Abstract
In today’s advanced network and digital age, the Internet of Things network is experiencing a significant growing trend and, due to its wide range of services and network coverage, has been able to take a special place in today’s technology era. Among the applications that can be mentioned for this network are the field of electronic health, smart residential complexes, and a wide level of connections that have connected the inner-city infrastructure in a complex way to make it smart. The notable and critical issue that exists in this network is the extent of the elements that make up the network and, due to this, the strong and massive data exchanges at the network level. With the increasing deployment of the Internet of Things, a wide range of challenges arise, especially in the discussion of establishing network security. Regarding security concerns, ensuring the confidentiality of the data being exchanged in the network, maintaining the privacy of the network nodes, protecting the identity of the network nodes, and finally implementing the security policies required to deal with a wide range of network cyber threats are of great importance. A fundamental element in the security of IoT networks is the authentication process, wherein nodes are required to validate each other’s identities to ensure the establishment of secure communication channels. Through the enforcement of security prerequisites, in this study, we suggested a security protocol focused on reinforcing security characteristics and safeguarding IoT nodes. By utilizing the security features provided by Elliptic Curve Cryptography (ECC) and employing the Elliptic Curve Diffie–Hellman (ECDH) key-exchange mechanism, we designed a protocol for authenticating nodes and establishing encryption keys for every communication session within the Internet of Things. To substantiate the effectiveness and resilience of our proposed protocol in withstanding attacks and network vulnerabilities, we conducted evaluations utilizing both formal and informal means. Furthermore, our results demonstrate that the protocol is characterized by low computational and communication demands, which makes it especially well-suited for IoT nodes operating under resource constraints.
1. Introduction
In recent years, the rapid progress of technology has caused considerable advancement in both the network industry and communication infrastructure, which has introduced a modern networking concept named the Internet of Things (IoT) to the realm of networks and technology [1,2]. Furthermore, the imperative issue is that the IoT has established its position in the current communication landscape, demonstrating notable importance and effectiveness in facilitating the connection of a wide range of elements and devices [3,4]. A specialized network category known as Low-Power and Lossy Networks (LLNs) has been identified within the communication infrastructure of the Internet of Things [5,6]. The utilization of LLNs can be seen as both effective and practical in the design and development of infrastructure and business devices, contributing to the emergence of new markets. Within the expansive domain covered by the IoT, low-power networks (LLNs) are featured, incorporating devices with restricted resources such as sensors and Radio Frequency Identification (RFID) tags [7]. The routing procedure for network elements possessing restricted resources within Low-Power and Lossy Networks necessitates a protocol capable of operating effectively within the present constraints while also fulfilling the necessary criteria [8]. In light of the challenges that arise due to the constraints encountered by Low-Power and Lossy Networks (LLNs) in facilitating communication within an Internet of Things (IoT) network, the Internet Engineering Task Force (IETF) put forth a practical and efficient protocol known as 6LOWPAN to assist these components [9]. The IoT network addresses a diverse set of applications, including intelligent urban infrastructure, advanced transportation technology, smart agriculture, rapid odor detection [10], health care, earthquake alert and detection systems, and intelligent electricity distribution systems [11]. The IoT faces many security challenges, which can be classified into two distinct groups: foundational security aspects that IoT should provide, and the specific security concerns at every level of the IoT framework. Two factors pose security challenges within the network [10]: (a) The nature of advanced networking technology—utilizing lightweight encryption and decryption algorithms known for streamlined operations and implementation. (b) Utilizing standardized protocols can be used to reduce the amount of data that network nodes exchange with one another. Challenges that affect the security and privacy of network components are addressed during the implementation phase of secure communications within the IoT. The technology of this network includes various components at the network level, so ensuring secure communication for all components is a significant challenge. Also, a substantial volume of data are transmitted within the Internet of Things network, which causes concerns about data privacy and confidentiality. However, the network is populated with a large number of devices, which makes it challenging to identify, evaluate, and monitor them to ensure compliance with security policies [12]. Within frameworks, data play a vital role, particularly in industrial infrastructures where sensitive and influential data play a vital role in system decisions and security is a critical consideration. Since the transmission of data takes place via an unsecured channel, attackers have the capability to intercept the data harvested from the sensors without difficulty. In addition, attackers possess the ability to impersonate user nodes, sensor nodes, or gateway nodes, thereby enabling them to conduct various attacks such as replay attacks and guessing attacks. Therefore, to ensure the safety of communication within the network, which involves communication between industrial users and sensors, as well as communication from sensors through gateway nodes, it is vital to design communication protocols following the specific requirements of these components. In addition, it is crucial to establish mutual authentication as an essential security measure that must be ensured. Considering the prevailing difficulties and the presented criteria for the Internet of Things, our primary aim has been to establish a protocol for deploying the security processes and necessary authentication mechanisms. Today, we are faced with significant advances in technology, and new technologies are emerging every day that can serve as a fundamental component in IoT systems and applications. This new structure with the technologies used in it imposes more threats, and the understanding of the security risks, the importance of security, and the potential solutions has significant gaps.
This is because all communication is based on an open channel and data are being exchanged within it. These conditions provide the ability to access and collect data to network adversaries and should provide safe conditions for all network nodes by implementing appropriate security policies. Also, network attackers will undoubtedly discover the Internet of Things as a smart and talented new space to enhance their unethical activities. According to them, the security requirements for the IoT include privacy, reliability, access, authentication, etc. [13]. Figure 1 shows the different components that are connected in an Internet of Things network. In this article, we examine the existing vulnerabilities and security requirements of the Internet of Things. Due to the extensive variety of devices, components, and users that make up the IoT network, the issues of exchanged information security, stored data, and privacy of the components are all serious challenges. With the endangerment of any of the mentioned cases, network attackers who have hostile intentions (such as delaying information packets and network services or even creating conditions for accessing unauthorized data) can cause significant destructive effects on the network. Also, another significant concern in the IoT network is the presence of limited computational capabilitiy nodes in this network, which forces the network to use a symmetric cryptography system to implement the confidentiality policies of the security infrastructure. The disclosure of the symmetric keys jeopardizes not only the existence of the connection but also compromises all network connections, resulting in the loss of information confidentiality. To address these security weaknesses, we propose a key-agreement and multiple authentication protocol to enhance the IoT node safety and protection policies. In the proposed plan to address the stability issue of the symmetric key, a mechanism has been implemented for communication entities to generate their unique symmetric key in each session. Additionally, due to the weakness and high vulnerability of nodes that have little computing power, we tried to implement the protocol process operations in a way that not only provides security mechanisms but also requires minimal processing power.
Figure 1.
Internet of Things communication.
The protocol contributed as follows.
1.1. Improving the Symmetric Encryption System
By taking advantage of the security advantages of the ECDH protocol, a mechanism has been implemented in the process of the presented protocol, so that the communication parties can generate the needed symmetric key. This key is used to encrypt the messages being exchanged in the protocol process and is used instead of the fixed symmetric key selected by the network. The symmetric key generated by the communication parties is unique and its security is guaranteed by the ECDH protocol.
1.2. The Implementation of the Key-Agreement Process Based on ECDH Protocol
The security protocol generates a secure session key for the communicating entities after the secure completion of the protocol process under mutual authentication conditions for the communicating entities.
1.3. Multiple Authentication Mechanisms Based on ECDH Protocol
During the presented protocol process, the private parameters of communication nodes and ECDH protocol are employed to implement an efficient authentication mechanism. Network entities examine each other’s identity by using private and secure items with multiple parameters, which increases the security of the provided protocol against network attacks.
1.4. A Considerably Low Computational Cost of Protocol Process Operations
With the awareness that nodes with low-power features contribute to the network, our protocol not only preserves its security features but also substantially reduces the computation time required for its operations. The suggested protocol has effectively offered significantly reduced computational time compared to the previously mentioned protocols.
1.5. Evaluating the Protocol’s Security and Performance
We evaluated our proposed protocol in both formal and informal security assessments. Additionally, we compared the presented method with similar protocols, considering security, efficiency, and computational cost. The results of the evaluations show that the proposed protocol provided better performance than similar designs in terms of security, operation calculations, and communication cost.
Following this, the three main theories of elliptic curve cryptography, specifically ECC, ECDLP, and ECDH, and their advantages are utilized within the suggested approach, and the safety concerns that have affected the Internet of Things are explained. Figure 1 shows the communication infrastructure and components of the network.
2. Basic Concept
In key-agreement and authentication protocols, various techniques and methods are utilized to implement security policies and ensure essential security features. In our presented method, the encryption system theories were utilized during the protocol process to implement the security policies. These theories are subsets of the ECC cryptosystem, each offering unique security features. Each of these is detailed in this section of the article.
2.1. Fundamental Principles of the Utilized Cryptographic Framework
Elliptic curve cryptography, abbreviated as ECC in the world of cryptography, is a public key cryptographic system. This encryption system is designed by using algebraic structural features and implementing elliptic curves on finite fields. Among the features of this encryption system, we can point out the short key length and provide higher security, which is used in key-exchange protocols, digital signature mechanisms, and pseudo-random generators. In the following, the ECC process and theories related to this encryption system are described.
