Realization of Authenticated One-Pass Key Establishment on RISC-V Micro-Controller for IoT Applications
Abstract
1. Introduction
- This research was the first to propose utilizing a signcryption key encapsulation mechanism in composition with an Elliptic Curve Qu–Vanstone (ECQV) implicit certificate scheme [16] to construct a two-level key establishment protocol. By applying a hybrid cryptosystem, the proposed protocol preserves the security characteristics of both schemes and takes advantage of both public key cryptography and symmetric cryptography. Depending on the demand of the security level, the protocol, at the very least, can enable a fast rekeying method of session keys derived from a generated key pair, allowing for sending session key generation materials and encrypted sensor data in one message exchange. At a higher level of security, the protocol allows for updating the public and private key pair; hence, only several sessions share a key pair to derive the session keys. At the highest security level, every communication session can issue a fresh key pair and session key to communicate.
- Under a two-party communication model, our approach integrates a physical unclonable function to the ECQV scheme to provide additional authentication data to the handshake. This lightweight solution enhances the ECQV scheme and allows for only authenticated node devices to request a key pair. Thus, the modified ECQV scheme can protect against common attacks, such as impersonation attacks and replay attacks.
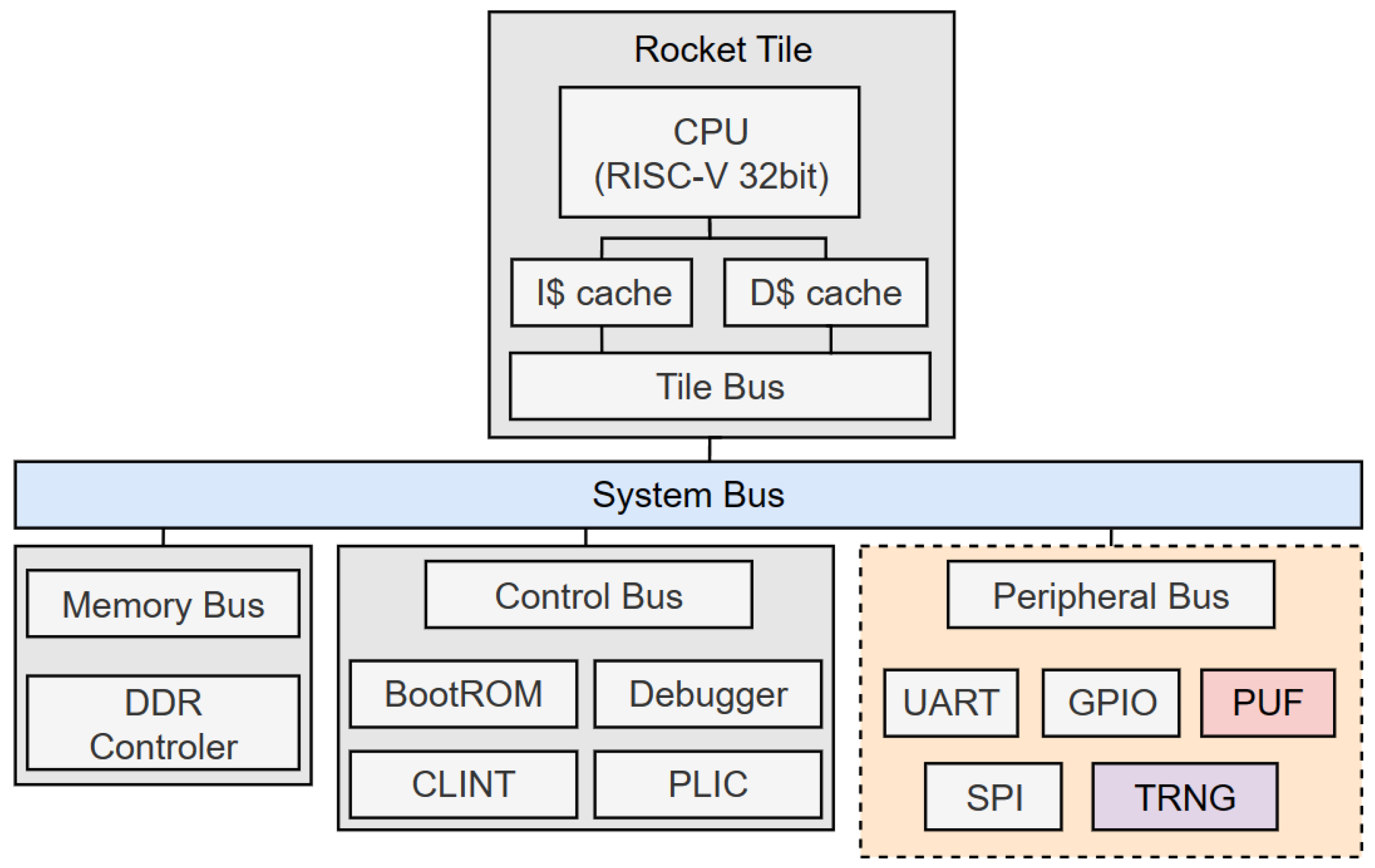
- We implemented a 32-bit RISC-V system that is suitable for a resource-constrained sensor node to assess the computational overheads of the proposed protocol. The software version of the protocol was tested on different configurations of the RISC-V processor to evaluate the timing cost. Moreover, instead of using software-based or pseudo-security primitives, the RISC-V system is equipped with standard physical security primitives, including a true random number generator (TRNG) and a PUF.
2. Preliminary Background
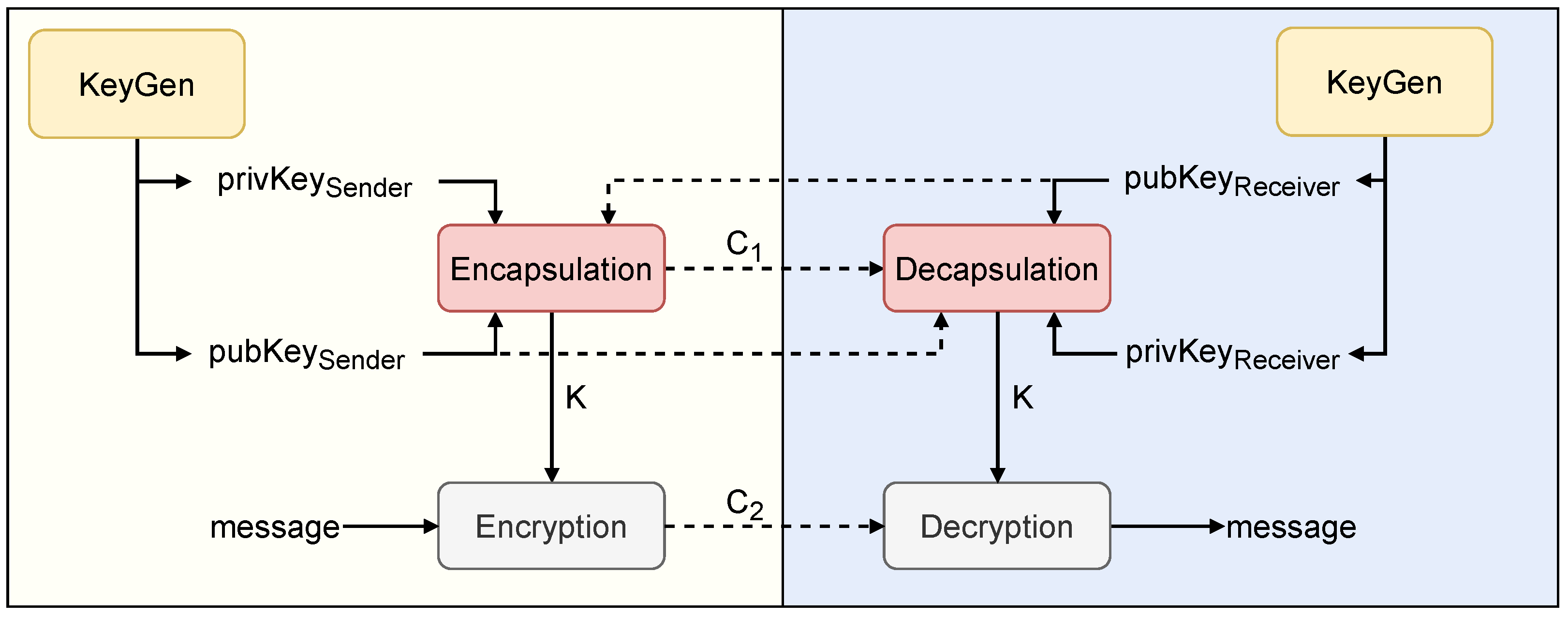
2.1. Hybrid Cryptosystem
- A key generation operation that outputs a public and private key pair. The generation of a key pair depends on the chosen underlying algorithm.
