Abstract
The requirements of low latency, low cost, less energy consumption, high flexibility, high network capacity, and high data safety are crucial challenges for future Internet of Things (IoT) wireless networks. Motivated by these challenges, this study deals with a novel design of green-cooperative IoT network, which employed coupled relays consisting of one IoT relay selected for forwarding signals to multiple IoT devices while another IoT relay transmitted jamming signals to an eavesdropper. For flexibility, all IoT nodes were powered by solar energy enough to sustain themselves, in order to consume less energy. To reach low latency, the study adopted the emerging non-orthogonal multiple access technique to serve multiple IoT devices simultaneously. Furthermore, the study adopted the simultaneous wireless information and power transfer technique which transmits wireless data for information processing and energy for energy harvesting. The study sketched a novel transmission block time period framework which plotted how a signal could travel via an individual IoT model. Maximizing the achievable bit-rate of IoT devices was considered to improve network capacity and data safety as well. Aiming at enhancing secrecy performance, a rest IoT relay played a role as a friendly jammer to transmit a jamming signal to an eavesdropper using energy harvested from the power splitting protocol. The results achieved in this study showed that the proposed model satisfied the requirements of future green IoT wireless networks. Derivatives leading to closed-form expressions are presented and verified by simulation results. The investigated results demonstrated that a friendly jammer based on radio frequency and energy harvesting strongly forces the intercept probability performance of the eavesdropper towards one, while outage probability performance of IoT devices towards zero showed that the signal to noise ratio tends to infinity.
1. Introduction
An IoT network deals with massive connections of a variety of objects, i.e., smart things, wearable devices, sensors, etc., through the Internet, for information processing. The massively connected IoT devices are challenging problems because of system performance requirements, i.e., lower latency, higher network capacity, less energy consumption, higher data safety, higher flexibility, higher reliability, etc.
In light of emerging techniques, the non-orthogonal multiple access (NOMA) technique was proposed for green IoT network applications, since the NOMA technique may provide massive connections simultaneously using the spectral sharing method. In the last decade, a number of studies on conventional NOMA-assisted IoT networks were published by academic researchers and networking providers. The pioneering studies examined outage probability, system throughput, ergodic capacity, and secrecy performance. The achieved results proved that the NOMA technique showed a system performance which outperformed the orthogonal multiple access (OMA) technique. NOMA system served multiple IoT devices by a single radio frequency (RF) transmission block [1,2,3]. The NOMA-IoT network employed superposition coding technique at the transmitter to encode the superimposed signals of multiple IoT devices over the same RF transmission block by allocating power multiplexing [4]. The initial signals of different IoT devices over the same RF transmission block at the base station (BS) are separated by allocating different power levels. Allocated power levels are based on the channel state information (CSI) of IoT devices [5]. The BS transmits the superimposed signal to those IoT devices with better CSI at lower transmitting power level. On the contrary, BS allocated high power level to transmit IoT device’s data with poorer CSI [6]. IoT devices employ successive interference cancellation (SIC) mechanism to decode their own message contained in the superimposed signal. The IoT device decodes the message with strongest power allocation (PA) factor by treating the other messages with lower PA factors and additive white Gaussian noise (AWGN) as interference. The IoT device then repeats SIC until detecting it own message successfully.
In the study by [7], the author examined a dual-hop cooperative network with a multi-branch using all participate relay. Overall, relay selection (RS) strategies are in two categories, i.e., single RS and multi-RS as shown in [8,9,10,11,12,13]. For clarity, the authors selected relay based on error rate and energy efficiency ratio [11] or signal to noise ratio (SNR) maximization [13]. The incremental relay led to the achievement of higher spectral efficiency; however, higher hardware cost and complexity [14]. Therefore, this study employed a coupled relay as in [15] which shared its benefits with the multi-relay scheme; however, there was a light incremental hardware cost. This study selects just one relay for forwarding signals, by adopting the decode-and-forward (DF) protocol.
Although there have been significant improvements in the benefits of spectral sharing efficiency, the study of the energy efficiency of NOMA-IoT networks is still at the initial stage. Furthermore, simultaneous wireless information and power transfer (SWIPT) the utility of RF to transfer wireless information and energy to the receiver simultaneously has been shown in many studies. Integration of the SWIPT technique in the NOMA system has been studied from the perspective of outage probability (OP) and energy harvesting (EH) performance [15,16,17,18]. Unfortunately, due to the utility functions of RF signal and broadcast superimposed signal of NOMA system, the wireless signal propagation from transmitter to receiver may be eavesdropped on by an illegitimate device. More specially, physical layer security (PLS) is another crucial challenge to protect legitimate devices from a potential eavesdropper in IoT wireless networks. In [3], the EH at receivers may intercept the threat to secure data propagated between legitimate IoT devices. To improve secrecy performance to the low-powered IoT devices, PLS was introduced as an alternative to the ultra-high complex cryptography algorithm [19]. PLS strategies may enhance the secrecy performance of IoT wireless networks by cooperative IoT relaying [18,20], multi-antenna beamforming [14,21,22,23,24,25], and jamming signal [26,27,28,29,30,31,32,33].
There is a gap for cooperative wireless communication networks to achieve distributed spatial diversity, wider networking coverage, lower energy consumption, and reduced interference [14,22]. Cooperative wireless communication networks were significantly improved by the benefit of RS protocol. RS protocols have been analyzed from classical adaptive diversity combining techniques (e.g., a diversity combiner adds diversified branches until the cumulative output is over a threshold [23,24]). This study also uses RS protocol to propose a new RS strategy enabling for green and secure IoT network.
