Abstract
Named Data Networking (NDN) is highly susceptible to Distributed Denial of Service (DDoS) attacks, such as Interest Flooding Attack (IFA) and Cache Pollution Attack (CPA). These attacks exploit the inherent data retrieval and caching mechanisms of NDN, leading to severe disruptions in data availability and network efficiency, thereby undermining the overall performance and reliability of the system. In this paper, an attack detection method based on an improved XGBoost is proposed and applied to the hybrid attack pattern of IFA and CPA. Through experiments, the performance of the new attacks and the efficacy of the detection algorithm are analyzed. In comparison with other algorithms, the proposed method is demonstrated to have advantages in terms of the advanced nature of the proposed classifier, which is confirmed by the AUC-score.
1. Introduction
Named Data Networking (NDN) [1] is a proposed future Internet architecture that significantly optimizes data distribution efficiency by leveraging name-based addressing and in-network caching mechanisms. Its content naming rules allow data packets to be cached directly on routers and forwarded through name prefix matching. This approach not only reduces the overhead of the traditional network Domain Name System (DNS), but also effectively reduces network latency through multicast capabilities and dynamic caching strategies, especially in high-mobility scenarios. In addition, NDN embeds security into the data itself through content object signing and ensures integrity verification through encrypted signatures.
Compared with TCP/IP’s reliance on transport layer encryption (such as TLS/SSL), this model is more in line with future data-driven security needs. However, NDN’s unique architecture also brings new security challenges, namely denial of service attacks. DoS attacks in TCP/IP networks and NDN have both similarities and differences. Both are distributed, use a large number of requests or packets to exhaust resources, and the source of the attack may be disguised. DDoS attacks in traditional networks and NDN differ significantly in both targets and methods [2]. In traditional networks, DDoS attackers usually target specific IP addresses. In NDN, DDoS attackers aim to exhaust network resources by sending a large number of interest packets, which not only overload content servers but also cache nodes and intermediate routing nodes. In addition, traditional DDoS attacks are usually implemented using techniques such as SYN flooding and UDP flooding, while attackers in NDN take advantage of its unique data center architecture and introduce unique attack modes such as Interest Flooding Attack (IFA) [3] and content poisoning. Attackers can use IFA to send false requests to the network to exhaust pending interest table (PIT) [4] resources, or manipulate cache replacement strategies through cache pollution attack (CPA) [5] to reduce cache hit rate. Despite these challenges, NDN still provides innovative solutions to key issues in traditional IP networks, such as mobility bottlenecks and redundant data transmission, through dynamic signature verification and distributed trust management. The design and optimization of NDN security mechanisms remain a focus of future research.
Flooding attacks encompass various forms, including the IFA, Collusive Interest Flooding Attack (CIFA) [6], and the Improved Collusive Interest Flooding Attack (I-CIFA) [7]. Combining the significant attack potency of IFA with the strong concealment ability of CIFA, I-CIFA has a better attack effect than both in large topologies. The PIT in NDN routers can be depleted due to the reception of a large number of collusive data packets, which results in the occurrence of an I-CIFA attack. Combining the two types of attacks (CPA and I-CIFA) can cause even greater harm, which we refer to as I-CIFPA [8], achieved by simultaneously launching a Cache Pollution Attack and an Improved Collusive Interest Flooding Attack. In response to this type of attack, we propose an improved XGBoost, a multiclassification-based algorithm to detect interval attacks. Based on this method, the contributions of this paper include the following three points:
- The limitations of the I-CIFPA model are analyzed, and an improved XGBoost-based detection algorithm is proposed, incorporating optimized feature selection and hyperparameter tuning to enhance IFA attack detection accuracy in NDN.
- An in-depth analysis of the impact of I-CIFPA on NDN stability and resource allocation is conducted by investigating key network performance indicators, including CacheHits, TimeOutInterests, and OutInterests.
- The attack data are tested and analyzed for both single-feature and multi-feature scenarios, and the proposed algorithm is evaluated against other algorithms based on the AUC score.
The remainder of this paper is structured as follows. Section 2 provides a comprehensive review of existing countermeasures against DDoS attacks in NDN. In Section 3, the principles of hybrid attacks are examined, and a detection method for interval attacks is proposed. Section 4 analyzes the impact of I-CIFPA through simulations. And experimental results demonstrating the effectiveness of the proposed countermeasure are presented. Finally, Section 5 concludes the paper with a summary of the study and potential future research directions.
2. Related Work
With the gradual development of the NDN architecture, the research on attack models and security for NDN networks has become an important direction in the field of network security mechanisms. NDN can improve the efficiency of data transmission through content-based naming and decentralized design, but at the same time, it also exposes some unique security risks, such as interest packet flooding attacks and cache pollution attacks. Research on these attack models and detection and defense methods has gradually become a hot research direction in the field of NDN network security.
