Energy-Optimized Content Refreshing of Age-of-Information-Aware Edge Caches in IoT Systems
Abstract
:1. Introduction
- We define a model-driven optimization problem to set the sampling frequency of the IoT device, and the value of the refresh window of the cache so that the device power consumption is minimized, while the AoI requirement expressed by the IoT application is satisfied. The device power consumption depends on the energy consumed to transmit the messages and the energy consumed to sense the environment.
- We solve the optimization problem, and we provide an extensive numerical evaluation of our cache-management scheme, showing the trade-off between minimizing the energy consumed to transmit the messages and the energy consumed to sense the environment.
- We evaluate the performance of our cache-management scheme in a realistic environment based on an emulated IoT network using the OMA LightweightM2M ([12,13]) protocol for IoT device management. In the experiments, we consider a sample scenario composed of an LWM2M Server, i.e., the IoT application, an LWM2M Client, i.e., the IoT device, and an LWM2M Proxy located in between them. The LWM2M Proxy implements the proposed cache management scheme to improve system performance [11], and the refresh window of the cache is selected using the proposed optimized method. We show that the proposed method chooses a refresh window that minimizes the energy cost while satisfying the AoI requirement.
2. Related Work
3. System Overview and Model
- IoT Devices: they collect data or perform actuation, e.g., they are either sensors or actuators, and they have communication capabilities to submit the data to the broader IoT system through an access network.
- IoT Applications: they typically run in the cloud and play three main roles: (i) data acquisition, storage, and access, to support the generation of a huge amount of data from devices, which is then stored to be processed and analyzed; (ii) data analytics on the collected data, which are examined to detect valuable information to support, for example, decision making; (iii) actuation support. In addition, they support several administrative functions, such as device management, user-account management, etc.
- IoT Gateways/Proxies: they collect, process, and transfer data from devices to applications and deliver the actuation requests from applications to devices. They may also act as intermediaries between the devices and the applications, e.g., they may support data storage, service discovery, etc.
3.1. System-Model Overview
3.1.1. IoT Device
3.1.2. IoT Application
3.1.3. IoT Proxy
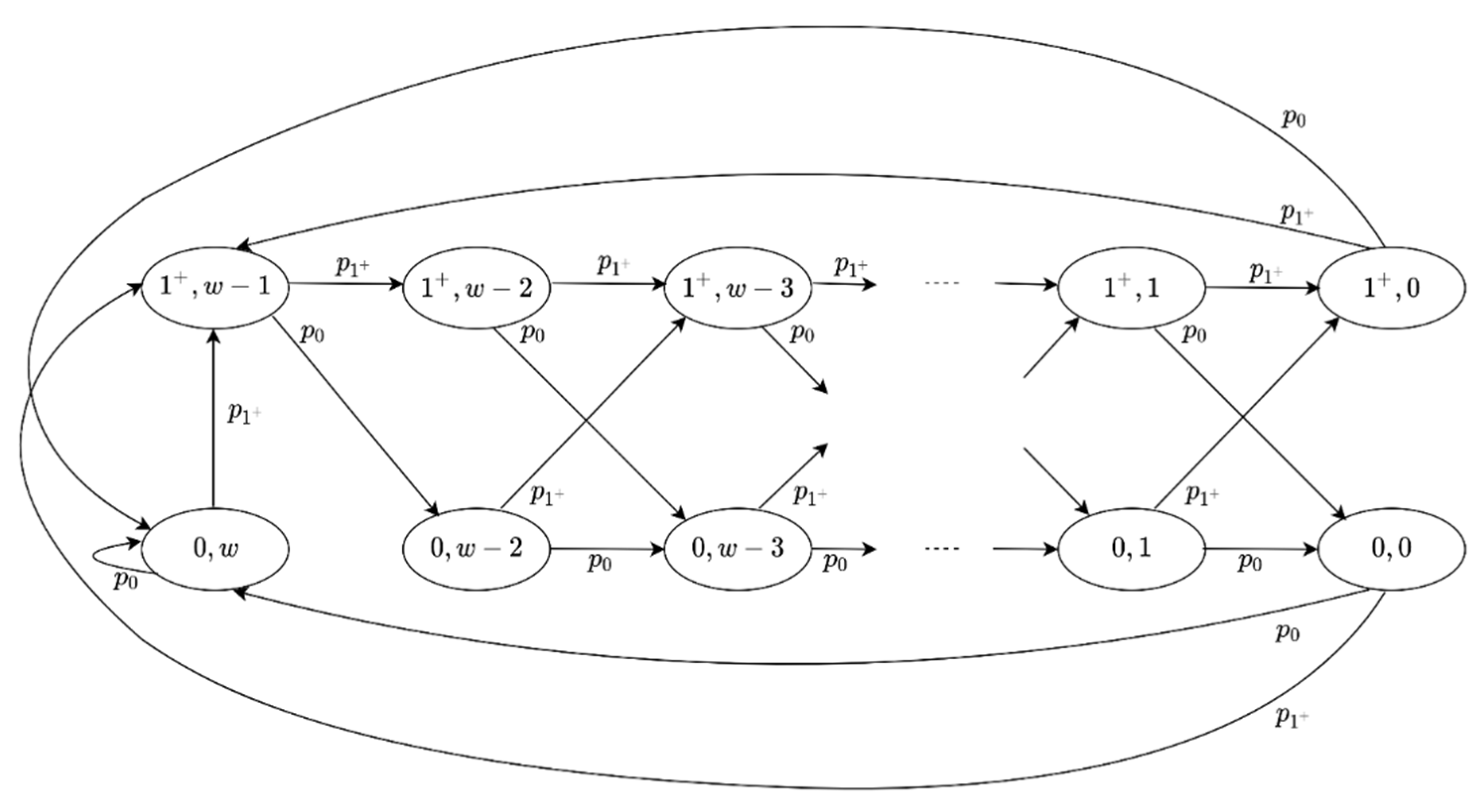
3.2. Model of the Cache-Management Scheme
- : no request arrived during the interval and there is not a fresh item in the cache. So, if a request arrives in the interval , the proxy fetches the latest update from the device, which will be cached and will expire in intervals.
