Studying the Impact of a UDP DoS Attack on the Parameters of VoIP Voice and Video Streams
Abstract
1. Introduction
2. Related Works
3. Research Methodology and Used Tools
3.1. Research Methodology
- The attack will be isolated to the “territory” of the modeled network. The modeled network will not be connected to the Internet or other IP networks. Thus, the attack action will be isolated, controlled and co-focused only on the territory of the modeled network;
- Real network device models will be used, which are very expensive, and not everyone can afford them. The main advantage of GNS3 is working with disk images of real operating systems of different network devices. Real/physical network devices are very expensive, and not every researcher can afford to buy them. This limiting factor is eliminated by the use of the GNS3, through which these network devices can be used by researchers, in the form of models. In this way, the modeled networks with GNS3 will be closer to the real networks.
3.2. Used Tools
- Network packet analyzer: Wireshark [31] was used due to its integration with GNS3 and the functionality to analyze RTP flows.
- Network analyzer: Colasoft Capsa 11 free was used [32]. It monitors the network interface of the Asterisk FreePBX.
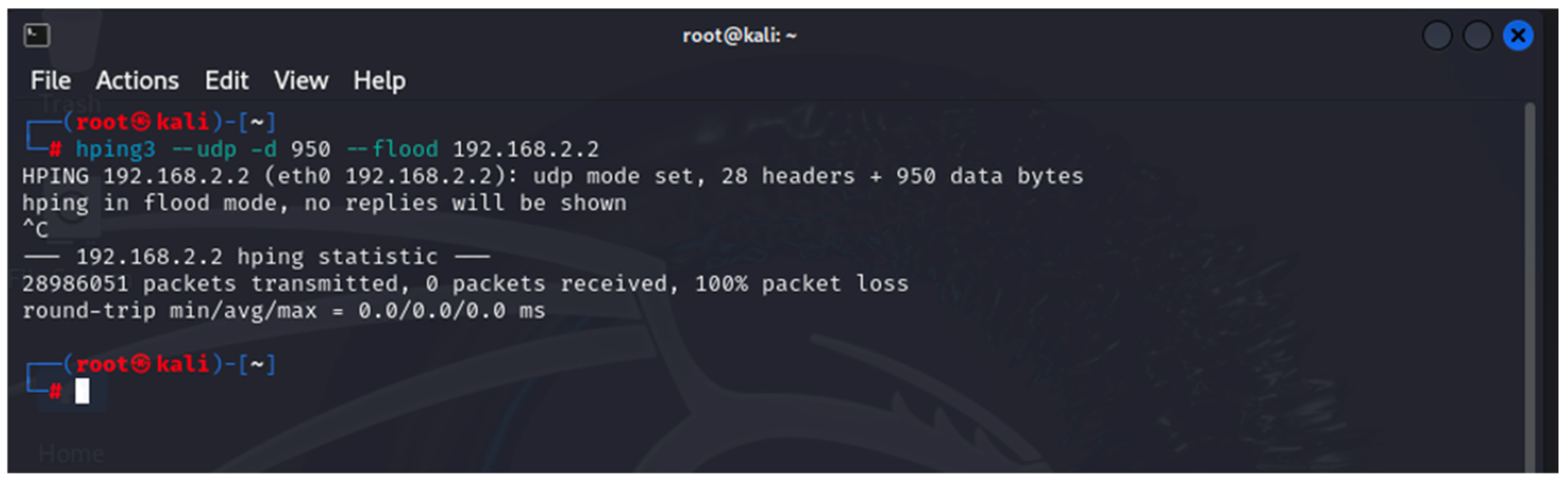
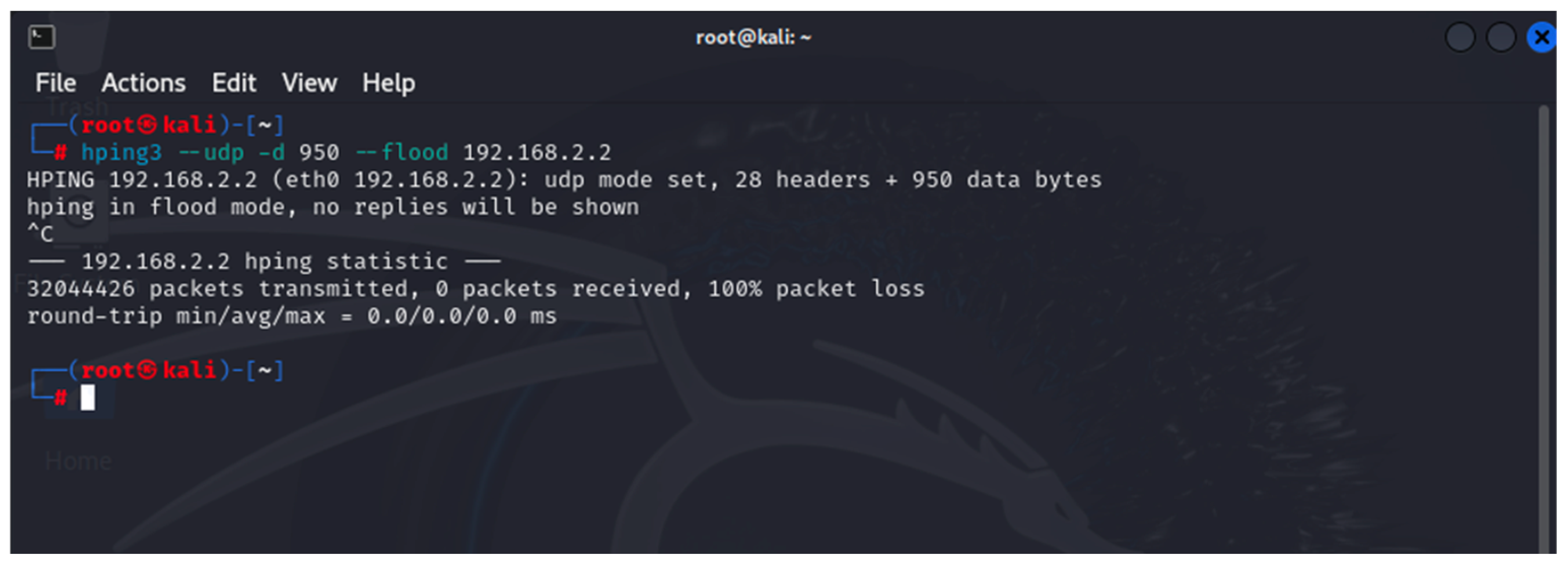
- hping3: This is a network tool that generates/sends modified ICMP/UDP/TCP packets. It is used to flood the attacked device—it implements UDP/TCP DoS attacks [33].
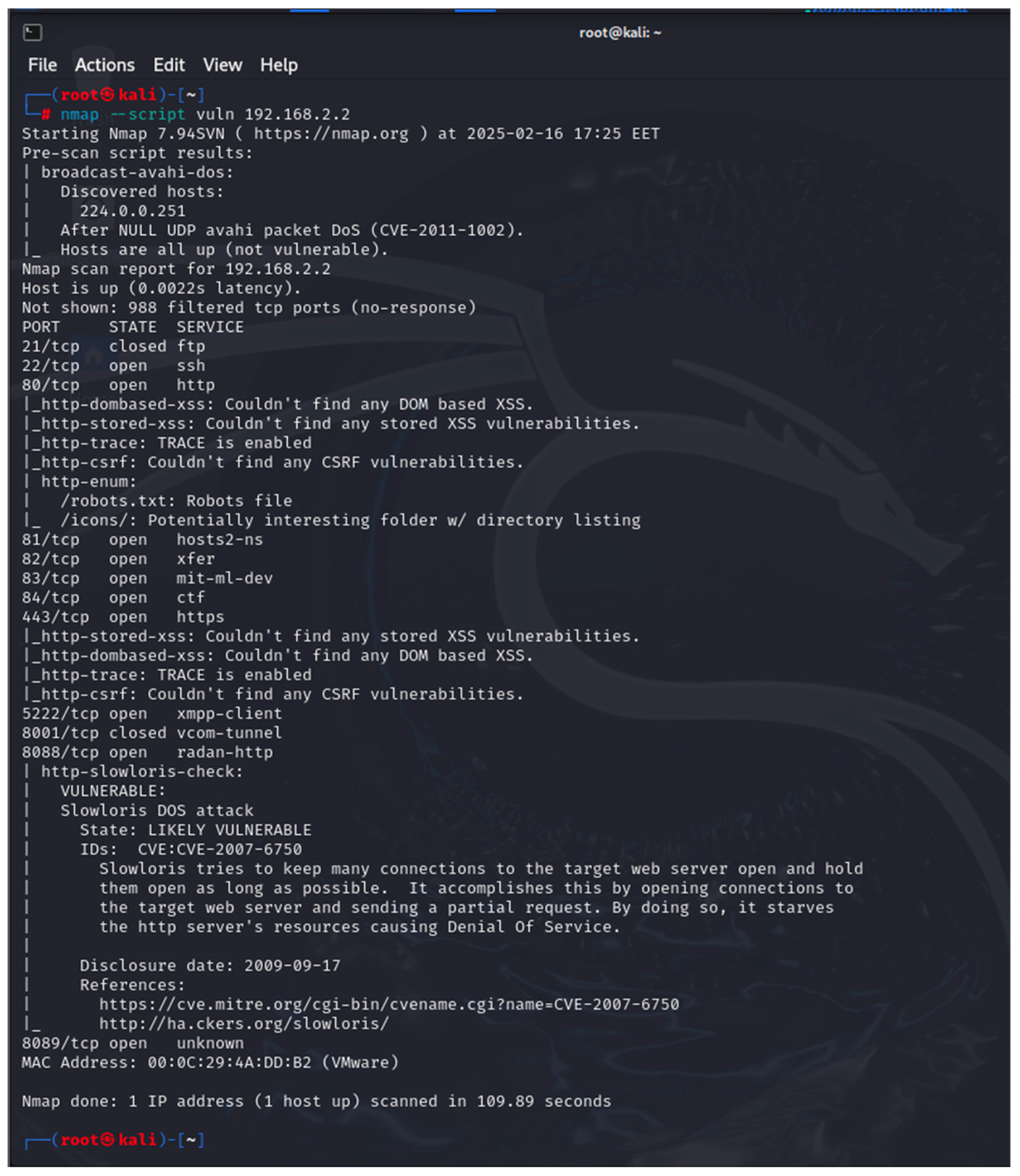
- Nmap: It is a tool for discovering network devices and for studying the network security level of a device [34].
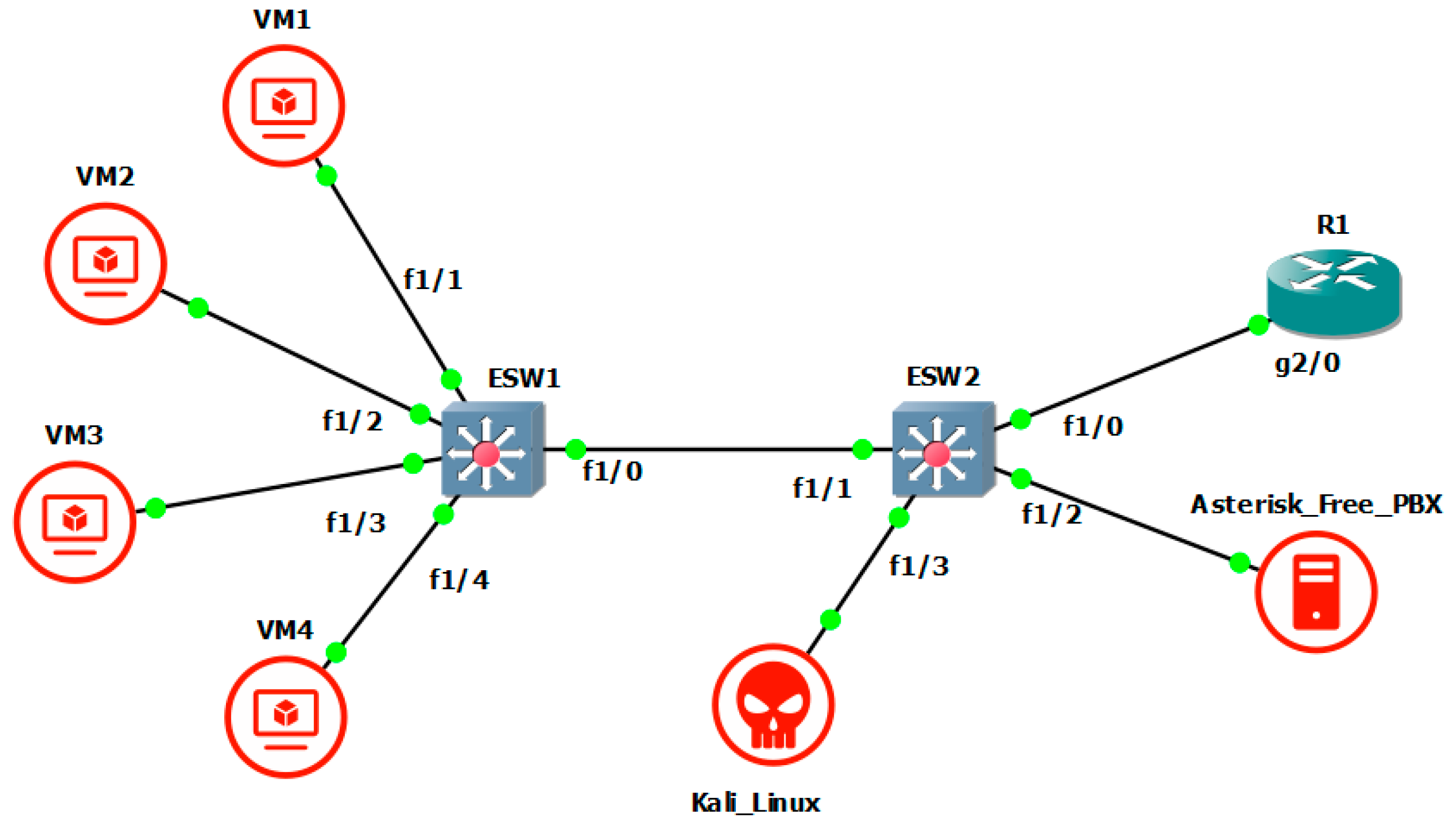
4. Topology of the Modeled Network
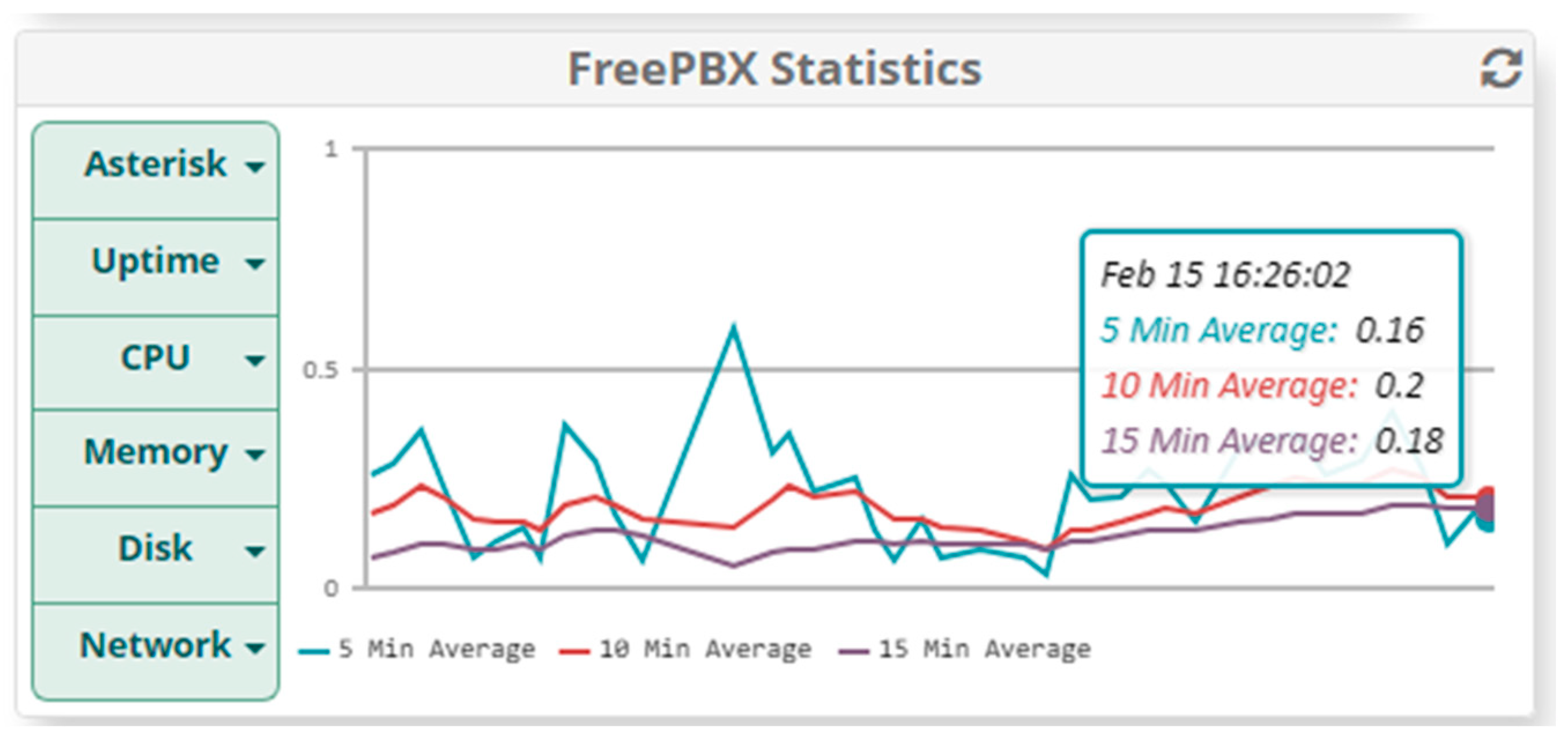
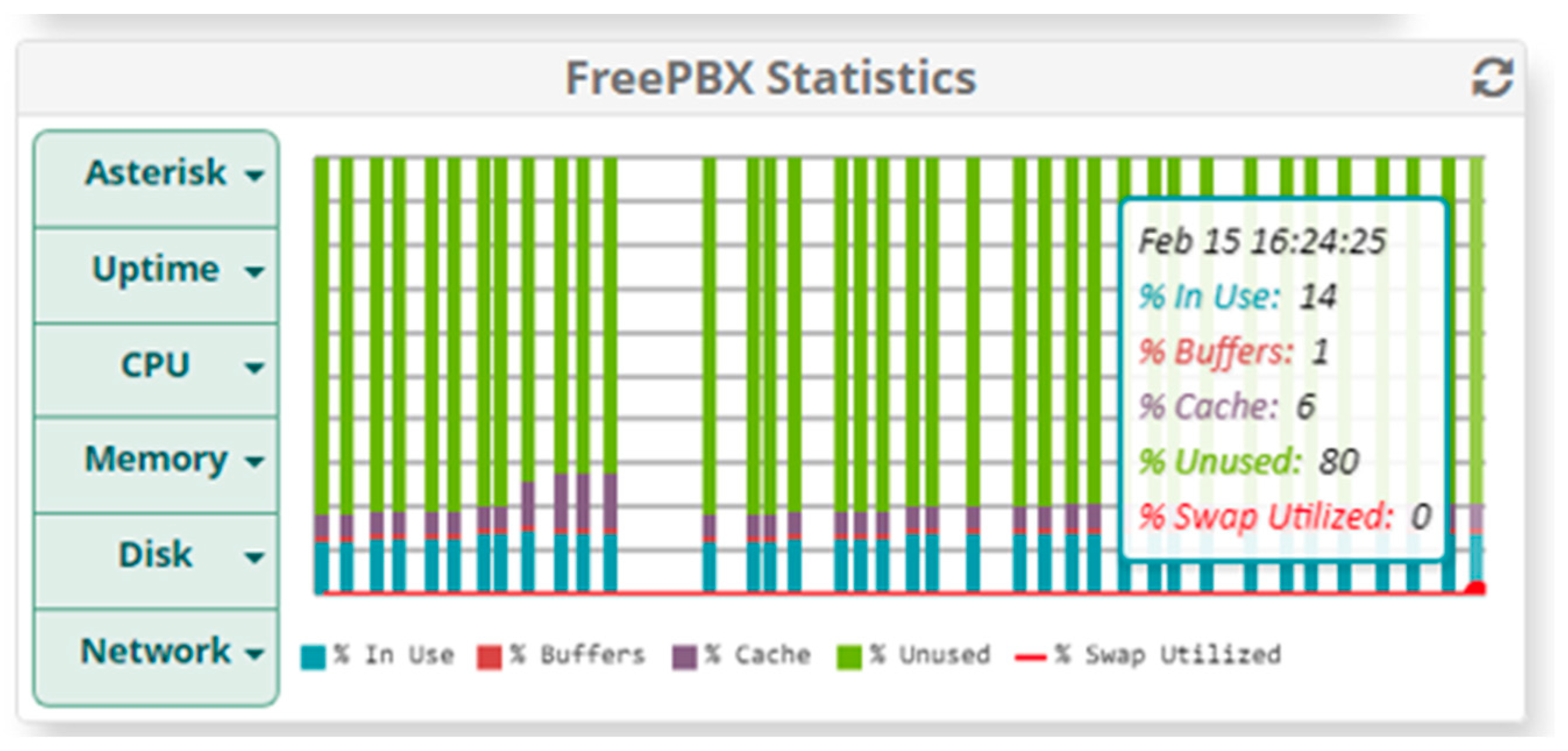
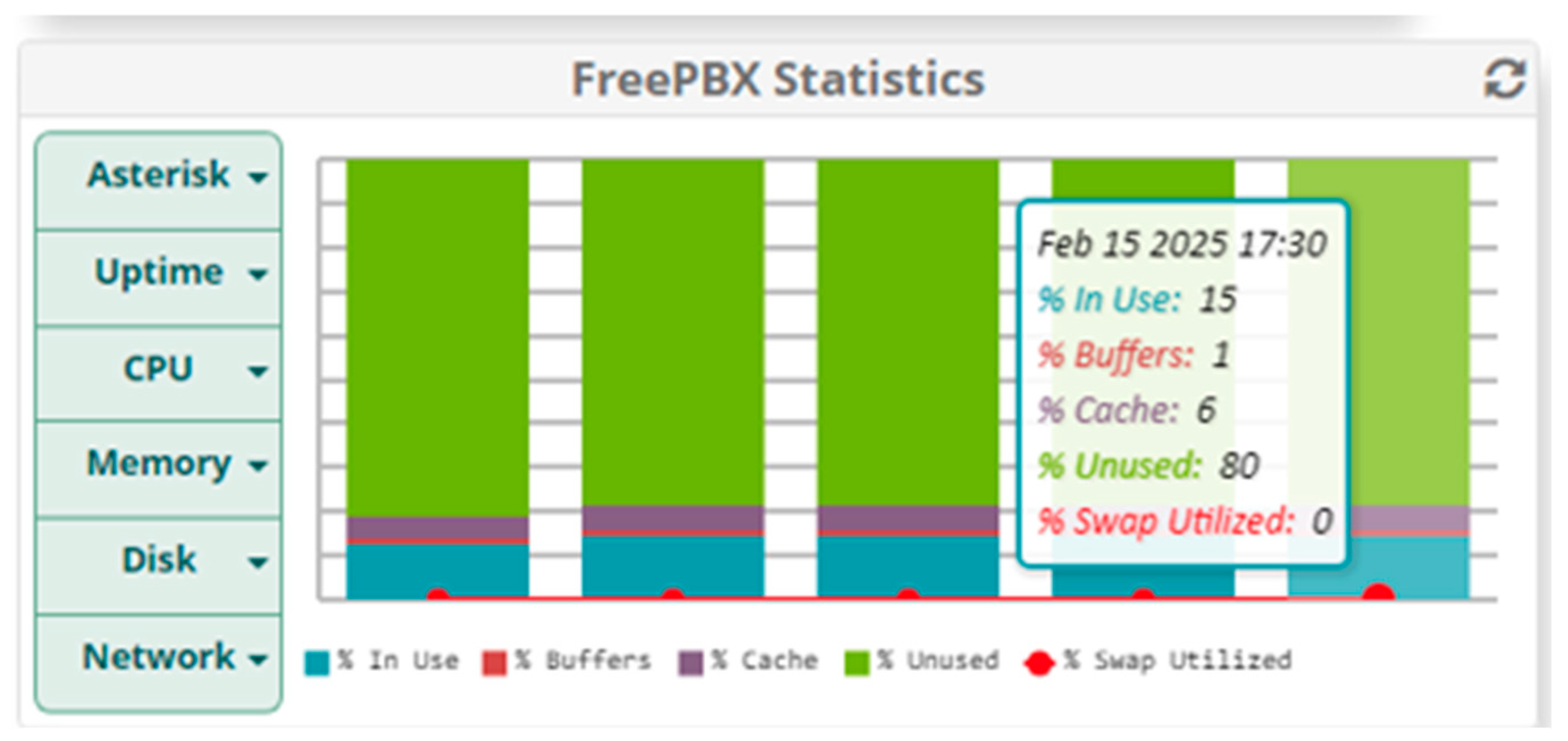
