Quantifying Website Privacy Posture Through Technical and Policy-Based Assessment
Abstract
1. Introduction
2. Methodology
- Web Applications Headers
- Content-Security-Policy (CSP)
- Strict-Transport-Security (HSTS)
- Referrer-Policy Header
- Email security
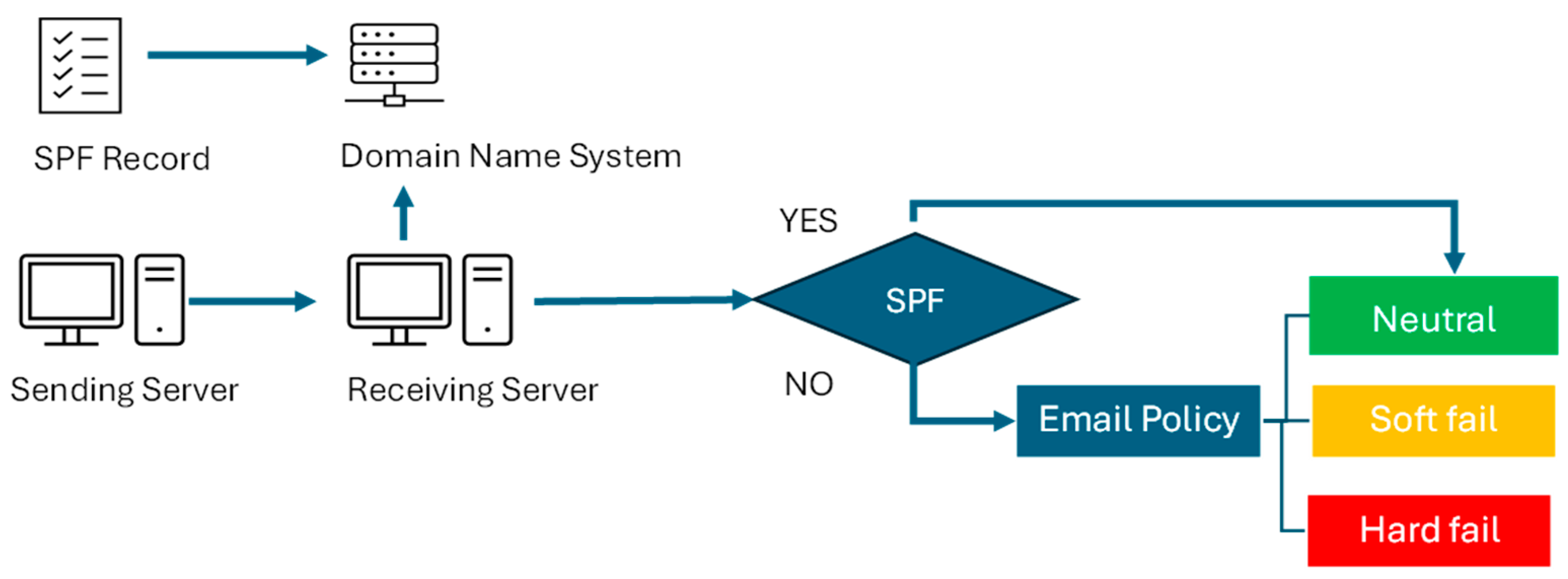
- Sender Policy Framework
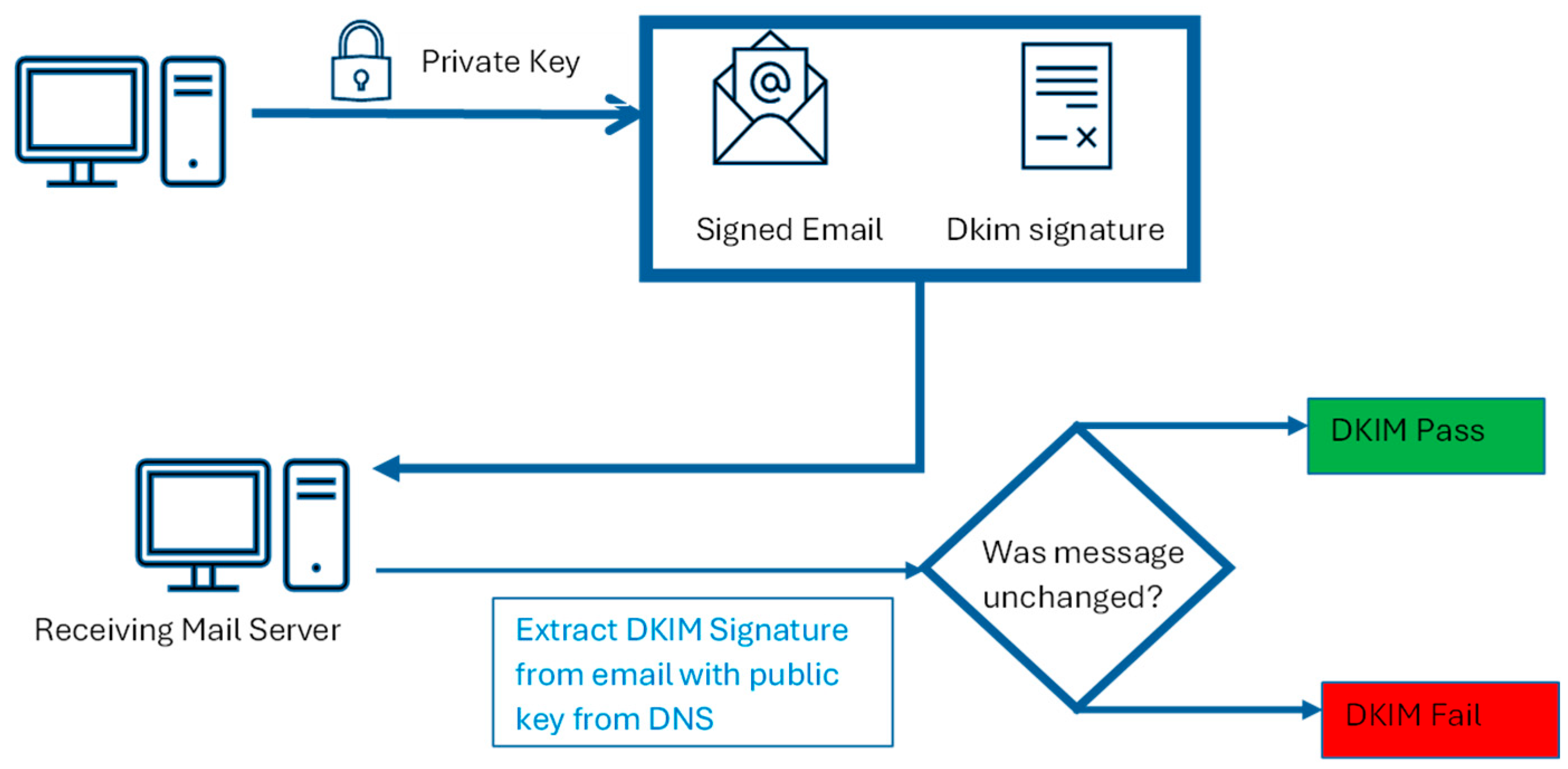
- DomainKeys Identified Mail
- Domain-based Message Authentication, Reporting & Conformance
- Certificates
- Phishing Domains and Squatting Domains
- Reputation domain score
- DNSSEC
- Cookies
- Privacy Policy
2.1. Web Applications Headers
- Access-Control-Allow-Origin Security Header
- Content-Type Header
- Content-Security-Policy (CSP)
- Cross-Origin-Embedder-Policy Security Header
- Cross-Origin-Resource-Policy Security Header
- Cross-Origin-Opener-Policy Security Header
- Set-Cookie Header
- Strict-Transport-Security (HSTS)
- Referrer-Policy Header
- X-Content-Type-Options Security Header