2.1.1. Theoretical Foundations of Elliptic Curve Cryptography
In the realm of contemporary public-key cryptographic methods, Elliptic Curve Cryptography (ECC) stands out as a sophisticated approach derived from the principles of elliptic curve theory. This form of asymmetric encryption is renowned for its capacity to generate keys that are not only more compact and faster but are also superior in efficiency. Within the ECC framework, a mathematical operation is employed to amalgamate a pair of distinct keys, which subsequently serve the purpose of encoding and decoding information. The foundational element of this cryptographic system is an elliptical curve denoted as E, accompanied by a collection of coordinate points on the curve, expressed as (x, y). The representation of these points adheres to specific mathematical equations associated with the graph of the elliptical curve. Within the framework of the ECC asymmetric cryptographic setup, an elliptic curve, E, is used. This curve includes points with coordinates (x, y) characterized by Pf ∈ ∗ Pf (x, y). The coordinates of the points on the graph can be determined using the following equation.
Equation (a) Y2 = x3 + ax + b
Two values, a and b, can be opted for from the fp field as long as they meet condition 4a3 + 27b2 ≠ 0. The Elliptic Curve Encryption (ECC) system can be described based on two basic operations: dot addition and scalar multiplication. These two operations are the main functions in this encryption system. The process of scalar multiplication can be described as the calculation result of multiplying a point called P on a curve with a scalar value, K (The scalar multiplication of an elliptic curve is an operation that adds a point, P, on the curve k times.). To illustrate the correct understanding of this concept, consider the following process that represents a scalar multiplication of a point, P, by a scalar number, K (with K times P).
Equation (b) KP = P + P + P + P … + P
2.1.2. Conceptual Aspects of the Elliptic Curve Discrete Logarithm Problem (ECDLP)
The public key cryptography mechanism takes advantage of the features of mathematical problems based on the intractability to increase the strength of the cryptographic system. In protocols whose structure is based on the elliptic curve, the assumption that it is impractical to solve the discrete logarithm of a random element of the elliptic curve is known as the Elliptic Curve Discrete Logarithm Problem (ECDLP). According to the described conditions, the elliptic curve encryption system ensures that network attackers cannot calculate the result of the multiplication using the equation’s coefficients, thereby guaranteeing the security features.
An essential pragmatic issue in the ECC asymmetric encryption system is the computational problem of the discrete logarithm problem of an elliptic curve, which is ECDLP. This problem constitutes the main block of the elliptic curve mechanism, which operates based on coupling. Now, to explain the problem, consider two completely distinct points named P and Q, which are located at the top of the elliptic curve. Point Q results from the computation of scalar multiplication on point P using a specified scalar coefficient, indicated as “k”. A noteworthy aspect of the discrete logarithm lies in the difficulty associated with reversing the computation of the resultant value, rendering it practically infeasible. Thus, even with access to points P and Q, ascertaining or deducing the value of K becomes exceedingly difficult. This difficulty in computation and the consequent impossibility of obtaining the value of K in the ECC asymmetric encryption system is recognized as ECDLP, or the Elliptic Curve Discrete Logarithm Problem [14,15].
2.1.3. Theoretical Perspectives on Diffie–Hellman and Elliptic Curve Diffie–Hellman (ECDH)
Elliptic-curve Diffie–Hellman (ECDH), is a mechanism in the public key system that allows communication parties to agree on a key to encrypt confidential information. Communication parties need a pair of elliptic curve public–private keys to generate keys, which gives the ability to generate keys directly or to generate a set of keys for each connection.
As part of ECC theory, another theoretical model for key agreement has been proposed within its range of suggested sub-theories, highlighting the characteristic of anonymity. This subcategory is commonly referred to as the Elliptic Curve Diffie–Hellman Key Exchange (ECDH). The process of generating public and private keys based on the elliptic curve by the communication parties can be considered as one of the essential aspects of this mechanism, which gives assurance to the communication parties that the joint session key generated for their communication remains completely confidential. Following the description, envision an elliptic curve where two specific points, p. ai and p. bi, are situated. The ECDH asserts that even with access to the specified points, it becomes impossible for the adversary in the network to calculate or attain the points bi (ai. p) and ai (bi. p).
2.2. IoT Security and Privacy Challenges
Within the broader scope of cybersecurity, IoT security is a specialized area with a focus on safeguarding, overseeing, and mitigating threats associated with the Internet of Things. IoT is characterized as a network encompassing a diverse set of interconnected devices, allowing for the collection, storage, and exchange of data over the Internet. The IoT has brought numerous advantages for users, including increased convenience, efficiency, and connectivity. However, there are some challenges associated with it. Considering that many components of the IoT have serious weaknesses in security due to limitations such as power and low energy, many security challenges in this field have been discussed by security researchers. Thanks to the Internet of Things, an extensive amount of devices (billions of devices) have successfully accessed the Internet and generated numerous data points where the primary demand is security. With so many Internet-connected devices, the potential for cyber-attacks rises, making it crucial for users to take steps to protect their privacy and security when using IoT devices. Because of the growing frequency of network attacks, cybersecurity and privacy component threats have become major concerns for security researchers and professionals. These threats pose significant challenges for both commercial and public organizations. Common cybersecurity attacks have exposed the inherent weaknesses of IoT technologies, highlighting the need for stronger security measures to protect against these threats. One of the main reasons for the vulnerabilities in IoT devices is that their networks and users have access to the anonymous and untrustworthy Internet and can establish their communications on this open and insecure platform. This can make it easier for cybercriminals to exploit vulnerabilities in these devices and access sensitive data without proper permission. It is very important for all users of a network to be aware of these types of network risks and to take the necessary security measures to protect privacy when using the advantages of the network or network devices. The new infrastructure and communication platform of the Internet of Things requires new and effective security solutions to increase the security of its entities [16,17,18,19,20,21,22,23,24,25]. Unfortunately, typical network users do not pay enough attention to the impact of security on preserving their information and privacy. They often do not understand its importance until a security breach occurs. This lack of attention can lead to major damages, such as the loss of critical data on the network. Due to the multitude of available methods for network penetration and the existence of security vulnerabilities, consumers are increasingly inclined towards weak security measures. Considering the inherent vulnerability of the IoT to various security threats, there is an authentic risk related to the exposure of information or economic detriment if necessary security precautions are not diligently implemented [17,18]. Many attacks have compromised the safety measures for IoT components and made them vulnerable [19,20]. Physical attacks and eavesdropping due to the use of wireless communication media are among the vulnerabilities of this network. Additionally, the components of the IoT have restricted computational capacity, which necessitates the need for security algorithms with low computational costs.
On the other hand, authentication within the IoT is of paramount importance. This sub-network is exposed to various vulnerabilities and stands as one of the most critical aspects of ensuring security in numerous applications. The presence of a robust authentication mechanism can safeguard the network against hazards, including Denial of Service (DoS) attacks and replay attacks. Additionally, information security constitutes a notable vulnerability within IoT authentication due to the existence of programs designed for data collection within the IoT environment [21,22,23,24,25,26,27]. For example, contactless credit cards allows hackers to access the cardholder’s bank account number, identity, and purchase.
Paper Organization
We have presented this research paper intending to investigate and research the security challenges of the Internet of Things nodes, securing communication between communicating nodes, generating and exchanging session keys in secure conditions, and implementing an efficient authentication mechanism. Section 3 delves into previous works in the field. In Section 4, a protocol for securing IoT is put forward. In Section 5, the analysis stemming from the security simulation of the suggested protocol is showcased, utilizing the AVISPA network protocol evaluation platform, including an assessment of the protocol’s ability to withstand common network attacks. Section 6 of the article examines how the proposed protocol performs in terms of computational cost, and a comparison is made with other security protocols specific to IoT. Finally, the paper concludes in Section 7.
