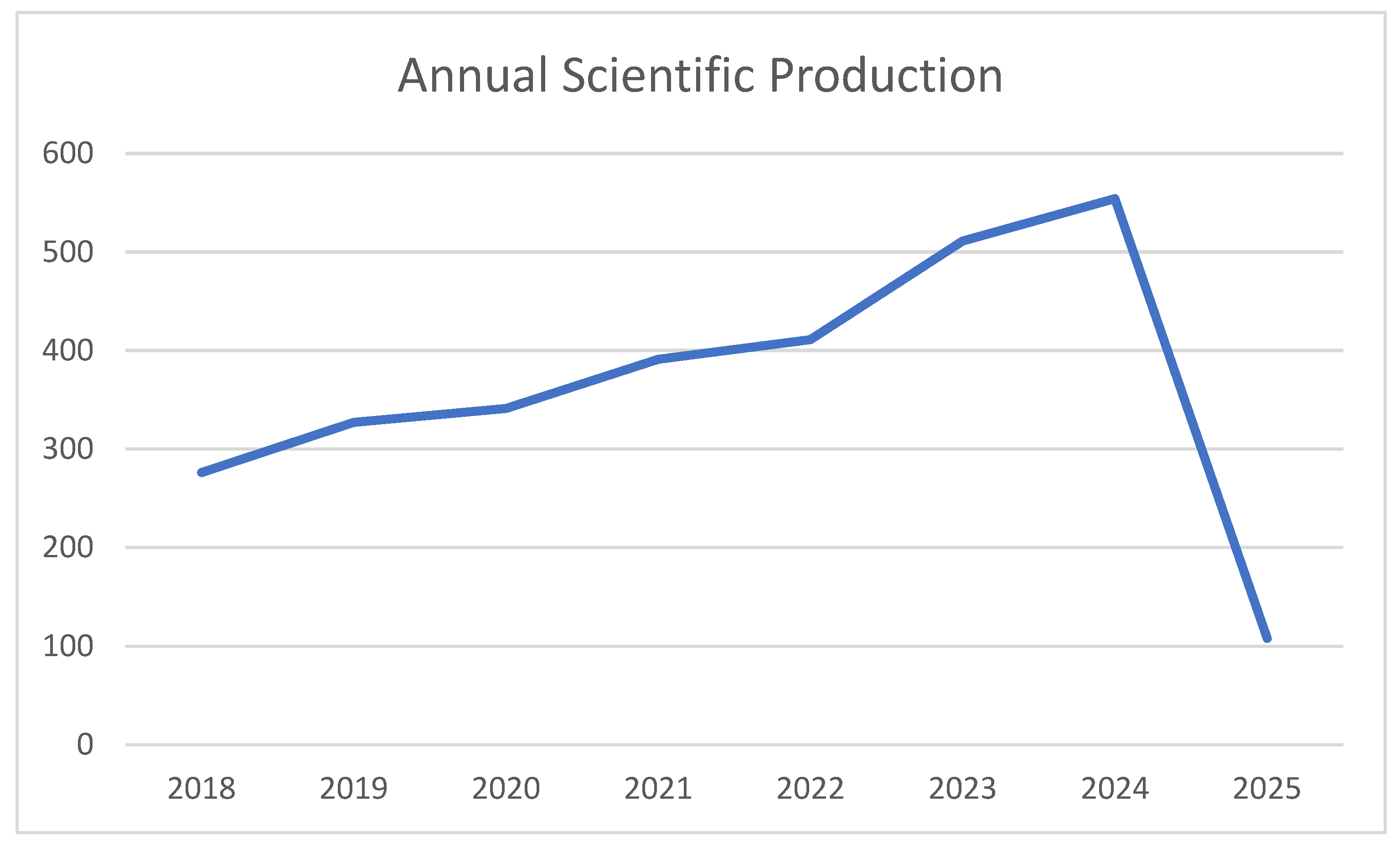
3.1.1. Annual Trends in Publication
3.1.2. Distribution of Organisations
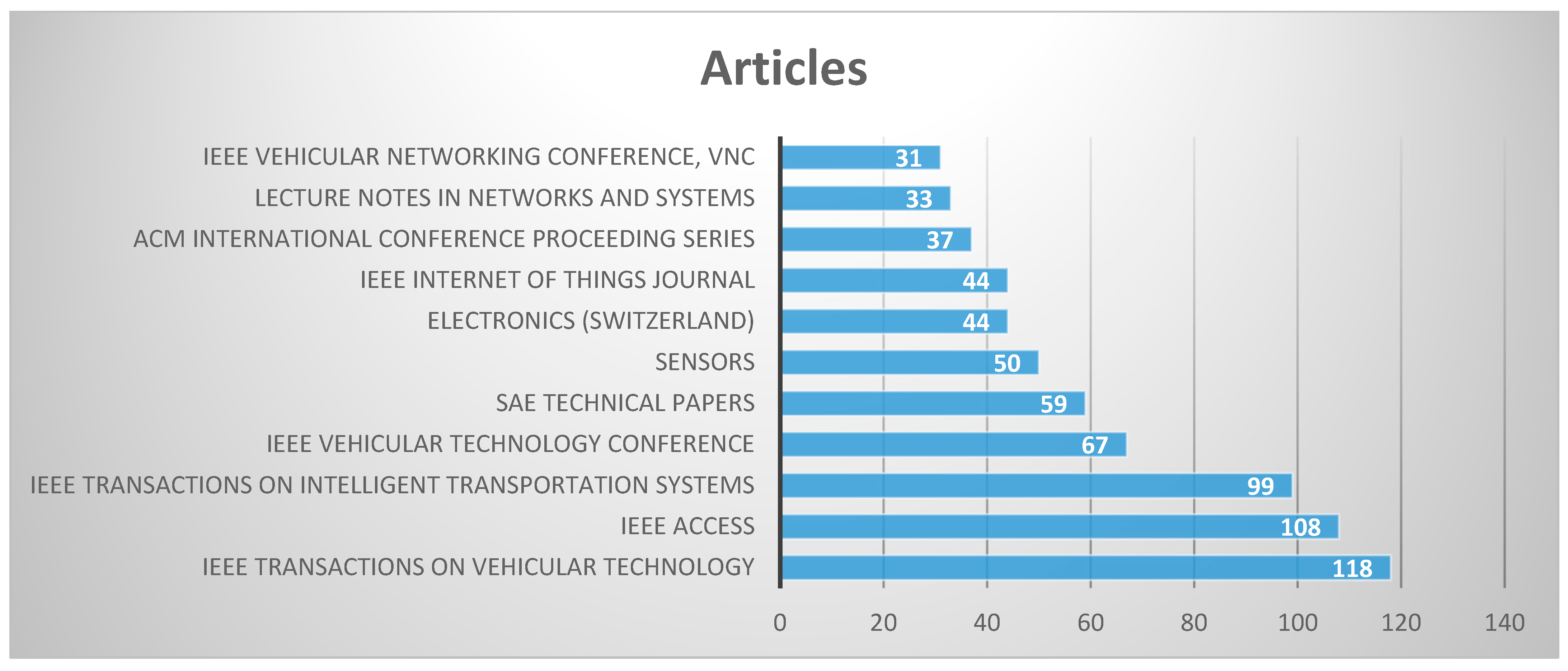
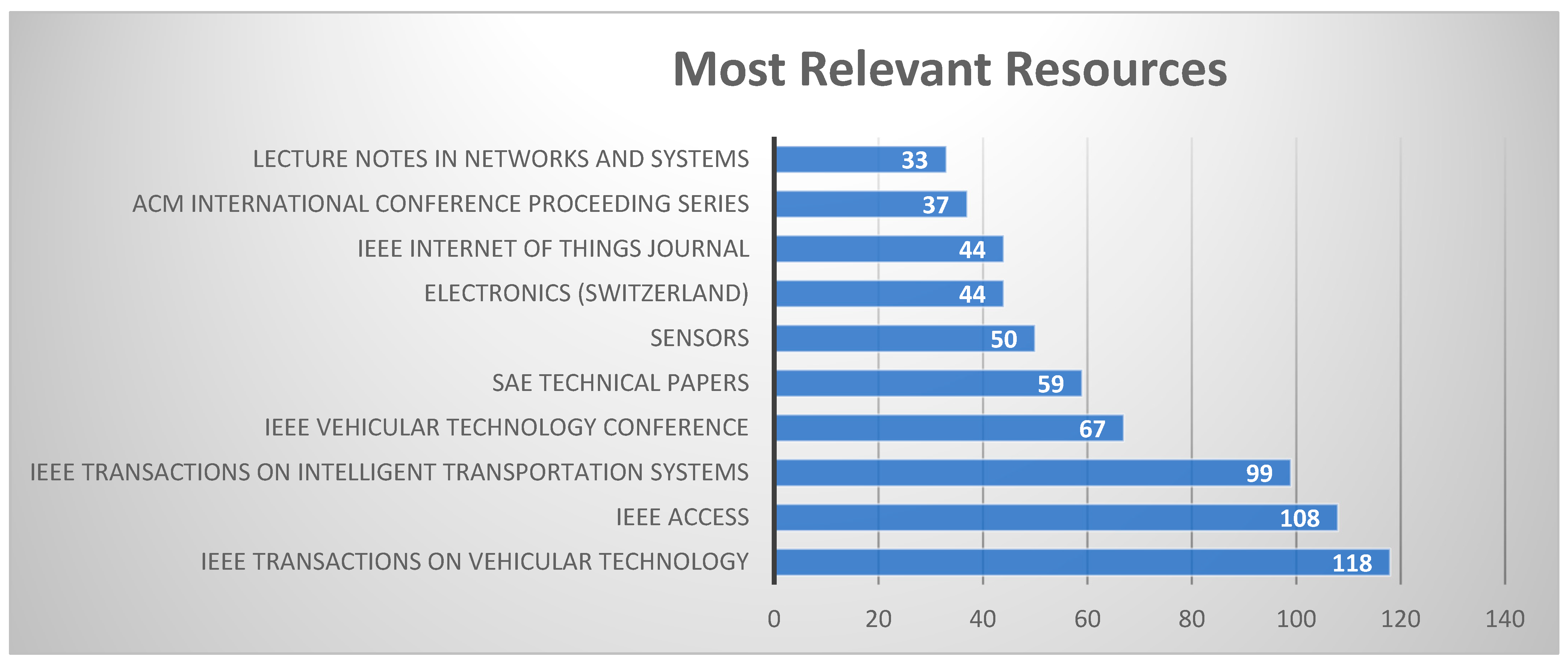
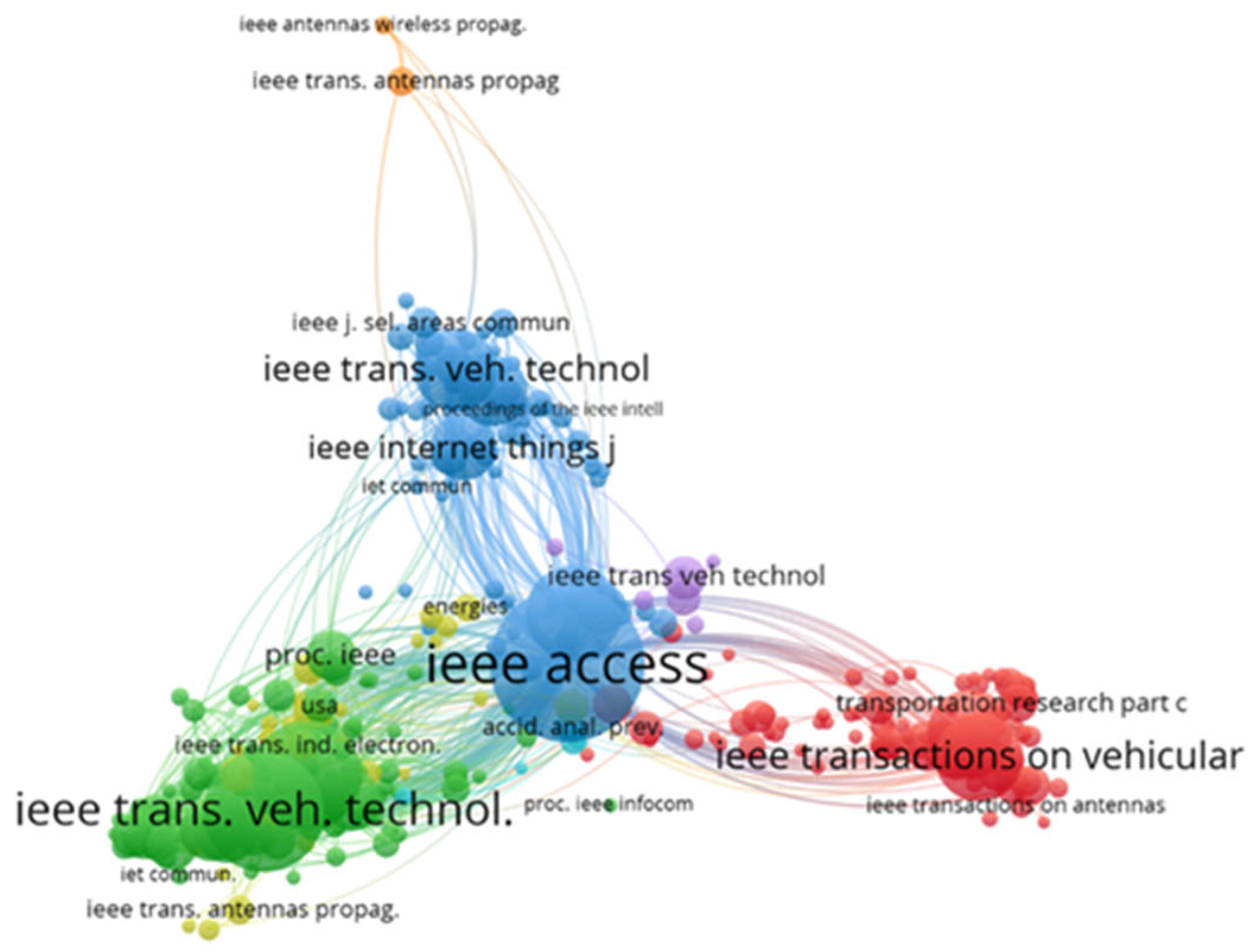
3.1.3. Distribution of Published Journals
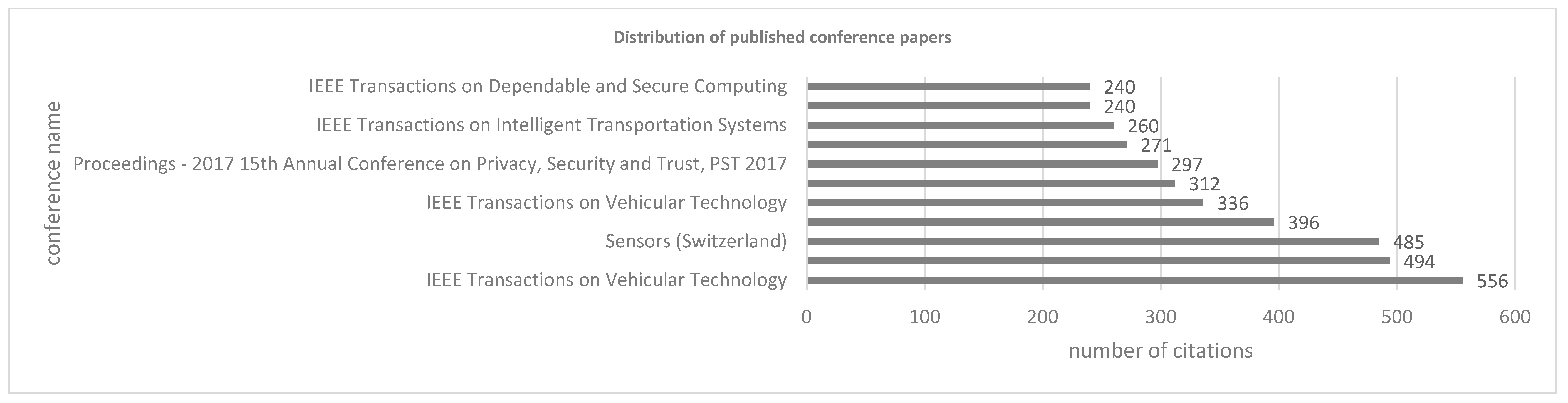
3.1.4. Distribution of Published Conference Papers
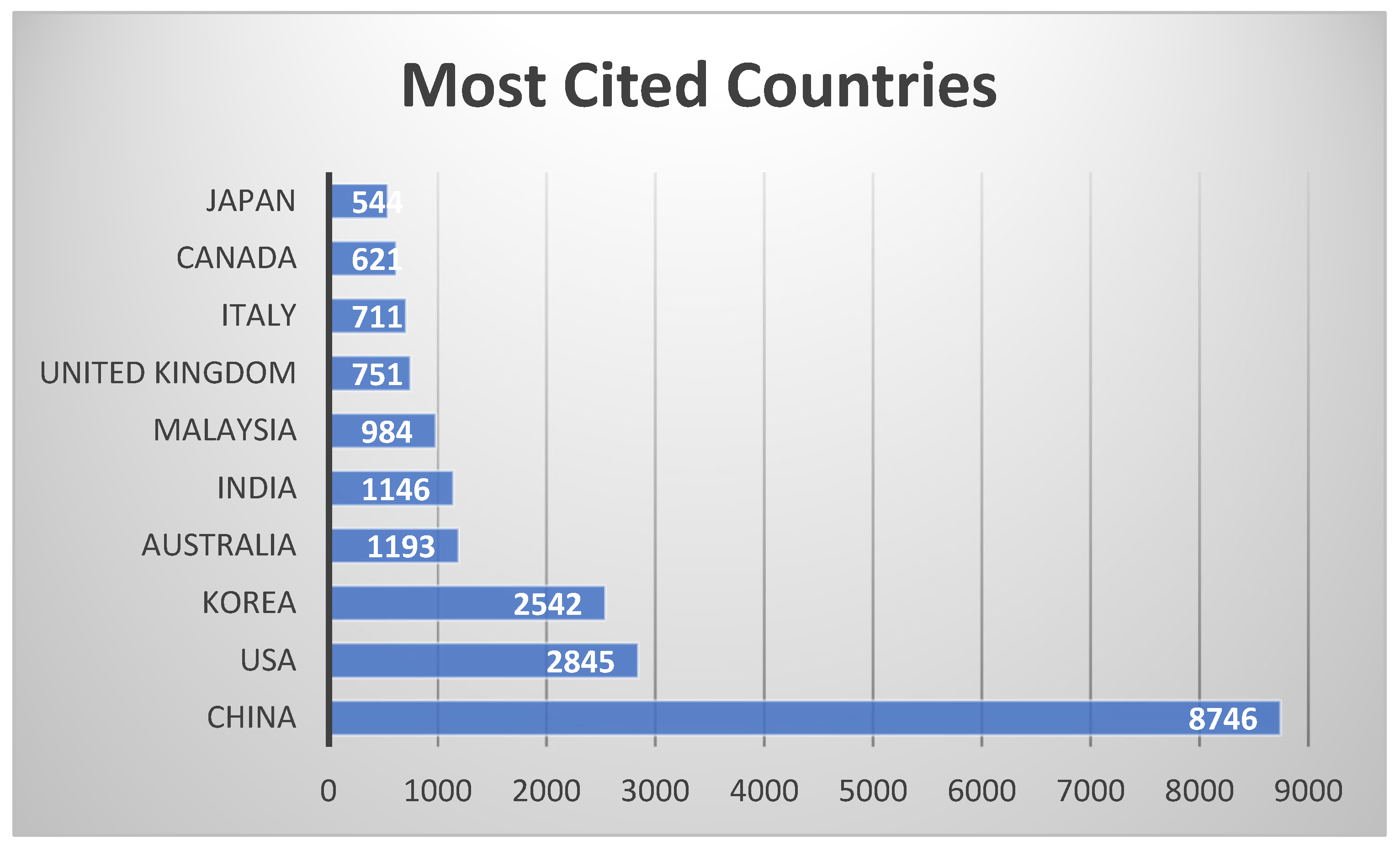
3.1.5. Most Cited Countries