In particular, a friendly jammer is promising as a PLS strategy to improve data safety by adopting jamming signals to poison illegitimate device [26,27,28,29,30,31,32]. In [30], friendly jammer strategies were employed to enhance the secrecy metric to maximize the secrecy outage probability (SOP) for an eavesdropper. In [31], the OP, of the legitimate devices and the intercept probability (IP) of the eavesdropper was obtained to investigate the impact of the jamming signal. The authors proposed an algorithm to pair source and destination using matching theory with a particular jammer [32]. In contrast, this study adopts the SWIPT protocol. There are two major SWIPT techniques, i.e., time switching (TS) and power slitting (PS). In [34], the authors investigated the wireless-powered cooperative networks with TS and PS protocols. Moreover, Yang et al. [16] investigated the impact of PA factors on the NOMA network with SWIPT. By different scope, this paper investigates the impact of the PS factor on the system performance of IoT networks.
Inspired by the above-mentioned studies, this paper employed the cooperation of a coupled IoT relay, on one hand, to improve OP performance and PLS performance for a green IoT network. To reach these aims, some work was undertaken, which are also the contributions of this paper, such as:
- (i)
- This study designed a green-and-cooperative IoT wireless network, where IoT relays and IoT devices are powered by solar and communicate using RF.
- (ii)
- To prolong IoT network lifetime, this study adopted SWIPT for EH at coupled relays by applying PS protocol. In particular, the study optimized OP performance of legitimate IoT devices by PS factor optimization in the first-half transmission block time period.
- (iii)
- In the second-half transmission block time period, the EH at the rest IoT relay intercepts the confidential information being exchanged between legitimate IoT devices. For clarity, the study proposed a selected IoT relay for forwarding signal to legitimate IoT devices using EH while another IoT relay for transmitting jamming signals to illegitimate device using EH as well. In this way, the study reached IP performance at an illegitimate device tending to one.
The rest of the present paper is structured as follows: Section 2 sketches and describes the design of IoT wireless communication models, and follows this by making formulations. Section 3 presents an analysis based on the proposed IoT model and presented the algorithms using for RS strategy and OP investigations. Section 4 presents the analysis and Monte Carlo simulation results. Section 5 concludes the achieved results of the study.
2. System Model and Formulation
Inspired by the study by [30], this study sketches a green-cooperative IoT wireless network, as shown in Figure 1 consisting of an IoT hub S, a coupled IoT relay, and the number of N IoT devices. Assuming all IoT nodes have been solar-powered enough for their operation and equipped with a single antenna. The study employed coupled IoT relays and to assist IoT devices. The coupled IoT relays adopted the DF protocol for forwarding superimposed signals to IoT devices. To prolong IoT network online time, the study employed the SWIPT technique with the PS protocol to transmit simultaneously information for information processing and energy for EH at coupled IoT relays. Furthermore, the study proposed an RS strategy to select the relay for the forwarding signal. The selected relay used RF-EH for forwarding the signal instead of its own energy. However, the IoT network as shown in Figure 1 had an eavesdropper E that eavesdropped the IoT relay or by wiretapping channel for odd transmission block or for even transmission block since the broadcast function of RF. Therefore, the study proposed the rest IoT relay to transmit the jamming signals to the eavesdropper E using RF-EH instead of its own energy. Table 1 shows a comparison of the works in this study, in contrast to previous studies. Please note that the IoT devices for had distances from IoT hub S as ordered .
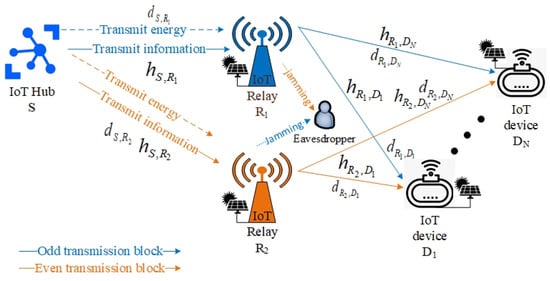
Figure 1.
The green-cooperative IoT wireless network.

Table 1.
Comparison to the other studies on secrecy performance.
2.1. Signal Transmission Block Time Period
Observing Figure 1, the IoT network needs two time slots to complete a signal propagation from the transmitter (IoT hub S) to the receivers (IoT device for ) through coupled IoT relays and . For clarity, the study designed a novel transmission block time period diagram as shown in Figure 2. By adopting the SWIPT technique (PS protocol), the IoT hub S transmits including simultaneous energy by power domain for EH and superimposed information by remaining power domain for information processing at the IoT relay , where , is PS factor and P is power domain at IoT hub S. By the RS strategy as shown in Algorithm 1, only the selected IoT relay is used for forwarding signal to legitimate IoT devices while the other IoT relay is used for transmitting the jamming signal to eavesdropper E. In the second transmission block time, Algorithm 1 switches the selected relay, where variable is zero and repeats the signal transmission period.
| Algorithm 1 Algorithm for switching relay selection |
| Input: ; |
| ; |
| ; |
| ; |
| ; |
| Output: The selected relay forwarded legitimate signals while the other relay transmitted jamming signals. |
| 1: while true do |
| 2: if then |
| 3: Function_Information_Processing(); |
| 4: Function_Forwarding_Signal(); |
| 5: Function_Jamming_Signal(); |
| 6: ; |
| 7: else |
| 8: ; |
| 9: ; |
| 10: end if |
| 11: end while |
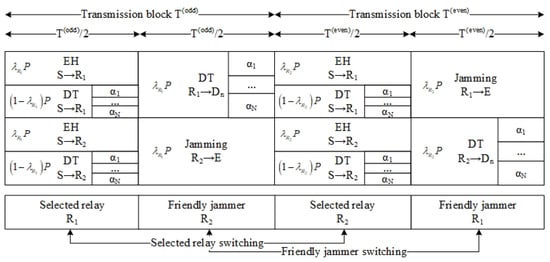
Figure 2.