3. Related Work
The Internet of Things (IoT) is defined by a harmonious integration of various nodes, and security is a significant concern within this network. To mitigate the vulnerability of this network, smart nodes must authenticate each other and establish mutual trust to communicate. Also, the security and confidentiality of information are of paramount importance. To safeguard information from the malicious actions of network attackers, Yuanbing et al. [28] introduced a protocol designed to enhance authentication performance in smart healthcare systems. While the proposed protocol leverages elliptic curve encryption techniques, it does have vulnerabilities that expose it to the Man-In-The-Middle (MITM), impersonation, and stolen smart card attacks. Rostampour et al. [29] proposed a secure ECC-based authentication protocol (ECCBAP) to improve the connection reliability between edge devices and the cloud server. However, the solution fails to consider defenses against replay attacks, enabling attackers to drain system resources by continuously resending captured messages via public channels to the server. Yu et al. [30] introduced a scheme concentrating on communication security and user privacy protection in smart home environments, offering an authentication method that is both secure and lightweight, utilizing three factors. However, the suggested method cannot attain the security-related aspects of untraceability and perfect forward secrecy, while also being vulnerable to attempts of guessing passwords and impersonation attacks. Xuyang et al. [31] introduced a network protocol based on elliptic curve techniques and encryption to secure devices with low processing power, aiming to enhance computing and communication capabilities constructed considering attributes like energy, power, and data transfer rate. While the security measures of the recommended protocol are substantiated by the random oracle model method, it falls behind in achieving the security characteristic of perfect forward secrecy and is open to impersonation attacks. As Internet of Things (IoT) technology becomes integrated into the industrial framework, security threats have evolved. Yanru et al. [32] introduced a key-agreement and authentication protocol utilizing the hashing process, executing XOR operations, and ECC encryption method for encrypting exchanged data. However, the proposed protocol cannot adequately address security concerns and is subject to issues such as untraceability, password guessing attacks, stolen user mobiles, man-in-the-middle, ESL, and de-synchronization. Chien-Ming et al. [33] introduced an improved protocol for securing IoT environments. However, contrary to their claim of safety, the presented protocol raises security concerns, including issues with clock synchronization, anonymity, and unlinkability. The integration of the IoT framework with medical equipment played a crucial role in enhancing patients’ health. However, security vulnerabilities in this field can lead to significant problems. In their work [34], Masud et al. presented a lightweight security protocol utilizing hash operations to authenticate users while also providing an anonymity feature. Despite these intentions, the presented plan exhibits several security weaknesses, making it susceptible to various attacks, including privileged-insider, off-line password guessing, impersonation, smart-card (device) loss, stolen-verifier, update asynchronous, identity anonymity, session-key secrecy, known session key, perfect forward secrecy, and unlinkability. Cloud computing presents a significant challenge for the Internet of Things, necessitating support against potential security threats. Ali, Hala, and Sridevi [35] introduced a credential-based authentication mechanism based on security requirements such as access control, privacy, integrity, and confidentiality. However, the suggested method has weak points that make it vulnerable to two kinds of attacks: offline password guessing and Ephemeral Secret Leakage (ESL). Basudeb et al. [36] offer a new safe protocol for authentication and key- management procedures named AKMS-AgriIoT for embedded IoT, which is based on blockchain. However, the proposed method faces challenges in maintaining the protocol’s security against password guessing, spoofing, session hijacking, and de-synchronization attacks. Keunok et al. [37] offered a lightweight schema based on hash functions and XOR operations for user authentication to enhance security and address the weaknesses of the Internet of Medical Things (IoMT) structure. However, the protocol faces challenges in implementing two notable security features: unlinkability and perfect forward secrecy. Additionally, it is open to risks such as impersonation attacks, sensor node captured attacks, session-key secrecy, and known session-key attacks. Shamim and Riham AlTawy [38] identified security weaknesses in the protocol put forward by Masud et al. [34] and introduced a new protocol to address these vulnerabilities. The proposed protocol is a lightweight mutual authentication scheme utilizing a cryptographic hash chain in a one-way process. However, it is unsecured against cloning and physical desynchronization attacks, posing a risk to the overall security of the protocol. Krishnasrija et al. [39] suggested lightweight multiple authentication protocols based on Chebyshev polynomials to address authentication issues in IoT networks. While suitable for deployment on devices with limited processing capacity, this protocol has not achieved the features of anonymity and perfect forward secrecy. Additionally, it is prone to encountering known session-specific, temporary information and replay attacks. Nikooghadam and Amintoosi [40] conducted research into the study of embedded IoT devices, addressing security weaknesses identified in previous designs. They proposed an authentication protocol designed to be lightweight, aiming to mitigate these weaknesses, with a focus on critical security demands, including mutual authentication, maintaining the anonymity of devices, and complete confidentiality. However, their proposed plan opens the door to potential security challenges, including tracing lost smart cards, stolen verifier, insider, and brute-force attacks. Additionally, it has not been able to fully meet the specified security requirements. The three-factor authentication model was introduced in the research by Servati and Safkhani [41] to secure communication in IoT smart medical systems. Despite their claims in the article that the presented protocol has the ability to address offline password guessing, impersonation, ephemeral secret leakage, and privileged insider attacks, these attacks have been observed to exploit weaknesses in its security and it has not fully met the security requirements.
4. Proposed Protocol Procedure
Several investigations have been carried out regarding the security challenges and requirements for the IoT structure, which shows that the use of devices with limited resources has caused several security challenges regarding the discussion of the security of all parts of the Internet of Things network and its routing protocols. As outlined earlier in this document, IoT possesses inherent vulnerabilities that create favorable conditions for various types of network attacks. The absence of a reliable authentication procedure and the exclusive reliance on shared-key encryption throughout the network significantly contribute to the vulnerability of the Internet of Things. The following section presents a strong authentication protocol with an incorporated key-exchange process, designed to enhance the security of communication in the IoT. Our proposed method incorporates ECC approaches and concepts specifically designed to address the constraints on resources experienced by IoT devices with lower performance capabilities. The method we put forward is divided into two phases:
The opening phase in the designed method is the initial registration phase of each node that intends to enter the network. It is mandatory to perform this step at least once for each node so that it is recognized in the network as an authorized node and it can use network services. Security processes and policies of communication parties are implemented in this phase. Also, the two communication parties produce a completely different encryption key in each communication session and evaluate each other’s identity in the protocol process using private parameters. In Table 1, an explanation of the parameters utilized in our presented protocol is provided.

Table 1.
The parameters utilized in the presented protocol.
4.1. Registration Phase
In the overarching steps of the provided protocol, the initial stage considered for the node is to successfully complete the registration phase. This phase must be completed at least one time by the node that intends to enter the network. In cases where a node has experienced prolonged disconnection to the network for a considerable time, it is required to repeat the registration phase steps and undergo authentication. During the initial step, the node picks a random number, referred to as ri. The purpose of using random numbers is to ensure that the parameters generated in each step are unique and distinct. Following that, the subsequent node operation results in the calculation of the Ri value, which is derived from the fusion of random numbers and the node’s private key. This value is an anonymous technique for utilizing the node’s private key within the protocol process. The motivation behind the generation of this parameter is to utilize the node’s private parameters indirectly in generating the “authentication certificate” parameter, allowing authentication to be implemented using the private parameters of both entities within the protocol process. It also contributes to the resilience of the showcased protocol against identity forgery attacks. By indirectly using the private keys, the protocol leverages their properties in generating secure parameters while maintaining the confidentiality of the private parameters.
- (1)
- Ri = H((PVNODE * ri) || ri ||PUNODE)
In the final step of the process, the node securely transmits the value Ri and IDNODE to the server, along with its public key. Next, the server selects random numbers, fi, and uses the technique of generating anonymous values for the indirect utilization of its private key, as described earlier. Subsequently, the server generates the value “Li” by combining these random numbers with its private key. Then, the server generates the required certificate of the node by generating the value of “Li” in the next operation. The “ACi” certificate is calculated using “Li” and “Ri” values.
- (1)
- Li = H((PVSERVER * fi) || fi || PUSERVER)
- (2)
- ACi = H(Ri || Li)
Finally, the server sends the ACi parameter to the node using a secure channel. In Figure 2, the registration process is outlined alongside the values utilized in this process.
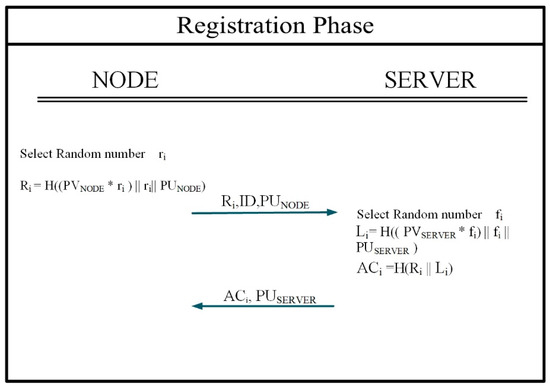
Figure 2.
Registration phase.
Summary of the register phase process:
- Node:
- Start
- Select random number ri
- Compute Ri = H((PVNODE * ri) || ri ||PUNODE)
- Send Message including Ri, IDNode, PUNode to the server
- End
- Server:
- Start
- Select a Random Number fi
- Compute Li = H((PVSERVER * fi) || fi || PUSERVER)
- Compute ACi = H(Ri || Li)
- Send Message including ACi and PUServer to the Node
- End
4.2. Authentication and Key-Exchange Phase
The authentication and key-exchange phase comprises three steps, wherein the communicating parties authenticate each other using various parameters within the proposed protocol. During this phase, specifically in the three-stage process of authentication and key agreement, a mechanism is employed. In this mechanism, the node and the server use a dynamic symmetric encryption key to secure the exchanged data. Additionally, throughout this phase, mutual authentication takes place with distinct parameters. Finally, in the last step, the communicating parties generate a secure session key based on private and verified parameters. The node acts as the starting point for communication with the server.
Step 1.
