A Dependency-Aware Task Stealing Framework for Mobile Crowd Computing
Abstract
1. Introduction
1.1. Research Challenge
- Extreme heterogeneity: Smartphones, tablets, and wearable and low-cost IoT nodes vary by two orders of magnitude in CPU speed, memory, and battery life [13]. Naive work distribution either overloads weak devices or under-utilizes capable ones.
- Task inter-dependency: Real-world mobile workloads (activity-recognition, on-board ML inference, and AR/VR pipelines) form Directed Acyclic Graphs (DAGs), not self-aware-parallel bags of tasks [14]. In such DAG-based workloads, a single, stalled edge representing a dependency between tasks can block the execution of all tasks that depend on it downstream.
- High churn: Empirical traces show median session times below 7 min for opportunistic Bluetooth/Wi-Fi Direct clusters; any robust scheduler must expect mid-task departures [15].
- Resource variability: Battery-aware OS governors, background apps, and radio state changes mean that a “fast” device at time t0 may be throttled or offline at t1 [16].
1.2. Proposed Approach and Contributions
- C1:
- Capability-aware job stealing: We introduce a mechanism that matches computational jobs to the most suitable mobile devices. Through a lightweight profiling handshake and a dynamic scoring system, the framework ensures that powerful devices are assigned intensive jobs while preventing resource-constrained devices from being overloaded.
- C2:
- Generalized DAG work stealing: We extend the classical work stealing model to support applications with complex task dependencies, represented as a static Directed Acyclic Graph (DAG). This allows the framework to correctly orchestrate multi-stage workflows in a decentralized manner, ensuring jobs are only executed after their prerequisites are met.
- C3:
- Resilience via staged result management: To ensure robustness in volatile mobile environments, we introduce a resilience mechanism featuring adaptive checkpointing and staged result transfers. By selectively transmitting intermediate results based on job criticality and worker reliability, this approach minimizes results loss from device disconnections and significantly reduces recovery time compared to a full restart.
2. Background
2.1. Key Concepts
2.2. From Cloud to Crowd
2.3. MCdC vs. MEC
2.4. Research Motivation
3. Related Work
3.1. Fundamental Collaborative Frameworks
3.2. Task Dependency Management
3.3. Dynamic Task Off-Loading and Hybrid Architectures
3.4. Energy-Aware Scheduling and Load Balancing
3.5. Fault Tolerance in Volatile Peer-to-Peer Environments
3.6. Critical Synthesis and Research Gaps
- True heterogeneity compatibility: Current solutions do not adequately support true device heterogeneity. They are often designed for homogeneous or narrowly defined device capabilities, failing to incorporate the diverse range of computational resources-from high-performance smartphones to low-power sensors-available in a dynamic mobile environment. This prevents the system from fully leveraging the collective power of all proximate devices.
| Approach (Year) | Collaboration Scope | Scheduling Approach/ Dep. Handling | Dynamic Adaptation | Energy-Awareness | Fault Tolerance | Key Limitations for Fully Decentralized MCdC |
|---|---|---|---|---|---|---|
| MAUI [28] (2010) | Mobile → Cloud | Centralized decision/ No explicit dep. | Static | Yes (code profiling) | No | Purely centralized off-loading to infrastructure |
| CloneCloud [29] (2011) | Mobile → Cloud (VM migration) | Centralized decision/ Basic object dep. | Static | Yes (VM state) | Limited (VM state consistency) | Centralized VM approach, not P2P task sharing |
| Serendipity [36] (2012) | Local devices (P2P) | Opportunistic off-load/ No (independent tasks) | Limited adaptivity | Implicit (local exec saves energy) | Limited (retry on disconnect) | Required intermittent connectivity, no complex dep. or guarantees |
| Circa [37] (2018) | Local devices (P2P, no infra) | Decentralized (fairness-based allocation)/No (independent tasks) | Static allocation | Implicit (local exec saves energy) | Limited (initial reliable peer selection) | Restricted to independent tasks, static allocation |
| Honeybee [17] (2016) | Local devices (P2P mesh) | Decentralized work stealing/Partial (sequential via extension [19]) | Yes (proactive work stealing) | No (focus on performance) | Yes (reassign on disconnect) | Limited dependency support, no explicit energy optimization |
| CASINO [40] (2018) | Mobile + Cloud (Hybrid) | Centralized heuristic scheduler/Yes (job/device graph) | Limited (batch schedule) | Partial (device battery profile) | No (assumes stable execution) | Centralized control, assumes stable resources |
| Centralized heuristic [42] (2022) | Vehicular + Edge + Cloud | Centralized RL scheduler/Yes (DAG model) | Yes (dynamic RL decisions) | No (latency primary focus) | No (no churn modeled) | Centralized control point (edge/cloud), specific IoV domain |
| Centralized RL scheduler [41] (2020) | Mobile + Edge | Centralized heuristic (dependency-aware HEFT variant)/Yes (general DAG) | Static plan, regenerated on topology change | No (energy not modelled) | No | Central controller assumed; edge helpers must stay reachable |
| UNION [55] (2023) | Opportunistic devices + Edge | Distributed (probabilistic + reactive)/Yes (reliability model influences schedule) | Yes (proactive & reactive) | No (focus on reliability) | Yes (replication, migration) | Dependency handling tied to reliability, not general DAG optimization |
| [45] (2025) | Edge + Fog + Cloud (3-tier) | Extended Honeybee work stealing/No (independent jobs) | Yes (stealing across tiers) | No (focus on throughput) | Yes (inherits Honeybee mechanisms) | Focus on independent jobs across tiers; general task graphs not fully supported |
4. The Honeybee-Tx Framework
4.1. System Architecture
4.2. Core Mechanism 1: Heterogeneity-Aware Job Stealing
4.2.1. Device Capability Assessment
4.2.2. Capability-Aware Job Selection
| Algorithm 1 Capability–aware job selection. |
| Require: Candidate set , worker profile , minimum score Ensure: Best matching job or Null
|
Complexity
Performance Considerations
4.3. Core Mechanism 2: Generalized DAG Work Stealing
| Algorithm 2 Dependency and capability-aware job stealing on delegator. |
|
- Generalized DAG-aware work stealing: Our work stealing algorithm differs from classical work stealing algorithms, such as [57], which are designed for fully strict computations, and dependencies are limited to parent–child relationships in a structured tree. They do not support general task graphs with complex dependencies. In contrast, our approach works with arbitrary DAG-based workloads. It checks all dependencies before allowing a job to be stolen (Algorithm 2, Line 6). This ensures that a worker only steals jobs for which all prerequisite jobs have been completed, thereby preventing deadlocks or wasted computation.