- X-Frame-Options Security Header
- X-Permitted-Cross-Domain-Policies Security Header
- Cache-Control Header
- X-Powered-By Header
2.1.1. Content-Security-Policy (CSP)
2.1.2. Strict-Transport-Security (HSTS)
2.1.3. Referrer-Policy Header
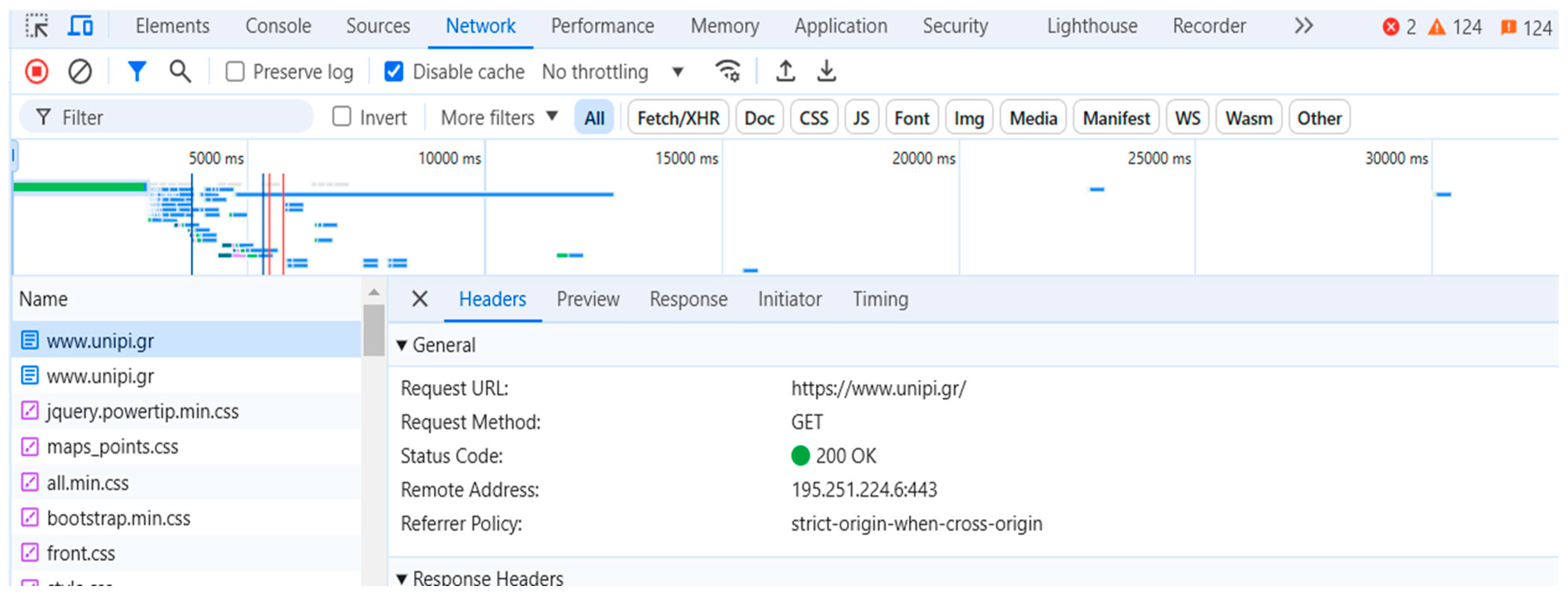
- Right-click anywhere at the domain.
- Select the option “Inspect”.
- From the development tools choose the Network tab.
- Refresh the page.
- Choose any HTTP request to find the way headers are implemented.
2.2. Email Security
- Sender Policy Framework
- DomainKeys Identified Mail
- Domain-based Message Authentication, Reporting & Conformance
2.2.1. Sender Policy Framework
2.2.2. DomainKeys Identified Mail
2.2.3. Domain-Based Message Authentication, Reporting & Conformance
2.3. Website Certificates
- Valid and up to date
- Issued by a trusted Certificate Authority (CA)
- Generated using a strong signature algorithm
2.4. Phishing Domains and Squatting Domains
2.5. Reputation Domain Score
- Hosting location
- IP address range associated with the domain
- Historical involvement in malware-related activities
- Presence of downloadable files with executable or suspicious code
- Overall domain history and behavior
|
|
|
|
|
|
|
|
2.6. Domain Name System Security Extensions (DNSSEC)
2.7. Cookies—Cookie Policy
2.8. Privacy Policy
3. A Framework for Website Privacy Evaluation
- The importance of each technical parameter in terms of how significantly it can impact the level of privacy protection on the website (for example, the consequences of a misconfigured cookie implementation are different from those of using a harmful domain—reputation score);
- The extent to which the website’s users are properly informed about the processing of their personal data (what data is collected, the purpose of the processing, whether their data is shared with third parties, how long the data is retained, how they can exercise their rights, etc.).