To initiate the protocol process, the node starts by selecting random numbers, ai and bi. In the protocol process, private parameters are used to generate different values. The reason for using private parameters is to make it impossible to calculate the values generated by network attackers and to maintain the security of the protocol. There are various attacks, such as reply, impersonation, and other network attacks, that can be prevented by using the features of private parameters. The utilization of private parameters requires security issues to be considered in the protocol process. In the process of the presented protocol, we have taken advantage of the features of the server and node’s private key, which we have prevented from being used directly to maintain the security of this sensitive private parameter. To protect the private keys of each entity in the provided protocol process, we have combined the keys with random numbers and used a root generated from the private keys. This operation prevents private keys from being used directly. Implementing the private key combination mechanism with random numbers in the protocol process enables us to furnish the security features mentioned for the presented protocol. Subsequently, the values S1, K, and Ni are produced.
- (1)
- S1 = (PVNODE * ai) + bi
- (2)
- K = bi.P
- (3)
- Ni = bi.PUSERVER
The generation of S1, K, and Ni involves scalar multiplication of the base point (P) and the server public key with the random number bi. With a two-fold purpose, these parameters handle dynamic symmetric key selection and authenticate the node to the server. The security of the dynamic symmetric session-key generation mechanism is implemented by taking advantage of the features of the ECDH. Upon generating the Ni value, the node picks the x-dimensional value of the Ni point as the symmetric encryption key. According to the process of calculating the value of Ni, it is completely understandable that the existence of random numbers (bi) in this process means that every time this parameter is produced, the value produced is completely different from before. The distinctiveness and uniqueness of the symmetric key eliminates the potential vulnerabilities that arise from using static keys in the realm of symmetric cryptography. Upon the selection of the symmetric encryption key, the node creates parameters A, S2, and S3. During this phase of the protocol procedure, the aim of generating these parameters is to enforce the authentication of both the node and the server. The server evaluates the node’s identity by re-calculating the parameters.
- (1)
- A = H(S1||Ni||ACi)
- (2)
- S2 = H(S1||Ni(x)||K||A)
- (3)
- S3 = H(A||S2||ACi)
In the authentication mechanism, the value A serves as a primary parameter and is determined through calculations involving the private parameters Ni and ACi, along with S1.
Through the utilization of ECDH protocol features, the protocol’s mechanism defines circumstances in which the node is not required to include the value of n in its message to the server. Furthermore, the secure calculation of this value on the server side is guaranteed according to the ECDH protocol. During the mutual authentication process conducted by both the node and the server, this mechanism serves as an effective factor in implementing security policies for the security of the protocol process. Furthermore, besides computing the value of Ni, the server needs to recalculate the values of S2 and S3 with the correct data available to obtain the parameters A, Ni(X), and S1. The parameters S2 and S3 are directly linked to the validation and confirmation of the node’s identity authorization, and the correctness of recalculating these parameters proves the validation of the node’s authorization. The noteworthy point is that only parameters S1 and S3 are encrypted by the node using the dynamically generated symmetric key (Ni(x)).
Finally, the node sends parameters S1, S3, PUNODE, and K (The K parameter is not included in the encrypted message) to the server in an encrypted form. The public key of the node is used to identify the identity of the message sender.
4.2.1. Step 2
In this step, The node’s encrypted message is received by the server, which includes parameters S1, S3, and K. After receiving the message, the server must first calculate the ΔT (|T2 − T1|) time gap upon message arrival to assess message freshness and to avoid sending duplicate messages and to prevent replay attacks (T1 refers to the time of sending the message and T2 refers to the time of receiving the message). Upon satisfaction with the message’s freshness, the server needs the symmetric key to decrypt the message. To obtain this key, the server calculates the Ni parameter by multiplying the scalar of its private key with the received value K. Two significant considerations arise in this context. First, in line with the ECDH protocol, the attacker’s capacity to calculate Ni, even with K, is restricted. Second, as dictated by the ECDLP problem, the value of Ni is only accessible through the scalar multiplication of the Server’s private key with K. Using the advantages of this theory helps the protocol to implement a better-quality authentication mechanism, and the presented protocol can provide significant efficiency against all kinds of network attacks.
- (1)
- Ni′ = PVSERVER.K
Note: The server needs to have the value of K to generate the value of Ni and reach the X dimension of Ni. The value of K is sent by the node, based on the ECDH described in the introduction section; network attackers cannot calculate the value of Ni by having the value of K.
After obtaining the encryption key through the accurate calculation of Ni′, the process of authentication and validation of parameter accuracy initiates. In pursuit of this goal, the server computes the parameters A′, S2′, and S3′ using the provided information.
- (2)
- A′= H(S1||Ni′||ACi)
- (3)
- S′2 = H(S1||Ni′ (x)||K||A′)
- (4)
- S′3 = H (A′|| S′2|| ACi)
The server, in order to produce the S3′ value, is required to initially compute A′ and S2′. For the calculation of A′, the server utilizes the encrypted form of the parameter S1 sent by the node, the previously generated ACi parameter for the node, and the Ni′ parameter obtained in the server’s prior calculations. As can be seen, if entities other than the server that owns the private key attempt to generate Ni, they will not be able to reach the symmetric encryption key because the Ni can be recalculated only with the server private key based on ECDLP. Also, parameter S1 is not accessible because it is encrypted by the dimension (x) of parameter Ni. In addition, in the process of calculating A′, the server-generated certificate (ACi) is needed for the node, which is a private parameter between the server and the node. Therefore, the hostile or unauthorized person needs access to the private parameters used in the production of A, which prevents the creation of calculation conditions and the access of the hostiles to the value of A′. Upon computing the parameters A′ and S′2, the server generates the parameter S′3 to verify both the accuracy of the transmitted information and the authenticity of the message sender. The server verifies the accuracy of the value information by comparing the value of S′3 with its ownvalue, simultaneously ensuring the authenticity of the sender (node). Identical values for these two parameters provide assurance to the server regarding the accuracy of the received information and the authorized identity of the node transmitting the data. Once the server has verified the identity and accuracy of the information, it proceeds to generate an anonymous value of its private key, referred to as SA. This value is obtained through the combination of the server’s private key and random numbers ci and di. Generating the SA value allows the server to finalize the information for session-key generation. Subsequently, after creating the session key, the S4 parameter is generated by it. In this process, the value of S4 provides conditions so that the node can check the authenticity of the server’s identity with the help of this parameter. The generation process for the SA, SK, and S4 parameters is as follows.
- (5)
- SA = (PVSERVER*ci) + di
- (6)
- SK= H(S1||A′||S′2||S′3||SA||ACi)
- (7)
- S4 = H(SK||SA||Ni(y))
Following that, utilizing the previously created values and its private key, the server generates the session key, which uses the y dimension of the N point obtained based on the principles of ECDH to reinforce the authentication mechanism and session-key security. Ultimately, the SA and S4 parameters are encrypted by the server with the acquired dynamic symmetric encryption key and then sent to the node.
4.2.2. Step 3
The third and final step concludes the key-agreement and authentication phase within the proposed protocol; the node verifies the server’s authenticity with the assistance of the private parameters. Following the verification of both the accuracy of server-side information and the server’s identity, the node proceeds to select the generated session key as the encryption key for securing data transmission. In the beginning stages, the node evaluates the freshness of the received message and moves forward with the protocol if the message is confirmed as fresh. Following this step, the node proceeds to compute the session key by utilizing both the received parameter (SA) and the parameters generated earlier in step 1 (A, S2, S3, ACi). As described in the node and server private key parameters protocol process, the ACi certificate plays a vital role in generating the effective session-key parameters. Therefore, the private parameters in session-key generation have significant effects on the implementation of security policies. In the next step, the node must ensure the identity of the server and the correctness of the received data. To accomplish this, the node recalculates the session key and S4 parameter, leveraging the parameters obtained in the previous steps, along with those sent by the server to the node. Then, the node compares the recalculated SK′ and S4′ with the SK and S4 sent by the server. The parameters are evaluated according to the following procedure.
- (1)
- SK′= H(S1||A||S2||S3||SA||ACi)
- (2)
- S′4 = H (SK′ ||SA||N(y))
If the values computed by the node match those received from the server, it indicates that the sender is the server and the received data is accurate. Subsequently, the session key produced is designated as the encryption key for maintaining secure communication. If any of the parameters used in the creation of the session key change under any circumstances, it will cause the value of the session key recalculated by the node to be different from the value received from the server. The changes directly affect the calculation result of the S4 parameter, and this parameter is used to authenticate the server and also check the accuracy of the information received from the server. Therefore, if the correctness of the values received by the node is not verified, the node will disconnect and prevent the continuation of the protocol process. Authentication of communication parties is one of the basic parameters in the presented protocol. We have used Ni, A, S2, S3, SK, and S4 parameters in the presented protocol process to implement the multiple authentication mechanism. Server and node entities at each step of the protocol recalculate certain parameters using the values they have, which helps them to evaluate the identity of the information sender. The process of authentication and key-agreement in the proposed protocol is illustrated in Figure 3.
