A Systematic Survey of Multi-Factor Authentication for Cloud Infrastructure
Abstract
1. Introduction
1.1. Research Background
1.2. Research Motivation
1.3. Outline and Contribution of Work
- It best utilizes only the Original Equipment Manufacturer (OEM)-fitted hardware and software without requiring additional or specialized Hardware and Software.
- Systematic analysis is conducted of various factors used for authentication in the light of multiple threats and vulnerabilities concerning user authentication for cloud environment.
- Systematic analysis is also conducted of available methods and means to be used to identify and make the best use of the least complex solution or combination of solutions towards implementing an efficient MFA for a Multi-Cloud scenario.
2. Authentication Process
2.1. Traditional Authentication
2.1.1. Proof-of-Knowledge
2.1.2. Proof-of-Ownership
2.1.3. Proof-of-Characteristic
2.1.4. Proof-of-Location
2.2. Cloud Authentication Mechanism
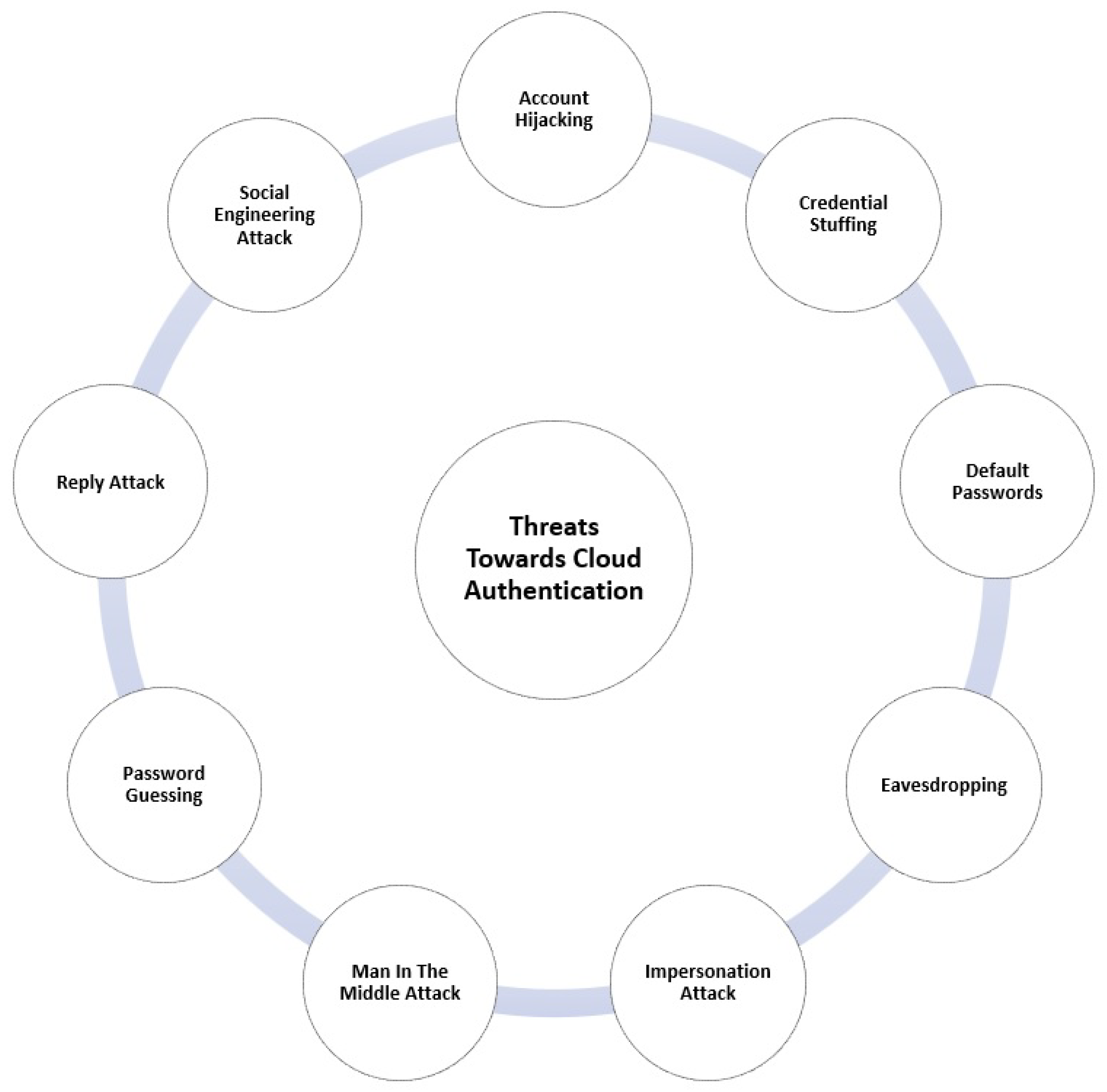
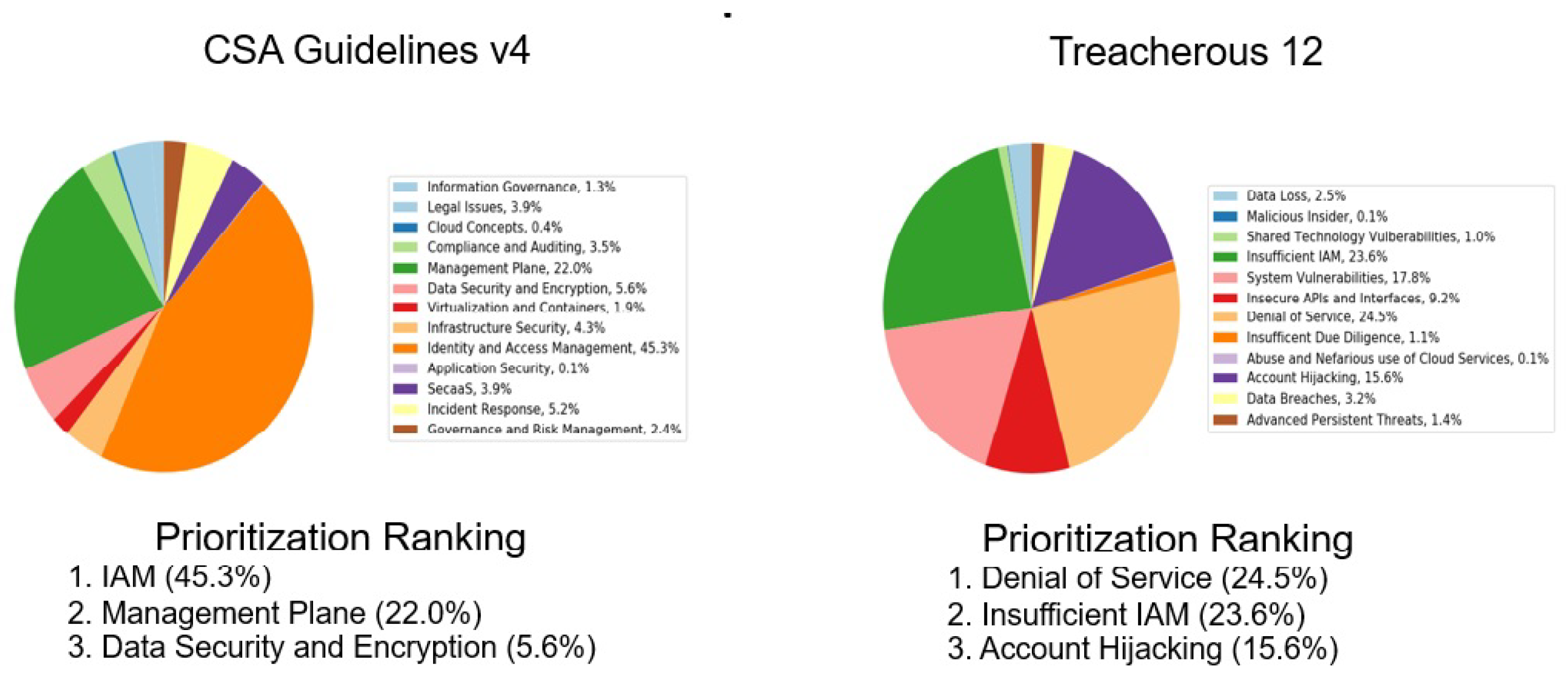
2.3. Threats towards Cloud Authentication
- Account hijacking: The process of an attacker stealing or hijacking a cloud account is known as cloud account hijacking. In identity theft schemes, cloud account hijacking is a typical strategy in which the attacker utilizes stolen account information to carry out illegal or unauthorized behavior. In reality, the attacker usually impersonates the account owner using stolen credentials to hijack a cloud account [49]. Attackers might use stolen credentials to access sensitive sections of cloud computing systems, jeopardizing their security, integrity, and availability.
- Credential Stuffing: In several cases, hackers have posted hacked and compromised credentials on the dark web. For credential stuffing, the attacker searches the dark web for a password that has already been hacked. Then, an attempt is made to penetrate the system using the already-compromised password as a credential. Similar efforts are made with other accounts of the same user who have passwords that have been hacked to access the system. When a person has numerous accounts in the system, it is usual practice to share a single password for convenience. Users’ habits of not choosing separate passwords for multiple accounts and reusing a common password are exploited in this form of attack [50]. Organizations like the Open Web Application Security Project (OWASP) have proposed many techniques to combat credential-stuffing attacks. The most generally recommended methods include using separate passwords for various user accounts and using the CAPTCHA system for authentication.
- Default Passwords: A pre-installed and factory-configured password is known as a default password. The system administrator and users do not update the default password of the system being used for convenience and occasionally due to ignorance. The failure to consider this essential factor is seen as a matter of concern for rendering the system vulnerable to cyber-attacks [51]. As a remedy, the system urges the system user to change the default password at initial use and with similar redirections for routine password changes with a pre-defined level of difficulty. Password policies such as a minimum length, a mix of upper- and lowercase alphabets, digits, and special characters are imposed on the user.