- Web Applications Headers (P1): 6 (scoring range from 0 to 6)
- Email security (P2): 6 (scoring range from 0 to 6)
- Certificates (P3): 9 (scoring range from 0 to 9)
- Phishing Domains and Squatting Domains (P4): 10 (scoring range from 0 to 10 (based on a percentage of found squatting domains))
- Reputation domain score (P5): 6 (scoring range from 0 to 6)
- DNSSEC (P6): 3 (scoring range from 0 to 3)
- Cookies (P7): 10 (scoring range from 0 to 10)
- Privacy Policy (P8): 50 (scoring range from 0 to 50)
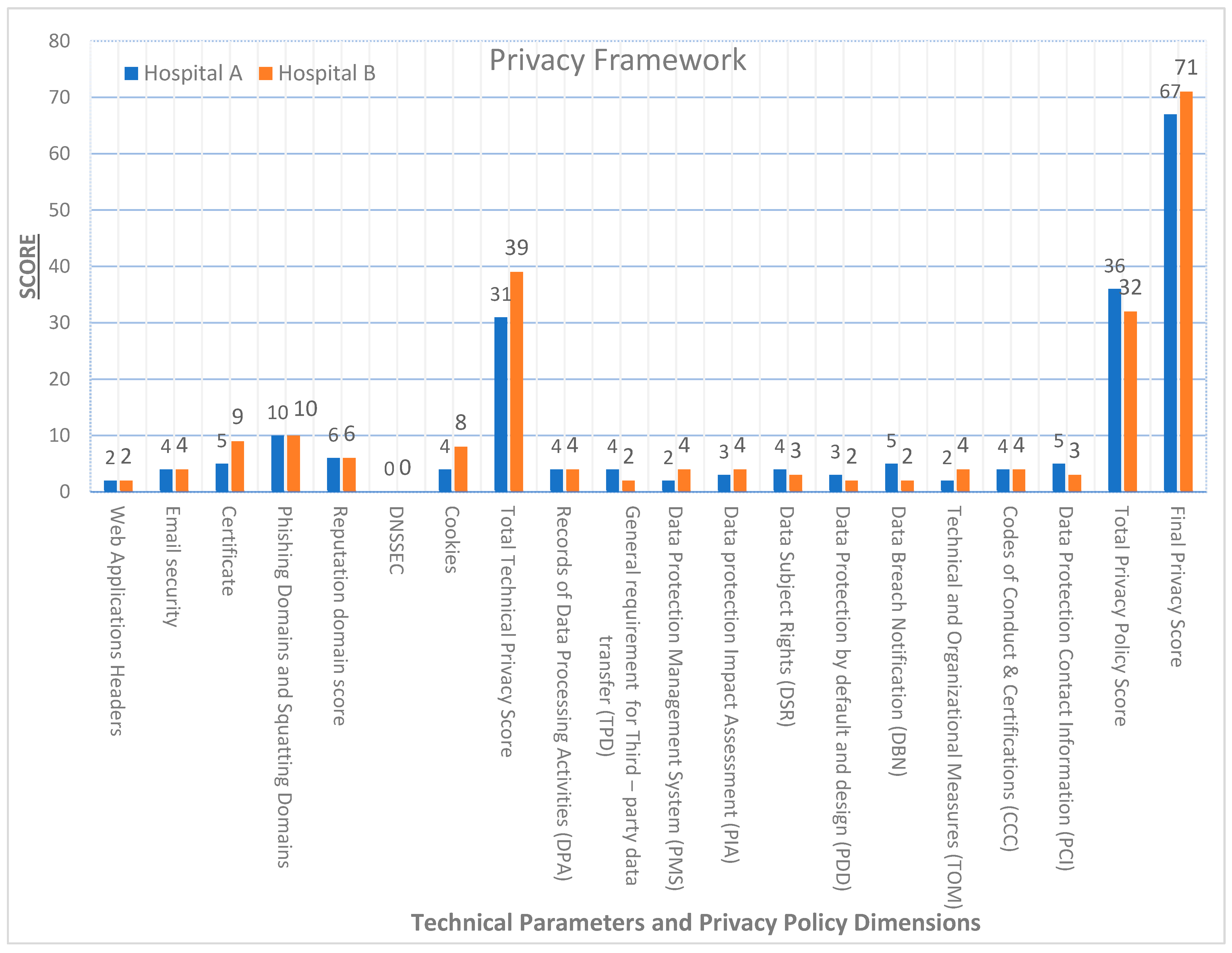
- Web Applications Headers Score for Hospital A: 2
- Web Applications Headers Score for Hospital B: 2
- Email security Score for Hospital A: 4
- Email security Score for Hospital B: 4
- Certificate Score for Hospital A: 5
- Certificate Score for Hospital B: 9
- Phishing Domains and Squatting Domains Score for Hospital A: 10
- Phishing Domains and Squatting Domains Score for Hospital B: 10
- DNSSEC Score for Hospital A: 0
- DNSSEC Score for Hospital B: 0
- Cookies Score for Hospital A: 4
- Cookies Score for Hospital B: 8
- Privacy Policy Score for Hospital A: 18
- Privacy Police Score for Hospital B: 16
4. Comparative Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix A.1. Acceptance Criteria for CSP/HSTS/Referrer Policy
- Content Security Policy Level 3
- Safe and secure | web.dev
- Referrer-Policy header—HTTP | MDN
Appendix A.2. Acceptance Criteria for SPF/DKIM/DMARC
- RFC 8616: Email Authentication for Internationalized Mail
- Trustworthy Email
- Best practices for sender authentication support—An Azure Communication Services article | Microsoft Learn
Appendix B. Privacy Policy Evaluation Rubric: 10 Criteria (0–5 Scale)
| Privacy Policy Category | 0—Not Implemented | 1—Minimal | 2—Weak | 3—Adequate | 4—Strong | 5—Optimal |
| Records of Data Processing Activities (DPA) | No records exist | Incomplete records | Partial, outdated records | Official documentation pertaining to fundamental processing activities | Comprehensive, updated, audited records | Comprehensively integrated, automated, and accessible for external auditing |
| Third-party Data Transfer (TPD) | No safeguards for transfers | Minimal safeguards | Partial compliance | Standard contractual clauses in use | Robust oversight and controls | Full compliance. |
| Data Protection Management System (PMS) | No PMS | Ad hoc policies | Limited PMS, partial coverage | Formal PMS, covers main processes | Mature PMS with regular audits | Company-wide PMS, continuous improvement, certifications |
| Data Protection Impact Assessment (PIA) | Not conducted | Conducted rarely. | Partially completed with limited detail | Formal PIAs for relevant activities | Comprehensive PIAs with regular updates | Integrated DPIA framework, proactive risk management |
