Study of Coded ALOHA with Multi-User Detection under Heavy-Tailed and Correlated Arrivals
Abstract
1. Introduction
2. System Model
2.1. Coded-Slotted ALOHA
- The packet loss ratio (). It is the probability that a packet is not decoded correctly. Observe that this event is the non-existence of resolvable patterns of decoding in any of the slots containing some replica of the packet.
- The delay of a decoded packet. This is defined as the number of slots between the user’s arrival and the slot where the packet is resolved and correctly decoded.
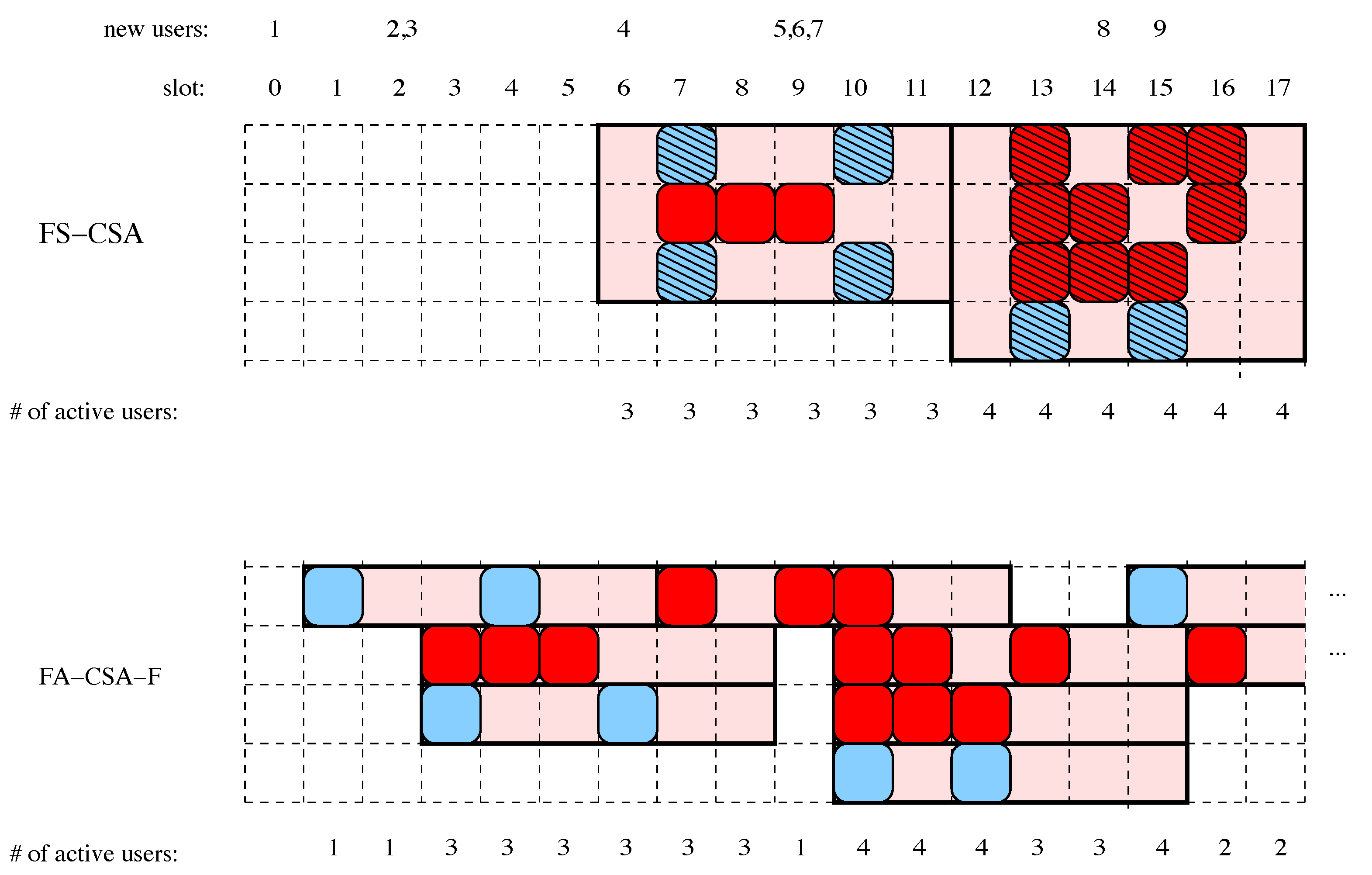
- Frame synchronous CSA (FS-CSA). In this scheme, time is divided in frames, each consisting of n slots. Any new packet from a transmitter must wait until the beginning of the next frame for attempting the transmission of its ℓ replicas, which are randomly and uniformly distributed over the frame time. A node with packets being scheduled for transmission in a frame is called an active node, thus the number M of active nodes in the frame is a random variable.For the receiver, in FS-CSA decoding is performed slot-by-slot by applying the following strategy: first, in a given slot all the interference caused by packets that have been successfully decoded in the previous slots of the frame is removed. If, after this step, the result is a degree-k (or lower) slot, then all the packets in it are decoded and the receiver proceeds to look for other slots in the frame from which the interference due to those newly decoded packets can be further removed. The decoding process finishes when the receiver cannot find any slots in the frame to which k-MUD can be applied to. Thus, notice that, at the end of a frame, all the packets from the active users will have been either decoded successfully or dropped at the receiver.