- Capability-driven job matching: The selection of a job to steal involves matching on the delegator (Algorithm 2, Line 6) that considers the specific computational and resource requirements of available jobs against the profiled capabilities (Equation (1)) of the prospective worker device.
- Dynamic chunk sizing: In contrast to fixed-size chunks in the original Honeybee [17], Honeybee-Tx adaptively determines the number of jobs in a chunk for a requesting worker (Algorithm 2, Line 3) based on the worker’s performance metrics, allowing more powerful devices to steal larger chunks and improving overall throughput.
- Centralized job pool with work stealing: The framework utilizes a centralized job pool on the delegator, structured as a double-ended queue, from which workers can steal jobs. This work stealing model allows workers to voluntarily and opportunistically pull work when idle, ensuring intrinsic load balancing.
4.3.1. Dependency Management and DAG Operations
4.3.2. DAG Management
4.4. Core Mechanism 3: Resilience via Staged Result Management
4.4.1. Staged Result Transfer and Job Recovery
| Algorithm 3 Staged result transfer from worker to delegator. |
|
Key Resilience Features
4.4.2. Heartbeat-Based Liveness Monitoring
4.4.3. Resilience Optimization: Adaptive Checkpointing
| Algorithm 4 Adaptive progress threshold for checkpointing. |
|
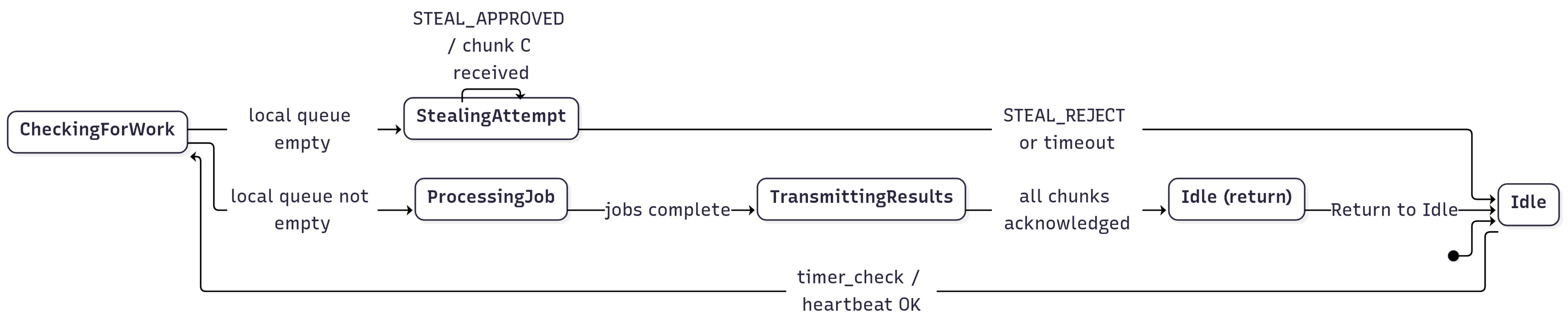
4.5. Worker Operational Model
4.5.1. Concurrency Remark
Delegator-Side Steal-Request Handler
- Initial sanity check: First, the delegator assesses its own state to decide if it should even consider off-loading work. It measures its current computational load factor () and checks for any critically stalled jobs. The request is immediately rejected if either the delegator’s own load is below a configurable threshold (), meaning it is under-utilized, or if it has a high-priority job stalled in its local queue that requires immediate attention. This prevents the delegator from giving away work when it could be completing tasks itself or when a critical dependency is blocked locally.
- Filtering for stealable jobs: If the initial check passes, the delegator filters its central JobPool to create a set of currently stealable jobs (E). A job is considered stealable only if it is dependency-safe (i.e., all its prerequisite jobs in the DAG have been completed) and is not already being processed by another worker. If this set is empty, the delegator does not respond with any job chunk.
- Capability-aware matching: If stealable jobs exist, the handler retrieves the capability profile (p) of the requesting worker, which contains its CPU, memory, and energy characteristics. Using the SelectForStealing routine (defined in Algorithm 1), it then finds the most suitable job () from the stealable set that best matches the worker’s specific capabilities.
- Job transfer and state update: If a suitable job is found, the delegator attempts to transfer it to the worker. If the network transfer is successful, the delegator atomically updates the job’s state in the DAG to indicate execution by the requesting worker and returns an APPROVED status, ensuring the job is not offered elsewhere. Conversely, if the transfer fails (e.g., due to network issues) or if no suitable job was found during the matching phase, the handler returns a FAILED status, and the job remains in the delegator’s pool to be stolen later.