- Eavesdropping: The attacker uses this approach to secretly listen to and sniff private conversations between two people without their consent or knowledge. It is thought to be more straightforward if the attacker controls the system’s networking equipment and network traffic [52]. Suppose that non-secured HTTP and FTP-like service traffic is sniffed using the default networking port, and data traffic are studied. In that case, an attacker can quickly uncover the password and credentials from the analyzed network’s plain-text data traffic using tools or software like Wireshark. However, employing encrypted services in conjunction with standard encryption techniques may alleviate this.
- Impersonation Attack: In such an attack, an unauthorized user or wrong user makes an attempt to act as a genuine user by fraudulently acquiring the credentials of the actual user [53]. Such attacks could lead to serious data breaches in highly secured working environments like bank and defense sectors where highly sensitive, crucial information and applications are handled. This can be controlled by using biological uniqueness associated with the user.
- Man-in-the-Middle Attacks: A man-in-the-middle attack can steal user credentials if the attacker can get inside the sender and the receiver. The attacker may now transmit and receive all data exchanges between the two computers. As a result, the attacker can pose as a sender to the recipient and vice versa [54]. The attacker has the power to modify and delete sections of the communications in transit in addition to sending and receiving messages. As a result, the attacker can collect sensitive information, such as the username and password, and use it for malicious purposes.
- Password Guessing: Password guessing is a technique in which an adversary attempts to guess the username and password of a legitimate user and then authenticate it as being such. The attacker merely guesses probable passwords that the user will likely use in a password-guessing attack. A brute-force attack is generally an exhaustive search that an adversary can use to guess a password. It is an attack in which the attacker attempts to generate all potential password combinations and then authenticates to the system using the username and various password combinations [55]. The time it takes to carry out this assault is determined by the password’s length. A dictionary attack is when an attacker tries each word in a dictionary as a password to breach a password-protected authentication system. A password dictionary attack is still classified as both a brute-force attack and a dictionary attack. Similarly, a password-spraying assault is a sort of attack that depends on a small number of frequently utilized passwords.
- Replay Attacks: Another prominent method of attacking authentication methods is a replay attack. The replay attack involves a hacker copying a password or credential from one organization and utilizing it to authenticate with another. The goal is to mimic the user whose credentials or passwords have been copied. The attacker replicates the message or credentials and transmits them to an authenticator, hoping they will be validated successfully [56].
- Social Engineering Attack: Using personal and interpersonal skills is common in social engineering approaches, although it is not always essential to apply information technology. When a user is subjected to a social engineering attack, the adversary tries to persuade them so that they are obliged to disclose certain information or even do a specific action [57]. In today’s world, social engineering may take three primary forms: in-person social engineering, phone social engineering, and digital social engineering.