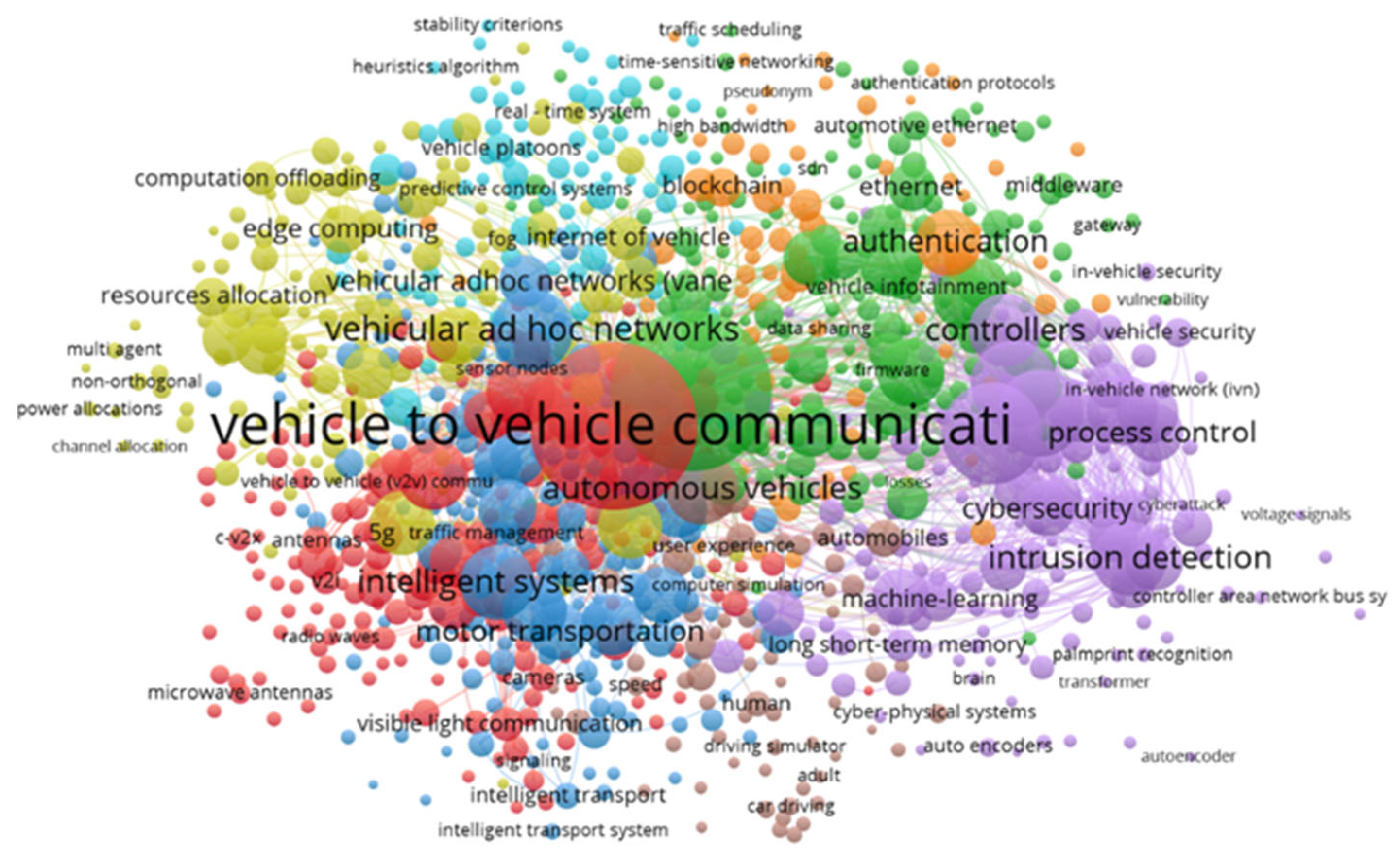
3.2. Keyword Analysis of Research Hotspots
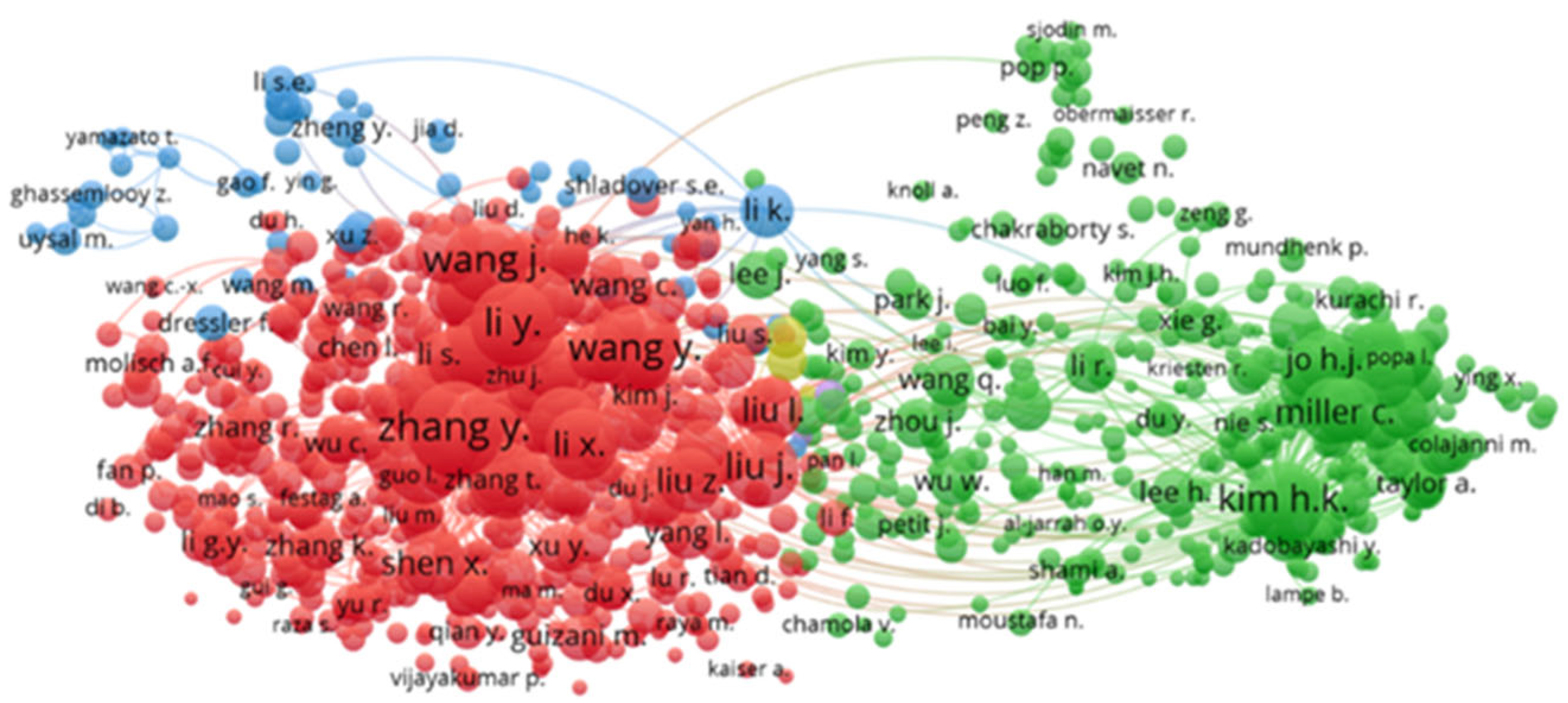
3.3. Co-Authorship Analysis
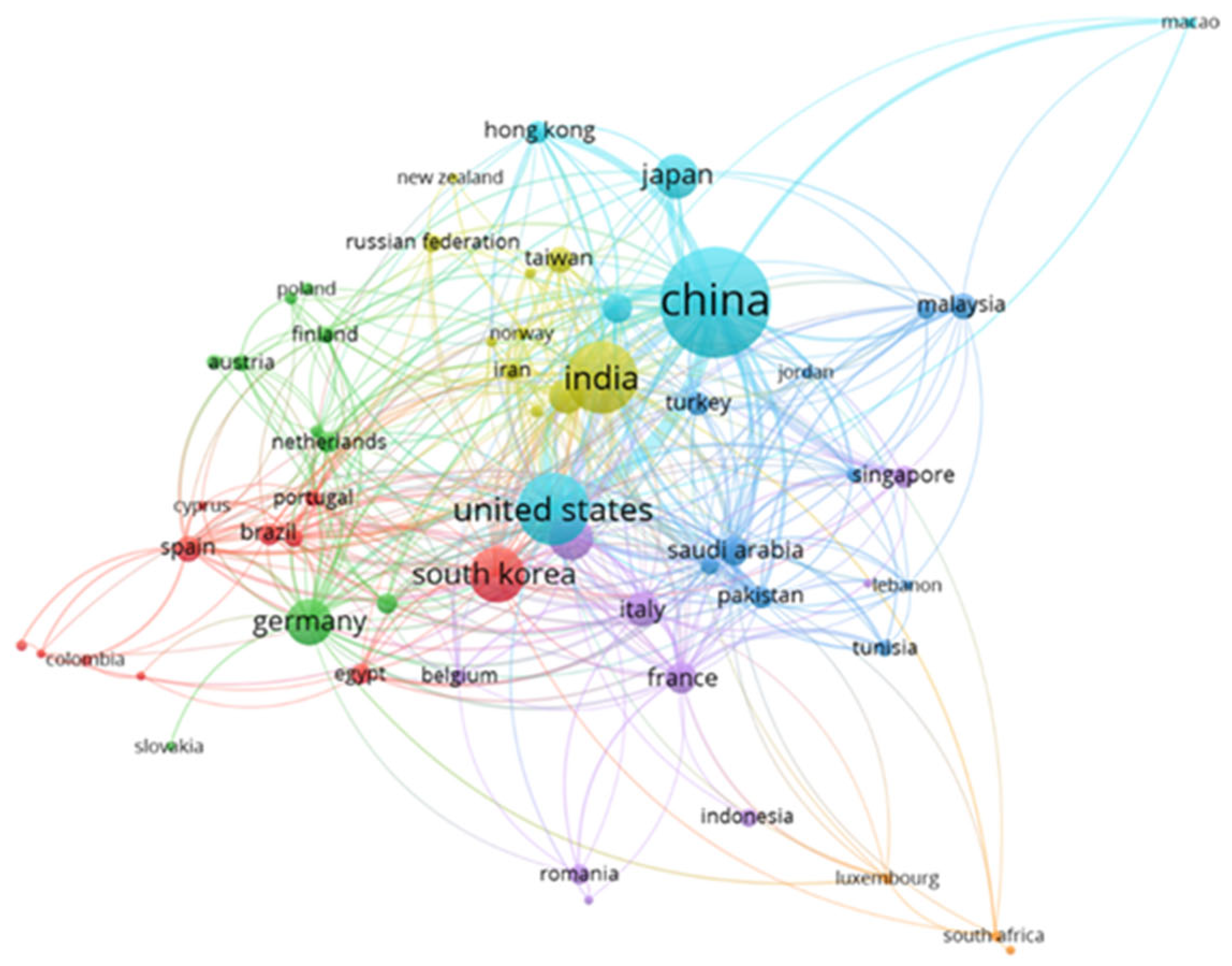
3.3.1. Country Co-Authorship Network
3.3.2. Highly Cited Publications
| Article Name | Journal/Conference Name | Author | Year | Number of Citations |
|---|---|---|---|---|
| IEEE 802.11ad-Based Radar: An Approach to Joint Vehicular Communication-Radar