Abstract
Blockchain technology is emerging as a pivotal framework to enhance the security of internet-based systems, especially as advancements in machine learning (ML), artificial intelligence (AI), and cyber–physical systems such as smart grids and IoT applications in healthcare continue to accelerate. Although these innovations promise significant improvements, security remains a critical challenge. Blockchain offers a secure foundation for integrating diverse technologies; however, vulnerabilities—including adversarial exploits—can undermine performance and compromise application reliability. To address these risks effectively, it is essential to comprehensively analyze the vulnerability landscape of blockchain systems. This paper contributes in two key ways. First, it presents a unique layer-based framework for analyzing and illustrating security attacks within blockchain architectures. Second, it introduces a novel taxonomy that classifies existing research on blockchain vulnerability detection. Our analysis reveals that while ML and deep learning offer promising approaches for detecting vulnerabilities, their effectiveness often depends on access to extensive and high-quality datasets. Additionally, the layer-based framework demonstrates that vulnerabilities span all layers of a blockchain system, with attacks frequently targeting the consensus process, network integrity, and smart contract code. Overall, this paper provides a comprehensive overview of blockchain security threats and detection methods, emphasizing the need for a multifaceted approach to safeguard these evolving systems.
1. Introduction
Blockchain is considered one of the most popular technologies in recent times due to its inherent potential to become a source of reliability. Due to the decentralized nature and trustworthiness of blockchain, it has been widely adopted in different applications such as cryptocurrency or electronic cash, financial transactions, healthcare, insurance, IoT, manufacturing, education, etc. IBM pointed out in [1] that the significant advantage of blockchain is having no single-point failure. Hence, it is very unlikely to be influenced. However, it is not entirely immune to adversarial vulnerabilities, as adversaries are becoming smarter in parallel to new technological development. It has always been a game between adversaries and defenders. Such adversarial vulnerabilities can affect—directly or indirectly—the integrity, availability, privacy, and confidentiality of the system. These are known as security vulnerabilities.
A series of high-profile breaches underscore these risks. For example, the theft of nearly USD 73 million in bitcoins from Bitfinex [2] and the exploitation of the Decentralized Autonomous Organization (DAO), which resulted in more than USD 60 million in lost ether [3], demonstrate that even large-scale, trusted systems are vulnerable. Similarly, an incident at Bithumb, where an employee’s compromised computer led to a hacking event affecting 30,000 users and resulting in a loss of USD 870,000 in bitcoin [4], further highlights the fragility of blockchain security. These incidents collectively emphasize the need for a systematic study of the attack surface in blockchain-based systems so that vulnerabilities can be detected and prevented effectively and efficiently.
Recent studies also highlight a wide array of vulnerabilities across different layers and components of blockchain systems but often lack a systematic classification approach. For example, Mollajafari et al. [5] presented a seven-layer perspective emphasizing smart contract vulnerabilities and centralization threats. However, their discussion lacked detailed coverage of vulnerabilities in emerging blockchain ecosystems, and their approach did not comprehensively address vulnerabilities beyond smart contracts at a detailed operational level. Similarly, Dwivedi et al. [6] presented an in-depth classification of blockchain attacks, categorizing vulnerabilities and mitigations across blockchain layers. Yet, their work provided limited integration of novel attack surfaces appearing in newer blockchain platforms such as Polkadot, Solana, or Avalanche, which increasingly face distinct vulnerabilities due to different consensus mechanisms and layer interactions.
Gurjar et al. [7], Hejazi et al. [8], and Chu [9] thoroughly explored smart contract vulnerabilities and detection techniques. While comprehensive in the smart contract context, their work lacked broader integration into the overall blockchain security landscape. This narrow focus overlooked critical vulnerabilities inherent in other layers, such as network, consensus, or application layers. while recent research by Rajawat et al. [10] emphasized AI-driven approaches for blockchain security, the integration and systematic analysis of machine learning methodologies across different blockchain layers remain limited. Magalhães et al. [11] systematically reviewed current blockchain vulnerabilities but did not fully capture or specifically analyze layer-specific vulnerabilities emerging within newer blockchain ecosystems. These modern platforms introduce novel attack vectors due to unique consensus algorithms, interoperability features, and sophisticated transaction processing methods, thus necessitating a revised and expanded taxonomy to address their distinct security challenges comprehensively.
Beyond these, Verma et al. [12] proposes a federated learning framework to tackle zero-day vulnerabilities, indicating the growing role of machine learning in both defending and attacking blockchain infrastructures. While existing surveys and research have explored blockchain security issues, they often lack a systematic approach to categorizing and analyzing vulnerabilities. Many existing reviews focus primarily on trending approaches and applications within specific domains such as Internet of Things (IoT), without dedicated examination of security and privacy in decentralized federated learning (DFL) [13,14]. Similarly, surveys on security and privacy in centralized federated learning (FL) do not adequately address the unique challenges posed by DFL [13,14,15]. Some studies have attempted to address security issues in centralized FL through blockchain integration, but a comprehensive security analysis of DFL threats and their potential defense mechanisms remains lacking [13,14,16,17]. Additionally, while existing surveys may mention attacks on different layers of the blockchain system, they rarely provide a detailed, layer-by-layer breakdown of vulnerabilities, their impact, and corresponding countermeasures [18,19]. This lack of a systematic approach can hinder a comprehensive understanding of blockchain security threats and their potential mitigations.
In this research, we address these limitations by proposing a comprehensive, novel, layer-based analysis to systematically categorize blockchain attacks. We provide an explicitly detailed and unified taxonomy structured around all blockchain layers, not restricted merely to smart contract vulnerabilities, but extensively covering network, consensus, data, application, and infrastructure layers, offering systematic insights into vulnerabilities, attack impacts, and countermeasures. Our paper provides a detailed analysis of common blockchain attacks, including their layer information, impact, potential countermeasures, and the taxonomy of blockchain vulnerability detection. Furthermore, we propose a novel taxonomy of blockchain vulnerability detection, organized into seven distinct categories based on their methodologies and focal problems.
The motivation behind adopting a structured, layer-based classification in this research stems from the critical need to systematically address and mitigate the growing complexity and diversity of blockchain security vulnerabilities. Existing literature often lacks comprehensive coverage of vulnerabilities across different blockchain layers, particularly neglecting how these vulnerabilities interact across layers and impact overall system integrity. Moreover, emerging blockchain ecosystems introduce unique cross-layer interactions and novel attack vectors, making a unified and adaptable classification increasingly essential. Therefore, a clearly defined, layer-based taxonomy provides researchers and practitioners with a practical and systematic framework to precisely identify, analyze, and respond to vulnerabilities, thereby significantly enhancing targeted security interventions. Additionally, this approach inherently accommodates continuous updates and scalability, ensuring its relevance as blockchain technologies advance, new threats emerge, and innovative defense mechanisms evolve.
In addition to that, this paper also explores the evolving role of machine learning (ML) in both facilitating and combating blockchain security attacks. In summary, we want to answer the following concerns in this survey:
- RQ1: How can blockchain security threats be categorized and analyzed based on the specific layer of the blockchain system they target?
- RQ2: What are the common attack vectors and their potential impact on different blockchain layers? What countermeasures can be implemented to mitigate these threats?
- RQ3: What are the prominent categories of research on blockchain vulnerability detection, and how can they be systematically classified based on their methodologies and focal problems?
- RQ4: What are the strengths and weaknesses of each vulnerability detection category, and how can this comparative analysis inform the selection of appropriate tools and techniques?
The remainder of this article is structured as follows: Section 2 provides a comprehensive overview of blockchain architecture and the system’s operational mechanisms. In Section 3, we introduce a unique layer-based framework to systematically categorize and analyze blockchain security attacks, presenting a detailed table that outlines common attack vectors, their target layers, potential impact, and countermeasures. This section aims to provide a clear and structured understanding of how vulnerabilities manifest and can be mitigated across different layers of a blockchain system. Section 4 presents a vulnerability detection taxonomy and provides a detailed analysis of various vulnerability detection approaches, along with a preliminary discussion on the evolving role of machine learning (ML) in both enhancing and threatening blockchain security. More details on specific aspects of ML are presented in Section 5. Finally, Section 6 concludes the article by summarizing key findings, emphasizing the significance of the proposed taxonomy and layer-based framework, and highlighting crucial areas for future research in blockchain security.
2. Blockchain: An Overview
Blockchain technology can be implemented in various forms, such as private, public, and consortium-based systems. Despite the differences in architecture, each blockchain system consists of a fixed set of core components that collectively handle transaction processing. In this section, we describe these key components and outline the general transaction life cycle, thereby providing the foundation for our subsequent discussion on security vulnerabilities.
2.1. Key Components of Blockchain
Based on a review of existing works [20,21,22,23,24,25], we identify several core components that are common across different blockchain implementations. These include the distributed ledger, consensus algorithm, smart contract, immutable records (or transactions), and nodes.
2.1.1. Node
A node represents an individual user or computer that participates in the blockchain network. Nodes are interconnected via the Internet, and their membership criteria vary depending on whether the blockchain is private or public. Each node possesses a unique pair of private and public keys, which are essential for securely initiating and validating transactions.
2.1.2. Immutable Records (Transactions)
Transactions, or immutable records, are the fundamental units of information exchanged within a blockchain network. When a transaction is completed and added to the shared ledger, it becomes immutable, ensuring that the recorded information remains tamper-proof. This immutability is central to establishing trust among network participants.
2.1.3. Distributed Ledger
The distributed ledger, also known as the shared ledger, is the database that records all transactions across the network. Since every node has access to the ledger, it ensures transparency and consistency across the blockchain. The management and updating of this ledger are governed by smart contracts and validated through consensus mechanisms.
2.1.4. Smart Contract
Smart contracts are self-executing programs embedded within the blockchain. They define a set of rules for processing transactions and automatically enforce these rules when certain conditions are met. By validating and controlling the propagation of transactions among nodes, smart contracts play a critical role in maintaining the integrity of the ledger.
2.1.5. Consensus Algorithm
The consensus algorithm is the core mechanism that enables a decentralized network to agree on the validity of transactions. It ensures that, once a transaction is initiated, all nodes reach a majority-based agreement on its legitimacy before the transaction is permanently added to the blockchain. This process, which involves proof-of-work, proof-of-stake, or other consensus techniques, is essential for maintaining security and trust in a system without a central authority.
2.2. How Blockchain Works
In this section, we describe the typical life cycle of a transaction in a blockchain system. This overview is informed by previous studies [18,19,21,24,26,27,28,29] and highlights the stages where security breaches may occur.
2.2.1. Request Transaction
Any node within the blockchain network can initiate a transaction request. For example, in Bitcoin, one node might request to transfer a certain amount of cryptocurrency to another. Each transaction is first digitally signed with the node’s private key and then broadcast across the network along with the corresponding public key. This process ensures that all nodes are informed of the pending transaction.
2.2.2. Validate Transaction
Once a transaction is broadcast, it is subject to validation by smart contracts, which enforce the predefined rules for transactions. If a transaction fails to meet these criteria, it is immediately discarded, thereby preventing any invalid data from entering the ledger.
2.2.3. Verify Transaction
Validated transactions then undergo verification through the consensus algorithm. This step involves combining the transaction with a timestamp and ensuring that it conforms to the network’s consensus rules. Only transactions that pass this verification are considered eligible for inclusion in a new block.
2.2.4. Append Block and Complete
After verification, the transaction is grouped into a block. Nodes then check that the new block correctly references the hash of its predecessor and that all contained transactions are valid. If these conditions are met, the block is appended to the blockchain. Otherwise, the block is rejected, ensuring the integrity and continuity of the ledger.
This overview of blockchain components and the transaction life cycle sets the stage for a detailed analysis of the security challenges and vulnerabilities discussed in the following sections.
3. Security Threats
In this section, we discuss the security vulnerabilities that can arise in a blockchain system. Before delving into the specific security issues, it is important to understand why ensuring security in blockchain-based systems is inherently challenging.
3.1. Methodology for Attack Classification
Our approach to classifying blockchain security threats involved a targeted literature review across major academic databases, including IEEE Xplore, ACM Digital Library, SpringerLink, and Google Scholar. The review process followed three key steps:
- Article Selection: We searched for papers using terms such as “blockchain attacks”, “security taxonomy”, and “vulnerabilities in distributed ledgers”. Studies were included if they (i) focused on blockchain-based systems, and (ii) presented or discussed a classification of security threats or attack types.
- Relevance Screening: Titles and abstracts were reviewed to filter out papers that were either not technical, not related to blockchain, or purely focused on cryptographic primitives. This helped ensure focus on architectural and systemic security threats.
- Classification Analysis: For each selected study, we examined how attacks were categorized (e.g., by type, impact, architecture layer). This comparative analysis informed the design of our own five-layer taxonomy, which maps attacks to the data, network, consensus, contract, and application layers of blockchain systems.
This structured yet flexible approach ensured that our taxonomy is informed by prior literature, while offering a more architecture-aligned and extensible classification framework.
3.2. Reviewed Security Literatures
In traditional centralized systems, components are grouped and organized so that every transaction or information exchange follows a defined route dictated by established policies or security controls. This arrangement helps minimize the potential scope of exploitation. In contrast, blockchain-based decentralized architectures lack well-defined boundaries among components, making it difficult to design and implement robust measures against adversarial manipulation. Furthermore, as noted in [18], authentication is the primary security control in blockchain systems, requiring open access to network nodes (or users) for autonomous operation. This structure limits the implementation of additional security measures beyond strong, cryptography-based authentication.
Security vulnerability analysis is a critical area of blockchain research, with various studies offering different perspectives on potential attacks. For example, the work in [30] identifies six different types of attacks. In [27], blockchain security threats are broadly classified into four types, discussing eleven distinct attacks. Similarly, Dasgupta et al. [31] groups eighteen different attacks into eight categories, while [32] divides sixteen attack types into seven classes. In [33], the authors identify nine classes covering twenty-four different attacks, and Saad et al. [28] categorizes blockchain attacks into three broad types encompassing twenty-two attacks. Moreover, Lee at al. [18] documents twenty-three different types of attack, and Mosakheil et al. [29] discusses five different security threat types, under which thirty attack incidents are identified.
Together, these studies underscore the complexity and diversity of security vulnerabilities in blockchain systems and highlight the pressing need for systematic analysis and effective countermeasures. Table 1 provides a summary of attack classifications by different works.

Table 1.
Comparison of our layer-based taxonomy with existing classifications.