Several approaches have been proposed to detect IFA in NDN. One early method relies on satisfaction-based detection [3], where nodes monitor the ratio of satisfied interests to identify abnormal behavior. The SBPB method identifies IFA by determining whether the satisfaction level of a node falls below a predefined threshold. However, this method is limited to simple, static attack models and assumes that interest packets do not comply with caching and forwarding policies, which may lead to excessive penalties for independent decisions and insufficient ability to deal with complex scenarios such as collusion and hybrid attacks. The Poseidon detection and defense framework [9] is proposed to respond to and mitigate attacks in real time, which responds to detection through threshold settings in local algorithms and mitigates attacks via a push-back mechanism. Fixed thresholds may prevent the system from adapting to various attack patterns, and since it is deployed at routing nodes, it is relatively dependent on the network topology. A method based on Random Forest [10] is used for detecting IFA attacks. This method identifies malicious prefixes among abnormal prefixes based on the number of PIT (Pending Interest Table) entries used. Compared with other methods, the proposed scheme could reduce the occupation of PIT. The random forest algorithm uses the ensemble learning method of Bagging [11], which can lead to issues such as long training time and instability when dealing with large-scale datasets. These methods have demonstrated certain effectiveness in identifying and mitigating high-intensity IFA attacks, but low-rate attacks can hide within normal traffic and do not produce specific indicators, making it difficult to judge whether an attack is occurring based on threshold-based approaches. It is challenging to address new models of IFA attacks using these methods.
With the development of Named Data Networking, the forms of Denial-of-Service (DoS) attacks have been continuously evolving. Xin et al. were the first to propose a novel type of DoS attack, the CIFA, which is characterized by its high level of stealth, making traditional detection methods ineffective [6]. CIFA employs multiple attackers working in coordination, sending carefully crafted Interest packets at a low rate while mimicking normal communication patterns, thereby avoiding the generation of obvious anomalous traffic features. This attack strategy surpasses the limitations of traditional Interest Flooding Attacks, making it difficult for defense mechanisms based on traffic statistics or anomaly detection to capture significant attack features. These algorithms primarily employ machine learning or other single-classification algorithms.
Building on the CIFA attack, the Improved CIFA (I-CIFA) is proposed [7] and further, the hybrid combined version is introduced through I-CIFA with CPA [8]. This attack not only inherits the stealth characteristics of CIFA and enhances its attack intensity, making it more effective in depleting network resources and impacting data forwarding performance, but also exacerbates the threat of CPA attacks on caching. Currently, no defense mechanisms have been proposed against the hybrid attack of I-CIFA and CPA. Existing detection methods often fail to capture the temporal and spatial correlation between malicious interests, making them unsuitable for identifying the low-rate, distributed patterns of CIFA [12,13]. In response to this, machine learning techniques—such as Random Forest, Support Vector Machines (SVM), and Convolutional Neural Networks (CNNs)—have been increasingly applied due to their capability to model complex, nonlinear attack behaviors [14,15]. Among these, deep learning models show promise in capturing hierarchical patterns in traffic data, while ensemble methods excel in handling high-dimensional, imbalanced datasets.
From the preceding discussion, it can be concluded that prior research primarily concentrated on developing countermeasures against individual types of attacks, often overlooking the complexities and interactions involved in multi-faceted attack scenarios. Simultaneous attacks may exist in NDN networks. Most detection schemes have primarily relied on feature recognition algorithms, particularly those based on binary classification or threshold-based approaches, to identify attacks. These methods often face limitations in handling complex and evolving attack patterns that require more adaptive and nuanced detection techniques, such as under a normal state, I-CIFPA, and other network states. Therefore, previous binary classification algorithms cannot detect interval attacks, and an effective multi-classification algorithm is required. There may be two different thresholds for network traffic under interval attacks, against which previous threshold-based methods will increase the missing detection rate. Below, we introduce the attack model of I-CIFPA and its countermeasure.
3. The Attack Model and Detection Method
In the context of increasingly intelligent complex network attacks, hybrid attacks targeting NDN networks, specifically I-CIFPA attacks, exhibit cross-layer concealment characteristics. This section conducts an in-depth modeling analysis of the I-CIFA and CPA hybrid attacks to uncover their core attack mechanisms. Based on this analysis, an improved XGBoost-enhanced detection framework is proposed to enhance the model’s generalization ability while ensuring real-time performance.