| Data Subject Rights (DSR) | No process | Manual response | Partial response capability | Follows procedures and meets deadlines consistently | Timely and monitored responses. | Automated, transparent processes that surpass GDPR compliance requirements |
| Data Protection by Design & Default (PDD) | Not considered | Minimal consideration in projects | Applied inconsistently | Considered in most system designs | Systematic application in projects | Fully embedded in culture & lifecycle, privacy-first |
| Data Breach Notification (DBN) | No process | Minimal, unclear process | Partial, may miss deadlines | Formal process within 72 h | Proactive breach handling & testing | Fully tested, automated detection & notification system |
| Technical & Organizational Measures (TOM) | No TOM | Minimal controls | Some controls, gaps exist | Formal TOM, regularly reviewed | Comprehensive TOM, penetration tested | State-of-the-art TOM, continuous monitoring |
| Codes of Conduct & Certifications (CCC) | No adoption | Minimal awareness | Partial participation | Consistent with industry standards | Adheres to codes, pursuing certifications | Certified, continuous improvement |
| Data Protection Contact Information (PCI) | DPO contact information is not provided. | Incomplete or unclear info | Documented, though not readily accessible. | Clear DPO/contact info published | Proactive communication channel | Fully integrated, multilingual, transparent processes |
References
- Fragkiadakis, I.; Lambrinoudakis, C. Assessment of Online Privacy Policies. In Proceedings of the 11th International Conference on Computer Technology Applications (ICCTA 2025), Vienna, Austria, 21–23 May 2025. [Google Scholar]
- Schnell, K.; Roy, K.; Siddula, M. A Descriptive Study of Webpage Designs for Posting Privacy Policies for Different-Sized US Hospitals to Create an Assessment Framework. Future Internet 2023, 15, 112. [Google Scholar] [CrossRef]
- Javed, Y.; Sajid, A. A Systematic Review of Privacy Policy Literature. ACM Comput. Surv. 2024, 57, 1–43. [Google Scholar] [CrossRef]
- Mazel, J.; Garnier, R.; Fukuda, K. A Comparison of web privacy protection techniques. Comput. Commun. 2019, 144, 162–174. [Google Scholar] [CrossRef]
- Andersdotter, A.; Jensen-Urstad, A. Evaluating Websites and Their Adherence to Data Protection Principles: Tools and Experiences. In Privacy and Identity Management. Facing up to Next Steps: Privacy and Identity 2016. IFIP Advances in Information and Communication Technology; Lehmann, A., Whitehouse, D., Fischer-Hübner, S., Fritsch, L., Raab, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; Volume 498. [Google Scholar] [CrossRef]