3.3. Layer-Based Attack Classification
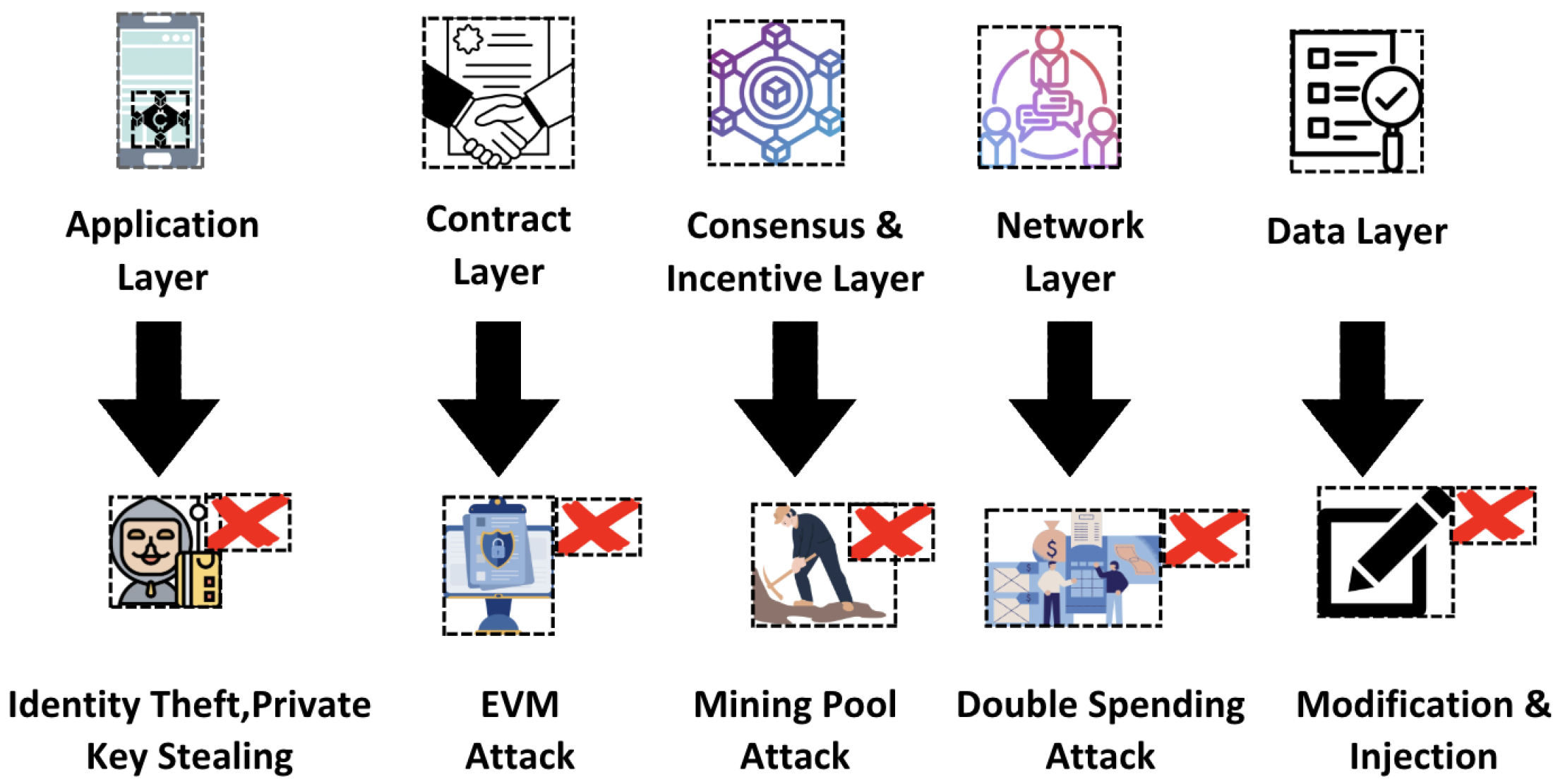
In Figure 1, a layer-wise decomposition of the blockchain network and the primary vulnerabilities are shown on the respective sides. Later, Table 2 provides a summary of different kinds of attacks on different layers, and their countermeasures are shown.
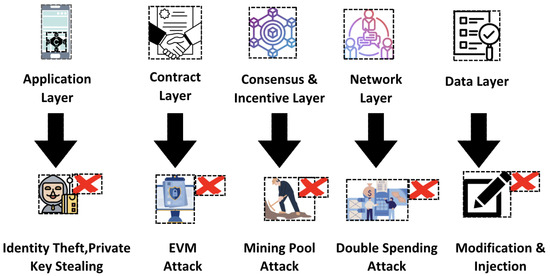
Figure 1.
Layer-based classification of blockchain attacks, highlighting representative vulnerabilities at each layer (application, contract, consensus and incentive, network, and data).

Table 2.
Summary of different attacks on blockchain.
To systematically assign attacks to blockchain layers, we established explicit classification criteria based on each attack’s primary mechanism and its point of impact within the blockchain architecture. This structured approach aligns vulnerabilities clearly with the specific blockchain layer they affect, enabling targeted and efficient mitigation strategies. By understanding attacks within this layered context, security researchers and blockchain developers can more effectively implement defense mechanisms that address the root architectural causes of vulnerabilities. Specifically, attacks targeting transaction structures, cryptographic integrity, or ledger consistency, such as the transaction malleability attack, where an adversary manipulates transaction IDs by altering digital signatures, are categorized within the Data Layer [36]. Attacks disrupting node-to-node communication, routing protocols, or network connectivity, such as the Sybil attack, which involves creating numerous fake identities to disproportionately influence network decisions, are classified under the Network Layer [37]. Vulnerabilities compromising consensus algorithms or incentive mechanisms designed to regulate miner or validator behavior are assigned to the Consensus & Incentive Layer; a prominent example includes the 51% attack, wherein an attacker seeks majority control over the network’s mining resources to manipulate blockchain state. Smart contract-specific vulnerabilities arising from programming flaws or execution logic errors, such as the re-entrancy attack, involving repeated calls to vulnerable functions before completion of their initial execution, are classified into the Contract Layer [5]. Lastly, vulnerabilities exploiting end-user interfaces, wallet security weaknesses, or external software applications such as cryptojacking, where attackers illicitly utilize computing resources to mine cryptocurrencies, are grouped under the Application Layer. This comprehensive, layer-centric approach enhances clarity, facilitates reproducibility, and supports the deployment of precise and effective blockchain security measures.
From Table 3, we can infer that while our taxonomy is designed around traditional chain-based blockchains (e.g., Bitcoin, Ethereum), it can be extended to accommodate other architectures such as DAG-based systems (e.g., IOTA [38], Hedera), hybrid blockchains (e.g., Hyperledger Fabric [39]), sharded blockchains (e.g., Ethereum 2.0 [40]), and BFT-based platforms (e.g., Cosmos, Tendermint [41]).

Table 3.
Applicability of layer-based taxonomy to blockchain architectures.
The core architectural concepts—data persistence, peer communication, consensus coordination, contract logic, and user-facing applications—are present in all these systems, albeit with architectural nuances. DAGs remove block serialization but retain vulnerabilities across the network and consensus layers. Hyperledger lacks incentive mechanisms but retains contract-level logic via chaincode. Sharded platforms require coordinated consensus across shards and routing mechanisms, while BFT-based protocols must address equivocation and round-skipping attacks. Despite these differences, the five-layer taxonomy remains applicable with only minor adjustments to consensus or contract layers, validating its utility across diverse decentralized architectures.
4. Security Attacks
In this section, we present some of the well-known attacks discovered per layer from our study focusing on security issues.
4.1. Data Layer
In this section, we discuss several security vulnerabilities that can arise at the data layer of blockchain systems. These vulnerabilities exploit weaknesses in transaction handling and cryptographic mechanisms, often resulting in double-spending or unauthorized manipulation of funds.
4.1.1. Transaction Malleability Attack
In a transaction malleability attack [18,27,29,31,42], the adversary exploits a design flaw where certain non-essential parts of a transaction can be modified without changing its underlying intent. This manipulation results in a different transaction ID, leading the sender to believe that the original transaction has failed or not been confirmed on the network. Consequently, the sender may inadvertently reissue the same transaction, effectively causing the funds to be transferred twice.
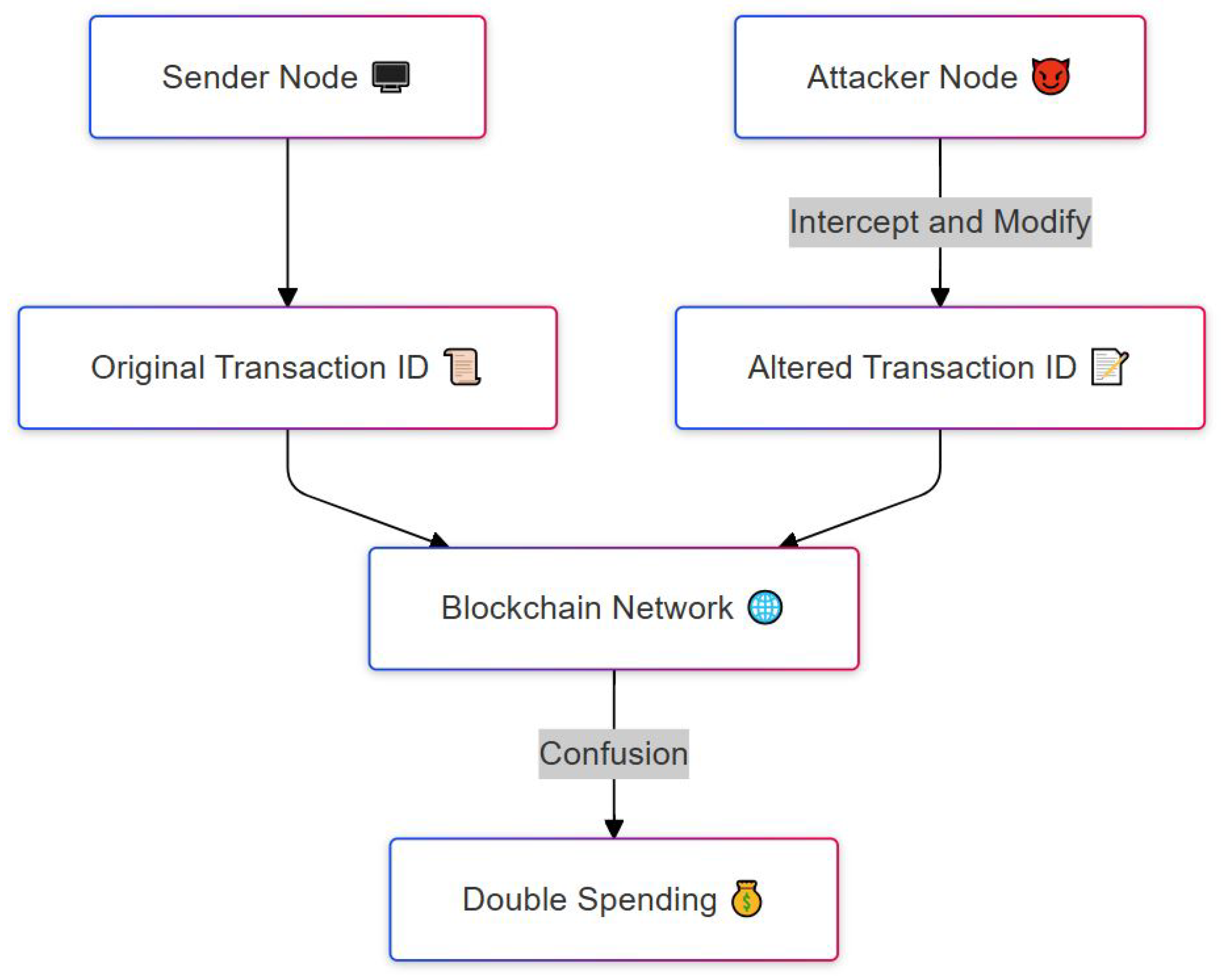
Figure 2 illustrates the process of a transaction malleability attack, which targets the integrity of transaction identifiers in a blockchain network. The attack begins with a sender node (top left) that initiates a legitimate transaction, generating an original transaction ID. Meanwhile, an attacker node (top right) intercepts this transaction as it is being broadcast to the network. The attacker slightly alters the transaction’s structure, such as by modifying a non-critical field, which changes its ID while keeping the core transaction valid. This results in an altered transaction ID, shown in the right branch. Both the original and the modified versions may reach the blockchain network at the same time, causing confusion over which transaction is valid. If the network accepts the altered version and discards the original, the sender may believe their payment did not go through and issue a second transaction. This leads to a double-spending scenario, where the same funds are spent more than once. The figure clearly shows how a small change introduced by an attacker at the transaction level can mislead the network and compromise the integrity of the ledger.
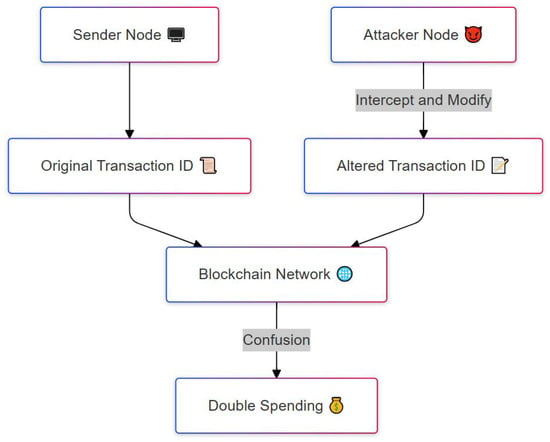
Figure 2.
Transaction malleability attack where the transaction ID is modified to enable double-spending.
If the network confirms the modified transaction before the original, the sender ends up paying twice the intended amount. Historically, this vulnerability played a significant role in the collapse of Mt. Gox in 2014, a major Bitcoin exchange that controlled approximately 70% of the market at the time. Although the exact impact of malleability on the Mt. Gox incident is subject to debate, it is widely cited as a contributing factor. Modern blockchain implementations, such as the upgraded Bitcoin protocols with Segregated Witness, have largely mitigated this risk, though the process can still introduce delays in transaction confirmations.
4.1.2. Quantum Attack
Blockchain systems currently depend on cryptographic schemes—such as RSA and elliptic curve (EC) cryptography—to secure transactions and generate private–public key pairs. However, advances in quantum computing have raised concerns about the future security of these systems. Quantum attacks [42] refer to the theoretical capability of quantum computers to break conventional cryptographic algorithms, potentially rendering these security measures ineffective. Although practical quantum attacks have not yet materialized, the substantial computational power of quantum systems suggests that no cryptography-based system can be considered entirely secure in the long term.
For instance, researchers estimate that a classical computer with a 5 GHz CPU would require approximately 13.7 billion years [43] to break a 2048-bit RSA cipher—the current standard for secure encryption. In stark contrast, a quantum computer operating at 10 MHz could potentially break the same cipher in roughly 42 min. This dramatic difference underscores the significant threat that quantum computing poses to blockchain security.
To address this issue, the development and implementation of quantum-resistant key generation techniques have become a priority [44]. These techniques are designed to withstand attacks from both classical and quantum computers, thereby ensuring the long-term security and integrity of blockchain systems.
4.2. Network Layer
The network layer plays a critical role in the functioning of blockchain systems by enabling communication among nodes and facilitating the propagation of transactions and blocks. However, the open and decentralized nature of the network also makes it susceptible to a variety of attacks. In this section, we discuss several common network-layer attacks, their mechanisms, and possible countermeasures.
4.2.1. Sybil Attack
A Sybil attack [18,27,29,31,32,42] occurs when an adversary creates multiple fake identities (or nodes) within the network. By doing so, the attacker can gain disproportionate influence over the network, disrupting consensus and manipulating the flow of information. To prevent Sybil attacks, robust identity management and reputation systems are essential. These systems help detect and mitigate the presence of fake nodes, ensuring that only legitimate participants contribute to the network.