3.1. The Attack Model of I-CIFPA
Figure 1 shows the attack scenario of I-CIFPA in NDN networks and cloud infrastructure composed of various routing nodes, where and are gateway nodes and is a backbone node. Before sending specific unpopular Interests to request corresponding content generated from the legitimate publisher, a CPA attacker determines which content is unpopular by tracking how often subscriber requests occur. As a result, the Content Stores (CS) in all routing nodes across the network are filled with less popular content, preventing popular content from replying to Interests and causing denial of service. Malicious Interests are intermittently sent by the I-CIFA attacker to request non-existent content carried in malicious data packets, and the collusive publisher produces malicious data packets in response.
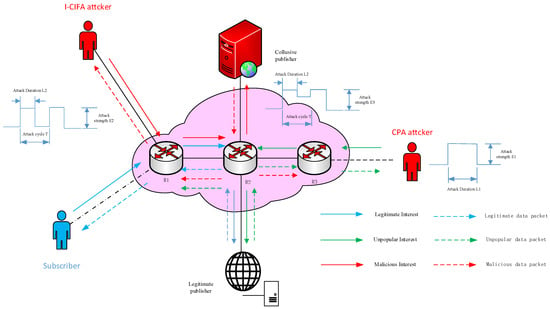
Figure 1.
Scenario of interval attacks.
In Figure 1, the attack strength of CPA is , and the attack duration is . The attack strength, duration, and cycle of I-CIFA are , , and T, respectively. To initiate a more destructive attack on NDN networks than I-CIFA and CPA, is equal to the time of the attack phase of I-CIFA. Due to the new interval attack, I-CIFPA is established by initiating I-CIFA and CPA concurrently; thus, the attack intensity of I-CIFPA is , and the attack cycle and duration are the same as those of I-CIFA, i.e., T and , respectively. Each attack pulse interval of I-CIFPA is , and CPA still exists in the network at this time.
To characterize this attack model, we propose three key features: CacheHits, the number TimeOutIntrests and OutInterests. These features are designed to better capture attack behaviors and enhance detection performance.
Consequently, I-CIFPA will cause the CS and PIT of all routing nodes to be occupied by malicious traffic in NDN networks, and subscribers will not receive a response from the publishers, leading to denial of service and seriously damaging the NDN networks.
Figure 2 shows the architecture for addressing I-CIFPA, which has four steps.
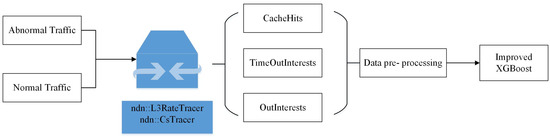
Figure 2.
Overall architecture of the detection method.
Step 1:
Design and launch I-CIFPA attack
The I-CIFPA attacker exploits the content request interval to generate spoofed interest packets that are very similar to legitimate traffic patterns. First, the I-CIFPA attack is simulated and launched in the NDN topology by controlling the infected consumer node.
Step 2:
Collect network traffic through routing nodes
In order to observe the network behavior under I-CIFPA, some routing node information is collected. These nodes are used to passively collect statistics related to interest packets and data packets, including CacheHits, TimeOutInterests and OutInterests. The data are used to provide multi-dimensional traffic attributes required for detection model training.
Step 3:
Data preprocessing and training
The raw traffic data are preprocessed to eliminate inconsistencies and ensure compatibility with the detection model. The data are labeled for known traffic states: normal, other network states, and I-CIFPA. The data are divided into training and testing subsets to support supervised learning and facilitate performance evaluation of the detection framework.
Step 4:
Develop Improved XGBoost Detection Model
We developed a real-time detection framework based on improved XGBoost to address the characteristics of I-CIFPA. The model incorporates optimized decision trees to capture nonlinear correlations between traffic features. In addition, we apply Bayesian optimization to fine-tune key hyperparameters (e.g., learning rate, tree depth, etc.) to maximize detection accuracy.
3.2. The Detection Mechanism of Improved XGBoost
Based on the overall detection process proposed earlier, the XGBoost algorithm is applied within the detection workflow. Compared with traditional IFA attack detection algorithms [10], XGBoost introduces the Gradient Boosting mechanism and automatic feature selection [16], enabling it to more precisely capture pattern changes in attack traffic. Furthermore, this method can address the issue of imbalanced data, effectively reducing the risk of minority attack samples being overlooked through sample weight adjustment and loss function optimization. Additionally, XGBoost does not rely on fixed thresholds but instead dynamically adjusts its detection strategy in a data-driven manner, meeting the real-time attack detection requirements in NDN environments. The core components of the detection framework are illustrated in Figure 3, which includes a feature extraction module, tree splits layer, transformed feature layer, softmax layer, and network decision layer. The feature extraction module collects and integrates multi-dimensional traffic features, the tree splits layer learns the importance of data features through multiple decision trees, the transformed feature layer further optimizes feature representation, the softmax layer is used for normalization calculations, and ultimately, the network decision layer provides the decision result for attack detection. The entire detection framework possesses strong generalization capability and real-time performance, making it suitable for various complex attack scenarios in NDN environments.