3. Factors of Authentication
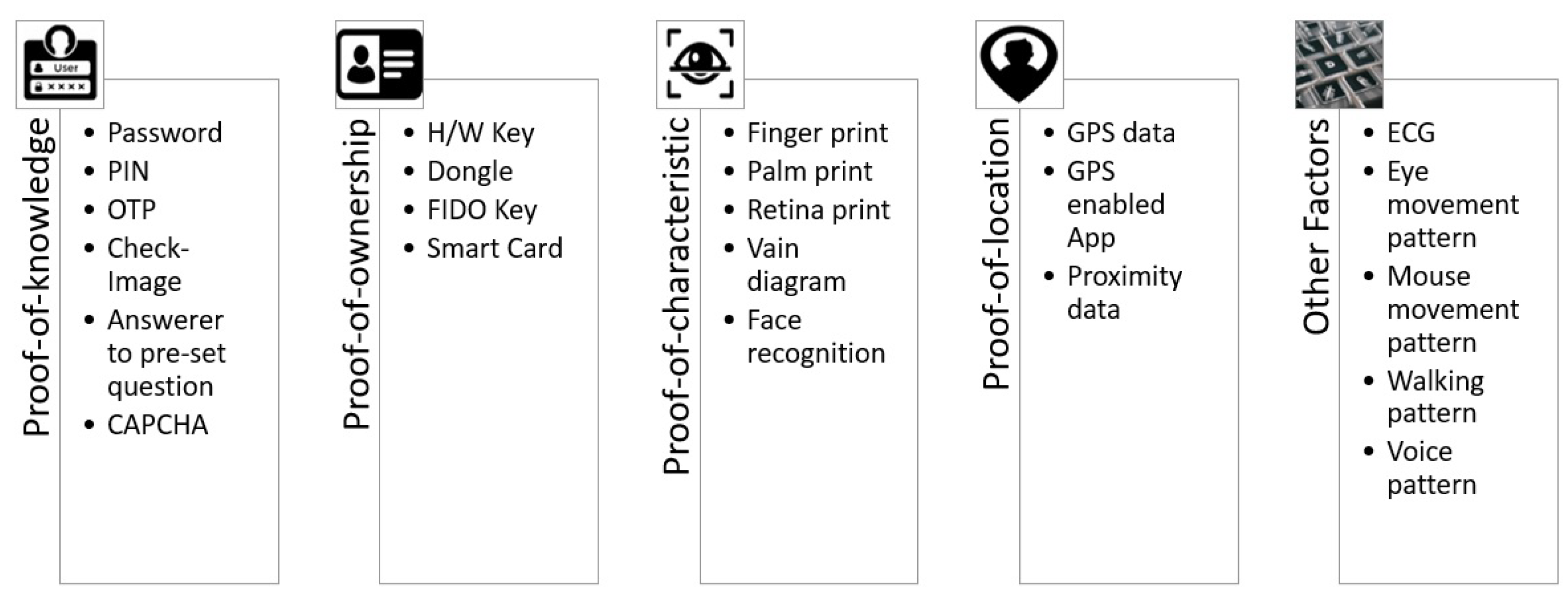
3.1. Knowledge Factors
3.2. Ownership Factors
3.3. Characteristic Factors
3.4. Location Factors
3.5. Other Related Factors
4. Analysis of Authentication Factors
4.1. Comparison of Factors for Authentication
- To access various services, users must remember the authentication factor. If one common password is used for several accounts, these programs may be affected if the password is compromised.
- When many passwords are used, the burden of its remembrance, upkeep, and safe-keeping for proof is on the users. Hence, password fatigue is evident when certain users only use one password for authentication.
- If this factor is penetrated or compromised, the user will be unable to utilize the service until the problem is fixed. It causes a considerable delay in obtaining the desired service or information needed when it is required.
- If a single element is compromised even without the user’s knowledge, the result might be disastrous.
| Approach | Advantages | Limitations | Ref. |
|---|---|---|---|
| Face Recognition | Convenient, quick, and efficient | Large storage requirement, can create data vulnerability, compromised biometric is irrecoverable | [23,67,68] |
| Fingerprint Scanner | Ease of use, cost-effective | Scanners may fail, easy to replicate fingerprint, compromised biometric is irrecoverable | [61,69,70,71] |
| Geographical Location | Effective in case the user needs to be present at a particular location | GPS may not be accurate at some locations | [61,72] |
| Ocular-based Methods | Very efficient and difficult to spoof | Need high-quality camera and robust mathematical techniques, compromised biometric is irrecoverable and cannot be changed | [23,73,74] |
| OTPs | Extra layer of security, hard to crack, expires after defined time | User availability required, lack of power backup, network issue, vulnerable to man-in-the-middle attacks | [20,75,76] |
| SmartPhone Applications | Code regenerated in defined time gap, hence safe from attacks | User availability required, lack of power backup, network issue, invalid codes for clock de-synchronization between device and service | [21,77,78] |
| SmartCards | More secure using encryption technology | Card may get lost, the chip may be damaged, radio interface for two-way communication | [78,79,80] |
| Thermal Image Recognition | Efficient, can be used from a large distance | Different thermal image in case of fever | [23,81,82] |
| Vein Recognition | Efficient, accurate | Expensive, but still vulnerable to spoofing attacks at the current stage, compromised biometric is irrecoverable | [61,71,83] |
| Voice Recognition | Convenient, quick and efficient | False negative in the loud background, change in voice due to sickness; compromised biometric is irrecoverable | [61,84,85] |
| Authentication Approach | Brute-Force Attack | Guess Attack | Phishing Attack | Spoofing Attack | Impersonation Attack | Ref. |
|---|---|---|---|---|---|---|
| Face Recognition | No | No | No | Yes | No | [23,67,68] |
| Fingerprint Scanner | No | No | No | Yes | No | [61,69,70,71] |
| Geographical Location | No | No | No | No | No | [61,72] |
| Ocular-based Methods | No | No | No | No (retina) & Yes (iris) | No | [23,73,74] |
| OTPs | No | No | Yes | No | Yes | [20,75,76] |
| Password/PIN | Yes | Yes | Yes | No | Yes | [14,70,71] |
| SmartPhone Applications | No | No | Yes | No | Yes | [21,77,78] |
| SmartCards | No | No | No | Yes | Yes | [78,79,80] |
| Thermal Image Recognition | No | No | No | No | No | [23,81,82] |
| Vein Recognition | No | No | No | Yes | No | [61,71,83] |
| Voice Recognition | No | No | No | Yes | No | [61,84,85] |
4.2. Weakness of Single-Factor Authentication
4.3. Emergence of Multi-Factor Authentication
4.4. Related Research Conducted on MFA
4.5. Face Recognition towards Potential MFA
- Capturing of the image.