4.2.2. Eclipse Attack
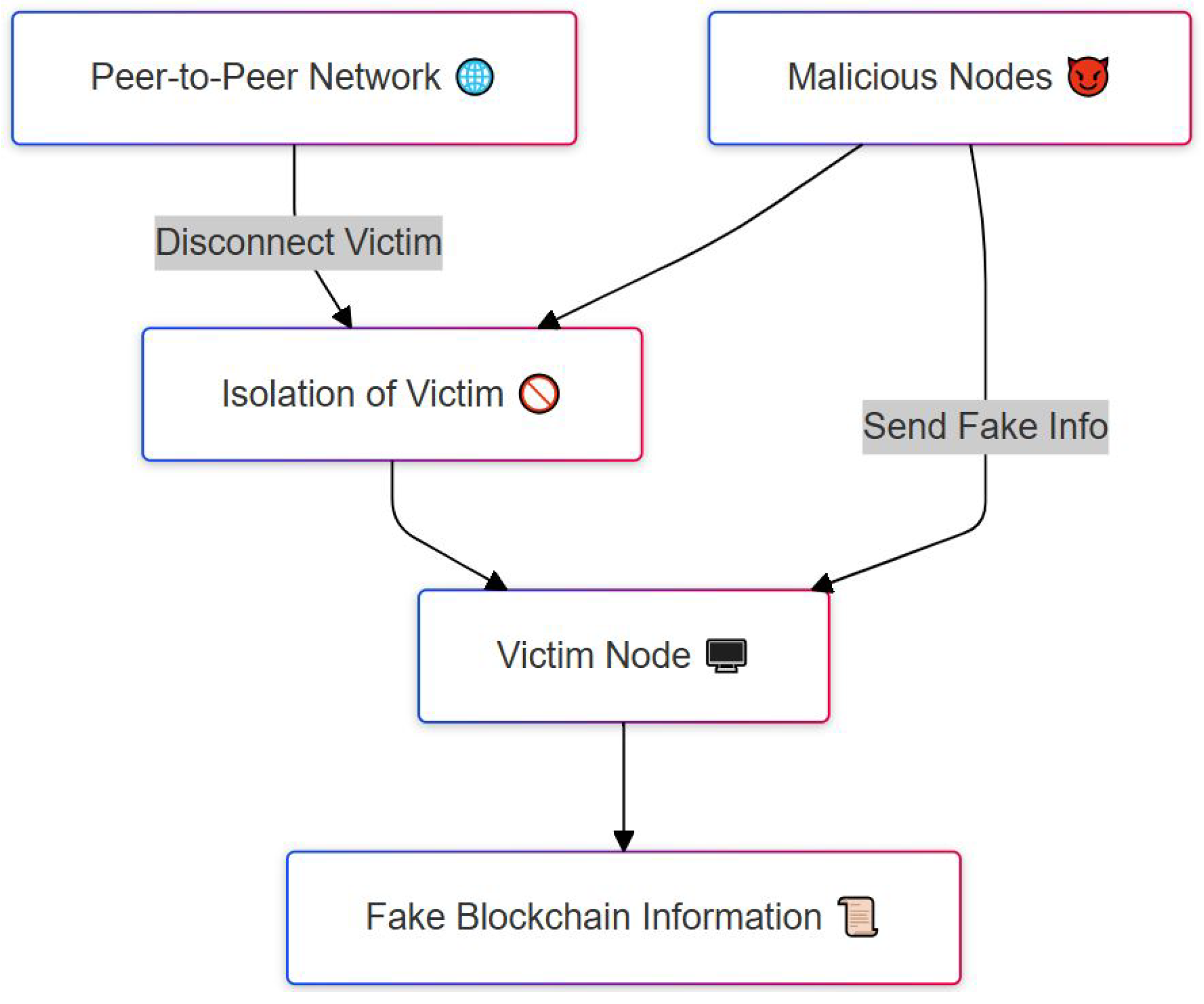
An eclipse attack [27,29,30,32,42] aims to isolate a targeted node by monopolizing its peer connections. In this attack, the adversary gains control over a large number of IP addresses and replaces the legitimate entries in the target node’s address table. When the target node restarts, it connects exclusively to these malicious nodes, effectively isolating it from the rest of the network. As a result, the attacker can feed the victim false blockchain data and manipulate its view of the network.
Figure 3 illustrates the process of an eclipse attack, a type of network-layer threat in blockchain systems where an attacker isolates a victim node from the rest of the network. The attack begins with malicious nodes that aim to cut off a victim node from the legitimate peer-to-peer network (top left). This is done by disconnecting the victim from honest peers, leading to the isolation of the victim (middle left). Once isolated, the attacker surrounds the victim with only malicious nodes and begins to send fake information (top right). Since the victim is now cut off from trustworthy sources, it relies entirely on the attacker-controlled nodes for blockchain data. As a result, the victim node is misled into accepting fake blockchain information, such as false transaction histories or manipulated block data. This can have serious consequences, including enabling double-spending or censoring transactions. The diagram clearly shows how isolation and misinformation are used together to compromise the victim’s view of the blockchain.
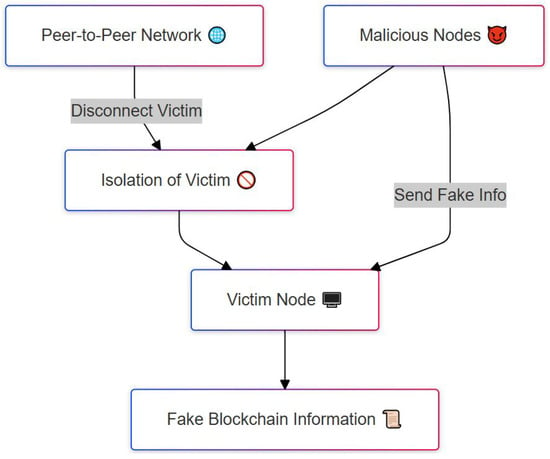
Figure 3.
Eclipse attack isolating a victim node and feeding it false blockchain data.
4.2.3. DDoS Attack
Distributed denial of service (DDoS) attacks [18,29,31,32,42] target the availability of blockchain systems by overwhelming network resources. In these attacks, an adversary leverages a network of compromised devices (a botnet) to flood the network with an excessive number of requests. This flood exhausts processing power and bandwidth, rendering the system unable to service legitimate traffic. High-profile incidents, such as those experienced by Bitfinex in 2017 and 2020, demonstrate the disruptive potential of DDoS attacks. Effective countermeasures include traffic filtering, rate limiting, and enhancements in network resilience and scalability to manage sudden spikes in traffic.
4.2.4. BGP Hijacking Attack
BGP hijacking attacks [18,30,42] exploit vulnerabilities in the border gateway protocol (BGP) to manipulate network-level traffic. In such an attack, an adversary alters the routing information so that network traffic is rerouted through malicious channels. This can delay the propagation of messages, adversely affecting mining operations, or even enable the theft of cryptocurrency. To mitigate BGP hijacking, network operators can implement BGP monitoring, route origin validation, and encrypted communication channels to safeguard routing information.
4.2.5. Routing Attack
Routing attacks [29,42] can occur in two primary forms: network partitioning and message delay. In a partitioning attack, adversaries split the network into disjoint segments, which may lead to the creation of parallel blockchains. Once the attack ceases, the smaller chain is typically discarded, resulting in significant loss of mining power and revenue. In delay attacks, adversaries tamper with the propagation of messages, causing blocks to reach victim nodes later than expected. This delay can facilitate double-spending or lead to wasted mining resources. Due to their stealthy nature, these attacks are challenging to detect. Preventative measures include using secure communication protocols and network segmentation to minimize the risk of such routing attacks.
4.2.6. DNS Attack
DNS attacks [18] target the domain name system (DNS) to compromise blockchain nodes, particularly new ones. In this scenario, an adversary manipulates the DNS cache by injecting false node information. As a result, a new node, during its bootstrapping process, may connect to a malicious set of peers instead of legitimate nodes. This false neighborhood can be exploited to manipulate transactions or the consensus process. Common defenses against DNS attacks include secure bootstrapping mechanisms, periodic DNS cache flushing, and robust peer verification protocols to ensure that connections are only established with trusted nodes.
4.3. Consensus and Incentive Layer
The consensus and incentive layer is crucial for maintaining the integrity and security of blockchain systems. It not only governs how transactions are agreed upon and appended to the ledger but also ensures that miners and validators are appropriately rewarded. However, this layer is vulnerable to several sophisticated attacks that exploit the incentives and consensus mechanisms. In the following subsections, we describe a range of attacks targeting this layer, explain their mechanisms, and discuss potential countermeasures.
4.3.1. 51% Majority Attacks
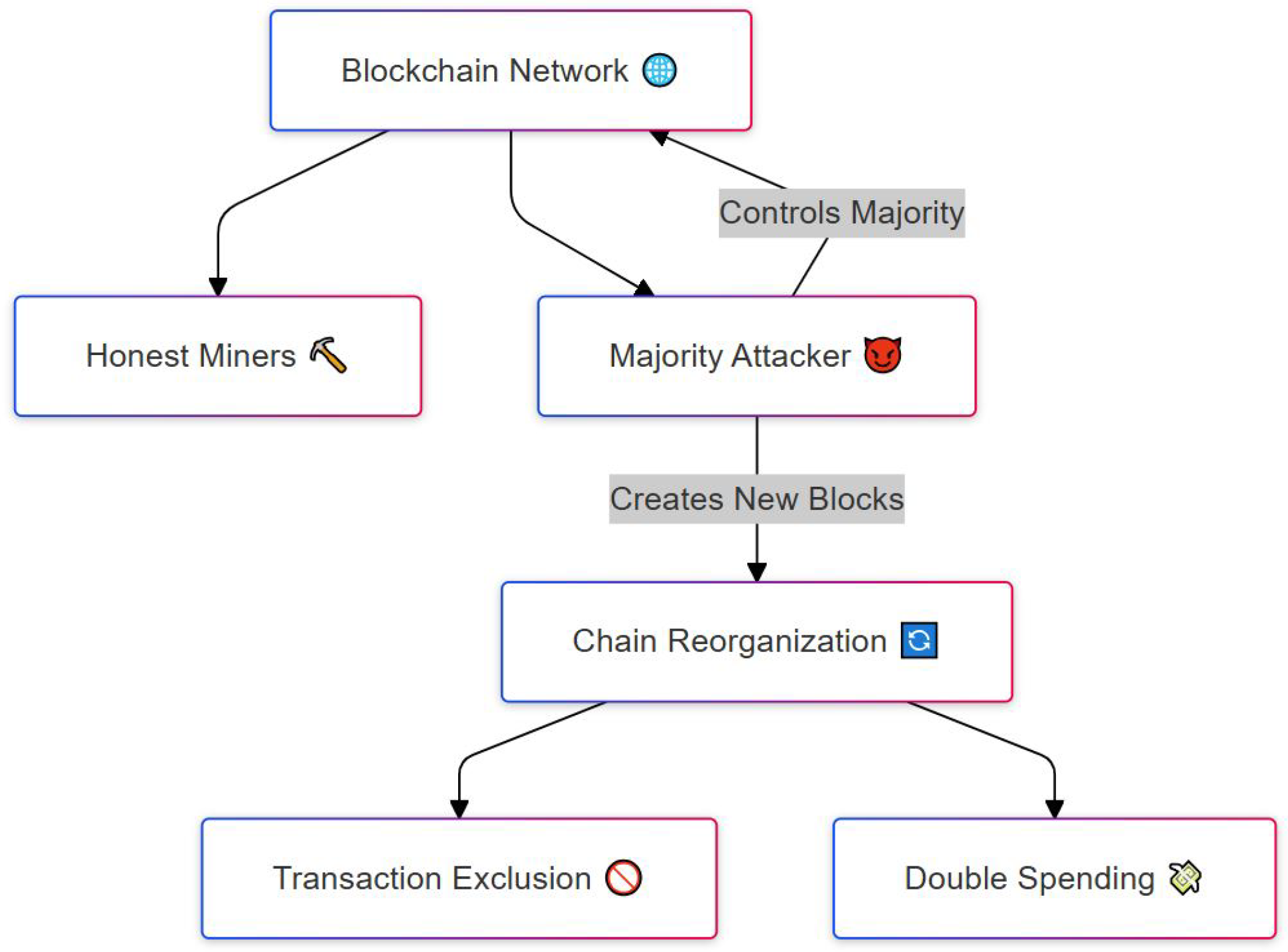
In a 51% majority attack [18,27,29,32,42,45], an adversary gains control of more than half of the network’s mining power. With this majority control, the attacker can determine which transactions are included in new blocks and which are excluded. This control enables the adversary to reverse previously confirmed transactions (facilitating double-spending) or prevent other miners from validating transactions and creating new blocks, effectively halting network operations.
Figure 4 depicts the sequence of actions in a 51% attack, also known as a majority attack, which occurs when a single entity or group gains control of more than half of the total computational power in a blockchain network. The diagram starts at the top with the blockchain network, which typically consists of many participants, including honest miners who follow the rules. However, if a majority attacker (shown on the right) gains control of over 50% of the mining power, they can create new blocks faster than the honest miners. This allows them to initiate a chain reorganization, replacing the legitimate blockchain history with their own version. As shown in the lower part of the diagram, this manipulation can lead to serious consequences: the attacker can exclude certain transactions from being recorded (left path) or perform double spending (right path), where the same cryptocurrency is spent multiple times. The image highlights how control over block creation enables manipulation of the ledger, undermining the core trust model of blockchain. A notable real-world example is the Ethereum Classic (ETC) attack in August 2020, where approximately $5.6 million worth of ETC was double-spent during a chain reorganization event. To mitigate such attacks, increasing the overall network hash rate makes it more difficult for an adversary to accumulate the required mining power. Improvements in consensus algorithms and continuous network monitoring also serve as effective countermeasures.
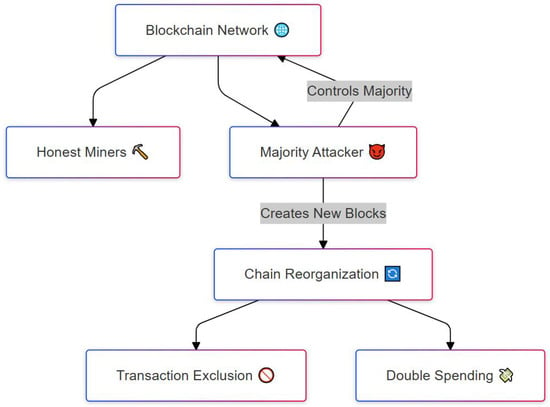
Figure 4.
Attack where the attacker controls 51% of mining power, manipulating transactions.
4.3.2. Replay Attacks
Replay attacks [28,31,32,46] primarily occur during hard forks, when the blockchain splits into two distinct versions, one following the older protocol and the other adopting the upgraded protocol. In this scenario, a transaction that was valid before the fork remains valid on both chains. A malicious attacker can exploit this situation by broadcasting a pre-fork transaction on both chains, effectively causing the same funds to be transferred to the attacker’s wallet on one chain while duplicating the transaction effect. Although hard forks are relatively infrequent, the potential financial losses resulting from replay attacks can be substantial.
To mitigate these risks, several countermeasures have been proposed. For example, transactions can be marked so that they are only valid on one specific chain; timestamps can be incorporated to prevent the reuse of transactions; and session keys can be employed to add an additional layer of security.
4.3.3. Race Attack
A race attack [27,29,31,42] exploits the time gap between the initiation of a transaction and its subsequent confirmation. In this attack, an adversary creates two transactions using the same funds: one legitimate and one fraudulent. The attacker leverages the delay in network confirmation so that if the fraudulent transaction is confirmed before the valid one, the attacker effectively spends the same funds twice. Initially, the valid transaction is broadcast to build trust within the target network, but the attacker later exploits this trust by rapidly broadcasting the conflicting transaction.
To mitigate race attacks, it is crucial to enforce a sufficient waiting period for transaction confirmations. Additionally, robust consensus mechanisms—such as Proof of Work or Proof of Stake—can further reduce the risk by ensuring the integrity of the ledger.
4.3.4. Finney Attack
A Finney attack [27,28,29,31,42] is a variant of the race attack that requires the attacker to control significant mining power. In this scenario, the attacker pre-mines a block containing a double-spending transaction but withholds the block from immediate broadcast. Instead, the attacker first uses the funds from the unbroadcast transaction to make a purchase from a merchant. After the goods or services have been received, the attacker then releases the pre-mined block, which includes the conflicting transaction, thereby effectively reversing the original payment. This method not only relies on network propagation delays but also on the attacker’s ability to manipulate block creation and confirmation timing. As with race attacks, increasing the waiting time for multiple confirmations before finalizing transactions can help mitigate the risk of Finney attacks.
4.3.5. Time Jacking
In a time jacking attack [28,29,31], an adversary manipulates the perceived network time of a target node. This is typically achieved by having the target node connect to multiple malicious peers that intentionally report falsified timestamps. As a consequence, the target node adopts these inaccurate timestamps, which then influence its block validation process. When the node’s internal clock is skewed, it may reject otherwise valid new blocks that appear to have timestamps outside a predetermined acceptable range, thereby disrupting the consensus mechanism.
To mitigate time jacking attacks, several countermeasures can be implemented. These include using the node’s system time as a trusted reference or enforcing strict limits on the acceptable deviation of incoming timestamps. In addition, securing time synchronization through network encryption, randomizing peer connections to reduce prolonged exposure to malicious nodes, increasing the diversity of the peer network, and monitoring round-trip times for anomalies can collectively enhance resilience against such attacks.