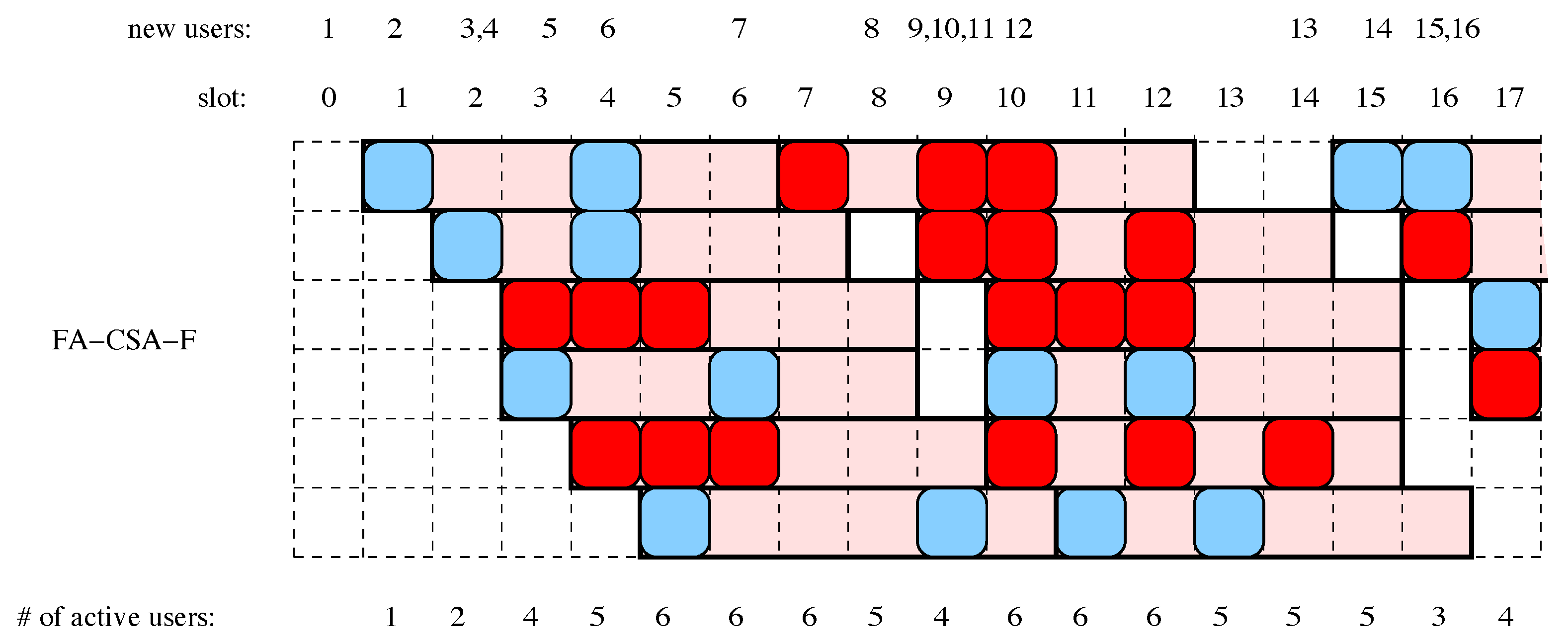
- Frame asynchronous CSA (FA-CSA). In this scheme, a new packet is transmitted immediately after its arrival, in the next slot, and its remaining replicas are transmitted at random times within the subsequent slots, uniformly drawn. Therefore, in FA-CSA there also exists a time period of n slots for sending the copies of a packet, but the nodes are no longer enforced to be synchronized in global frames. Nodes are active (i.e., they have some replica of a packet awaiting for transmission) during the n slots following the new arrival, and again the total number M of active nodes in a slot is a random value. Unlike FS-CSA, where M only changes from frame to frame, here in FA-CSA M varies on a lost basis. In the literature, two minor variants of FA-CSA have been considered. One is the system described here, when the transmission of the first copy of a packet is immediate. The second consists in treating the first copy in the same way as the remaining ones, i.e., the replicas are transmitted randomly and uniformly over the next n time slots.The decoding process in