Trajectory Optimization for UAV-Aided IoT Secure Communication Against Multiple Eavesdroppers †
Abstract
1. Introduction
- A secure communication framework for IoT systems is introduced, incorporating UAVs alongside multiple eavesdropping entities. Through the optimization of UAV flight trajectories, we improve the worst-case secrecy rate, thereby augmenting physical layer security in environments with multiple eavesdropping nodes.
- To mitigate the computational complexity of continuous trajectory optimization, we discretize the UAV trajectory into a limited collection of coordinate points and develop an optimization model based on these discrete coordinate variables.
- To address the challenge of maximizing secrecy rates under the worst-case scenario, where the optimization problem is inherently non-convex and non-differentiable, we utilize SCA techniques and hypograph theory. By implementing a novel set of trajectory increment variables to replace the original UAV trajectory coordinates, we reformulate the initial non-convex problem into a set of convex subproblems. Moreover, by utilizing hypograph theory, we equivalently convert the non-differentiable subproblems into standard convex optimization formats, facilitating rapid resolution.
- Simulation results indicate that under varied parameter conditions, the proposed method can efficiently evade multiple eavesdroppers with a low computational complexity while significantly improving the system’s physical layer security (PLS) performance. This validates the substantial impact of UAV trajectory optimization on improving PLS effectiveness.