Power resource allocation with PS factor and PA factors for .
2.2. Relay Selection Strategy
This study proposed the IoT hub S controlled whole private IoT network. It means that the IoT hub S pre-defined the cooperative script and synchronized the cooperative script to the coupled IoT relays and N devices. Please note that the cooperative script is re-configurable to achieve flexible cooperation.
Algorithm 1 selects which IoT relay ( or ) is being selected among coupled relays. For clarity, we first assigned values zero and one for coupled IoT relays and , respectively. The study initialized to hold the number of times an IoT relay would be selected for information processing and forwarding legitimate signals to legitimate IoT devices. Variable is used for counting whether the selected IoT relay forwarded signals enough number of transmission block time period or not. We had a while loop of to ensure the IoT network operated in real-time. We had an if condition to check variable . There are two cases:
- (i)
- If variable is non-zero, it means that an IoT relay has been selected. The selected IoT relay has to process legitimate information and then forward legitimate information after, while the non-selected IoT relay has to transmit a jamming signal. We counted down variable .
- (ii)
- If variable is zero, it means that the selected IoT relay finishing its obligation. Algorithm 1 swaps obligations between IoT relays and resets variable .
This assumes that the coupled relays own the cooperative script and activated synchronization.
2.3. Formulations
To keep the following simple, the study assumed that variables in Algorithm 1 were assigned initial values as and without losing general properties of Algorithm 1. It is worth noticing that we have sequential block time period . Since assuming and , we split the set T into two subsets, where for odd transmission block and for even transmission block.
The EH at the receiver was provided as [36] (Equation (6)) for the PS protocol. From the aforementioned expressions, the EH at the coupled IoT relays in the first phase of the first time slot or , is expressed as follows:
where and are the PS factors ( in the odd transmission block and in the even transmission block), P is power domain at IoT hub S, is collect factor for , and expected channel gains and are given by and , respectively.
Furthermore, in the second phase of the first time slot or , in terms of NOMA benefit, the IoT hub S encodes the messages for of IoT devices and superimposes the messages into the signal by superposition coding and sharing the remaining power domain for or for with different PA factors . Then, the received signals at the IoT relays and express as follows:
where and are AWGN, i.e., and , at IoT relays and , respectively. Moreover, is channel coefficient from IoT hub S to IoT relay (), g denoted Rayleigh distribution from IoT hub to coupled IoT relays with , is path-loss exponent, and are distances from IoT hub S to IoT relays and , respectively. Assuming IoT relays are closed to each other ().
From the system model as shown in Figure 1, the devices and are nearest and farthest from the IoT hub S, respectively. In the concept of NOMA, the farthest device was allocated the biggest PA factor since the farthest device owned poorest CSI. Inspired by studies [21,37], the PA factor for carried the message is given as follows:
In another term of NOMA theory, the SIC mechanism was adopted at coupled IoT relays. Please note that the message owned the biggest PA factor . The message thereby is prioritized SIC first by treating the other messages and AWGN as interference. The SIC mechanism repeats until successfully decoded the last message since it was allocated the smallest PA factor .
Therefore, signal to interference plus noise ratio (SINR) obtained at the IoT relay in odd transmission block time period , when decoded the message () by treating the messages and AWGN as interference, as follows:
where SNR .
Similarly, SINR obtained at the IoT relay in even transmission block time period , when decoded the message () by treating the messages and AWGN as interference, as follows:
An instantaneous bit-rate threshold is achievable after the coupled IoT relays and decoded the message in the received signal given by (5) for odd transmission block time period and (8) for even transmission block time period as follows:
Minimum of instantaneous bit-rates at relay in odd transmission block time period and relay in even transmission block time period express as follows:
In the second time slot, the IoT relays for and for retrieves, re-encodes and forwards the superimposed signals to the IoT devices. There are two feature forwarding protocols (i.e., amplify-and-forward (AF) and DF). This study employed the DF protocol at IoT relays and to ensure that and received and decoded the messages successfully. After receiving the signals as given by (5) for odd transmission block and (8) for even transmission block, the IoT relays and decoded the messages of devices and retrieved the messages and then forwarded them to the devices using the EH as given by (1) for odd transmission block and (4) for even transmission block . The received signal at IoT device for is expressed as follows:
where is AWGN at the terminal device , i.e., .
IoT device also adopted the SIC mechanism to decode its own message . By substituting (1) into (20) and (4) into (21), we obtain SINR at device for when the device , respectively, decoded the data symbol , where , as follows:
where expression (22) is used for IoT device ( and ) while IoT device has to adopt, respectively, expressions (22) first and then (23) to decode its own message .
Similarly, the device in the even transmission block also adopted the SIC mechanism to decode its own message . SINR obtained at device for when the device , respectively, decoded the data symbol , where , as follows:
where expression (24) is used for IoT device ( and ) while IoT device has to adopt, respectively, expressions (24) first and then (25) to decode its own message .
The instantaneous bit-rate threshold is reachable when the IoT device decodes the data symbols in odd and even transmission blocks, respectively, as follows:
The minimum of the achievable bit-rate threshold reached at device () in odd and even transmission blocks, respectively, as follows:
It is the presence of the eavesdropper E as shown in Figure 1. The eavesdropper E eavesdrops the IoT devices by wiretapping channel for odd transmission block time period or wiretapping channel for even transmission block time period . To combat eavesdropper E, this study adopted the rest relay as a friendly jammer. Please note that the selected IoT relay and the rest IoT relay in the odd transmission block time period are IoT relays and , respectively. This study proposes the IoT relay uses the EH as given by (2) to transmit jamming signals to the eavesdropper E. Simultaneously, the eavesdropper E receives the wiretapping signal from the IoT relay and the jamming signal from the rest IoT relay in the second time slot . In contrast, the selected IoT relay and the rest IoT relay in the even transmission block time period are IoT relays and , respectively. Similarly, the IoT relay forwards signal using EH as given by (4) while IoT relay uses the EH as given by (3) to transmit the jamming signal to eavesdropper E. The eavesdropper E receives simultaneously the wiretapping signal from the IoT relay and the jamming signal from the rest IoT relay in the second time slot .