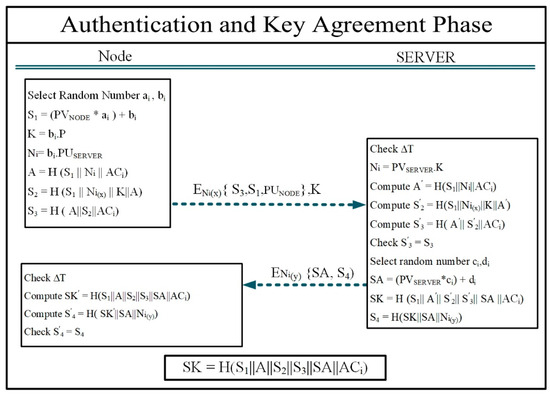
Figure 3.
Process of authentication and key-agreement phase.
Summary of the Authentication and Key-Exchange Phase:
- (1) Node:
- Start
- Select random number ai and bi
- Compute S1 = (PVNODE * ai) + bi
- Compute K = bi.P
- Compute Ni = bi.PUSERVER
- Compute A =H(S1||Ni||ACi)
- Compute S2 = H(S1||Ni(x)||K||A)
- S3 = H(A||S2|| ACi)
- Send Message include S3, S1 Encrypted and K to server
- End
- (2) Server:
- Start
- Check ΔT
- If Message is Fresh Continue the process
- Else
- Disconnect the communication
- Compute A′= H(S1||N′|| ACi)
- Compute S′2 = H(S1||N′ (x)||K||A′)
- Compute S′3 = H (A′|| S′2|| ACi)
- if S3′ = S3 Continue the process
- else
- Disconnect the communication
- Select Random Number ci and di
- Compute SA = (PVSERVER*ci) + di
- Compute SK= H(S1||A′||S′2||S′3||SA|| ACi)
- Compute S4 = H(SK||SA||N(y))
- Send Encrypted Message include SA and S4 to the Node
- End
- (3) Node:
- Check ΔT
- If Message is Fresh Continue the process
- Else
- Disconnect the communication
- Compute SK′= H(S1||A||S2||S3||SA|| ACi)
- Compute S′4 = H(SK′ ||SA||N(y))
- if S4′ = S4 Continue the process
- else
- Disconnect the communication
- Select SK′ as Session key
- End
5. Evaluation of the Security Aspects of the Designed Protocol
This section aims to confirm the security of our proposed method through an assessment of our proposed protocol’s security, employing both formal and informal techniques. Through the utilization of the official AVISPA tool, we evaluated the security characteristics of the private variables belonging to the parties involved in communication within the protocol process and additionally proved the strength of the protocol’s security robustness against active and passive attacks. Furthermore, in the informal analysis section, we outline various typical network attack types and assert the resilience of the designed protocol against such threats.
5.1. Informal Security Evaluation of the Suggested Protocol
5.1.1. Reply Attack
Among the frequently occurring threats in network platforms, the reply attack stands out. Within this context, the attacker in the network seeks to intercept and capture the packets being exchanged. These intercepted packets are then retransmitted through the network over different time periods. The process of retransmission and the transmission delays can be started by either the sender or the network nodes. Therefore, it is crucial to have robust security measures to prevent such attacks. In the proposed protocol, two key factors have been incorporated to thwart such attacks: message freshness verification and the utilization of the numbers that are chosen randomly. As outlined in the protocol process description, parties of communication initially verify that the received message is fresh. the evaluation is done based on network rules that define the permissible time period for network messages (∆T = | T2 − T1|). The freshness of the message is the permission to continue the process of the protocol, otherwise the entities will terminate the established connection. Additionally, the parameters generated in each communication session are combined with random numbers, which makes the values generated in each session unique. This uniqueness of the parameters helps the protocol to be safe against attacks such as repeating messages and DOS and maintains the security of the parameters. Consequently, upon receipt of repeated messages or those outside the specified time frame, network entities will terminate the communication and prevent a potential adversary from launching an attack.
5.1.2. Impersonation Attack
Whenever the adversaries within the network desire to establish themselves as an authenticated node capable of utilizing network resources and interacting with other nodes, they deploy this attack to realize their objectives. To thwart this attack, we have utilized the authentication mechanism at various stages and incorporated the private parameters of communication entities to augment both security and the distinctiveness of the calculated values. As mentioned in the protocol description, Ni is the initial parameter employed by both the node and the server in performing the authentication process. The security of this parameter is guaranteed by its transmission via a secure channel and its computation using the private keys of both the node and the server, as per the Elliptic Curve Diffie–Hellman (ECDH) protocol. To enhance the security robustness of the protocol, we avoid dependency on the authentication of the node and server to a single parameter, instead incorporating parameters A, S2, S3, and S4 into the authentication process. Considering the principle of confidentiality of these parameters and utilization of them in the protocol process for the authentication mechanism and session-key generation, in order to maintain their security and also to meet security features such as non-dependence, ensuring unpredictability, random numbers are utilized to generate parameters A, S2, S3, and S4. This combination guarantees that the parameters generated by the node and the server in the process of authentication and session-key generation are completely unique for each communication session. For enhanced security of the generated parameters, alongside utilizing the features of random numbers, we have incorporated the private parameters of both the node and the server, which are exchanged through a secure channel. As outlined in the conditions, the security mechanism utilized for the parameters generated within the protocol process guarantees the security of both communication entities during the protocol execution and prevents the occurrence of an impersonation attack. For a better understanding, we will continue to evaluate the S3 parameter calculation. To produce this parameter, it is necessary to calculate and access the following parameters.
- Calculation of S1: To compute this parameter, the node employs a technique where its private key is combined with random elements. This strategy mitigates the risk associated with exposing the private key directly and ensures that the resultant value is unique for every session.
- The Ni parameter: This parameter is also generated using random numbers in order for it to be unique in each communication session.
- The ACi parameter: Created during the registration of the node, this parameter is maintained as private by both the node and the server.
- Parameter A: This parameter is calculated using confidential values of S1, Ni, and ACi.
- S2: This is the combination of S1, the X dimension of Ni, K, and A parameters.
Also, in order to obtain the encryption key, it needs the server’s private key or the disclosure of private numbers. Given that a multitude of necessary private parameters are required and the protection of these parameters is maintained in the protocol process, it is impossible for a hostile person to access S3.
5.2. Perfect Forward Secrecy
The security feature of Perfect Forward Secrecy (PFS) is indeed crucial in authentication and key-agreement protocols, and it should be an integral component of any protocol aiming to safeguard the generating session keys and confidential parameters during the protocol process. PFS offers the significant advantage of generating distinct session keys for each session without any correlation between the keys of different sessions.
As elucidated in the description of the presented protocol, random number generation has been employed to compute the S1, S2, S3, SA, A, and Ni parameters, which play a pivotal role in session-key generation. The utilization of random numbers in this process ensures that the session keys calculated in each session are not only unique but also entirely unrelated to those generated in previous sessions. Consequently, even if an attacker manages to acquire keys from prior sessions under specific conditions, they would be unable to calculate the current session’s key or establish any connection between session keys.
The use of random numbers helps the protocol session-key generation process so that the keys calculated in the session are unique and completely different from previous sessions. Therefore, if the attacker is able to obtain the keys that are generated during prior sessions, it is beyond his/her capacity to perform the calculation of the previous keys and formulate the connection among the session keys.
5.3. Man-in-the-Middle Attack
In contemporary computer networks, the Man-in-the-Middle (MitM) attack is among the most perilous threats, commonly referred to as MITM, MitM, MIM, or MITMA in different publications. It is unfortunate that this kind of attack is often overlooked by users, potentially resulting in unauthorized access to a user’s information. The primary objective of a MitM attacker is to intercept and manipulate the data flow between the network nodes during their communication. Moreover, the attacker has the potential to access network traffic, creating a substantial threat to the confidentiality and integrity of the data in transit. To counter this attack, encrypting information is one of the most effective solutions as it assists in safeguarding the secrecy of data during its transmission over the network. Within our suggested protocol, we use a dynamic symmetric key to secure the messages being exchanged. Additionally, multi-factor authentication mechanisms have been incorporated into our protocol procedure to ensure identity verification. Even if the attacker succeeds in obtaining the parameter K, according to ECDLP theory, they still need the server’s private key, which is a significant obstacle for the attacker. Moreover, other security policies are taken into consideration:
- (1)
- Message Freshness: Communication parties verify the freshness of messages, and the protocol utilizes random numbers combined with private parameters. This dynamic aspect ensures that intercepted messages become obsolete and cannot be reused.
- (2)
- Unique ACi Parameter: The ACi parameter used in the protocol is unique for each network entity. Consequently, when recalculating the verification parameters S2, S3, and A on the server side, it will not match the data manipulated by the adversary, leading to a disconnection.
- (3)
- Session Key: To derive the session key, the adversary would need access to the S1, S2, S3, SA, ACi, A, and Ni parameters. These values are neither transmitted over the channel nor easily accessible. As previously described in the impersonation attack section, it is practically impossible for an adversary to acquire these critical values.