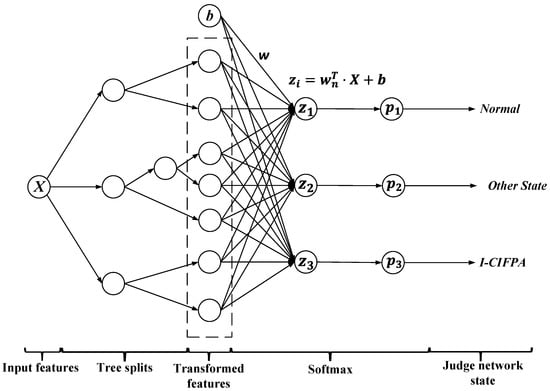
Figure 3.
Detection model based on improved XGBoost.
To evaluate the designed detection model, a data set is proposed, where represents the network traffic composed of m features. The label indicates different network states, including normal (0), I-CIFPA (1) and other network state (2). We further define , denoting the true score of the i-th sample on the n-th class, where
In order to effectively detect and distinguish normal traffic from I-CIFPA attacks, we adopted a multi-class classification model based on XGBoost. This approach enables us to build a separate decision tree for each network state and iteratively optimize it using the gradient boosting algorithm.
Let the training dataset be represented as . The model output for the i-th sample on class n after t rounds is denoted as , and the aggregated score from the previous rounds is
We use softmax to convert the raw scores into probabilities:
In this case, the corresponding loss function can be expressed as
where is the regularization term defined as:
Here, T is the number of leaves in the t-th tree, is the score of the j-th leaf node, and , are regularization parameters that help control model complexity and overfitting.
To optimize the model efficiently, we apply a second-order Taylor expansion to approximate the loss function. This leads to the following objective:
where and are the respective summations of first- and second-order derivatives on each sample belonging to the j-th leaf node:
To decide whether a node should be split, the model calculates the information gain as:
where , , and represent the loss values of the left and right leaf nodes, respectively.
After feature transformation through decision tree ensemble, each sample is represented by a fixed-length vector that encodes the high-level structural patterns learned from the original input. For the final classification of the network state, we apply a fully connected layer followed by a Softmax activation.
The score is obtained by passing the transformed features and bias b through a fully connected layer, where , and is the weight matrix. After exponentiation and normalization of the score , the probability is
where .
The final predicted network state corresponds to the class with the highest probability:
If , the network status will be judged as normal.
If , the network status will be judged as other attack.
If , the network status will be judged as I-CIFPA.
To further enhance classification accuracy, particularly in detecting the I-CIFPA class, we perform Bayesian optimization on the hyperparameters of the XGBoost model. This tuning process yields the final optimized version, called Improved XGBoost.
4. Experiment Analysis
To ensure the accuracy of the experiment, we use ndnSIM in NS-3 to simulate the experimental environment, and adopt a large topology structure for network simulation and data generation [8]. The impact of interval attacks is examined by analyzing the multi-dimensional network traffic characteristics of various routing nodes extracted from a particular network topology. These features include the counts of CacheHits, TimeOutInterests and OutInterest of backbone routing node.
4.1. Simulation Environment
Figure 4 [8] illustrates the network topology, which includes 169 red routing nodes on the outermost layer that represent subscribers, 45 green routing nodes in the intermediate layer representing gateway nodes, and the remaining 65 blue routing nodes signifying backbone nodes. In the simulation, the packet size is set to 1024 bytes, with a Content Poisoning Attack rate of 15 attacks per second and an Interval-Centric Interest Flooding Attack rate of 35 attacks per second. The attack cycle is 7 s, with an attack duration of 6 s within each cycle. The simulation spans a total time period of 0 to 200 s, during which interval attacks occur in the period between 50 and 150 s. These parameters are designed to mimic realistic network conditions under both legitimate and malicious traffic.
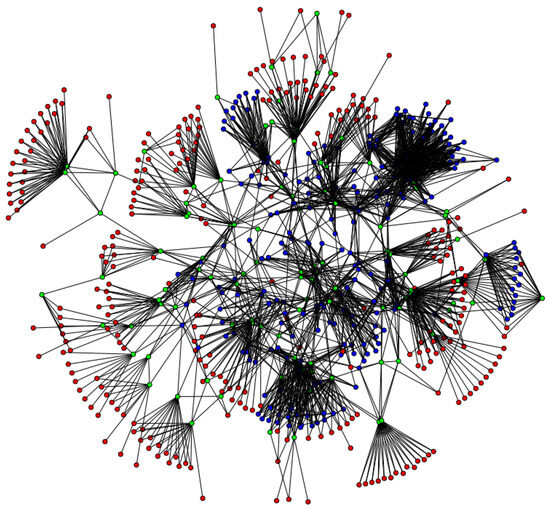
Figure 4.