4.3.6. Vector 76 Attack
In the Vector 76 attack [27,31,42], an adversary exploits a double-spending opportunity using two separate nodes. One node connects to the service (e.g., an E-Wallet), while the other is connected to the broader blockchain network. The attacker initiates two transactions—one with a high value and another with a low value. The high-value transaction is directed to the service node to create a false impression of a substantial deposit. Meanwhile, the attacker continues mining until a target transaction is detected and confirmed on the blockchain. At that moment, the attacker withdraws the high-value amount from the service node while broadcasting the low-value transaction to the network. As a result, the network accepts the low-value transaction, invalidating the high-value one. To mitigate this attack, blockchain networks can reduce transaction confirmation times, adopt consensus mechanisms less susceptible to this attack (e.g., Proof of Stake), and enforce stricter mempool validation rules to prevent unauthorized transactions from entering the system.
4.3.7. Selfish Mining
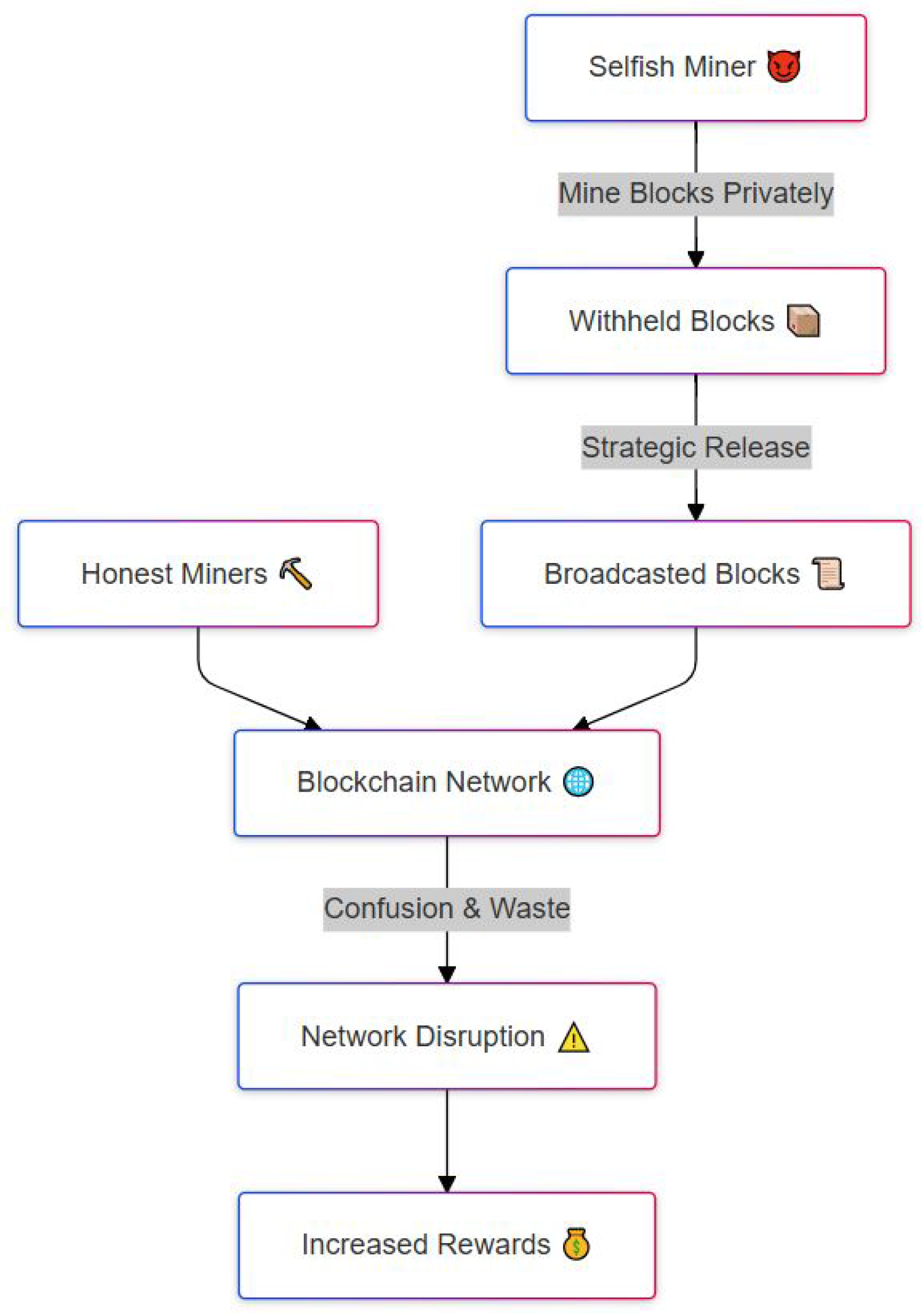
Selfish mining [27,30,32,42] occurs when an adversarial miner withholds mined blocks from the public network. Instead of immediately broadcasting a newly mined block, the selfish miner keeps it private, extending a private chain. The attacker’s goal is to strategically release the withheld blocks to force honest miners to work on an outdated chain. This causes regular miners to waste their computational resources, while the selfish miner reaps disproportionate rewards.
Figure 5 illustrates the workflow of a selfish mining attack, a strategy where a malicious miner manipulates the block publication process to gain more rewards than they would fairly earn. The attack begins with a selfish miner (top box) who chooses to mine blocks privately instead of immediately broadcasting them to the network. These withheld blocks are kept secret, giving the selfish miner a temporary lead over honest miners, who are unaware of the hidden progress. At a carefully chosen moment, the attacker strategically releases the withheld blocks, shown as broadcasted blocks, to the blockchain network.
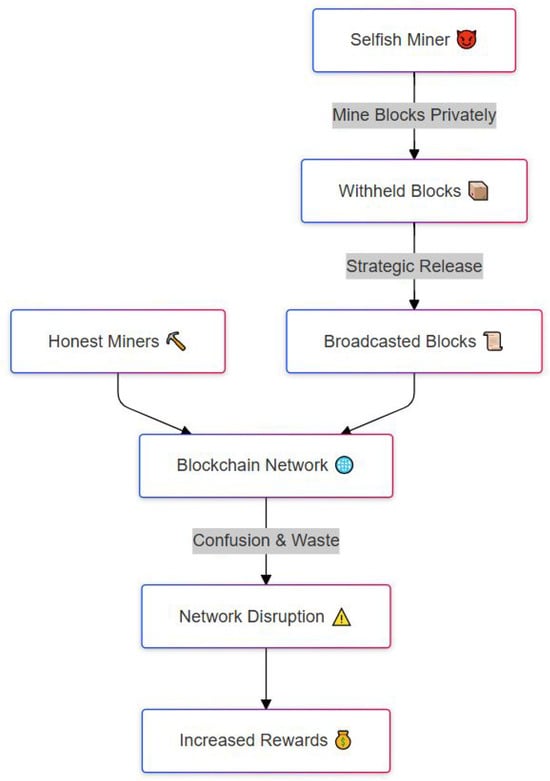
Figure 5.
Selfish mining attack where a miner withholds blocks to waste resources and gain additional rewards.
At this point, the blockchain network, now receiving conflicting information from both honest and selfish miners, experiences confusion and waste. Honest miners may have unknowingly mined on a shorter chain, causing their work to be discarded when the longer withheld chain is revealed. This results in network disruption (shown with a warning symbol), which ultimately benefits the selfish miner. By manipulating the timing of block releases, the attacker can force honest miners to waste computational resources and thereby secure increased rewards for themselves, gaining an unfair advantage without necessarily controlling the majority of the network’s hash power.
4.3.8. Block-Withholding Attack (BWH)
Block withholding is a variant of selfish mining [27,29] where an attacker intentionally withholds valid blocks from the network. In this attack, a miner who discovers a valid block refrains from broadcasting it, instead keeping it secret to gain a competitive advantage. By continuing to mine privately, the attacker can eventually force other miners to work on an outdated or incomplete blockchain, which leads to an increase in stale (or orphaned) blocks. This behavior not only disrupts the fair reward distribution among miners but also threatens the overall decentralization of the network. To counteract block withholding attacks, blockchain systems can implement protocols that incentivize timely block propagation and penalize miners who exhibit selfish behavior.
4.3.9. Bribery Attack
Bribery attacks [29] involves an adversary attempting to influence the blockchain by manipulating transaction confirmations. In this scenario, the attacker first creates a legitimate transaction that becomes confirmed after a certain number of confirmations, ensuring it is irreversible. Then, the attacker initiates a conflicting fraudulent transaction and constructs a new, fraudulent block. By bribing or renting a significant portion of the network’s mining power, the attacker extends the fraudulent branch until it becomes longer than the legitimate one. Once the fraudulent chain overtakes the original, the conflicting transaction becomes valid, effectively reversing the original transaction. Preventing bribery attacks is challenging, as they often involve ethical and governance considerations. However, enhancing decentralization and ensuring that decision-making is distributed can reduce the influence of any single participant.
4.4. Contract Layer
The contract layer is where smart contracts reside and execute on blockchain platforms, such as Ethereum. These self-executing programs manage digital assets, enforce agreements, and facilitate transactions without intermediaries. However, vulnerabilities in smart contracts can be exploited by attackers to disrupt contract behavior, steal funds, or manipulate contract state. In the following subsections, we discuss common contract layer attacks, their mechanisms, and potential countermeasures.
4.4.1. Re-Entrancy Attack
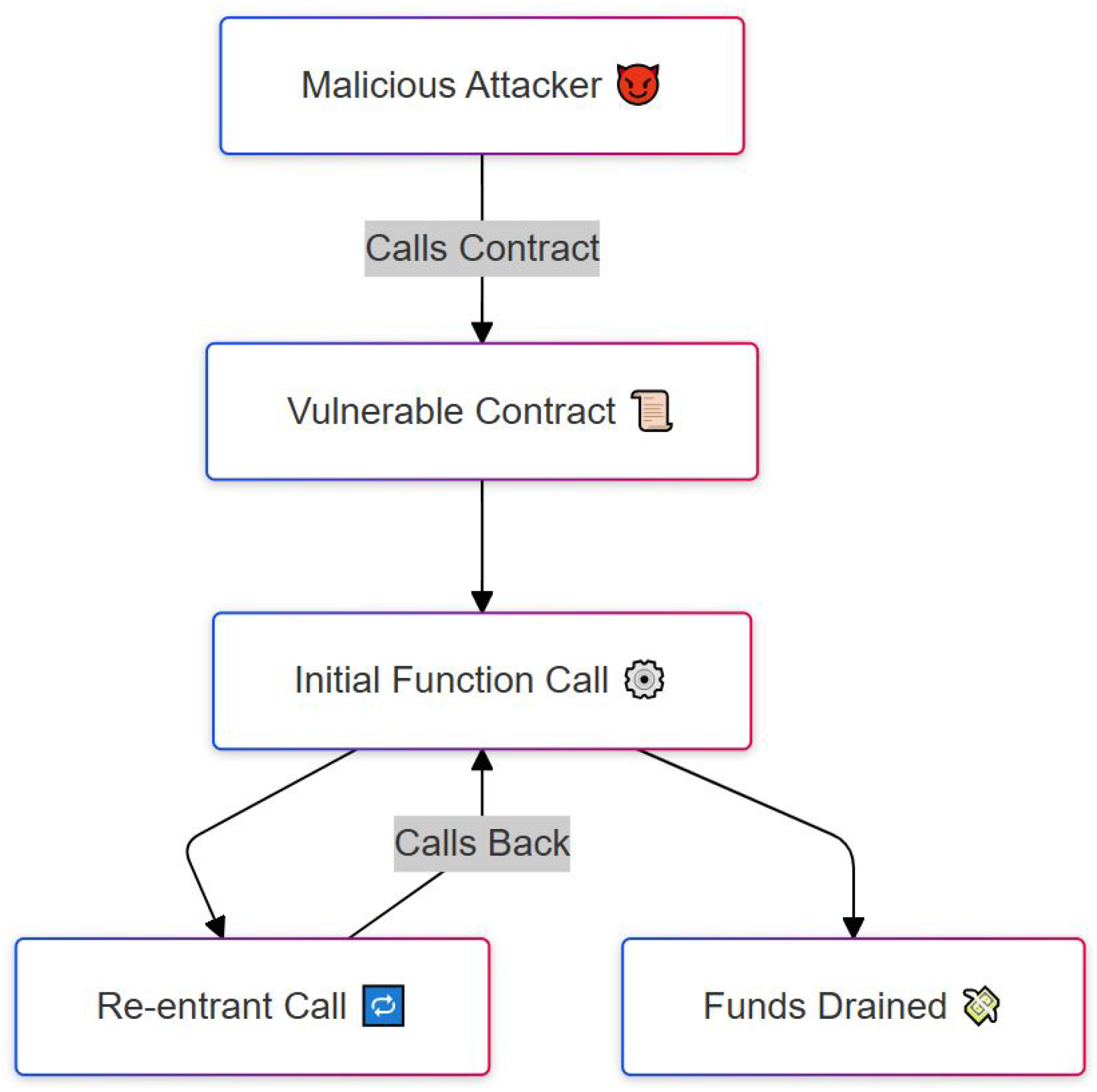
A re-entrancy attack [18,30,42,47] occurs when a smart contract’s function is called recursively before the initial invocation completes its execution. In this scenario, an attacker repeatedly calls a vulnerable function, manipulating the contract’s state and draining funds before the original transaction has been finalized. The primary impact of a re-entrancy attack is the unauthorized withdrawal of funds or assets stored within the contract, along with unintended modifications to critical contract parameters.
Figure 6 visually illustrates the sequence of actions in a re-entrancy attack, using a step-by-step flow. It begins with a malicious attacker (top box) who initiates the process by calling a vulnerable smart contract. This contract contains a flaw: it does not update its internal state (such as the user’s balance) before sending out funds. Once the initial function call is triggered (center of the diagram), the contract sends funds to the attacker’s external address or contract. However, instead of completing the transaction, the attacker’s contract calls back into the vulnerable contract before it finishes execution. This triggers a re-entrant call, shown on the left branch, which reactivates the same withdrawal logic repeatedly. Since the contract has not yet marked the initial transaction as complete, it continues to send funds, resulting in funds being drained, as shown on the right side of the flow. The image clearly shows how the recursive loop is formed and how control flow returns to the vulnerable contract multiple times, emphasizing the core vulnerability. This attack exploits the contract’s failure to follow safe design patterns, such as updating state before making external calls.
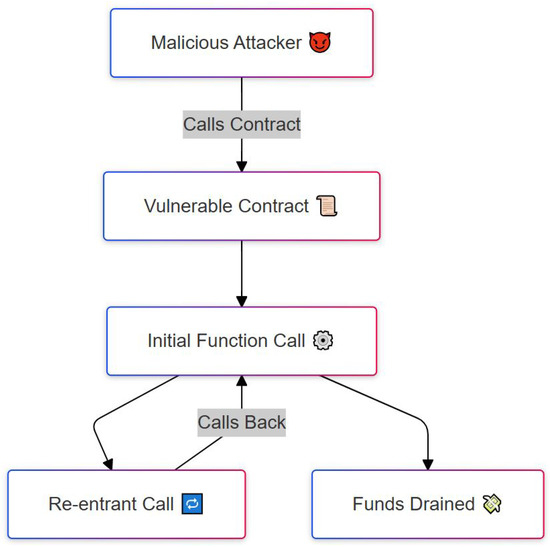
Figure 6.
Re-entrancy attack where a contract is repeatedly called to drain funds.
4.4.2. Overflow Attacks
Overflow attacks exploit arithmetic vulnerabilities in smart contracts [28,48]. These occur when a variable exceeds its maximum or falls below its minimum value, causing it to “wrap around”. For example, a 32-bit integer can only represent values from −2,147,483,648 to 2,147,483,647. In a smart contract for online betting, if a user sends an amount that exceeds this limit, the resulting value may wrap around to 0, leading to unexpected behavior. A notable case of an overflow attack occurred in 2018 on the Beauty Chain smart contract, where an attacker exploited this vulnerability to bypass verification checks and withdraw tokens exceeding the contract balance [49]. Employing safe arithmetic libraries and adhering to secure programming practices in Solidity can help prevent such attacks.