- An encapsulation operation that takes a key pair of the sender, and a public key of the receiver, and outputs a shared key K and an encapsulated text .
- A decapsulation operation that takes a key pair of the receiver, a public key of the sender, and an encapsulated text , and extracts the shared key K if the operation is valid.
2.2. ECQV Implicit Certificate Scheme
2.3. Signcryption
3. Proposed Key Exchange Protocol
3.1. Security Model Assumption
3.2. Practical Application of ECQV and One-Pass SKEM Methodologies
- The session key generation with signcryption gives assurance to the sender that the session key is available only to the recipient and assurance to the recipient that the key came from the sender.
- One-pass key establishment provides a very efficient construction of session keys, which reduces the complexity of the handshake and computation at the sensor nodes.
- The encrypted sensor data can be transmitted simultaneously with key generation materials, which favors the intermittent operation of the sensor nodes.
3.3. Protocol Proposal
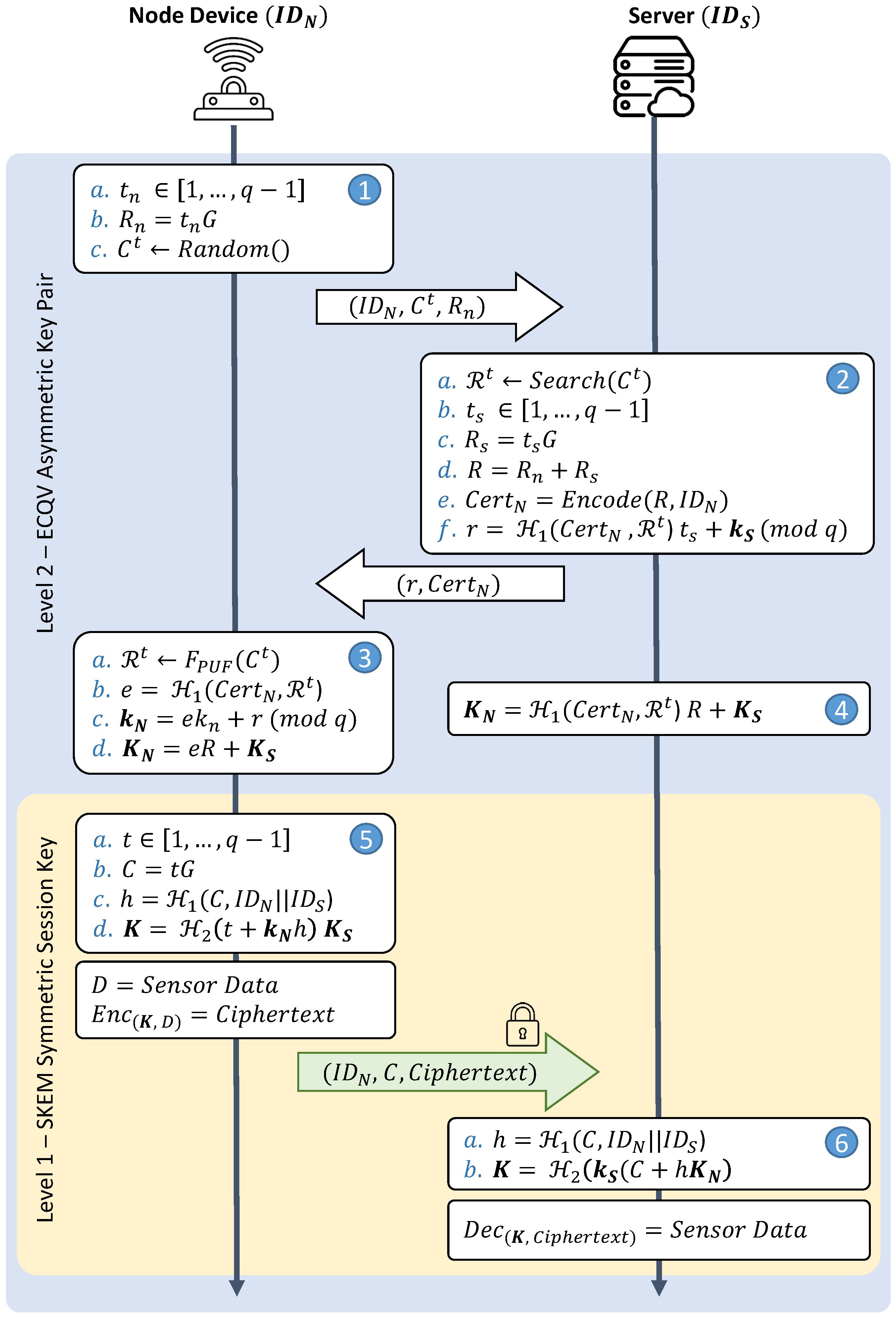
3.3.1. Level 2: ECQV Asymmetric Key
- Step 1—Certificate request: A node generates a random number and calculates the corresponding elliptic curve point using . The random number must be securely stored at the node side; then, the point , the node’s identity , and a randomly chosen challenge are sent to the server as a certificate request.
- Step 2—Certificate generation: After receiving the request, the server generates another random number and its corresponding point (). Then, the implicit certificate is generated through hashing an elliptic curve point . Upon storing the challenge–response pair, the server computes the implicit signature r with the corresponding response of the received challenge .
- Step 3—Key extraction: After receiving the implicit certificate, the node generates the response from the previously selected challenge . Afterward, it extracts its designated key pair using .
- Step 4—The server can compute the public key of the node with Equations (2) and (3) by itself, thus reducing the cost of a message from the node to share its public key.
3.3.2. Level 1: One-Pass SKEM Symmetric Session Key