Network topology.
It provides detailed experimental parameters corresponding to specific configurations of network topologies. In general, attackers have different attack rates, and the attack rates of I-CIFA and CPA are different, so the changes in network traffic can be clearly analyzed. Ideally, the CS and PIT capacities of each routing node are both set to 1000.
4.2. Performance Analysis of I-CIFPA
The I-CIFPA is simulated on the ndnSIM platform, and the built-in output program of the platform, namely the trace helper, is utilized to track the simulation results. The requested statistics are collected and aggregated by this tool, where data on CacheHits are generated by ndn::CsTracer, and TimeOutInterests and OutInterests are generated by ndn::L3RateTracer. The experimental results are shown in Figure 5, Figure 6 and Figure 7.
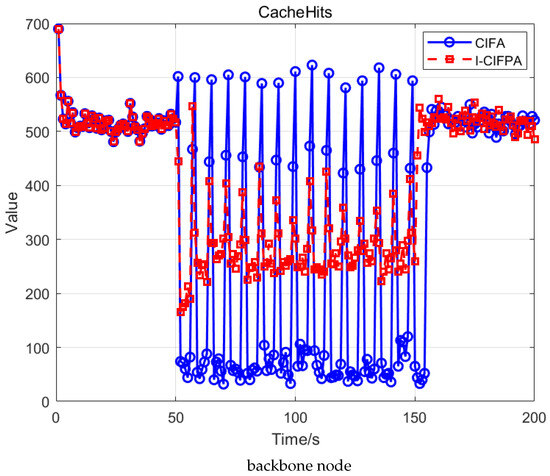
Figure 5.
Changes in CacheHits of routing nodes under different attacks.
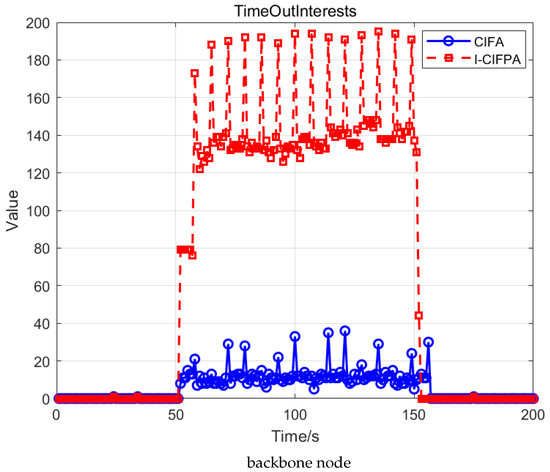
Figure 6.
Changes in TimeOutInterests of routing nodes under different attacks.
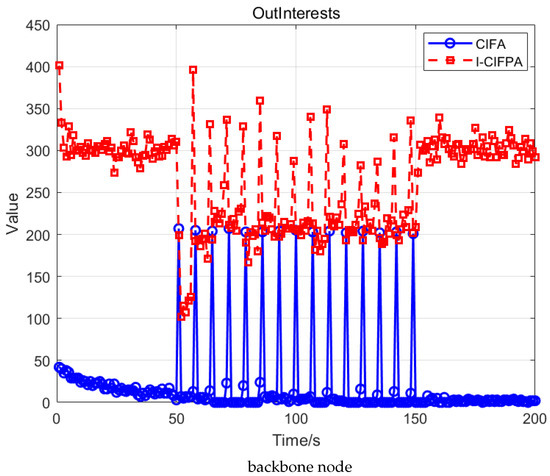
Figure 7.
Changes in OutInterests of routing nodes under different attacks.
Figure 5 shows that in the I-CIFPA scenario, the number of CacheHits is higher than that under normal and I-CIFA conditions. Additionally, CacheHits significantly increases during the attack intervals, indicating that I-CIFPA has higher stealth. Although the ideal CS capacity for each routing node is set to 1000, under limited CS capacity, I-CIFPA exhausts CS resources by caching too much unpopular content, leading to link congestion. This reduces the caching and forwarding efficiency of legitimate data packets, severely impacting the performance of the NDN network.
As shown in Figure 6, the number of TimeOutInterests under I-CIFPA is greater than those of I-CIFA, and it increases significantly during each interval attack. As a result, TimeOutInterests cannot be forwarded to publishers, so subscribers cannot receive replies from the legitimate publisher, causing a denial of service. This observation indicates that the robustness and stealth capabilities of I-CIFPA surpass those of CIFA.