In odd or even transmission blocks, the received signal at eavesdropper E is expressed as follows:
where is AWGN at eavesdropper E with , is status of jamming signal. If , the rest IoT relay did not transmit the jamming signal. If , the rest IoT relay transmitted the jamming signal fully by EH as (2) or (4).
From expression (30) for odd transmission block time period, eavesdropper E adopted SIC to detect IoT devices’ message . SINR obtained at the eavesdropper E, after the eavesdropper E decoded the data symbol () as follows:
Similarly, from expression (31) for even transmission block, eavesdropper E also adopted the SIC mechanism to detect IoT devices’ messages. SINR obtained at eavesdropper E, after the eavesdropper E decoded the data symbol (), as follows:
Instantaneous bit-rate threshold is reachable, after the eavesdropper E decoded the data symbols in odd or even transmission block, as follows:
where expressions (36) and (37) are with the case the eavesdropper E has wiretapped cooperative transmission script.
In contrast, the selected IoT relay is random and switchable as in Algorithm 1. If the eavesdropper E has no cooperative transmission script, eavesdropper E wiretapped randomly an IoT relay or . The expressions (36) and (37) are rewritten as follows:
3. System Performance Analysis
The probability density function (PDF) and cumulative distribution function (CDF) of Rayleigh distribution are given by and , respectively, where are random independent variables namely x in PDF and CDF and is expected channel gain with .
3.1. Outage Probability
Theorem 1.
The outage events at coupled IoT relays and occur if the minimum of instantaneous bit-rate thresholds as given by (18) and (19) for, respectively, transmission block time period could not reach IoT devices’ threshold . In other words, the OP at IoT relay () are given as follows:
where is pre-defined IoT devices’ bit-rate threshold.
By applying CDF over Rayleigh distribution, we obtain OP at coupled IoT relays in closed-form as follows:
where SINR threshold , either for transmission block or for transmission block .
Lemma 1.
OP at coupled IoT relays may be improved by equipping multi-antennas at IoT hub S and relays by the number of antennas and , respectively. By adopting transmit antenna selection (TAS) at IoT hub S and selection combining (SC) at coupled relays, OP at coupled IoT relay in multi-input multi-output (MIMO) scenario could be obtained as shown in (A2).
See Appendix A for proof.
From expression (40), the study presents an algorithm for Monte Carlo simulation at IoT relay in transmission block t as Algorithm 2.
| Algorithm 2 The algorithm for investigation OP at IoT relay for in transmission block |
| Input: Initialize the parameters as distances and ( and ), path-loss exponent factor , PA factors as (9), randomly generate samples for each fading channel over Rayleigh distribution; |
| Output: Simulation (Sim) results of OP at the relay (). |
| 1: Calculate SINR at IoT relay by applying (12)–(15); |
| 2: Calculate achievable bit-rate at IoT relay by applying (16) or (17); |
| 3: Find the minimum of achievable data rate by applying (18) or (19); |
| 4: Initialize variable ; |
| 5: for to samples do |
| 6: if then |
| 7: ; |
| 8: end if |
| 9: end for |
| 10: return OP at the IoT relay in transmission block as given . |
Theorem 2.
The outage event at IoT device () in transmission block t occurs, on one hand, if IoT relay cannot decode at least a message () in the received signal as (5) for or (8) for . On the other hand, if IoT device cannot decode at least a message () in the received signal as (20) for or (21) for .
In other words, the OP at IoT device in transmission block t is expressed as follows:
By applying CDF, expression (44) has been solved and obtained in closed-form as follows:
Lemma 2.
Assuming IoT hub S, relay and device have been equipped by number of antennas , and , respectively. TAS/SC techniques have been employed at transmitter and receiver to select the best signal. As a result, OP at IoT device in MIMO scenario is expressed as shown in (A13).
See Appendix B for proof.
From expression (44), the study provides an algorithm for OP Monte Carlo simulation at the IoT device as Algorithm 3.
| Algorithm 3 Algorithm for investigation OP at IoT device in a transmission block |
| Input: Initialize the parameters as in Algorithm 2; |
| Output: Simulation (Sim) results of OP at the IoT device ; |
| 1: Calculate SINR at relay by applying (12) and (13) for or (14) and (15) for ; |
| 2: Calculate achievable bit-rate at relay as (16) for or (17) for ; |
| 3: Find the minimum of achievable data rate ; |
| 4: Calculate SINR at device applying (22) and (23) for or (24) and (25) for ; |
| 5: Calculate achievable bit-rate at device by applying (26) for or (27) for ; |
| 6: Find the minimum of achievable data rate ; |
| 7: Initialize variable ; |
| 8: for to samples do |
| 9: if then |
| 10: ; |
| 11: end if |
| 12: end for |
| 13: return OP at device in transmission block as given ; |
3.2. IP at Eavesdropper
Theorem 3.
The IP event at eavesdropper E in transmission block t refers to IoT relays and devices decoded the messages successfully; however, the eavesdropper E cannot decode the messages successfully. IP at eavesdropper E is expressed as follows:
In other words, expression (49) may be rewritten as follows:
By substituting expressions (16), (17), (36)–(39) into expression (50), we always obtain expression (51) since .