- Step 5—Key encapsulation: The node device generates a random point C on the elliptic curve. Then, the encapsulation of the random point C and the s of the node and the server are computed:The session key is created at the node side using the encapsulation, the node’s private key, and the server’s public key. The session key is computed as follows:With the session key, the node can encrypt its data and send it to the server. Thanks to the one-way design of SKEM, the node can combine the ciphertext and the materials to generate the same session key into a compound message. Then, it transmits the message to the server.
- Step 6—Key decapsulation: After receiving the information, the server retrieves each segment and starts computing the session key:
4. Security Analysis
- (a)
- Mutual authentication: In the level 1 secure channel, signcryption assures that only the intended participants with valid identities can extract the correct session key K. The modified ECQV scheme guarantees the server that only the sensor node having and a valid CPR can derive the correct key pair () from the implicit certificate. On the other hand, knowing the server is the only one having stored its CRPs, the sensor node can be certain that only the server (with its valid private key ) can derive the correct session key K. Therefore, the proposed protocol can achieve mutual authentication even for level 1 security communication channels.
- (b)
- Integrity: Both parties using ECQV and SKEM schemes verify their knowledge of a key pair and a symmetric key after successfully using the keys. Thus, the content of the exchange messages can be verified after meaningful communication is conducted. Any modification of the messages will result in invalid keys and meaningless decrypted messages.
- (c)
- Impersonation attack:
- Node impersonation attack: We assumed that an adversary tries to impersonate a node with to communicate with the server. At level 1 security, the adversary cannot compute the session key due to lacking a valid key pair () that is bound to the and the PUF’s response . While at level 2 security, the adversary cannot replicate a PUF primitive on the node; hence, it cannot derive the valid key pair () without knowledge of the response .