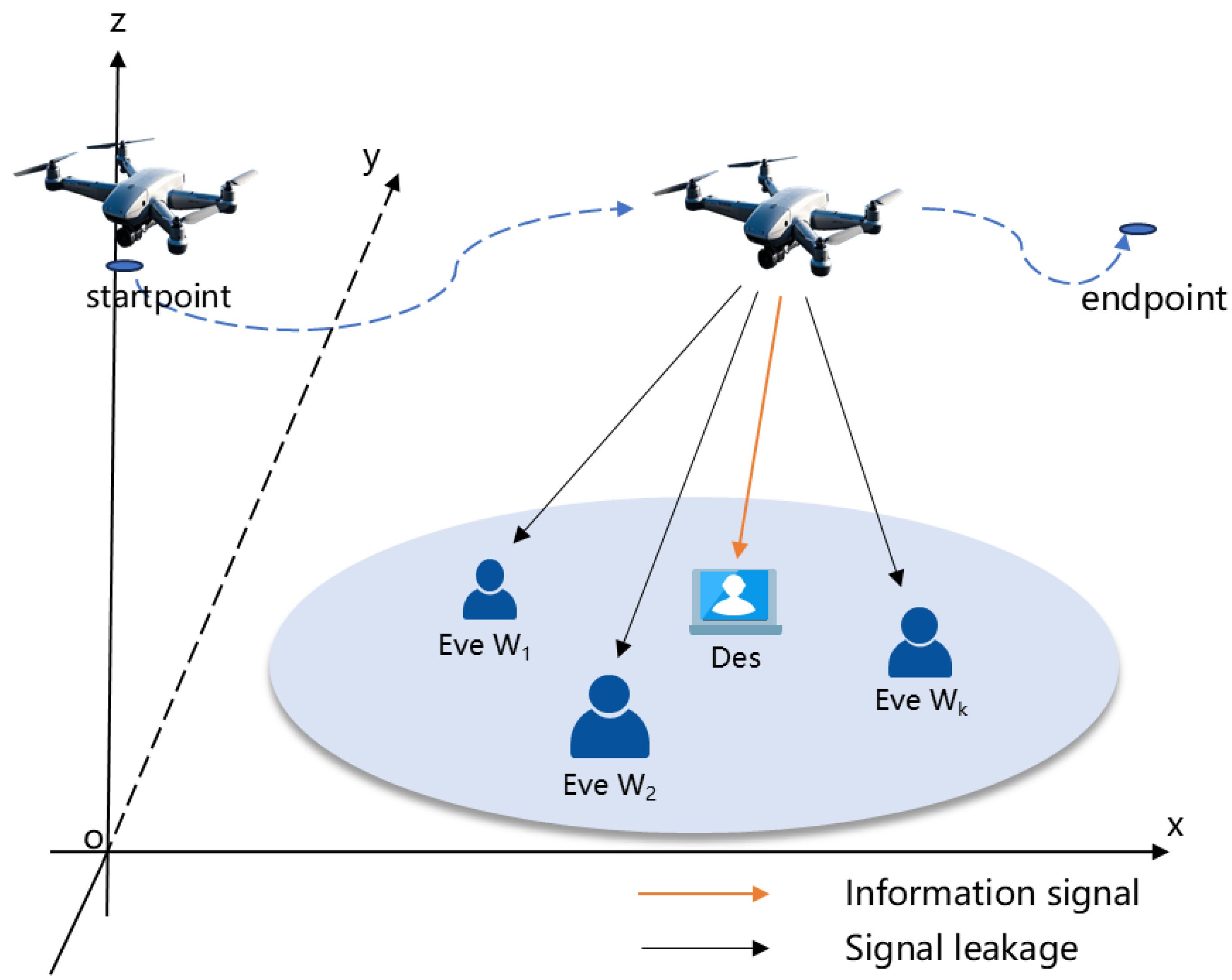
2. System Model and Problem Formulation
2.1. System Model
2.2. Problem Formulation
3. Trajectory Optimization
3.1. Change of Variables
3.2. Hypograph
4. Simulation Results
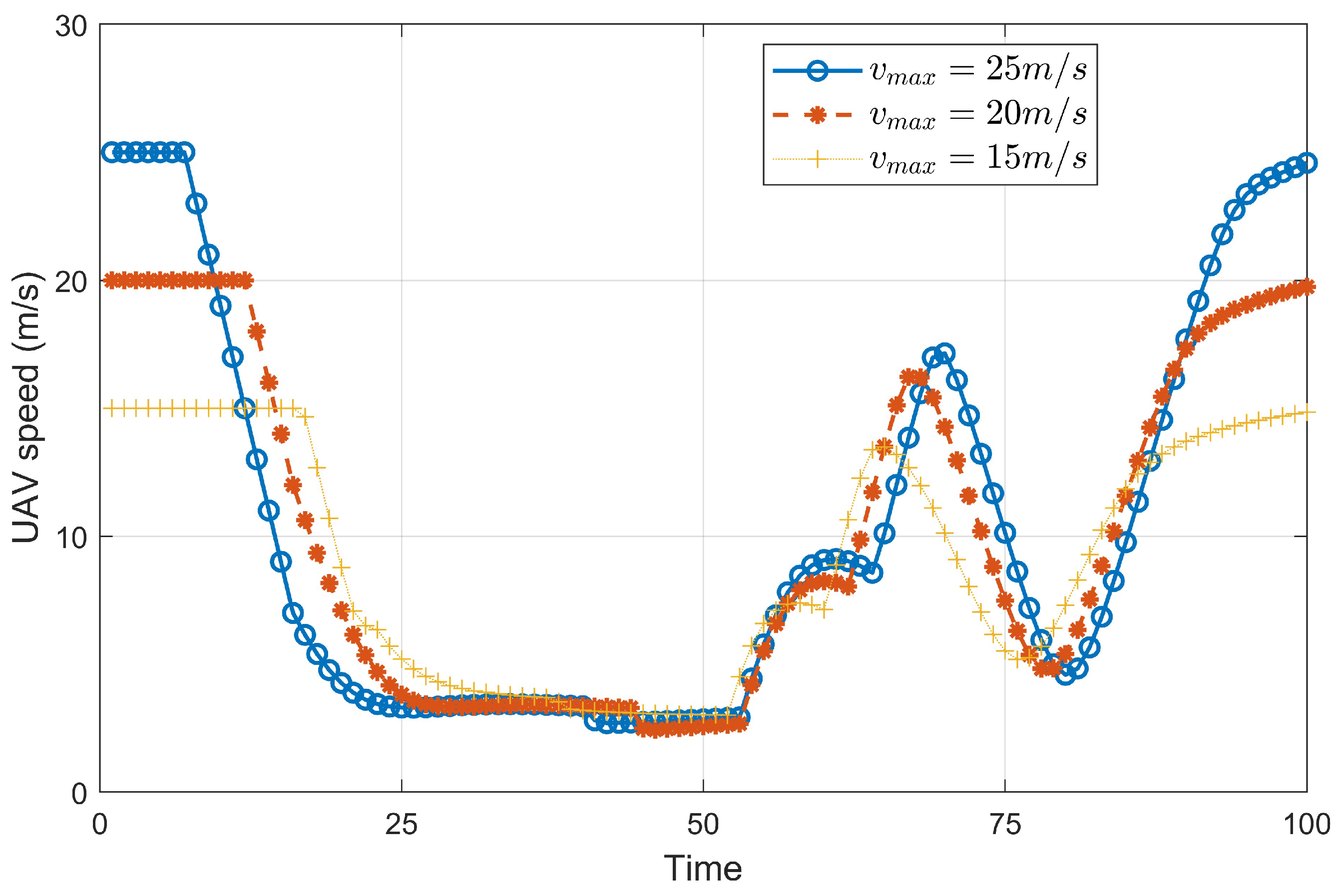
4.1. UAV Trajectories
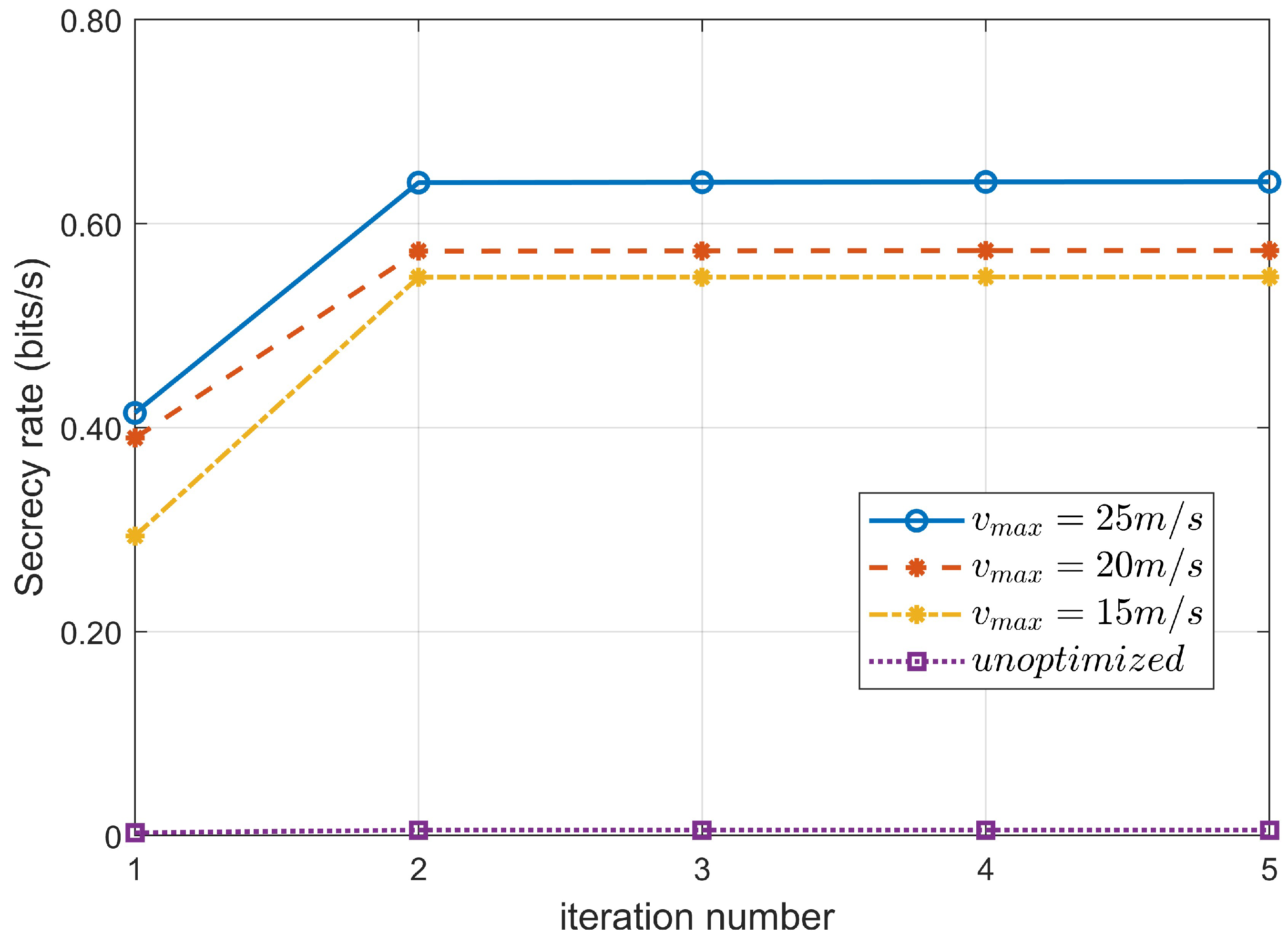
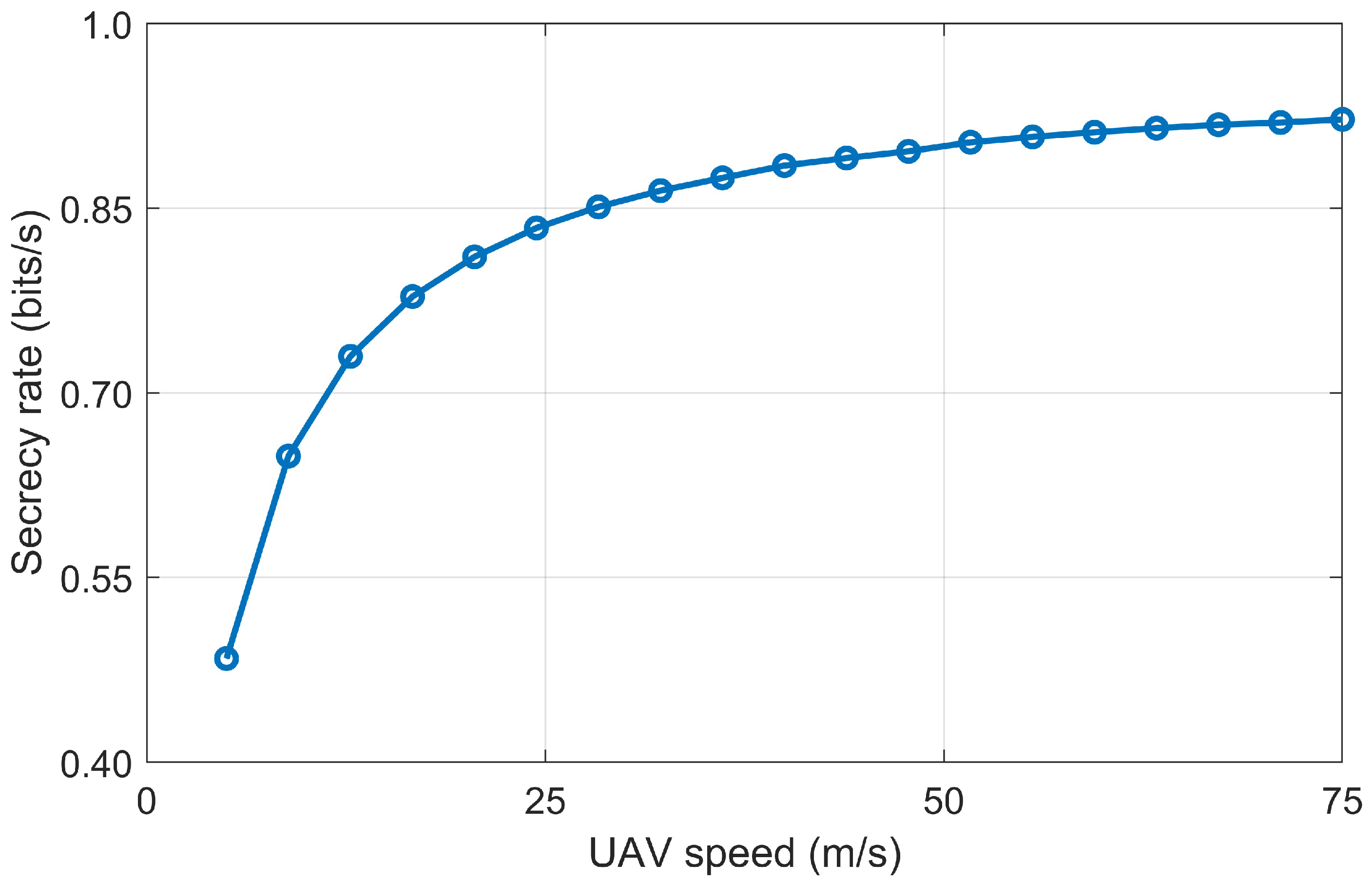
4.2. Secrecy Rate Versus Iteration Number and UAV Speed
5. Conclusions
6. Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| UAV | Unmanned Aerial Vehicle |
| LoS | line-of-sight |
| BS | base stations |
| RIS | reconfigurable intelligent surface |
| CSI | channel state information |
| PLS | physical layer security |
| SCA | successive convex approximation |
References
- Subrahmanyam, V.; Sagar, M.; Balram, G.; Ramana, J.V.; Tejaswi, S.; Mohammad, H.P. An Efficient Reliable Data Communication For Unmanned Air Vehicles (UAV) Enabled Industry Internet of Things (IIoT). In Proceedings of the 2024 3rd International Conference on Artificial Intelligence For Internet of Things (AIIoT), Vellore, India, 3–4 May 2024; pp. 1–4. [Google Scholar]
- Gu, X.; Zhang, G. A Survey on UAV-Assisted Wireless Communications: Recent Advances and Future Trends. Comput. Commun. 2023, 208, 44–78. [Google Scholar] [CrossRef]
