Approaches and Challenges in Internet of Robotic Things
Abstract
:1. Introduction
- a.
- We present a novel taxonomy for Internet of robotic things strategies.
- b.
- We provide an in-depth study and analysis of several IoRT literature approaches and techniques.
- c.
- We briefly illustrate the security methods for IoRT.
- d.
- We highlight some open research problems, as well as futuristic scope, in this active field of research.
Organization of Paper
2. IoRT: An Overview
2.1. Definitions and Concept of IoRT
2.1.1. How Does Communication Take Place in IoRT?
2.1.2. How Does Robot-to-Human Communication Take Place?
2.1.3. Security Importance in Robot Communication
2.2. Abilities of IoRT
2.3. Evolution in IoRT
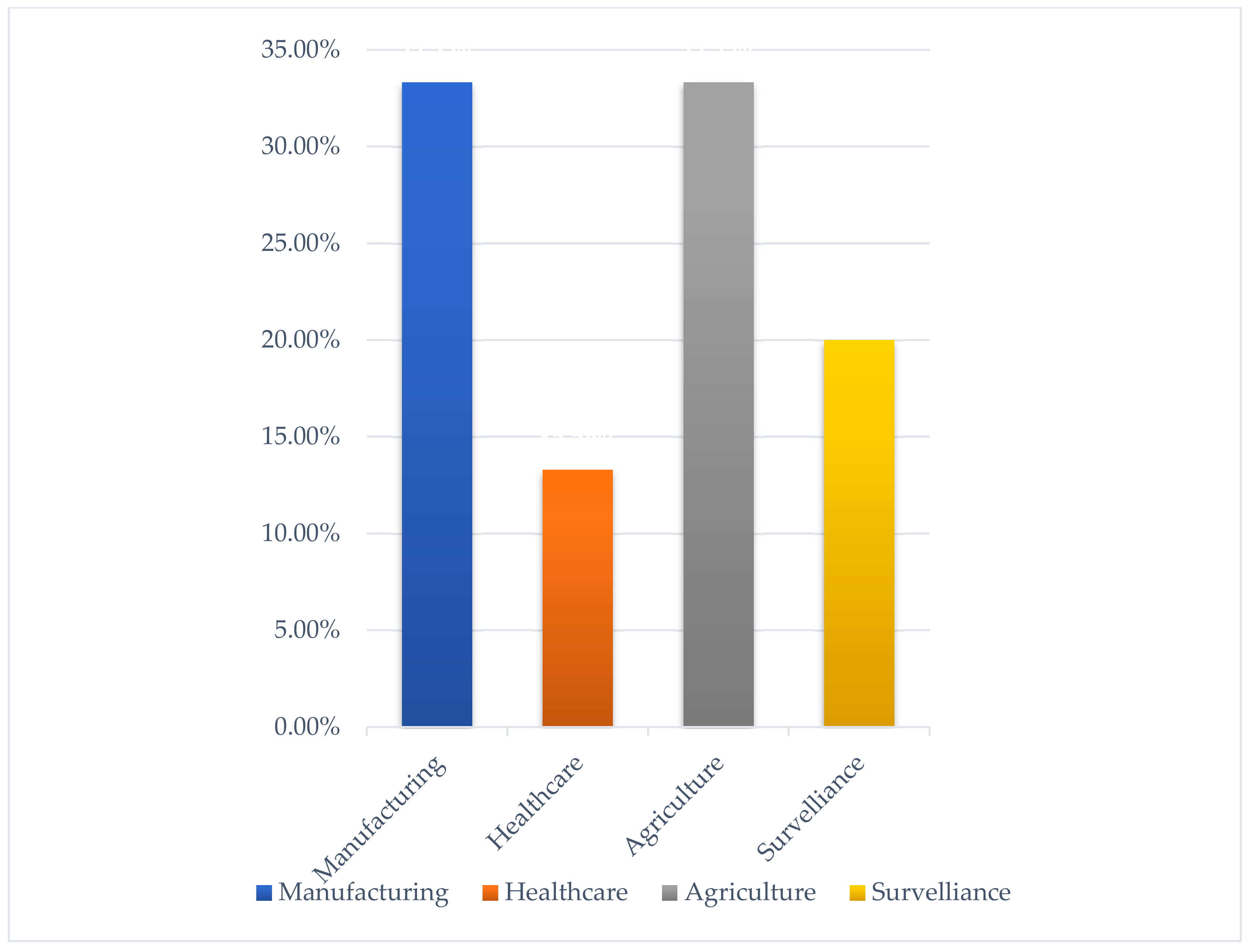
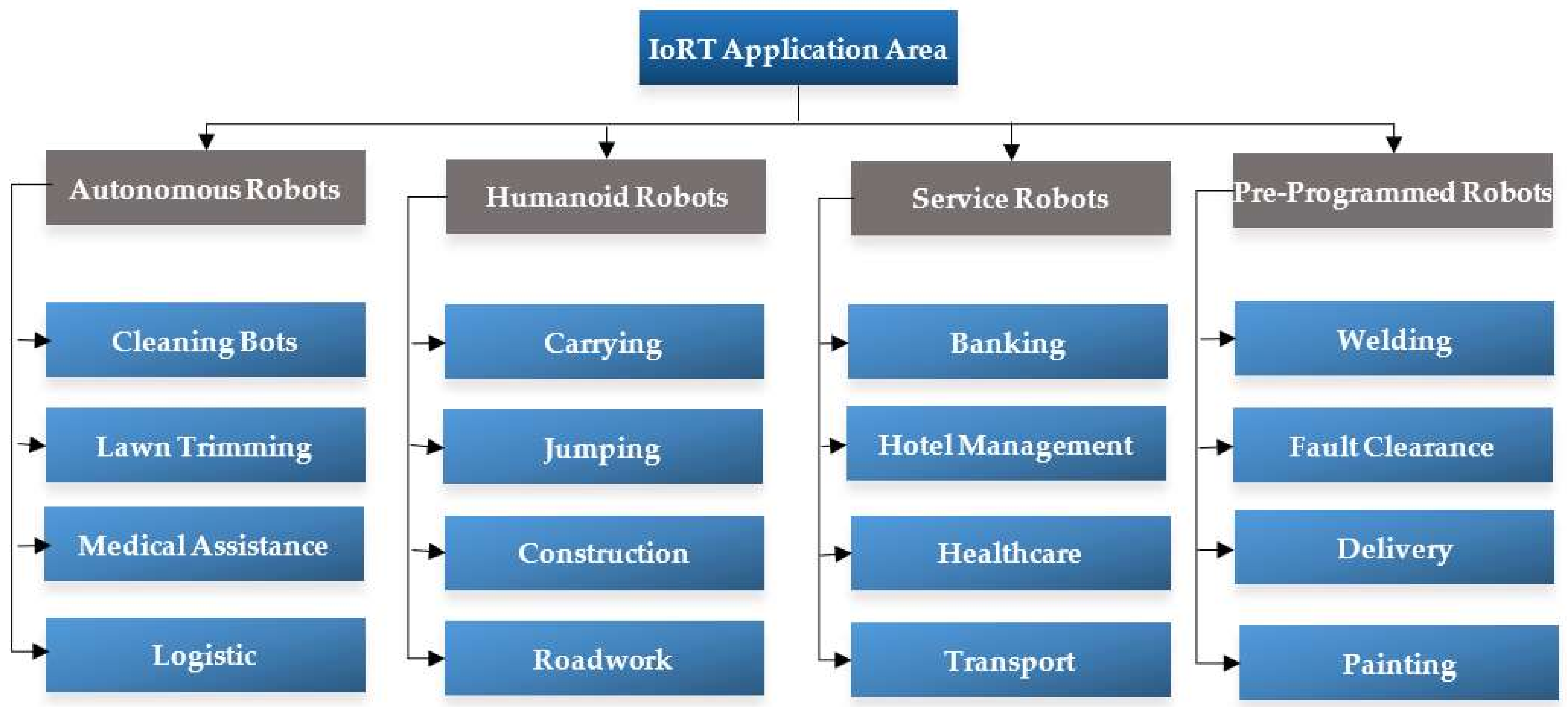
2.4. Applications of IoRT
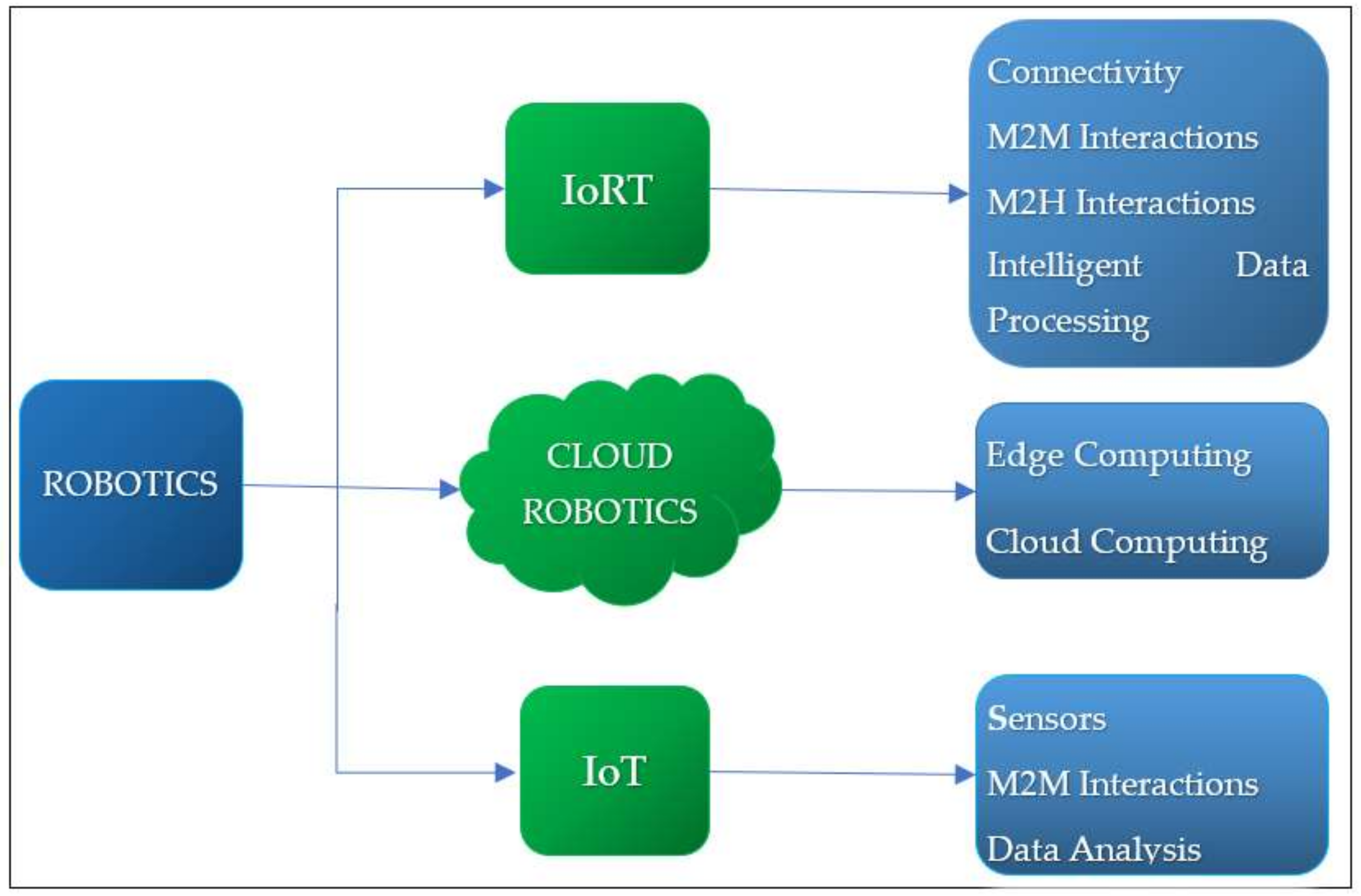
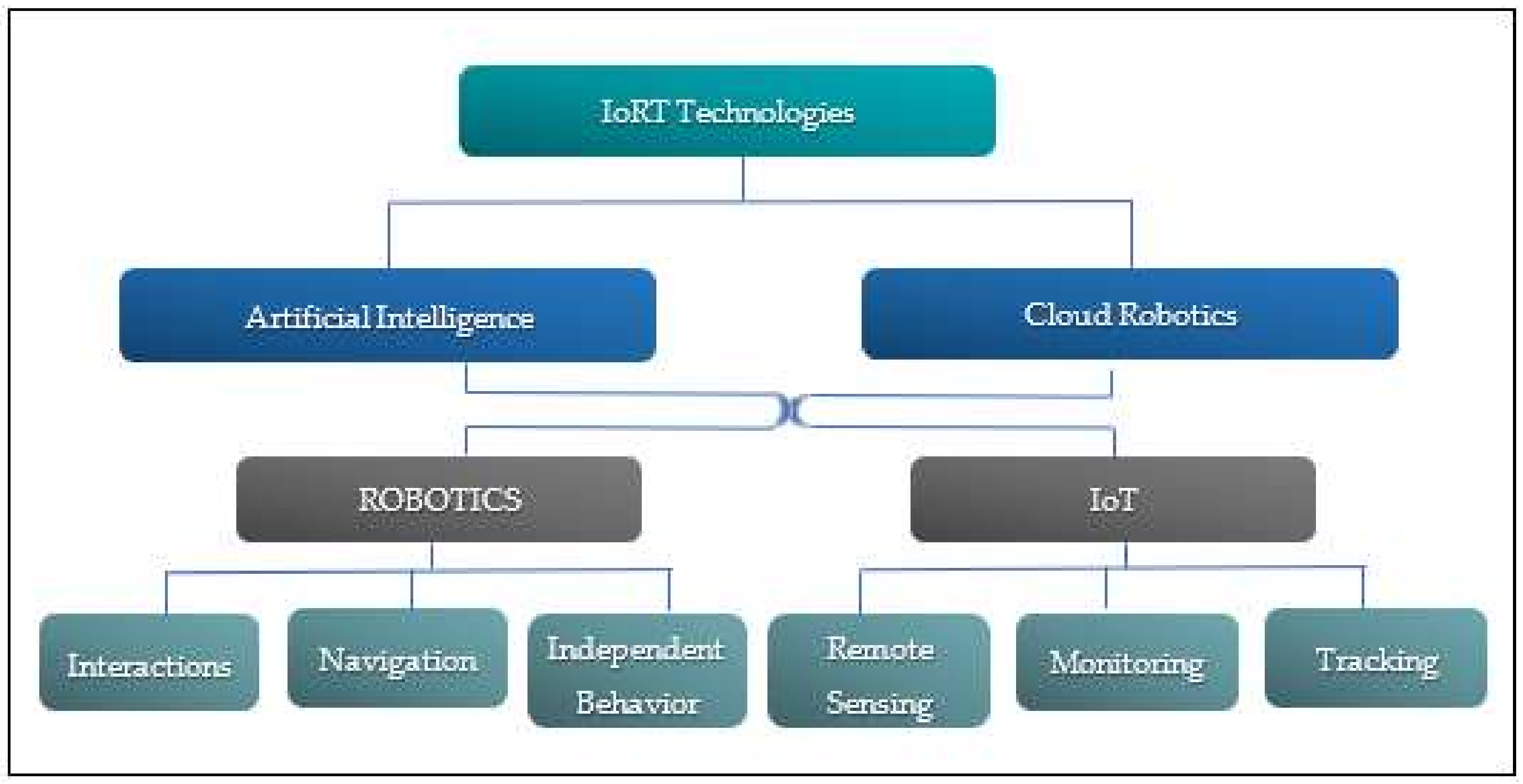