System | IEEE Transactions on Vehicular Technology | [26] | 2018 | 556 |
| Deep Reinforcement Learning for Offloading and Resource Allocation in Vehicle Edge Computing and Networks | IEEE Transactions on Vehicular Technology | [19] | 2019 | 494 |
| Sensor technologies for intelligent transportation systems | Sensors (Switzerland) | [27] | 2018 | 485 |
| GIDS: GAN-based Intrusion Detection System for In-Vehicle Network | 2018 16th Annual Conference on Privacy, Security and Trust, PST 2018 | [24] | 2018 | 396 |
| Mobility-aware edge caching and computing in-vehicle networks: A deep reinforcement learning | IEEE Transactions on Vehicular Technology | [23] | 2018 | 336 |
| Challenges and Solutions for Cellular-Based V2X Communications | IEEE Communications Surveys and Tutorials | [28] | 2020 | 312 |
| VoltageIDS: Low-level communication characteristics for an automotive intrusion detection system | IEEE Transactions on Information Forensics and Security | [25] | 2018 | 271 |
| A survey of intrusion detection for in-vehicle networks | IEEE Transactions on Intelligent Transportation Systems | [29] | 2019 | 260 |
| Cybersecurity challenges in vehicular communications | Vehicular Communications | [9] | 2020 | 240 |
| PA-CRT: Chinese Remainder Theorem-Based Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks | IEEE Transactions on Dependable and Secure Computing | [30] | 2019 | 240 |
3.4. Co-Citation Analysis
3.4.1. Reference Co-Citations Analysis
3.4.2. Journal Co-Citation Cited Analysis
4. Discussion
5. Conclusions
Limitations and Future Research Directions
- Incorporate alternative impact metrics, such as altmetrics, emerging author indices, and social media or preprint citation signals, which offer complementary perspectives on scholarly influence.