- , : no request arrived in the interval , and the cached item will expire in intervals.
- , : at least one request arrived during the interval , and the cached item will expire in intervals.
3.2.1. Network Cost
3.2.2. Average AoI
3.2.3. Probability Distribution of AoI
3.3. Model of the Power Consumption
4. Model-Driven Cache-Management Optimization
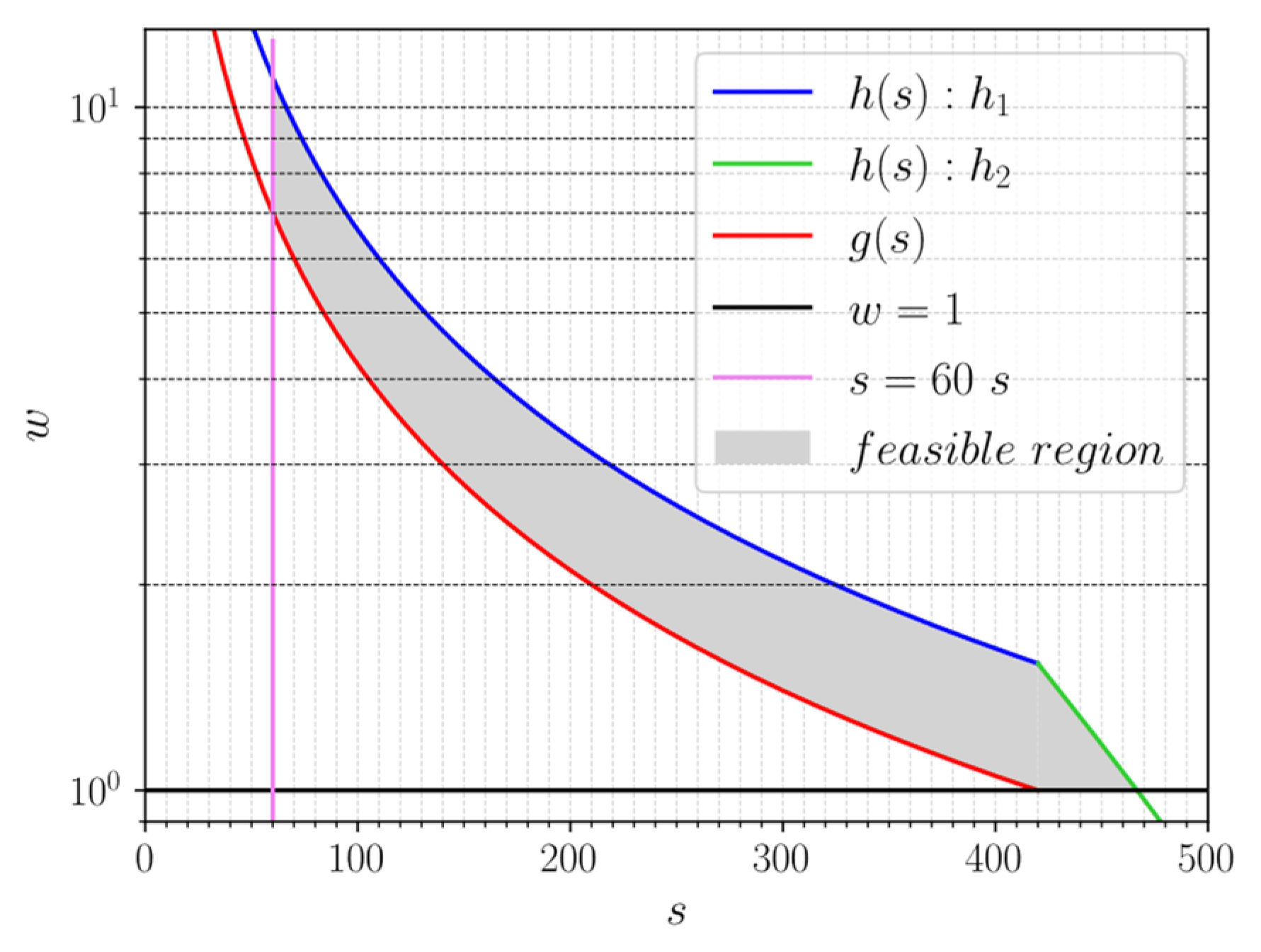
4.1. Energy-Optimized Cache Refresh
- If (i.e.,
- If (i.e., ):
4.1.1. Devices with Transmission Energy Consumption Equal to Zero:
4.1.2. Devices with Sampling Energy Consumption Equal to Zero:
4.1.3. Hybrid Sensors:
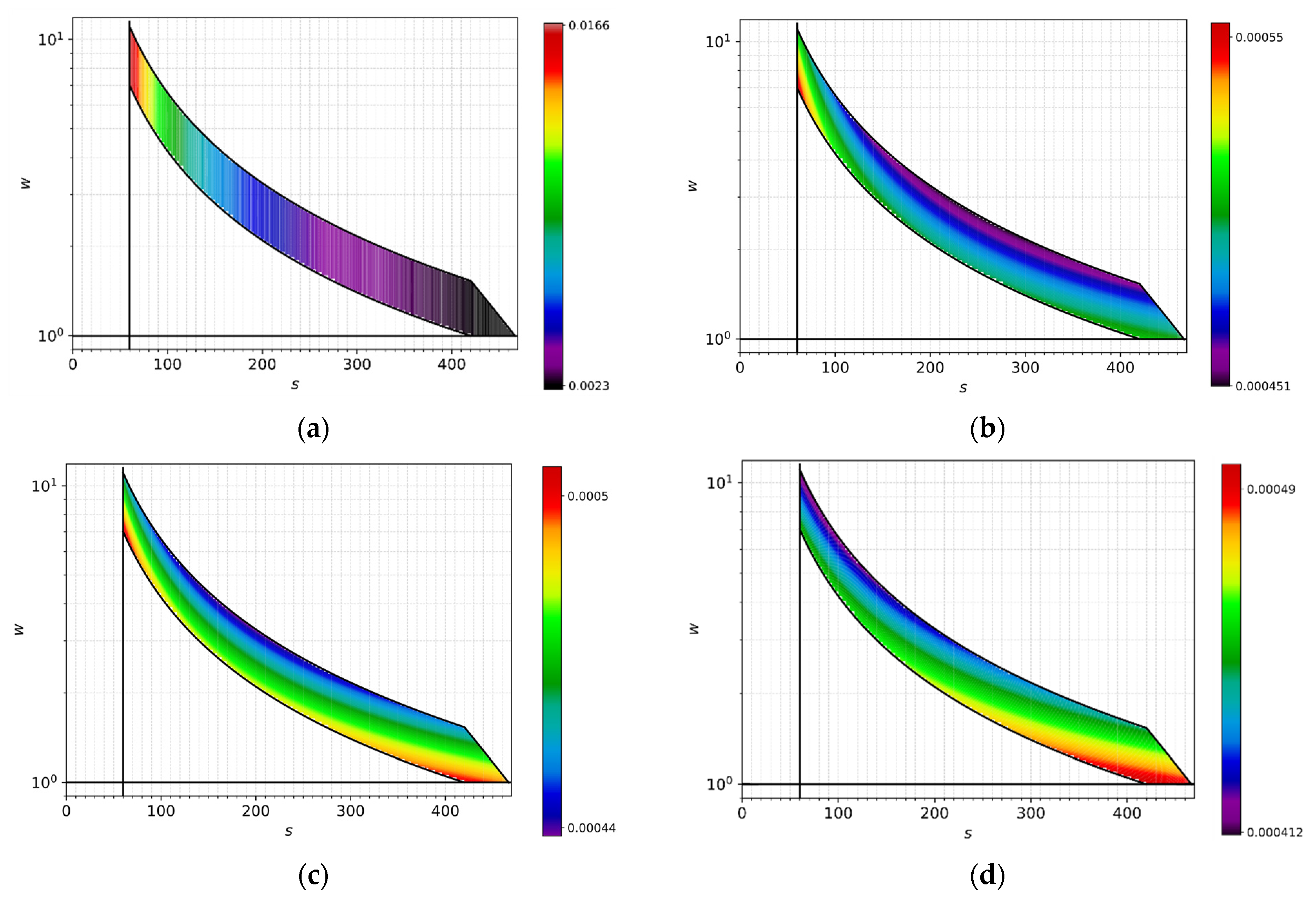
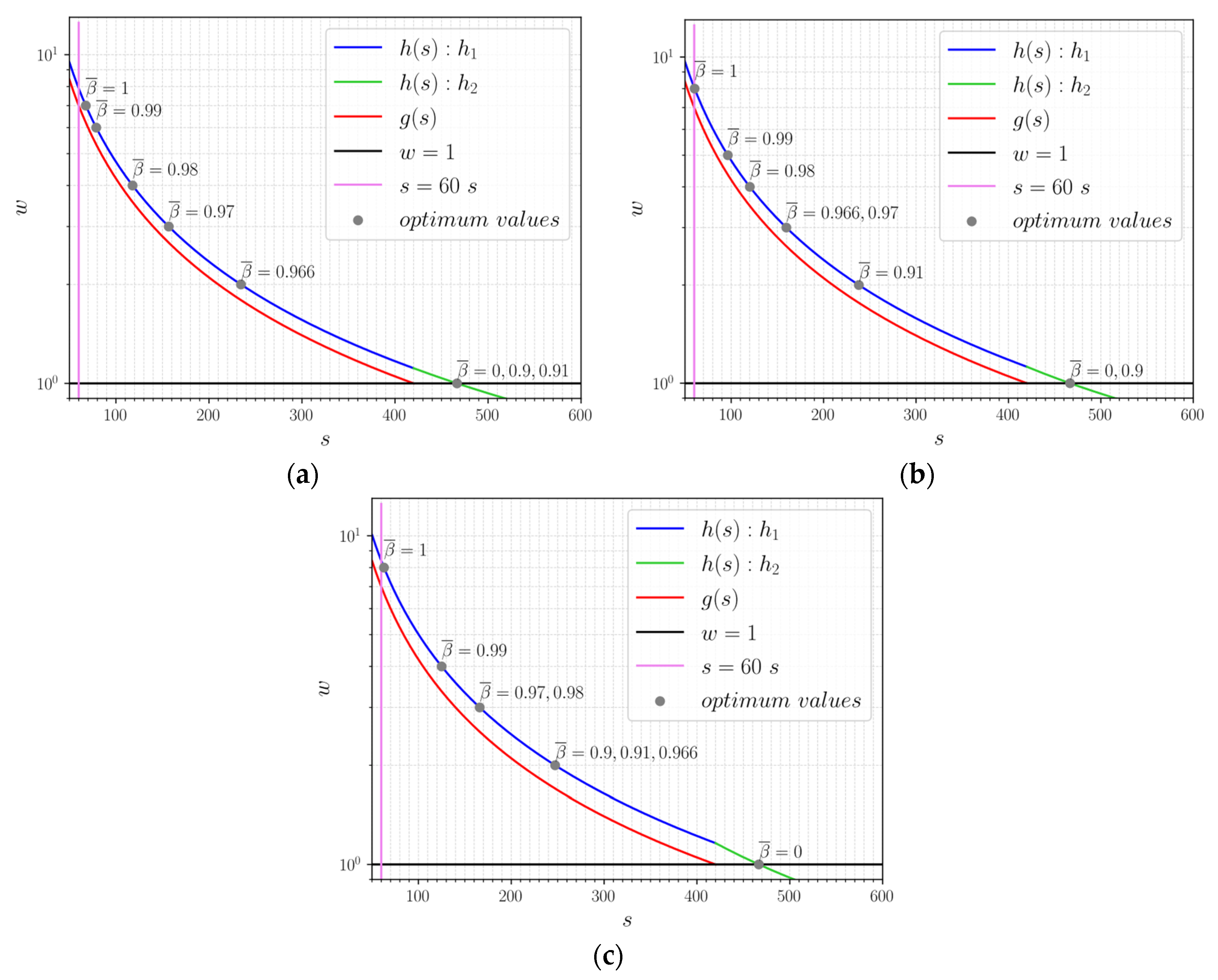
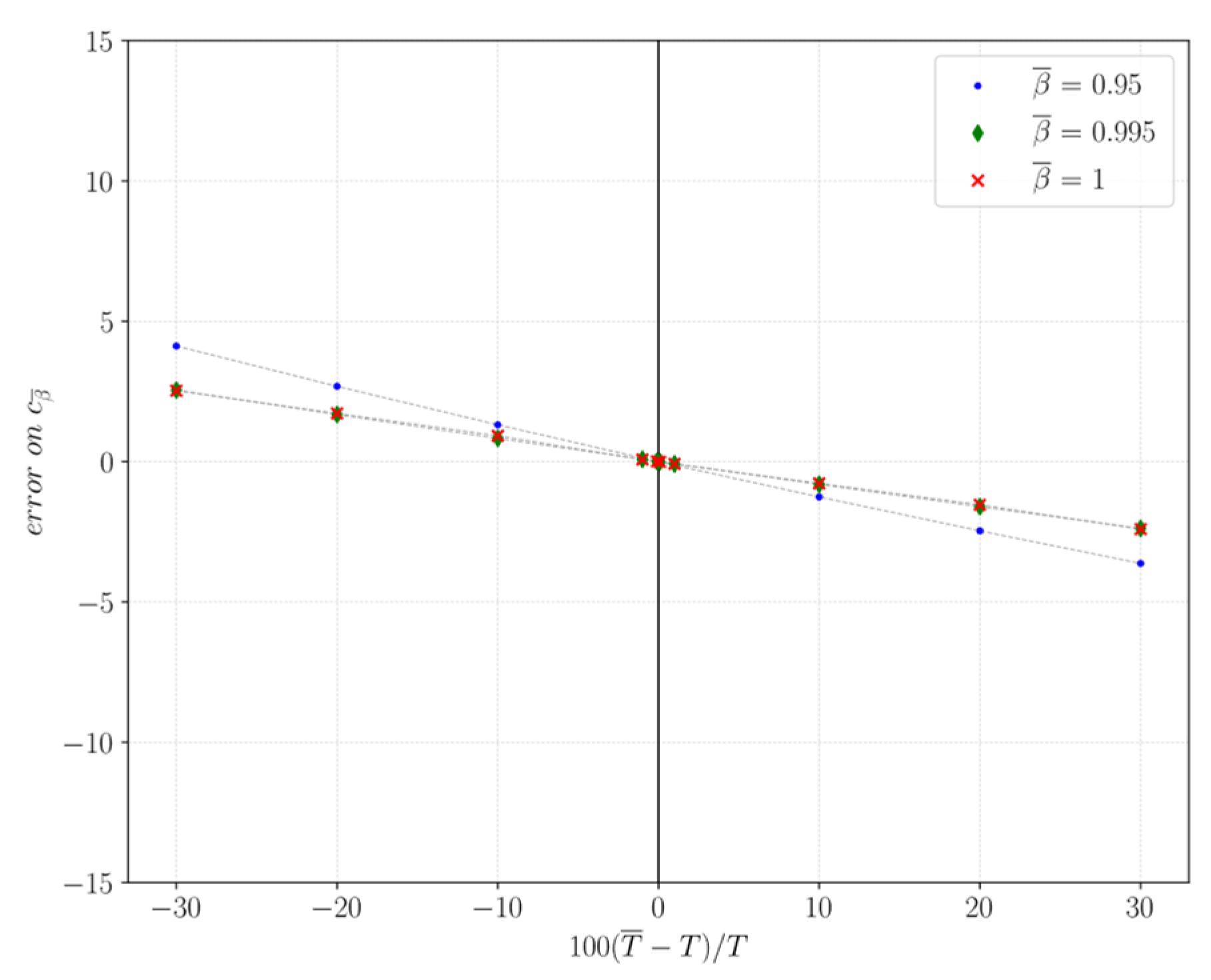
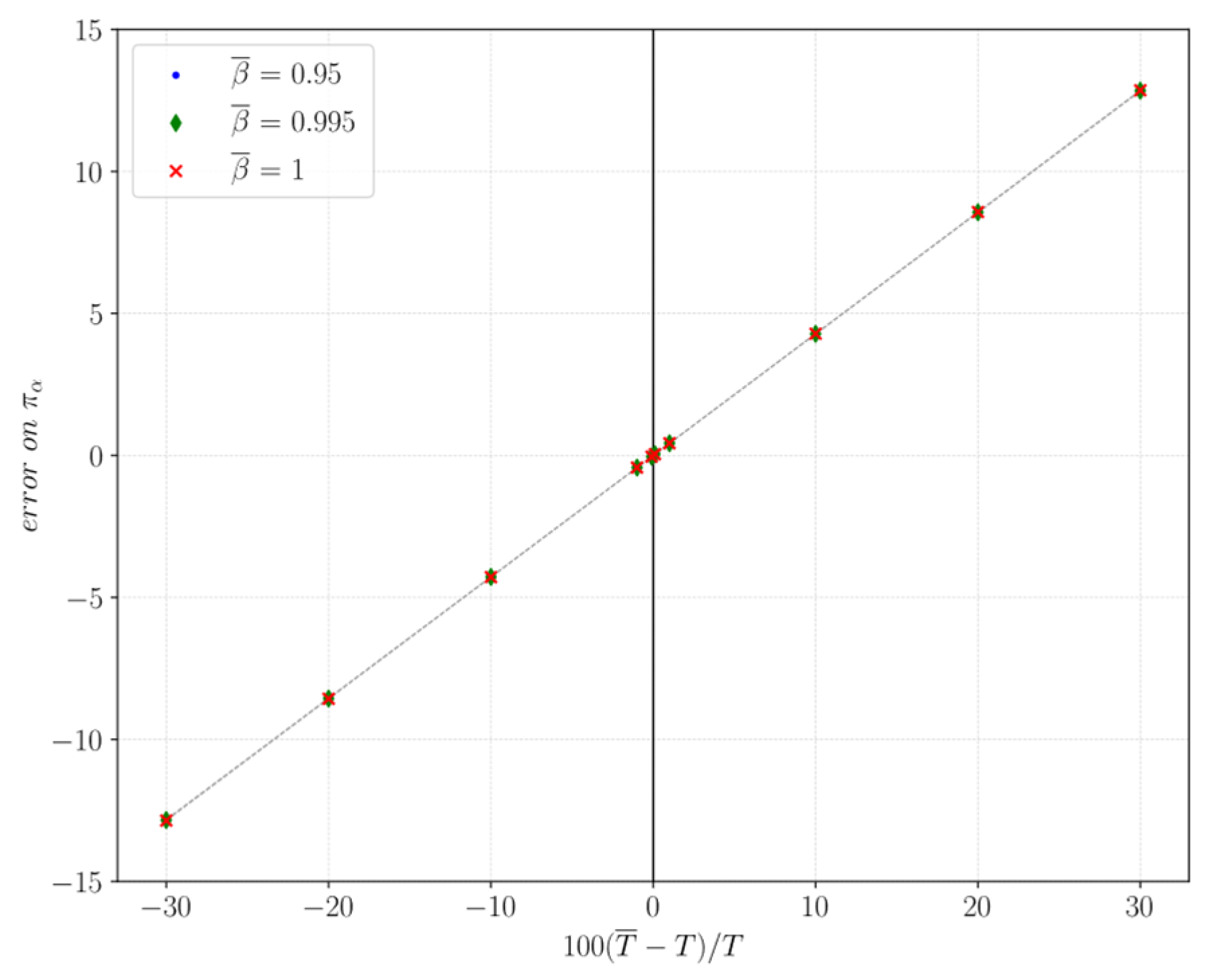
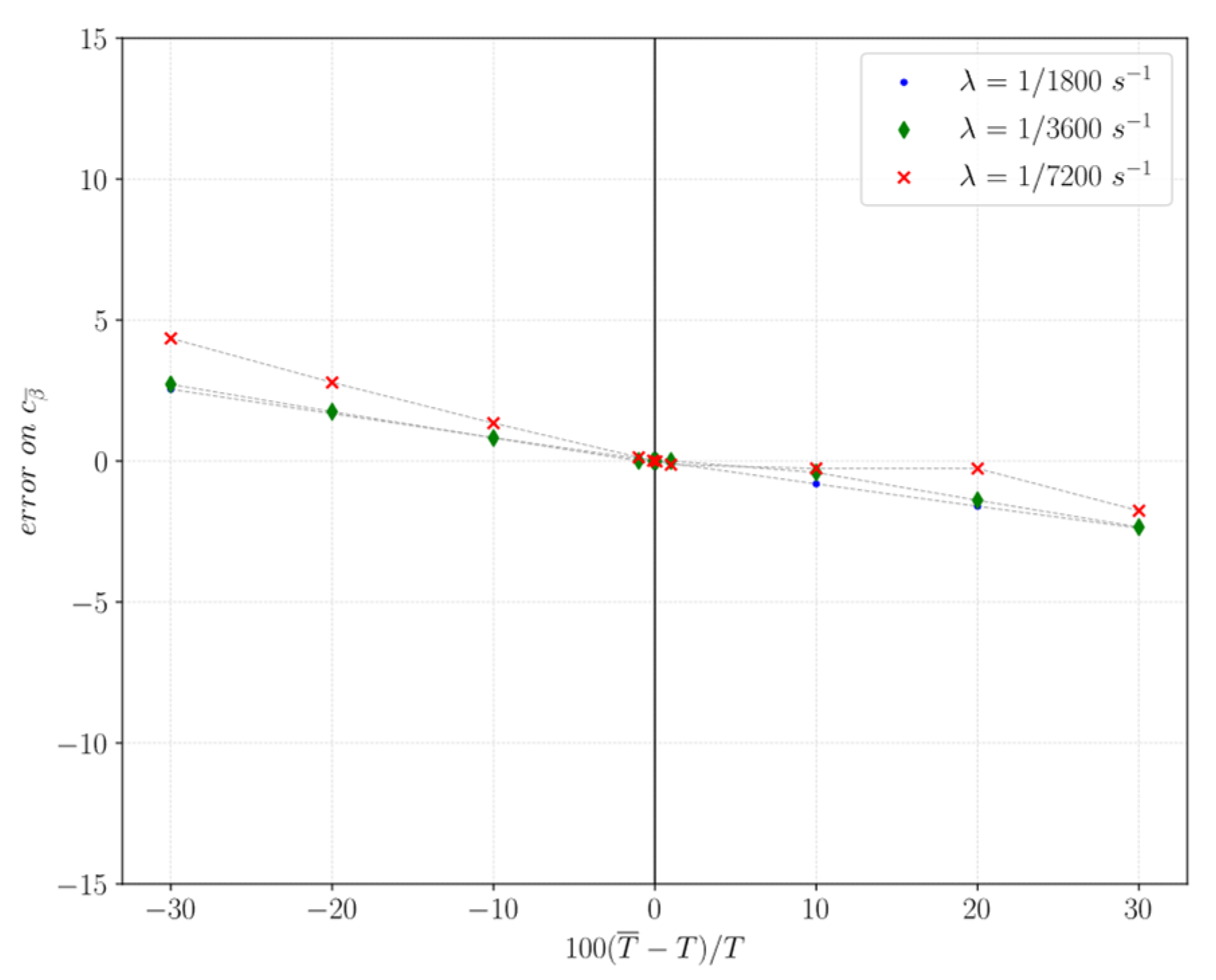
4.2. Sensitivity Analysis
5. Performance Evaluation
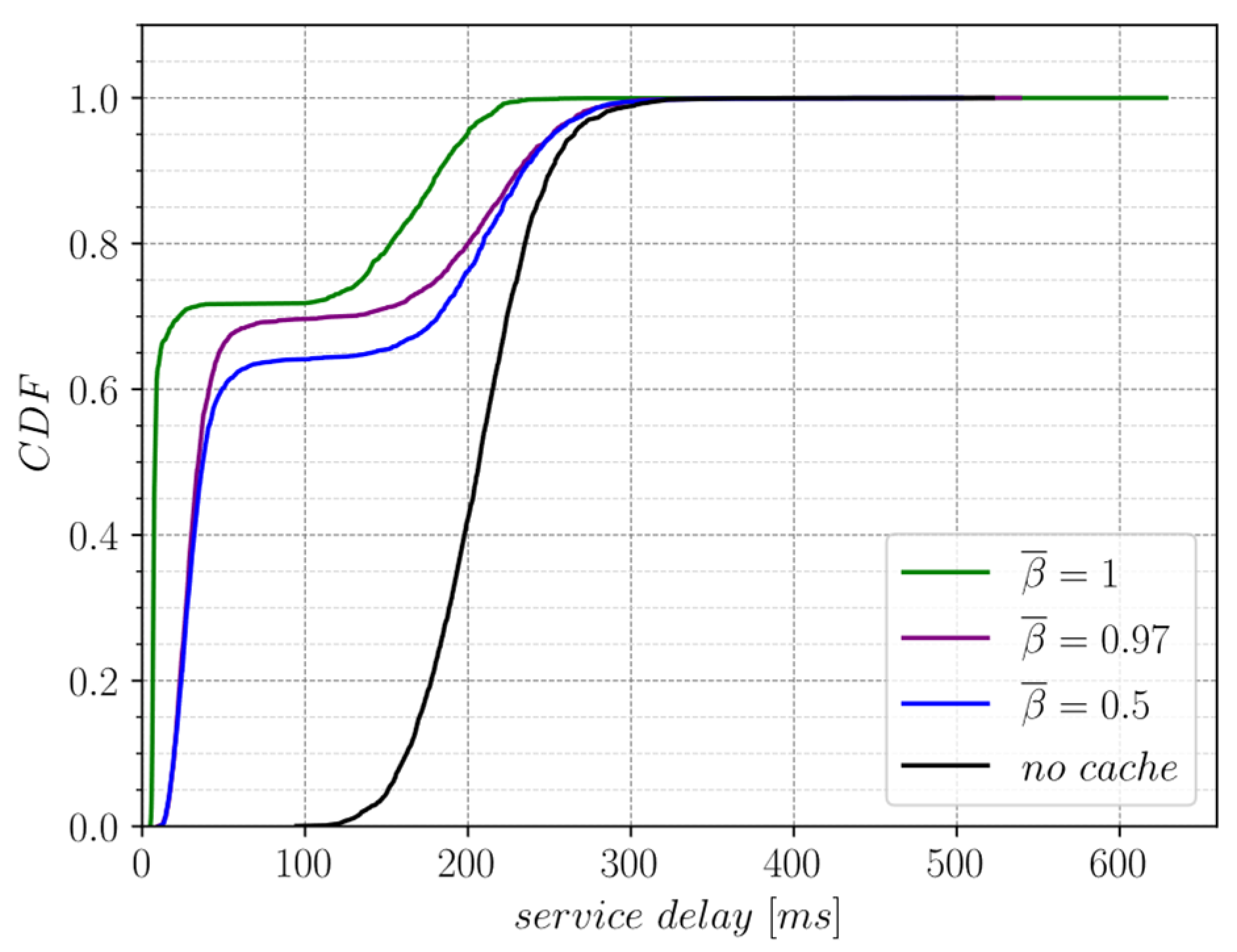
Exemplary Use Case: LWM2M
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix B
- If :
- If :
References
- Huang, H.; Qiao, D.; Gursoy, M.C. Age-Energy Tradeoff Optimization for Packet Delivery in Fading Channels. IEEE Trans. Wirel. Commun. 2021, 21, 179–190. [Google Scholar] [CrossRef]