Figure 7 demonstrates that during the attack interval, the number of OutInterests generated by I-CIFPA exceeds that produced by CIFA. This indicates that in the I-CIFPA scenario, the intensive transmission of interest packets leads to higher cache occupancy rates and excessive request hotspots, necessitating substantial remote resource requests. Compared with CIFA, the I-CIFPA attack integrates characteristics of CPA by simultaneously generating massive interest packets while occupying cache resources.
In summary, the numbers of CacheHits, TimeOutInterests and OutInteres take the form of periodic pulses under I-CIFPAs, severely damaging the NDN network and making the detection of and defense against I-CIFPAs more difficult.
4.3. Analysis of Experiment Result
In this section, we first determined the evaluation criteria for I-CIFPAs, and conducted analysis and experiments based on the proposed XGBoost detection model. At the same time, the parameters are continuously adjusted according to the Bayesian optimization algorithm to obtain an enhanced XGBoost model. Finally, the results are compared with other algorithms to verify the performance of the proposed method.
Table 1 presents the optimized classifier. Bayesian optimization was applied to adjust the key hyperparameters of XGBoost, aiming to enhance its performance in detecting Distributed Denial of Service (DDoS) attacks in NDN. Compared to the XGBoost baseline model, after applying Bayesian optimization, the max_depth parameter was increased from 6 to 7, allowing the model to have stronger expressive power while maintaining generalization; the n_estimators was increased from 100 to 200 to enhance the model’s learning capability; the eta (learning rate) was reduced from 0.3 to 0.1 to ensure a more stable training process and avoid performance degradation due to premature convergence. Additionally, the gamma (penalty coefficient) was adjusted from 0 to 0.01, introducing moderate regularization to prevent overfitting; the subsample (random sampling ratio) was decreased from 1 to 0.8, introducing some randomness during training to improve generalization; the min_child_weight was increased from 1 to 10, imposing stricter constraints on the minimum weight of leaf nodes to reduce noise influence and make the model more robust. These adjustments to the optimized parameters not only ensure real-time detection but also improve the generalization ability of the XGBoost model, making it more accurate and efficient in DDoS attack detection tasks within NDN environments.

Table 1.
Optimal parameters of Improved XGBoost.
Figure 8, Figure 9, Figure 10 and Figure 11 present the detection results of I-CIFPA attacks using the proposed method. In this experiment, test data were utilized for validation and detection purposes. To demonstrate the superiority of multi-feature integration, individual feature values were first separately employed for detection, followed by a comprehensive analysis using combined multi-feature values. The detection results are presented as follows.
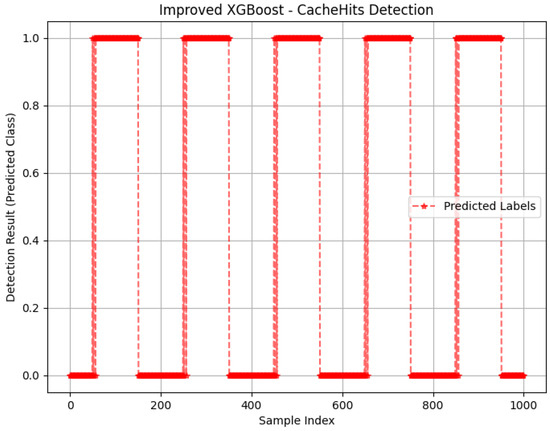
Figure 8.
The result of the proposed method through CacheHits.
Figure 9.
The result of the proposed method through TimeOutInterests.
Figure 10.
The result of the proposed method through OutInterests.
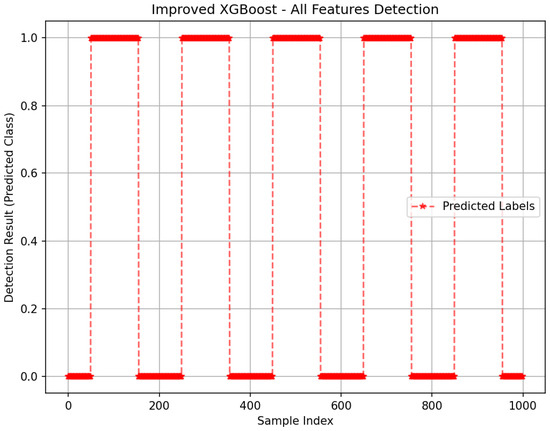
Figure 11.
The result of the proposed method through combined features.