5.4. Session-Key Computation Attack
The objective of network attackers in this scenario is to find a way to compute the session key that the two communicating parties generate during the process. The session key in our proposed approach is generated using the following parameters and formula.
- (1)
- SK= H(S1||A||S2||S3||SA||ACi)
As can be seen, different factors such as random numbers, a root value of the private key of the communication parties, ECDH, and ECDPL theory are considered in the process of calculating the communication session key. As stated by the ECDLP, even with the values of K, the attacker cannot obtain the Ni. Indeed, the utilization of private parameters S1, A, S2, S3, SA, and ACi in the session-key generation process provides an additional layer of security in the protocol. It is crucial to emphasize that neither of these parameters is exposed or exchanged over the communication channel during the protocol’s execution, bolstering the protocol’s security against potential attacks. The security of the parameters is detailed in the preceding attacks and the protocol text.
5.5. Selective Forwarding Attack
This attack, which involves selectively capturing and resending packets in the RPL routing protocol, is a common threat. This type of attack can disrupt network communication and potentially compromise its integrity. To mitigate such attacks, a robust authentication mechanism is essential to thwart the intrusion of malicious nodes into the network. As stated previously, the recommended protocol incorporates an optimal authentication system into its process, leveraging parameters such as S1, A, S2, S3, SA, Ni, and ACi. However, there may be unique circumstances where the hostile person in the network chance to transmit messages through the network with the intention of executing a selective transmission attack. The presented protocol has several security measures in place to counteract this threat:
- (1)
- Message Freshness: At each step of the protocol, there is a rigorous check for the freshness of messages. Verifying the currency of messages ensures that either the node or the server can detect messages from earlier, duplicated, or expired sessions, leading to the disconnection of the message recipient.
- (2)
- Random Numbers Utilization: In the context of implementing the security features of our protocols, the utilization of random numbers is considered as the basic component in the protocol process. Random numbers ensure the absolute uniqueness of generated values, making it challenging for network attackers to execute selective transmission attacks. Consequently, the presented protocol has improved its flexibility against selective forward attacks by taking advantage of random number features as well as the security feature of checking draft message freshness during the protocol process.
5.6. Secure against the DOS Attack
Among the prevalent and widely encountered network intrusions, Distributed Denial of Service (DDoS) attack stands out, which are utilized by the attacker for the purpose of repeatedly transmitting messages. The primary objective of this attack is to disrupt network operations, introduce deficiencies in optimal performance, and, most significantly, cause delays in network services. To safeguard the security and operational integrity of a network, it is imperative to establish security mechanisms designed to counteract DoS and DDoS attacks. To safeguard against this vulnerable attack, we implemented security measures during the execution of our protocol process.
Random Numbers: As mentioned earlier, the use of random numbers has different advantages, which can face serious challenges in the implementation of attacks against all types of network attacks. To prevent the reuse of expired messages and their repetition in other communication sessions, random numbers guarantee the condition of message uniqueness in each session, which challenges the condition of message reuse for adversarial purposes. The attribute of uniqueness enables communication parties to detect unauthorized communication requests by examining consistency in generated values.
Timeframe Verification (∆T): Utilizing a method to calculate the time differential of received messages serves as an additional security measure, aiding in the detection of unauthorized messages and communication requests. The receiving entity evaluates the value “∆T” to detect the allowed time interval of the message as well as the oldness of the message. Therefore, to maintain the security and performance of the network, if the received message is outside the allowed time frame, it will disconnect the connection.
5.7. Formal Analysis of the Presented Method and the Results of the Reviews
The following section provides a detailed examination of our proposed method through formal analysis. Our proposed method underwent comprehensive security validation employing the AVISPA tool. This efficient official tool has been used by security researchers in extensive research for security evaluations of security protocols as well as analysis of security protocols used on the Internet. An automated security analysis system is employed, complemented by specialized servers like On-the-Fly Modeler (OFMC) and Constraint-Logic (Cl-AtSe). Moreover, AVISPA can conduct assessments of protocols in the presence of various attack scenarios. Acknowledging the capabilities of this software, we utilized the AVISPA tool for examining the security of our designed protocol against diverse attack scenarios and to guarantee the confidentiality of private information [42]. The results of the security evaluations performed with the AVISPA tool are illustrated in Figure 4.
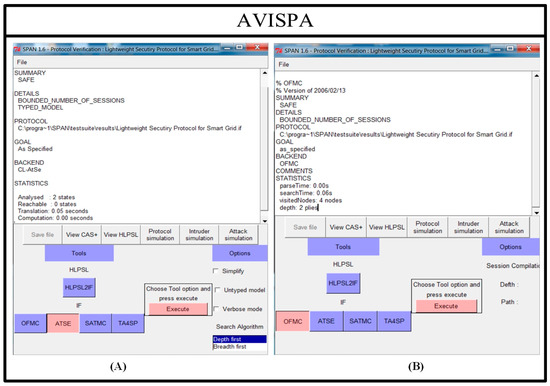
Figure 4.
AVISPA results. (A) ATSE (B) OFMC.
Stemming from the formal scrutiny and the findings presented in Figure 4, it is apparent that the offered method exhibits robustness against both categories of active and passive network attacks. The results derived from the OFMC and CL-ATSE outputs within the official AVISPA tool indicate that the confidentiality of private parameters that are exchanged among communication parties during the protocol’s execution is maintained. Also, network attackers or unauthorized nodes are incapable of calculating or accessing these parameters. Table 2 outlines a comparative assessment of the proposed design against similar protocols, emphasizing their respective security features and resilience to security threats. According to the information in Table 2, related protocols aimed at securing communications within the Internet of Things (IoT) network exhibit notable security vulnerabilities. Recognizing the security requirements within the IoT network and the observed attacks, we effectively addressed these vulnerabilities by introducing a comprehensive protocol.

Table 2.
Security Features Comparison.
6. Performance Evaluation of the Proposed Protocol
6.1. Computation Costs Comparison
As highlighted in the examination of security concerns associated with the Internet of Things (IoT), nodes operating in this network often have limited computational resources. Consequently, these components of the Internet of Things network require security arrangements and policies that can efficiently implement the security features, with low computational cost. This is crucial to ensure that the security measures do not hinder the performance or functionality of the IoT devices. It is a delicate balance between maintaining robust security and ensuring optimal device performance. In the subsequent analysis, we determined the time complexity of our protocol based on the operators involved in the authentication and key-exchange processes of the proposed method. A system is considered for implementation and determines the execution time of each operator utilized in the protocol. The system specifications encompass a 2.20 GHz Intel Pentium E2200 processor and 2 GB of RAM. As reported in [55,56], Table 3 showcases the time required for executing various cryptographic operations pertaining to each cryptographic element. In an effort to highlight the enhanced efficiency of our proposed protocol compared to similar protocols within the IoT network, we conducted a comparative analysis of computational costs. The results of this comparison are provided in Table 4.

Table 3.
Execution time of cryptographic elements.

Table 4.
Computation cost comparison of the related protocols.
Table 4 provides a comparative analysis of the computation time expenditure involved in the process of our presented method versus security protocols proposed by security researchers for securing Internet of Things communications. It can be inferred from the results displayed in the table that our proposed method offers a notably reduced execution time for the protocol process and attainment of the session key when compared to alternative methods. Considering the limited resources and low power constraints of IoT network nodes, it is essential to adopt security mechanisms that optimize energy usage during protocol operations and routing, especially when employing the RPL protocol. Consequently, our proposed protocol, characterized by its diminished computing time for the protocol process involving authentication operations and key agreement, can be effectively applied and integrated into different segments of an Internet of Things network.
6.2. Communication Costs Comparison
Within this segment of the evaluation paper, we have elucidated the communication cost linked to our proposed method and conducted comparisons with those of other pertinent protocols. To determine the communication cost, the following conditions are taken into consideration: the SHA-1 one-way hashing algorithm, the identity parameter comprises 160 bits, 160 bits are allocated for random numbers, the hash algorithm yields an output of 160 bits, and the time interval is represented by 32 bits. For an elliptic curve point characterized by P = (Px; Py), where Px and Py signify the coordinates of two points, x and y, respectively, the conjectures equate to (160 + 160) = 320 bits [43]. In the progression of the provided protocol, two communicating parties interchange two messages via the channel until they attain the session key, designated as (MSG1= ENi(x) {S1, S3, PUNode},K MSG2 = ENi(y) {SA, S4}). The communication cost associated with these messages is detailed as:
MSG1 = (480 + 160 + 320 + 320) (2) MSG2 = (160 + 160)
As evident from the comparative data showcased in Table 5, our proposed protocol demonstrates a notably lower communication cost in contrast to other protocols showcased within the Internet of Things network platform. In two cases [46,60], the number of bits in the transmitted messages is lower; however, the method presented in [46] is vulnerable to impersonation and man-in-the-middle attacks. The method presented in [60] requires 17.64 milliseconds of computation time, while our proposed method requires 6.70 milliseconds for the protocol process, making it more optimal.