- Zhou, B.; Saad, W. Optimal Sampling and Updating for Minimizing Age of Information in the Internet of Things. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Razzaque, M.A.; Dobson, S. Energy-efficient sensing in wireless sensor networks using compressed sensing. Sensors 2014, 14, 2822–2859. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kim-Hung, L.; Le-Trung, Q. User-Driven Adaptive Sampling for Massive Internet of Things. IEEE Access 2020, 8, 135798–135810. [Google Scholar] [CrossRef]
- Zhong, J.; Yates, R.D.; Soljanin, E. Two Freshness Metrics for Local Cache Refresh. In Proceedings of the 2018 IEEE International Symposium on Information Theory (ISIT), Vail, CO, USA, 17–22 June 2018; pp. 1924–1928. [Google Scholar]
- Kaul, S.; Gruteser, M.; Rai, V.; Kenney, J. Minimizing Age of Information in Vehicular Networks. In Proceedings of the 2011 8th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, Salt Lake City, UT, USA, 27–30 June 2011; pp. 350–358. [Google Scholar]
- Yates, R.D.; Sun, Y.; Brown, D.R.; Kaul, S.K.; Modiano, E.; Ulukus, S. Age of information: An introduction and survey. IEEE J. Sel. Areas Commun. 2021, 39, 1183–1210. [Google Scholar] [CrossRef]
- Kosta, A.; Pappas, N.; Angelakis, V. Age of information: A new concept, metric, and tool. Found. Trends Netw. 2017, 12, 162–259. [Google Scholar] [CrossRef] [Green Version]
- Costa, M.; Codreanu, M.; Ephremides, A. On the age of information in status update systems with packet management. IEEE Trans. Inf. Theory 2016, 62, 1897–1910. [Google Scholar] [CrossRef]
- Pappalardo, M.; Mingozzi, E.; Virdis, A. A Model-Driven Approach to Aol-Based Cache Management in IoT. In Proceedings of the 2021 IEEE 26th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Porto, Portugal, 25–27 October 2021; pp. 1–6. [Google Scholar]
- Pappalardo, M.; Virdis, A.; Mingozzi, E. An Edge-Based LWM2M Proxy for Device Management to Efficiently Support QoS-Aware IoT Services. IoT 2022, 3, 169–190. [Google Scholar] [CrossRef]
- Open Mobile Alliance. Lightweight Machine to Machine Technical Specification: Core; Open Mobile Alliance: San Diego, CA, USA, 2020. [Google Scholar]