2.5. Robotic and IoRT Enabling Technologies
2.5.1. Robotic Technologies
2.5.2. IoRT Enabling Technologies
| Technologies | Author | Domain | Findings |
|---|---|---|---|
| IoT/IIoT, autonomous robotic system, intelligent connectivity, AI, DL, ML, swarm technology, and VR and AR | Versemen et al. [4] | IoRT—intelligent connectivity and frameworks |
|
| Voice recognition and voice control, ML, and security framework | Khalid et al. [3] | IoRT—detailed review |
|
| Architecture and network framework, multi-robotic system, computing (edge, fog, cloud), and security | Ilya et al. [46] | IoRT—analysis |
|
2.6. IoRT Architectures
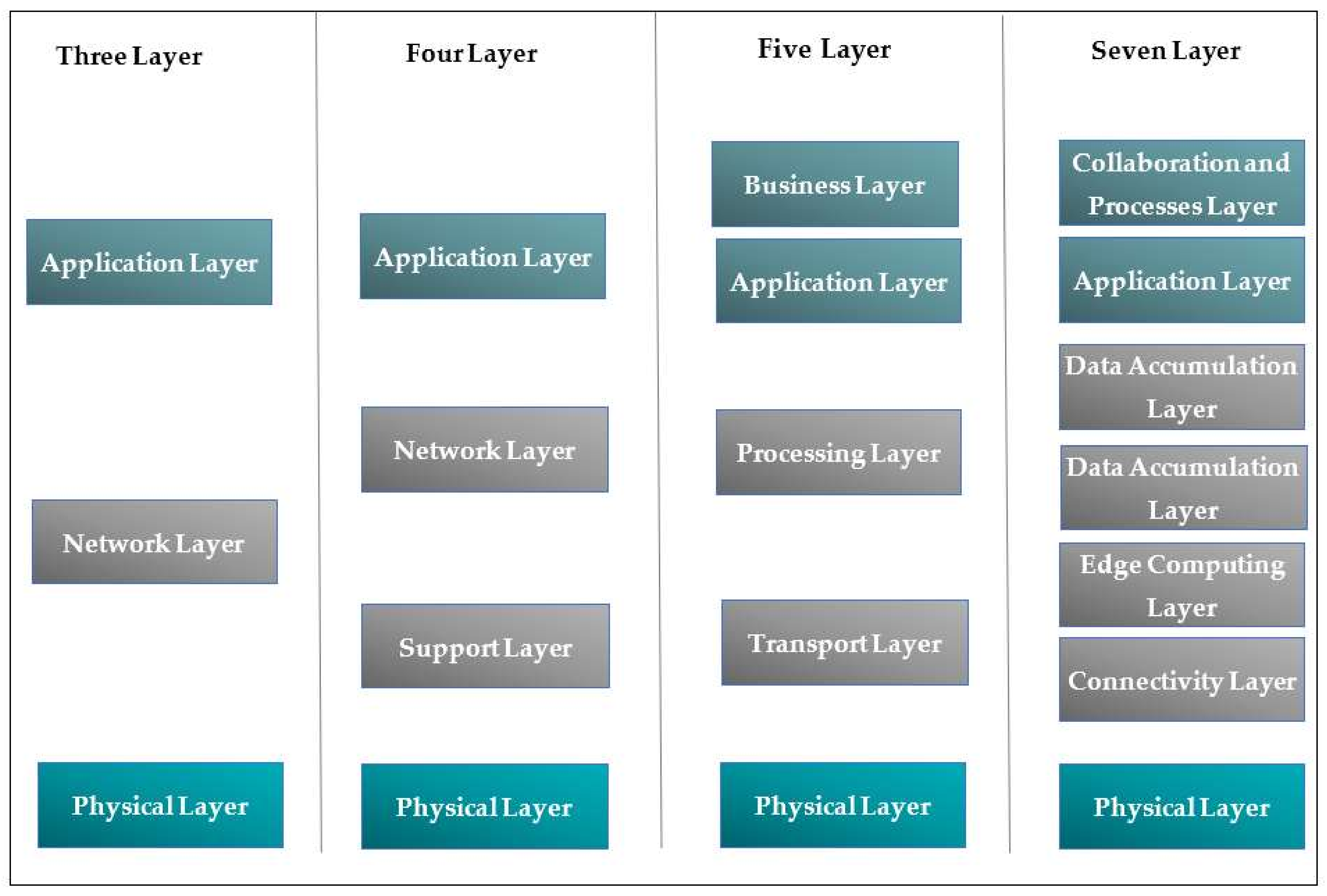
2.6.1. Three-Tier Architecture
2.6.2. Four-Tier Architecture
2.6.3. Five-Tier Architecture
2.6.4. Seven-Layer Architecture
3. Related Work
3.1. IoRT: An Outline
3.2. Secure Communication Mechanisms for IoRT
- Trust-based mechanisms,
- Encryption-based mechanisms.
3.2.1. Trust-Based Mechanisms for Robotic Devices
3.2.2. Encryption-Based Mechanism
3.3. Robot Navigation Techniques
- Robot navigation using fuzzy logic
- Robot navigation using probabilistic roadmap algorithm
- a.
- Creating a map of the neighboring world,
- b.
- Storing the map in an intelligible form,
- c.
- Selecting a suitable path from start to finish on the preserved map,
- d.
- Ultimately navigating the robot on the detected path.
- Robot navigation using laser scan matching algorithm
- Robot navigation using heuristic functions
- Robot navigation using bumper event
- Vision-based navigation
3.4. Remote Server Access in IoRT
- 1
- Record the service profile on a cloud server,
- 2
- Request to ASP server for the service package,
- 3
- Send service package using ASP server,
- 4
- Control function codes using the data core network,
- 5
- Update function codes.