4.4.3. Short Address Attacks
Short address attacks [28,48] target vulnerabilities in Ethereum’s virtual machine, particularly affecting ERC20 tokens. In this attack, an adversary creates an Ethereum wallet with an address ending in zeroes and then manipulates the address by removing the trailing zeroes during a transaction. If the contract does not verify the sender’s address length correctly, the Ethereum Virtual Machine (EVM) automatically pads the address with missing zeroes. This discrepancy can lead to incorrect token transfers. For instance, an attacker might exploit this flaw such that for every 1000 tokens purchased, the contract erroneously credits 256,000 tokens. Ensuring strict input validation and address length verification can mitigate this risk.
4.4.4. Balance Attack
The balance attack [29] targets PoW-based blockchains by disrupting communication between subgroups of miners with similar mining power. In this attack, an adversary introduces delays between these subgroups—one subgroup (the transaction subgroup) processes transactions, while the attacker mines blocks in another subgroup (the block subgroup). By strategically delaying communication, the attacker ensures that the block subgroup’s chain becomes longer than the transaction subgroup’s chain. Consequently, even if a transaction is committed, the attacker can override or remove the block containing that transaction. The balance attack highlights that PoW-based blockchains may be “block oblivious”, where there is always a probability that an adversary can override a transaction-containing block. Implementing protocols that enhance communication and synchronization among mining nodes can help reduce the likelihood of such attacks.
4.5. Application Layer
The application layer represents the interface through which users interact with blockchain systems. This layer comprises software applications, wallets, and services that manage digital assets and facilitate transactions. Due to its direct interaction with end users, the application layer is a prime target for various attacks. In the following subsections, we outline common attacks on both cold and hot wallets, as well as other application-level threats, and discuss potential countermeasures.
4.5.1. Cryptojacking
Cryptojacking [28,31] is an attack targeting web and cloud-based services to illicitly perform Proof of Work (PoW) calculations for cryptocurrency mining without the user’s consent. The most prevalent form of cryptojacking today is in-browser cryptojacking, where compromised websites turn visitors’ devices into mining nodes. PoW requires intensive computational resources to solve complex mathematical problems. As the overall network hash rate increases, the mining difficulty also rises, leading to the use of specialized hardware such as GPUs and ASICs in professional mining operations. Cryptojacking can burden unsuspecting users by draining device resources and increasing energy consumption. To combat cryptojacking, it is essential to implement robust security measures on web platforms, such as script blocking, frequent security audits, and user awareness programs regarding unauthorized mining activities.
4.5.2. Attacks on Cold Wallets
Cold wallets, also known as blockchain hardware wallets [27,31], store private keys offline and are generally considered more secure than their online counterparts. However, these wallets can still be compromised through sophisticated methods such as bug implantation. For example, an Evil Maid attack involves an adversary physically accessing a device and implanting malicious software that extracts private keys, PINs, recovery seeds, and passphrases from the wallet. In one notable incident in 2019, during a routine transfer of funds to a cold wallet at the UPbit cryptocurrency exchange, attackers exploited timing vulnerabilities to steal $342,000 worth of ETH. This incident highlights that even offline storage solutions can be vulnerable if physical or procedural security measures are inadequate.
4.5.3. Attacks on Hot Wallets
Hot wallets [27,31] are internet-connected applications that store private cryptographic keys. Although cryptocurrency exchanges often claim to keep user data in wallets isolated from the internet, history has shown otherwise. For instance, a $500 million attack on Coincheck in 2018 exposed significant vulnerabilities in hot wallet security. In June 2019, an attack on GateHub resulted in unauthorized access to dozens of native XRP wallets and the theft of various crypto assets. Similarly, the Singapore-based crypto exchange Bitrue experienced a hot wallet breach around the same period, with attackers stealing funds worth over $4.5 million in XRP and $237,500 in ADA. These incidents underscore the importance of robust security measures and constant monitoring for online wallets.
4.5.4. Dictionary Attack
A dictionary attack [50] involves an adversary systematically attempting to guess a target node’s password by trying a large number of likely possibilities. This attack becomes feasible when the target employs weak or easily guessable passwords. The effectiveness of such an attack is directly related to the randomness and strength of the hash generator used to secure the password. To mitigate dictionary attacks, it is essential to enforce strong password policies and implement multifactor authentication schemes, which add additional layers of security beyond just a password.
4.5.5. Malware Attack
Malware attacks [31] on the application layer are designed to stealthily compromise the target device and potentially its connected network. In a blockchain context, malware can hijack a device’s computational resources to perform unauthorized tasks, such as mining blocks in the background without the user’s consent. Ransomware attacks are a common variant, wherein the malware locks the target out of its own system resources until a ransom is paid. These attacks not only disrupt normal device operations but can also lead to significant financial losses if critical assets or credentials are compromised. Implementing robust anti-malware solutions and maintaining up-to-date security practices are key measures in defending against such threats.
In summary, we have examined a wide range of attacks spanning multiple layers of blockchain systems. These include network-level exploits—such as 51% majority attacks, Sybil, eclipse, DDoS, BGP hijacking, routing, and DNS attacks—as well as consensus and contract layer threats such as vector 76, selfish mining, block withholding, bribery, re-entrancy, overflow, and short address attacks. We have also discussed application-level vulnerabilities that target both cold and hot wallets. For a quick overview of these attacks, please refer to Table 2. This comprehensive analysis highlights the multifaceted security challenges inherent in blockchain technology. With a solid understanding of these attack vectors, we now shift our focus to vulnerability detection. The following section will explore state-of-the-art techniques and emerging approaches designed to identify, analyze, and mitigate these vulnerabilities, ultimately strengthening the overall security posture of blockchain systems.
5. Vulnerability Detection
In recent years, the rapid development of blockchain technologies and decentralized applications has highlighted the critical importance of smart contract security [51]. Researchers have proposed various methods to detect and mitigate vulnerabilities in smart contracts, each leveraging different techniques and addressing unique challenges. To systematically address these security concerns, we have conducted a comprehensive review and developed a structured taxonomy that categorizes existing literature into clearly defined methodological clusters.
5.1. A Systematic Taxonomy of Vulnerability Detection
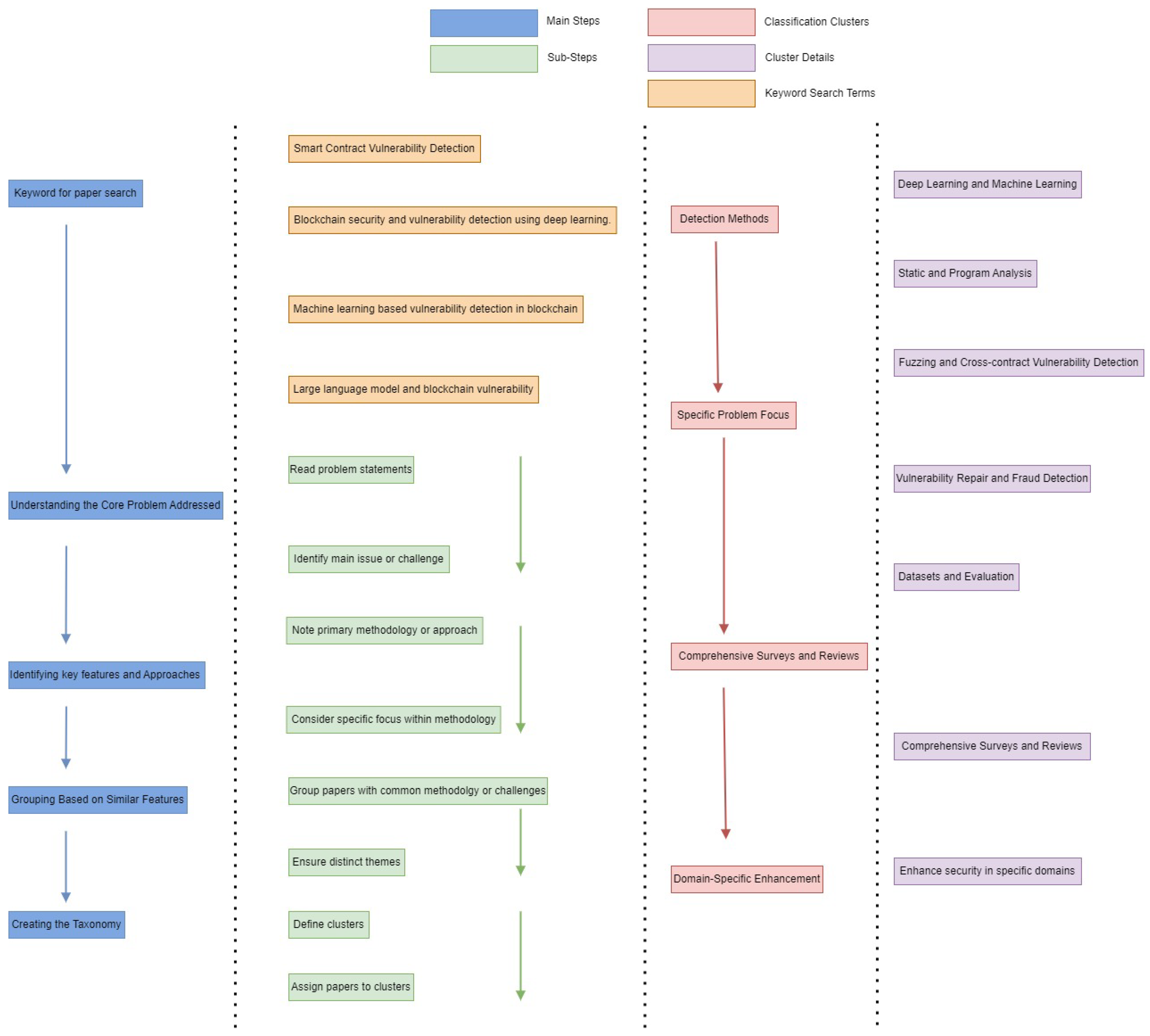
Our taxonomy provides a coherent framework, allowing a nuanced comparison of methods and identification of gaps in current research. In Figure 7, we present a systematic taxonomy that classifies research papers focused on blockchain vulnerability detection. This taxonomy was developed through a structured process that involved several key steps, ensuring a comprehensive and accurate categorization of the state-of-the-art literature in this field.
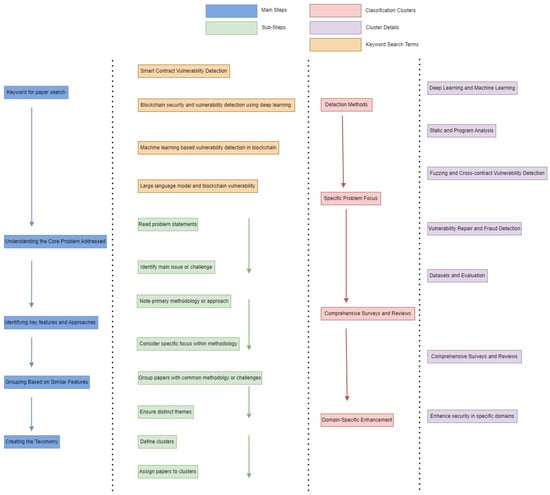
Figure 7.
Systematic taxonomy creation for blockchain vulnerability detection research papers.
The classification emerged from a rigorous, multi-step analytical process.
Paper Identification: Initially we performed comprehensive keyword searches in academic databases to gather relevant state-of-the art literature. This step ensured that all significant and recent contributions were included.
Understanding the Core Problem: Each identified paper was critically examined to identify its primary research problem. This involved recognizing whether the focus was on specific vulnerabilities, novel detection methodologies, or particular domains within blockchain security.
Identifying Key Features and Approaches: In this step, we extracted the methodologies and techniques used by the papers. Key methodologies such as deep learning, static analysis, fuzzing, or hybrid approaches were extracted. This allowed us to map techniques clearly to identified vulnerabilities and research problems.
Grouping Based on Similar Features: Papers were then grouped together based on shared characteristics and approaches. This clustering process ensured that each category represented a distinct theme or focus. This facilitated a detailed comprehensive analysis.
Formalizing the Taxonomy: Clusters were systematically organized into a coherent taxonomy, clearly delineating methodological boundaries and ensuring each paper was categorized based on its primary contributions.This organization reflects the common themes and features identified in the previous steps.
KeyAspects of the Taxonomy
The taxonomy is organized around several key aspects, which provide insights into current research trends and help identify potential gaps.
1. Detection Methods:
Deep Learning and Machine Learning: Papers using neural networks, graph neural networks, attention models, or other machine learning techniques for vulnerability detection.
Static Program Analysis: Research focusing on static code analysis, program analysis, and formal methods to identify vulnerabilities in smart contracts and blockchain applications.
Fuzzing: Studies that utilize fuzz testing techniques to uncover vulnerabilities by inputting random data into blockchain systems.
2. Specific Problem Focus:
Vulnerability Repair and Fraud Detection: Research dedicated to the automated repair of detected vulnerabilities and the identification of fraudulent transactions within blockchain networks.
Datasets and Evaluation: Papers that create or leverage large datasets for evaluating the performance and robustness of smart contract analysis techniques.
3. Comprehensive Surveys and Reviews: These works provide broad overviews of the field, classifying existing tools and methodologies while outlining future research directions in blockchain vulnerability detection.
4. Domain-Specific Enhancements: This category includes research focused on enhancing security in specific domains, such as the Internet of Things (IoT) or blockchain consensus mechanisms, to address unique challenges in those areas.
In summary, this taxonomy not only clarifies the landscape of blockchain vulnerability detection research but also offers guidance for future studies by highlighting current trends and identifying areas that require further exploration. As illustrated in Figure 7, the classification provides a structured framework that can help researchers select suitable techniques and address potential gaps in the literature.
5.2. Detailed Comparative Analysis on Vulnerability Detection Methods
Blockchain vulnerability detection is a diverse research area in which various methodologies are employed to address different aspects of blockchain security. Our proposed taxonomy enables us to identify papers in distinct clusters, thereby providing a detailed comparative analysis. In Table 4, we summarize the strengths and weaknesses of the different categories of vulnerability detection techniques.

Table 4.
Taxonomy of blockchain vulnerability detection and analysis approaches.
5.2.1. Machine Learning and Deep Learning Approaches
This cluster has shown remarkable promise due to its ability to recognize complex vulnerability patterns beyond conventional analysis. Techniques involving attention mechanisms [105,106] and transfer learning allow models to focus on the most relevant parts of the code, increasing detection accuracy. Approaches such as those presented in [54] transform contract bytecode or abstract syntax trees into graphs, using graph neural networks (GNNs) to identify structural patterns indicative of vulnerabilities. Studies such as [55,64] incorporate attention layers (e.g., self-attention, dual-attention) to highlight critical code fragments—often referred to as “hotspots”—where bugs are more likely. Moreover, frameworks such as [67,68,69] leverage distributed machine learning to detect new (zero-day) vulnerabilities while safeguarding sensitive code and data. Transfer learning further addresses the data scarcity problem by reusing feature representations learned from large code corpora. Hybrid approaches, such as combining CNNs with RNNs or merging symbolic execution with deep learning, have shown promise in balancing interpretability with accuracy.
Issues in the Existing Approaches
Despite these advances, the computational intensity and complexity of these models remain significant challenges for large-scale practical deployment. In addition, ensuring high-quality, representative training data is essential, and strategies for enhanced data collection, pre-processing, and augmentation are needed. Moving beyond simplistic binary classification to more nuanced detection strategies can further improve detection accuracy.