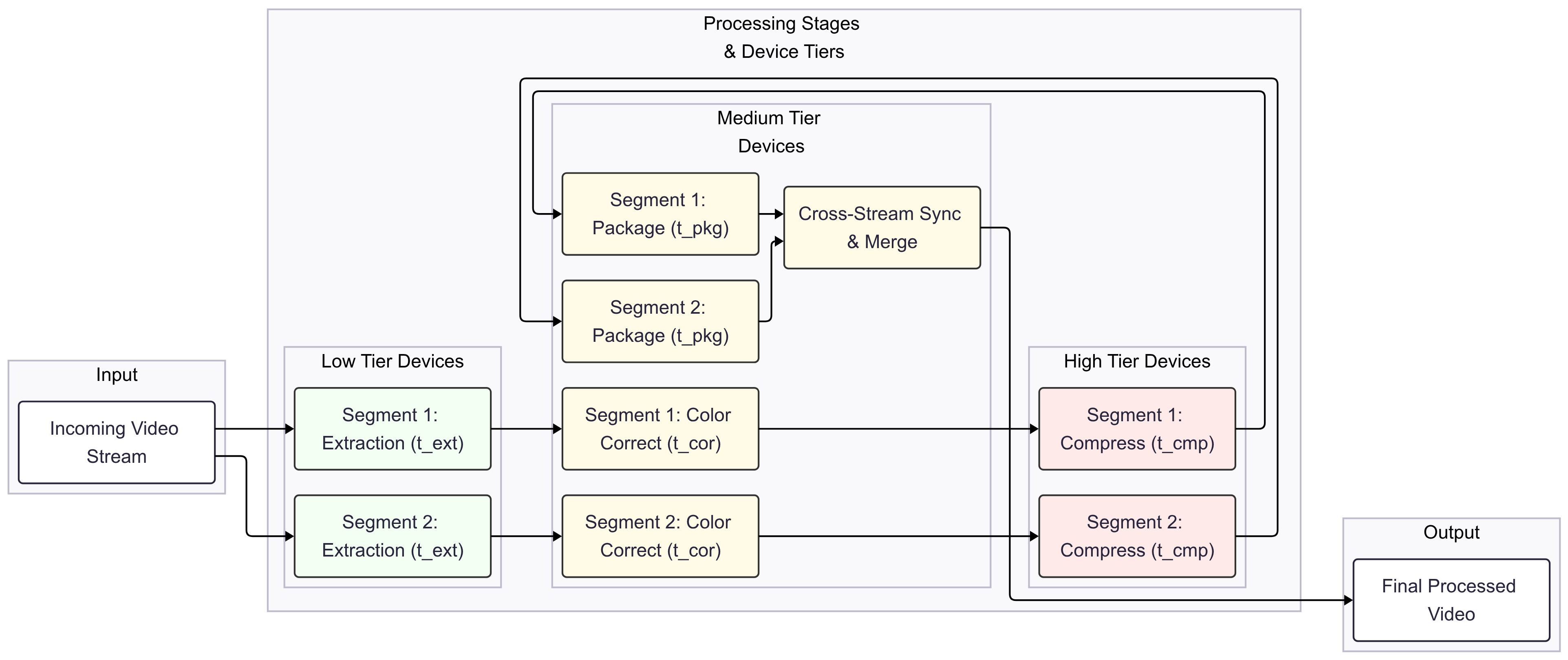
4.6. Application-Specific Parallelization: Video Processing Case
4.6.1. Pipeline Initialization
4.6.2. Heuristic Assignment
5. Application Programming Model
5.1. Job Execution Environment
5.2. Application Preparation and Resource Specification
5.3. Data Transfer and Dependency Management
5.4. Runtime Progress Evaluation and Checkpointing
5.5. Execution Orchestration
5.6. Design Constraint
6. Application and Evaluation
6.1. Application Scenarios
6.1.1. Human Activity Recognition (HAR)
6.1.2. Multi-Camera Video Pipeline
6.2. Experimental Setup
6.3. Evaluation Methodology
6.3.1. Performance Metrics
6.3.2. HAR (Performance and Scalability Focus)
6.3.3. Video Pipeline (Dependency Focus)
6.4. Results and Analysis
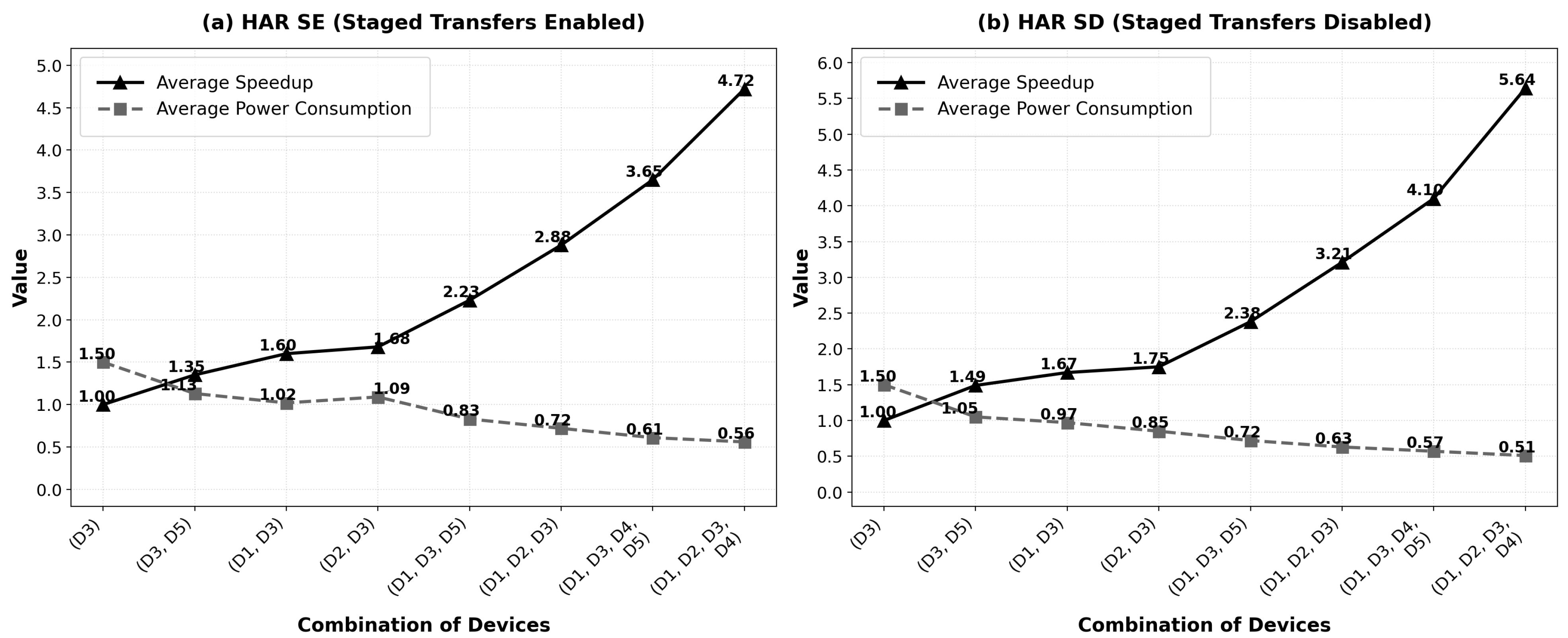
6.4.1. HAR: Speed-Up and Energy
- Scalability: The speed-up increases near-linearly with additional workers, proving that Honeybee-Tx effectively parallelizes the HAR workload across heterogeneous devices. The near-linear scaling from 1× (monolithic) to 4.72× (4 workers with staged transfers) validates the efficiency of our capability-aware job stealing mechanism (Algorithm 1).