4. IoRT Security
- a.
- Packet dropping or modification attacks—black hole and gray hole,
- b.
- Wormhole attack,
- c.
- Sybil attacks,
- d.
- Newcomer attacks,
- e.
- Badmouthing attacks,
- f.
- On–off attacks,
- g.
- Collusion attacks.
- a.
- Uncovering the illegitimate mastermind in the organization,
- b.
- Figuring out the breaking-in method,
- c.
- Choosing the priority method,
- d.
- Portraying the countermeasures,
- e.
- Implementing the solution and testing it.
- i.
- ARMbed for ARM to develop IoT products,
- ii.
- Brillo and Weave connectivity for IoT/IoRT devices by Google,
- iii.
- Homekit by Apple,
- iv.
- Kura Eclipse offersing application program interface access to hardware interfaces of IoT/IoRT ports,
- v.
- Secure operations for robotic automation by BILA.
| Security Techniques | Author | Domain | Description |
|---|---|---|---|
| Secure IoRT network for data transmission | Khalid et al. [3] | IoRT—analysis | The paper mentions the security challenges and the reasons for data breaches |
| Integrity, trust, and confidentiality of secure data. | Ray et al. [1] | IoRT—architecture, technologies | The author discusses the security issues, the trustworthy IoRT VM, and the idea of the protection of secure data. |
| IoT protocols | Neerendra et al. [59] | Modern communication protocols for IoT | On the basis of six key factors of protocols, IoT protocols are analyzed and compared for optimal communication |
| Automated key update mechanism for M2M communication, preshared key | Tsai et al. [53] | IoT security enhancement | This paper focuses on a technique for increasing security performance for IoT devices in M2M communication |
| Privacy filter framework, probabilistic model | Zahir et al. [7] | IoRT—applications | A privacy filter framework is designed for attacks in IoRT-HRI applications |
| Mobile phone security | Liao et al. [86] | Mobile computing used to evaluate IoT device security | The author discusses the security, accuracy, and limitations of IoT devices and mobile phones |
| Software-defined network | Waseem et al. [77] | IoT security requirements, challenges | This paper mentions the security challenges, the threats of various layers of the IoT architecture, and approaches to network security |
| Three-way system authentication | Nida et al. [76] | Three-way security structure for cloud-based IoT network | This framework can offer the ability to register IoT devices using digital certificates and users on cloud servers |
| Cyber-security, encryption | Ilya et al. [46] | IoRT architecture analysis | The author draws attention to the authentication mechanism of data. |
| Blockchain, software-defined networking | Djamel et al. [87] | IoRT survey—securities, privacy, the blockchain | The effective mechanisms in IoT and the security issues surrounding the safety of systems |
| UML extension for IoT system security modeling | David et al. [88] | IoT security | According to the author, IoT security is a UML extension; to describe IoT systems, the extension attempts to encapsulate security knowledge |
| AI, DL algorithms, security | Hui-WU et al. [89] | IoT security—using AI | Different algorithms are employed in this study to improve secure networking |
| Intelligent community security system (ICSS) | Sathish et al. [90] | IoRT—security and privacy issues | The author discusses various ICSS and their subsystems |
| Security Services | Countermeasures |
|---|---|
| Authentication | Encryption, trusted server authentication |
| Authorization | Access controls are required |
| Data validation | Output encoding |
| User session management | Encrypted authentic cookies, secure sessions |
5. Open Research Challenges
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| Acronym | Description | Acronym | Description |
| IoRT | Internet of robotic things | AR | Augmented reality |
| IoT | Internet of things | VR | Virtual reality |
| AI | Artificial intelligence | BLE | Bluetooth Low Energy |
| ML | Machine learning | BGAN | Broadband global area network |
| VR | Voice recognition | 6LowPAN | Low-power wireless area network |
| DT | Distributed technologies | ROS | Robotic operating system |
| DLTs | Distributed ledger technologies | VC | Voice control |
| TCP | Transmission control protocol | LORA | Long-range transmission with low power |
| IP | Internet protocol | MQTT | Message Queueing Telemetry Transport |
| M2H | Machine to human | CoAP | Constrained Application Protocol |
| LAN | Local area network | XMPP | Extensible Messaging and Presence Protocol |
| M2M | Machine to machine | IPV6 | IP Version 6 |
| UDP | User datagram protocol | DTLS | Datagram Transport Layer Security |
| HRI | Human–robot interfaces | AMQP | Advanced Message Queuing Protocol |
| RoIS | Robotic interface services | LLAP | Live Long and Process |
| M2M2A | Machine to machine to actuator | DDS | Data Distribution Service |
| VANET | Vehicular ad hoc network | WSDL | Web Services Description Language |
| ORM | Online reputation management | ULP | Upper Layer Protocol |
| CIA | Confidentiality, integrity, availability | SNS | Simple Notification Service |
| API | Application programming interface | UNR-PF | Open Source of Cloud Robotics |
| ANN | Artificial neural networks | RSNP | Robot Service Network Protocol |
| VEC | Vehicular edge computing | ORiN | Standard Network Interface for Factor Automation |
| MEC | Mobile edge computing | RPL | Robot Programming Language |
| ASP | Active server pages | CORPL | Cobalt-RPL |
References
- Ray, P.P. Internet of Robotic Things: Concept, Technologies, and Challenges. IEEE Access 2017, 4, 9489–9500. [Google Scholar] [CrossRef]
- Simoens, P.; Dragone, M.; Saffiotti, A. The Internet of Robotic Things: A review of concept, added value and applications. Int. J. Adv. Robot. Syst. 2018, 15, 1729881418759424. [Google Scholar] [CrossRef]
- Khalid, S. Internet of Robotic Things: A Review. J. Appl. Sci. Technol. Trends 2021, 2, 78–90. [Google Scholar] [CrossRef]
- Vermesan, O.; Bahr, R.; Ottella, M.; Serrano, M.; Karlsen, T.; Wahlstrøm, T.; Sand, H.E.; Ashwathnarayan, M. Internet of Robotic Things Intelligent Connectivity and Platforms. Front. Robot. AI 2020, 7, 104. [Google Scholar] [CrossRef]
- Vandewinckele, L.; Claessens, M.; Dinkla, A.; Brouwer, C.; Crijns, W.; Verellen, D.; Elmpt, W. Van Overview of artificial intelligence-based applications in radiotherapy: Recommendations for implementation and quality assurance. Radiother. Oncol. 2020, 153, 55–66. [Google Scholar] [CrossRef]
- Nayyar, A. Internet of Robotic Things: Driving Intelligent Robotics of Future—Concept, Architecture, Applications and Technologies. In Proceedings of the 2018 4th International Conference on Computing Sciences (ICCS), Jalandhar, India, 30–31 August 2018; 2020; pp. 151–160. [Google Scholar] [CrossRef]
- Alsulaimawi, Z. A Privacy Filter Framework for Internet of Robotic Things Applications. In Proceedings of the 2020 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 21–21 May 2020; pp. 262–267, ISBN 9781479966646. [Google Scholar] [CrossRef]