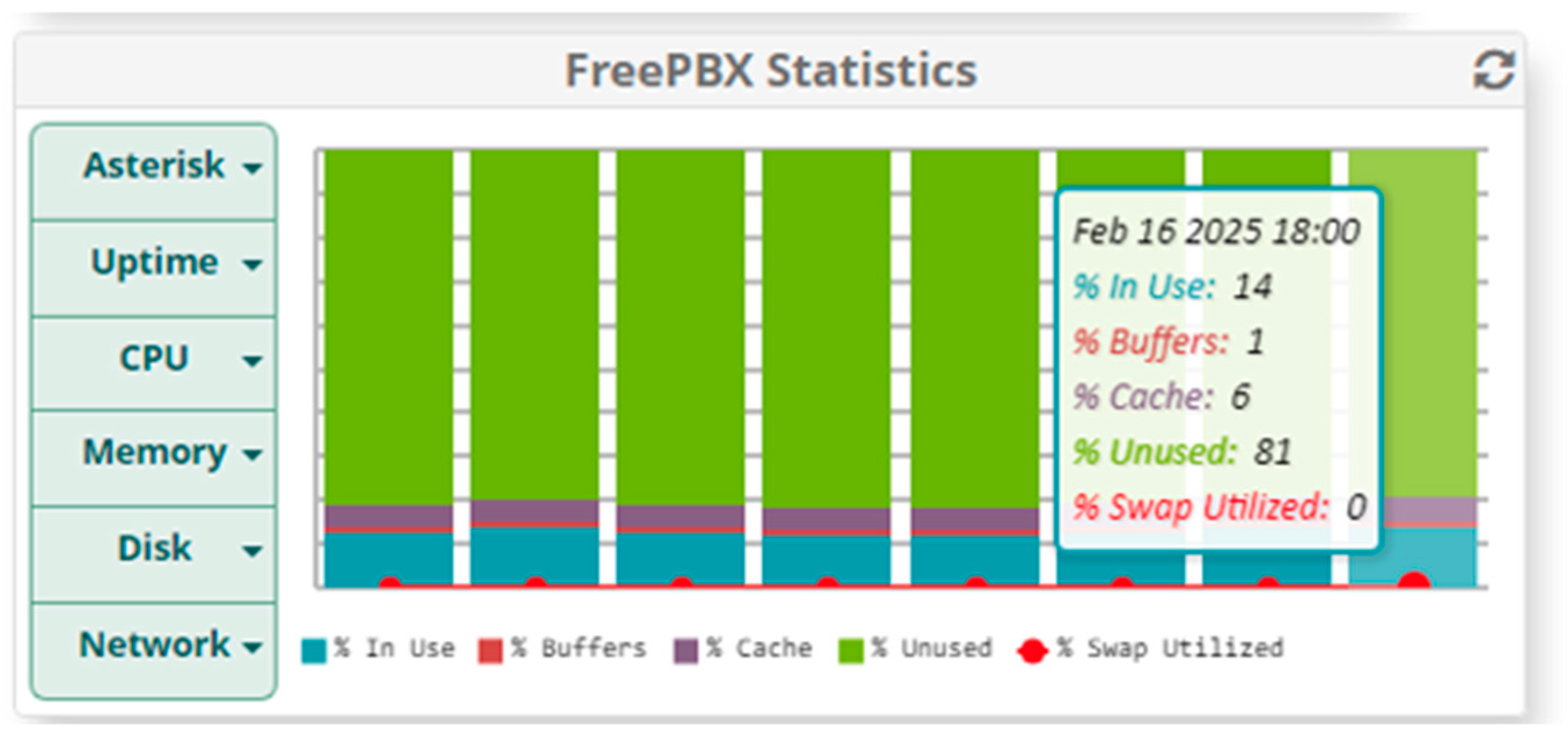
5. Results
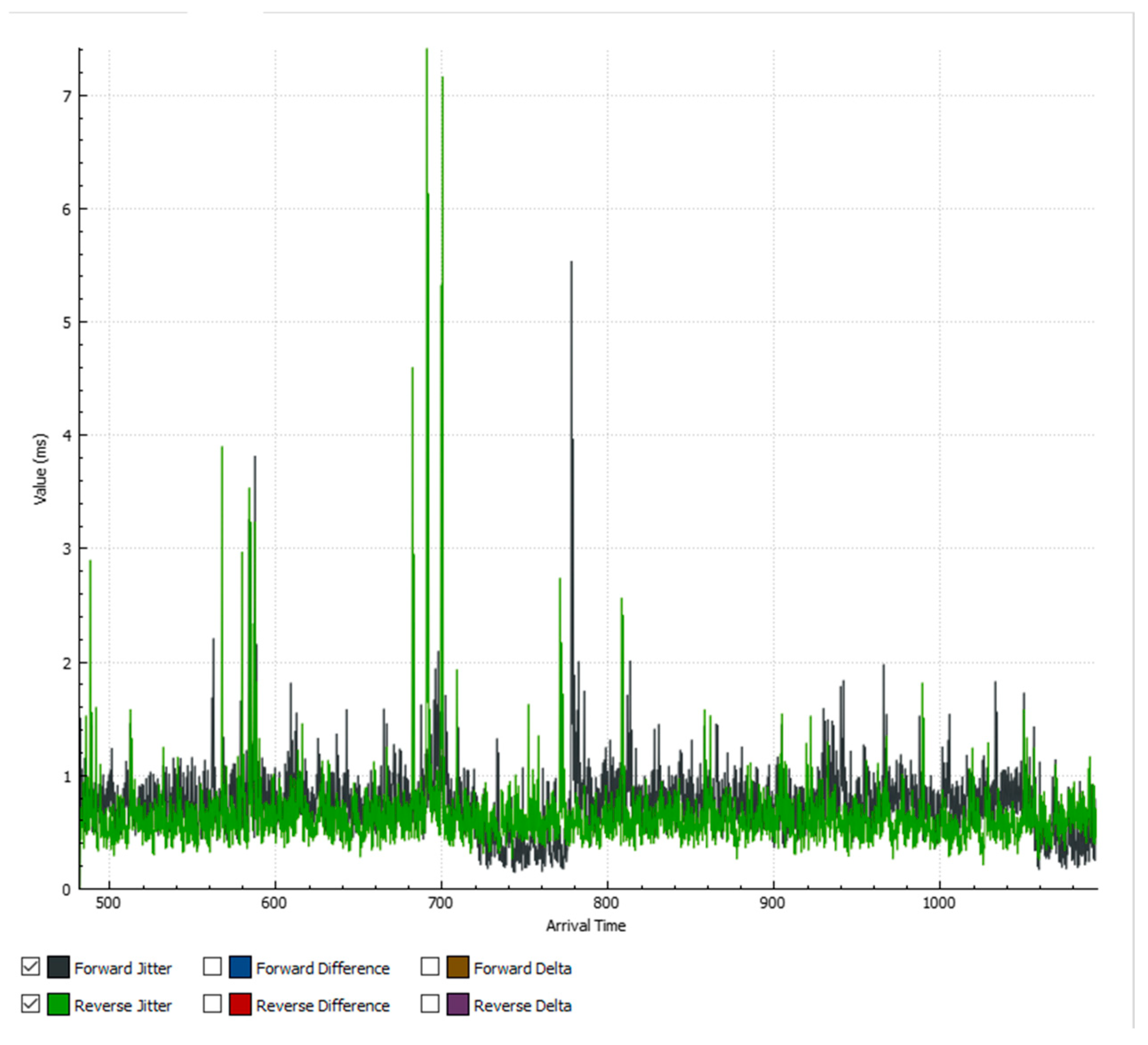
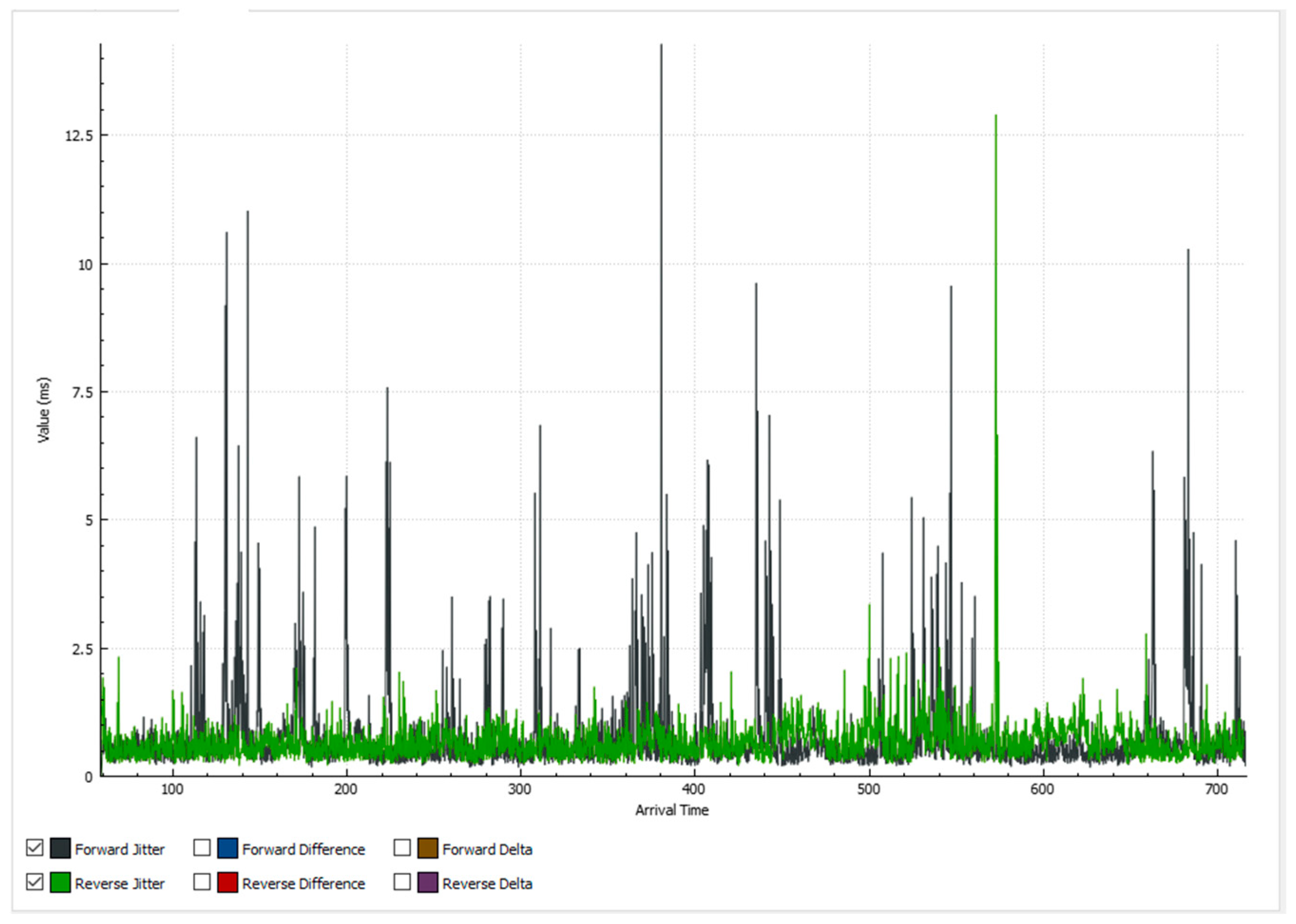
5.1. Results When Only Voice Traffic Is Exchanged
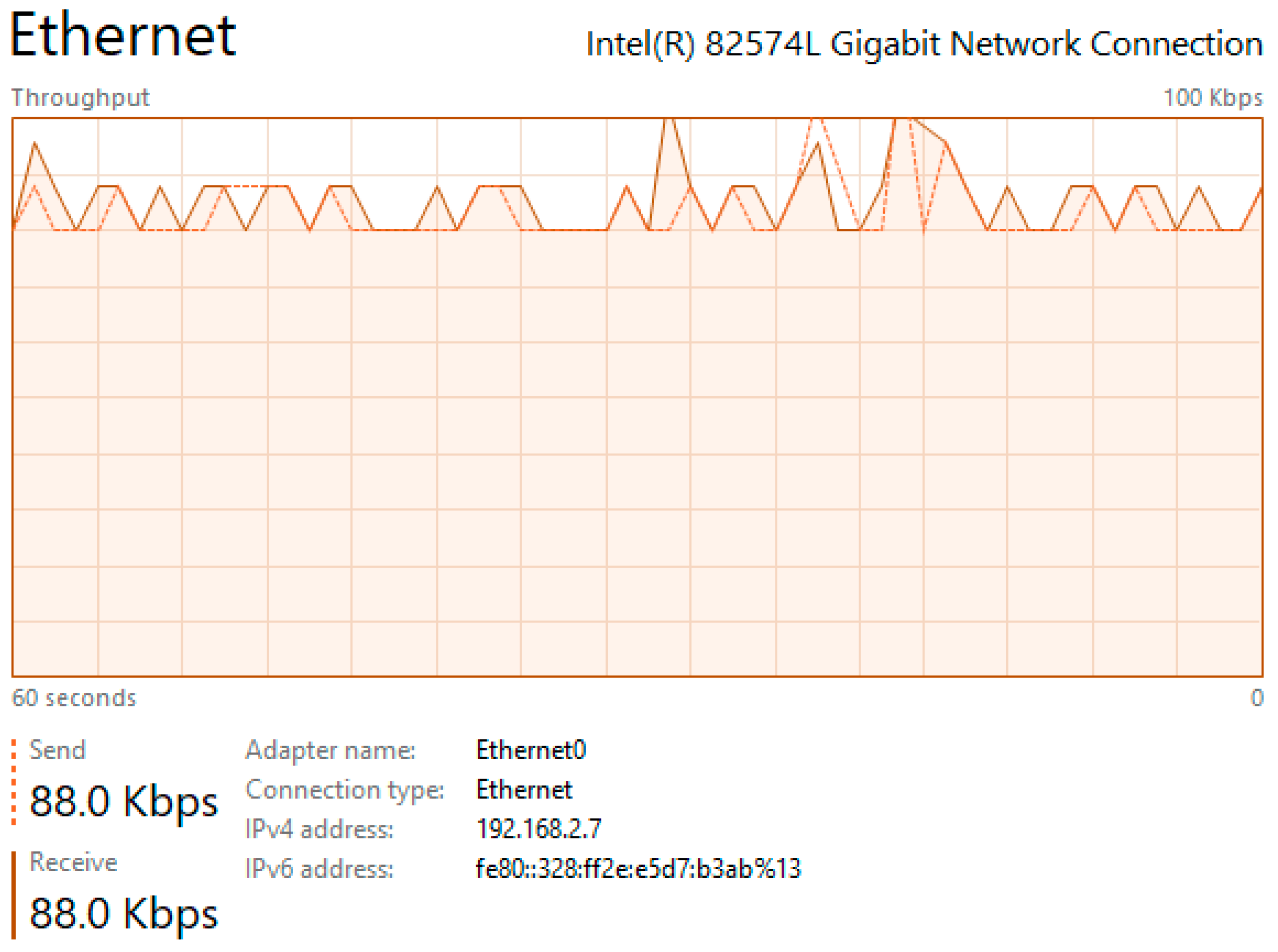
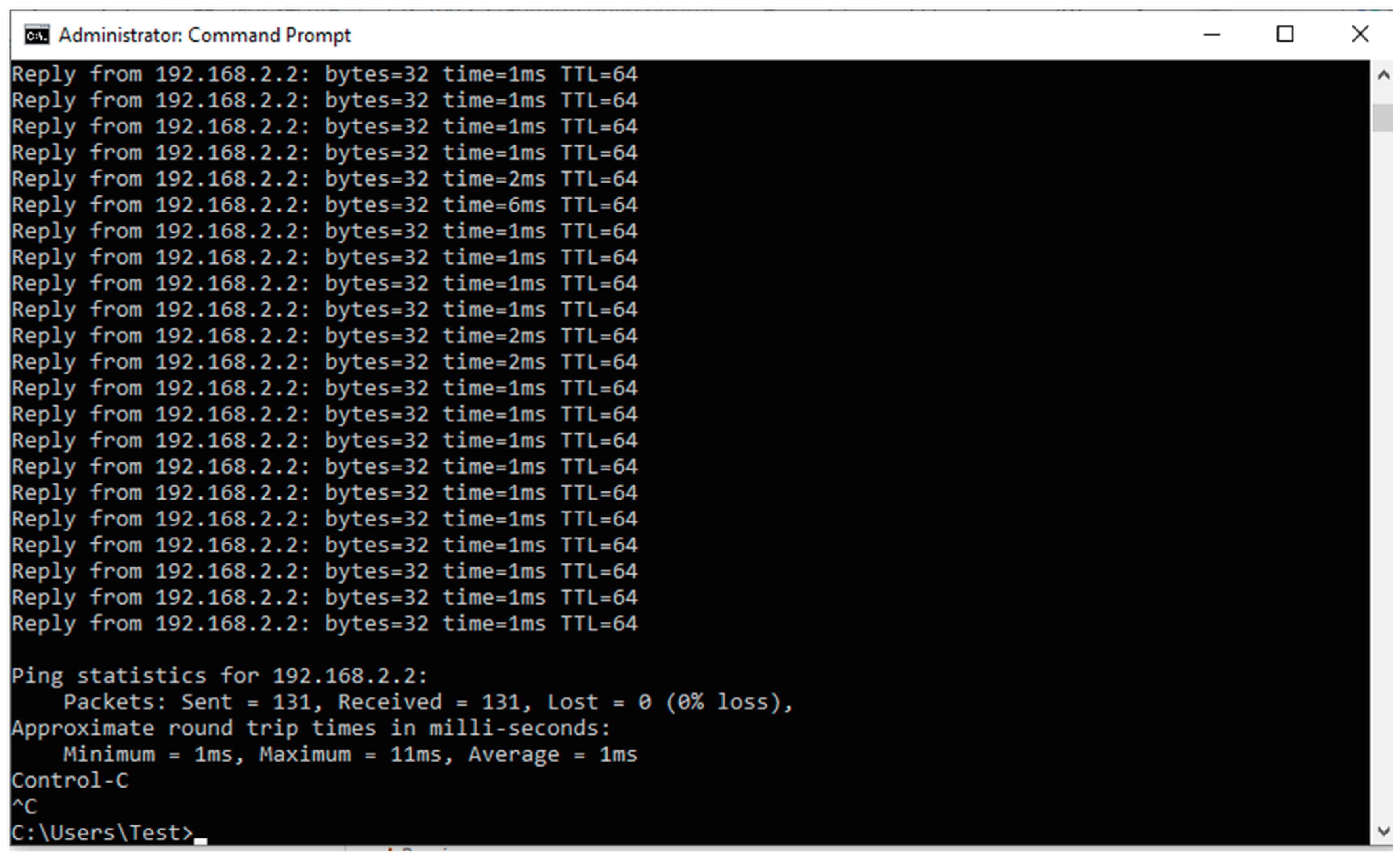
5.1.1. Results from Normal Mode of Operation
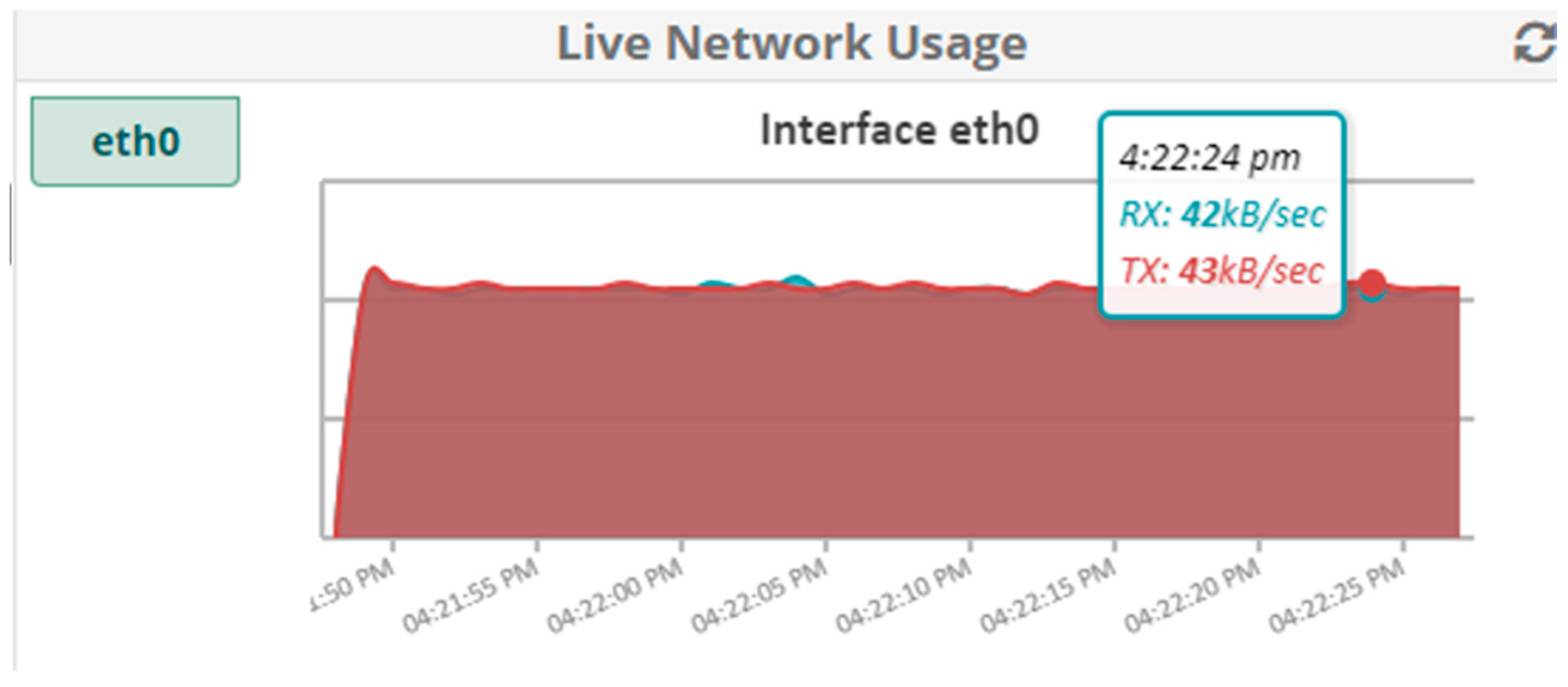
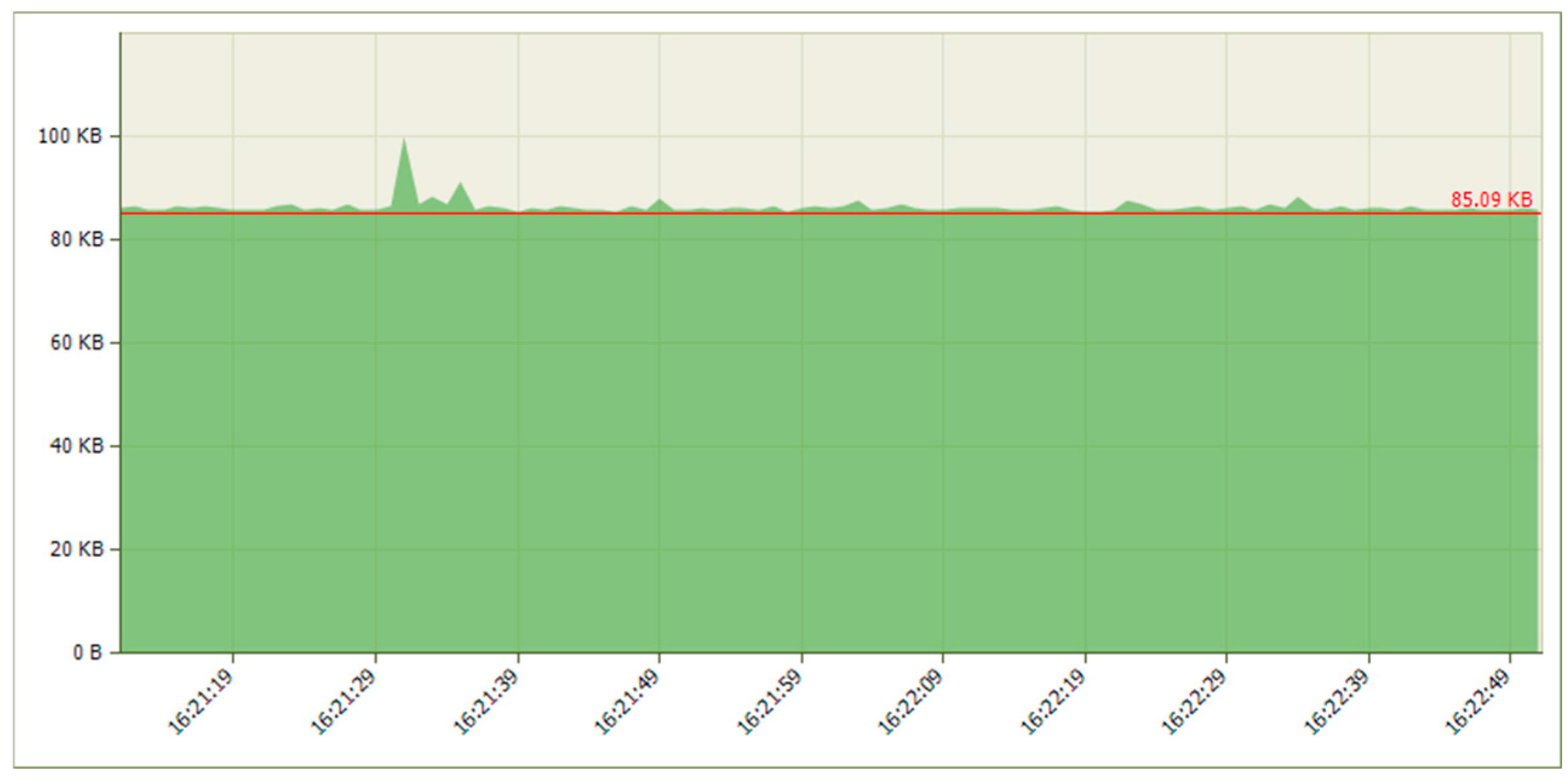
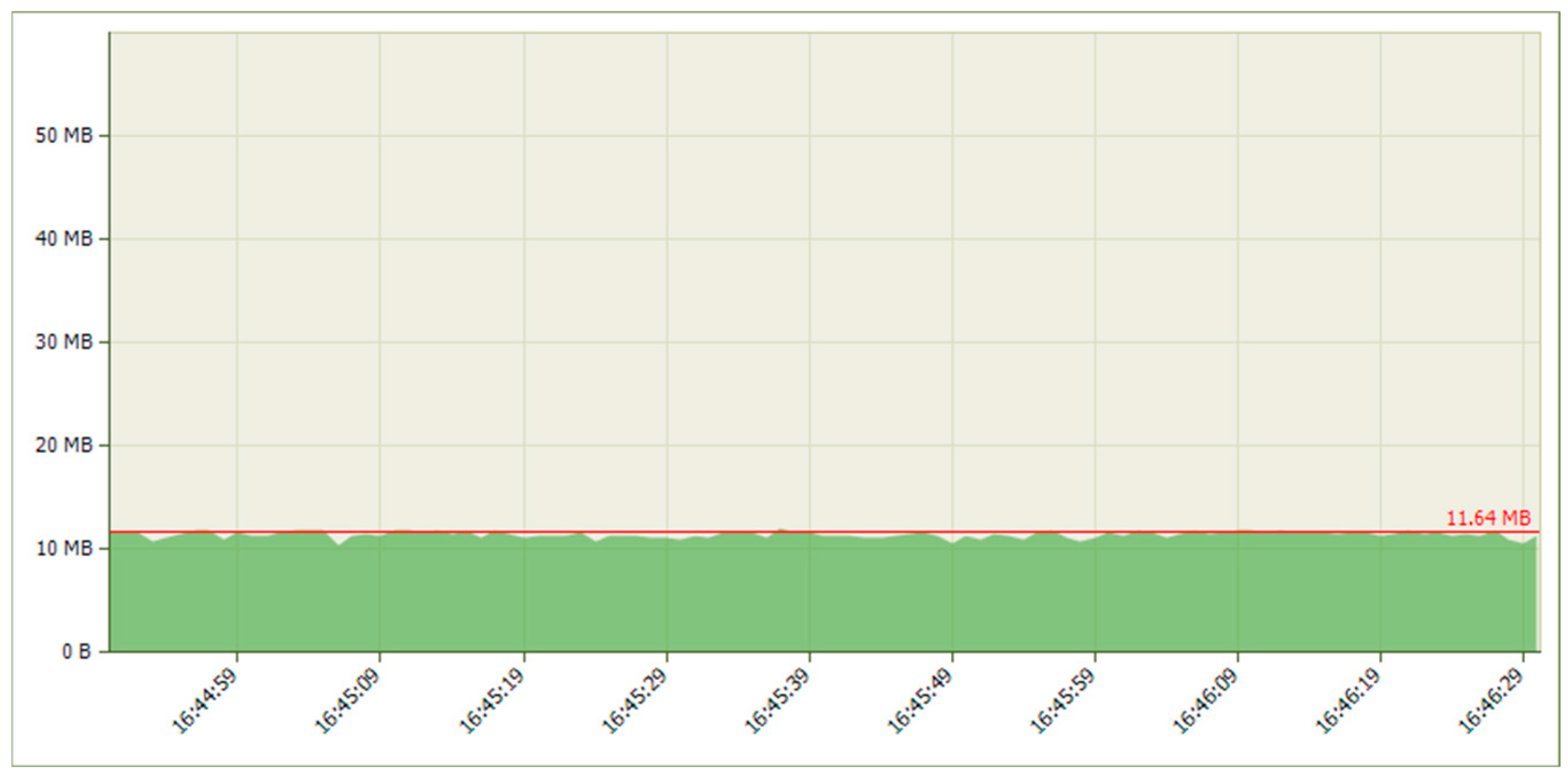
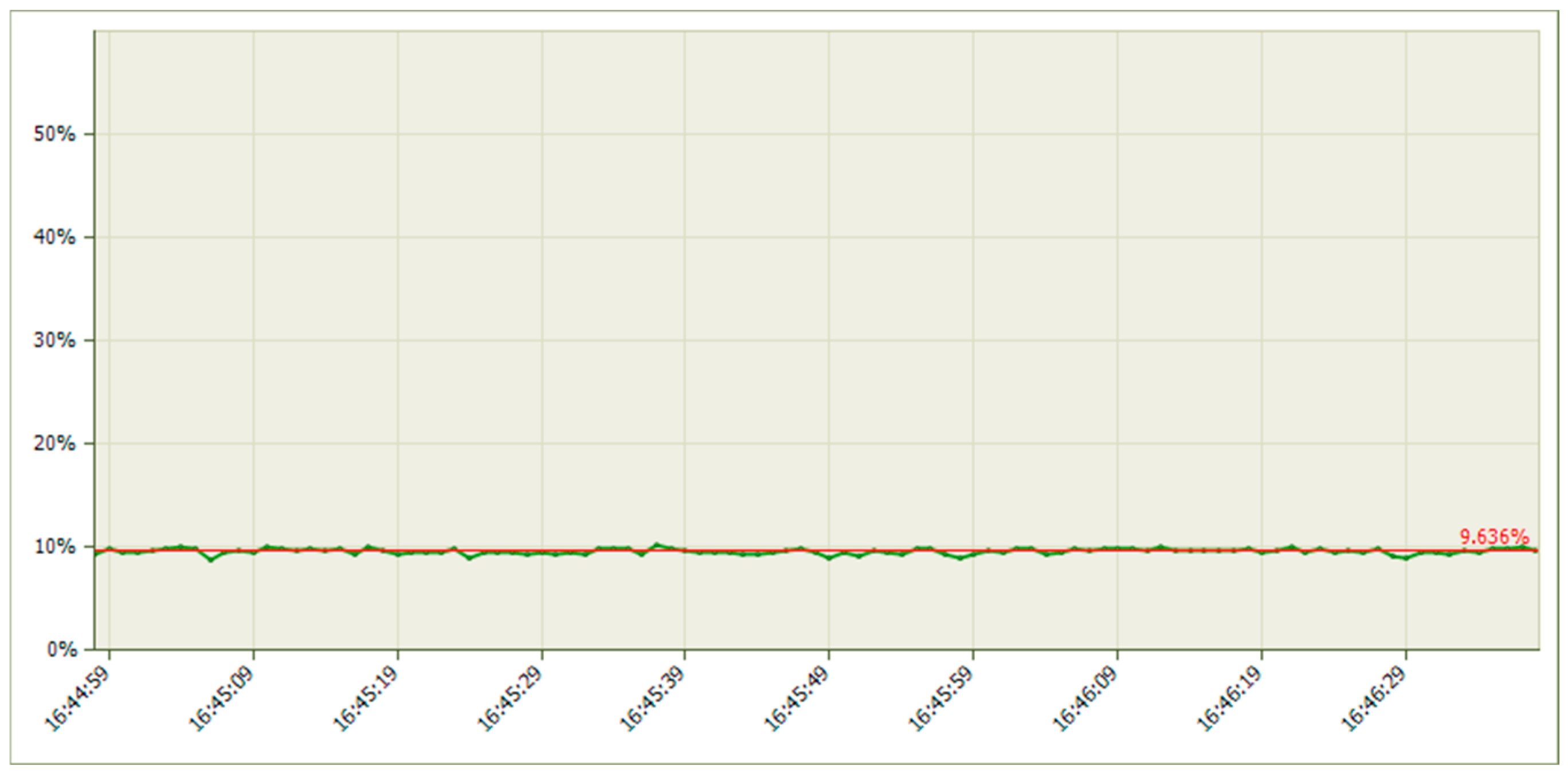
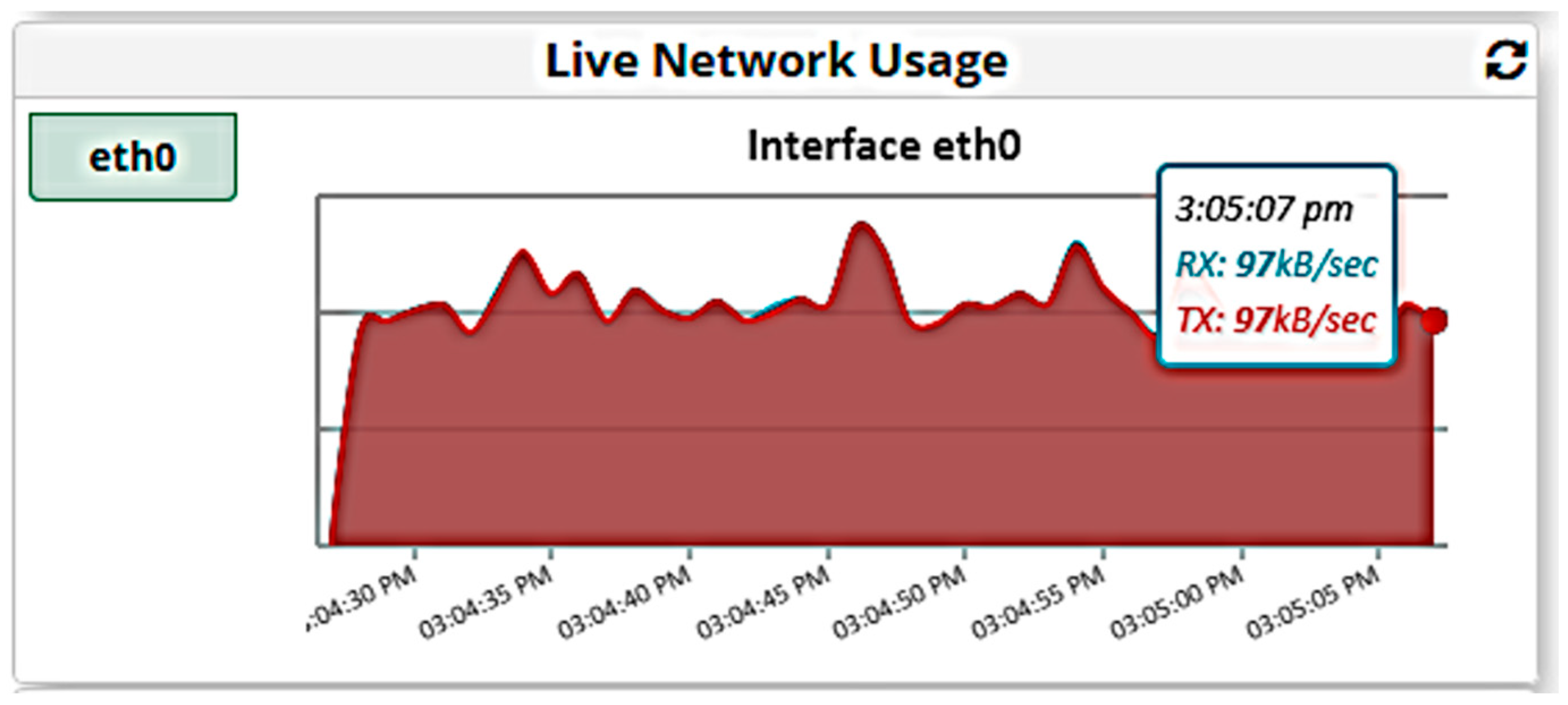
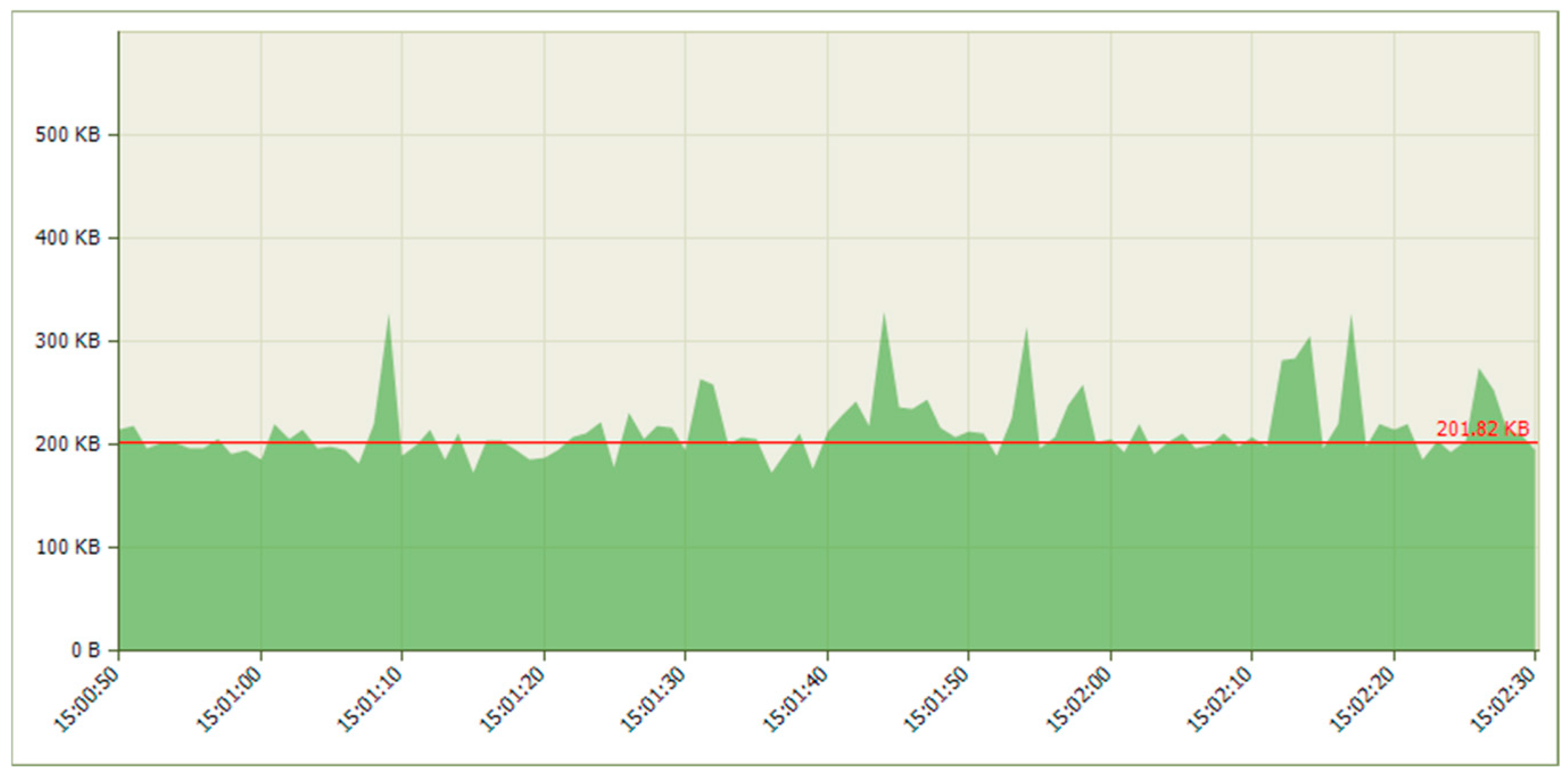
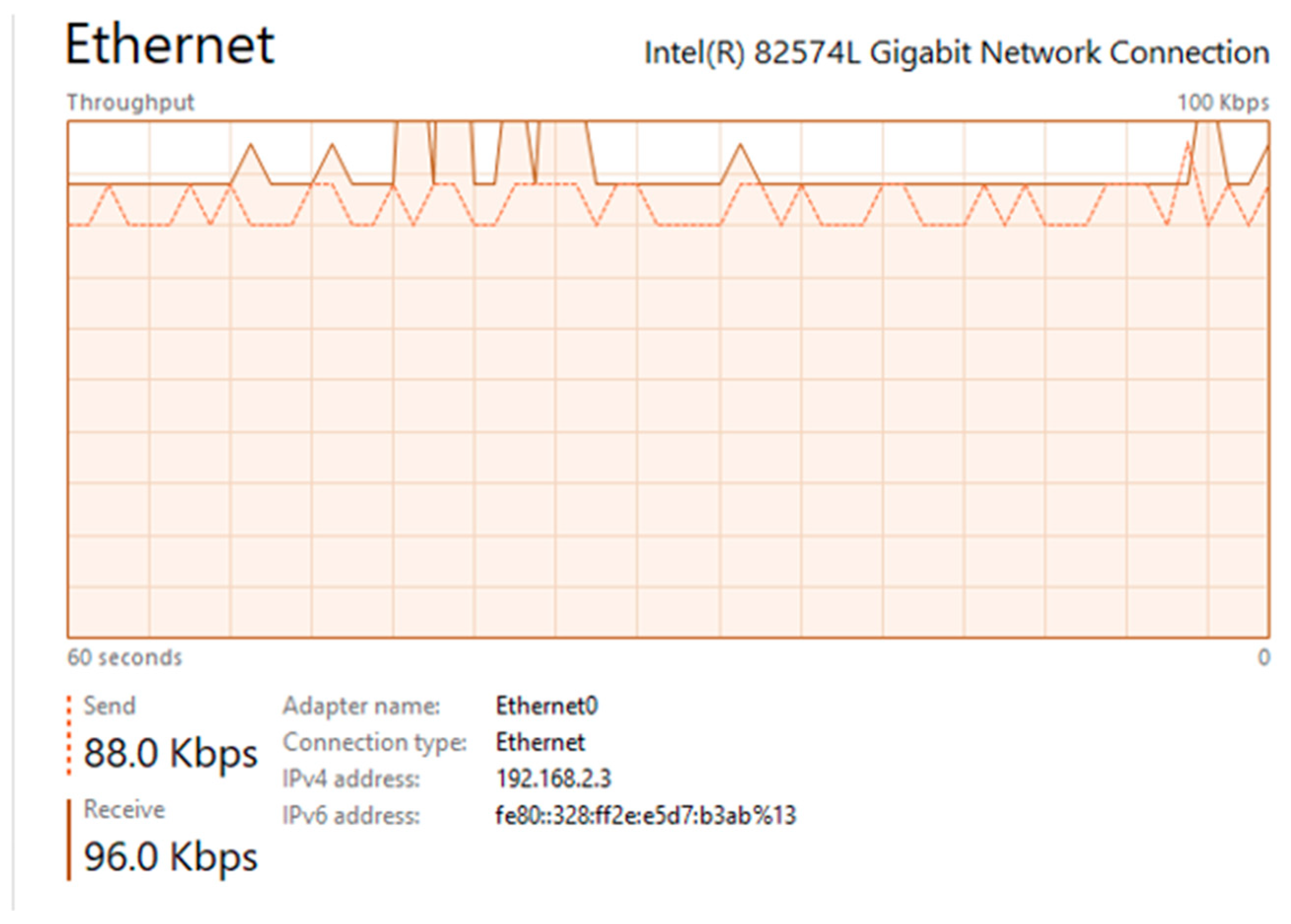
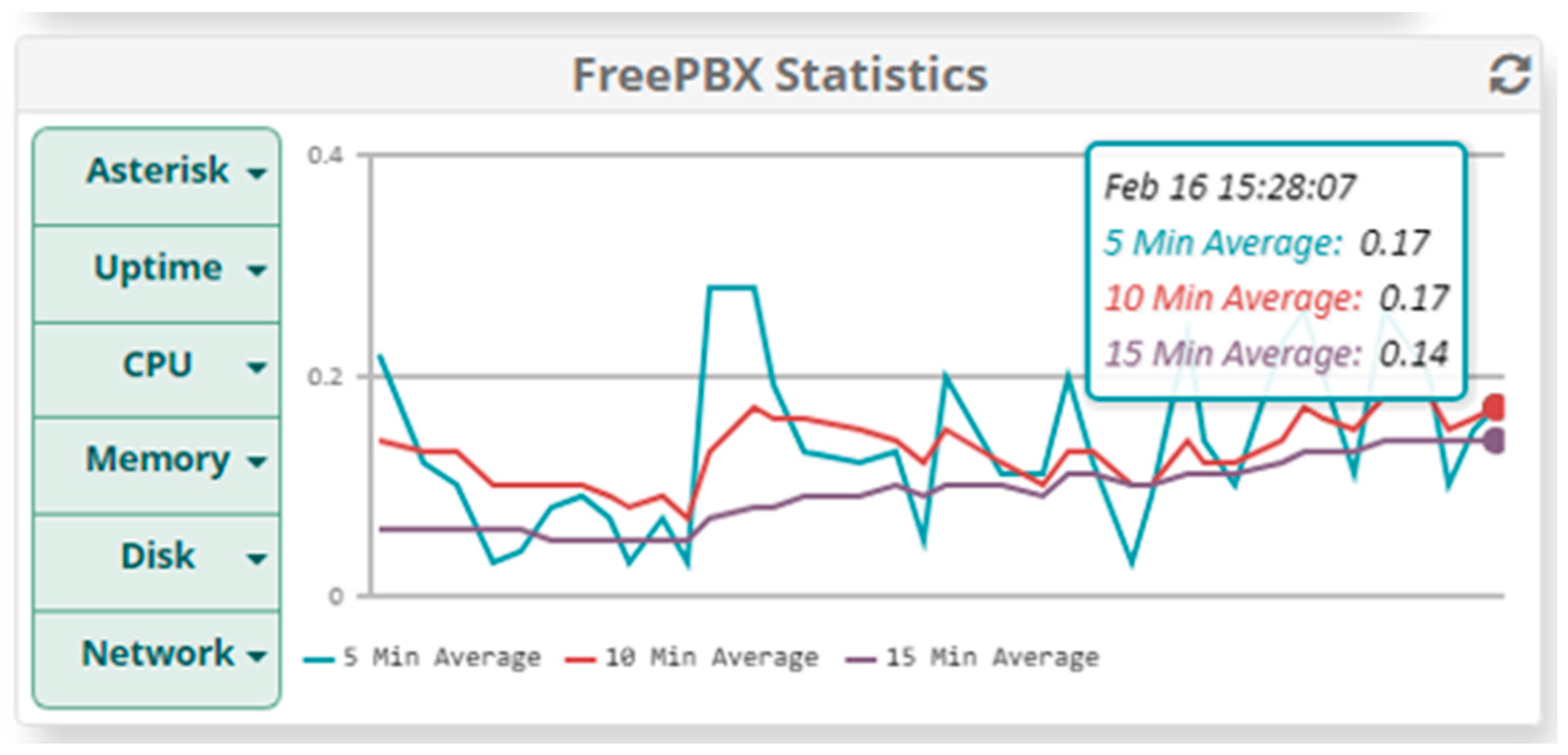