- Delegator energy efficiency: The average battery consumption of the delegator device consistently decreases as more workers join the collaboration, dropping from 1.5% (monolithic execution) to 0.56% (with 4 workers). This proves that distributing work to nearby devices significantly reduces the energy burden on the delegator, even though it continues to orchestrate the computation. The delegator’s reduced workload more than compensates for its coordination overhead.
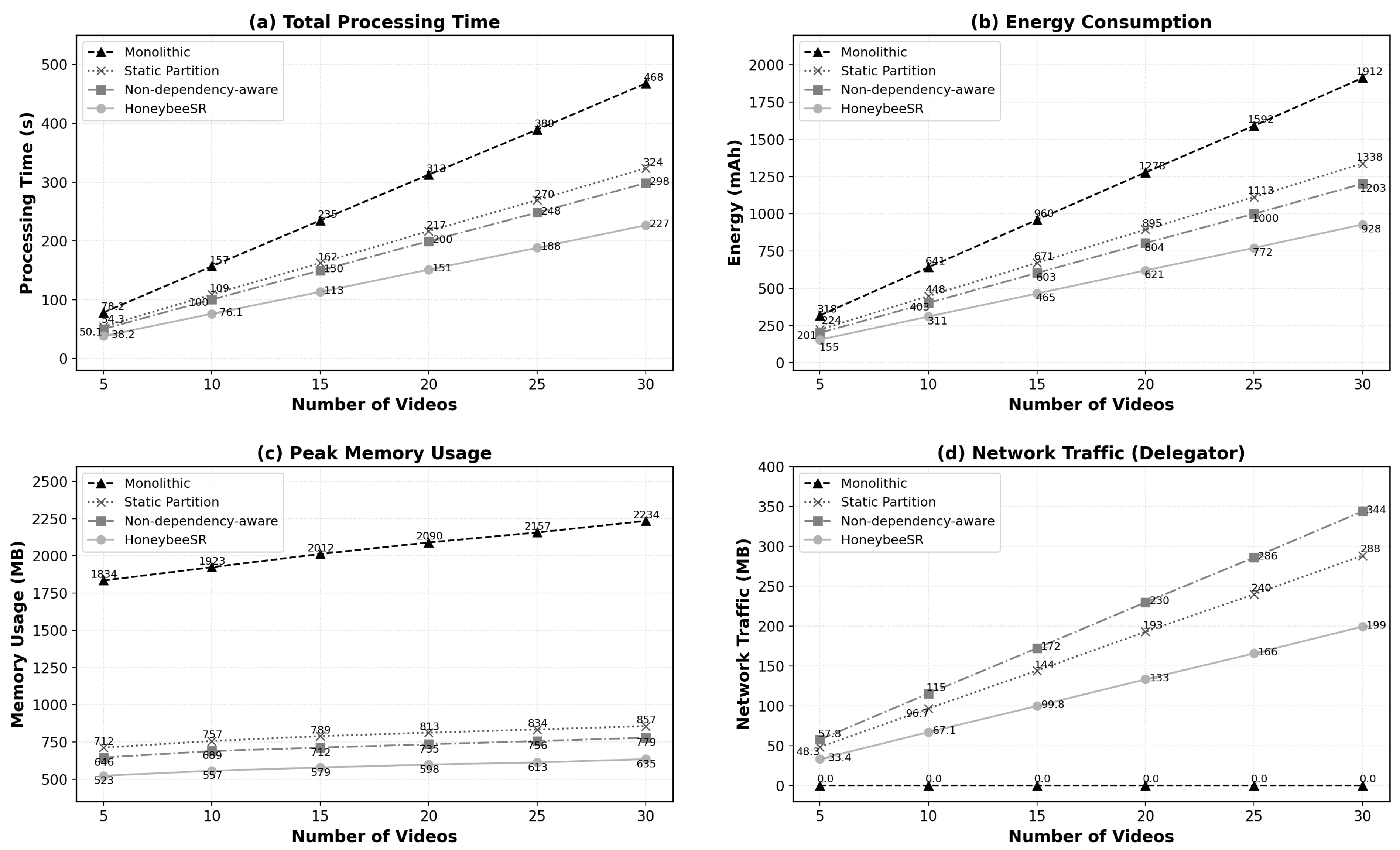
6.4.2. Multi-Camera Video Pipeline
6.4.3. Processing Time and Energy Consumption
6.4.4. Peak Memory and Network Traffic
7. Discussion
7.1. Validation of Core Mechanisms
7.2. Energy and Resource Efficiency
7.3. Trade-Offs and Design Decisions
7.4. Practical Deployment Considerations
- Device selection: The performance differences between device models (particularly between Snapdragon and Tensor architectures) suggest that capability profiling during the handshake phase is crucial. Applications should implement device-specific optimizations, particularly for ML-accelerated workloads.