- Yuan, B.; Lin, C.; Zhao, H.; Zou, D.; Yang, L.T. Secure Data Transportation with Software-defined Networking and k-n Secret Sharing for High-confidence IoT Services. IEEE Internet Things J. 2020, 7, 7967–7981. [Google Scholar] [CrossRef]
- Cao, Q.H.; Khan, I.; Farahbakhsh, R.; Madhusudan, G.; Lee, G.M.; Crespi, N. A Trust Model for Data Sharing in Smart Cities. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; ISBN 9781479966646. [Google Scholar]
- Yfantis, E.A.; Fayed, A. Authentication and secure robot communication. Int. J. Adv. Robot. Syst. 2014, 11, 10. [Google Scholar] [CrossRef]
- Romeo, L.; Petitti, A.; Marani, R.; Milella, A. Internet of Robotic Things in Smart Domains: Applications and Challenges. Sensors 2020, 20, 3355. [Google Scholar] [CrossRef]
- Goh, S. Three architectures for trusted data dissemination in edge computing. Data Knowl. Eng. 2006, 58, 381–409. [Google Scholar] [CrossRef]
- Pinto, S.; Pereira, J.; Cabral, J. IIoTEED: An Enhanced, Trusted Execution Environment for Industrial IoT Edge Devices. IEEE Internet Comput. 2017, 21, 40–47. [Google Scholar] [CrossRef]
- Khan, Z.A.; Herrmann, P.; Ullrich, J.; Voyiatzis, A.G. A trust-based resilient routing mechanism for the internet of things. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; Volume Part F1305. [Google Scholar] [CrossRef]
- Chahal, R.K.; Kumar, N.; Batra, S. Trust management in social Internet of Things: A taxonomy, open issues, and challenges. Comput. Commun. 2019, 150, 13–46. [Google Scholar] [CrossRef]
- Zhu, Y.; Sampath, R.Z.; Jennifer, R. Cabernet: Connectivity architecture for better network services Cabernet: Connectivity Architecture for Better Network Services. In Proceedings of the 2008 ACM CoNEXT Conference, Madrid, Spain, 9–12 December 2008. [Google Scholar] [CrossRef]
- Zhao, F.; Li, C.; Liu, C.F. A cloud computing security solution based on fully homomorphic encryption. In Proceedings of the 16th International Conference on Advanced Communication Technology, Pyeongchang, Korea, 16–19 February 2014; pp. 485–488. [Google Scholar] [CrossRef]
- Hemalatha, N.; Jenis, A.; Cecil Donald, A.; Arockiam, L. A Comparative Analysis of Encryption Techniques and Data Security Issues in Cloud Computing. Int. J. Comput. Appl. 2014, 96, 1–6. [Google Scholar] [CrossRef]
- Gulzar, M.; Abbas, G. Internet of Things Security: A Survey and Taxonomy. In Proceedings of the 2019 International Conference on Engineering and Emerging Technologies (ICEET), Lahore, Pakistan, 21–22 February 2019; pp. 1–6. [Google Scholar]
- Kumar, N.; Chaudhary, P. Performance evaluation of encryption/decryption mechanisms to enhance data security. Indian J. Sci. Technol. 2016, 9, 1–10. [Google Scholar] [CrossRef]
- Alqahtani, A.; Li, Y.; Patel, P.; Solaiman, E.; Ranjan, R. End-to-End Service level Agreement Specification for IoT Applications. In Proceedings of the 2018 International Conference on High Performance Computing & Simulation (HPCS), Orleans, France, 16–20 July 2018. [Google Scholar] [CrossRef]
- Wu, H.; Han, H.; Wang, X.; Sun, S. Research on Artificial Intelligence Enhancing Internet of Things Security: A Survey. IEEE Access 2020, 8, 153826–153848. [Google Scholar] [CrossRef]
- Abbasi, M.H. Deep Visual Privacy Preserving for Internet of Robotic Things. In Proceedings of the 2019 5th Conference on Knowledge Based Engineering and Innovation (KBEI), Tehran, Iran, 28 February–1 March 2019; pp. 292–296. [Google Scholar]
- Su, J. Authentication and Encryption for a Robotic Ad Hoc Network using Identity-Based Cryptography. In Proceedings of the 2018 4th International Conference on Big Data Innovations and Applications (Innovate-Data), Barcelona, Spain, 6–8 August 2018. [Google Scholar] [CrossRef]
- Kumar, N.; Jamwal, P. Analysis of Modern Communication Protocols for IoT applications. Karbala International Journal of Modern Science 2021, 7, 390–404. [Google Scholar] [CrossRef]
- Zhong, C.; Zhu, Z.; Huang, R. Study on the IOT Architecture and Access Technology. In Proceedings of the 2017 16th International Symposium on Distributed Computing and Applications to Business, Engineering and Science (DCABES), Anyang, China, 13–16 October 2017. [Google Scholar] [CrossRef]
- Li, Y.; Tan, D.; Wu, Z.; Zhong, H.; Zu, D. Dynamic stability analyses based on ZMP of a wheel-based humanoid robot. In Proceedings of the 2006 IEEE International Conference on Robotics and Biomimetics, Kunming, China, 17–20 December 2006; pp. 1565–1570. [Google Scholar] [CrossRef]
- Yanjie, L.; Zhenwei, W.; Hua, Z. The dynamic stability criterion of the wheel-based humanoid robot based on ZMP modeling. In Proceedings of the 2009 Chinese Control and Decision Conference, Guilin, China, 17–19 June 2009; pp. 2349–2352. [Google Scholar] [CrossRef]
- URL-Robot Motion. Available online: https://scaron.info/robot-locomotion/equations-of-motion.html (accessed on 2 May 2022).
- Rostami, M.; Koushanfar, F.; Karri, R. A primer on hardware security: Models, methods, and metrics. Proc. IEEE 2014, 102, 1283–1295. [Google Scholar] [CrossRef]
- Ariffin, I.M.; Rasidi, A.I.H.M.; Yussof, H.; Mohamed, Z.; Miskam, M.A.; Amin, A.T.M.; Omar, A.R. Sensor Based Mobile Navigation Using Humanoid Robot Nao. Procedia Comput. Sci. 2015, 76, 474–479. [Google Scholar] [CrossRef]
- Ariffin, I.M.; Baharuddin, A.; Atien, A.C.; Yussof, H. Real-Time Obstacle Avoidance for Humanoid-Controlled Mobile Platform Navigation. Procedia Comput. Sci. 2017, 105, 34–39. [Google Scholar] [CrossRef]
- Muzammal, S.M.; Murugesan, R.K.; Jhanjhi, N.Z. A Comprehensive Review on Secure Routing in Internet of Things: Mitigation Methods and Trust-Based Approaches. IEEE Internet Things J. 2021, 8, 4186–4210. [Google Scholar] [CrossRef]
- Munawar, A.; De Magistris, G.; Pham, T.H.; Kimura, D.; Tatsubori, M.; Moriyama, T.; Tachibana, R.; Booch, G. MaestROB: A Robotics Framework for Integrated Orchestration of Low-Level Control and High-Level Reasoning. In Proceedings of the 2018 IEEE International Conference on Robotics and Automation (ICRA), Brisbane, QLD, Australia, 21–25 May 2018; pp. 527–534. [Google Scholar] [CrossRef] [Green Version]
- Burghart, C.; Mikut, R.; Stiefelhagen, R.; Asfour, T.; Holzapfel, H.; Steinhaus, P.; Dillmann, R. A cognitive architecture for a humanoid robot: A first approach. In Proceedings of the 5th IEEE-RAS International Conference on Humanoid Robots, Tsukuba, Japan, 5 December 2005; pp. 357–362. [Google Scholar] [CrossRef]
- Pessoa, L. Do Intelligent Robots Need Emotion? Trends Cogn. Sci. 2017, 21, 817–819. [Google Scholar] [CrossRef]
- Zaraki, A.; Pieroni, M.; De Rossi, D.; Mazzei, D.; Garofalo, R.; Cominelli, L.; Dehkordi, M.B. Design and evaluation of a unique social perception system for human-robot interaction. IEEE Trans. Cogn. Dev. Syst. 2017, 9, 341–355. [Google Scholar] [CrossRef]
- Chen, F.; Cao, L.; Tian, M.; Du, G. Research and Improvement of Competitive Double Arm Wheeled Humanoid Robot. In Proceedings of the 2020 IEEE 3rd International Conference on Information Systems and Computer Aided Education (ICISCAE), Dalian, China, 27–29 September 2020; pp. 599–601. [Google Scholar] [CrossRef]
- Mordern Robotics. Available online: https://modernrobotics.northwestern.edu/nu-gm-book-resource/2-2-degrees-of-freedom-of-a-robot/ (accessed on 2 May 2022).