- Wen, X.; Ruan, Y.; Li, Y.; Xia, H.; Zhang, R.; Wang, C.; Liu, W.; Jiang, X. Improved Genetic Algorithm Based 3-D Deployment of UAVs. J. Commun. Netw. 2022, 24, 223–231. [Google Scholar] [CrossRef]
- Luo, X.; Xie, J.; Xiong, L.; Wang, Z.; Tian, C. 3-D Deployment of Multiple UAV-Mounted Mobile Base Stations for Full Coverage of IoT Ground Users with Different QoS Requirements. IEEE Commun. Lett. 2022, 26, 3009–3013. [Google Scholar] [CrossRef]
- Safwat, N.E.-D.; Hafez, I.M.; Newagy, F. 3D Placement of a New Tethered UAV to UAV Relay System for Coverage Maximization. Electronics 2022, 11, 385. [Google Scholar] [CrossRef]
- Tran, D.-H.; Chatzinotas, S.; Vu, T.X.; Ottersten, B. UAV Relay-Assisted Emergency Communications in IoT Networks: Resource Allocation and Trajectory Optimization. IEEE Trans. Wirel. Commun. 2022, 21, 1621–1637. [Google Scholar] [CrossRef]
- Yu, J.; Liu, X.; Gao, Y.; Zhang, C.; Zhang, W. Deep Learning for Channel Tracking in IRS-Assisted UAV Communication Systems. IEEE Trans. Wirel. Commun. 2022, 21, 7711–7722. [Google Scholar] [CrossRef]
- Mekdad, Y.; Aris, A.; Babun, L.; Fergougui, A.E.; Conti, M.; Lazzeretti, R.; Uluagac, A.S. A Survey on Security and Privacy Issues of UAVs. Comput. Netw. 2023, 224, 109626. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Alsamhi, S.H.; Barb, G.; Zywiołek, J.; Ullah, I.; Noor, F.; Shah, J.A.; Almuhaideb, A.M. Security and Privacy Issues and Solutions for UAVs in B5G Networks: A Review. IEEE Trans. Netw. Serv. Manag. 2025, 22, 892–912. [Google Scholar] [CrossRef]