By applying PDF over Rayleigh distribution, we obtain IP at eavesdropper E in closed-form as follows:
where is the selected relay and is the rest relay, if the rest IoT relay sent jamming signal or if the rest IoT relay did not send jamming signal to the eavesdropper E, and SINR threshold in expression (52) is with or for well known or unknown transmission script at eavesdropper E, respectively.
See Appendix C for proof.
3.3. System Throughput Maximization
The IoT network capacity is a crucial factor. The authors analyzed and obtained an ergodic sum rate as shown in [38] (Equation (28)). The authors then obtained the sum of devices’ bit-rate threshold as shown in [38] (Equation (29)). In contrast, this study aims to prove that devices’ bit-rate threshold improves network capacity and enhances secrecy performance as well. In the considered IoT network as shown in Figure 1, the target SINR has belonged to the IoT devices’ bit-rate threshold . From expression OP at IoT device as shown in (45) and expression IP at eavesdropper E as shown in (52), this study obtained the maximum of achievable bit-rate threshold for IoT device () as follows:
By substituting (53) into expressions (45) and (52), the OP at IoT devices and IP at eavesdropper E always tend to one with any SNR since expression (53) given ceiling bit-rate threshold of IoT device . It means that IoT devices’ pre-defined bit-rate threshold cannot tend to equal or greater than (53). On the other hand, expression (53) provides achievable maximum data rates for IoT devices in a heterogeneous manner. It means that the IoT devices are served with different throughput leading to unfairness between IoT devices. Therefore, this paper proposes to unify a data rate threshold for all IoT devices as follows:
where factor deals with tolerance for . The expression (54) is to ensure all IoT devices could decode their own message successfully and reach the same throughput while SNR .
3.4. PS Factor Optimization and IP Maximization
This paper proposed a unity of IoT devices’ bit-rate threshold as shown in (54) to ensure all IoT devices could decode their own message successfully; however, the eavesdropper E could also eavesdrop and detect IoT devices’ messages. From expressions (45) and (52), the study analyzed that the OP and IP performance may be impacted by the factors, i.e., PA factors , SNR , channel gain coefficients, data rate threshold , and PS factor , etc. Assuming PA factor , channel gain coefficients and SNR are fixed while a unify of IoT devices’ bit-rate threshold is given by (54). Furthermore, the study optimizes PS factor for .
To optimize the OP and IP performance, this study considers the OP performance at IoT relay and OP performance at the farthest device is approximate and IP performance at eavesdropper E is maximization. As a result, we exploits the optimal PS factor for EH at IoT relay as follows:
4. Numerical Results
For simplicity, this study assumed the coupled IoT relays are closed to each other. Therefore, the distances from IoT hub S to coupled relays and are m. The IoT network shows the number of IoT devices. Distances from coupled IoT relays to IoT device are equally ( for ). In this section, the paper conducts the analysis and Monte Carlo simulation results. The outcomes presented in this paper are given by parameters as shown in Table 2.

Table 2.
Table of parameters (denoted ).
The study examined the impact of crucial factors, i.e., PS factor and pre-defined IoT devices’ threshold . Figure 3a plotted the impact of PS factor onto OP performance at coupled IoT relays and IoT devices by fixed pre-defined bit-rate threshold b/s/Hz. Allocated unsuitability of PS factor leads to OP performance at either coupled IoT relays or IoT devices tending to one. On the other hand, Figure 3b also sketched OP performance at coupled IoT relays and IoT devices; however, considering the impact of pre-defined bit-rate threshold . A lower pre-defined bit-rate threshold leads to better OP performance (), however, lower system throughput (). Observing Figure 3b, it is worth noticing that if the pre-defined bit-rate threshold b/s/Hz and SNR , the OP at all IoT nodes then tends to zero. on the other hand, if pre-defined bit-rate threshold b/s/Hz, the OP at all IoT nodes then always tends to one since b/s/Hz is the ceiling bit-rate threshold.
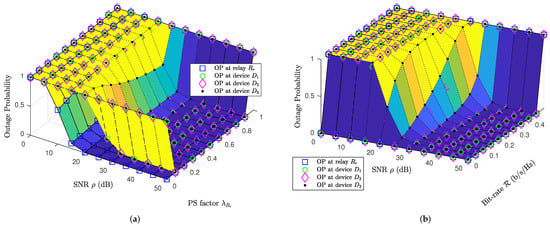
Figure 3.
Comparisons of OP at coupled IoT relay and IoT devices with (a) fixed pre-defined bit-rate threshold b/s/Hz versus PS factors while (b) fixed PS factor versus pre-defined bit-rate threshold b/s/Hz.
Figure 4a presented OP performance at coupled IoT relays and IoT devices, where fixed pre-defined bit-rate threshold b/s/Hz and PS factor . The OP performance of IoT devices are approximate and tend to zero when SNR . Figure 4b also plotted OP performance of coupled IoT coupled relays and IoT devices; however, where pre-defined bit-rate threshold given by (54) and PS factor as given by (55). Although OP performance of IoT devices also tended to zero as shown in Figure 4b; however, the OP performance of IoT devices are worse than the obtained results as shown in Figure 4a. Since the pre-defined bit-rate threshold b/s/Hz in Figure 4b is greater than the pre-defined bit-rate threshold b/s/Hz in Figure 4a, therefore, SNR in Figure 4b is higher SNR in Figure 4a.
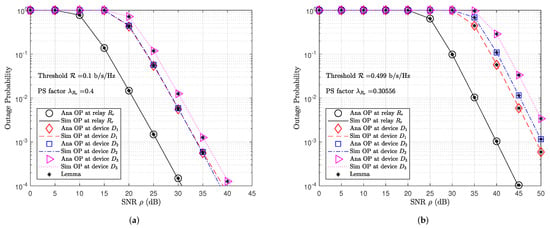
Figure 4.