- Server impersonation attack: With one-pass SKEM, the server does not respond to the sensor node; thus, we assumed that an adversary tries to impersonate the server to issue the implicit certificate. This attack is only possible if the adversary can break into the server and retrieve the CRP database. Otherwise, the certificate issued by the adversary is meaningless and shall result in an invalid key pair ().
As a result, the malicious adversary cannot impersonate either a legitimate server or an IoT device. - (d)
- Known session key attack: A protocol with this property can prevent an adversary from accessing future communication to the server, even if they obtain one or more previous session keys. In the proposed protocol, the generation of a sensor node’s key pair and session keys requires ephemeral random materials. Therefore, if the session keys are revealed, the future communication channels will remain secure.
- (e)
- Node capture attack: We assumed that an adversary has captured a node with . Through physical memory disclosure attacks, the adversary can retrieve stored data on the node device, such as the valid key pair. As a result, the communication with the level 1 channel would be compromised. To eliminate the risk, a level 2 secure channel computes a fresh key pair (requiring new random numbers and shuffling with new CRP) for every communication session. Another approach to mitigate the risk is to periodically update the key pair by triggering the ECQV scheme after a certain period. Consequently, the proposed protocol offers two methods: (a) complete immunity to the node capture attack and (b) a method that minimizes data leaking.
- (f)
- Perfect/partial forward secrecy: Perfect forward secrecy is a security property that ensures that compromising the key pair of one or both entities does not lead to the compromise of past session key establishment. Partial forward secrecy refers to a situation where some, but not all, past communications remain confidential, even if the key pairs are compromised. The level 1 secure channel can offer partial forward secrecy in the case of updating a node’s key pair after a certain time. In contrast, triggering the ECQV scheme at level 2 security creates ephemeral key pairs, meaning that one session key corresponds to one key pair. A three-pass handshake can ensure perfect forward secrecy.
- (g)
- Replay attack: A replay attack is a form of network attack where an attacker intercepts and maliciously retransmits data that was previously recorded. A one-pass SKEM is susceptible to this kind of attack. Gorantla addressed some solutions to this problem by assigning a session ID for every communication session or applying a time stamp [25]. Updating the key pair of a node is a method to mitigate the issue. Therefore, a secure channel at level 2 can completely prevent this kind of attack.
- (h)
- Message modification attack: As we discussed regarding the integrity property, if an attacker manages to capture and alter any part of a message being exchanged over a secure channel, it can result in different keys being extracted by both the sensor node and the server. This can also cause both parties to fail to agree upon the same session key. Consequently, the communication is meaningless and will not leak any critical information; therefore, the protocol is immune to modification attacks.
5. Performance Evaluation
5.1. Communication Overhead
5.2. Computation Overhead
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Aras, E.; Ramachandran, G.S.; Lawrence, P.; Hughes, D. Exploring the Security Vulnerabilities of LoRa. In Proceedings of the 2017 3rd IEEE International Conference on Cybernetics (CYBCONF), Exeter, UK, 21–23 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Sundaram, J.P.S.; Du, W.; Zhao, Z. A Survey on LoRa Networking: Research Problems, Current Solutions, and Open Issues. IEEE Comm. Surv. Tutor. 2019, 22, 371–388. [Google Scholar] [CrossRef]
- Loukil, S.; Fourati, L.C.; Nayyar, A.; In, C.S. Investigation on Security Risk of LoRaWAN: Compatibility Scenarios. IEEE Access 2022, 10, 101825–101843. [Google Scholar] [CrossRef]