5.2.2. Static and Program Analysis-Based Methods
Static analysis and program analysis-based methods play a crucial role in reducing false positives and reliably detecting vulnerabilities. Tools such as SmartCheck [75] and SafeCheck [70] apply rule-based analysis to Solidity code, effectively detecting known anti-patterns such as re-entrancy and integer overflow. Other approaches, including RA [74] and SmartFast [78], introduce specialized symbolic execution engines tailored to uncover logic bugs in Ethereum bytecode. Formal verification methods [73,76] use rigorous mathematical proofs, such as model checking, to guarantee the absence of certain classes of bugs.
Issues in the Existing Approaches
While these methods are cost-effective and efficient in detecting vulnerabilities, their implementation complexity, resource requirements, and need for expert configuration can limit their accessibility. Balancing cost and performance, simplifying the implementation process, and reducing dependency on specific tools can improve the overall usability of these methods.
5.2.3. Fuzzing and Cross-Contract Methods
Fuzzing techniques have emerged as effective means of improving code coverage and vulnerability detection in smart contracts. Intelligent guidance and prioritization—as demonstrated by LLM4Fuzz [88]—along with approaches such as CrossFuzz [87] have proven effective in exploring multiple execution paths to identify vulnerabilities. EvoFuzzer [80] employs evolutionary algorithms to generate inputs more intelligently.
Issues in the Existing Approaches
Although these methods enhance detection capabilities, they are often resource intensive and complex to implement. Their success depends heavily on fine-tuning, the use of multiple large language models (LLMs) for consensus, and expert configuration. Scalability and adaptability remain challenging for the widespread adoption of fuzzing techniques.
5.2.4. Vulnerability Repair and Fraud Detection
A key finding in vulnerability repair and fraud detection research is the importance of achieving high precision and recall. Approaches such as bytecode-based repair [82] focus on patching re-entrancy vulnerabilities at the Ethereum Virtual Machine (EVM) level, thereby bypassing the need for source code modifications. Fraud detection methods [85,86] leverage heuristic or machine learning-based classification to identify suspicious transactions, thus mitigating financial risks in decentralized applications (DApps). Tools such as sGuard+ [83] automatically repair vulnerable contracts by modifying them to fix known logic errors (e.g., integer overflows) before redeployment. The scalability of these methods is a significant advantage, particularly in diverse smart contract environments, though their dependency on specific models emphasizes the need for continuous improvement and adaptation.
5.2.5. Datasets and Evaluation-Based Methods
Datasets and evaluation-based methods provide detailed, comprehensive insights into vulnerabilities. For instance, DAppSCAN [89] plays a crucial role in improving our understanding of smart contract weaknesses. Fine-grained vulnerability detection techniques [90] maintain granular labels (e.g., re-entrancy, integer overflow) for each function or code block, thereby enhancing training and evaluation processes. Tools such as Oyente and Mythril [73,92] have contributed partial datasets for benchmarking new solutions, while SmartFast [78] and ReDefender [94] offer curated test cases focusing on common vulnerabilities. Despite these advances, there remains a need for continuous updating and expansion of vulnerability databases, such as the SWC Registry [107], to ensure comprehensive vulnerability coverage.
5.2.6. Comprehensive Surveys and Domain-Specific Enhancements
Numerous surveys synthesize existing research, highlight trends, and suggest promising directions. For example, works such as [77,79,93] provide broad overviews of blockchain vulnerabilities, ranging from protocol-level to DApp-level weaknesses. Other studies [63,98] focus on the evolution of analysis tools and the rise of deep learning in detection. Additional surveys [81,95,96] concentrate on Ethereum-specific issues, while others [65,68,99] highlight modern challenges such as zero-day vulnerabilities and advanced ML approaches. The consensus emerging from these surveys is that no single method can cover the extensive, evolving threat landscape; instead, hybrid strategies are necessary.
Domain-specific enhancements are also crucial. In the context of blockchain and IoT security, research [100,101] adapts ML-based intrusion detection and consensus strategies to accommodate IoT constraints, such as limited computational power. Similarly, automotive security research [103] addresses vulnerabilities in automotive blockchain networks, focusing on real-time and safety-critical requirements. Other works [64,69,104] propose domain-focused modifications to block structure, consensus, or communication patterns, aiming to balance security and efficiency. Future research should focus on optimizing these approaches to minimize resource consumption without compromising security, and on developing robust data collection and preprocessing techniques to ensure high-quality training data.
5.2.7. Key Insights from the Vulnerability Detection Taxonomy
Through comprehensive analysis, several key insights emerge regarding vulnerability detection and security within blockchain environments.
- Hybrid Approaches Enhance Security: No single approach—whether based on machine learning, static analysis, or fuzzing—can fully cover the vast and evolving threat landscape in blockchain environments. Hybrid strategies, such as combining symbolic execution with deep neural networks [57] or using static analysis to identify suspicious points before applying fuzzing, are emerging as best practices. The integration of multiple methods—including formal verification for critical invariants, deep learning for dynamic anomaly detection, and fuzzing for real-world scenario testing—provides a more robust defense against malicious actors.
- Adaptability and Machine Learning: Machine learning provides the flexibility and adaptability necessary for real-time anomaly detection and novel vulnerability identification, complementing traditional security measures. Its capability for advanced pattern recognition makes it highly effective against evolving threats.
- Persistent Challenges Require Attention: Several challenges persist, demanding ongoing research and community collaboration: (1) Scalability and Efficiency: Techniques must effectively handle large-scale contracts and cross-chain interactions without incurring excessive overhead. (2) Data Quality and Benchmarking: High-quality, standardized datasets and consensus-driven benchmarks are critical for developing and evaluating reliable security tools. (3) Interpretability and Transparency: Tools must provide clear, understandable explanations suitable for end-users, auditors, and regulatory compliance. (4) Future-Proofing Against Evolving Threats: Solutions must continually evolve to counter emerging threats, including quantum-based vulnerabilities and sophisticated MEV exploits.
- Community-Driven Collaboration is Essential: Successfully addressing blockchain vulnerabilities demands collaboration across disciplines such as software engineering, cryptography, artificial intelligence, and other specialized fields. A multidisciplinary approach is essential to keep blockchain systems innovative and secure.
Collectively, these insights underline the necessity for an integrated, dynamic approach that leverages the strengths of various methods to provide comprehensive and adaptive security solutions. Ultimately, ongoing innovation, proactive collaboration, and a commitment to addressing emerging challenges will ensure the resilience and continued evolution of secure blockchain technologies.
Having thoroughly analyzed the diverse approaches to vulnerability detection, it is clear that traditional methods alone cannot fully address the rapidly evolving threat landscape in blockchain environments. In this context, machine learning (ML) emerges as a powerful tool with the potential to complement and enhance existing security techniques. ML approaches not only improve detection accuracy through advanced pattern recognition and anomaly detection but also offer the adaptability needed to identify novel vulnerabilities in real time. As we transition to the next Section 6, we will explore how ML is being leveraged to fortify blockchain systems, examine its integration with conventional methods, and discuss the unique challenges and opportunities it presents in maintaining robust blockchain security.
6. ML and the Security of Blockchain
The growing adoption of blockchain technology across various sectors has underscored the need to address security concerns inherent in decentralized systems. Although the core characteristics of blockchain—decentralization, immutability, and transparency—provide a strong foundation for secure transactions, vulnerabilities persist that can be exploited by adversaries. In response, machine learning (ML) approaches have emerged as a promising solution to strengthen blockchain security. ML-based techniques are now employed to detect and mitigate attacks, improve system performance, and enhance the overall integrity of blockchain networks.
6.1. Anomaly Detection and Intrusion Prevention
One of the primary applications of ML in blockchain security is anomaly detection. Given the decentralized nature of blockchain, detecting malicious behavior or anomalies can be particularly challenging. Supervised ML models, such as decision trees, random forests, and support vector machines (SVMs), can be trained to detect abnormal activities on the blockchain network. These anomalies may include fraudulent transactions, irregular mining patterns, or unusual block generation times, which could signal attempts at double-spending or other forms of fraud [108].
In addition to supervised techniques, unsupervised learning methods, such as clustering algorithms, can learn normal behavior patterns and subsequently flag deviations. These approaches are particularly useful for detecting novel attacks that have not been previously encountered [109,110]. Together, these ML models help bolster blockchain security by providing real-time intrusion prevention and early warning systems.
6.2. Smart Contract Security
Smart contracts are self-executing agreements whose terms are directly embedded in code. Despite their power in automating transactions, they are vulnerable to a range of security issues, including re-entrancy attacks, integer overflows, and faulty logic. ML techniques—particularly deep learning and natural language processing (NLP)—have increasingly been used to detect such vulnerabilities before contracts are deployed.
For instance, deep learning models can be trained on large datasets of known smart contract vulnerabilities to classify and identify problematic code. NLP techniques, on the other hand, analyze the semantic structure of the contract source code to detect patterns indicative of security flaws. As reported in [111], bidirectional encoder representations from transformers (BERT) is leveraged to capture semantic features from smart contract opcodes. When combined with a bidirectional LSTM (BiLSTM), the model effectively handles long-term dependencies in the contract code, while an attention mechanism prioritizes critical segments. These innovations enable blockchain developers to automate vulnerability detection and reduce the risk of deploying insecure contracts.
6.3. Consensus Mechanism Enhancement
ML techniques are also applied to enhance blockchain consensus mechanisms. For example, ML models can analyze mining patterns and participant behavior to predict potential 51% attacks. Reinforcement learning has been used to develop adaptive consensus mechanisms that dynamically adjust based on real-time network conditions. This adaptability is crucial in networks utilizing Proof of Work (PoW) or Proof of Stake (PoS), where miners or validators might be incentivized to act maliciously. By integrating ML, consensus algorithms can mitigate risks such as centralization and enhance overall network resilience.
6.4. Sybil Attack Mitigation
Sybil attacks, which involve the creation of multiple fake identities to gain undue influence over a network, can also be countered using ML techniques. Graph-based ML algorithms, such as graph neural networks (GNNs), are effective in analyzing peer-to-peer relationships within the network. These algorithms can detect anomalous patterns indicative of clusters of fake or suspicious nodes [109]. By classifying nodes based on behavior and contribution, ML models can help prevent adversaries from manipulating consensus through artificial node creation.
6.5. Quantum Attack Resistance
Although quantum attacks remain largely theoretical, ML can contribute to the development of quantum-resistant cryptographic methods. ML models can simulate quantum attack scenarios on various cryptographic algorithms, enabling researchers to identify potential vulnerabilities. These insights facilitate the development and optimization of post-quantum cryptographic techniques [112]. ML thus plays a dual role by both simulating advanced attack vectors and assisting in the design of more robust, quantum-resistant security measures.
6.6. Network Traffic Analysis
ML-based intrusion detection systems (IDS) are critical for analyzing network traffic in real time and mitigating distributed denial of service (DDoS) attacks. Unsupervised learning methods enable these systems to learn normal network behavior patterns and flag unusual traffic spikes or irregular patterns. Furthermore, reinforcement learning techniques can be applied to develop dynamic traffic-filtering mechanisms that adjust in real time, ensuring continued network availability even during DDoS attacks.
6.7. Blockchain Forensics
In the event of a security breach, ML-based forensic tools can analyze blockchain data to trace the origin and flow of malicious activities. Supervised learning algorithms can identify suspicious addresses and flag those involved in known attack patterns. These ML techniques facilitate comprehensive blockchain forensics by tracking stolen assets and mapping the methods used by attackers, thereby providing critical insights for preventing future incidents.
6.8. BlockGPT Framework
A recent breakthrough in this domain is the BlockGPT framework [113], a novel real-time anomaly detection system tailored for blockchain transactions, particularly within decentralized finance (DeFi) applications. BlockGPT utilizes a large language model (LLM) to analyze Ethereum transaction execution traces without relying on predefined patterns, making it highly adaptable to various types of attacks. Trained on a dataset of 68 million Ethereum transactions, including those involving smart contract attacks, BlockGPT captures detailed execution traces such as function calls, state changes, and event logs. This enables the framework to rank transactions by their likelihood of being abnormal, demonstrating strong performance in real-time detection with high throughput and low false-positive rates.
6.9. Adversarial Use of ML in Blockchain Security
While ML offers significant benefits for enhancing blockchain security, it also introduces new vulnerabilities. Adversaries can leverage AI and ML-based systems to execute sophisticated attacks, such as 51% attacks or Sybil attacks, at scale. For instance, research [114] discusses how AI bots may be exploited to carry out these attacks, and [115] reports that an AI bot attack resulted in a $20 million loss for Ethereum. Additionally, [116] demonstrates how large language platforms can be used to identify smart contract vulnerabilities, potentially enabling malicious actors to exploit them. Despite these challenges, the rapid advancements in ML and generative AI (GenAI) provide an opportunity to design more effective systems for early detection and prevention of adversarial attacks.
6.10. Broader Perspectives on ML in Blockchain Security
Overall, while many blockchain vulnerabilities are detectable, the primary challenge lies in the timeliness of detection to mitigate losses. AI technologies can accelerate breach detection and enhance the quality of security measures. With the emergence of generative AI and large language models (LLMs), there is significant potential for designing systems capable of real-time detection and prevention of adversarial attacks. For a broader perspective on the application of ML in blockchain security, readers are encouraged to refer to [117,118,119].
In this section, we explored the multifaceted role of machine learning (ML) in enhancing the security of blockchain systems. We began by discussing anomaly detection and intrusion prevention techniques that leverage both supervised and unsupervised ML models to identify irregular behaviors in blockchain transactions. Next, we examined how ML aids smart contract security by employing deep learning and NLP to detect vulnerabilities before deployment, followed by an analysis of ML-driven enhancements to consensus mechanisms and mitigation strategies against Sybil attacks. We also highlighted the application of ML in network traffic analysis, blockchain forensics, and innovative frameworks such as BlockGPT for real-time anomaly detection. Finally, we addressed the emerging dual role of ML, noting that while it offers powerful defenses against attacks, it also introduces new vulnerabilities that adversaries can exploit. Overall, ML technologies present both opportunities and challenges in maintaining robust blockchain security, underscoring the need for continuous research and adaptive strategies.
7. Discussion and Future Directions
This survey underscores the multifaceted nature of blockchain security, emphasizing that comprehensive security measures require structured analysis of vulnerabilities and methodological clarity in their detection. The proposed taxonomies offer practical frameworks that help blockchain practitioners, developers, and cybersecurity analysts categorize attacks systematically and design targeted mitigation strategies. Practically, this means smart contract developers can leverage existing auditing frameworks (e.g., Slither or Mythril) in alignment with the vulnerabilities identified by our taxonomy, potentially increasing the effectiveness and efficiency of vulnerability detection and mitigation processes.
More broadly, the taxonomy can serve as a foundational tool to inform real-world blockchain security policies by enabling system designers and security teams to map out threat surfaces layer by layer, assess which operational components are at risk, and define security controls that directly correspond to those architectural layers. This structured alignment between vulnerabilities and architectural responsibilities can help formalize internal audit procedures, incident response planning, and regulatory compliance strategies in both enterprise and public blockchain settings.
An important consideration is the adaptability of our taxonomies to evolving blockchain paradigms. Future iterations of our taxonomies can explicitly address emerging threats and technological advancements such as quantum computing and artificial intelligence-driven vulnerabilities. Quantum-resistant cryptographic schemes and consensus algorithms will become increasingly critical as quantum computing capabilities advance. Furthermore, as machine learning, particularly federated learning (FL), becomes more prevalent, its application to decentralized, privacy-preserving security analytics emerges as a promising research direction. Another critical avenue is the integration of zero-trust security paradigms to enable continuous authentication and verification within blockchain networks, addressing the growing sophistication of attacks.
The emergence of large language models (LLMs) also opens new possibilities for automated, sophisticated code analysis and real-time vulnerability detection. However, adversaries could leverage similar models for vulnerability identification and exploitation. This duality emphasizes the urgent need for robust, explainable, and adaptive ML-based defense mechanisms. Addressing these challenges will necessitate continued interdisciplinary collaboration among blockchain specialists, cybersecurity researchers, cryptographers, quantum computing experts, and policymakers. Such collaboration will ensure that blockchain ecosystems remain resilient against current vulnerabilities and future threats.