Table 5.
Comparison of communication costs.
By reducing communication costs, overhead is alleviated and energy consumption is lowered, thus enhancing the compatibility of our designed protocol involving IoT nodes that have restricted computing resources.
6.3. Energy Consumption
In this part of the article, we have calculated the energy consumption for each of the presented protocols and compared them with the proposed protocol.
To complete the protocol process, communication entities use several operations, such as point multiplication, bilinear peering, octal functions, etc., for which communication devices must consume energy to perform. This energy consumption is measured in millijoules (mJ), which can be calculated through the relationship EC = TCT ∗ C [62,63]. In this regard, EC expresses energy consumption, TCT expresses total computational time, and C expresses maximum processing power (10.88 W) during wireless communications. Using Table 4, which provides the computing cost of each protocol and the maximum processing power (10.88 W), the energy consumption of each of the key-agreement protocols has been calculated. Table 6 compares the proposed protocol with other related protocols based on energy consumption criteria.

Table 6.
Energy consumption comparison of the related protocols.
As the results in Table 6 show, the proposed protocol has been able to provide more optimal energy consumption than other protocols. This low energy consumption provides the conditions that the presented protocol has suitable compatibility with nodes with low processing power and energy.
7. Conclusions
The Internet of Things (IoT) is a developing network with a global infrastructure that sustains numerous communication protocols and standards, reflecting its broad spectrum of services. Furthermore, its attributes and functionalities create avenues for a wide variety of services, ranging from healthcare to smart city solutions, home automation, and industrial applications. This assortment of services has made the network an attractive target for potential adversaries.
On the flip side, restrictions in resources and computational capabilities have brought about vulnerabilities in certain aspects of this network, especially in smart home devices, wireless sensor networks (WSNs), and the Routing Protocol for Low-Power and Lossy Networks (RPL). The objective of this article is to investigate the obstacles and vulnerabilities within the Internet of Things landscape, while also addressing its security vulnerabilities.
In conclusion, we recommend a framework to mitigate vulnerabilities in IoT systems, especially when faced with constraints on node resources. Both formal assessments and informal appraisals regarding the security of our recommended method indicate that our schema effectively safeguards against a multitude of network attacks while addressing vulnerabilities within IoT systems. In addition, due to the importance of energy consumption and the need for a mechanism compatible with energy consumption efficiency, our protocol boasts the shortest computational time when compared to other proposed solutions.
In the end, due to the extensive developments that are happening in infrastructure and communication technologies, every day we are facing new and serious challenges in the implementation of security. Among the developments that can be mentioned is the emergence of powerful quantum systems that have created very serious challenges in encryption algorithms. Our team is trying to improve security by providing effective research for improving security mechanisms in the field of quantum-resistant cryptography.
Author Contributions
All authors have participated in (a) conception and design, or analysis and interpretation of the data; (b) drafting the article or revising it critically for important intellectual content. All authors have read and agreed to the published version of the manuscript.
Funding
The research leading to these results has received funding from the Ministry of Higher Education, Research & Innovation (MoHERI) of the Sultanate of Oman under the Block Funding Program (Block Funding Agreement No.: MoHERI/BFP/GULF/2022, Project Code: BFP/RGP/ICT/22/474). We certify that all financial and material support for the conduct of this study and/or preparation of this manuscript is clearly described in the Compliance with Ethical Standards section of the manuscript.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Harb, H.; Idrees, A.K.; Jaber, A.; Makhoul, A.; Zahwe, O.; Taam, M.A. Wireless sensor networks: A big data source in internet of things. Int. J. Sens. Wirel. Commun. Control 2017, 7, 93–109. [Google Scholar] [CrossRef]
- Darabkh, K.; Aygün, R. TCP traffic control evaluation and reduction over wireless networks using parallel sequential decoding mechanism. EURASIP J. Wirel. Commun. Netw. 2007, 2007, 052492. [Google Scholar] [CrossRef][Green Version]
- Iova, O.; Picco, P.; Istomin, T.; Kiraly, C. Rpl: The routing standard for the internet of things... or is it? IEEE Commun. Mag. 2016, 54, 16–22. [Google Scholar] [CrossRef]
- Al-Zubi, R.; Hawa, M.; Al-Sukkar, G.; Darabkh, K.A. Markov-based distributed approach for mitigating self-coexistence problem in IEEE 802.22 WRANs. Comput. J. 2013, 57, 1765–1775. [Google Scholar] [CrossRef]
- Raoof, A.; Matrawy, A.; Lung, C.-H. Routing attacks and mitigation methods for RPL-based Internet of Things. IEEE Commun. Surv. Tutor. 2018, 21, 1582–1606. [Google Scholar] [CrossRef]
- Pavkovic, B.; Duda, A.; Hwang, W.J.; Theoleyre, F. Efficient topology construction for RPL over IEEE 802.15. 4 in wireless sensor networks. Ad Hoc Netw. 2014, 15, 25–38. [Google Scholar] [CrossRef]
- Ma, H.; Liu, L.; Zhou, A.; Zhao, D. On networking of internet of things: Explorations and challenges. IEEE Internet Things J. 2015, 3, 441–452. [Google Scholar] [CrossRef]
- Laghari, A.A.; Wu, K.; Laghari, R.A.; Ali, M.; Khan, A.A. Retraction Note: A Review and State of Art of Internet of Things (IoT). Arch. Computat. Methods Eng. 2023, 30, 5105. [Google Scholar] [CrossRef]
- Adarbah, H.Y.; Moghadam, M.F.; Maata, R.L.R.; Mohajerzadeh, A.; Al-Badi, A.H. Security Challenges of Selective Forwarding Attack and design a Secure ECDH-Based Authentication Protocol to Improve RPL Security. IEEE Access 2022, 11, 11268–11280. [Google Scholar] [CrossRef]
- Ouhmad, S.; El Makkaoui, K.; Beni-Hssane, A.; Hajami, A.; Ezzati, A. An electronic nose natural neural learning model in real work environment. IEEE Access 2019, 7, 134871–134880. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Satapathy, U.; Patnaik, S. Survey on IoT security: Challenges and solution using machine learning, artificial intelligence and blockchain technology. Internet Things 2020, 11, 100227. [Google Scholar] [CrossRef]
- Rose, K.; Eldridge, S.; Chapin, L. The internet of things: An overview. Internet Soc. (ISOC) 2015, 80, 1–50. [Google Scholar]
- Amirhossein, S. Improving the security of internet of things using encryption algorithms. Int. J. Comput. Inf. Eng. 2017, 11, 558–561. [Google Scholar]
- Moghadam, M.F.; Nikooghadam, M.; Al Jabban, M.A.B.; Alishahi, M.; Mortazavi, L.; Mohajerzadeh, A. An efficient authentication and key agreement scheme based on ECDH for wireless sensor network. IEEE Access 2020, 8, 73182–73192. [Google Scholar] [CrossRef]
- Silverman, J.H. The Arithmetic of Elliptic Curves; Springer Science & Business Media: Berlin, Germany, 2009. [Google Scholar]
- Hu, P.; Ning, H.; Qiu, T.; Song, H.; Wang, Y.; Yao, X. Security and privacy preservation scheme of face identification and resolution framework using fog computing in internet of things. IEEE Internet Things J. 2017, 4, 1143–1155. [Google Scholar] [CrossRef]
- Ban, H.J.; Choi, J.; Kang, N. Fine-grained support of security services for resource constrained internet of things. Int. J. Distrib. Sens. Netw. 2016, 12, 7824686. [Google Scholar] [CrossRef]
- Miloslavskaya, N.; Tolstoy, A. Internet of Things: Information security challenges and solutions. Clust. Comput. 2018, 22, 103–119. [Google Scholar] [CrossRef]
- HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Aledhari, M.; Karimipour, H. A survey on internet of things security: Requirements, challenges, and solutions. Internet Things 2021, 14, 100129. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and security: Challenges and solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Hermann, K.; Steiner, W. Internet of things. In Real-Time Systems: Design Principles for Distributed Embedded Applications; Springer International Publishing: Cham, Switzerland, 2022; pp. 325–341. [Google Scholar]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Hou, J.; Qu, L.; Shi, W. A survey on internet of things security from data perspectives. Comput. Netw. 2019, 148, 295–306. [Google Scholar] [CrossRef]