OP performance at IoT relays and devices with (a) fixed PS factor and fixed bit-rate threshold , (b) optimized bit-rate threshold and PS factors.
The system throughput results in Figure 5a,b tended to pre-defined bit-rate threshold when SNR . It is important to notice that IoT devices’ throughput performance reached in Figure 5b is higher IoT devices’ throughput performance reached in Figure 5a since IoT devices’ bit-rate threshold b/s/Hz is greater than fixed IoT devices’ bit-rate threshold b/s/Hz.
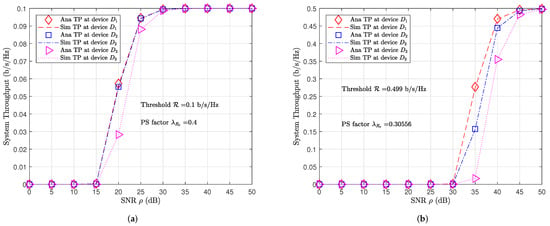
Figure 5.
Comparisons of system throughput at IoT devices with (a) fixed PS factor and fixed bit-rate threshold , (b) optimized bit-rate threshold and PS factors.
To verify the potential threat affecting the information propagated on the proposed IoT network, the study investigated the probability that an eavesdropper successfully decoded information from the wiretapping signal as shown in Figure 6. Unfortunately, the results obtained plotted that eavesdropper E has a better probability result than legitimate IoT devices decoding their own proprietary information. In other words, the results shown in Figure 6 are better than those shown in Figure 4a. It is worth explaining cause eavesdropper E has better probability results in decoding information than legitimate IoT devices. Please note that the expression (52) becomes (45), where . In addition, the distance from the eavesdropper E to the IoT relays ( m) is less than the distance from the IoT devices to the IoT relays ( m, m, m). As a consequence, eavesdropper E has channel gain () that is greater than the channel gains possessed by IoT devices (, , ). Thus, we obtained probability results that eavesdropper E can successfully decode the information better than IoT devices can. In other words , where and .
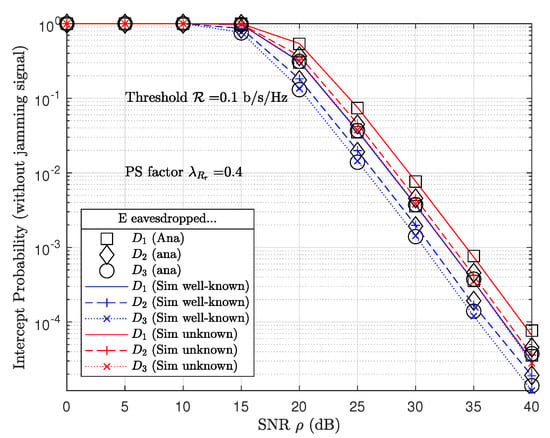
Figure 6.
IP performance of cooperative NOMA-IoT network without jamming signal.
In contrast, the major aim of this study is to improve the security of an individual IoT wireless network as shown in Figure 1. There are two cases. In the first case, transmission script is unknown at eavesdropper E. Eavesdropper E randomly selected a received signal (30) or (31) for SIC. In the second case, the transmission script is well-known at eavesdropper E, eavesdropper E selected signal as (30) for SIC in odd transmission block and then signal as (31) for SIC in even transmission block. Figure 7a shows the potential threat when eavesdropper E is able to decode messages of legitimate devices from the wiretapping signal. For example, the eavesdropper E had probability to decode message successfully at SNR dB. However, IP performance reached approximately at SNR dB. In particular, the eavesdropper E had just even since the impact of the friendly jamming signal as shown in Figure 7b.
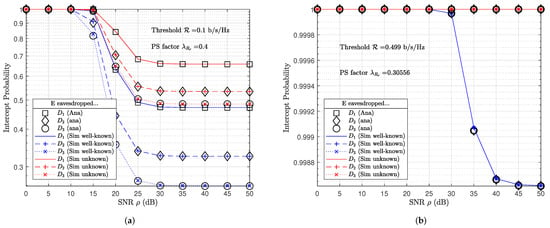
Figure 7.
IP performance of cooperative NOMA-IoT network with jamming signal, (a) fixed PS factor and fixed bit-rate threshold , (b) optimized bit-rate threshold and PS factor.
5. Conclusions
Future IoT network requirements have accelerated information propagation rapidly and safely. To satisfy these major aims, the study employed the emerging cooperative NOMA technique and proposed some new solutions, i.e., RS strategy and RF-EH-enabling for forwarding signal and transmitting jamming signal. On one hand, IoT devices’ threshold is defined to maximize throughput performance. On the other hand, the PS factor is also defined to optimize OP and IP as well. Based on the practical model, analysis and simulation results, the study conducted the propositions may provide high network capacity and high reliability to toward next IoT networks. The study is still opening some future tasks such as how Nakagami-m distributions affect OP performance, or how secrecy performance is impacted if eavesdropper equipped multi-antennas.
Author Contributions
T.-N.T., V.-C.H. and T.P.V. delivered main ideas for discussion; V.-C.H. and T.P.V. collected and provided theoretical knowledge about wireless communication techniques to T.-N.T. for analyzing. T.-N.T. and K.N.N.T. designed a system model and formulated its parameters and performance characteristics. T.-N.T. and K.N.N.T. programmed simulations to validate results of the model while V.-C.H. and T.P.V. prepared the manuscript by MS Word. T.-N.T. organized and re-wrote the paper in LaTeX template. M.V. formed initial research ideas and directions, provided supervisions, critically reviewed the organization of the paper and served as a corresponding author. All authors have read and agreed to the published version of the manuscript.