Lastly, although we did not perform a comparative empirical study, our layer-based framework can help identify which architectural layers may be more susceptible in specific blockchain architectures. For instance, platforms using DAG-based structures such as IOTA may face unique data-layer vulnerabilities, while PoW-based systems are more exposed to consensus-layer threats such as selfish mining. Such insights offer a strong starting point for future research into architecture-specific threat modeling.
8. Conclusions
Blockchain technology is inherently robust due to its decentralized architecture and immutable data integrity. Nonetheless, persistent security incidents highlight existing vulnerabilities and potential exploits within blockchain systems. In this work, we introduced two structured frameworks to enhance blockchain security: a layer-based taxonomy for categorizing blockchain attacks and a methodological taxonomy for blockchain vulnerability detection. The proposed layer-based taxonomy systematically categorizes vulnerabilities across blockchain layers, including the application, contract, consensus and incentive, network, and data layers facilitating precise identification of vulnerabilities and enabling targeted, layer-specific mitigation strategies. This structured approach promotes a nuanced understanding of attack vectors, revealing that vulnerabilities frequently target consensus mechanisms, network infrastructure, or smart contract logic. Effective mitigation thus requires comprehensive technical solutions, secure coding standards, robust consensus protocols, and strategic network governance practices, such as enhancing miner diversity and peer selection criteria.
The methodological taxonomy presented in this study systematically categorizes existing vulnerability detection approaches into coherent clusters: machine learning (ML) and deep learning (DL) techniques, static program analysis, fuzz testing, vulnerability repair methods, and fraud detection. By organizing existing research methodologies clearly, this taxonomy provides insights into the strengths and limitations inherent in each approach. Our analysis reveals that, while ML and DL methods generally achieve high accuracy and performance, they frequently rely on extensive, high-quality datasets and may lack explainability. Conversely, vulnerability repair and fraud detection methods show strong practical effectiveness but may exhibit inconsistent performance across various vulnerability classes.
Overall, our proposed frameworks provide clarity, structure, and actionable guidance for both academia and industry, significantly enhancing the blockchain security community’s capability to prioritize security investments and align research agendas effectively. By systematically addressing blockchain vulnerabilities, this work lays a solid foundation for future research aimed at strengthening blockchain resilience against existing and emerging threats.
Author Contributions
Conceptualization, M.H. and S.M.R.I.; methodology, M.J.I., S.I. and S.M.R.I.; validation, M.J.I., S.I. and S.M.R.I.; formal analysis, M.J.I. and S.I.; investigation, M.J.I., S.I., M.H., S.N. and S.M.R.I.; writing—original draft preparation, M.J.I., S.I. and S.M.R.I.; writing—review and editing, M.H. and S.N.; visualization, M.J.I., S.I. and S.M.R.I.; supervision, S.M.R.I.; project administration, M.J.I., S.I. and S.N.; funding acquisition, S.M.R.I. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data presented in this study is only contained in the article itself.
Conflicts of Interest
Mahmud Hossain was employed by the company Amazon Web Services (AWS). The authors declare no conflicts of interest.
References
- IBM. What Is Blockchain Security? Available online: https://www.ibm.com/topics/blockchain-security (accessed on 27 January 2024).
- Baldwin, C. Bitcoin Worth 72 Million Stolen from Bitfinex Exchange in Hong Kong. 2016. Available online: https://www.reuters.com/article/us-bitfinex-hacked-hongkong-idUSKCN10E0KP (accessed on 15 March 2024).
- Popper, N. A Hacking of More than 50 Million Dashes Hopes in the World of Virtual Currency. 2016. Available online: https://www.nytimes.com/2016/06/18/business/dealbook/hacker-may-have-removed-more-than-50-million-from-experimental-cybercurrency-project.html (accessed on 13 February 2024).
- Zhao, W. Crypto Exchange Bithumb Hacked for 13 Million in Suspected Insider Job. 2019. Available online: https://www.coindesk.com/markets/2019/03/30/crypto-exchange-bithumb-hacked-for-13-million-in-suspected-insider-job (accessed on 10 April 2025).
- Mollajafari, S.; Bechkoum, K. Blockchain technology and related security risks: Towards a seven-layer perspective and taxonomy. Sustainability 2023, 15, 13401. [Google Scholar] [CrossRef]
- Dwivedi, K.; Agrawal, A.; Bhatia, A.; Tiwari, K. A novel classification of attacks on blockchain layers: Vulnerabilities, attacks, mitigations, and research directions. arXiv 2024, arXiv:2404.18090. [Google Scholar]
- Gurjar, A.; Chandavarkar, B. Smart Contract Vulnerabilities and Detection Methods: A Survey. In Proceedings of the 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kamand, India, 24–28 June 2024; IEEE: New York, NJ, USA, 2024; pp. 1–7. [Google Scholar]
- Hejazi, N.; Lashkari, A.H. A comprehensive survey of smart contracts vulnerability detection tools: Techniques and methodologies. J. Netw. Comput. Appl. 2025, 237, 104142. [Google Scholar] [CrossRef]
- Chu, H.; Zhang, P.; Dong, H.; Xiao, Y.; Ji, S.; Li, W. A survey on smart contract vulnerabilities: Data sources, detection and repair. Inf. Softw. Technol. 2023, 159, 107221. [Google Scholar] [CrossRef]
- Rajawat, A.S.; Goyal, S.; Kumar, M.; Singh, T.P. An AI-Enabled Blockchain Algorithm: A Novel Approach to Counteract Blockchain Network Security Attacks. EAI Endorsed Trans. Internet Things 2024, 10, 1–9. [Google Scholar] [CrossRef]
- Magalhães, J. Current Vulnerabilities and Risks of Blockchain: A Systematic Literature Review. In Digital Technologies and Transformation in Business, Industry and Organizations; Springer: Cham, Switzerland, 2025; pp. 159–175. [Google Scholar]
- Verma, P.; Bharot, N.; Breslin, J.G.; O’Shea, D.; Vidyarthi, A.; Gupta, D. Zero-day guardian: A dual model enabled federated learning framework for handling zero-day attacks in 5G enabled IIoT. IEEE Trans. Consum. Electron. 2023, 70, 3856–3866. [Google Scholar] [CrossRef]
- Hallaji, E.; Razavi-Far, R.; Saif, M.; Wang, B.; Yang, Q. Decentralized federated learning: A survey on security and privacy. IEEE Trans. Big Data 2024, 10, 194–213. [Google Scholar] [CrossRef]
- Huan, N.T.Y.; Zukarnain, Z.A. A Survey on Addressing IoT Security Issues by Embedding Blockchain Technology Solutions: Review, Attacks, Current Trends, and Applications. IEEE Access 2024, 12, 69765–69782. [Google Scholar] [CrossRef]
- Li, D.; Han, D.; Weng, T.H.; Zheng, Z.; Li, H.; Liu, H.; Castiglione, A.; Li, K.C. Blockchain for federated learning toward secure distributed machine learning systems: A systemic survey. Soft Comput. 2022, 26, 4423–4440. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Liu, P.; Xu, X.; Wang, W. Threats, attacks and defenses to federated learning: Issues, taxonomy and perspectives. Cybersecurity 2022, 5, 4. [Google Scholar] [CrossRef]
- Lee, J.H. Systematic Approach to Analyzing Security and Vulnerabilities of Blockchain Systems. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2019. [Google Scholar]
- Zamani, E.; He, Y.; Phillips, M. On the security risks of the blockchain. J. Comput. Inf. Syst. 2020, 60, 495–506. [Google Scholar] [CrossRef]
- Singh, S.; Hosen, A.S.; Yoon, B. Blockchain security attacks, challenges, and solutions for the future distributed iot network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Zarrin, J.; Wen Phang, H.; Babu Saheer, L.; Zarrin, B. Blockchain for decentralization of internet: Prospects, trends, and challenges. Clust. Comput. 2021, 24, 2841–2866. [Google Scholar] [CrossRef]
- Manu, M.; Musthafa, N.; Balamurugan, B.; Chauhan, R. Blockchain components and concept. In Blockchain Technology and Applications; Auerbach Publications: Boca Raton, FL, USA, 2020; pp. 21–50. [Google Scholar]
- Patel, V.; Khatiwala, F.; Shah, K.; Choksi, Y. A review on blockchain technology: Components, issues and challenges. In Proceedings of the ICDSMLA 2019: Proceedings of the 1st International Conference on Data Science, Machine Learning and Applications, Hyderabad, India, 26–28 July 2019; Springer: Berlin/Heidelberg, Germany, 2020; pp. 1257–1262. [Google Scholar]
- Puthal, D.; Malik, N.; Mohanty, S.P.; Kougianos, E.; Das, G. Everything you wanted to know about the blockchain: Its promise, components, processes, and problems. IEEE Consum. Electron. Mag. 2018, 7, 6–14. [Google Scholar] [CrossRef]
- IBM. What Is Blockchain Technology? 2022. Available online: https://www.ibm.com/topics/what-is-blockchain (accessed on 10 September 2024).
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. (CSUR) 2019, 52, 1–34. [Google Scholar] [CrossRef]
- Bhushan, B.; Sinha, P.; Sagayam, K.M.; Andrew, J. Untangling blockchain technology: A survey on state of the art, security threats, privacy services, applications and future research directions. Comput. Electr. Eng. 2021, 90, 106897. [Google Scholar] [CrossRef]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the attack surface of blockchain: A systematic overview. arXiv 2019, arXiv:1904.03487. [Google Scholar]
- Mosakheil, J.H. Security Threats Classification in Blockchains. Master’s Thesis, Herberger School of Business, St. Cloud, MN, USA, 2018. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
- Dasgupta, D.; Shrein, J.M.; Gupta, K.D. A survey of blockchain from security perspective. J. Bank. Financ. Technol. 2019, 3, 1–17. [Google Scholar] [CrossRef]
- Anita, N.; Vijayalakshmi, M. Blockchain security attack: A brief survey. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kanpur, India, 6–8 July 2019; IEEE: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Putz, B.; Pernul, G. Detecting blockchain security threats. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; IEEE: New York, NJ, USA, 2020; pp. 313–320. [Google Scholar]
- Gao, R.; Zhang, Q.; Chen, Y.; Ma, J. A Taxonomy of Consensus Attacks in Blockchain. Future Gener. Comput. Syst. 2022, 128, 325–338. [Google Scholar] [CrossRef]
- Cheng, J.; Xie, L.; Tang, X.; Xiong, N.; Liu, B. A survey of security threats and defense on Blockchain. Multimed. Tools Appl. 2021, 80, 30623–30652. [Google Scholar] [CrossRef]
- Toapanta, T.S.M.; Del Pozo, D.R.; Izurieta, R.R.; Guamán, J.A.; Orizaga, J.A.; Arellano, R.M.; Hifóng, M.M.B. Blockchain-based Security Model to Mitigate the Risks of a Database for a Public Organization. J. Internet Serv. Inf. Secur. (JISIS) 2024, 14, 78–98. [Google Scholar] [CrossRef]
- Parino, F.; Beiro, M.; Gauvin, L. Analysis of the Bitcoin blockchain: Socio-economic factors behind the adoption. EPJ Data Sci. 2018, 7, 38. [Google Scholar] [CrossRef]
- Popov, S. The Tangle; White Paper; IOTA: Berlin, Germany, 2018. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the EuroSys, Porto, Portugal, 23–26 April 2018. [Google Scholar]
- Buterin, V. Ethereum 2.0 Phase 0—Beacon Chain. 2020. Available online: https://ethereum.org/en/upgrades/beacon-chain/ (accessed on 10 August 2024).
- Kwon, J.; Buchman, E. Cosmos: A Network of Distributed Ledgers. Cosm. Whitepaper 2019, 1–32. [Google Scholar]
- Wen, Y.; Lu, F.; Liu, Y.; Huang, X. Attacks and countermeasures on blockchains: A survey from layering perspective. Comput. Netw. 2021, 191, 107978. [Google Scholar] [CrossRef]
- Kearney, J.J.; Perez-Delgado, C.A. Vulnerability of blockchain technologies to quantum attacks. Array 2021, 10, 100065. [Google Scholar] [CrossRef]
- Allende, M.; León, D.L.; Cerón, S.; Pareja, A.; Pacheco, E.; Leal, A.; Da Silva, M.; Pardo, A.; Jones, D.; Worrall, D.J.; et al. Quantum-resistance in blockchain networks. Sci. Rep. 2023, 13, 5664. [Google Scholar] [CrossRef]
- Hasanova, H.; Baek, U.J.; Shin, M.G.; Cho, K.; Kim, M.S. A survey on blockchain cybersecurity vulnerabilities and possible countermeasures. Int. J. Netw. Manag. 2019, 29, e2060. [Google Scholar] [CrossRef]
- Cooper, E.; Weese, E.; Fortson, A.; Lo, D.; Shi, Y. Cyber Security in Blockchain. In Proceedings of the 2023 IEEE Conference on Dependable and Secure Computing (DSC), Tampa, FL, USA, 7–9 November 2023; IEEE: New York, NJ, USA, 2023; pp. 1–11. [Google Scholar]
- Wang, H.; Wang, Y.; Cao, Z.; Li, Z.; Xiong, G. An overview of blockchain security analysis. In Proceedings of the Cyber Security: 15th International Annual Conference, CNCERT 2018, Beijing, China, 14–16 August 2018; Revised Selected Papers 15. Springer: Singapore, 2019; pp. 55–72. [Google Scholar]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Georgia, W. Arithmetic Underflow and Overflow Vulnerabilities in Smart Contracts. 2023. Available online: https://101blockchains.com/underflow-and-overflow-vulnerabilities-in-smart-contracts/ (accessed on 22 April 2024).