- Detection of the face in the captured image.
- Comparison of detected facial features with the registered user’s stored credentials.
4.6. Threats to MFA
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| CNN | Convoluted Neural Network |
| CSP | Cloud Service Provider |
| LBA | Location-Based Authentication |
| MFA | Multi-Factor Authentication |
| PIN | Personal Identification Number |
| SFA | Single Factor Authentication |
| TTP | Trusted Third Party |
References
- Cybersecurity: Trends from 2022 and Predictions for 2023. Available online: https://www.infosecurity-magazine.com/blogs/trends-from-2022-predictions-for/ (accessed on 1 January 2023).
- Top Trends in Cybersecurity 2022. Available online: https://www.gartner.com/doc/reprints?id=1-29OTFFPI&ct=220411&st=sb (accessed on 3 January 2023).
- Boonkrong, S. Multi-factor Authentication. In Authentication and Access Control: Practical Cryptography Methods and Tools; Apress: Berkeley, CA, USA, 2021; pp. 133–162. [Google Scholar] [CrossRef]
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. Methodological Performance Analysis Applied to a Novel IIoT Access Control System Based on Permissioned Blockchain. Inf. Process. Manag. 2021, 58, 102558. [Google Scholar] [CrossRef]
- Rawal, B.S.; Manogaran, G.; Peter, A. Manage the Identification and Authentication of People, Devices, and Services. Cybersecurity and Identity Access Management; Springer Nature: Singapore, 2023; pp. 149–157. [Google Scholar] [CrossRef]
- Mihailescu, M.I.; Nita, S.L. A Searchable Encryption Scheme with Biometric Authentication and Authorization for Cloud Environments. Cryptography 2022, 6, 8. [Google Scholar] [CrossRef]
- Parikshit, N.; Shashikant, M.; Bhong, S.; Gitanjali, R. Authorization and Access Control, Authorization and Access Control; CRC Press: Boca Raton, FL, USA, 2022; pp. 19–31. [Google Scholar] [CrossRef]
- Goel, A. Access Control and Authorization Techniques w.r.t. Client Applications. Data Intelligence and Cognitive Informatics; Springer: Berlin/Heidelberg, Germany, 2022; pp. 23–44. [Google Scholar] [CrossRef]
- Gupta, M.; Awaysheh, F.; Benson, J.; Azab, M.; Patwa, F.; Sandhu, R. An Attribute-Based Access Control for Cloud-Enabled Industrial Smart Vehicles. IEEE Trans. Ind. Infor. 2021, 17, 4288–4297. [Google Scholar] [CrossRef]
- Gupta, M.; Sandhu, R. Towards Activity-Centric Access Control for Smart Collaborative Ecosystems. In Proceedings of the ACM Symposium on Access Control Models And Technologies (SACMAT), Trento, Italy, 7–9 June 2021. [Google Scholar] [CrossRef]
- Michal, T.; Amr, S.; Aishwarya, S.; Michael, C.; Tomas, C. Systematic Review of Authentication and Authorization Advancements for the Internet of Things. Sensors 2022, 22, 1361. [Google Scholar] [CrossRef]
- Ettore, F.; Maria, E.V. Generalities on Boolean and vectorial functions. In Boolean Functions for Cryptography and Coding Theory; Cambridge University Press: Cambridge, UK, 2020; pp. 27–75. [Google Scholar] [CrossRef]
- Ometov, A.; Bezzateev, S.; Mäkitalo, N.; Andreev, S.; Mikkonen, T.; Koucheryavy, Y. Multi-Factor Authentication: A Survey. Cryptography 2018, 2, 1. [Google Scholar] [CrossRef]
- Wang, C.; Wang, Y.; Chen, Y.; Liu, H.; Liu, J. User authentication on mobile devices: Approaches, threats and trends. Comput. Netw. 2020, 170, 107118. [Google Scholar] [CrossRef]
- Wang, D.; Zhang, X.; Zhang, Z.; Wang, P. Understanding security failures of multi-factor authentication schemes for multi-server environments. Comput. Secur. 2020, 88, 101619. [Google Scholar] [CrossRef]
- 2020 Annual Report. Identity Theft Resource Center. Available online: https://www.idtheftcenter.org/wp-content/uploads/2021/03/03.25.2020-2020-Annual-Report-FINAL-optimized.pdf (accessed on 22 December 2022).
- Security Guidance for Critical Areas of Focus in Cloud Computing v4.0. Available online: https://cloudsecurityalliance.org/artifacts/security-guidance-v4/ (accessed on 22 December 2022).
- The Treacherous Twelve’ Cloud Computing Top Threats in 2016. Available online: https://cloudsecurityalliance.org/artifacts/the-treacherous-twelve-cloud-computing-top-threats-in-2016/ (accessed on 22 December 2022).