- Mohammadi, V.; Rahmani, A.M.; Darwesh, A.M.; Sahafi, A. Trust-based recommendation systems in Internet of Things: A systematic literature review. Hum. Cent. Comput. Inf. Sci. 2019, 9, 21. [Google Scholar] [CrossRef]
- Liu, R.; Yu, G.; Qu, F.; Zhang, Z. Device-to-Device Communications in Unlicensed Spectrum: Mode Selection and Resource Allocation. IEEE Access 2016, 4, 4720–4729. [Google Scholar] [CrossRef]
- Razafimandimby, C.; Loscri, V.; Vegni, A.M. A neural network and IoT based scheme for performance assessment in Internet of Robotic Things. In Proceedings of the 2016 IEEE first international conference on internet-of-things design and implementation (IoTDI), Berlin, Germany, 4–8 April 2016. [Google Scholar] [CrossRef]
- Möller, R.; Furnari, A.; Battiato, S.; Härmä, A.; Farinella, G.M. A survey on human-aware robot navigation. Rob. Auton. Syst. 2021, 145, 103837. [Google Scholar] [CrossRef]
- Kim, D.; Kim, S.; Park, J.H. Remote Software Update in Trusted Connection of Long Range IoT Networking Integrated with Mobile Edge Cloud. IEEE Access 2018, 6, 66831–66840. [Google Scholar] [CrossRef]
- Zhu, C.; Rodrigues, J.J.P.C.; Leung, V.C.M.; Shu, L.; Yang, L.T. Trust-based communication for the industrial internet of things. IEEE Commun. Mag. 2018, 56, 16–22. [Google Scholar] [CrossRef]
- Afanasyev, I.; Mazzara, M.; Chakraborty, S.; Zhuchkov, N.; Maksatbek, A.; Yesildirek, A.; Kassab, M.; Distefano, S. Towards the Internet of Robotic Things: Analysis, Architecture, Components and Challenges. In Proceedings of the 2019 12th International Conference on Developments in eSystems Engineering (DeSE), Kazan, Russia, 7–10 October 2019; pp. 3–8. [Google Scholar] [CrossRef]
- Rana, B. A systematic survey on internet of things: Energy efficiency and interoperability perspective. Trans. Emerg. Telecommun. Technol. 2020, 32, e4166. [Google Scholar] [CrossRef]
- Kumar, J.S. A Survey on Internet of Things: Security and Privacy Issues. Int. J. Comput. Appl. 2014, 90, 20–26. [Google Scholar]
- Mukherjee, A. Physical-Layer Security in the Internet of Things: Sensing and Communication Confidentiality Under Resource Constraints. Proc. IEEE 2015, 103, 1747–1761. [Google Scholar] [CrossRef]
- Dizdarević, J.; Carpio, F.; Jukan, A.; Masip-Bruin, X. A survey of communication protocols for internet of things and related challenges of fog and cloud computing integration. ACM Comput. Surv. 2019, 51, 1–29. [Google Scholar] [CrossRef]
- Jeong, J.; Yang, J.; Baltes, J. Robot magic show as testbed for humanoid robot interaction. Entertain. Comput. 2022, 40, 100456. [Google Scholar] [CrossRef]
- Althumali, H.; Othman, M.; Member, S. A Survey of Random Access Control Techniques for Machine-to-Machine Communications in LTE/LTE-A Networks. IEEE Access 2018, 6, 74961–74983. [Google Scholar] [CrossRef]
- Tsai, W.; Wang, T. An Automatic Key-update Mechanism for M2M Communication and IoT Security Enhancement. In Proceedings of the 2020 IEEE International Conference on Smart Internet of Things (SmartIoT), Beijing, China, 14–16 August 2020; pp. 354–355. [Google Scholar] [CrossRef]
- Batet, M.; Gibert, K.; Valls, A. The data abstraction layer as knowledge provider for a medical multi-agent system. In AIME Workshop on Knowledge Management for Health Care Procedures; Springer: Berlin/Heidelberg, Germany, 2007; pp. 87–100. [Google Scholar] [CrossRef]
- Hendrich, N.; Bistry, H.; Zhang, J. Architecture and Software Design for a Service Robot in an Elderly-Care Scenario. Engineering 2015, 1, 27–35. [Google Scholar] [CrossRef]
- Ankele, R.; Marksteiner, S.; Nahrgang, K. Requirements and Recommendations for IoT/IIoT Models to automate Security Assurance through Threat Modelling, Security Analysis and Penetration Testing. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019. [Google Scholar]
- Kumar, N.; Vámossy, Z.; Szabó-Resch, Z.M. Robot Path Pursuit Using Probabilistic Roadmap. In Proceedings of the 2016 IEEE 17th International Symposium on Computational Intelligence and Informatics (CINTI), Budapest, Hungary, 17–19 November 2016; pp. 139–144. [Google Scholar]
- Kumar, N.; Vámossy, Z.; Szabó-Resch, Z.M. Robot Obstacle Avoidance Using Bumper Event. In Proceedings of the 2016 IEEE 11th International Symposium on Applied Computational Intelligence and Informatics (SACI), Timisoara, Romania, 12–14 May 2016; pp. 485–490. [Google Scholar]
- Kishi, T.; Shimomura, S.; Futaki, H.; Yanagino, H.; Yahara, M.; Cosentino, S.; Nozawa, T.; Hashimoto, K.; Takanishi, A. Development of a Humorous Humanoid Robot Capable of Quick-and-Wide Arm Motion. IEEE Robot. Autom. Lett. 2016, 1, 1081–1088. [Google Scholar] [CrossRef]
- Ravankar, A.; Ravankar, A.A.; Kobayashi, Y.; Hoshino, Y.; Peng, C.C. Path smoothing techniques in robot navigation: State-of-the-art, current and future challenges. Sensors 2018, 18, 3170. [Google Scholar] [CrossRef]
- Kumar, N.; Takács, M.; Vámossy, Z. Robot Navigation in Unknown Environment using Fuzzy Logic. In Proceedings of the 2017 IEEE 15th International Symposium on Applied Machine Intelligence and Informatics (SAMI), Herl’any, Slovakia, 26–28 January 2017; pp. 279–284. [Google Scholar]
- Rath, A.K.; Parhi, D.R.; Das, H.C.; Muni, M.K.; Kumar, P.B. Analysis and use of fuzzy intelligent technique for navigation of humanoid robot in obstacle prone zone. Def. Technol. 2018, 14, 677–682. [Google Scholar] [CrossRef]
- Muni, M.K.; Parhi, D.R.; Kumar, P.B.; Sahu, C.; Kumar, S. Towards motion planning of humanoids using a fuzzy embedded neural network approach. Appl. Soft Comput. 2022, 119, 108588. [Google Scholar] [CrossRef]
- Kashyap, A.K.; Parhi, D.R.; Pandey, A. Multi-objective optimization technique for trajectory planning of multi-humanoid robots in cluttered terrain. ISA Trans. 2021, 125, 591–613. [Google Scholar] [CrossRef]
- Kumar, N.; Vámossy, Z. Laser Scan Matching in Robot Navigation. In Proceedings of the 2018 IEEE 12th International Symposium on Applied Computational Intelligence and Informatics (SACI), Timisoara, Romania, 17–19 May 2018; pp. 241–246. [Google Scholar]
- Kastner, L.; Lambrecht, J. Augmented-Reality-Based Visualization of Navigation Data of Mobile Robots on the Microsoft Hololens—Possibilities and Limitations. In Proceedings of the 2019 IEEE International Conference on Cybernetics and Intelligent Systems (CIS) and IEEE Conference on Robotics, Automation and Mechatronics (RAM), Bangkok, Thailand, 18–20 November 2019; pp. 344–349. [Google Scholar] [CrossRef]