As shown in Figure 11, the enhanced XGBoost model under multiple features shows a good advantage in detection rate. This section verifies the effectiveness and practicality of the multi-feature fusion strategy by comparing the experimental results of single-feature detection and joint multi-feature detection. Figure 8, Figure 9 and Figure 10 reveal the limitations of single-feature detection; CacheHits reflects the node cache efficiency, but cannot distinguish between normal high-demand traffic and abnormal cache behavior caused by attacks. TimeOutInterest represents the proportion of unresponded interest packets, and its detection results are easily affected by non-attack factors such as network congestion. OutInterests can intuitively indicate interest packet flooding attacks, but it is not sensitive enough to low-rate covert attacks. In contrast, the joint multi-feature method integrates multiple dimensions such as cache occupancy patterns and interest packet routing characteristics to obtain better detection results and better performance. This method significantly improves the model’s ability to distinguish complex attacks without introducing too much computational overhead.
To demonstrate the performance of the proposed improved XGBoost, we conducted experiments to compare it with XGB [17], KNN [18], ADA [19] and Random Forest [20]. Figure 12 shows the final results of multiple experiments and the average of each experiment.
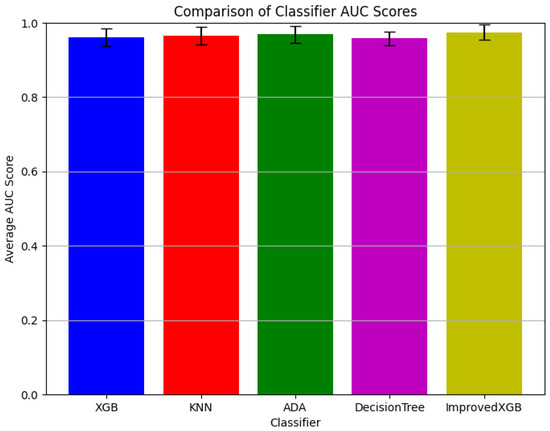
Figure 12.
AUC scores between Improved XGBoost and other methods.
As shown in Figure 12, the AUC score corresponding to the enhanced XGBoost model exceeds the baseline model of other multi-classification based machine learning algorithms. After averaging the results over 10 experiments, the final AUC values for each classifier are as follows: XGB: 0.9615, KNN: 0.9653, ADA: 0.9695, DecisionTree: 0.9583, and ImprovedXGB: 0.9746. Experimental results shows that the Improved XGBoost achieves higher AUC values across multiple experiments, indicating better classification performance. And compared to other models, the Improved XGBoost exhibits less fluctuation across different runs, proving its robustness. These findings confirm that the proposed Improved XGBoost model is more effective and reliable than traditional machine learning models in detecting and classifying network states.
5. Conclusions
In this paper, an enhanced XGBoost-based detection method is proposed to identify the I-CIFPA in NDN. The study first evaluates the performance characteristics of IFA and I-CIFPA, demonstrating that I-CIFPA exhibits significantly enhanced stealthiness and destructiveness. In feature detection experiments, results confirm that multi-feature fusion outperforms single-feature approaches. Comparative validations against other algorithms show the proposed method achieves superior performance in key metrics such as detection rate and AUC score, providing a reliable solution for efficient security protection in NDN. It is recommended that future research combine the cooperation mechanism between routing nodes and adopt a federated learning framework to optimize the detection scheme of I-CIFPA. By combining the dynamic cache strategy with the PIT space management mechanism, the practicality and defense effect of the detection scheme will be further improved.
Author Contributions
Conceptualization, Z.W.; Validation, W.Y.; Formal analysis, S.P.; Writing—original draft, L.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by a research project funded by the National Key R&D Program of China (2022YFB3904503), the National Natural Science Foundation of China (62172418), and the Education Commission Research Project of Tianjin, China under Grant (2022KJ067).