- Open Mobile Alliance. Lightweight Machine to Machine Technical Specification: Transport Bindings; Open Mobile Alliance: San Diego, CA, USA, 2020. [Google Scholar]
- Chen, Z.; Sivaparthipan, C.B.; Muthu, B. IoT based smart and intelligent smart city energy optimization. Sustain. Energy Technol. Assess. 2022, 49, 101724. [Google Scholar] [CrossRef]
- Naeem, A.; Javed, A.R.; Rizwan, M.; Abbas, S.; Lin, J.C.-W.; Gadekallu, T.R. DARE-SEP: A Hybrid Approach of Distance Aware Residual Energy-Efficient SEP for WSN. IEEE Trans. Green Commun. Netw. 2021, 5, 611–621. [Google Scholar] [CrossRef]
- Dev, K.; Maddikunta, P.K.R.; Gadekallu, T.R.; Bhattacharya, S.; Hegde, P.; Singh, S. Energy optimization for green communication in IoT using harris hawks optimization. IEEE Trans. Green Commun. Netw. 2022, 6, 685–694. [Google Scholar] [CrossRef]
- Abbas, Q.; Hassan, S.A.; Pervaiz, H.; Ni, Q. A Markovian Model for the Analysis of Age of Information in IoT Networks. IEEE Wirel. Commun. Lett. 2021, 10, 1596–1600. [Google Scholar] [CrossRef]