- Han, J.; Wang, J. An Enhanced Key Management Scheme for LoRaWAN. Cryptography 2018, 2, 34. [Google Scholar] [CrossRef]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Enhancing the Security of the IoT LoraWAN Architecture. In Proceedings of the International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris, France, 22–25 November 2016; pp. 1–7. [Google Scholar]
- Pu, C.; Zerkle, H.; Wall, A.; Lim, S.; Choo, K.-K.R.; Ahmed, I. A Lightweight and Anonymous Authentication and Key Agreement Protocol for Wireless Body Area Networks. IEEE Internet Things J. 2022, 9, 21136–21146. [Google Scholar] [CrossRef]
- Zheng, Y.; Chang, C.-H. Secure Mutual Authentication and Key-Exchange Protocol between PUF-Embedded IoT Endpoints. In Proceedings of the 2021 IEEE International Symposium on Circuits and Systems (ISCAS), Daegu, Republic of Korea, 22–28 May 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Torres, N.; Pinto, P.; Lopes, S.I. Security Vulnerabilities in LPWANs—An Attack Vector Analysis for the IoT Ecosystem. Appl. Sci. 2021, 11, 3176. [Google Scholar] [CrossRef]
- Keoh, S.L.; Kumar, S.S.; Tschofenig, H. Securing the Internet of Things: A Standardization Perspective. IEEE Internet Things J. 2014, 1, 265–275. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Piro, G.; Boggia, G.; Bianchi, G. Public Key Authentication and Key Agreement in IoT Devices with Minimal Airtime Consumption. IEEE Embed. Syst. Lett. 2017, 9, 1–4. [Google Scholar] [CrossRef]
- Rehman, A.; Haseeb, K.; Fati, S.M.; Lloret, J.; Peñalver, L. Reliable Bidirectional Data Transfer Approach for the Internet of Secured Medical Things Using ZigBee Wireless Network. Appl. Sci. 2021, 11, 9947. [Google Scholar] [CrossRef]
- Gaabouri, I.E.; Senhadji, M.; Belkasmi, M.; Bhiri, B.E. A Systematic Literature Review on Authentication and Threat Challenges on RFID Based NFC Applications. Future Internet 2023, 15, 354. [Google Scholar] [CrossRef]
- Mao, G.; Liu, Y.; Dai, W.; Li, G.; Zhang, Z.; Lam, A.H.F.; Cheung, R.C.C. REALISE-IoT: RISC-V-Based Efficient and Lightweight Public-Key System for IoT Applications. IEEE Internet Things J. 2024, 11, 3044–3055. [Google Scholar] [CrossRef]
- Li, B.; Zhang, G.; Lei, S.; Fu, H.; Wang, J. A Lightweight Authentication and Key Agreement Protocol for IoT Based on ECC. In Proceedings of the 2021 International Conference on Advanced Computing and Endogenous Security, Nanjing, China, 21–22 April 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Zhang, W.; Lin, D.; Zhang, H.; Chen, C.; Zhou, X. A Lightweight Anonymous Mutual Authentication with Key Agreement Protocol on ECC. In Proceedings of the IEEE Trustcom/BigDataSE/ICESS, Sydney, Australia, 1–4 August 2017; pp. 170–176. [Google Scholar] [CrossRef]
- Certicom Research. SEC 4: Elliptic Curve Qu-Vanstone Implicit Certificate Scheme (ECQV); Certicom Research: Mississauga, ON, Canada, 2013. [Google Scholar]
- Cramer, R.; Shoup, V. Design and Analysis of Practical Public-Key Encryption Schemes Secure against Adaptive Chosen Ciphertext Attack. SIAM J. Comp. 2003, 33, 167–226. [Google Scholar] [CrossRef]
- Bjørstad, T.E.; Dent, A.W. Building Better Signcryption Schemes with Tag-KEMs. In Proceedings of the International Conference on Public Key Cryptography (PKC), New York, NY, USA, 24–26 April 2006; pp. 491–507. [Google Scholar] [CrossRef]
- Bjørstad, T.E.; Dent, A.W.; Smart, N.P. Efficient KEMs with Partial Message Recovery. In Proceedings of the International Conference on Cryptography and Coding, London, UK, 12–14 December 2023; pp. 233–256. [Google Scholar] [CrossRef]
- Barnes, R.; Bhargavan, K.; Lipp, B.; Wood, C. RFC9180-Hybrid Public Key Encryption. February 2022. Available online: https://www.rfc-editor.org/rfc/rfc9180.html (accessed on 2 February 2024).
- Zheng, Y. Digital Signcryption or How to Achieve Cost(Signature & Encryption) << Cost(Signature) + Cost(Encryption). In Proceedings of the Annual International Cryptology Conference CRYPTO ’97, Santa Barbara, CA, USA, 17–21 August 1997; Volume 1294, pp. 165–179. [Google Scholar]
- Dent, A.W. Hybrid Cryptography. IACR Cryptology ePrint Archive, 2004. p. 210. Available online: https://eprint.iacr.org/2004/210 (accessed on 30 April 2024).