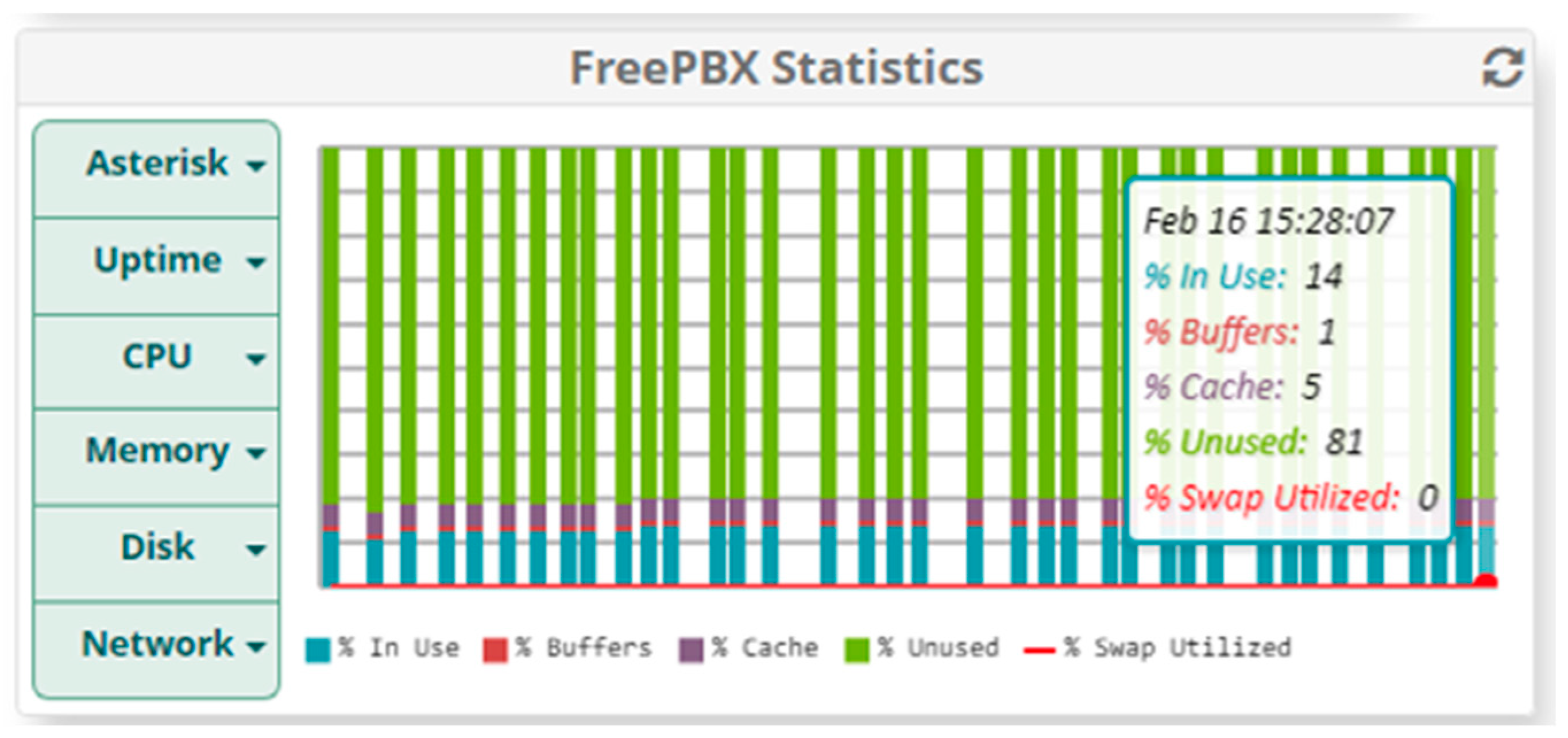
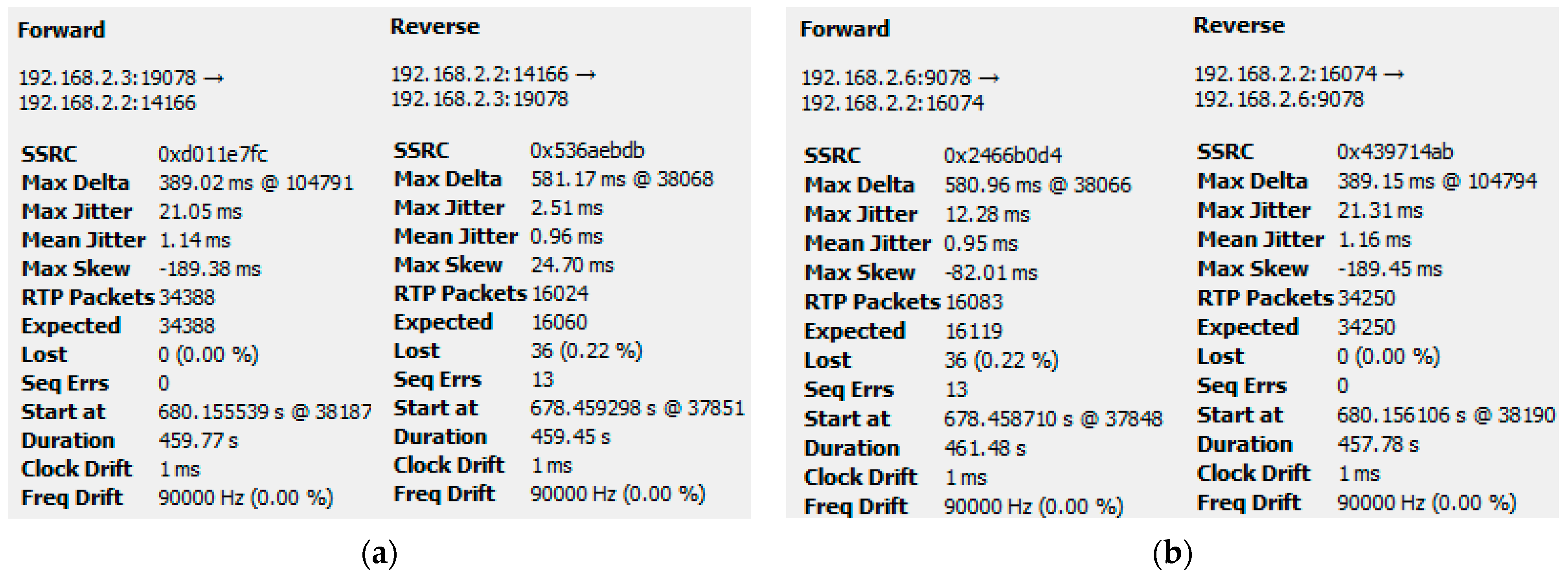
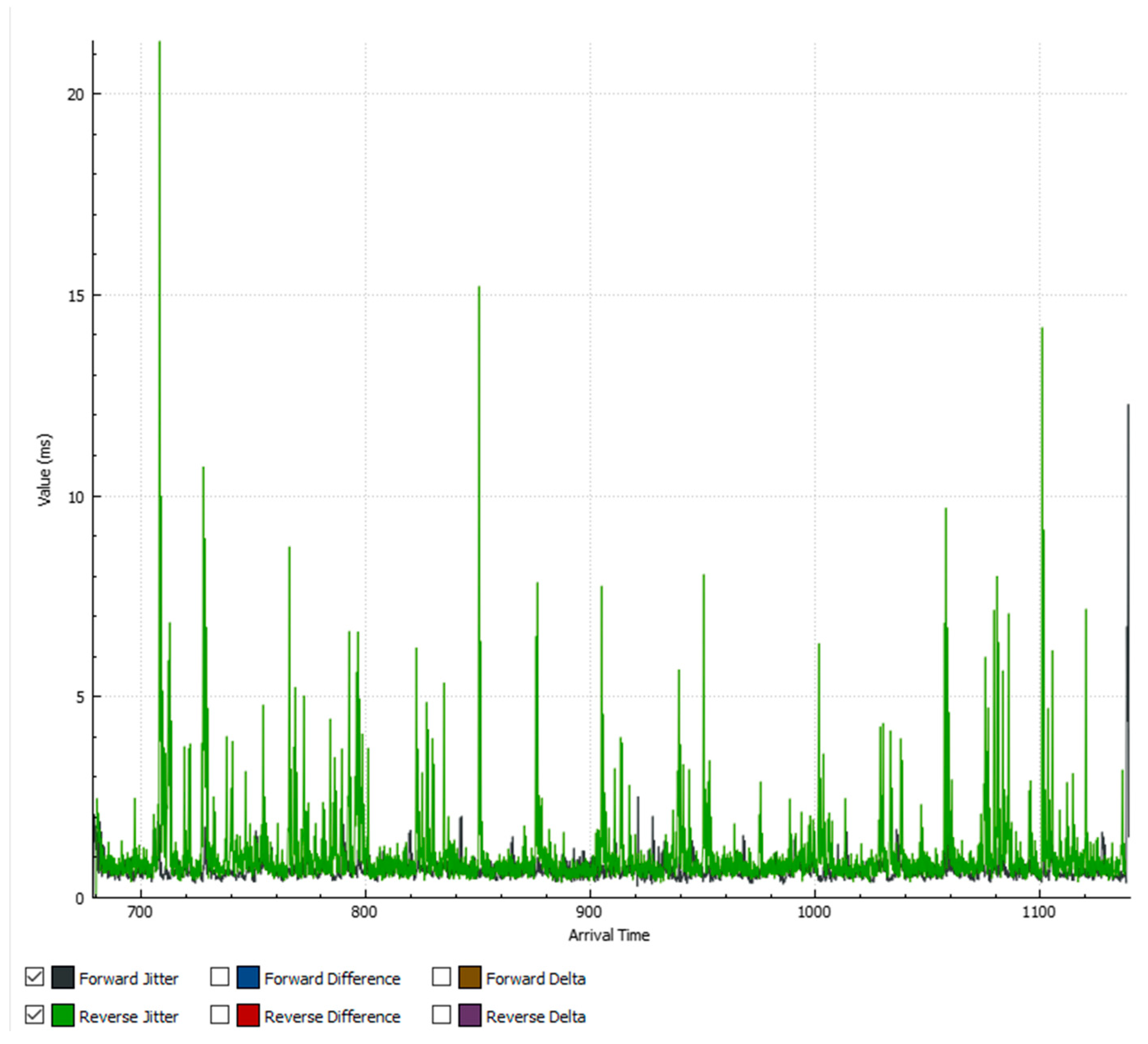
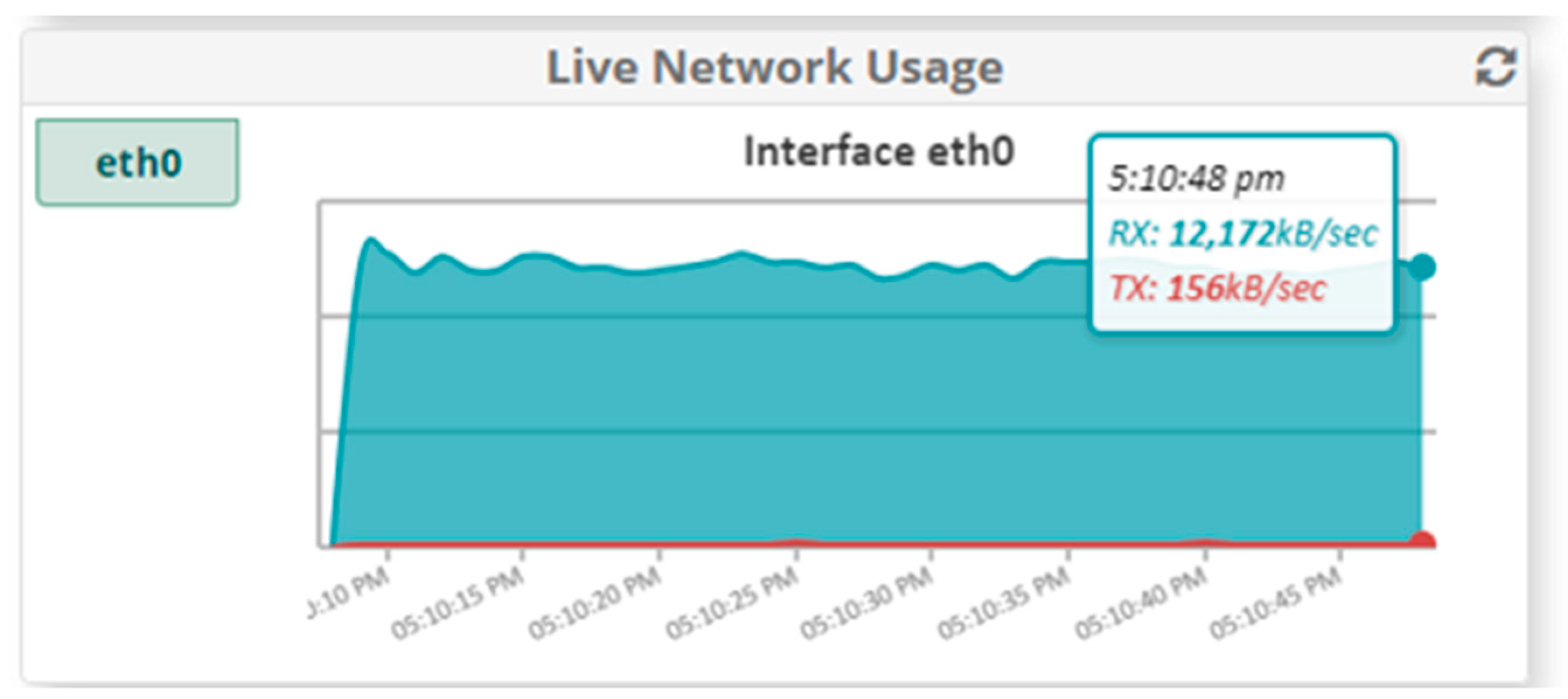
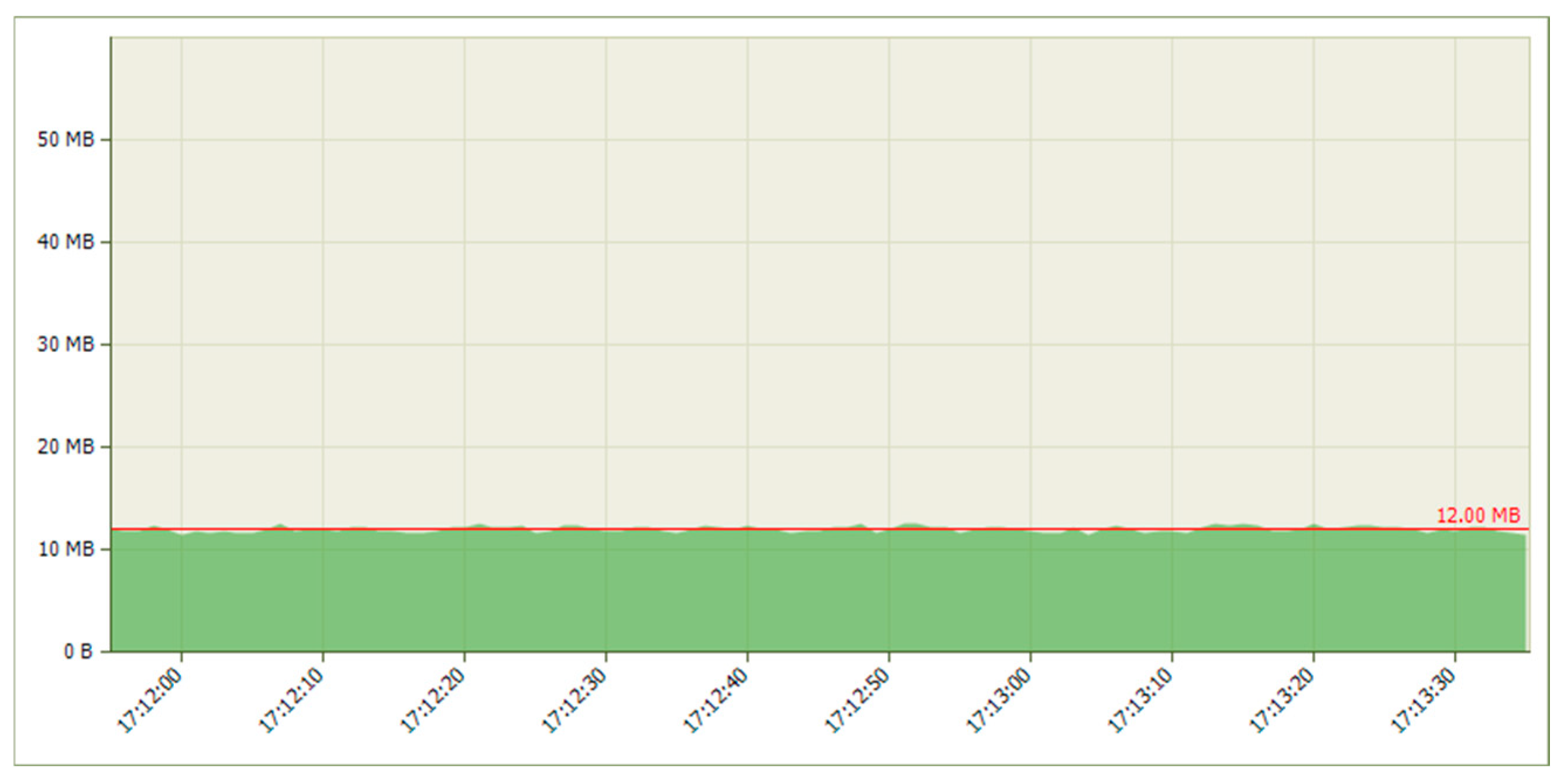
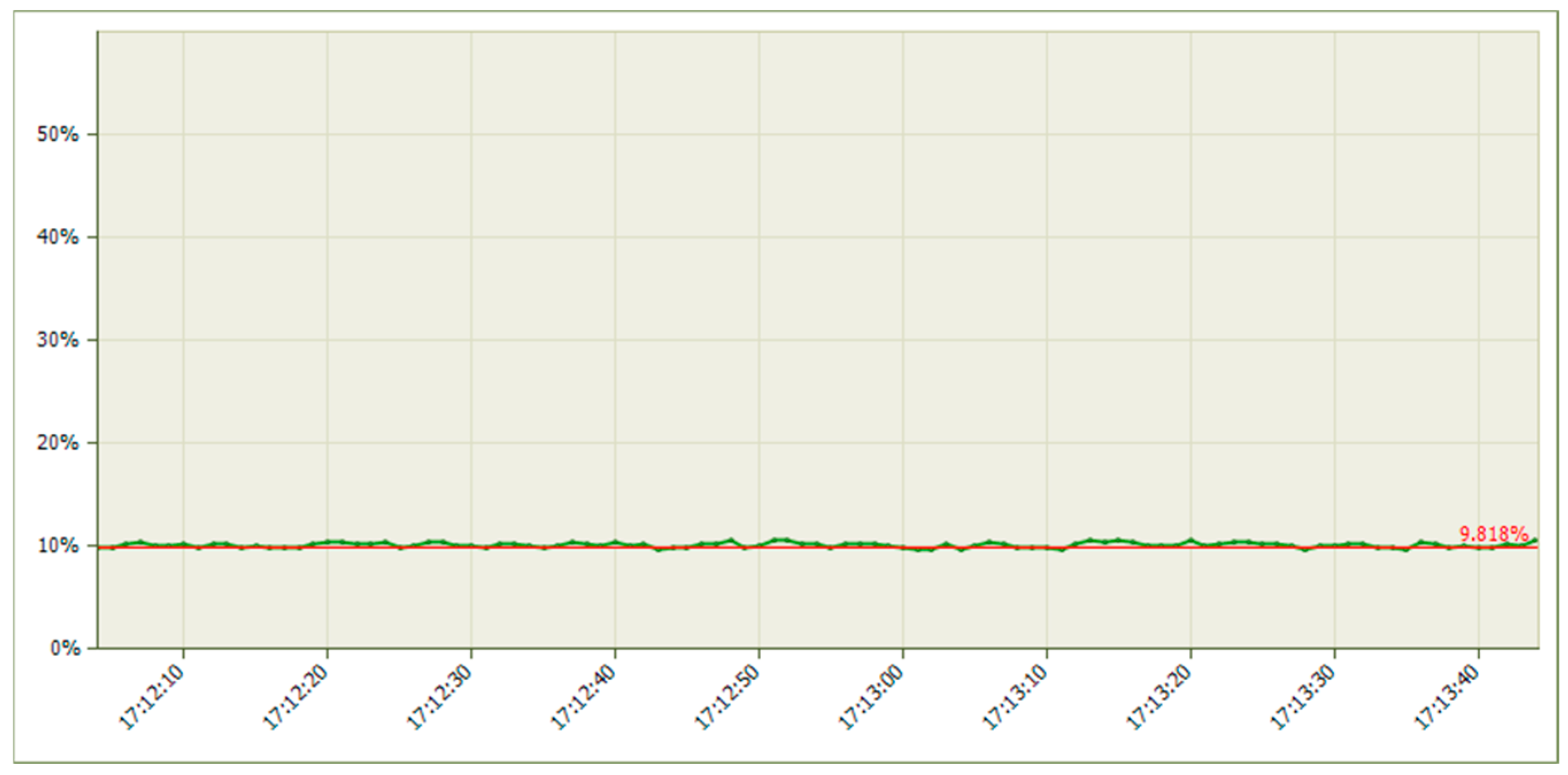
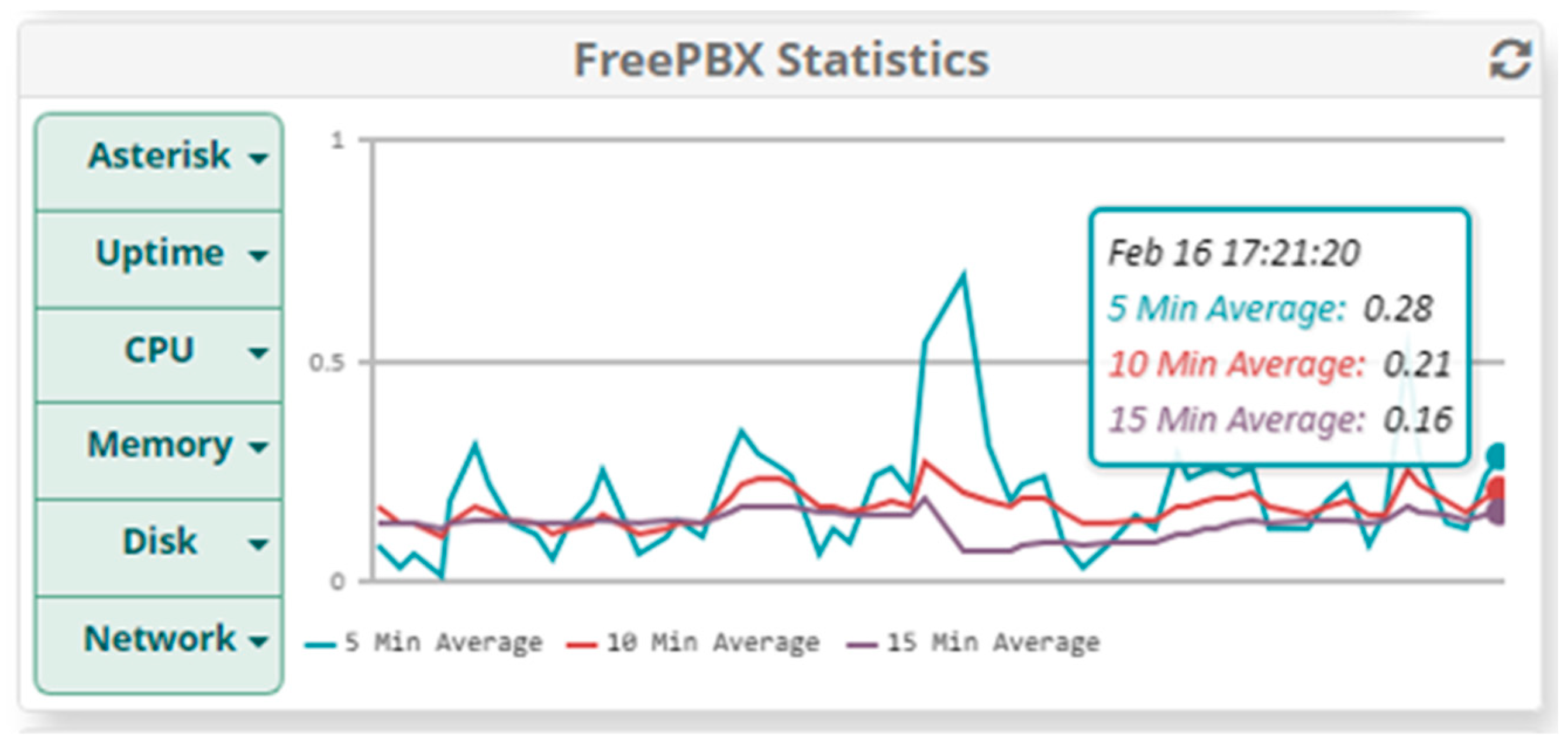
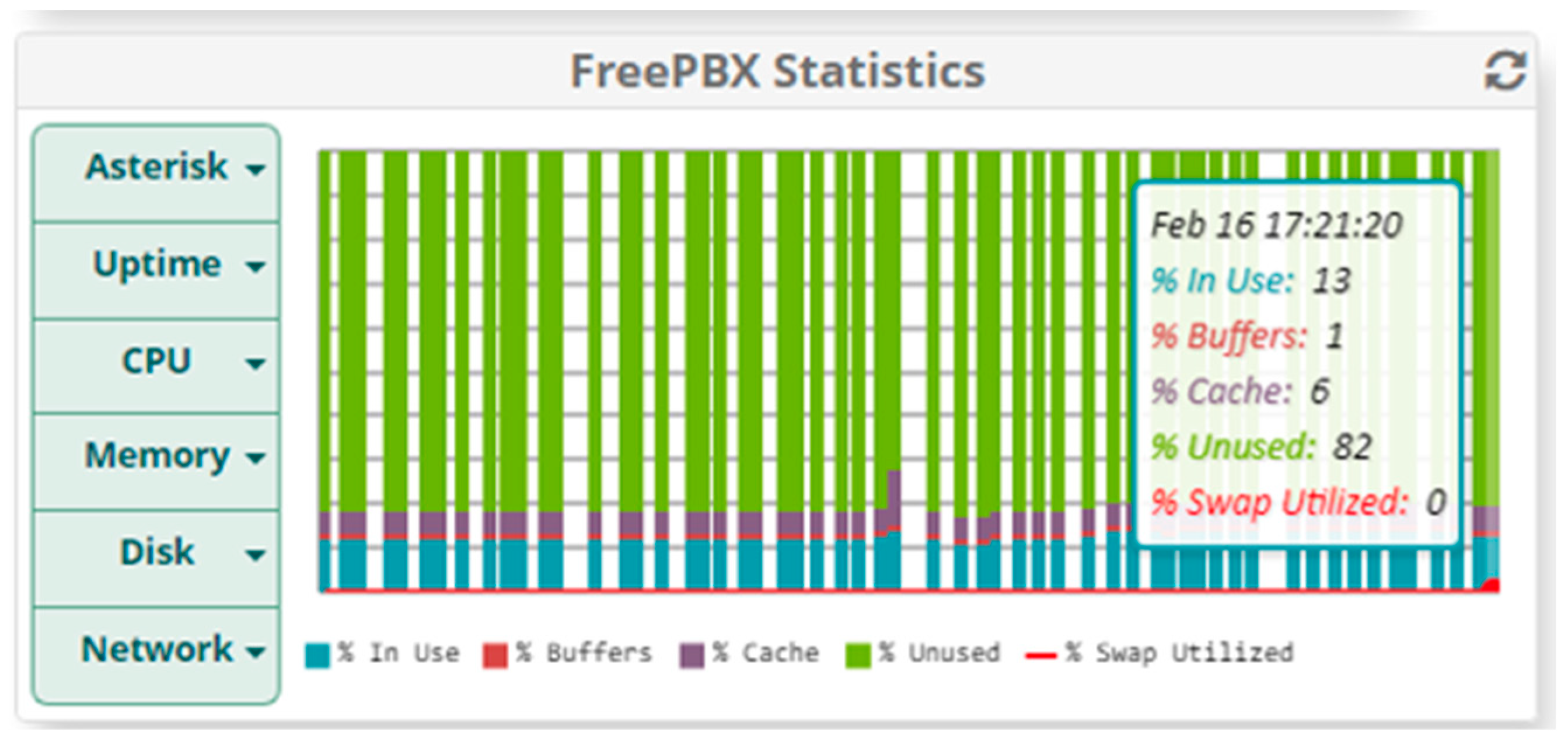
5.1.2. Results When Asterisk Is Attacked
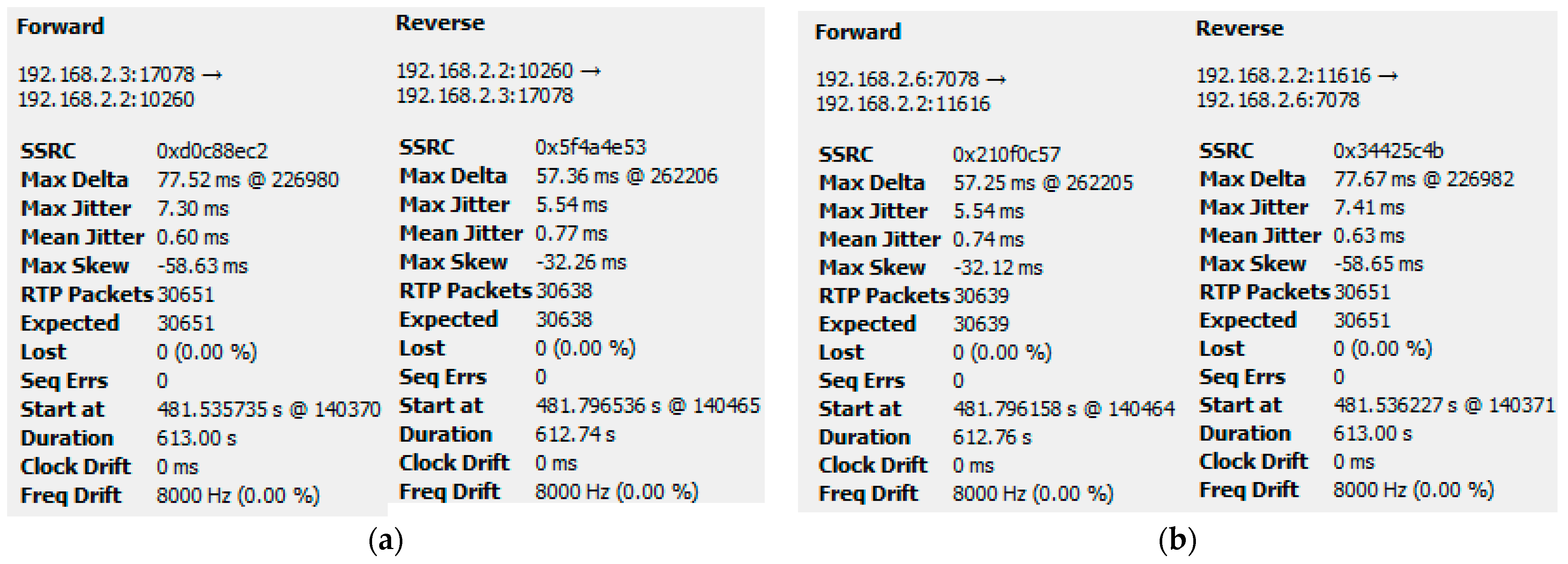
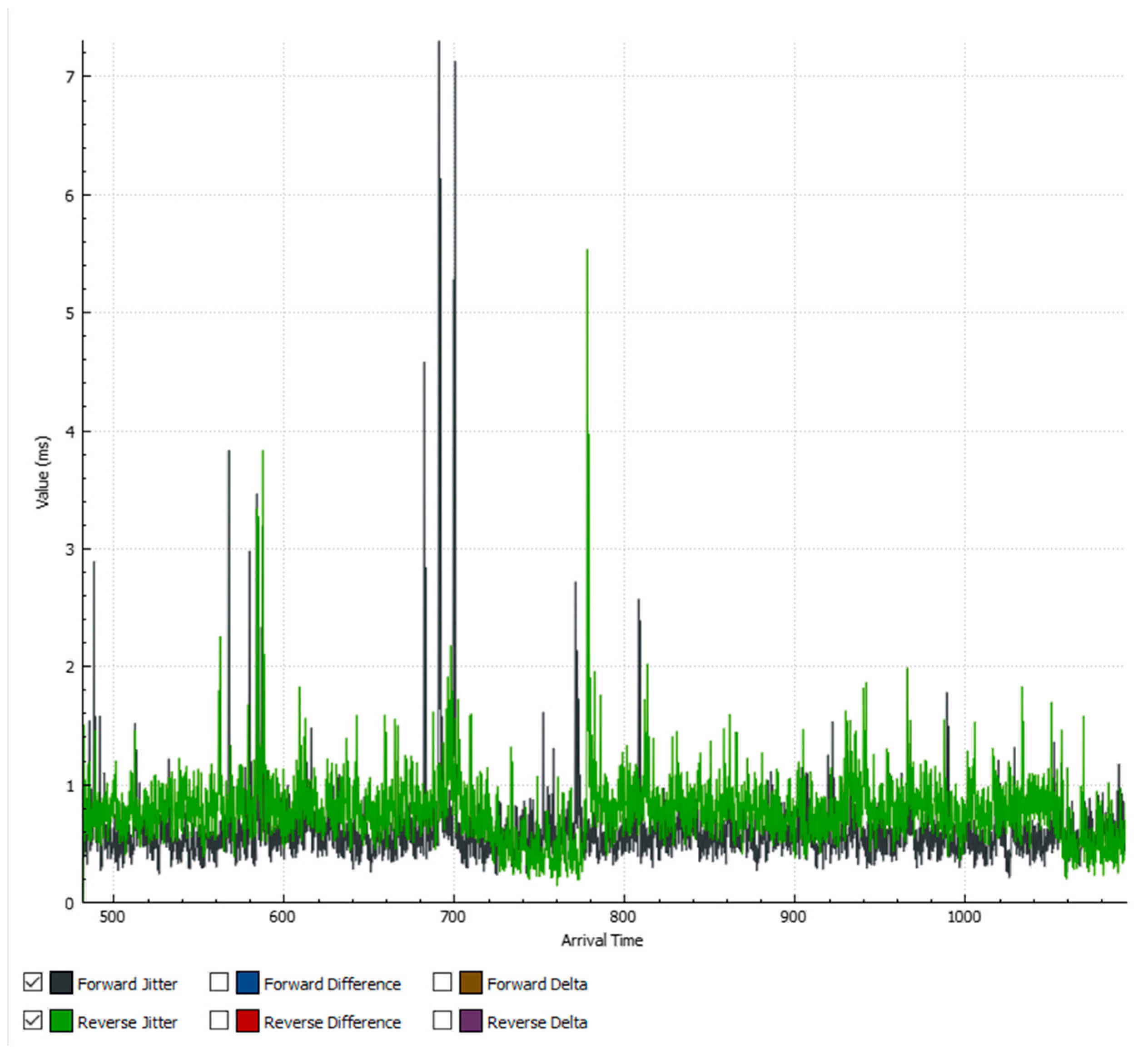
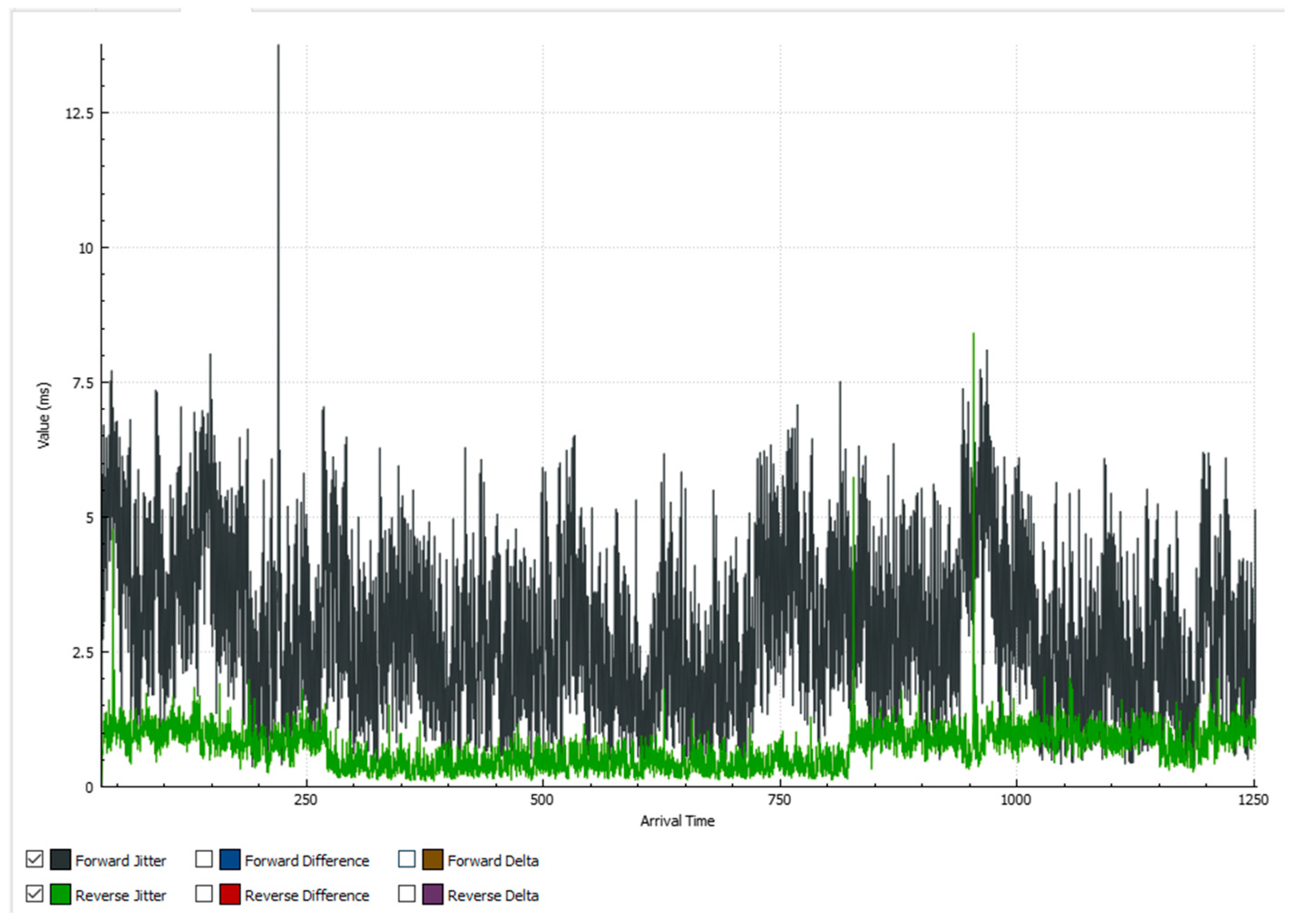
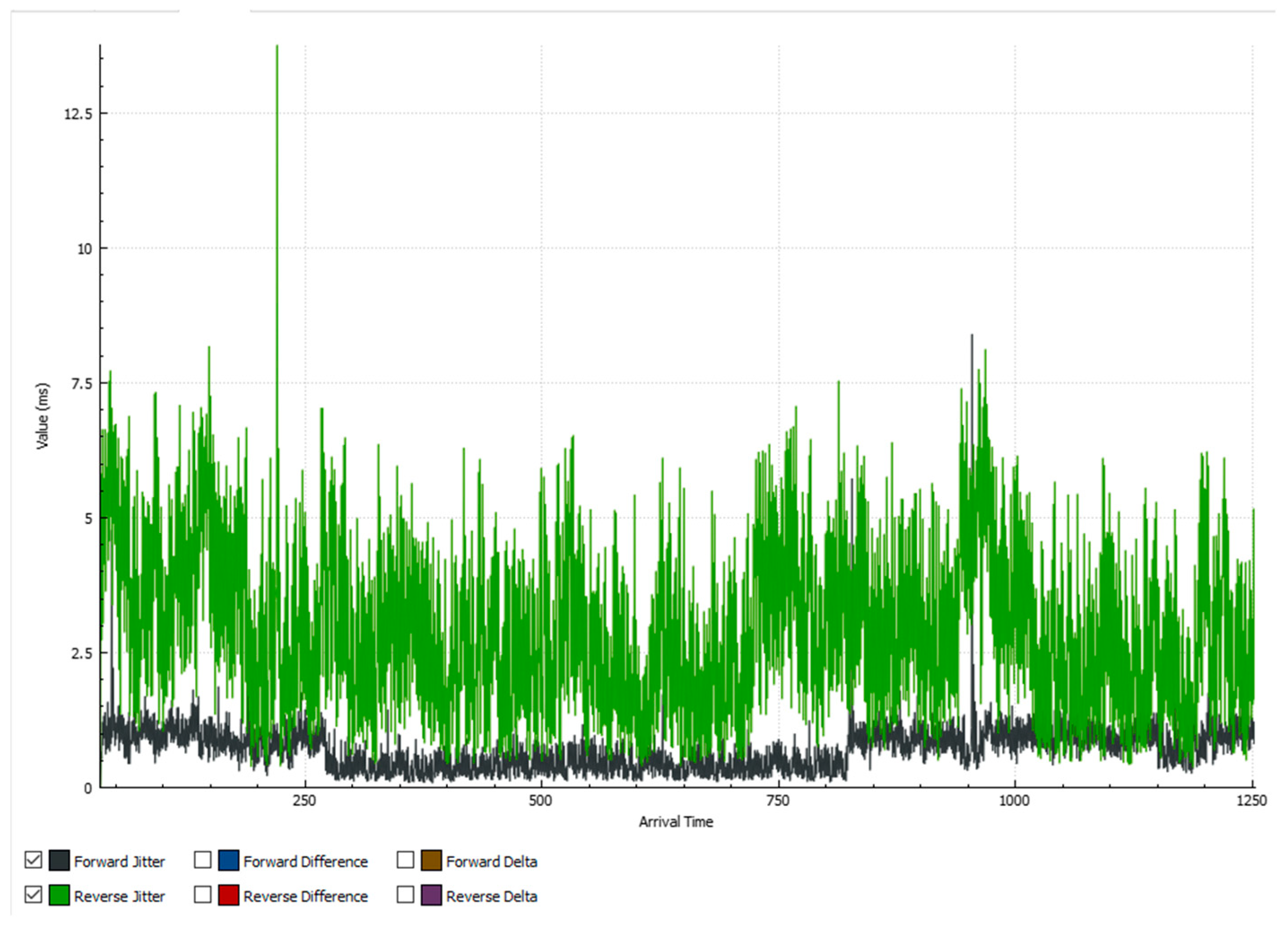
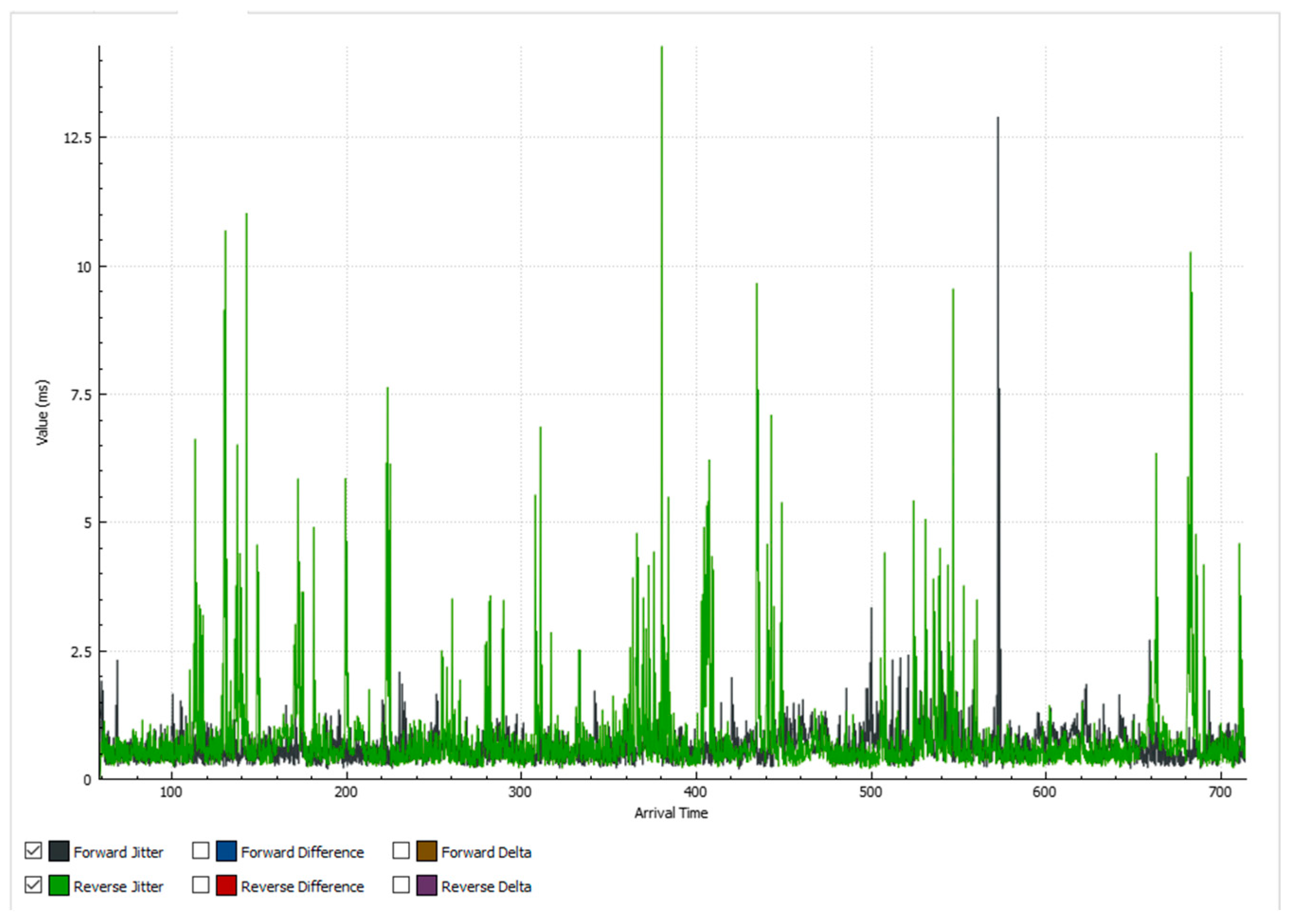
5.2. Results When Only Video Traffic Is Exchanged