- Guggenberger, T.; Schlatt, V.; Schmid, J.; Urbach, N. A Structured Overview of Attacks on Blockchain Systems. In Proceedings of the PACIS, Dubai, United Arab Emirates, 12–14 July 2021; p. 100. [Google Scholar]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In Proceedings of the Principles of Security and Trust: 6th International Conference, POST 2017, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2017, Uppsala, Sweden, 22–29 April 2017; Proceedings 6. Springer: Berlin/Heidelberg, Germany, 2017; pp. 164–186. [Google Scholar]
- Chen, Y.; Sun, Z.; Gong, Z.; Hao, D. Improving Smart Contract Security with Contrastive Learning-based Vulnerability Detection. In Proceedings of the IEEE/ACM 46th International Conference on Software Engineering, Lisbon, Portugal, 14–20 April 2024; pp. 1–11. [Google Scholar]
- Luo, F.; Luo, R.; Chen, T.; Qiao, A.; He, Z.; Song, S.; Jiang, Y.; Li, S. Scvhunter: Smart contract vulnerability detection based on heterogeneous graph attention network. In Proceedings of the IEEE/ACM 46th International Conference on Software Engineering, Lisbon, Portugal, 14–20 April 2024; pp. 1–13. [Google Scholar]
- Zhen, Z.; Zhao, X.; Zhang, J.; Wang, Y.; Chen, H. DA-GNN: A smart contract vulnerability detection method based on Dual Attention Graph Neural Network. Comput. Netw. 2024, 242, 110238. [Google Scholar] [CrossRef]
- Sun, Y.; Gu, L. Attention-based machine learning model for smart contract vulnerability detection. J. Phys. Conf. Ser. 2021, 1820, 012004. [Google Scholar] [CrossRef]
- Lutz, O.; Chen, H.; Fereidooni, H.; Sendner, C.; Dmitrienko, A.; Sadeghi, A.R.; Koushanfar, F. Escort: Ethereum smart contracts vulnerability detection using deep neural network and transfer learning. arXiv 2021, arXiv:2103.12607. [Google Scholar]
- Colin, L.S.H.; Mohan, P.M.; Pan, J.; Keong, P.L.K. An Integrated Smart Contract Vulnerability Detection Tool Using Multi-layer Perceptron on Real-time Solidity Smart Contracts. IEEE Access 2024, 12, 23549–23567. [Google Scholar] [CrossRef]
- Jain, V.K.; Tripathi, M. An integrated deep learning model for Ethereum smart contract vulnerability detection. Int. J. Inf. Secur. 2024, 23, 557–575. [Google Scholar] [CrossRef]
- Zhou, Q.; Zheng, K.; Zhang, K.; Hou, L.; Wang, X. Vulnerability analysis of smart contract for blockchain-based IoT applications: A machine learning approach. IEEE Internet Things J. 2022, 9, 24695–24707. [Google Scholar] [CrossRef]
- Narayana, K.L.; Sathiyamurthy, K. Automation and smart materials in detecting smart contracts vulnerabilities in Blockchain using deep learning. Mater. Today Proc. 2023, 81, 653–659. [Google Scholar] [CrossRef]
- Rabieinejad, E.; Yazdinejad, A.; Parizi, R.M. A deep learning model for threat hunting in ethereum blockchain. In Proceedings of the 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Shenyang, China, 20–22 October 2021; IEEE: New York, NJ, USA, 2021; pp. 1185–1190. [Google Scholar]
- Ismail, S.; Nouman, M.; Dawoud, D.W.; Reza, H. Towards a lightweight security framework using blockchain and machine learning. Blockchain Res. Appl. 2024, 5, 100174. [Google Scholar] [CrossRef]
- Bresil, M.; Prasad, P.; Sayeed, M.S.; Bukar, U.A. Deep Learning-based Vulnerability Detection Solutions in Smart Contracts: A Comparative and Meta-Analysis of Existing Approaches. IEEE Access 2025, 13, 28894–28919. [Google Scholar] [CrossRef]
- Chen, J.; Wang, W.; Liu, B.; Cai, S.; Towey, D.; Wang, S. Hybrid semantics-based vulnerability detection incorporating a Temporal Convolutional Network and Self-attention Mechanism. Inf. Softw. Technol. 2024, 171, 107453. [Google Scholar] [CrossRef]
- Crisostomo, J.; Bacao, F.; Lobo, V. Machine learning methods for detecting smart contracts vulnerabilities within Ethereum blockchain—A review. Expert Syst. Appl. 2025, 268, 126353. [Google Scholar] [CrossRef]
- Duy, P.T.; Khoa, N.H.; Quyen, N.H.; Trinh, L.C.; Kien, V.T.; Hoang, T.M.; Pham, V.H. Vulnsense: Efficient vulnerability detection in ethereum smart contracts by multimodal learning with graph neural network and language model. Int. J. Inf. Secur. 2025, 24, 48. [Google Scholar] [CrossRef]
- Mohammed, H.A.; Husien, I.M. A Deep Transfer Learning Framework for Robust IoT Attack Detection: A Review. Informatica 2024, 48, 55–64. [Google Scholar] [CrossRef]
- Korba, A.A.; Boualouache, A.; Ghamri-Doudane, Y. Zero-X: A Blockchain-Enabled Open-Set Federated Learning Framework for Zero-Day Attack Detection in IoV. IEEE Trans. Veh. Technol. 2024, 73, 12399–12414. [Google Scholar] [CrossRef]
- Mbaya, E.B.; Adetiba, E.; Badejo, J.A.; Wejin, J.S.; Oshin, O.; Isife, O.; Thakur, S.C.; Moyo, S.; Adebiyi, E.F. SecFedIDM-V1: A secure federated intrusion detection model with blockchain and deep bidirectional long short-term memory network. IEEE Access 2023, 11, 116011–116025. [Google Scholar] [CrossRef]
- Chen, H.; Zhao, X.; Wang, Y.; Zhen, Z. SafeCheck: Detecting smart contract vulnerabilities based on static program analysis methods. Secur. Priv. 2024, 7, e393. [Google Scholar] [CrossRef]
- Sun, Y.; Wu, D.; Xue, Y.; Liu, H.; Wang, H.; Xu, Z.; Xie, X.; Liu, Y. Gptscan: Detecting logic vulnerabilities in smart contracts by combining gpt with program analysis. In Proceedings of the IEEE/ACM 46th International Conference on Software Engineering, Lisbon, Portugal, 14–20 April 2024; pp. 1–13. [Google Scholar]
- Pise, R.G.; Patil, S. Pioneering automated vulnerability detection for smart contracts in blockchain using KEVM: Guardian ADRGAN. Int. J. Inf. Secur. 2024, 23, 1805–1819. [Google Scholar] [CrossRef]
- Singh, A.; Parizi, R.M.; Zhang, Q.; Choo, K.K.R.; Dehghantanha, A. Blockchain smart contracts formalization: Approaches and challenges to address vulnerabilities. Comput. Secur. 2020, 88, 101654. [Google Scholar] [CrossRef]
- Chinen, Y.; Yanai, N.; Cruz, J.P.; Okamura, S. RA: Hunting for re-entrancy attacks in ethereum smart contracts via static analysis. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Virtual, 2–6 November 2020; IEEE: New York, NJ, USA, 2020; pp. 327–336. [Google Scholar]
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static analysis of ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 9–16. [Google Scholar]
- Krichen, M.; Lahami, M.; Al-Haija, Q.A. Formal methods for the verification of smart contracts: A review. In Proceedings of the 2022 15th International Conference on Security of Information and Networks (SIN), Sousse, Tunisia, 11–13 November 2022; IEEE: New York, NJ, USA, 2022; pp. 01–08. [Google Scholar]
- Kushwaha, S.S.; Joshi, S.; Singh, D.; Kaur, M.; Lee, H.N. Systematic review of security vulnerabilities in ethereum blockchain smart contract. IEEE Access 2022, 10, 6605–6621. [Google Scholar] [CrossRef]
- Li, Z.; Lu, S.; Zhang, R.; Xue, R.; Ma, W.; Liang, R.; Zhao, Z.; Gao, S. SmartFast: An accurate and robust formal analysis tool for Ethereum smart contracts. Empir. Softw. Eng. 2022, 27, 197. [Google Scholar] [CrossRef]
- Cao, X.; Zhang, J.; Wu, X.; Liu, B. A survey on security in consensus and smart contracts. Peer-to-Peer Netw. Appl. 2022, 15, 1008–1028. [Google Scholar] [CrossRef]
- Li, B.; Pan, Z.; Hu, T. EvoFuzzer: An Evolutionary Fuzzer for Detecting Reentrancy Vulnerability in Smart Contracts. IEEE Trans. Netw. Sci. Eng. 2024, 11, 5790–5802. [Google Scholar] [CrossRef]
- Praitheeshan, P.; Pan, L.; Yu, J.; Liu, J.; Doss, R. Security analysis methods on ethereum smart contract vulnerabilities: A survey. arXiv 2019, arXiv:1908.08605. [Google Scholar]
- Feng, Z.; Feng, Y.; He, H.; Zhang, W.; Zhang, Y. A bytecode-based integrated detection and repair method for reentrancy vulnerabilities in smart contracts. IET Blockchain 2024, 4, 235–251. [Google Scholar] [CrossRef]
- Gao, C.; Yang, W.; Ye, J.; Xue, Y.; Sun, J. sGuard+: Machine learning guided rule-based automated vulnerability repair on smart contracts. ACM Trans. Softw. Eng. Methodol. 2024, 33, 1–55. [Google Scholar] [CrossRef]
- Senanayake, J.; Kalutarage, H.; Petrovski, A.; Piras, L.; Al-Kadri, M.O. Defendroid: Real-time Android code vulnerability detection via blockchain federated neural network with XAI. J. Inf. Secur. Appl. 2024, 82, 103741. [Google Scholar] [CrossRef]
- Priya, J.C.; Rudzki, K.; Nguyen, X.H.; Nguyen, H.P.; Chotechuang, N.; Pham, N.D.K. Blockchain-Enabled Transfer Learning for Vulnerability Detection and Mitigation in Maritime Logistics. Pol. Marit. Res. 2024, 31, 135–145. [Google Scholar] [CrossRef]
- He, N.; Wang, H.; Wu, L.; Luo, X.; Guo, Y.; Chen, X. A survey on eosio systems security: Vulnerability, attack, and mitigation. Front. Comput. Sci. 2025, 19, 196806. [Google Scholar] [CrossRef]
- Yang, H.; Gu, X.; Chen, X.; Zheng, L.; Cui, Z. CrossFuz: Cross-contract fuzzing for smart contract vulnerability detection. Sci. Comput. Program. 2024, 234, 103076. [Google Scholar] [CrossRef]
- Shou, C.; Liu, J.; Lu, D.; Sen, K. LLM4Fuzz: Guided fuzzing of smart contracts with large language models. arXiv 2024, arXiv:2401.11108. [Google Scholar]
- Zheng, Z.; Su, J.; Chen, J.; Lo, D.; Zhong, Z.; Ye, M. DAppSCAN: Building large-scale datasets for smart contract weaknesses in dapp projects. IEEE Trans. Softw. Eng. 2024, 50, 1360–1373. [Google Scholar] [CrossRef]
- Cai, J.; Li, B.; Zhang, T.; Zhang, J.; Sun, X. Fine-grained smart contract vulnerability detection by heterogeneous code feature learning and automated dataset construction. J. Syst. Softw. 2024, 209, 111919. [Google Scholar] [CrossRef]
- Victor, F.; Lüders, B.K. Measuring ethereum-based erc20 token networks. In Proceedings of the Financial Cryptography and Data Security: 23rd International Conference, FC 2019, Frigate Bay, Saint Kitts and Nevis, 18–22 February 2019; Revised Selected Papers 23. Springer: Berlin/Heidelberg, Germany, 2019; pp. 113–129. [Google Scholar]
- Luu, L.; Chu, D.H.; Olickel, H.; Saxena, P.; Hobor, A. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 254–269. [Google Scholar]
- Taylor, P.J.; Dargahi, T.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R. A systematic literature review of blockchain cyber security. Digit. Commun. Netw. 2020, 6, 147–156. [Google Scholar] [CrossRef]
- Li, B.; Pan, Z.; Hu, T. Redefender: Detecting reentrancy vulnerabilities in smart contracts automatically. IEEE Trans. Reliab. 2022, 71, 984–999. [Google Scholar] [CrossRef]
- Wu, G.; Wang, H.; Lai, X.; Wang, M.; He, D.; Chan, S. A comprehensive survey of smart contract security: State of the art and research directions. J. Netw. Comput. Appl. 2024, 226, 103882. [Google Scholar] [CrossRef]
- He, D.; Wu, R.; Li, X.; Chan, S.; Guizani, M. Detection of vulnerabilities of blockchain smart contracts. IEEE Internet Things J. 2023, 10, 12178–12185. [Google Scholar] [CrossRef]
- Yao, Y.; Duan, J.; Xu, K.; Cai, Y.; Sun, Z.; Zhang, Y. A survey on large language model (llm) security and privacy: The good, the bad, and the ugly. High-Confid. Comput. 2024, 4, 100211. [Google Scholar] [CrossRef]
- Homoliak, I.; Venugopalan, S.; Hum, Q.; Szalachowski, P. A security reference architecture for blockchains. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Seoul, Republic of Korea, 14–17 May 2019; IEEE: New York, NY, USA, 2019; pp. 390–397. [Google Scholar]
- He, Z.; Li, Z.; Yang, S.; Qiao, A.; Zhang, X.; Luo, X.; Chen, T. Large language models for blockchain security: A systematic literature review. arXiv 2024, arXiv:2403.14280. [Google Scholar]
- Venkatesan, K.; Rahayu, S.B. Blockchain security enhancement: An approach towards hybrid consensus algorithms and machine learning techniques. Sci. Rep. 2024, 14, 1149. [Google Scholar] [CrossRef]
- Ali, S.; Li, Q.; Yousafzai, A. Blockchain and federated learning-based intrusion detection approaches for edge-enabled industrial IoT networks: A survey. Ad Hoc Netw. 2024, 152, 103320. [Google Scholar] [CrossRef]
- Taher, S.S.; Ameen, S.Y.; Ahmed, J.A. Advanced Fraud Detection in Blockchain Transactions: An Ensemble Learning and Explainable AI Approach. Eng. Technol. Appl. Sci. Res. 2024, 14, 12822–12830. [Google Scholar] [CrossRef]
- Kim, S.K. Automotive vulnerability analysis for deep learning blockchain consensus algorithm. Electronics 2021, 11, 119. [Google Scholar] [CrossRef]
- Ibba, G.; Baralla, G.; Destefanis, G. Large Language Models for Synthetic Dataset Generation: A Case Study on Ethereum Smart Contract DoS Vulnerabilities. In Proceedings of the IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER) 2025, Montréal, QC, Canada, 4–7 March 2025. [Google Scholar]
- Li, Z.; Zou, D.; Xu, S.; Ou, X.; Jin, H.; Wang, S.; Deng, Z.; Zhong, Y. Vuldeepecker: A deep learning-based system for vulnerability detection. arXiv 2018, arXiv:1801.01681. [Google Scholar]
- Kong, L.; Luo, S.; Pan, L.; Wu, Z.; Li, X. A multi-type vulnerability detection framework with parallel perspective fusion and hierarchical feature enhancement. Comput. Secur. 2024, 140, 103787. [Google Scholar] [CrossRef]
- SWC Registry. Smart Contract Weakness Classification and Test Cases. Available online: https://swcregistry.io/ (accessed on 5 May 2022).
- Hasan, M.; Rahman, M.S.; Janicke, H.; Sarker, I.H. Detecting anomalies in blockchain transactions using machine learning classifiers and explainability analysis. Blockchain Res. Appl. 2024, 5, 100207. [Google Scholar] [CrossRef]
- Mounnan, O.; Manad, O.; Boubchir, L.; El Mouatasim, A.; Daachi, B. A review on deep anomaly detection in blockchain. Blockchain Res. Appl. 2024, 5, 100227. [Google Scholar] [CrossRef]
- Mishra, S. Blockchain and machine learning-based hybrid IDS to protect smart networks and preserve privacy. Electronics 2023, 12, 3524. [Google Scholar] [CrossRef]
- He, F.; Li, F.; Liang, P. Enhancing smart contract security: Leveraging pre-trained language models for advanced vulnerability detection. IET Blockchain 2024, 4, 543–554. [Google Scholar] [CrossRef]
- Radanliev, P. Artificial intelligence and quantum cryptography. J. Anal. Sci. Technol. 2024, 15, 4. [Google Scholar] [CrossRef]
- Gai, Y.; Zhou, L.; Qin, K.; Song, D.; Gervais, A. Blockchain large language models. arXiv 2023, arXiv:2304.12749. [Google Scholar]
- Brew, B. Can Artificial Intelligence Hack Blockchain Technology? 2023. Available online: https://medium.com/@blockchaindevelopment121/can-artificial-intelligence-hack-blockchain-technology-e26ac4f17c3 (accessed on 9 February 2024).
- Knight, O. Ethereum Bot Gets Attacked for 20M as Validator Strikes Back. 2023. Available online: https://www.coindesk.com/business/2023/04/03/ethereum-mev-bot-gets-attacked-for-20m-as-validator-strikes-back/ (accessed on 12 April 2024).
- Coghlan, J. This AI Chatbot Is Either an Exploiter’s Dream or Their Nightmare. 2022. Available online: https://cointelegraph.com/news/this-ai-chatbot-is-either-an-exploiter-s-dream-or-their-nightmare (accessed on 19 August 2024).
- Kayikci, S.; Khoshgoftaar, T.M. Blockchain meets machine learning: A survey. J. Big Data 2024, 11, 9. [Google Scholar] [CrossRef]
- Palaiokrassas, G.; Bouraga, S.; Tassiulas, L. Machine Learning on Blockchain Data: A Systematic Mapping Study. arXiv 2024, arXiv:2403.17081. [Google Scholar]
- Azad, P.; Akcora, C.G.; Khan, A. Machine Learning for Blockchain Data Analysis: Progress and Opportunities. arXiv 2024, arXiv:2404.18251. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).