- Oh, H.S.; Lee, C.W.; Mitsuru, I. Navigation control of a mobile robot based on active vision. In Proceedings of the IECON’91: 1991 International Conference on Industrial Electronics, Control and Instrumentation, Kobe, Japan, 28 October–1 November 1991; Volume 2, pp. 1122–1126. [Google Scholar] [CrossRef]
- Kumar, N.; Vámossy, Z.; Szabó-resch, Z.M. Heuristic Approaches in Robot Navigation. In Proceedings of the 2016 IEEE 20th Jubilee International Conference on Intelligent Engineering Systems (INES), Budapest, Hungary, 30 June–2 July 2016; pp. 219–222. [Google Scholar]
- Tang, L. Vision Based Navigation for Mobile Robots in Indoor Environment bly Teaching and Playing-back Scheme. In Proceedings of the 2001 ICRA, IEEE International Conference on Robotics and Automation, Seoul, Korea, 21–26 May 2001; pp. 3072–3077. [Google Scholar]
- Al-Mutib, K. Smart stereovision based gaze control for navigation in low-feature unknown indoor environments. In Proceedings of the 2014 5th International Conference on Intelligent Systems, Modelling and Simulation, Langkawi, Malaysia, 27–29 January 2014; 2015; Volume 2015, pp. 121–126. [Google Scholar] [CrossRef]
- Yoo, J.K.; Kim, J.H. Gaze Control-Based Navigation Architecture with a Situation-Specific Preference Approach for Humanoid Robots. IEEE/ASME Trans. Mechatron. 2015, 20, 2425–2436. [Google Scholar] [CrossRef]
- Adachi, Y.; Tsunenari, H.; Matsumoto, Y.; Ogasawara, T. Guide robot’s navigation based on attention estimation using gaze information. In Proceedings of the 2004 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Sendai, Japan, 28 September–2 October 2004; Volume 1, pp. 540–545. [Google Scholar] [CrossRef]
- Awan, K.A.; Ud, I.; Senior, D.I.N.; Almogren, A.; Member, S.; Fellow, M.G.; Khan, S. StabTrust—A Stable and Centralized Trust-based Clustering Mechanism for IoT enabled Vehicular Ad-hoc Networks. IEEE Access 2020, 8, 21159–21177. [Google Scholar] [CrossRef]
- Zeeshan, N.; Member, M.R. Three-way Security Framework for Cloud based IoT Network. In Proceedings of the 2019 International Conference on Computing, Electronics & Communications Engineering (iCCECE), London, UK, 22–23 August 2019; pp. 183–186. [Google Scholar]
- Iqbal, W.; Abbas, H.; Daneshmand, M.; Rauf, B.; Abbas, Y. An In-Depth Analysis of IoT Security Requirements, Challenges and their Countermeasures via Software Defined Security. IEEE Internet Things J. 2020, 7, 10250–10276. [Google Scholar] [CrossRef]
- Wu, A.; Guo, J.; Yang, P. Research on Data Sharing Architecture for Ecological Monitoring Using Iot Streaming Data. IEEE Access 2020, 8, 195385–195397. [Google Scholar] [CrossRef]
- Rostami, M.; Koushanfar, F.; Rajendran, J.; Karri, R. Hardware security: Threat models and metrics. In Proceedings of the 2013 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, CA, USA, 18–21 November 2013; pp. 819–823. [Google Scholar] [CrossRef]
- Hussain, S.; Erwin, H.; Dunne, P. Threat modeling using Formal Methods: A New Approach to Develop Secure Web Applications. In Proceedings of the 2011 7th International Conference on Emerging Technologies, Islamabad, Pakistan, 5–6 September 2011. [Google Scholar]
- Bradbury, M.; Jhumka, A.; Watson, T.I.M.; Burton, J.; Butler, M.; Data, M.M. Threat-modeling-guided Trust-based Task Offloading for Resource-constrained Internet of Things. ACM Trans. Sens. Netw. 2022, 18, 1–41. [Google Scholar] [CrossRef]
- Maciel, R.; Araujo, J.; Dantas, J.; Melo, C.; Guedes, E.; Maciel, P. Impact of a DDoS Attack on Computer Systems: An Approach Based on an Attack Tree Model. In Proceedings of the 2018 Annual IEEE International Systems Conference (SysCon), Vancouver, BC, Canada, 23–26 April 2018. [Google Scholar]
- Fei, Y.; Ning, J.; Jiang, W. A quantifiable Attack-Defense Trees model for APT attack. In Proceedings of the 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 12–14 October 2018; pp. 2303–2306. [Google Scholar] [CrossRef]
- Trček, D. A formal apparatus for modeling trust in computing environments. Math. Comput. Model. 2009, 49, 226–233. [Google Scholar] [CrossRef]
- Liao, B.I.N.; Ali, Y.; Nazir, S. Security Analysis of IoT Devices by Using Mobile Computing: A Systematic Literature Review. IEEE Access 2020, 8, 120331–120350. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H.P.T. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef]
- Robles-Ramirez, D.A.; Escamilla, P.J.; Tryfonas, T. IoTsec: UML extension for Internet of things systems security modelling. In Proceedings of the 2017 International Conference on Mechatronics, Electronics and Automotive Engineering (ICMEAE), Cuernavaca, Mexico, 21–24 November 2017. [Google Scholar] [CrossRef]
- Huang, X.; Yu, R.; Kang, J. Distributed Reputation Management for Secure and Efficient Vehicular Edge Computing and Networks. IEEE Access 2017, 5, 25408–25420. [Google Scholar] [CrossRef]
- Tandon, A.; Srivastava, P. Trust-based Enhanced Secure Routing against Rank and Sybil Attacks in IoT. In Proceedings of the 2019 Twelfth International Conference on Contemporary Computing (IC3), Noida, India, 8–10 August 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Nagarajan, U.; Kantor, G.; Hollis, R. The ballbot: An omnidirectional balancing mobile robot. Int. J. Rob. Res. 2014, 33, 917–930. [Google Scholar] [CrossRef]
- Gurunath, R.; Agarwal, M.; Nandi, A.; Samanta, D. An Overview: Security Issue in IoT Network. In Proceedings of the 2018 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 30–31 August 2018; pp. 1–4. [Google Scholar]
- Shiomi, M.; Shatani, K.; Minato, T.; Ishiguro, H. How Should a Robot React before People’s Touch?: Modeling a Pre-Touch Reaction Distance for a Robot’s Face. IEEE Robot. Autom. Lett. 2018, 3, 3773–3780. [Google Scholar] [CrossRef]
- Aucouturier, J.-J. Cheek to Chip: Dancing Robots and AI’s Future. IEEE Intell. Syst. 2008, 23, 74–84. [Google Scholar] [CrossRef]
- Velásquez, J.D. When robots weep: Emotional memories and decision-making. In Proceedings of the Fifteenth National Conference on Artificial Intelligence (AAAI-98); The AAAI Press: Menlo Park, CA, USA, 1998; pp. 70–75. Available online: https://www.aaai.org/Papers/AAAI/1998/AAAI98-010.pdf (accessed on 2 May 2022).