- Dabrowski, A.; Merzdovnik, G.; Ullrich, J.; Sendera, G.; Weippl, E. Measuring Cookies and Web Privacy in a Post-GDPR World. In Proceedings of the International Conference on Passive and Active Network Measurement (PAM 2019), Lecture Notes in Computer Science 11419, Puerto Varas, Chile, 27–29 March 2019; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar] [CrossRef]
- Pan, R.; Ruiz-Martínez, A. Evolution of web tracking protection in Chrome. J. Inf. Secur. Appl. 2023, 79, 103643. [Google Scholar] [CrossRef]
- Morić, Z.; Dakic, V.; Djekic, D.; Regvart, D. Protection of Personal Data in the Context of E-Commerce. J. Cybersecur. Priv. 2024, 4, 731–761. [Google Scholar] [CrossRef]
- Goldberg, S.; Johnson, G.; Shriver, S. Regulating Privacy Online: An Economic Evaluation of the GDPR. Am. Econ. J. Econ. Policy 2024, 16, 325–358. [Google Scholar] [CrossRef]
- Böyük, M. User Data and Digital Privacy: Privacy Policies of Social Media Platforms. Turk. Online J. Des. Art Commun. 2025, 15, 225–239. [Google Scholar] [CrossRef]
- Sim, K.; Heo, H.; Cho, H. Combating Web Tracking: Analyzing Web Tracking Technologies for User Privacy. Future Internet 2024, 16, 363. [Google Scholar] [CrossRef]
- HTTP Security Headers: A Complete Guide to HTTP Headers. Available online: https://www.darkrelay.com/post/http-security-headers (accessed on 18 August 2025).
- HTTP Security Response Headers Cheat Sheet—OWASP Cheat Sheet Series. Available online: https://cheatsheetseries.owasp.org/cheatsheets/HTTP_Headers_Cheat_Sheet.html (accessed on 18 August 2025).
- RFC 1049—Content-Type Header Field for Internet Messages. Available online: https://datatracker.ietf.org/doc/html/rfc1049 (accessed on 18 August 2025).
- RFC 6265—HTTP State Management Mechanism. Available online: https://datatracker.ietf.org/doc/html/rfc6265 (accessed on 18 August 2025).
- RFC 6797—HTTP Strict Transport Security (HSTS). Available online: https://datatracker.ietf.org/doc/html/rfc6797 (accessed on 18 August 2025).
- RFC 9111—HTTP Caching. Available online: https://datatracker.ietf.org/doc/rfc9111/ (accessed on 18 August 2025).
- Analyse Your HTTP Response Headers. Available online: https://securityheaders.com/ (accessed on 18 August 2025).
- Al Qahtani, E.; Javed, Y.; Tabassum, S.; Sahoo, L.; Shehab, M. Managing Access to Confidential Documents: A Case Study of an Email Security Tool. Future Internet 2023, 15, 356. [Google Scholar] [CrossRef]
- RFC 8616—Email Authentication for Internationalized Mail. Available online: https://datatracker.ietf.org/doc/html/rfc8616 (accessed on 18 August 2025).