- Akar, N.; Dogan, O. Discrete-Time Queueing Model of Age of Information with Multiple Information Sources. IEEE Internet Things J. 2021, 8, 14531–14542. [Google Scholar] [CrossRef]
- Kaul, S.; Yates, R.; Gruteser, M. Real-Time Status: How Often Should One Update? In Proceedings of the 2012 Proceedings IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 2731–2735. [Google Scholar]
- Abd-Elmagid, M.A.; Pappas, N.; Dhillon, H.S. On the role of age of information in the Internet of Things. IEEE Commun. Mag. 2019, 57, 72–77. [Google Scholar] [CrossRef] [Green Version]
- Chiariotti, F.; Holm, J.; Kalør, A.E.; Soret, B.; Jensen, S.K.; Pedersen, T.B.; Popovski, P. Query Age of Information: Freshness in Pull-Based Communication. IEEE Trans. Commun. 2022, 70, 1606–1622. [Google Scholar] [CrossRef]
- Niyato, D.; Kim, D.I.; Wang, P.; Song, L. A Novel Caching Mechanism for Internet of Things (IoT) Sensing Service with Energy Harvesting. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 23–27 May 2016; pp. 1–6. [Google Scholar]
- Xu, C.; Wang, X.; Yang, H.H.; Sun, H.; Quek, T.Q. AoI and Energy Consumption Oriented Dynamic Status Updating in Caching Enabled IoT Networks. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 710–715. [Google Scholar]