- Workload characteristics: The framework excels with workloads exhibiting natural parallelism (HAR’s sliding windows) or clear pipeline structures (video processing stages). Applications with tighter coupling between tasks may experience reduced benefits.
- Scale considerations: While our experiments used up to five devices, the near-linear scaling suggests larger device clusters could yield proportionally greater benefits, limited primarily by coordination overhead and network topology constraints.
7.5. Limitations and Future Directions
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Additional Algorithms
| Algorithm A1 DAG update upon job status change. |
|
| Algorithm A2 Job recovery by delegator after worker failure. |
|
| Algorithm A3 Barrier-style synchronization across devices. |
|
| Algorithm A4 Worker-side operational loop. |
|
| Algorithm A5 Delegator-side steal-request handler. |
|
| Algorithm A6 Heuristic first-fit partitioning for a video pipeline. |
|
References
- Roser, M.; Ritchie, H.; Mathieu, E. Technological Change. 2023. Available online: https://ourworldindata.org/technological-change (accessed on 5 June 2024).
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.H.; Konwinski, A.; Lee, G.; Patterson, D.A.; Rabkin, A.; Stoica, I.; et al. A View of Cloud Computing. Commun. ACM 2010, 53, 50–58. [Google Scholar] [CrossRef]
- Pal, S. Extending Mobile Cloud Platforms Using Opportunistic Networks: Survey, Classification and Open Issues. J. Univers. Comput. Sci. 2015, 21, 1594–1634. [Google Scholar] [CrossRef]
- Halpern, M.; Zhu, Y.; Reddi, V.J. Mobile CPU’s rise to power: Quantifying the impact of generational mobile CPU design trends on performance, energy, and user satisfaction. In Proceedings of the 2016 IEEE International Symposium on High Performance Computer Architecture (HPCA), Barcelona, Spain, 12–16 March 2016; pp. 64–76. [Google Scholar]
- Google. Pixel 6 Pro-Technical Specifications. 2021. Available online: https://store.google.com/product/pixel_6_pro (accessed on 22 April 2025).
- Liu, F.; Shu, P.; Jin, H.; Ding, L.; Yu, J.; Niu, D.; Li, B. Gearing resource-poor mobile devices with powerful clouds: Architectures, challenges, and applications. IEEE Wirel. Commun. 2013, 20, 14–22. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Yu, R.; Li, P. Toward resource-efficient federated learning in mobile edge computing. IEEE Netw. 2021, 35, 148–155. [Google Scholar] [CrossRef]
- Cai, H.L.; Xu, B.; Jiang, L.; Vasilakos, A.V. IoT-Based Big Data Storage Systems in Cloud Computing: Perspectives and Challenges. IEEE Internet Things J. 2017, 4, 75–87. [Google Scholar] [CrossRef]
- Tuli, S.; Mahmud, R.; Tuli, S.; Buyya, R. FogBus: A Blockchain-Based Lightweight Framework for Edge and Fog Computing. J. Syst. Softw. 2019, 154, 22–36. [Google Scholar] [CrossRef]
- Boubiche, D.E.; Imran, M.; Maqsood, A.; Shoaib, M. Mobile crowd sensing–taxonomy, applications, challenges, and solutions. Comput. Hum. Behav. 2019, 101, 352–370. [Google Scholar] [CrossRef]
- Taleb, T.; Samdanis, K.; Mada, B.; Flinck, H.; Dutta, S.; Sabella, D. On Multi-Access Edge Computing: A Survey of the Emerging 5G Edge-Cloud Architecture and Orchestration. IEEE Commun. Surv. Tutor. 2017, 19, 1657–1681. [Google Scholar] [CrossRef]
- Ye, S.; Zeng, L.; Chu, X.; Xing, G.; Chen, X. Asteroid: Resource-Efficient Hybrid Pipeline Parallelism for Collaborative DNN Training on Heterogeneous Edge Devices. In Proceedings of the 30th ACM International Conference on Mobile Computing and Networking (MobiCom), Washington, DC, USA, 18–22 November 2024; pp. 312–326. [Google Scholar] [CrossRef]
- Lou, J.; Tang, Z.; Jia, W.; Zhao, W.; Li, J. Startup-Aware Dependent Task Scheduling With Bandwidth Constraints in Edge Computing. IEEE Trans. Mob. Comput. 2024, 23, 1586–1600. [Google Scholar] [CrossRef]
- Bartolomeo, G.; Cao, J.; Su, X.; Mohan, N. Characterizing Distributed Mobile Augmented Reality Applications at the Edge. In Proceedings of the 19th ACM International Conference on Emerging Networking EXperiments and Technologies (CoNEXT ’23), Paris, France, 5–8 December 2023; pp. 1–10. [Google Scholar] [CrossRef]
- Tang, Z.; Peng, W.; Guo, J.; Lou, J.; Cui, H.; Wang, T.; Wu, Y.; Jia, W. LRScheduler: A Layer-Aware and Resource-Adaptive Container Scheduler in Edge Computing. In Proceedings of the 2024 20th International Conference on Mobility, Sensing and Networking (MSN), Harbin, China, 20–22 December 2024; pp. 1–9. [Google Scholar] [CrossRef]
- Fernando, N.; Loke, S.W.; Rahayu, W. Computing with nearby mobile devices: A work sharing algorithm for mobile edge-clouds. IEEE Trans. Cloud Comput. 2019, 7, 329–343. [Google Scholar] [CrossRef]
- Fernando, N. Honeybee: Android Implementation of the Honeybee Model for Mobile Crowd Computing. 2015. Available online: https://github.com/niroshini/honeybee (accessed on 15 May 2021).