- Apply temporal citation normalization or field-weighted metrics to better highlight recent and impactful publications across disciplines.
- Use content-based approaches—such as full-text analysis, keyword embedding, and topic modeling—to uncover latent themes and early-stage research clusters beyond citation frequency.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Prerana, S.; Reddy, N.N.; Varghese, S.G.; Sabhahit, J.N. Review on Communication Technologies used in Electric Vehicles. In Proceedings of the 2024 IEEE International Conference on Distributed Computing, VLSI, Electrical Circuits and Robotics (DISCOVER), Mangalore, India, 18–19 October 2024; pp. 445–451. [Google Scholar] [CrossRef]
- Aliwa, E.; Rana, O.; Perera, C.; Burnap, P. Cyberattacks and Countermeasures for In-Vehicle Networks. ACM Comput. Surv. 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Ma, B.; Yang, S.; Zuo, Z.; Zou, B.; Cao, Y.; Yan, X.; Zhou, S.; Li, J. An authentication and secure communication scheme for in-vehicle networks based on SOME/IP. Sensors 2022, 22, 647. [Google Scholar] [CrossRef] [PubMed]
- Ali, I.; Chen, Y.; Ullah, N.; Kumar, R.; He, W. An Efficient and Provably Secure ECC-Based Conditional Privacy-Preserving Authentication for Vehicle-to-Vehicle Communication in VANETs. IEEE Trans. Veh. Technol. 2021, 70, 1278–1291. [Google Scholar] [CrossRef]
- Lo Bello, L.; Patti, G.; Leonardi, L. A Perspective on Ethernet in Automotive Communications—Current Status and Future Trends. Appl. Sci. 2023, 13, 1278. [Google Scholar] [CrossRef]
- Xu, L.; Zhou, X.; Khan, M.A.; Li, X.; Menon, V.G.; Yu, X. Communication Quality Prediction for Internet of Vehicle (IoV) Networks: An Elman Approach. IEEE Trans. Intell. Transp. Syst. 2022, 23, 19644–19654. [Google Scholar] [CrossRef]
- Fang, Y.; Min, H.; Wu, X.; Wang, W.; Zhao, X.; Mao, G. On-Ramp Merging Strategies of Connected and Automated Vehicles Considering Communication Delay. IEEE Trans. Intell. Transp. Syst. 2022, 23, 15298–15312. [Google Scholar] [CrossRef]
- Dibaei, M.; Zheng, X.; Xia, Y.; Xu, X.; Jolfaei, A.; Bashir, A.K. Investigating the Prospect of Leveraging Blockchain and Machine Learning to Secure Vehicular Networks: A Survey. IEEE Trans. Intell. Transp. Syst. 2022, 23, 683–700. [Google Scholar] [CrossRef]
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity challenges in vehicular communications. Veh. Commun. 2020, 23, 100214. [Google Scholar] [CrossRef]
- Pranckutė, R. Web of Science (WoS) and Scopus: The Titans of Bibliographic Information in Today’s Academic World. Publications 2021, 9, 12. [Google Scholar] [CrossRef]
- Farooq, R. Knowledge management and performance: A bibliometric analysis based on Scopus and WOS data (1988–2021). J. Knowl. Manag. 2022, 27, 1948–1991. [Google Scholar] [CrossRef]
- Ashjaei, M.; Lo Bello, L.; Daneshtalab, M.; Patti, G.; Saponara, S.; Mubeen, S. Time-Sensitive Networking in automotive embedded systems: State of the art and research opportunities. J. Syst. Archit. 2021, 117, 102137. [Google Scholar] [CrossRef]
- Zanbouri, K.; Noor-A-Rahim, M.; John, J.; Sreenan, C.J.; Poor, H.V.; Pesch, D. A Comprehensive Survey of Wireless Time-Sensitive Networking (TSN): Architecture, Technologies, Applications, and Open Issues. IEEE Commun. Surv. Tutor. 2024. Available online: https://ieeexplore.ieee.org/document/10735349 (accessed on 15 June 2025).