5.2.1. Results from Normal Mode of Operation
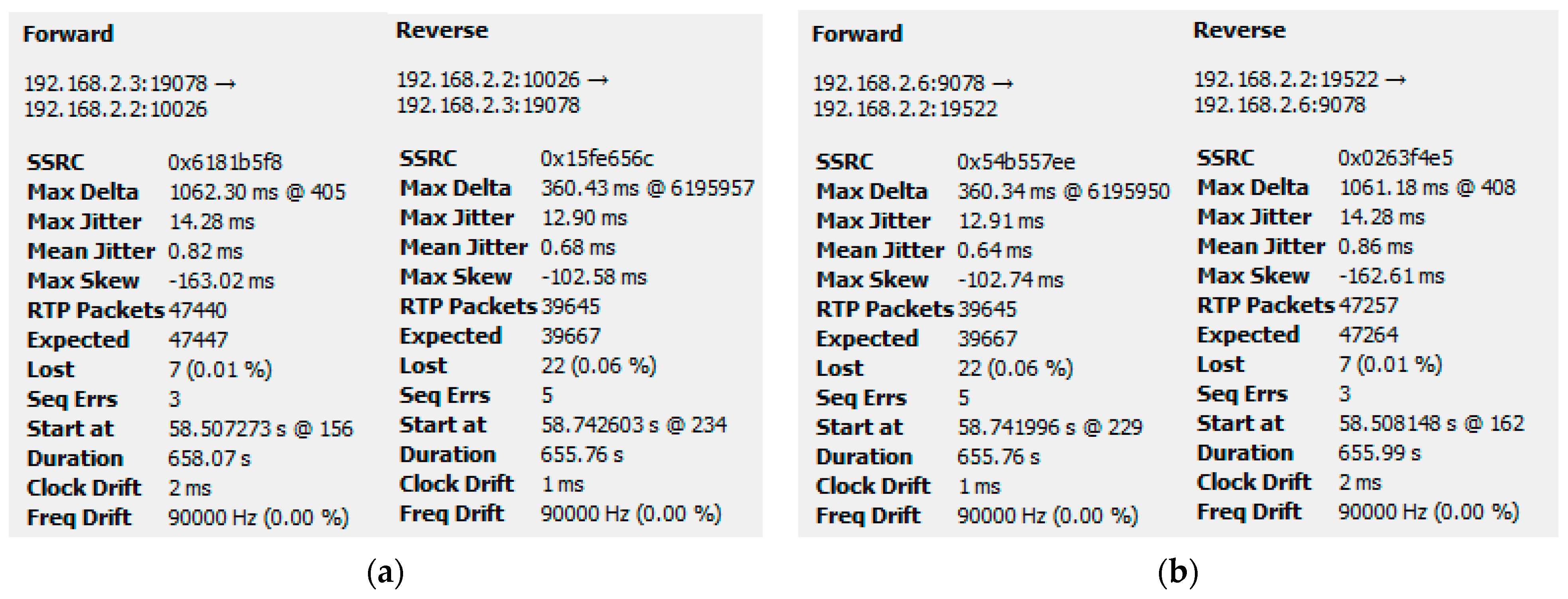
5.2.2. Results When Asterisk Is Attacked
6. Discussion
6.1. Analysis of Results When Only Voice Traffic Is Exchanged
6.2. Analysis of Results When Only Video Traffic Is Exchanged
6.3. Summary of Results
7. Limitations and Future Work
8. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| VoIP | Voise over Internet Protocol |
| UDP | User Datagram Protocol |
| DoS | Denial of service |
| TCP | Transmission Control Protocol |
| DDoS | Distributed denial of service |
| P2P | Peer to Peer |
| DHCP | Dynamic Host Configuration Protocol |
| VM | Virtual machine |
| ESW | Etherswitch |
| kB/s | Kilobytes per second |
| CPU | Central Processor Unit |
| ms | Millisecond |
| µs | Microsecond |
| RX | Receive |
| TX | Transmit |
| ICMP | Internet Control Message Protocol |
| MB | Megabyte |
| MB/s | Megabyte per second |
| RTP | Real-time Transport Protocol |
| MTU | Maximum Transmission Unit |
| PPPoE | Point-to-Point Protocol over Ethernet |
| NIC | Network interface card |
References
- Jie, Z. What Is UDP Flood? 9 August 2022. Available online: https://info.support.huawei.com/info-finder/encyclopedia/en/UDP+Flood.html (accessed on 21 February 2025).