- Dent, A.W. Hybrid Signcryption Schemes with Outsider Security. In Proceedings of the Information Security (ISC 2005), Singapore, 20–23 September 2005; pp. 203–217. [Google Scholar]
- Dent, A.W. Hybrid Signcryption Schemes with Insider Security. In Proceedings of the Information Security and Privacy (ACISP), Brisbane, Australia, 4–6 July 2005; pp. 253–266. [Google Scholar]
- Gorantla, M.C.; Boyd, C.; Nieto, G.; Manuel, J. On the Connection between Signcryption and One-Pass Key Establishment. In Proceedings of the Cryptography and Coding, Cirencester, UK, 18–20 December 2007; pp. 277–301. [Google Scholar]
- Krawczyk, H. HMQV: A High-performance Secure Diffie-Hellman Protocol. In Proceedings of the Annual International Conference on Advances in Cryptology (CRYPTO), Santa Barbara, CA, USA, 14–18 August 2005; pp. 546–566. [Google Scholar]
- Okamoto, T.; Tso, R.; Okamoto, E. One-Way and Two-Party Authenticated ID-Based Key Agreement Protocols Using Pairing. In Proceedings of the International Conference on Modeling Decisions for Artificial Intelligence (MDAI), Tsukuba, Japan, 25–27 July 2005; pp. 122–133. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Reddy, A.G.; Yoon, E.-J.; Yoo, K.-Y. Secure Signature-Based Authenticated Key Establishment Scheme for Future IoT Applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Porambage, P.; Braeken, A.; Schmitt, C.; Gurtov, A.; Ylianttila, M.; Stiller, B. Group Key Establishment for Enabling Secure Multicast Communication in Wireless Sensor Networks Deployed for IoT Applications. IEEE Access 2015, 3, 1503–1511. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Vasilakos, A.V. Designing Secure User Authentication Protocol for Big Data Collection in IoT-Based Intelligent Transportation System. IEEE Internet Things J. 2021, 8, 7727–7744. [Google Scholar] [CrossRef]
- Porambage, P.; Schmitt, C.; Kumar, P.; Gurtov, A.; Ylianttila, M. Two-phase Authentication Protocol for Wireless Sensor Networks in Distributed IoT Applications. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 2728–2733. [Google Scholar] [CrossRef]
- Pu, C.; Lim, S. A Light-Weight Countermeasure to Forwarding Misbehavior in Wireless Sensor Networks: Design, Analysis, and Evaluation. IEEE Syst. J. 2018, 12, 834–842. [Google Scholar] [CrossRef]
| Symbols | Corresponding Meaning | |
|---|---|---|
| The identity | ||
| G | The base point of ECC | |
| Parameters | q | A prime order of a specific elliptic curve |
| and | A challenge and its corresponding response at time t | |
| variables | Generated random values in | |
| Curve points generated from random values | ||
| Implicit certificate designated for a node with | ||
| A private–public key pair of the server | ||
| Keys | A private–public key pair of a node with | |
| K | A symmetric session key | |
| Hash modulo function | ||
| Hash function | ||
| Functions | Function of a PUF | |
| Encryption algorithm using the symmetric key K | ||
| Decryption algorithm using the symmetric key K |
| Features | Proposed | Proposed | [14] | [28] | [29] | [30] | [31] |
|---|---|---|---|---|---|---|---|
| Level 2 | Level 1 | ||||||