- Wang, D.; Cao, Y.; Lam, K.-Y.; Hu, Y.; Kaiwartya, O. Authentication and Key Agreement Based on Three Factors and PUF for UAV-Assisted Post-Disaster Emergency Communication. IEEE Internet Things J. 2024, 11, 20457–20472. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J.; Obaidat, M.S.; Li, X.; Vijayakumar, P. A PUF-based Lightweight Authentication and Key Agreement Protocol for Smart UAV Networks. IET Commun. 2021, 16, 1142–1159. [Google Scholar] [CrossRef]
- Li, T.; Zhang, J.; Obaidat, M.S.; Lin, C.; Lin, Y.; Shen, Y.; Ma, J. Energy-Efficient and Secure Communication Toward UAV Networks. IEEE Internet Things J. 2022, 9, 10061–10076. [Google Scholar] [CrossRef]
- Wang, J.; Jiao, Z.; Chen, J.; Hou, X.; Yang, T.; Lan, D. Blockchain-Aided Secure Access Control for UAV Computing Networks. IEEE Trans. Netw. Sci. Eng. 2024, 11, 5267–5279. [Google Scholar] [CrossRef]
- Illi, E.; Qaraqe, M.; Althunibat, S.; Alhasanat, A.; Alsafasfeh, M.; De Ree, M.; Mantas, G.; Rodriguez, J.; Aman, W.; Al-Kuwari, S. Physical Layer Security for Authentication, Confidentiality, and Malicious Node Detection: A Paradigm Shift in Securing IoT Networks. IEEE Commun. Surv. Tutor. 2024, 26, 347–388. [Google Scholar] [CrossRef]
- Xu, F.; Ahmad, S.; Khan, M.N.; Ahmed, M.; Raza, S.; Khan, F.; Ma, Y.; Khan, W.U. Beyond Encryption: Exploring the Potential of Physical Layer Security in UAV Networks. J. King Saud Univ. Comput. Inf. Sci. 2023, 35, 101717. [Google Scholar] [CrossRef]