- Patel, C.; Doshi, N. Security challenges in IoT cyber world. In Security in Smart Cities: Models, Applications, and Challenges; Springer: Cham, Switzerland, 2019; pp. 171–191. [Google Scholar]
- Litoussi, M.; Kannouf, N.; El Makkaoui, K.; Ezzati, A.; Fartitchou, M. IoT security: Challenges and countermeasures. Procedia Comput. Sci. 2020, 177, 503–508. [Google Scholar] [CrossRef]
- Azrour, M.; Mabrouki, J.; Guezzaz, A.; Kanwal, A. Internet of things security: Challenges and key issues. Secur. Commun. Netw. 2021, 2021, 5533843. [Google Scholar] [CrossRef]
- Yuanbing, W.; Wanrong, L.; Bin, L. An improved authentication protocol for smart healthcare system using wireless medical sensor network. IEEE Access 2021, 9, 105101–105117. [Google Scholar] [CrossRef]
- Rostampour, S.; Safkhani, M.; Bendavid, Y.; Bagheri, N. ECCbAP: A secure ECC-based authentication protocol for IoT edge devices. Pervasive Mob. Comput. 2020, 67, 101194. [Google Scholar] [CrossRef]
- Yu, S.; Jho, N.; Park, Y. Lightweight three-factor-based privacy-preserving authentication scheme for iot-enabled smart homes. IEEE Access 2021, 9, 126186–126197. [Google Scholar] [CrossRef]
- Ding, X.; Wang, X.; Xie, Y.; Li, F. A lightweight anonymous authentication protocol for resource-constrained devices in internet of things. IEEE Internet Things J. 2021, 9, 1818–1829. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Arshad, H.; Nikooghadam, M.; Abbasinezhad-Mood, D. Three party secure data transmission in IoT networks through design of a lightweight authenticated key agreement scheme. Future Gener. Comput. Syst. 2019, 100, 882–892. [Google Scholar] [CrossRef]
- Chen, C.-M.; Li, X.; Liu, S.; Wu, M.-E.; Kumari, S. Enhanced authentication protocol for the Internet of Things environment. Secur. Commun. Netw. 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Masud, M.; Gaba, G.S.; Choudhary, K.; Hossain, M.S.; Alhamid, M.F.; Muhammad, G. Lightweight and anonymity-preserving user authentication scheme for IoT-based healthcare. IEEE Internet Things J. 2021, 9, 2649–2656. [Google Scholar] [CrossRef]
- Ali, H.S.; Sridevi, R. Credential-Based Authentication Mechanism for IoT Devices in Fog-Cloud Computing. In ICT Analysis and Applications; Springer: Singapore, 2022; pp. 307–318. [Google Scholar]
- Bera, B.; Vangala, A.; Das, A.K.; Lorenz, P.; Khan, M.K. Private blockchain-envisioned drones-assisted authentication scheme in IoT-enabled agricultural environment. Comput. Stand. Interfaces 2022, 80, 103567. [Google Scholar] [CrossRef]
- Kim, K.; Ryu, J.; Lee, Y.; Won, D. An Improved Lightweight User Authentication Scheme for the Internet of Medical Things. Sensors 2023, 23, 1122. [Google Scholar] [CrossRef] [PubMed]
- Shihab, S.; AlTawy, R. Lightweight Authentication Scheme for Healthcare with Robustness to Desynchronization Attacks. IEEE Internet Things J. 2023, 10, 18140–18153. [Google Scholar] [CrossRef]
- Krishnasrija, R.; Mandal, A.K.; Cortesi, A. A lightweight mutual and transitive authentication mechanism for IoT network. Ad Hoc Netw. 2023, 138, 103003. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H. Secure communication in CloudIoT through design of a lightweight authentication and session key agreement scheme. Int. J. Commun. Syst. 2023, 36, e4332. [Google Scholar] [CrossRef]
- Abdussami, M.; Amin, R.; Vollala, S. LASSI: A lightweight authenticated key agreement protocol for fog-enabled IoT deployment. Int. J. Inf. Secur. 2022, 21, 1373–1387. [Google Scholar] [CrossRef]
- Belfaik, Y.; Lotfi, Y.; Sadqi, Y.; Safi, S. A Comparative Study of Protocols’ Security Verification Tools: Avispa, Scyther, ProVerif, and Tamarin. In International Conference on Digital Technologies and Applications; Springer Nature: Cham, Switzerland, 2024. [Google Scholar]
- Kaur, D.; Kumar, D. Cryptanalysis and improvement of a two-factor user authentication scheme for smart home. J. Inf. Secur. Appl. 2021, 58, 102787. [Google Scholar] [CrossRef]
- Rangwani, D.; Sadhukhan, D.; Ray, S.; Khan, M.K.; Dasgupta, M. A robust provable-secure privacy-preserving authentication protocol for Industrial Internet of Things. Peer-Peer Netw. Appl. 2021, 14, 1548–1571. [Google Scholar] [CrossRef]
- Shamshad, S.; Ayub, M.F.; Mahmood, K.; Kumari, S.; Chaudhry, S.A.; Chen, C.-M. An enhanced scheme for mutual authentication for healthcare services. Digit. Commun. Netw. 2021, 8, 150–161. [Google Scholar] [CrossRef]
- Ryu, J.; Oh, J.; Kwon, D.; Son, S.; Lee, J.; Park, Y.; Park, Y. Secure ECC-based three-factor mutual authentication protocol for telecare medical information system. IEEE Access 2022, 10, 11511–11526. [Google Scholar] [CrossRef]
- Lin, G.; Wang, H.; Wan, J.; Zhang, L.; Huang, J. A blockchain-based fine-grained data sharing scheme for e-healthcare system. J. Syst. Archit. 2022, 132, 102731. [Google Scholar] [CrossRef]
- Razdan, S.; Sharma, S. Internet of medical things (IoMT): Overview, emerging technologies, and case studies. IETE Tech. Rev. 2022, 39, 775–788. [Google Scholar] [CrossRef]
- Chatterjee, U.; Ray, S.; Khan, M.K.; Dasgupta, M.; Chen, C.-M. An ECC-based lightweight remote user authentication and key management scheme for IoT communication in context of fog computing. Computing 2022, 104, 1359–1395. [Google Scholar] [CrossRef]
- Bouchaala, M.; Ghazel, C.; Saidane, L.A. Enhancing security and efficiency in cloud computing authentication and key agreement scheme based on smart card. J. Supercomput. 2022, 78, 497–522. [Google Scholar] [CrossRef]
- Xiang, X.; Cao, J.; Fan, W. Decentralized authentication and access control protocol for blockchain-based e-health systems. J. Netw. Comput. Appl. 2022, 207, 103512. [Google Scholar] [CrossRef]
- Wazid, M.; Gope, P. BACKM-EHA: A novel blockchain-enabled security solution for IoMT-based e-healthcare applications. ACM Trans. Internet Technol. 2023, 23, 1–28. [Google Scholar] [CrossRef]
- Xu, Y.; Zhou, Y.; Yang, B.; Qiao, Z.; Wang, Z.; Xia, Z.; Zhang, M. An Efficient Identity Authentication Scheme With Provable Security and Anonymity for Mobile Edge Computing. IEEE Syst. J. 2022, 17, 1012–1023. [Google Scholar] [CrossRef]
- Servati, M.R.; Safkhani, M. ECCbAS: An ECC based authentication scheme for healthcare IoT systems. Pervasive Mob. Comput. 2023, 90, 101753. [Google Scholar] [CrossRef]
- Moghadam, M.F.; Nikooghadam, M.; Mohajerzadeh, A.H.; Movali, B. A lightweight key management protocol for secure communication in smart grids. Electr. Power Syst. Res. 2020, 178, 106024. [Google Scholar] [CrossRef]
- Farhdi Moghadam, M.; Mohajerzdeh, A.; Karimipour, H.; Chitsaz, H.; Karimi, R.; Molavi, B. A privacy protection key agreement protocol based on ECC for smart grid. In Handbook of Big Data Privacy; Springer: Cham, Switzerland, 2020; pp. 63–76. [Google Scholar]
- Vangala, A.; Das, A.K.; Lee, J. Provably secure signature-based anonymous user authentication protocol in an Internet of Things-enabled intelligent precision agricultural environment. Concurr. Comput. Pract. Exp. 2023, 35, e6187. [Google Scholar] [CrossRef]
- Singh, A.K.; Nayyar, A.; Garg, A. A secure elliptic curve based anonymous authentication and key establishment mechanism for IoT and cloud. Multimed. Tools Appl. 2022, 82, 22525–22576. [Google Scholar] [CrossRef]
- Rangwani, D.; Om, H. 4F-MAKA: Four-factor mutual authentication and key agreement protocol for internet of things. Peer-Peer Netw. Appl. 2023, 16, 35–56. [Google Scholar] [CrossRef]
- Singh, N.; Das, A.K. TFAS: Two factor authentication scheme for blockchain enabled IoMT using PUF and fuzzy extractor. J. Supercomput. 2024, 80, 865–914. [Google Scholar] [CrossRef]
- Idrissi, H.; Palmieri, P. Agent-based blockchain model for robust authentication and authorization in IoT-based healthcare systems. J. Supercomput. 2024, 80, 6622–6660. [Google Scholar] [CrossRef]
- Limbasiya, T.; Das, D. Lightweight secure message broadcasting protocol for vehicle-to-vehicle communication. IEEE Syst. J. 2019, 14, 520–529. [Google Scholar] [CrossRef]
- Soni, M.; Singh, D.K. LAKA: Lightweight authentication and key agreement protocol for internet of things based wireless body area network. Wirel. Pers. Commun. 2022, 127, 1067–1084. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).