| Mutual authentication | • | • | • | • | • | • | • |
| Integrity | • | • | • | • | • | • | • |
| Impersonation attack | • | • | • | • | • | • | ∘ |
| Session key attack | • | • | • | • | ∘ | • | • |
| Node capture attack | • | ∘ | ∘ | • | • | • | ∘ |
| Perfect forward secrecy | • | • | • | • | • | • | • |
| Replay attack | • | ∘ | • | • | ∘ | • | ∘ |
| Message modification attack | • | • | • | • | • | • | • |
| Anonymity | ∘ | ∘ | • | • | ∘ | • | ∘ |
| Protocol | Number of | Total Message |
|---|---|---|
| Messages | Size (Bytes) | |
| Ours—level 2 | 3 | 160 |
| Ours—level 1 | 1 | 40 |
| [14] | 4 | 168 |
| [28] | 3 | 316 |
| [29]—Protocol #1 | 4 | 420 |
| [29]—Protocol #2 | 2 | 142 |
| [30] | 3 | 332 |
| Notation | Description | RV32-IMAC #Cycle | RV32-I #Cycle |
|---|---|---|---|
| Hash function | 13,943 ± 10 | 14,178 ± 7 | |
| ECC scalar multiplication | 129,821,421 ± 26,894 | 136,189,184 ± 17,860 | |
| ECC point addition | 266,589 ± 32 | 274,658 ± 13 | |
| * | Random number generation | 80,649 ± 20 | 82,349 ± 9 |
| * | PUF function | 135,810 ± 14 | 137,442 ± 28 |
| Modulo | 23,711 ± 4 | 25,160 ± 18 | |
| Big number addition | 698 ± 2 | 838 ± 1 | |
| Big number multiplication | 5009 ± 5 | 5075 ± 6 |
| Protocol | Sensor Node | Sever |
|---|---|---|
| Ours—level 2 | ||
| Ours—level 1 | ||
| [14] | ||
| [28] | ||
| [29]—Protocol 1 | 11 | 4 |
| [29]—Protocol 2 | 5 | 3 |
| [30] |
| Proposed Protocol | Computation | #Cycle | Time (ms) | |
|---|---|---|---|---|
| Level 2 ECQV Asymmetric key pair | 1.a | 105,810 ± 24 | 2.11 | |
| 1.b | 130,443,888 ± 56,314 | 2608.88 | ||
| 1.c | 80,649 ± 20 | 1.78 | ||
| 3.a | 135,810 ± 14 | 2.72 | ||
| 3.b | 39,103 ± 28 | 0.78 | ||
| 3.c | 30,867 ± 20 | 0.62 | ||
| 3.d | + | 130,789,946 ± 56,350 | 2615.80 | |
| Subtotal | 261,626,073 | 5232.69 | ||
| Level 1 SKEM Symmetric session key | 5.a | 105,810 ± 20 | 2.11 | |
| 5.b | 130,443,888 ± 56,314 | 2608.88 | ||
| 5.c | 39,103 ± 28 | 0.78 | ||
| 5.d | 130,463,538 ± 56,326 | 2609.27 | ||
| Subtotal | 261,052,339 | 5221.04 | ||
| Total | 522,678,412 | 10,453.73 | ||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dang, T.-K.; Nguyen, K.-D.; Kieu-Do-Nguyen, B.; Hoang, T.-T.; Pham, C.-K. Realization of Authenticated One-Pass Key Establishment on RISC-V Micro-Controller for IoT Applications. Future Internet 2024, 16, 157. https://doi.org/10.3390/fi16050157
Dang T-K, Nguyen K-D, Kieu-Do-Nguyen B, Hoang T-T, Pham C-K. Realization of Authenticated One-Pass Key Establishment on RISC-V Micro-Controller for IoT Applications. Future Internet. 2024; 16(5):157. https://doi.org/10.3390/fi16050157
Chicago/Turabian StyleDang, Tuan-Kiet, Khai-Duy Nguyen, Binh Kieu-Do-Nguyen, Trong-Thuc Hoang, and Cong-Kha Pham. 2024. "Realization of Authenticated One-Pass Key Establishment on RISC-V Micro-Controller for IoT Applications" Future Internet 16, no. 5: 157. https://doi.org/10.3390/fi16050157
APA StyleDang, T.-K., Nguyen, K.-D., Kieu-Do-Nguyen, B., Hoang, T.-T., & Pham, C.-K. (2024). Realization of Authenticated One-Pass Key Establishment on RISC-V Micro-Controller for IoT Applications. Future Internet, 16(5), 157. https://doi.org/10.3390/fi16050157