FA-CSA is performed following the same steps as with FS-CSA, but with the important difference that the receiver needs to keep memory of all the slots that precede the current one (FS-CSA works only on the set of slots of the current frame, n). However, it is clear that in practice the receivers in FA-CSA would need a finite memory during the decoding decisions in order to keep the memory finite. We will denote by this finite size of the receiver memory counted in number of slots. To all matters, operates as a sliding window for the recovery of the packets, and we will assume that any packets received in a slot out of this window and not yet recovered are dismissed.
2.2. Bipartite Graph Representation and Degree Distributions
3. Modeling the Arrival Processes
3.1. Marginal Distribution of the Arrivals
3.1.1. Poisson Distribution
3.1.2. Lognormal Distribution
3.1.3. Pareto Distribution
3.2. Correlated Arrivals
- The marginal distribution is .
- The covariance function is .
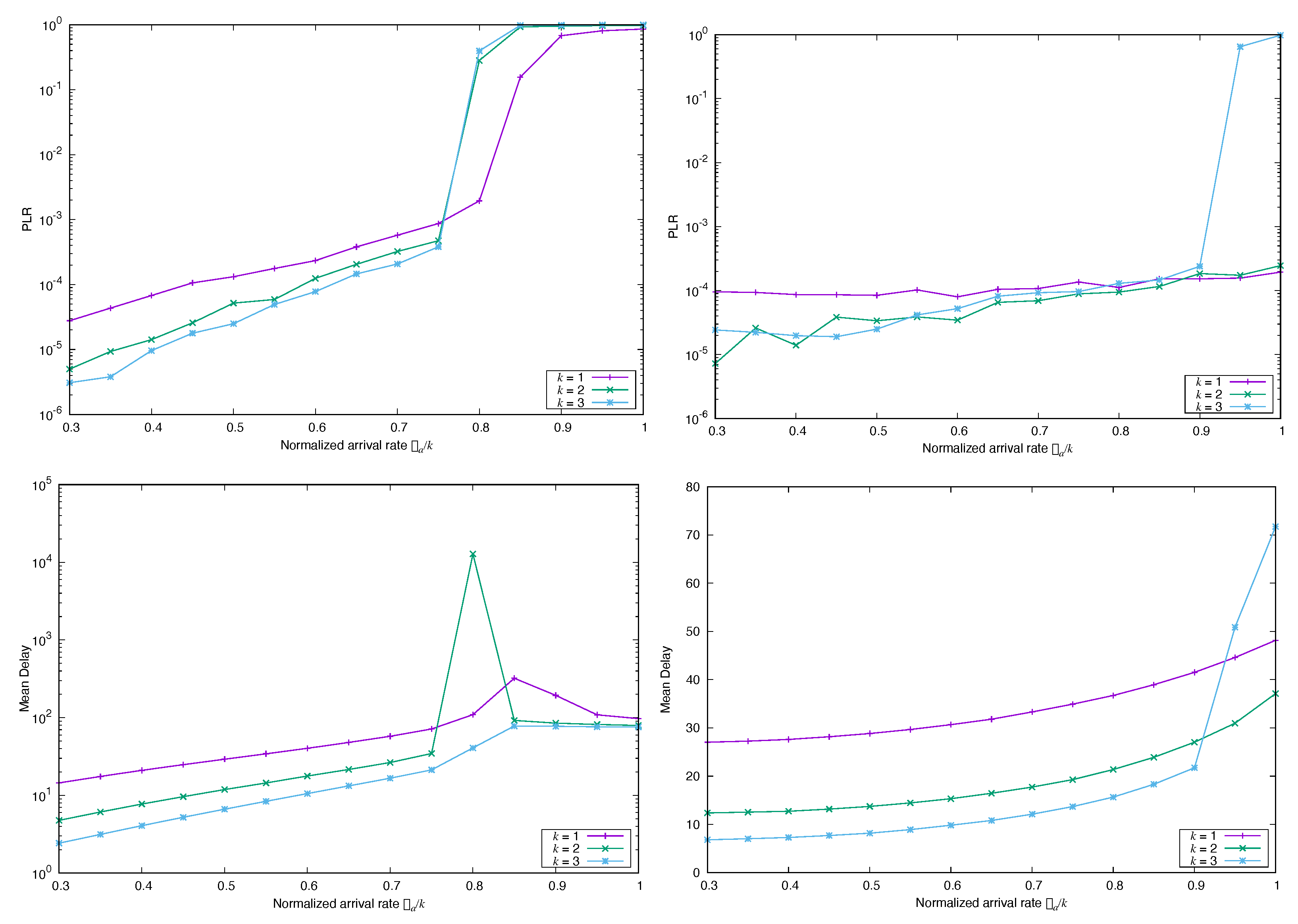
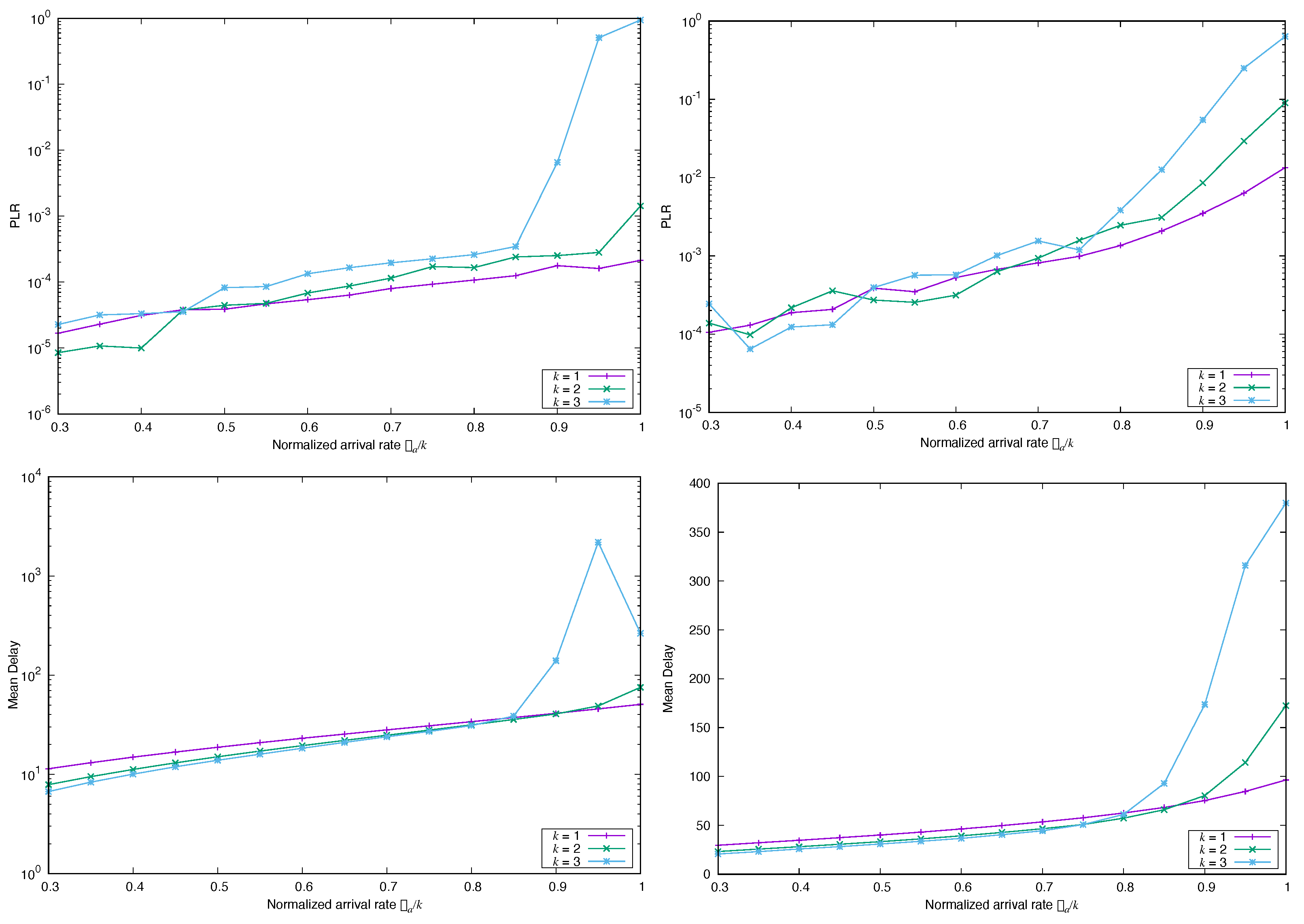
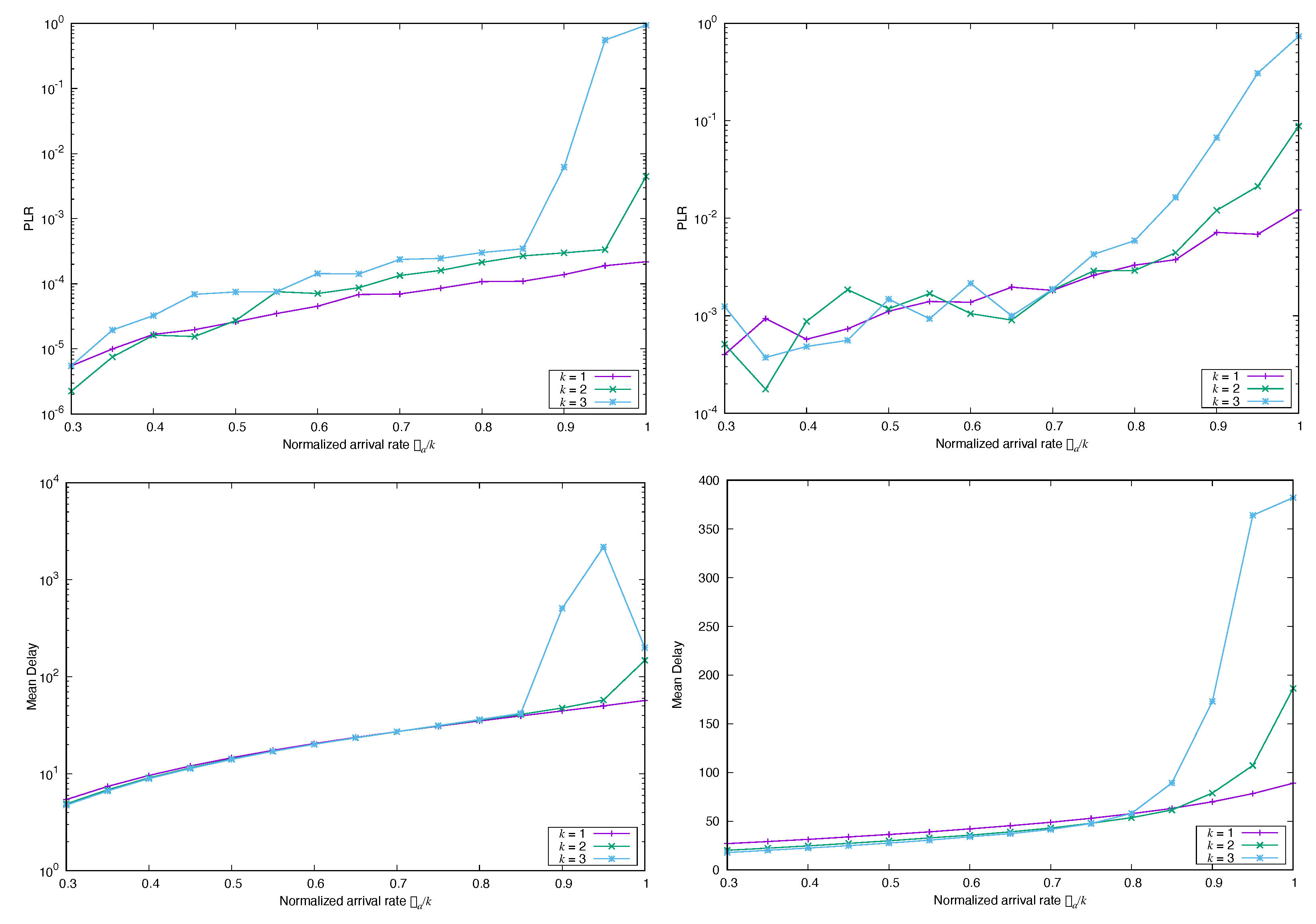