- Khan, W.U.; Lagunas, E.; Ali, Z.; Javed, M.A.; Ahmed, M.; Chatzinotas, S.; Ottersten, B.; Popovski, P. Opportunities for Physical Layer Security in UAV Communication Enhanced with Intelligent Reflective Surfaces. IEEE Wirel. Commun. 2022, 29, 22–28. [Google Scholar] [CrossRef]
- Xu, Y.; Xie, H.; Li, D.; Hu, R.Q. Energy-Efficient Beamforming for Heterogeneous Industrial IoT Networks With Phase and Distortion Noises. IEEE Trans. Ind. Informat. 2022, 18, 7423–7434. [Google Scholar] [CrossRef]
- Na, Z.; Ji, C.; Lin, B.; Zhang, N. Joint Optimization of Trajectory and Resource Allocation in Secure UAV Relaying Communications for Internet of Things. IEEE Internet Things J. 2022, 9, 16284–16296. [Google Scholar] [CrossRef]
- Chen, Y.; Liu, G.; Zhang, Z.; He, L.; He, S. Improving Physical Layer Security for Multi-UAV Systems Against Hybrid Wireless Attacks. IEEE Trans. Veh. Technol. 2024, 73, 7034–7048. [Google Scholar] [CrossRef]
- Wang, Z.; Guo, J.; Chen, Z.; Yu, L.; Wang, Y.; Rao, H. Robust Secure UAV Relay-Assisted Cognitive Communications with Resource Allocation and Cooperative Jamming. J. Commun. Netw. 2022, 24, 139–153. [Google Scholar] [CrossRef]
- Liu, Z.; Zhu, B.; Xie, Y.; Ma, K.; Guan, X. UAV-Aided Secure Communication With Imperfect Eavesdropper Location: Robust Design for Jamming Power and Trajectory. IEEE Trans. Veh. Technol. 2024, 73, 7276–7286. [Google Scholar] [CrossRef]