- Ferrag, M.A.; Maglaras, L.; Derhab, A.; Janicke, H. Authentication schemes for smart mobile devices: Threat models, countermeasures, and open research issues. Telecommun. Syst. 2019, 73, 317–348. [Google Scholar] [CrossRef]
- Mujeye, S.; Levy, Y.; Mattord, H.; Li, W. Empirical results of an experimental study on the role of password strength and cognitive load on employee productivity. J. Appl. Knowl. Manag. 2016, 4, 99–116. [Google Scholar] [CrossRef]
- Sain, M.; Normurodov, O.; Hong, C.; Hui, K.L. A Survey on the Security in Cyber Physical System with Multi-Factor Authentication. In Proceedings of the 23rd International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 7–10 February 2021. [Google Scholar] [CrossRef]
- Federico, S.; Roberto, C.; Gabriele, C.; Nicola, Z. A survey on multi-factor authentication for online banking in the wild. Comput. Secur. 2020, 95, 101745. [Google Scholar] [CrossRef]
- ALSaleem, B.O.; Alshoshan, A.I. Multi-Factor Authentication to Systems Login. In Proceedings of the 2021 National Computing Colleges Conference (NCCC), Taif, Saudi Arabia, 27–28 March 2021. [Google Scholar] [CrossRef]
- Otta, S.P.; Panda, S. Decentralized Identity and Access Management of Cloud for Security as a Service. In Proceedings of the 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS), Bengaluru, India, 3–8 January 2022. [Google Scholar] [CrossRef]
- Otta, S.P.; Panda, S. Cloud Identity and Access Management Solution with Blockchain. In Blockchain Technology: Applications and Challenges; Springer: Berlin/Heidelberg, Germany, 2021; pp. 243–270. [Google Scholar] [CrossRef]
- Gupta, M.; Sandhu, R.; Mawla, T.; Benson, J. Reachability analysis for attributes in ABAC with group hierarchy. IEEE Trans. Dependable Secur. Comput. 2022, 20, 841–858. [Google Scholar] [CrossRef]
- Barkadehi, M.H.; Nilashi, M.; Ibrahim, O.; Fardi, A.Z.; Samad, S. Authentication systems: A literature review and classification. Telemat. Infor. 2018, 35, 1491–1511. [Google Scholar] [CrossRef]
- Huang, J.C.; Shu, M.H.; Hsu, B.M.; Hu, C.M. Service architecture of IoT terminal connection based on blockchain identity authentication system. Comput. Commun. 2020, 160, 411–422. [Google Scholar] [CrossRef]
- NIST Special Publication 800-63B. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-63b.pdf (accessed on 22 December 2022).
- Ibrokhimov, S.; Hui, K.L.; Al-Absi, A.A.; Sain, M. Multi-factor authentication in cyber physical system: A state of art survey. In Proceedings of the 2019 21st International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 17–20 February 2019. [Google Scholar] [CrossRef]
- Zahid, G.; Shafiq, A.; Khalid, M.; Hafizul, S.; Mohammad, M.H.; Giancarlo, F. An Improved Authentication Scheme for Remote Data Access and Sharing Over Cloud Storage in Cyber-Physical-Social-Systems. IEEE Access 2020, 8, 47144–47160. [Google Scholar] [CrossRef]
- Malina, L.; Dzurenda, P.; Hajny, J.; Martinasek, Z. Secure and efficient two-factor zero-knowledge authentication solution for access control systems. Comput. Secur. 2018, 77, 500–513. [Google Scholar] [CrossRef]
- Gajmal, Y.M.; Udayakumar, R. Analysis of Authentication based Data Access Control Systems in Cloud. J. Adv. Res. Dyn. Control Syst. 2020, 12, 2961–2967. [Google Scholar] [CrossRef]
- Li, Q.; Zhang, Q.; Huang, H.; Zhang, W.; Chen, W.; Wang, H. Secure, Efficient, and Weighted Access Control for Cloud-Assisted Industrial IoT. IEEE Internet Things J. 2022, 9, 16917–16927. [Google Scholar] [CrossRef]
- Prajapati, P.; Shah, P. A review on secure data deduplication: Cloud storage security issue. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 3996–4007. [Google Scholar] [CrossRef]
- Yuan, C.; Shuai, G.; Xindi, H. A Secure Authentication Mechanism for Multi-Dimensional Identifier Network. In Proceedings of the 2022 International Conference on Networking and Network Applications (NaNA), Urumchi, China, 3–5 December 2022. [Google Scholar] [CrossRef]
- Neha, C.K. Biometric re-authentication: An approach towards achieving transparency in user authentication. Multimed. Tools Appl. 2018, 78, 6679–6700. [Google Scholar] [CrossRef]
- Zuriati, A.; Zukarnain, A.M.; Mohd, K. Authentication Securing Methods for Mobile Identity Issues, Solutions and Challenges. Symmetry 2022, 14, 821. [Google Scholar] [CrossRef]
- Alamleh, H.; AlQahtani, A.A.S. Architecture for continuous authentication in location-based services. In Proceedings of the 2020 International Conference on Innovation and Intelligence for Informatics, Computing and Technologies (3ICT), Zallaq, Bahrain, 20–21 December 2020. [Google Scholar] [CrossRef]
- Gupta, M.; Sandhu, R. Authorization framework for secure cloud assisted connected cars and vehicular internet of things. In Proceedings of the 23nd ACM Symposium on Access Control Models and Technologies, Indianapolis, IN, USA, 7 June 2018. [Google Scholar] [CrossRef]
- Ahmad, W.; Rasool, A.; Javed, A.R.; Baker, T.; Jalil, Z. Cyber Security in IoT-Based Cloud Computing: A Comprehensive Survey. Electronics 2021, 11, 16. [Google Scholar] [CrossRef]
- Eranga, B.; Sachin, S.; Ravi, M.; Xueping, L.; Peter, F.; Nalin, R. Casper: A blockchain-based system for efficient and secure customer credential verification. J. Bank. Financ. Technol. 2021, 6, 43–62. [Google Scholar] [CrossRef]
- Rangwani, D.; Om, H. A Secure User Authentication Protocol Based on ECC for Cloud Computing Environment. Arab. J. Sci. Eng. 2021, 46, 3865–3888. [Google Scholar] [CrossRef]
- Cathey, G.; Benson, J. Edge centric secure data sharing with digital twins in smart ecosystems. In Proceedings of the 2021 Third IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Atlanta, GA, USA, 13–15 December 2021; pp. 70–79. [Google Scholar]
- Boonkrong, S. Methods and Threats of Authentication. In Authentication and Access Control; Springer: Berlin/Heidelberg, Germany, 2021; pp. 45–70. [Google Scholar] [CrossRef]