- Set Up DMARC to Validate the From Address Domain for Cloud Senders. Available online: https://learn.microsoft.com/en-us/defender-office-365/email-authentication-dmarc-configure (accessed on 18 August 2025).
- Understanding Website Certificates|CISA. Available online: https://www.cisa.gov/news-events/news/understanding-website-certificates (accessed on 18 August 2025).
- Qualys SSL Labs. Available online: https://www.ssllabs.com/ (accessed on 18 August 2025).
- Web Filter Lookup|FortiGuard Labs. Available online: https://fortiguard.fortinet.com/webfilter (accessed on 18 August 2025).
- Reputation Lookup||Cisco Talos Intelligence Group—Comprehensive Threat Intelligence. Available online: https://talosintelligence.com/reputation_center (accessed on 18 August 2025).
- MX Lookup Tool—Check Your DNS MX Records Online—MxToolbox. Available online: https://mxtoolbox.com/ (accessed on 18 August 2025).
- VirusTotal—Home. Available online: https://www.virustotal.com/gui/home/upload (accessed on 18 August 2025).
- BarracudaCentral.org—Technical Insight for Security Pros. Available online: https://www.barracudacentral.org/ (accessed on 18 August 2025).
- DNSSEC—What Is It and Why Is It Important? Available online: https://www.icann.org/resources/pages/dnssec-what-is-it-why-important-2019-03-05-en (accessed on 18 August 2025).
- Guillén Cava, Á.D.; Ruiz-Martínez, A. WebTrackingScore: A Combined Web Tracking Risk Score System for Websites. Future Internet 2025, 17, 3. [Google Scholar] [CrossRef]
- Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the Protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of Such Data, and Repealing Directive 95/46/EC (General Data Protection Regulation). Available online: http://data.europa.eu/eli/reg/2016/679/oj (accessed on 18 August 2025).
- Directive 2002/58/EC of the European Parliament and of the Council of 12 July 2002 Concerning the Processing of Personal Data and the Protection of Privacy in the Electronic Communications Sector (Directive on Privacy and Electronic Communications). Available online: https://eur-lex.europa.eu/eli/dir/2002/58/oj (accessed on 18 August 2025).
- Google Certified Publishing Partner. Available online: https://www.google.com/ads/publisher/partners/ (accessed on 18 August 2025).
- Tang, C.; Liu, Z.; Ma, C.; Wu, Z.; Li, Y.; Liu, W.; Zhu, D.; Li, Q.; Li, X.; Liu, T.; et al. PolicyGPT: Automated Analysis of Privacy Policies with Large Language Models. arXiv 2023, arXiv:2309.10238v1. [Google Scholar] [CrossRef]

| Level | Total Privacy Score | Description |
|---|---|---|
| Poor | 0–25 | Minimal or no privacy protections in place. |
| Low | 25–49 | Basic measures are present, but significant gaps remain. |
| Moderate | 50–74 | Adequate protection, though improvements are still needed. |
| Good | 75–100 | Strong privacy posture with comprehensive measures in place. |
| Category | Maximum Score | Scoring Range | Sub-Scoring |
|---|---|---|---|
| Web Applications Headers (P1) | 6 | 0 to 6 | Award two points for each of the three Web application headers that is implemented.
|
| Email security (P2) | 6 | 0 to 6 | Award two points for each of the three email security features that are implemented.
|
| Certificates (P3) | 9 | 0 to 9 | Points are awarded as follows: 4 points: Certificate from a trusted Certificate Authority 3 points: Certificate is valid 2 points: Strong signature algorithm |
| Phishing Domains and Squatting Domains (P4) | 10 | 0 to 10 | Award five points if dnstwist results are satisfactory. Award five points if technical measures are in place (use of canonical tags, ensure that the same domain name is used consistently across multiple top-level domains, including .com, .net, or .org, to block deceptive tactics such as mirror websites that copy legitimate sites. |
| Reputation domain score (P5) | 6 | 0 to 6 | Award six points if there is no prior record of malware-related activity. |
| DNSSEC (P6) | 3 | 0 to 3 | Award three points if DNSSEC has been deployed |
| Cookies (P7) | 10 | 0 to 10 | Each of the following criteria will be evaluated using a scoring range from 0 to 2.