- Nagesh, S.S.; Fernando, N.; Loke, S.W.; Neiat, A.; Pathirana, P.N. Opportunistic mobile crowd computing: Task-dependency based work-stealing. In Proceedings of the 28th Annual International Conference on Mobile Computing and Networking, Sydney, NSW, Australia, 17–21 October 2022; pp. 775–777. [Google Scholar]
- Nagesh, S.S.; Fernando, N.; Loke, S.W.; Neiat, A.G.; Pathirana, P.N. Honeybee-RS: Enhancing Trust through Lightweight Result Validation in Mobile Crowd Computing. In Proceedings of the 2024 IEEE 23rd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Sanya, China, 17–21 December 2024; pp. 2553–2558. [Google Scholar]
- Islam, M.; Nagesh, S.S.; Fernando, N.; Loke, S.W.; Neiat, A.; Pathirana, P.N. Blockchain Based Trust and Validation Mechanism for Mobile Collaborative Computing. In Proceedings of the SIGCOMM Workshop on Zero Trust Architecture for Next Generation Communications (ZTA-NextGen ’24), Sydney, NSW, Australia, 4–8 August 2024; pp. 37–39. [Google Scholar] [CrossRef]
- Pan, J.; McElhannon, J. Future Edge Cloud and Edge Computing for Internet of Things Applications. IEEE Internet Things J. 2018, 5, 439–449. [Google Scholar] [CrossRef]
- Al-Ansi, A.; Al-Ansi, A.M.; Muthanna, A.; Elgendy, I.A.; Koucheryavy, A. Survey on intelligence edge computing in 6G: Characteristics, challenges, potential use cases, and market drivers. Future Internet 2021, 13, 118. [Google Scholar] [CrossRef]
- Satyanarayanan, M. The Emergence of Edge Computing. Computer 2017, 50, 30–39. [Google Scholar] [CrossRef]
- Fernando, N.; Loke, S.W.; Rahayu, W. Computing. In Mobile and Ubiquitous Systems: Computing, Networking, and Services, Proceedings of the 9th International Conference, MOBIQUITOUS 2012, Beijing, China, 12–14 December 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 224–236. [Google Scholar] [CrossRef]
- Ganti, R.K.; Ye, F.; Lei, H. Mobile crowdsensing: Current state and future challenges. IEEE Commun. Mag. 2011, 49, 32–39. [Google Scholar] [CrossRef]
- Ang, K.L.M.; Seng, J.K.P.; Ngharamike, E. Towards crowdsourcing internet of things (crowd-iot): Architectures, security and applications. Future Internet 2022, 14, 49. [Google Scholar] [CrossRef]
- Cuervo, E.; Balasubramanian, A.; Cho, D.K.; Wolman, A.; Saroiu, S.; Chandra, R.; Bahl, P. MAUI: Making Smartphones Last Longer with Code Offload. In Proceedings of the 8th ACM International Conference on Mobile Systems, Applications, and Services (MobiSys ’10), San Francisco, CA, USA, 15–18 June 2010; pp. 49–62. [Google Scholar] [CrossRef]
- Chun, B.G.; Ihm, S.; Maniatis, P.; Musuvathi, M.; Roscoe, T.; Witchel, E. CloneCloud: Elastic Execution Between Mobile Device and Cloud. In Proceedings of the 6th ACM European Conference on Computer Systems (EuroSys ’11), Salzburg, Austria, 10–13 April 2011; pp. 301–314. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A survey on mobile edge computing: The communication perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Trestian, R.; Comsa, I.S.; Tuysuz, M.F. Seamless Multimedia Delivery Within a Heterogeneous Wireless Networks Environment: Are We There Yet? IEEE Commun. Surv. Tutor. 2018, 20, 945–977. [Google Scholar] [CrossRef]
- Schildt, S.; Büsching, F.; Wolf, L. DroidCluster: Towards Smartphone Cluster Computing. In Proceedings of the 2012 32nd International Conference on Distributed Computing Systems Workshops, Macau, China, 18–21 June 2012; pp. 114–117. [Google Scholar] [CrossRef]
- Zhou, R.; Wu, X.; Tan, H.; Zhang, R. Two Time-Scale Joint Service Caching and Task Offloading for UAV-assisted Mobile Edge Computing. In Proceedings of the IEEE INFOCOM 2022-IEEE Conference on Computer Communications, London, UK, 2–5 May 2022; pp. 1189–1198. [Google Scholar] [CrossRef]
- Tran, T.X.; Pompili, D. Joint Task Offloading and Resource Allocation for Multi-Server Mobile-Edge Computing Networks. IEEE Trans. Veh. Technol. 2019, 68, 856–868. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Maharjan, S.; Zhang, Y. Joint Load Balancing and Offloading in Vehicular Edge Computing and Networks. IEEE Internet Things J. 2019, 6, 4377–4387. [Google Scholar] [CrossRef]
- Shi, C.; Lakafosis, V.; Ammar, M.H.; Zegura, E.W. Serendipity: Enabling remote computing among intermittently connected mobile devices. In Proceedings of the 13th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Hilton Head, SC, USA, 11–14 June 2012. [Google Scholar] [CrossRef]
- Lin, X.; Jiang, J.; Li, B.; Li, B. Circa: Offloading Collaboratively in the Same Vicinity with iBeacons. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 3751–3756. [Google Scholar] [CrossRef]
- Alwateer, M.; Loke, S.W.; Fernando, N. Enabling Drone Services: Drone Crowdsourcing and Drone Scripting. IEEE Access 2019, 7, 110035–110049. [Google Scholar] [CrossRef]