- Carlsson-Wall, M.; Lukas, G.; Jesper, H.; Kalle, K.; Carl-Johan, N. Exploring the implications of cloud-based enterprise resource planning systems for public sector management accountants. Financ. Account. Manag. 2021, 38, 177–201. [Google Scholar] [CrossRef]
- Pasika, R.; Anca, D.J.; Madhusanka, L. Survey on Multi-Access Edge Computing Security and Privacy. IEEE Commun. Surv. Tutor. 2021, 23, 1078–1124. [Google Scholar] [CrossRef]
- Kumar, R.; Goyal, R. On cloud security requirements, threats, vulnerabilities and countermeasures: A survey. Comput. Sci. Rev. 2019, 33, 1–48. [Google Scholar] [CrossRef]
- Nafea, R.A.; Ami, A.M. Cyber Security Threats in Cloud: Literature Review. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021. [Google Scholar] [CrossRef]
- Tankard, C. Credential stuffing—The New Hack. Netw. Secur. 2021, 2, 20. [Google Scholar] [CrossRef]
- AlHumaidan, Y.; AlAjmi, L.; Aljamea, M.; Mahmud, M. Analysis of Cloud Computing Security in Perspective of Saudi Arabia. In Proceedings of the 2018 IEEE 20th International Conference on E-Health Networking, Applications and Services (Healthcom), Ostrava, Czech Republic, 17–20 September 2018. [Google Scholar] [CrossRef]
- Sun, X. Critical Security Issues in Cloud Computing: A Survey. In Proceedings of the 2018 IEEE 4th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Omaha, NE, USA, 3–5 May 2018. [Google Scholar] [CrossRef]
- Lu, Y.; Zhao, D. Providing impersonation resistance for biometric-based authentication scheme in mobile cloud computing service. Comput. Commun. 2022, 182, 22–30. [Google Scholar] [CrossRef]
- Malani, S.; Srinivas, J.; Das, A.K.; Srinathan, K.; Jo, M. Certificate-based anonymous device access control scheme for IoT environment. IEEE Internet Things J. 2019, 6, 9762–9773. [Google Scholar] [CrossRef]
- Kumar, G.S.; Kandavel, N.; Madhavan, K. To Discovery The Cloud Services Authentication An Expert Based System Using Multi-Factor Authentication. In Proceedings of the 2020 6th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 March 2020. [Google Scholar] [CrossRef]
- Singh, V.; Pandey, S.K. Revisiting Cloud Security Threats: Replay attack. In Proceedings of the 2018 4th International Conference on Computing Communication and Automation (ICCCA), Greater Noida, India, 14–15 December 2018. [Google Scholar] [CrossRef]
- Ye, Z.; Guo, Y.; Ju, A.; Wei, F.; Zhang, R.; Ma, J. A Risk Analysis Framework for Social Engineering Attack Based on User Profiling. J. Organ. End User Comput. 2020, 32, 37–49. [Google Scholar] [CrossRef]
- Velásquez, I.; Caro, A.; Rodríguez, A. Authentication schemes and methods: A systematic literature review. Inf. Softw. Technol. 2018, 94, 30–37. [Google Scholar] [CrossRef]
- Ometov, A.; Petrov, V.; Bezzateev, S.; Andreev, S.; Koucheryavy, Y.; Gerla, M. Challenges of Multi-Factor Authentication for Securing Advanced IoT Applications. IEEE Netw. 2019, 33, 82–88. [Google Scholar] [CrossRef]
- Abbott, J.; Patil, S. How Mandatory Second Factor Affects the Authentication User Experience. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 17 June 2020. [Google Scholar] [CrossRef]
- Jaikla, T.; Pichetjamroen, S.; Vorakulpipat, C.; Pichetjamroen, A. A Secure Four-factor Attendance System for Smartphone Device. In Proceedings of the 2020 22nd International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 16–19 February 2020. [Google Scholar] [CrossRef]
- Tse, K.W.; Hung, K. User Behavioral Biometrics Identification on Mobile Platform using Multimodal Fusion of Keystroke and Swipe Dynamics and Recurrent Neural Network. In Proceedings of the 2020 IEEE 10th Symposium on Computer Applications & Industrial Electronics (ISCAIE), Penang, Malaysia, 18–19 April 2020. [Google Scholar] [CrossRef]
- Patel, S.C.; Jaiswal, S.; Singh, R.S.; Chauhan, J. Access Control Framework Using Multi-Factor Authentication in Cloud Computing. Int. J. Green Comput. 2018, 9, 1–15. [Google Scholar] [CrossRef]
- Six Types of Password Attacks & How to Stop Them. Available online: https://www.onelogin.com/learn/6-types-password-attacks (accessed on 27 June 2022).
- Subangan, S.; Senthooran, V. Secure authentication mechanism for resistance to password attacks. In Proceedings of the 2019 19th International Conference on Advances in ICT for Emerging Regions (ICTer), Colombo, Sri Lanka, 2–5 September 2019. [Google Scholar] [CrossRef]
- Alpatskiy, M.A.; Borzunov, G.I.; Epishkina, A.V.; Kogos, K.G. New Approach in the Rainbow Tables Method for Human-Like Passwords. In Proceedings of the 2020 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Moscow, Russia, 27–30 January 2020. [Google Scholar] [CrossRef]
- Liu, S.; Song, Y.; Zhang, M.; Zhao, J.; Yang, S.; Hou, K. An Identity Authentication Method Combining Liveness Detection and Face Recognition. Sensors 2019, 19, 4733. [Google Scholar] [CrossRef] [PubMed]
- Musa, A.; Vishi, K.; Rexha, B. Attack Analysis of Face Recognition Authentication Systems Using Fast Gradient Sign Method. Appl. Artif. Intell. 2021, 35, 1346–1360. [Google Scholar] [CrossRef]
- Kakkad, V.; Patel, M.; Shah, M. Biometric authentication and image encryption for image security in cloud framework. Multiscale Multidiscip. Model. Exp. Des. 2019, 2, 233–248. [Google Scholar] [CrossRef]
- AlQahtani, A.A.S.; El-Awadi, Z.; Min, M. A Survey on User Authentication Factors. In Proceedings of the 2021 IEEE 12th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 27–30 October 2021. [Google Scholar] [CrossRef]
- Adiraju, R.V.; Masanipalli, K.K.; Reddy, T.D.; Pedapalli, R.; Chundru, S.; Panigrahy, A.K. An extensive survey on finger and palm vein recognition system. Mater. Today Proc. 2021, 45, 1804–1808. [Google Scholar] [CrossRef]