|
| Privacy Policy (P8) | 50 | 0 to 50 | Award five points for each of the ten criteria required for full compliance (according to the Privacy Policy Evaluation Rubric presented in Appendix B) |
| Hospital A | Hospital B | ||
|---|---|---|---|
| Technical Parameters | Web Applications Headers | 2 | 2 |
| Email security | 4 | 4 | |
| Certificate | 5 | 9 | |
| Phishing Domains and Squatting Domains | 10 | 10 | |
| Reputation domain score | 6 | 6 | |
| DNSSEC | 0 | 0 | |
| Cookies | 4 | 8 | |
| Total Technical Privacy Score | 31 | 39 | |
| Privacy Policy Parameters | Records of Data Processing Activities (DPA) (GDPR Article 30) | 4 | 4 |
| General requirement for Third—party data transfer (TPD) (GDPR Articles 44–50) | 4 | 2 | |
| Data Protection Management System (PMS) (GDPR Article 24) | 2 | 4 | |
| Data Protection Impact Assessment (PIA) (GDPR Articles 35–36) | 3 | 4 | |
| Data Subject Rights (DSR) (GDPR Articles 12,15,16) | 4 | 3 | |
| Data Protection by default and design (PDD) (GDPR Article 25) | 3 | 2 | |
| Data Breach Notification (DBN) (GDPR Articles 33–34) | 5 | 2 | |
| Technical and Organizational Measures (TOM) (GDPR Article 32) | 2 | 4 | |
| Codes of Conduct & Certifications (CCC) (GDPR Articles 40–43) | 4 | 4 | |
| Data Protection Contact Information (PCI) (GDPR Articles 13,14) | 5 | 3 | |
| Total Privacy Policy Score | 36 | 32 | |
| Final Privacy Score | 67 | 71 |
| Technical Parameters and Privacy Policy Metrics | Ref. [11] Combating Web Tracking: Analyzing Web Tracking Technologies for User Privacy | Ref. [5] Evaluating Websites and Their Adherence to Data Protection Principles: Tools and Experiences | Ref. [4] A Comparison of Web Privacy Protection Techniques | Ref. [34] PolicyGPT: Automated Analysis of Privacy Policies with LLMs | Quantifying Website Privacy Posture through Technical and Policy-Based Assessment |
|---|---|---|---|---|---|
| Web Applications Headers |  |  |  |  | |
| Email security |  | ||||
| Certificate |  |  |  |  | |
| Phishing Domains and Squatting Domains |  | ||||
| Reputation domain score |  | ||||
| DNSSEC |  |  |  | ||
| Cookies |  |  |  |  | |
| Records of Data Processing Activities (DPA) |  |  | |||
| General requirement for Third—party data transfer (TPD) |  |  | |||
| Data Protection Management System (PMS) |  |  | |||
| Data Protection Impact Assessment (PIA) |  |  | |||
| Data Subject Rights (DSR) |  |  | |||
| Data Protection by default and design (PDD) |  |  | |||
| Data Breach Notification (DBN) |  |  | |||
| Technical and Organizational Measures (TOM) |  |  | |||
| Codes of Conduct & Certifications (CCC) |  |  | |||
| Data Protection Contact Information (PCI) |  |  |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fragkiadakis, I.; Gritzalis, S.; Lambrinoudakis, C. Quantifying Website Privacy Posture Through Technical and Policy-Based Assessment. Future Internet 2025, 17, 463. https://doi.org/10.3390/fi17100463
Fragkiadakis I, Gritzalis S, Lambrinoudakis C. Quantifying Website Privacy Posture Through Technical and Policy-Based Assessment. Future Internet. 2025; 17(10):463. https://doi.org/10.3390/fi17100463
Chicago/Turabian StyleFragkiadakis, Ioannis, Stefanos Gritzalis, and Costas Lambrinoudakis. 2025. "Quantifying Website Privacy Posture Through Technical and Policy-Based Assessment" Future Internet 17, no. 10: 463. https://doi.org/10.3390/fi17100463
APA StyleFragkiadakis, I., Gritzalis, S., & Lambrinoudakis, C. (2025). Quantifying Website Privacy Posture Through Technical and Policy-Based Assessment. Future Internet, 17(10), 463. https://doi.org/10.3390/fi17100463