- Shihoub, R.M.; Abdaljlil, S.A.; Laassiri, F.; Zerek, A.R. A Study Analysis of VoIP Traffic Between RIP and OSPF Using OPNET. In Proceedings of the 2023 IEEE Third International Conference on Signal, Control and Communication (SCC), Hammamet, Tunisia, 1–3 December 2023; pp. 1–6. [Google Scholar]
- Vichev, V.; Georgieva, T. Behavior of VoIP Traffic QoS Metrics in Loaded Networks. In Proceedings of the 32nd National Conference with International Participation (TELECOM), Sofia, Bulgaria, 21–22 November 2024; pp. 1–4. [Google Scholar]
- Nalla, N.R.; Sakthivel, S.; Shankar, R. Low Cost VOIP System Incorporation with Raspberry Pi. In Proceedings of the 6th International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 25–27 May 2022; pp. 94–99. [Google Scholar]
- Moravcik, M.; Kontsek, M. Proposal of VoIP infrastructure and services for academia—Case study. In Proceedings of the 17th International Conference on Emerging eLearning Technologies and Applications (ICETA), Starý Smokovec, Slovakia, 21–22 November 2019; pp. 540–545. [Google Scholar]
- Mahato, R.K. Enhancing VoIP Mobility: Dynamic Call Transfer Across 5G, 4G, and Wi-Fi Networks Using Asterisk PBX. In Proceedings of the 2024 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Tbilisi, Georgia, 24–27 June 2024; pp. 390–393. [Google Scholar]
- Grushko, S.A.; Pshenichnikov, A.P.; Malikova, E.E.; Malikov, A.Y. Virtual Asterisk IP-PBX Operation Studying and Exploring at the University. In Proceedings of the 2022 Systems of Signals Generating and Processing in the Field of on Board Communications, Moscow, Russia, 15–17 March 2022; pp. 1–5. [Google Scholar]
- Oliveira, L.P.; do Nascimento, G.A. A Systematic Literature Review on Asterisk: Teach More than VoIP Communication. In Proceedings of the 29th International Conference on Telecommunications (ICT), Toba, Indonesia, 8–9 November 2023; pp. 1–6. [Google Scholar]
- Yakubova, M.; Alipbayev, K.; Manankova, O. Research on Voice Traffic Transmitted Over an IP Network Based on IP PBX Asterisk Under the Use of Various Codecs and Cryptosystems. In Proceedings of the 8th International Conference on Cryptography, Security and Privacy (CSP), Osaka, Japan, 20–22 April 2024; pp. 106–111. [Google Scholar]
- Konshin, S.; Yakubova, M.Z.; Nishanbayev, T.N.; Manankova, O.A. Research and Development of an IP network model based on PBX Asterisk on the Opnet Modeler simulation package. In Proceedings of the 2020 International Conference on Information Science and Communications Technologies (ICISCT), Tashkent, Uzbekistan, 4–6 November 2020; pp. 1–5. [Google Scholar]
- Nedyalkov, I. Studying the Impact of Different TCP DoS Attacks on the Parameters of VoIP Streams. Telecom 2024, 5, 556–587. [Google Scholar] [CrossRef]
- Lina, B.; Merouane, M.; Abdelkarim, C. Enhancing VoIP Security: Recent Advances in Deep Learning for DoS Detection. In Proceedings of the 2nd International Conference on Electrical Engineering and Automatic Control (ICEEAC), Setif, Algeria, 12–14 May 2024; pp. 1–6. [Google Scholar]
- Suthar, D.; Rughani, P.H. A Comprehensive Study of VoIP Security. In Proceedings of the 2nd International Conference on Advances in Computing, Communication Control and Networking (ICACCCN), Greater Noida, India, 18–19 December 2020; pp. 812–817. [Google Scholar]
- Khan, H.M.A.; Inayat, U.; Zia, M.F.; Ali, F.; Jabeen, T.; Ali, S.M. Voice Over Internet Protocol: Vulnerabilities and Assessments. In Proceedings of the International Conference on Innovative Computing (ICIC), Lahore, Pakistan, 9–10 November 2021; pp. 1–6. [Google Scholar]
- Sanlioz, G.; Kara, M.; Aydin, M.A. Security and Performance Evaluation in Peer-To-Peer VoIP Communication. In Proceedings of the 2024 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Tbilisi, Georgia, 24–27 June 2024; pp. 340–343. [Google Scholar]
- Syafiuddin, N.H.; Mandala, S.; Cahyani, N.D.W. Detection Syn Flood and UDP Lag Attacks Based on Machine Learning Using AdaBoost. In Proceedings of the 2023 International Conference on Data Science and Its Applications (ICoDSA), Bandung, Indonesia, 9–10 August 2023; pp. 36–41. [Google Scholar]
- Shen, Z.Y.; Su, M.W.; Cai, Y.Z.; Tasi, M.H. Mitigating SYN Flooding and UDP Flooding in P4-based SDN. In Proceedings of the 22nd Asia-Pacific Network Operations and Management Symposium (APNOMS), Tainan, Taiwan, 8–10 September 2021; pp. 374–377. [Google Scholar]
- Patil, P.S.; Deshpande, S.L.; Hukkeri, G.S.; Goudar, R.H.; Siddarkar, P. Prediction of DDoS Flooding Attack using Machine Learning Models. In Proceedings of the Third International Conference on Smart Technologies in Computing, Electrical and Electronics (ICSTCEE), Bengaluru, India, 16–17 December 2022; pp. 1–6. [Google Scholar]
- Tego, E.; Attanasio, V.; Matera, F. GNS-3 Emulation Platform to Study Wide Area Network Performance in Contexts Close to Reality. In Proceedings of the 2022 AEIT International Annual Conference (AEIT), Rome, Italy, 3–5 October 2022; pp. 1–6. [Google Scholar]
- Getting Started with GNS3. Available online: https://docs.gns3.com/docs/ (accessed on 22 February 2025).
- Dumitrache, C.; Predusca, G.; Gavriloaia, G.; Angelescu, N.; Circiumarescu, D.; Puchianu, D.C. Comparative analysis of routing protocols using GNS3, Wireshark and IPerf3. In Proceedings of the 14th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Ploiesti, Romania, 30 June–1 July 2022; pp. 1–6. [Google Scholar]
- Tashev, T.D.; Marinov, M.B.; Arnaudov, D.D.; Monov, V.V. Computer simulations for determining of the upper bound of throughput of LPF-algorithm for crossbar switch. AIP Conf. Proc. 2022, 2505, 080030. [Google Scholar]
- Tashev, T.D.; Alexandrov, A.K.; Arnaudov, D.D.; Tasheva, R.P. Large-Scale Computer Simulation of the Performance of the Generalized Nets Model of the LPF-algorithm. In Large-Scale Scientific Computing. LSSC 2021. Lecture Notes in Computer Science; Lirkov, I., Margenov, S., Eds.; Springer: Cham, Switzerland, 2022; Volume 13127. [Google Scholar]
- Hensel, S.; Marinov, M.B.; Elabed, A.E. Simulation Environment for the Evaluation of LiDAR Odometry Algorithms. In Proceedings of the XXXIII International Scientific Conference Electronics (ET), Sozopol, Bulgaria, 17–19 September 2024; pp. 1–5. [Google Scholar]
- Sapundzhi, F.I. Computer modelling and optimization of the structure-activity relationship by using surface fitting methods. Bulg. Chem. Commun. 2019, 51, 569–579. [Google Scholar]
- Sapundzhi, F.; Chikalov, A.; Georgiev, S.; Georgiev, I. Predictive Modeling of Photovoltaic Energy Yield Using an ARIMA Approach. Appl. Sci. 2024, 14, 11192. [Google Scholar] [CrossRef]
- Kravets, O.J.; Aksenov, I.A.; Redkin, Y.V.; Rahman, P.A.; Kochegarov, M.V.; Gorshkov, A.V.; Sorokin, S.A. Modeling of neural network monitoring agent to predict traffic spikes and agent training. Int. J. Inf. Technol. Secur. 2024, 16, 49–56. [Google Scholar] [CrossRef]
- Zelmanov, S.S.; Krylov, V.V. Computer simulation of strength testing of an object based on signal shaped resources. Int. J. Inf. Technol. Secur. 2023, 15, 59–68. [Google Scholar] [CrossRef]
- Tim, S.; Christina, H. End-to-End QoS Network Design: Quality of Service in LANs, WANs, and VPNs. In Part of the Networking Technology Series; Cisco Press: Indianapolis, IN, USA, 2004; ISBN 1-58705-176-1. [Google Scholar]
- Cisco-Understanding Delay in Packet Voice Networks, White Paper. Available online: https://www.cisco.com/c/en/us/support/docs/voice/voice-quality/5125-delay-details.html (accessed on 22 February 2025).
- Wireshark. Available online: https://www.wireshark.org/docs/wsug_html_chunked/ (accessed on 22 February 2025).
- Capsa Free Network Analyzer. Available online: https://www.colasoft.com/capsa-free/ (accessed on 22 February 2025).
- hping3 Tool Documentation. Available online: https://www.kali.org/tools/hping3/ (accessed on 22 February 2025).
- Nmap Network Scanning the Official Nmap Project Guide to Network Discovery and Security Scanning. Available online: https://nmap.org/book/toc.html (accessed on 22 February 2025).
- Dimitrov, W.; Spasov, K.; Trenchev, I.; Syarova, S. Complexity Assessment of Research Space for Smart City Cybersecurity. IFAC-PapersOnLine 2022, 55, 1–6. [Google Scholar] [CrossRef]
- Jekov, B.; Dimitrov, W.; Panayotova, G.S.; Kovatcheva, E. Intelligent protection of Internet of things systems. In Proceedings of the 2022 International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME), Maldives, Maldives, 16–18 November 2022; pp. 1–4. [Google Scholar]
- Dimitrov, W.; Dimitrov, G.; Spassov, K.; Petkova, L. Vulnerabilities Space and the Superiority of Hackers. In Proceedings of the 2021 International Conference Automatics and Informatics (ICAI), Varna, Bulgaria, 30 September–2 October 2021; pp. 433–436. [Google Scholar]
- Chithra, P.L.; Aparna, R. Blockchain enabled dual level security scheme with spiral shuffling and hashing technique for secret video transmission. Int. J. Inf. Technol. Secur. 2023, 15, 97–108. [Google Scholar] [CrossRef]
- Rakesh, V.S.; Vasanthakumar, G.U. Evaluation of supervised classification approach for DDoS threat detection in Software Defined Networks. Int. J. Inf. Technol. Secur. 2024, 16, 95–103. [Google Scholar]
- Diana, L.; Dini, P.; Paolini, D. Overview on Intrusion Detection Systems for Computers Networking Security. Computers 2025, 14, 87. [Google Scholar] [CrossRef]
- Zhang, T.; Tang, X.; Wang, J.; Liu, J. Network Security Management in Heterogeneous Networks. Electronics 2025, 14, 568. [Google Scholar] [CrossRef]
- Mao, J.; Yang, X.; Hu, B.; Lu, Y.; Yin, G. Intrusion Detection System Based on Multi-Level Feature Extraction and Inductive Network. Electronics 2025, 14, 189. [Google Scholar] [CrossRef]
- Alshdadi, A.A.; Almazroi, A.A.; Ayub, N.; Lytras, M.D.; Alsolami, E.; Alsubaei, F.S. Big Data-Driven Deep Learning Ensembler for DDoS Attack Detection. Future Internet 2024, 16, 458. [Google Scholar] [CrossRef]
- Ni, T.; Lan, G.; Wang, J.; Zhao, Q.; Xu, W. Eavesdropping mobile app activity via radio-frequency energy harvesting. In Proceedings of the 32nd USENIX Conference on Security Symposium (SEC ’23), Anaheim, CA, USA, 9–11 August 2023; USENIX Association: Berkeley, CA, USA, 2023; pp. 3511–3528. [Google Scholar]
- Spiekermann, D.; Eggendorfer, T.; Keller, J. Deep Learning for Network Intrusion Detection in Virtual Networks. Electronics 2024, 13, 3617. [Google Scholar] [CrossRef]
- Grossi, M.; Alfonsi, F.; Prandini, M.; Gabrielli, A. Increasing the Security of Network Data Transmission with a Configurable Hardware Firewall Based on Field Programmable Gate Arrays. Future Internet 2024, 16, 303. [Google Scholar] [CrossRef]
- Li, J.; Zhou, H.; Wu, S.; Luo, X.; Wang, T.; Zhan, X.; Ma, X. FOAP: Fine-Grained Open-World Android App Fingerprinting. In Proceedings of the 31st USENIX Security Symposium, Security, Boston, MA, USA, 10–12 August 2022; pp. 1579–1596. [Google Scholar]
- Jiao, J.; Li, W.; Guo, D. The Vulnerability Relationship Prediction Research for Network Risk Assessment. Electronics 2024, 13, 3350. [Google Scholar] [CrossRef]
- Liu, J. Design of Computer Network Security Management System based on Neural Network Technology. In Proceedings of the 2024 International Conference on Integrated Circuits and Communication Systems (ICICACS), Raichur, India, 23–24 February 2024; pp. 1–5. [Google Scholar]
- Patel, S.; Christian, P.; Mistry, K.; Raj, K.; Raithatha, H. Enhancing Network Security with Advanced Network Scanning Tools. In Proceedings of the 2024 Parul International Conference on Engineering and Technology (PICET), Vadodara, India, 3–4 May 2024; pp. 1–8. [Google Scholar]







Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nedyalkov, I. Studying the Impact of a UDP DoS Attack on the Parameters of VoIP Voice and Video Streams. Future Internet 2025, 17, 139. https://doi.org/10.3390/fi17040139
Nedyalkov I. Studying the Impact of a UDP DoS Attack on the Parameters of VoIP Voice and Video Streams. Future Internet. 2025; 17(4):139. https://doi.org/10.3390/fi17040139
Chicago/Turabian StyleNedyalkov, Ivan. 2025. "Studying the Impact of a UDP DoS Attack on the Parameters of VoIP Voice and Video Streams" Future Internet 17, no. 4: 139. https://doi.org/10.3390/fi17040139
APA StyleNedyalkov, I. (2025). Studying the Impact of a UDP DoS Attack on the Parameters of VoIP Voice and Video Streams. Future Internet, 17(4), 139. https://doi.org/10.3390/fi17040139