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Zhang, Z.; Yu, Y.; Zhang, H.; Newberry, E.; Mastorakis, S.; Li, Y.; Afanasyev, A.; Zhang, L. An Overview of Security Support in Named Data Networking. IEEE Commun. Mag. 2018, 56, 62–68. [Google Scholar] [CrossRef]
- Gasti, P.; Tsudik, G.; Uzun, E.; Zhang, L. DoS and DDoS in Named-Data Networking. In Proceedings of the 2013 22nd International Conference on Computer Communication and Networks (ICCCN), Nassau, Bahamas, 30 July–2 August 2013; pp. 1–7. [Google Scholar]
- Afanasyev, A.; Mahadevan, P.; Moiseenko, I.; Uzun, E.; Zhang, L. Interest flooding attack and countermeasures in Named Data Networking. In Proceedings of the 2013 IFIP Networking Conference, Brooklyn, NY, USA, 22–24 May 2013; pp. 1–9. [Google Scholar]
- Khaderani, H.A.; Muhammadi, I.; Muhammad, L.R.; Sucipto, A.; Kusumastuti, L.R.; Nurhayati, A.; Ahdan, S.; Syambas, N.R. Effect of Interest Variation and Prefix Length on Pending Interest Table (PIT) Performance in Named Data Networking (NDN). In Proceedings of the 2023 9th International Conference on Wireless and Telematics (ICWT), Solo, Indonesia, 6–7 July 2023; pp. 1–5. [Google Scholar]
- Conti, M.; Gasti, P.; Teoli, M. A lightweight mechanism for detection of cache pollution attacks in Named Data Networking. Comput. Netw. 2013, 57, 3178–3191. [Google Scholar] [CrossRef]
- Xin, Y.; Li, Y.; Wang, W.; Li, W.; Chen, X. A Novel Interest Flooding Attacks Detection and Countermeasure Scheme in NDN. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–7. [Google Scholar]
- Mulyana, E.; Syambas, N.R. The Impact of Interest Flooding Attack (IFA) and Collusive IFA on Named Data Networking (NDN). In Proceedings of the 2023 6th International Seminar on Research of Information Technology and Intelligent Systems (ISRITI), Batam, Indonesia, 11 December 2023; pp. 207–212. [Google Scholar]
- Liu, L.; Peng, S. Detection of A Novel Dual Attack in Named Data Networking. In Proceedings of the 2022 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Melbourne, Australia, 17–19 December 2022; pp. 1–8. [Google Scholar]
- Compagno, A.; Conti, M.; Gasti, P.; Tsudik, G. Poseidon: Mitigating interest flooding DDoS attacks in Named Data Networking. In Proceedings of the 38th Annual IEEE Conference on Local Computer Networks, Sydney, NSW, Australia, 21–24 October 2013; pp. 630–638. [Google Scholar]
- Xing, G.; Chen, J.; Hou, R.; Zhou, L.; Dong, M.; Zeng, D.; Luo, J.; Ma, M. Isolation Forest-Based Mechanism to Defend against Interest Flooding Attacks in Named Data Networking. IEEE Commun. Mag. 2021, 59, 98–103. [Google Scholar] [CrossRef]
- Carletti, M.; Terzi, M.; Susto, G.A. Interpretable Anomaly Detection with DIFFI: Depth-based feature importance of Isolation Forest. Eng. Appl. Artif. Intell. 2023, 119, 105730. [Google Scholar] [CrossRef]
- Benmoussa, A.; Tahari, A.e.K.; Kerrache, C.A.; Lagraa, N.; Lakas, A.; Hussain, R.; Ahmad, F. MSIDN: Mitigation of Sophisticated Interest flooding-based DDoS attacks in Named Data Networking. Future Gener. Comput. Syst. 2020, 107, 293–306. [Google Scholar] [CrossRef]
- Salah, H.; Strufe, T. Evaluating and mitigating a collusive version of the interest flooding attack in NDN. In Proceedings of the 2016 IEEE Symposium on Computers and Communication (ISCC), Messina, Italy, 27–30 June 2016; pp. 938–945. [Google Scholar]
- Zhou, J.; Luo, J.; Deng, L.; Wang, J. Defense Mechanism of Interest Flooding Attack Based on Deep Reinforcement Learning. In Proceedings of the 2020 3rd International Conference on Hot Information-Centric Networking (HotICN), Hefei, China, 12–14 December 2020; pp. 65–70. [Google Scholar]
- Hidouri, A.; Hajlaoui, N.; Touati, H.; Hadded, M.; Muhlethaler, P. A Survey on Security Attacks and Intrusion Detection Mechanisms in Named Data Networking. Computers 2022, 11, 186. [Google Scholar] [CrossRef]
- Deng, J.; Cheng, L.; Yuan, H.; Zheng, K.; Li, X.; Li, Q. An Online Detection System for LDoS attack Based on XGBoost. In Proceedings of the 2023 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Wuhan, China, 21–24 December 2023; pp. 1083–1088. [Google Scholar]
- Chen, Z.; Jiang, F.; Cheng, Y.; Gu, X.; Liu, W.; Peng, J. XGBoost Classifier for DDoS Attack Detection and Analysis in SDN-Based Cloud. In Proceedings of the 2018 IEEE International Conference on Big Data and Smart Computing (BigComp), Shanghai, China, 15–17 January 2018; pp. 251–256. [Google Scholar]
- Ma, Z.; Kaban, A. K-Nearest-Neighbours with a novel similaritymeasure for intrusion detection. In Proceedings of the IEEE 13th UK Workshop on Computational Intelligence (UKCI), Guildford, UK, 9–11 September 2013; pp. 266–271. [Google Scholar]
- Hu, W.; Maybank, S. AdaBoost-Based Algorithm for Network Intrusion Detection. IEEE Trans. Syst. Man Cybern. Part Cybern. 2008, 38, 577–583. [Google Scholar]
- He, H.; Garcia, E.A. Learning from Imbalanced Data. IEEE Trans. Knowl. Data Eng. 2009, 21, 1263–1284. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).