- Lee, J.H.; Park, K.H.; Ko, Y.C.; Alouini, M.-S. Throughput Maximization of Mixed FSO/RF UAV-Aided Mobile Relaying with a Buffer. IEEE Trans. Wirel. Commun. 2021, 20, 683–694. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Tran, M.H.; Tran, X.N. Joint Resource and Trajectory Optimization for Secure UAV-Based Two-Way Relay System. Digital Signal Process. Digit. Signal Process. 2024, 153, 104626. [Google Scholar] [CrossRef]
- Mamaghani, M.T.; Zhou, X.; Yang, N.; Swindlehurst, A.L. Secure Short-Packet Communications via UAV-Enabled Mobile Relaying: Joint Resource Optimization and 3D Trajectory Design. IEEE Trans. Wirel. Commun. 2023, 23, 7802–7815. [Google Scholar] [CrossRef]
- Kang, H.; Chang, X.; Mišic, V.B. Improving Dual-UAV Aided Ground-UAV Bi-Directional Communication Security: Joint UAV Trajectory and Transmit Power Optimization. IEEE Trans. Veh. Technol. 2022, 71, 10570–10583. [Google Scholar] [CrossRef]
- Lei, H.; Meng, D.; Ran, H.; Park, K.H.; Pan, G.; Alouini, M.S. Multi-UAV Trajectory Design for Fair and Secure Communication. IEEE Trans. Cognit. Commun. Netw. 2024. [Google Scholar] [CrossRef]
- DangNgoc, H.; Nguyen, D.N.; HoVan, K.; Hoang, D.T.; Dutkiewicz, E.; Pham, Q.V.; Hwang, W.J. Secure Swarm UAV-Assisted Communications with Cooperative Friendly Jamming. IEEE Internet Things J. 2022, 9, 25596–25611. [Google Scholar] [CrossRef]