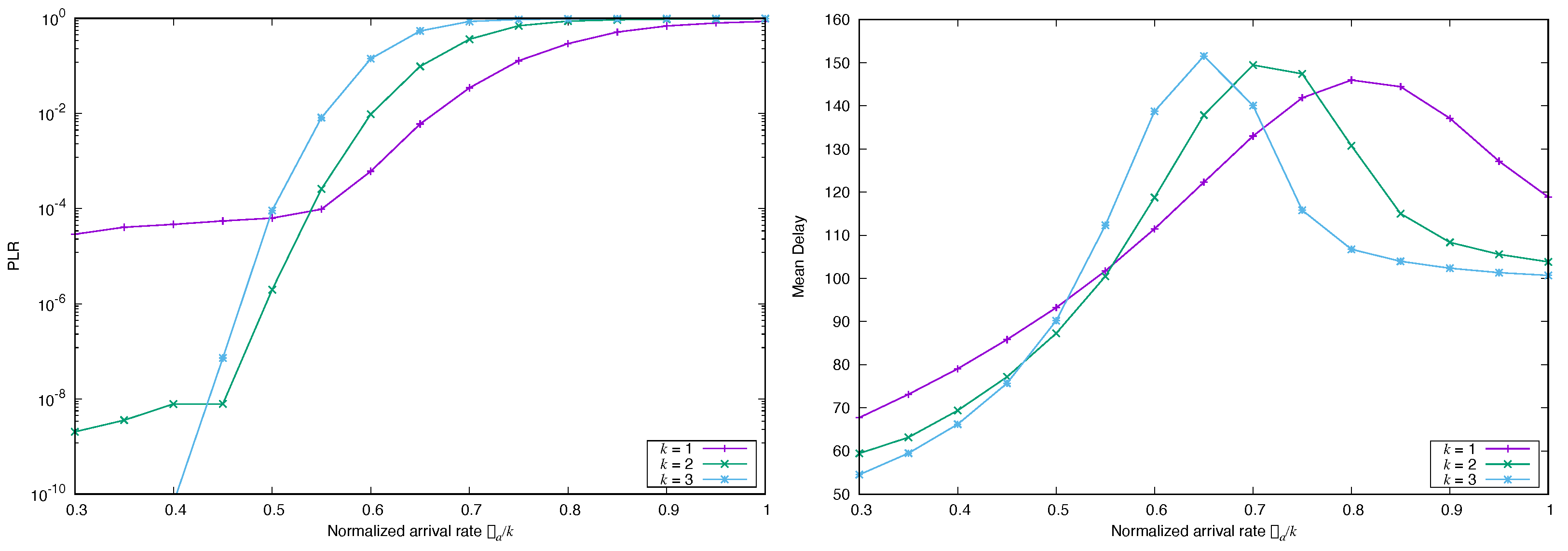
4. Numerical Experiments
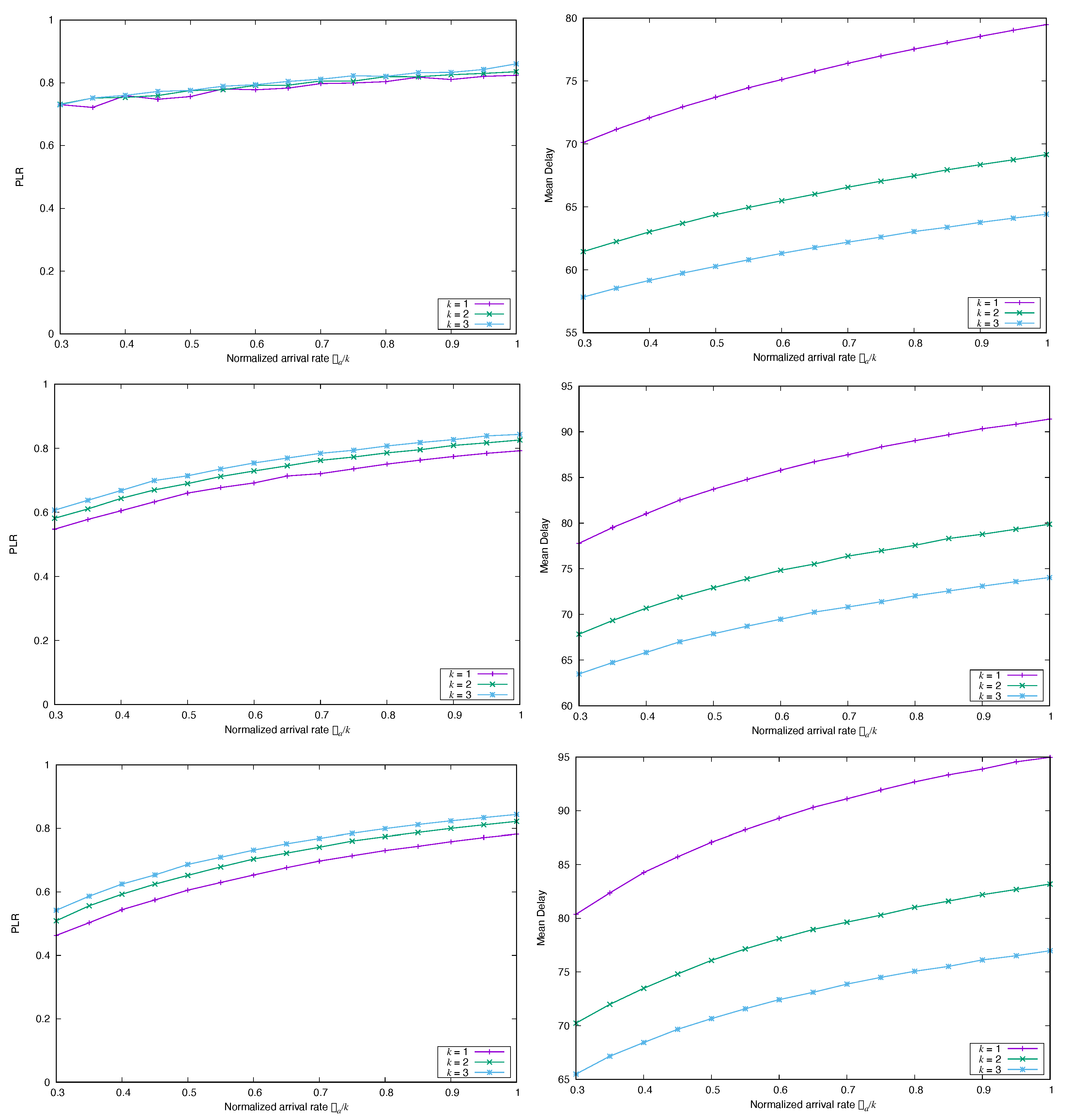
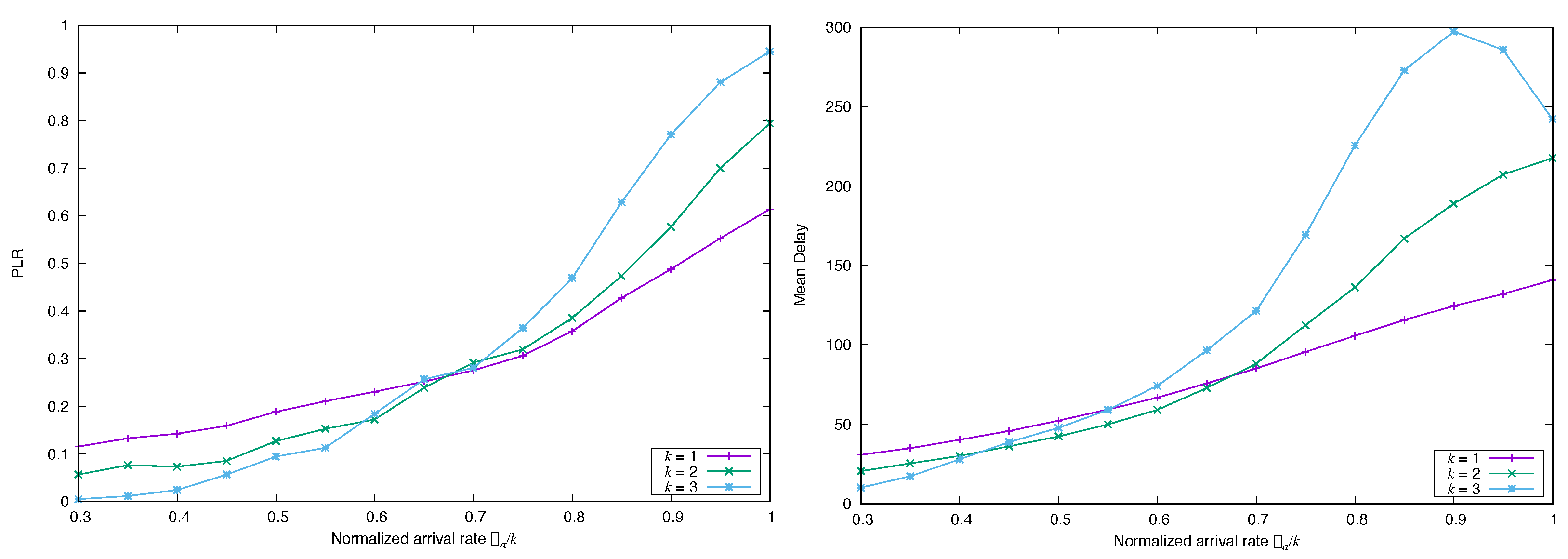
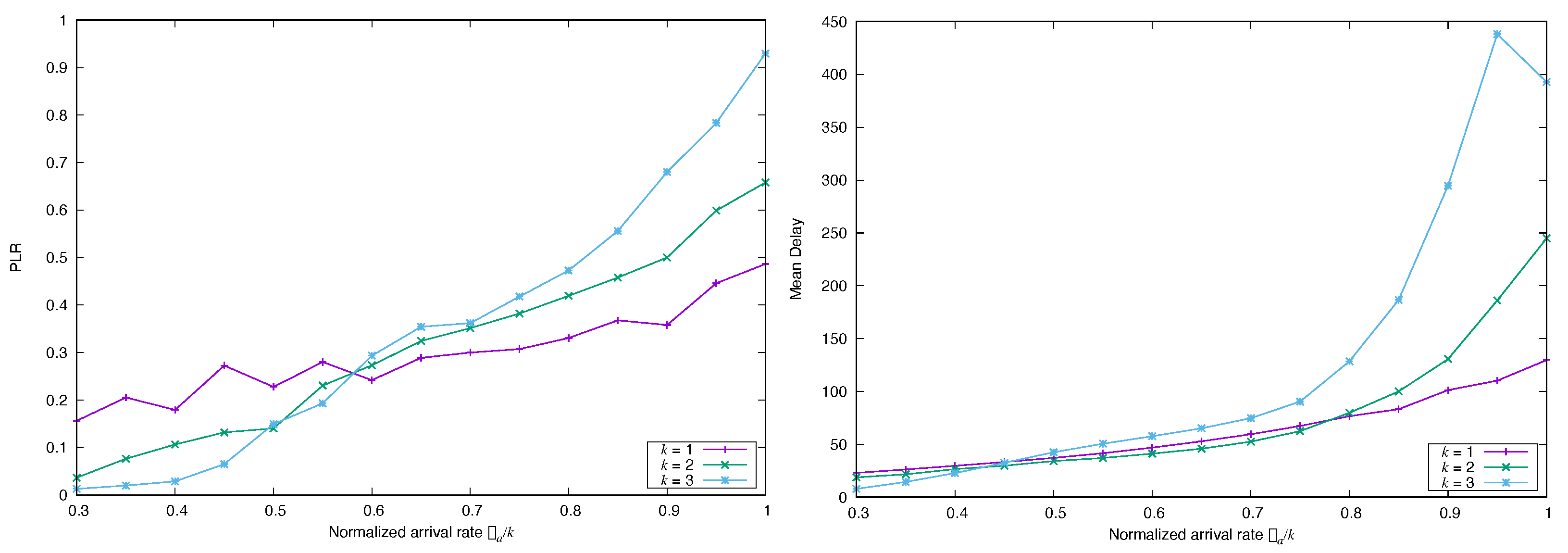
4.1. Impact of the Marginal Distribution of the Arrival Process
4.1.1. Frame Synchronous Coded-Slotted ALOHA
4.1.2. Frame Asynchronous Coded-Slotted ALOHA
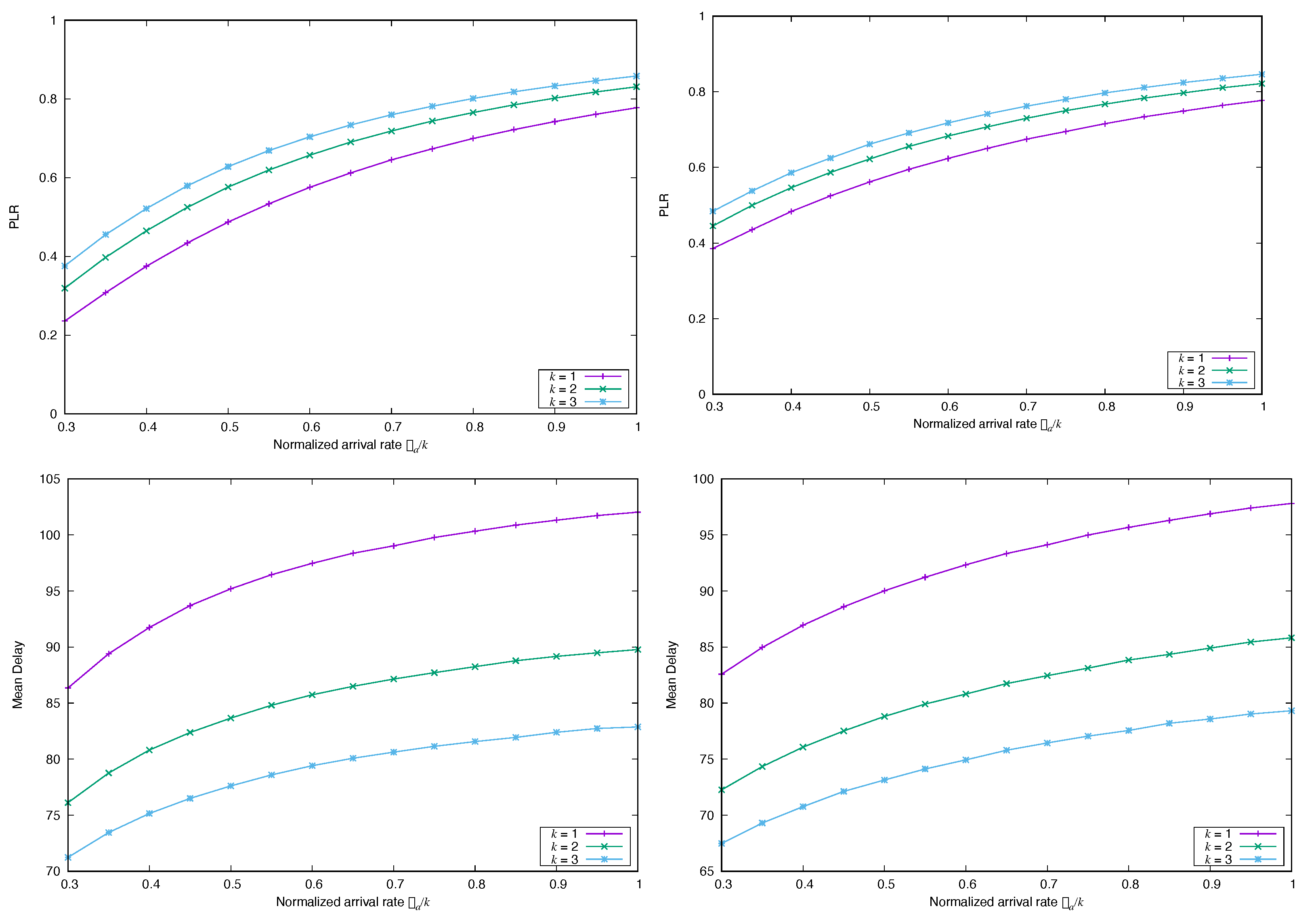
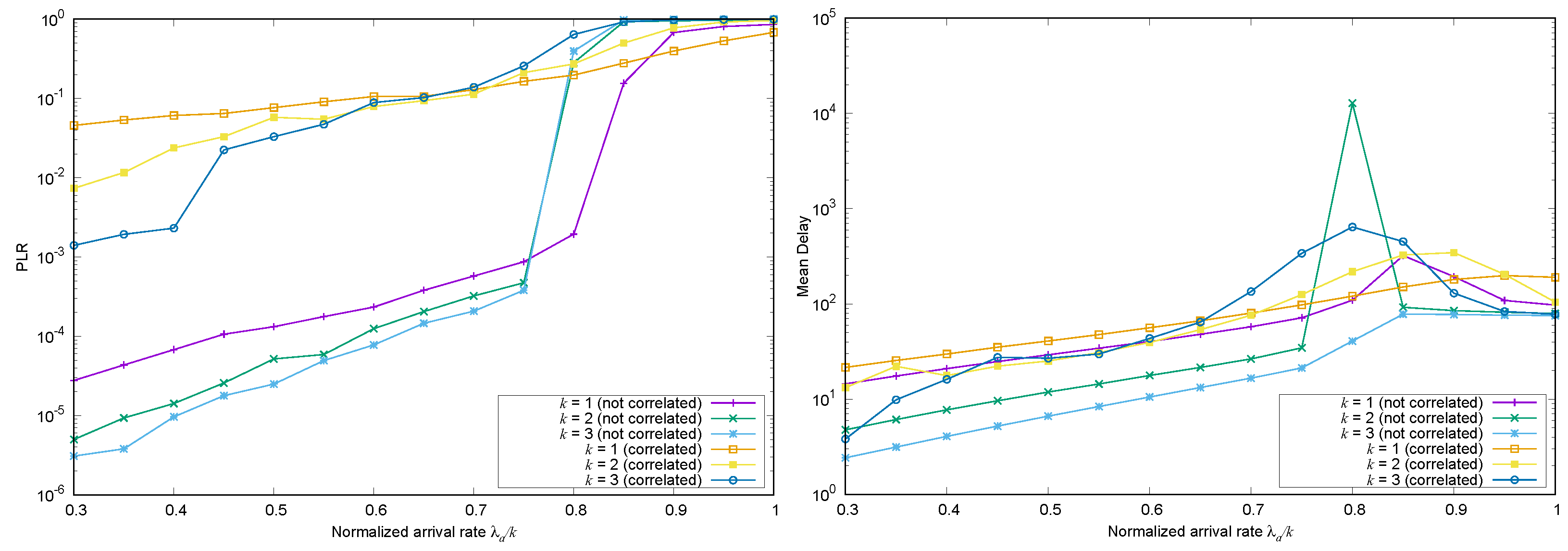
4.2. Impact of the Correlation Structure of the Arrival Process
4.2.1. Frame Synchronous Coded-Slotted ALOHA
4.2.2. Frame Asynchronous Coded-Slotted ALOHA
5. Discussion
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Abramson, N. The Throughput of Packet Broadcasting Channels. IEEE Trans. Commun. 1977, 25, 117–128. [Google Scholar] [CrossRef]
- Abramson, N. Development of the Alohanet. IEEE Trans. Inf. Theory 1985, 31, 119–123. [Google Scholar] [CrossRef]
- Kleinrock, L.; Tobagi, F. Packet Switching in Radio Channels: Carrier Sense Multiple-Access Modes and Their Throughput-Delay Characteristics. IEEE Trans. Commun. 1975, 23, 1400–1416. [Google Scholar] [CrossRef]