- Eric, F.; Vendel, T.; Alexandre, K.; Radu, S. A Tale of Location-Based User Authentication. In Proceedings of the 2019 IEEE International Conference on Big Data and Smart Computing (BigComp), Kyoto, Japan, 27 February–2 March 2019. [Google Scholar] [CrossRef]
- Almadan, A.; Rattani, A. Compact CNN Models for On-device Ocular-based User Recognition in Mobile Devices. In Proceedings of the 2021 IEEE Symposium Series on Computational Intelligence (SSCI), Orlando, FL, USA, 5–7 December 2021. [Google Scholar] [CrossRef]
- Reddy, M.V.B.; Goutham, V. Iris Technology: A Review on Iris Based Biometric Systems for Unique Human Identification. Int. J. Res.-Granthaalayah 2018, 6, 80–90. [Google Scholar] [CrossRef]
- Erdem, E.; Sandikkaya, M.T. OTPaaS—One Time Password as a Service. IEEE Trans. Inf. Forensics Secur. 2019, 14, 743–756. [Google Scholar] [CrossRef]
- Kim, H.; Han, J.; Park, C.; Yi, O. Analysis of Vulnerabilities That Can Occur When Generating One-Time Password. Appl. Sci. 2020, 10, 2961. [Google Scholar] [CrossRef]
- Ozkan, C.; Bicakci, K. Security Analysis of Mobile Authenticator Applications. In Proceedings of the 2020 International Conference on Information Security and Cryptology (ISCTURKEY), Ankara, Turkey, 3–4 December 2020. [Google Scholar] [CrossRef]
- Gordin, I.; Graur, A.; Potorac, A. Two-factor authentication framework for private cloud. In Proceedings of the 2019 23rd International Conference on System Theory, Control and Computing (ICSTCC), Sinaia, Romania, 9–11 October 2019. [Google Scholar] [CrossRef]
- Bouchaala, M.; Ghazel, C.; Saidane, L.A. Enhancing security and efficiency in cloud computing authentication and key agreement scheme based on smart card. J. Supercomput. 2021, 78, 497–522. [Google Scholar] [CrossRef]
- Bobba, S.; Paruchuri, V. Single Sign-On Using Contactless Smart Cards and Fingerprint Authentication. In Advances on Broad-Band Wireless Computing, Communication and Applications; Springer: Berlin/Heidelberg, Germany, 2021; pp. 158–166. [Google Scholar] [CrossRef]
- Aiordachioaie, D.; Culea-Florescu, A.; Pavel, S.M. On Human Faces Thermal Image Processing for Classification Purposes. In Proceedings of the 2019 6th International Symposium on Electrical and Electronics Engineering (ISEEE), Galati, Romania, 18–20 October 2019. [Google Scholar] [CrossRef]
- Kakarwal, S.N.; Chaudhari, K.P.; Deshmukh, R.R.; Patil, R.B. Thermal Face Recognition using Artificial Neural Network. In Proceedings of the 2020 International Conference on Smart Innovations in Design, Environment, Management, Planning and Computing (ICSIDEMPC), Aurangabad, India, 30–31 October 2020. [Google Scholar] [CrossRef]
- Bowyer, K.W.; Boult, T.E.; Evans, N.; Hassner, T.; Kakadiaris, I.A.; Kittler, J.; Kumar, A.; Lu, J.; Maio, D.; Marcel, S.; et al. 2020 Index IEEE Transactions on Biometrics, Behavior, and Identity Science. IEEE Trans. Biom. Behav. Identity Sci. 2020, 2, 431–437. [Google Scholar] [CrossRef]
- Chang, Y.T.; Dupuis, M.J. My Voiceprint Is My Authenticator: A Two-Layer Authentication Approach Using Voiceprint for Voice Assistants. In Proceedings of the 2019 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Leicester, UK, 19–23 August 2019. [Google Scholar] [CrossRef]
- Debnath, S.; Ramalakshmi, K.; Senbagavalli, M. Multimodal Authentication System based on Audio-Visual data: A Review. In Proceedings of the 2022 International Conference for Advancement in Technology (ICONAT), Goa, India, 21–22 January 2022. [Google Scholar] [CrossRef]
- Most Common Passwords: Latest 2022 Statistics. Available online: https://cybernews.com/best-password-managers/most-common-passwords/ (accessed on 12 January 2023).
- Mawla, T. Activity Control: A Vision for “Active” Security Models for Smart Collaborative Systems. In Proceedings of the 27th ACM on Symposium on Access Control Models and Technologies, New York, NY, USA, 8–10 June 2022; pp. 207–216. [Google Scholar]
- Dasgupta, D.; Roy, A.; Nag, A. Toward the design of adaptive selection strategies for multi-factor authentication. Comput. Secur. 2016, 63, 85–116. [Google Scholar] [CrossRef]
- Oke, B.A.; Olaniyi, O.M.; Aboaba, A.A.; Arulogun, O.T. Developing multifactor authentication technique for secure electronic voting system. In Proceedings of the 2017 International Conference on Computing Networking and Informatics (ICCNI), Lagos, Nigeria, 29–31 October 2017. [Google Scholar] [CrossRef]
- Sciarretta, G.; Carbone, R.; Ranise, S.; Viganò, L. Formal Analysis of Mobile Multi-Factor Authentication with Single Sign-On Login. Princ. Secur. Trust. 2018, 23, 188–213. [Google Scholar] [CrossRef]
- Hammad, M.; Liu, Y.; Wang, K. Multimodal Biometric Authentication Systems Using Convolution Neural Network Based on Different Level Fusion of ECG and Fingerprint. IEEE Trans. Inf. Forensics Secur. 2019, 7, 26527–26542. [Google Scholar] [CrossRef]
- Zimmermann, V.; Gerber, N. The password is dead, long live the password—A laboratory study on user perceptions of authentication schemes. Int. J. Hum.-Comput. Stud. 2020, 133, 26–44. [Google Scholar] [CrossRef]
- Sharma, U.; Tomar, P.; Ali, S.S.; Saxena, N.; Bhadoria, R.S. Optimized Authentication System with High Security and Privacy. Electronics 2021, 10, 458. [Google Scholar] [CrossRef]
- Voege, P.; Ouda, A. An Innovative Multi-Factor Authentication Approach. In Proceedings of the 2022 International Symposium on Networks, Computers and Communications (ISNCC), Shenzhen, China, 19–22 July 2022. [Google Scholar] [CrossRef]
- Wenting, L.; Haibo, C.; Ping, W.; Kaitai, L. Practical Threshold Multi-Factor Authentication. IEEE Access 2021, 16, 3573–3588. [Google Scholar] [CrossRef]
- Aghili, S.; Sedaghat, M.; Singelée, D.; Gupta, M. MLS-ABAC: Efficient multi-level security attribute-based access control scheme. Future Gener. Comput. Syst. 2022, 131, 75–90. [Google Scholar] [CrossRef]
- Riseul, R.; Soonja, Y.; Soo-Hyung, K.; David, H. Continuous Multimodal Biometric Authentication. IEEE Access 2021, 9, 34541–34557. [Google Scholar] [CrossRef]