- Zhang, S.; Li, J.; Luo, H.; Gao, J.; Zhao, L.; Shen, X.S. Low-Latency and Fresh Content Provision in Information-Centric Vehicular Networks. IEEE Trans. Mobile Comput. 2020, 21, 1723–1738. [Google Scholar] [CrossRef]
- Zhang, S.; Li, J.; Luo, H.; Gao, J.; Zhao, L.; Shen, X.S. Towards fresh and low-latency content delivery in vehicular networks: An edge caching aspect. In Proceedings of the 2018 10th International Conference on Wireless Communications and Signal Processing (WCSP), Hangzhou, China, 18–20 October 2018; pp. 1–6. [Google Scholar]
- Zhang, S.; Wang, L.; Luo, H.; Ma, X.; Zhou, S. AoI-delay tradeoff in mobile edge caching with freshness-aware content refreshing. IEEE Trans. Wirel. Commun. 2021, 20, 5329–5342. [Google Scholar] [CrossRef]
- Mezair, T.; Djenouri, Y.; Belhadi, A.; Srivastava, G.; Lin, J.C.-W. Towards an Advanced Deep Learning for the Internet of Behaviors: Application to Connected Vehicle. Available online: https://dl.acm.org/doi/abs/10.1145/3526192 (accessed on 23 June 2022).