Funding
This research received funding from the Ministry of Education, Youth and Sports within the grant reg. No. SP2021/25 and partially within the Large Infrastructures for Research, Experimental Development and Innovations project reg. No. LM2018140.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, or in the decision to publish the results.
Appendix A. Proof of Theorem 1
By substituting (1), (4) into (5), (8), respectively, we obtain the received signals at IoT relays and in odd and even transmission blocks, respectively. By applying SIC, we obtain an instantaneous bit-rate threshold at coupled IoT relays as shown in (16) and (17). By substituting expression (16) or (17) into expression (40) and after the algebraic transformation, we obtain OP at coupled IoT relays in closed-form by applying PDF over Rayleigh distribution as follows:
In Lemma 1, this study assumed that IoT hub S has been equipped with the number of antennas and coupled IoT relays have been equipped with the number of antennas . By employing TAS protocol at IoT hub S, SC protocol at coupled IoT relay as in [15] and applying CDF as given by [21] (Equation (57)), we obtain OP at coupled IoT relays for MIMO scenario as follows:
where .
Appendix B. Proof of Theorem 2
From (44), OP at IoT device is rewritten as follows:
After the algebraic transformation, expression in (A3) could be obtained by applying PDF given by [21] (Equation (55)) for or [21] (Equation (56)) for as follows:
where in expression (A5) is given by (42).
By substituting (26) for or (27) for into (A3) and applying PDF given by [21] (Equation (55)) for or [21] (Equation (56) for , expression in (A3) could be obtained as follows:
where in (A6) is given by (A5).
From results presented in study [18], the OP result at IoT device referred to OP result at either IoT relays or IoT device. Therefore, expression (A3) could be rewritten as follows:
In Lemma 2, IoT hub S, relays and devices have been equipped multiple antennas with , and , respectively. Therefore, expressions and in (A3) are rewritten as follows:
By substituting (A11) and (A12) into (A3), we obtain OP at device in MIMO scenario as follows:
where is given by (A10) and or if or , respectively.
Appendix C. Proof of Theorem 3
From expression (49), IP at eavesdropper E is rewritten as follows:
After the algebraic transformation, we obtain IP at eavesdropper E as follows:
Observing expression (A15), IP at eavesdropper E referred to since the impact of the jamming signal. IP at eavesdropper E then tends to floor since when SNR . The major aim of this study is to improve secrecy performance for IoT network. It means that expression U in (A15) needs to tend to zero (). To reach this aim, the study proposed a pre-defined bit-rate threshold as given (54) and a PS factor as given (55). As a result, the IP at eavesdropper E tended to one approximately at almost SNR as shown in Figure 5b.
References
- Qian, L.P.; Feng, A.; Huang, Y.; Wu, Y.; Ji, B.; Shi, Z. Optimal SIC ordering and computation resource allocation in MEC-aware NOMA NB-IoT networks. IEEE Internet Things J. 2018, 6, 2806–2816. [Google Scholar] [CrossRef]
- Qian, L.P.; Shi, B.; Wu, Y.; Sun, B.; Tsang, D.H. NOMA-enabled mobile edge computing for Internet of Things via joint communication and computation resource allocations. IEEE Internet Things J. 2019, 7, 718–733. [Google Scholar] [CrossRef]
- Jameel, F.; Khan, W.U.; Chang, Z.; Ristaniemi, T.; Liu, J. Secrecy analysis and learning-based optimization of cooperative NOMA SWIPT systems. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Liu, M.; Gui, G.; Zhao, N.; Sun, J.; Gacanin, H.; Sari, H. UAV-aided air-to-ground cooperative nonorthogonal multiple access. IEEE Internet Things J. 2019, 7, 2704–2715. [Google Scholar] [CrossRef]
- Khan, W.U.; Yu, Z.; Yu, S.; Sidhu, G.A.S.; Liu, J. Efficient power allocation in downlink multi-cell multi-user NOMA networks. IET Commun. 2019, 13, 396–402. [Google Scholar] [CrossRef]
- Khan, W.U.; Jameel, F.; Sidhu, G.A.S.; Ahmed, M.; Li, X.; Jäntti, R. Multiobjective optimization of uplink NOMA-enabled vehicle-to-infrastructure communication. IEEE Access 2020, 8, 84467–84478. [Google Scholar] [CrossRef]
- Laneman, J.; Wornell, G. Distributed space-time-coded protocols for exploiting cooperative diversity in wireless networks. IEEE Trans. Inf. Theory 2003, 49, 2415–2425. [Google Scholar] [CrossRef] [Green Version]
- Sadek, A.K.; Han, Z.; Ray Liu, K.J. A Distributed Relay-Assignment Algorithm for Cooperative Communications in Wireless Networks. In Proceedings of the 2006 IEEE International Conference on Communications, Istanbul, Turkey, 11–15 June 2006; Volume 4, pp. 1592–1597. [Google Scholar]
- Bletsas, A.; Khisti, A.; Reed, D.; Lippman, A. A simple Cooperative diversity method based on network path selection. IEEE J. Sel. Areas Commun. 2006, 24, 659–672. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Y.; Adve, R.; Lim, T.J. Improving Amplify-and-Forward Relay Networks: Optimal Power Allocation versus Selection. In Proceedings of the 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, 9–14 July 2006; pp. 1234–1238. [Google Scholar] [CrossRef] [Green Version]