- Georgios, F.; Cyrus, M.; Jim, P.; Eirini, E.T. Reinforcement Learning Toward Decision-Making for Multiple Trusted-Third-Parties in PUF-Cash. In Proceedings of the 2020 6th World Forum on Internet of Things (WF-IoT), New Orleans, LO, USA, 2–16 June 2020. [Google Scholar] [CrossRef]
- Otta, S.P.; Kolipara, S.; Panda, S.; Hota, C. User Identification with Face Recognition: A Systematic Analysis. In Proceedings of the 2022 3rd International Conference for Emerging Technology (INCET), Belgaum, India, 27–29 May 2022. [Google Scholar] [CrossRef]
| Potential Threat | Suggested Remedial Measures | Ref. |
|---|---|---|
| Account Hijacking | Use of MFA Use of One Time Password (OTP) Use of End-to-End Encryption | [21,49] |
| Credential Stuffing | Use of different passwords for different accounts Use of MFA | [23,50] |
| Default Passwords | Use of random and unique default passwords Prompting and forcing users for changing default passwords | [23,51] |
| Eavesdropping | Adopting strong and robust encryption mechanism | [25,52] |
| Impersonation Attack | Use of biometric means to uniquely identify the user Use of MFA | [53] |
| Man-in-the-Middle Attacks | Use of Virtual Private Network (VPN) Adopting strong and robust encryption mechanism | [25,54] |
| Password Guessing | Using long and strong passwords that are not obvious No reuse of same and already used password | [45,55] |
| Replay Attacks | Use of a strong and robust Challenge-Response means | [25,56] |
| Social Engineering Attack | Educating users on how to avoid being a victim of in-person, over-the-phone, and digital attacks such as phishing or e-mail attacks. | [25,57] |
| Ref. (Year) | Advantages | Limitations | Inherent Vulnerability |
|---|---|---|---|
| [88] (2016) | (i) Dynamic and environment dependent to choose most suited modalities. (ii) Reduces predictability for the attacker. (iii) Positive experience regarding usability. | (i) Quite complex. (ii) Requires large storage. (iii) Registration is lengthy as multiple input of biometrics of the user is required for password creation. | Depends on a particular set of approaches selected at a time |
| [89] (2017) | The data is stored in the smartcard in an encrypted way. | (i) Card may be lost or stolen. (ii) Spoofed fingerprints from other sources may be used. | Spoofing attack |
| [90] (2018) | (i) Secured approach. (ii) Transmissions are encoded cryptographically. (iii) OTPs are timed. | (i) Requires downloading of different app. (ii) Unavailability of smartphone. | Phishing attack |
| [91] (2019) | The combination of the fingerprint with ECG is more secure as it provides the liveness factor. | Slow and requires high power consumption; costly. | NA |
| [92] (2020) | (i) Use of textual and figurative credentials. (ii) Use of human factors. | (i) More cognitive on the human brain. (ii) Special hardware for human-specific biometric verification | Guessing attack |
| [23] (2021) | (i) Cheap and secure in comparison to textual passwords. Anti-key-logger and anti-screen recorder | (i) Increases cognitive load of the user. (ii) A small approach, not suitable on a large scale. (iii) More time-consuming. | Phishing attack |
| [93] (2021) | Templates are such that attackers cannot access the original fingerprint details from them | Fingerprints may be stolen from other sources and spoofed | Spoofing attack |
| [94] (2022) | (i) Uses Autonomous Inquiry-based Authentication Chatbot (AIAC). (ii) Human Dynamics Insight And Metrics segment of the authentication framework is used. | (i) Chatbot needs sufficient training on user credential data. (ii) It incorporates a huge credential dataset depending on the number of registered users of the system. | (i) Impersonation attack. (ii) Central point of failure of the authentication process. |
| Threat | Envisaged Effect |
|---|---|
| Biometric Spoofing | Biometric authentication mechanisms may be vulnerable to spoofing attacks, where attackers create fake biometric data to fool the authentication system. |
| Credential stuffing | Attackers may use stolen MFA credentials to gain access to other accounts belonging to the same user. |
| Denial of Service (DoS) attacks | Attackers may launch DoS attacks against the authentication system, preventing legitimate users from accessing their accounts. |
| Insider Threats | Employees or contractors with access to sensitive systems may abuse their privileges to bypass MFA or steal MFA credentials. |
| Malware | Malicious software such as keyloggers or screen capture tools may be used to steal MFA credentials from infected devices. |
| Man-in-the-middle attacks | Attackers may intercept communication between users and the authentication system, allowing them to steal MFA credentials. |
| Social Engineering | Attackers may attempt to trick users into divulging their MFA credentials through phishing attacks or other forms of social engineering. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Otta, S.P.; Panda, S.; Gupta, M.; Hota, C. A Systematic Survey of Multi-Factor Authentication for Cloud Infrastructure. Future Internet 2023, 15, 146. https://doi.org/10.3390/fi15040146
Otta SP, Panda S, Gupta M, Hota C. A Systematic Survey of Multi-Factor Authentication for Cloud Infrastructure. Future Internet. 2023; 15(4):146. https://doi.org/10.3390/fi15040146
Chicago/Turabian StyleOtta, Soumya Prakash, Subhrakanta Panda, Maanak Gupta, and Chittaranjan Hota. 2023. "A Systematic Survey of Multi-Factor Authentication for Cloud Infrastructure" Future Internet 15, no. 4: 146. https://doi.org/10.3390/fi15040146
APA StyleOtta, S. P., Panda, S., Gupta, M., & Hota, C. (2023). A Systematic Survey of Multi-Factor Authentication for Cloud Infrastructure. Future Internet, 15(4), 146. https://doi.org/10.3390/fi15040146