- Kwon, J.-H.; Kim, H.-J.; Lee, S. Optimizing Traffic Scheduling in Autonomous Vehicle Networks Using Machine Learning Techniques and Time-Sensitive Networking. Electronics 2024, 13, 2837. [Google Scholar] [CrossRef]
- Luo, F.; Ren, Y.; Yu, Y.; Li, Y.; Wang, Z. A Centralized Discovery-Based Method for Integrating Data Distribution Service and Time-Sensitive Networking in In-Vehicle Networks. arXiv 2024. [Google Scholar] [CrossRef]
- Alanazi, F. Development of Smart Mobility Infrastructure in Saudi Arabia: A Benchmarking Approach. Sustainability 2023, 15, 3158. [Google Scholar] [CrossRef]
- Donthu, N.; Kumar, S.; Mukherjee, D.; Pandey, N.; Lim, W.C. How to conduct a bibliometric analysis: An overview and guidelines. J. Bus. Res. 2021, 133, 285–296. [Google Scholar] [CrossRef]
- Muslam, M.M.A. Enhancing Security in Vehicle-to-Vehicle Communication: A Comprehensive Review of Protocols and Techniques. Vehicles 2024, 6, 450–467. [Google Scholar] [CrossRef]
- Liu, Y.; Yu, H.; Xie, S.; Zhang, Y. Deep Reinforcement Learning for Offloading and Resource Allocation in Vehicle Edge Computing and Networks. IEEE Trans. Veh. Technol. 2019, 68, 11158–11168. [Google Scholar] [CrossRef]
- Ullah, M.; Shahid, A.; Din, I.U.; Roman, M.; Assam, M.; Fayaz, M.; Ghadi, Y.; Aljuaid, H. Analyzing Interdisciplinary Research Using Co-Authorship Networks. Complexity 2022, 2022, 2524491. [Google Scholar] [CrossRef]
- Ji, P.; Jin, J.; Ke, Z.T.; Li, W. Co-citation and Co-authorship Networks of Statisticians. J. Bus. Econ. Stat. 2022, 40, 469–485. [Google Scholar] [CrossRef]
- Chen, S.; Song, Y.; Shu, F.; Larivière, V. Interdisciplinarity and impact: The effects of the citation time window. Scientometrics 2022, 127, 2621–2642. [Google Scholar] [CrossRef]
- Tan, L.T.; Hu, R.Q. Mobility-Aware Edge Caching and Computing in Vehicle Networks: A Deep Reinforcement Learning. IEEE Trans. Veh. Technol. 2018, 67, 10190–10203. [Google Scholar] [CrossRef]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN based Intrusion Detection System for In-Vehicle Network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Choi, W.; Joo, K.; Jo, H.J.; Park, M.C.; Lee, D.H. VoltageIDS: Low-Level Communication Characteristics for Automotive Intrusion Detection System. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2114–2129. [Google Scholar] [CrossRef]
- Kumari, P.; Choi, J.; González-Prelcic, N.; Heath, R.W. IEEE 802.11ad-Based Radar: An Approach to Joint Vehicular Communication-Radar System. IEEE Trans. Veh. Technol. 2018, 67, 3012–3027. [Google Scholar] [CrossRef]
- Guerrero-Ibáñez, J.; Zeadally, S.; Contreras-Castillo, J. Sensor Technologies for Intelligent Transportation Systems. Sensors 2018, 18, 1212. [Google Scholar] [CrossRef] [PubMed]
- Gyawali, S.; Xu, S.; Qian, Y.; Hu, R.Q. Challenges and Solutions for Cellular Based V2X Communications. IEEE Commun. Surv. Tutorials 2021, 23, 222–255. [Google Scholar] [CrossRef]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A Survey of Intrusion Detection for In-Vehicle Networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese Remainder Theorem Based Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks. IEEE Trans. Dependable Secur. Comput. 2021, 18, 722–735. [Google Scholar] [CrossRef]
- Bernatović, I.; Slavec Gomezel, A.; Černe, M. Mapping the knowledge-hiding field and its future prospects: A bibliometric co-citation, co-word, and coupling analysis. Knowl. Manag. Res. Pract. 2022, 20, 394–409. [Google Scholar] [CrossRef]
- Raman, R.; Singh, P.; Singh, V.K.; Vinuesa, R.; Nedungadi, P. Understanding the Bibliometric Patterns of Publications in IEEE Access. IEEE Access 2022, 10, 35561–35577. [Google Scholar] [CrossRef]
- Qasim, H.H.; Abidin, H.Z.; Abdullah, S.A. Handover management in vehicle communication: Applications, techniques, issues, and challenges: A review. Bull. Electr. Eng. Inform. 2024, 13, 3167–3186. [Google Scholar] [CrossRef]
| Type of Document | Frequency | Proportion |
|---|---|---|
| Article | 1324 | 45.36% |
| Book chapter | 86 | 2.95% |
| Conference paper | 1465 | 50.19% |
| Review | 44 | 1.51% |
| Grand Total | 2919 | 100.00% |
| Journal/Conference | Subject | Number of Citations |
|---|---|---|
| IEEE Transactions on Vehicular Technology | Vehicular Technology | 4175 |
| IEEE Access | General Engineering/Technology | 2664 |
| IEEE Transactions on Intelligent Transportation Systems | Intelligent Transportation | 2628 |
| Sensors | Sensor Technology | 1132 |
| Vehicular Communications | Vehicular Communications | 809 |
| IEEE Internet of Things Journal | Internet of Things (IoT) | 679 |
| IEEE Communications Surveys and Tutorials | Communications/Surveys | 474 |
| Study | Focus | Time Range | Methodology | Dataset Size | Novelty Compared to Our Work |
|---|---|---|---|---|---|
| Muslam (2024) [18] | Security in V2V Communication | ~2010–2023 | Qualitative Review | ~150 papers | Narrow focus, no co-citation or network analysis |
| Qasim et al. (2024) [33] | Handover Management in Vehicular Comms | ~2015–2023 | Survey | ~100 papers | Specialized focus, no bibliometric scope |
| This Study | Comprehensive review of in-vehicle protocols | 2018–2025 | Bibliometric: co-citation, co-authorship, keyword clustering | 2919 papers | Broad scope, visual network analysis, emerging trend detection |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hussain, I.; Reis, M.J.C.S.; Serôdio, C.; Branco, F. A Bibliometric Analysis and Visualization of In-Vehicle Communication Protocols. Future Internet 2025, 17, 268. https://doi.org/10.3390/fi17060268
Hussain I, Reis MJCS, Serôdio C, Branco F. A Bibliometric Analysis and Visualization of In-Vehicle Communication Protocols. Future Internet. 2025; 17(6):268. https://doi.org/10.3390/fi17060268
Chicago/Turabian StyleHussain, Iftikhar, Manuel J. C. S. Reis, Carlos Serôdio, and Frederico Branco. 2025. "A Bibliometric Analysis and Visualization of In-Vehicle Communication Protocols" Future Internet 17, no. 6: 268. https://doi.org/10.3390/fi17060268
APA StyleHussain, I., Reis, M. J. C. S., Serôdio, C., & Branco, F. (2025). A Bibliometric Analysis and Visualization of In-Vehicle Communication Protocols. Future Internet, 17(6), 268. https://doi.org/10.3390/fi17060268