- Fernandes, J.B.; de Assis, Í.A.; Martins, I.; Barros, T.; Xavier-de-Souza, S. Adaptive Asynchronous Work-Stealing for distributed load-balancing in heterogeneous systems. arXiv 2024, arXiv:2401.04494. [Google Scholar]
- Debnath, H.; Gezzi, G.; Corradi, A.; Gehani, N.; Ding, X.; Curtmola, R.; Borcea, C. Collaborative Offloading for Distributed Mobile-Cloud Apps. In Proceedings of the 2018 6th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Bamberg, Germany, 26–29 March 2018; pp. 87–94. [Google Scholar] [CrossRef]
- Shu, C.; Zhao, Z.; Han, Y.; Min, G.; Duan, H. Multi-User Offloading for Edge Computing Networks: A Dependency-Aware and Latency-Optimal Approach. IEEE Internet Things J. 2020, 7, 1678–1689. [Google Scholar] [CrossRef]
- Liu, G.; Dai, F.; Huang, B.; Qiang, Z.; Wang, S.; Li, L. A Collaborative Computation and Dependency-Aware Task Offloading Method for Vehicular Edge Computing: A Reinforcement Learning Approach. J. Cloud Comput. 2022, 11, 68. [Google Scholar] [CrossRef]
- An, X.; Fan, R.; Hu, H.; Zhang, N.; Atapattu, S.; Tsiftsis, T.A. Joint Task Offloading and Resource Allocation for IoT Edge Computing with Sequential Task Dependency. IEEE Internet Things J. 2022, 9, 16546–16561. [Google Scholar] [CrossRef]
- Li, X.; Abdallah, M.; Lou, Y.Y.; Chiang, M.; Taik Kim, K.; Bagchi, S. Dynamic DAG-Application Scheduling for Multi-Tier Edge Computing in Heterogeneous Networks. arXiv 2024, arXiv:2409.10839. [Google Scholar]
- Fernando, N.; Shrestha, S.; Loke, S.W.; Lee, K. On Edge–Fog–Cloud Collaboration and Reaping Its Benefits: A Heterogeneous Multi-Tier Edge Computing Architecture. Future Internet 2025, 17, 22. [Google Scholar] [CrossRef]
- Ke, H.C.; Wang, H.; Zhao, H.W.; Sun, W.J. Deep Reinforcement Learning-Based Computation Offloading and Resource Allocation in Security-Aware Mobile Edge Computing. Wirel. Netw. 2021, 27, 3357–3373. [Google Scholar] [CrossRef]
- Camps-Mur, D.; Pérez-Costa, X.; Sallent-Ribes, S. Designing energy efficient access points with Wi-Fi Direct. Comput. Netw. 2011, 55, 2838–2855. [Google Scholar] [CrossRef]
- Li, Z.; Chang, V.; Ge, J.; Pan, L.; Hu, H. Energy-Aware Task Offloading with Deadline Constraint in Mobile Edge Computing. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 56. [Google Scholar] [CrossRef]
- Wang, E.; Dong, P.; Xu, Y.; Li, D.; Wang, L.; Yang, Y. Distributed Game-Theoretical Task Offloading for Mobile Edge Computing. In Proceedings of the IEEE 18th International Conference on Mobile Ad Hoc and Smart Systems (MASS), Denver, CO, USA, 4–7 October 2021; pp. 213–220. [Google Scholar] [CrossRef]
- Xie, Z.; Song, X.; Cao, J.; Xu, S. Energy Efficiency Task Scheduling for Battery Level-Aware Mobile Edge Computing in Heterogeneous Networks. ETRI J. 2022, 44, 746–758. [Google Scholar] [CrossRef]
- Meng, S.; Li, Q.; Wu, T.; Huang, W.; Zhang, J.; Li, W. A fault-tolerant dynamic scheduling method on hierarchical mobile edge cloud computing. Comput. Intell. 2019, 35, 577–598. [Google Scholar] [CrossRef]
- Long, T.; Xia, Y.; Ma, Y.; Peng, Q.; Zhao, J. A fault-tolerant workflow scheduling method on deep reinforcement learning-based in edge environment. In Proceedings of the 2022 IEEE International Conference on Networking, Sensing and Control (ICNSC), Shanghai, China, 15–18 December 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Zhang, J.; Liu, Y.; Yeh, E. Result and congestion aware optimal routing and partial offloading in collaborative edge computing. arXiv 2022, arXiv:2205.00714. [Google Scholar] [CrossRef]
- Cao, G.; Singhal, M. Mutable Checkpoints: A New Checkpointing Approach for Mobile Computing Systems. IEEE Trans. Parallel Distrib. Syst. 2001, 12, 157–172. [Google Scholar] [CrossRef]
- Xiao, W.; Fang, X.; Liu, B.; Wang, J.; Zhu, X. UNION: Fault-Tolerant Cooperative Computing in Opportunistic Mobile Edge Cloud. ACM Trans. Internet Technol. 2023, 23, 59. [Google Scholar] [CrossRef]
- Mehrabi, M.; Shen, S.; Latzko, V.; Wang, Y.; Fitzek, F.H.P. Energy-Aware Cooperative Offloading Framework for Inter-dependent and Delay-sensitive Tasks. In Proceedings of the GLOBECOM 2020-2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Blumofe, R.D.; Leiserson, C.E. Scheduling Multithreaded Computations by Work Stealing. J. ACM 1999, 46, 720–748. [Google Scholar] [CrossRef]
- Cruciani, F.; Sun, C.; Zhang, S.; Nugent, C.; Li, C.; Song, S.; Cheng, C.; Cleland, I.; Mccullagh, P. A Public Domain Dataset for Human Activity Recognition in Free-Living Conditions. In Proceedings of the 2019 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Leicester, UK, 19–23 August 2019; pp. 166–171. [Google Scholar] [CrossRef]
- Fleuret, F.; Berclaz, J.; Lengagne, R.; Fua, P. Multicamera People Tracking with a Probabilistic Occupancy Map. IEEE Trans. Pattern Anal. Mach. Intell. 2008, 30, 267–282. [Google Scholar] [CrossRef]