- Li, J.; Sun, G.; Kang, H.; Wang, A.; Liang, S.; Liu, Y.; Zhang, Y. Multi-Objective Optimization Approaches for Physical Layer Secure Communications Based on Collaborative Beamforming in UAV Networks. IEEE/ACM Trans. Netw. 2023, 31, 1902–1917. [Google Scholar] [CrossRef]
- Zhang, H.; Shen, L.; Wang, N.; Mu, X. UAV Trajectory Optimization for PHY Secure Communication Against Cooperative Eavesdroppers. In Proceedings of the 2022 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Suzhou, China, 14–16 October 2022; pp. 289–293. [Google Scholar]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shen, L.; Nie, J.; Li, M.; Wang, G.; Zhang, Q.; He, X. Trajectory Optimization for UAV-Aided IoT Secure Communication Against Multiple Eavesdroppers. Future Internet 2025, 17, 225. https://doi.org/10.3390/fi17050225
Shen L, Nie J, Li M, Wang G, Zhang Q, He X. Trajectory Optimization for UAV-Aided IoT Secure Communication Against Multiple Eavesdroppers. Future Internet. 2025; 17(5):225. https://doi.org/10.3390/fi17050225
Chicago/Turabian StyleShen, Lingfeng, Jiangtao Nie, Ming Li, Guanghui Wang, Qiankun Zhang, and Xin He. 2025. "Trajectory Optimization for UAV-Aided IoT Secure Communication Against Multiple Eavesdroppers" Future Internet 17, no. 5: 225. https://doi.org/10.3390/fi17050225
APA StyleShen, L., Nie, J., Li, M., Wang, G., Zhang, Q., & He, X. (2025). Trajectory Optimization for UAV-Aided IoT Secure Communication Against Multiple Eavesdroppers. Future Internet, 17(5), 225. https://doi.org/10.3390/fi17050225