- Taivalsaari, A.; Mikkonen, T. A roadmap to the programmable world: Software challenges in the IoT era. IEEE Softw. 2017, 34, 72–80. [Google Scholar] [CrossRef]
- Li, C.; Li, S.; Hou, Y.T. A general model for minimizing age of information at network edge. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 118–126. [Google Scholar]
- Fragkiadakis, A.; Charalampidis, P.; Tragos, E. Adaptive compressive sensing for energy efficient smart objects in IoT applications. In Proceedings of the 2014 4th International Conference on Wireless Communications, Vehicular Technology, Information Theory and Aerospace & Electronic Systems (VITAE), Aalborg, Denmark, 11–14 May 2014; pp. 1–5. [Google Scholar]
- Hedengren, J.D.; Asgharzadeh Shishavan, R.; Powell, K.M.; Edgar, T.F. Nonlinear Modeling, Estimation and Predictive Control in APMonitor. Comput. Chem. Eng. 2014, 70, 133–148. [Google Scholar] [CrossRef] [Green Version]
- Beal, L.D.R.; Hill, D.; Martin, R.A.; Hedengren, J.D. GEKKO Optimization Suite. Processes 2018, 8, 106. [Google Scholar] [CrossRef] [Green Version]
- Available online: https://github.com/contiki-ng/cooja (accessed on 3 June 2022).
- Available online: https://datatracker.ietf.org/wg/6lowpan/documents/ (accessed on 3 June 2022).
- IEEE Std 802.15.4-2015; IEEE Standard for Low-RateWireless Networks. IEEE: Piscataway Township, NJ, USA, 2016.
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks; RFC 6550; IETF: Fremont, CA, USA, 2012. [Google Scholar]
- Available online: https://github.com/contiki-ng/contiki-ng (accessed on 3 June 2022).
- Available online: https://github.com/eclipse/leshan (accessed on 3 June 2022).






| Sensor | ||
|---|---|---|
| MMA7269Q (Accelerometer) | 0.0000268 | 0.97 |
| GE/Telaire 6004 (CO2 sensor) | 1249.25 | 0.0008 |
| SHT1X (H) (Humidity sensor) | 0.4 | 0.71 |
| SHT1X (T) (Temperature sensor) | 1.5 | 0.4 |
| CP 18 (Proximity sensor) | 0.267 | 0.8 |
| LUC-M10 (Level sensor) | 9.22 | 0.098 |
| 0 | 0.9 | 0.91 | 0.966 | 0.97 | 0.98 | 0.99 | 1 | ||
|---|---|---|---|---|---|---|---|---|---|
| 1 | 1 | 1 | 2 | 3 | 4 | 6 | 7 | ||
| 466.67 | 466.67 | 466.67 | 234.37 | 156.79 | 117.88 | 78.82 | 67.63 | ||
| 1 | 1 | 2 | 3 | 3 | 4 | 5 | 8 | ||
| 466.67 | 466.67 | 238.14 | 159.7 | 159.7 | 120.18 | 96.36 | 60.44 | ||
| 1 | 2 | 2 | 2 | 3 | 3 | 4 | 8 | ||
| 466.67 | 247.25 | 247.25 | 247.25 | 166.05 | 166.05 | 125.03 | 62.91 |
| 0.5 | 0.97 | 1 | |
|---|---|---|---|
| 1 | 3 | 8 | |
| 466.67 | 159.7 | 60.44 | |
| 231.53 95% CI [221.93, 241.16] | 212.31 95% CI [203.51, 221.11] | 189.98 95% CI [182.08, 197.88] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pappalardo, M.; Virdis, A.; Mingozzi, E. Energy-Optimized Content Refreshing of Age-of-Information-Aware Edge Caches in IoT Systems. Future Internet 2022, 14, 197. https://doi.org/10.3390/fi14070197
Pappalardo M, Virdis A, Mingozzi E. Energy-Optimized Content Refreshing of Age-of-Information-Aware Edge Caches in IoT Systems. Future Internet. 2022; 14(7):197. https://doi.org/10.3390/fi14070197
Chicago/Turabian StylePappalardo, Martina, Antonio Virdis, and Enzo Mingozzi. 2022. "Energy-Optimized Content Refreshing of Age-of-Information-Aware Edge Caches in IoT Systems" Future Internet 14, no. 7: 197. https://doi.org/10.3390/fi14070197
APA StylePappalardo, M., Virdis, A., & Mingozzi, E. (2022). Energy-Optimized Content Refreshing of Age-of-Information-Aware Edge Caches in IoT Systems. Future Internet, 14(7), 197. https://doi.org/10.3390/fi14070197