- Bianchi, G. Performance Analysis of the IEEE 802.11 Distributed Coordination Function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Mulyanasari, A.R.; Pamukti, B.; Hambali, A. Frameless Coded Slotted ALOHA Scheme with Frequency Domain-Extended on NLOS Visible Light Communication Channel. In Proceedings of the 2022 International Conference of Science and Information Technology in Smart Administration (ICSINTESA), Denpasar, Indonesia, 10–12 November 2022. [Google Scholar] [CrossRef]
- Tseng, S.M.; Chang, C.K.; Liu, M.Y.; Wang, Y.C. Throughput analysis of 2-D OCDMA/pure ALOHA Networks with Access Control and Two User Classes of Variable Length for Multimedia Traffic. Int. J. Light Electron Opt. 2021, 241, 166928. [Google Scholar] [CrossRef]
- Abid, M.; Ma, H.; Muhammad, S.; Jin, Y. Optimizing the Performance of Pure ALOHA for LoRa-Based ESL. Sensors 2021, 21, 5060. [Google Scholar] [CrossRef]
- Berioli, M.; Cocco, G.; Liva, G.; Munari, A. Modern Random Access Protocols; Now Publishers: Norwell, MA, USA, 2016. [Google Scholar] [CrossRef]
- Vem, A.; Narayanan, K.R.; Chamberland, J.F.; Cheng, J. A User-Independent Successive Interference Cancellation Based Coding Scheme for the Unsourced Random Access Gaussian Channel. IEEE Trans. Commun. 2019, 67, 8258–8272. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, S.; Mu, X.; Ding, Z.; Schober, R.; Al-Dhahir, N.; Hossain, E.; Shen, X. Evolution of NOMA toward Next Generation Multiple Access (NGMA) for 6G. IEEE J. Sel. Areas Commun. 2022, 4, 1037–1071. [Google Scholar] [CrossRef]
- Sandgren, E.; Amat, A.G.; Brannstrom, F. On Frame Asynchronous Coded Slotted ALOHA: Asymptotic, Finite-Length and Delay Analysis. IEEE Trans. Commun. 2017, 65, 691–704. [Google Scholar] [CrossRef]
- Amat, A.G.; Liva, G. Finite-Length Analysis of Irregular Repetition Slotted ALOHA in the Waterfall Region. IEEE Commun. Lett. 2018, 22, 886–889. [Google Scholar] [CrossRef]
- Ivanov, M.; Brannstrom, F.; Amat, A.G.; Popovski, P. Error Floor Analysis of Coded Slotted ALOHA over Packet Erasure Channels. IEEE Commun. Lett. 2015, 19, 419–422. [Google Scholar] [CrossRef]
- Casini, E.; Gaudenzi, R.D.; Río, O. Contention Resolution Diversity Slotted ALOHA (CRDSA): An Enhanced Random Access Scheme for Satellite Access Packet Networks. IEEE Trans. Wirel. Commun. 2007, 6, 1408–1419. [Google Scholar] [CrossRef]
- Meloni, A.; Murroni, M.; Kissling, C.; Berioli, M. Sliding Window-based Contention Resolution Diversity Slotted ALOHA. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012. [Google Scholar] [CrossRef]
- Río, O.; Gaudenzi, R. Generalized Analytical Framework for the Performance Assessment of Slotted Random Access Protocols. IEEE Trans. Wirel. Commun. 2014, 13, 809–821. [Google Scholar] [CrossRef]
- Akyildiz, T.; Demirhan, U.; Duman, T.M. Energy Harvesting Irregular Repetition ALOHA with Replica Concatenation. IEEE Trans. Wirel. Commun. 2021, 20, 955–968. [Google Scholar] [CrossRef]
- Clazzer, F.; Amat, A.G. Error Floor Analysis of Irregular Repetition ALOHA. In Proceedings of the 2022 IEEE International Conference on Conmunications, Foshan, China, 11–13 August 2022. [Google Scholar] [CrossRef]
- EN 301 545-2; Digital Video Broadcasting (DVB); Second Generation DVB Interactive Satellite System (DVB-RCS2); Part 2: Lower Layers for Satellite Standard. Technical Report; ETSI: Sophia Antipolis, France, 2020.