- Kodera, S.; Fujihashi, T.; Saruwatari, S.; Watanabe, T. Multi-view video streaming with mobile cameras. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 1412–1417. [Google Scholar] [CrossRef]
- Zhao, S.; Dai, X.; Bate, I.; Burns, A.; Chang, W. DAG Scheduling and Analysis on Multi-Core Systems by Modelling Parallelism and Dependency. IEEE Trans. Parallel Distrib. Syst. 2022, 33, 4019–4038. [Google Scholar] [CrossRef]
- Marchetti-Spaccamela, A.; Megow, N.; Schlöter, J.; Skutella, M.; Stougie, L. On the Complexity of Conditional DAG Scheduling in Multiprocessor Systems. In Proceedings of the 2020 IEEE International Parallel and Distributed Processing Symposium (IPDPS), New Orleans, LA, USA, 18–22 May 2020; pp. 1061–1070. [Google Scholar] [CrossRef]




| Framework | Core Components and Contributions |
|---|---|
| Honeybee [17] |
|
| Honeybee-T [19] |
|
| Honeybee-RS [20] |
|
| BTVMCC [21] |
|
| Honeybee-Tx (this work) |
|
| Symbol | Description |
|---|---|
| Capability Assessment Parameters | |
| Capability score for device i based on CPU, memory, and energy | |
| Weighting parameters for CPU, memory, and energy in capability score calculation, with | |
| Normalized score for CPU performance of device i | |
| Normalized score for memory availability of device i | |
| Normalized score for energy status of device i | |
| Capability vector of worker w: , which represents the worker’s currently available, normalized resources for CPU, memory, and energy. | |
| Demand vector of job t: , which represents the job’s estimated CPU, memory, and energy requirements needed for execution. | |
| Network quality metric (0 = poor, 1 = excellent) based on latency. | |
| Minimum score threshold for job-worker matching | |
| Dependency and Job Management | |
| Set of prerequisite jobs that must complete before job can begin | |
| Set of prerequisite jobs for a synchronization job | |
| Periodic interval for checking job availability | |
| Load threshold for steal request approval. This is a configurable threshold representing the minimum load factor the delegator must be experiencing before it approves a steal request from a worker. | |
| Job state (e.g., READY, RUNNING, COMPLETED, FAILED) | |
| Resilience and Checkpoint Parameters | |
| Adaptive progress threshold for checkpointing | |
| Minimum and maximum bounds for adaptive progress threshold | |
| Base progress threshold before adaptation | |
| Normalized job criticality metric | |
| Normalized job size metric | |
| Current progress of a job (0.0–1.0) | |
| Progress at last checkpoint (0.0–1.0) | |
| Video Processing Parameters | |
| Incoming video stream | |
| Segment length for video partitioning | |
| Tiered grouping of devices by capability | |
| DAG for video processing pipeline | |
| Contribution | Innovation | Key Differentiator |
|---|---|---|
| C1: Heterogeneity-Aware Job Stealing | Capability-aware matching using weighted scoring (, , parameters) that dynamically adapts to device profiles | Goes beyond binary capable/incapable decisions; considers nuanced resource vectors |
| C2: Generalized DAG Work Stealing | Supports arbitrary task graphs with complex dependencies, not limited to parent-child relationships | Extends classical work stealing to handle general DAGs in mobile environments |
| C3: Resilience via Staged Result Management | Adaptive checkpointing and staged transfers that balance resilience vs. overhead based on worker reliability and job criticality | Reduces recovery time from O(job duration) to O(checkpoint interval) |
| ID | Model | Role | CPU | RAM | Android |
|---|---|---|---|---|---|
| A | OnePlus 5T | Delegator | Snapdragon 835 | 8 GB | 10 |
| B | Pixel 7 | Worker | Tensor G2 | 8 GB | 14 |
| C | Pixel 6 Pro | Worker | Tensor | 12 GB | 13 |
| D | Pixel 6 Pro | Worker | Tensor | 12 GB | 13 |
| E | Pixel 6 Pro | Worker | Tensor | 12 GB | 13 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Segu Nagesh, S.; Fernando, N.; Loke, S.W.; Neiat, A.G.; Pathirana, P.N. A Dependency-Aware Task Stealing Framework for Mobile Crowd Computing. Future Internet 2025, 17, 446. https://doi.org/10.3390/fi17100446
Segu Nagesh S, Fernando N, Loke SW, Neiat AG, Pathirana PN. A Dependency-Aware Task Stealing Framework for Mobile Crowd Computing. Future Internet. 2025; 17(10):446. https://doi.org/10.3390/fi17100446
Chicago/Turabian StyleSegu Nagesh, Sanjay, Niroshinie Fernando, Seng W. Loke, Azadeh Ghari Neiat, and Pubudu N. Pathirana. 2025. "A Dependency-Aware Task Stealing Framework for Mobile Crowd Computing" Future Internet 17, no. 10: 446. https://doi.org/10.3390/fi17100446
APA StyleSegu Nagesh, S., Fernando, N., Loke, S. W., Neiat, A. G., & Pathirana, P. N. (2025). A Dependency-Aware Task Stealing Framework for Mobile Crowd Computing. Future Internet, 17(10), 446. https://doi.org/10.3390/fi17100446