- Dorner, D.; Hille, K. Artificial Souls: & Motivated Emotional Robots. In Proceedings of the 1995 IEEE International Conference on Systems, Man and Cybernetics. Intelligent Systems for the 21st Century, Vancouver, BC, Canada, 22–25 October 1995; pp. 3828–3832. [Google Scholar]
- Hornung, A.; Wurm, K.M.; Bennewitz, M. Humanoid robot localization in complex indoor environments. In Proceedings of the 2010 IEEE/RSJ International Conference on Intelligent Robots and Systems, Taipei, Taiwan, 18–22 October 2010; pp. 1690–1695. [Google Scholar] [CrossRef]
- Taylor, C.; Ward, C.; Sofge, D.; Lofaro, D.M. LPS: A Local Positioning System for Homogeneous and Heterogeneous Robot-Robot Teams, Robot-Human Teams, and Swarms. In Proceedings of the LPS: A Local Positioning System for Homogeneous and Heterogeneous Robot-Robot Teams, Robot-Human Teams, and Swarms, Jeju, Korea, 24–27 June 2019; pp. 200–207. [Google Scholar] [CrossRef]
- Huang, K.; Xian, Y.; Zhen, S.; Sun, H. Robust control design for a planar humanoid robot arm with high strength composite gear and experimental validation. Mech. Syst. Signal Process. 2021, 155, 107442. [Google Scholar] [CrossRef]





| Multidisciplinary Attributes | Evolution In Multidisciplinary Nature of IoRT |
|---|---|
| Think | Computing, cognition, connectivity, and control |
| Connect | Connectivity in robotic things and the environment |
| Locate | High-definition dynamic maps, GPS, GNSS, and location of networks |
| Learn | AI algorithms are used for learning robotic things |
| Sense | Collection and processing of data streams from the perception domain radars, LIDARs, cameras, and ultrasound sensors |
| Collaborate | Activities with their robotic things, autonomous vehicles, edge cloud, etc. |
| Act | Acting, speed, and stopping |
| Type | Description |
|---|---|
| Cloud robotics | Robots + cloud infrastructure |
| Collaborative robotics | Robot–human collaboration |
| Cognitive robotics | Robots use AI algorithms to learn and respond the complex tasks |
| Fog robotics | Robots use fog computing to process data and services |
| Network robotics | To complete a task, multiple robots collaborate and coordinate through networked communication |
| Smart robotics | AI + robots + ML + DL + cloud computing |
| Swarm robotics | Multiple robotic systems with physical robots |
| Layers | Domain |
|---|---|
| Services and application layer | Smart environments Installation and execution of programs are carried out here by interconnected IoRT |
| Network and control layer | Routers, switches, local and cloud servers, and network and management protocols |
| Physical/hardware layer | Sensors, robots, actuators, robot-to-robot communication, and multi-robotic systems |
| Author | IoRT Domain | Architecture |
|---|---|---|
| Ray et al. [1] | IoRT—infrastructure | Five-layered |
| Khalid et al. [3] | IoRT—applications | Three-layered |
| Anand et al. [6] | Intelligent robotics | Five-layered |
| Ilya et al. [46] | IoRT—architecture and components | Three-layered |
| Rana et al. [47] | IoT—energy efficiency and interoperability | Three-, four-, five-, and seven-layered |
| Sathish et al. [48] | IoRT—security and privacy | Three-layered |
| Author | Paper Focus | Limitations | Future Task |
|---|---|---|---|
| Burghart et al. [35] | Cognitive framework for an intelligent humanoid robotic system | A multimodal fusion of speech and motions | Access to active models through tight integration |
| Nagarajan et al. [91] | Physical HRI mechanism | One-wheeled, continuous position displacements of ballbot | Laser range finders and stereo cameras are needed for accurate localization |
| Yoo et al. [51] | Gaze control-based localization for mobile robots | The main issue is how to transmit and display various types of data at the same time | The presented design can be expanded to deal with arbitrarily formed and equally sized objects traveling in peculiar ways |
| Ariffin et al. [32] | ACI used to build a humanoid-led navigation mobile platform within an obstacle in the surroundings by integrating exterior laser sensing with a humanoid | Security concerns | Path planning and trust-based mechanisms can be involved to overcome navigation and security issues |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sayeed, A.; Verma, C.; Kumar, N.; Koul, N.; Illés, Z. Approaches and Challenges in Internet of Robotic Things. Future Internet 2022, 14, 265. https://doi.org/10.3390/fi14090265
Sayeed A, Verma C, Kumar N, Koul N, Illés Z. Approaches and Challenges in Internet of Robotic Things. Future Internet. 2022; 14(9):265. https://doi.org/10.3390/fi14090265
Chicago/Turabian StyleSayeed, Aqsa, Chaman Verma, Neerendra Kumar, Neha Koul, and Zoltán Illés. 2022. "Approaches and Challenges in Internet of Robotic Things" Future Internet 14, no. 9: 265. https://doi.org/10.3390/fi14090265
APA StyleSayeed, A., Verma, C., Kumar, N., Koul, N., & Illés, Z. (2022). Approaches and Challenges in Internet of Robotic Things. Future Internet, 14(9), 265. https://doi.org/10.3390/fi14090265