- Munari, A.; Clazzer, F. Modern Random Access for Beyond-5G Systems: A Multiple-Relay ALOHA Perspective. arXiv 2019, arXiv:1906.02054. [Google Scholar] [CrossRef]
- Polyanskiy, Y. A Perspective on Massive Random-Access. In Proceedings of the 2017 IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017. [Google Scholar] [CrossRef]
- Liva, G. Graph-Based Analysis and Optimization of Contention Resolution Diversity Slotted ALOHA. IEEE Trans. Commun. 2011, 59, 477–487. [Google Scholar] [CrossRef]
- Paolini, E.; Liva, G.; Chiani, M. Coded Slotted ALOHA: A Graph-Based Method for Uncoordinated Multiple Access. IEEE Trans. Inf. Theory 2015, 61, 6815–6832. [Google Scholar] [CrossRef]
- Paolini, E.; Valentini, L.; Tralli, V.; Chiani, M. Irregular Repetition Slotted ALOHA in an Information-Theoretic Setting. In Proceedings of the 2022 IEEE International Symposium on Information Theory (ISIT), IEEE, Espoo, Finland, 26 June–1 July 2022. [Google Scholar] [CrossRef]
- Tseng, S.M.; Chen, W.Y. Cross-Layer Codebook Allocation for Uplink SCMA and PDNOMA-SCMA Video Transmission Systems and a Deep Learning-Based Approach. IEEE Trans. Inf. Theory 2023, 17, 294–305. [Google Scholar] [CrossRef]
- Gallager, R. Low-Density Parity-Check Codes. IEEE Trans. Inf. Theory 1962, 8, 21–28. [Google Scholar] [CrossRef]
- Luby, M.; Mitzenmacher, M.; Shokrollahi, M.A.; Spielman, D.A. Improved Low-Density Parity-Check Codes using Irregular Graphs. IEEE Trans. Inf. Theory 2001, 47, 585–598. [Google Scholar] [CrossRef]
- Richardson, T.J.; Shokrollahi, M.A.; Urbanke, R.L. Design of Capacity-Approaching Irregular Low-Density Parity-Check Codes. IEEE Trans. Inf. Theory 2001, 47, 619–637. [Google Scholar] [CrossRef]
- Clazzer, F.; Kissling, C.; Marchese, M. Enhancing contention resolution ALOHA using combining techniques. IEEE Trans. Commun. 2018, 66, 2576–2587. [Google Scholar] [CrossRef]
- Mengali, A.; Gaudenzi, R.; Arapoglou, P.D. Enhancing the Physical Layer of Contention Resolution Diversity Slotted ALOHA. IEEE Trans. Commun. 2017, 65, 4295–4308. [Google Scholar] [CrossRef]
- Alvi, S.; Durrani, S.; Zhou, X. Enhancing CRDSA With Transmit Power Diversity for Machine-Type Communication. IEEE Trans. Veh. Technol. 2018, 67, 7790–7794. [Google Scholar] [CrossRef]
- Shao, X.; Sun, Z.; Yang, M.; Gu, S.; Guo, Q. NOMA-Based Irregular Repetition Slotted ALOHA for Satellite Networks. IEEE Commun. Lett. 2019, 23, 624–627. [Google Scholar] [CrossRef]
- Munari, A.; Lazaro, F.; Durisi, G.; Liva, G. The Dynamic Behavior of Frameless ALOHA: Stability, Throughput, and Age of Information. arXiv 2023, arXiv:2301.10078. [Google Scholar] [CrossRef]
- Ghanbarinejad, M.; Schlegel, C. Irregular Repetition Slotted ALOHA with Multiuser Detection. In Proceedings of the 2013 Annual Conference on Wireless On-Demand Network Systems and Services (WONS), Banff, AB, Canada, 18–20 March 2013. [Google Scholar] [CrossRef]
- Hmedoush, I.; Adjih, C.; Muhlethaler, P.; Kumar, V. On the Performance of Irregular Repetition Slotted ALOHA with Multiple Packet Reception. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020. [Google Scholar] [CrossRef]
- Pipiras, V.; Taqqu, S.M. Long-Range Dependence and Self-Similarity; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar] [CrossRef]
- Ivanov, M.; Brannstrom, F.; Graell, A.; Popovski, P. Broadcast Coded Slotted ALOHA: A Finite Frame Length Analysis. IEEE Trans. Commun. 2017, 65, 651–662. [Google Scholar] [CrossRef]
- Cox, D.R. Point Processes; Chapman and Hall: London, UK, 1980. [Google Scholar] [CrossRef]
- Suárez-González, A.; López-Ardao, J.C.; López-García, C.; Fernández-Veiga, M.; Rodríguez-Rubio, R.F.; Sousa-Vieira, M.E. A New Heavy-Tailed Discrete Distribution for LRD M/G/∞ Sample Generation. Perform. Eval. 2002, 47, 197–219. [Google Scholar] [CrossRef]
- Hurst, H.E. Long-Term Storage Capacity of Reservoirs. Trans. Am. Soc. Civ. Eng. 1951, 116, 770–799. [Google Scholar] [CrossRef]
- Sousa-Vieira, M.E.; Suárez-González, A.; López-García, C.; Fernández-Veiga, M.; López-Ardao, J.C.; Rodríguez-Rubio, R.F. Fast Simulation of Self-Similar and Correlated Processes. Math. Comput. Simul. 2010, 80, 2040–2061. [Google Scholar] [CrossRef]
- Mao, Y.; Dizdar, O.; Clerckx, B.; Schober, R.; Popovski, P.; Vincent, H. Rate-Splitting Multiple Access: Fundamentals, Survey, and Future Research Trends. IEEE Commun. Surv. Tutor. 2022, 24, 2073–2126. [Google Scholar] [CrossRef]




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sousa-Vieira, M.E.; Fernández-Veiga, M. Study of Coded ALOHA with Multi-User Detection under Heavy-Tailed and Correlated Arrivals. Future Internet 2023, 15, 132. https://doi.org/10.3390/fi15040132
Sousa-Vieira ME, Fernández-Veiga M. Study of Coded ALOHA with Multi-User Detection under Heavy-Tailed and Correlated Arrivals. Future Internet. 2023; 15(4):132. https://doi.org/10.3390/fi15040132
Chicago/Turabian StyleSousa-Vieira, María E., and Manuel Fernández-Veiga. 2023. "Study of Coded ALOHA with Multi-User Detection under Heavy-Tailed and Correlated Arrivals" Future Internet 15, no. 4: 132. https://doi.org/10.3390/fi15040132
APA StyleSousa-Vieira, M. E., & Fernández-Veiga, M. (2023). Study of Coded ALOHA with Multi-User Detection under Heavy-Tailed and Correlated Arrivals. Future Internet, 15(4), 132. https://doi.org/10.3390/fi15040132