- Michalopoulos, D.S.; Karagiannidis, G.K.; Tsiftsis, T.A.; Mallik, R.K. WLC41-1: An Optimized User Selection Method for Cooperative Diversity Systems. In Proceedings of the IEEE Globecom2006, San Francisco, CA, USA, 27 November–1 December 2006; Volume 2006, pp. 1–6. [Google Scholar] [CrossRef]
- Madan, R.; Mehta, N.B.; Molisch, A.F.; Zhang, J. Energy-Efficient Cooperative Relaying over Fading Channels with Simple Relay Selection. IEEE Trans. Wirel. Commun. 2008, 7, 3013–3025. [Google Scholar] [CrossRef] [Green Version]
- Jing, Y.; Jafarkhani, H. Single and multiple relay selection schemes and their achievable diversity orders. IEEE Trans. Wirel. Commun. 2009, 8, 1414–1423. [Google Scholar] [CrossRef]
- Laneman, J.N.; Tse, D.N.; Wornell, G.W. Cooperative diversity in wireless networks: Efficient protocols and outage behavior. IEEE Trans. Inf. Theory 2004, 50, 3062–3080. [Google Scholar] [CrossRef]
- Tran, T.N.; Voznak, M. Switchable Coupled Relays Aid Massive Non-Orthogonal Multiple Access Networks with Transmit Antenna Selection and Energy Harvesting. Sensors 2021, 21, 1101. [Google Scholar] [CrossRef] [PubMed]
- Yang, Z.; Ding, Z.; Fan, P.; Al-Dhahir, N. The impact of power allocation on cooperative non-orthogonal multiple access networks with SWIPT. IEEE Trans. Wirel. Commun. 2017, 16, 4332–4343. [Google Scholar] [CrossRef] [Green Version]
- Tran, T.N.; Voznak, M.; Fazio, P.; Ho, V.C. Emerging cooperative MIMO-NOMA networks combining TAS and SWIPT protocols assisted by an AF-VG relaying protocol with instantaneous amplifying factor maximization. Aeu-Int. J. Electron. Commun. 2021, 135, 153695. [Google Scholar] [CrossRef]
- Tran, T.N.; Vo, T.P.; Fazio, P.; Voznak, M. SWIPT Model Adopting a PS Framework to Aid IoT Networks Inspired by the Emerging Cooperative NOMA Technique. IEEE Access 2021, 9, 61489–61512. [Google Scholar] [CrossRef]
- Jameel, F.; Wyne, S.; Ding, Z. Secure communications in three-step two-way energy harvesting DF relaying. IEEE Commun. Lett. 2017, 22, 308–311. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, N.; Pan, G.; Chen, Y.; Fan, L.; Jin, M.; Alouini, M.S. Secrecy Analysis for Cooperative NOMA Networks With Multi-Antenna Full-Duplex Relay. IEEE Trans. Commun. 2019, 67, 5574–5587. [Google Scholar] [CrossRef] [Green Version]
- Tran, T.N.; Voznak, M. On secure system performance over SISO, MISO and MIMO-NOMA wireless networks equipped a multiple antenna based on TAS protocol. Eurasip J. Wirel. Commun. Netw. 2020, 2020, 11. [Google Scholar] [CrossRef]
- Laneman, J.N.; Wornell, G.W. Energy-efficient antenna sharing and relaying for wireless networks. In Proceedings of the 2000 IEEE Wireless Communications and Networking Conference. Conference Record (Cat. No. 00TH8540), Chicago, IL, USA, 23–28 September 2000; Volume 1, pp. 7–12. [Google Scholar]
- Yang, H.C.; Alouini, M.S. MRC and GSC diversity combining with an output threshold. IEEE Trans. Veh. Technol. 2005, 54, 1081–1090. [Google Scholar] [CrossRef]
- Lioumpas, A.S.; Karagiannidis, G.K.; Tsiftsis, T.A. Adaptive generalized selection combining (A-GSC) receivers. IEEE Trans. Wirel. Commun. 2008, 7, 5214–5219. [Google Scholar] [CrossRef] [Green Version]
- Zhao, N.; Wang, W.; Wang, J.; Chen, Y.; Lin, Y.; Ding, Z.; Beaulieu, N.C. Joint Beamforming and Jamming Optimization for Secure Transmission in MISO-NOMA Networks. IEEE Trans. Commun. 2019, 67, 2294–2305. [Google Scholar] [CrossRef] [Green Version]
- Li, B.; Qi, X.; Huang, K.; Fei, Z.; Zhou, F.; Hu, R.Q. Security-reliability tradeoff analysis for cooperative NOMA in cognitive radio networks. IEEE Trans. Commun. 2018, 67, 83–96. [Google Scholar] [CrossRef]
- Zhou, F.; Chu, Z.; Sun, H.; Hu, R.Q.; Hanzo, L. Artificial noise aided secure cognitive beamforming for cooperative MISO-NOMA using SWIPT. IEEE J. Sel. Areas Commun. 2018, 36, 918–931. [Google Scholar] [CrossRef]
- Zhou, F.; Chu, Z.; Wu, Y.; Al-Dhahir, N.; Xiao, P. Enhancing PHY security of MISO NOMA SWIPT systems with a practical non-linear EH model. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Jameel, F.; Wyne, S.; Kaddoum, G.; Duong, T.Q. A comprehensive survey on cooperative relaying and jamming strategies for physical layer security. IEEE Commun. Surv. Tutor. 2018, 21, 2734–2771. [Google Scholar] [CrossRef] [Green Version]
- Vilela, J.P.; Bloch, M.; Barros, J.; McLaughlin, S.W. Wireless secrecy regions with friendly jamming. IEEE Trans. Inf. Forensics Secur. 2011, 6, 256–266. [Google Scholar] [CrossRef]
- Ding, X.; Song, T.; Zou, Y.; Chen, X. Security-reliability tradeoff for friendly jammer assisted user-pair selection in the face of multiple eavesdroppers. IEEE Access 2016, 4, 8386–8393. [Google Scholar] [CrossRef]
- Bayat, S.; Louie, R.H.; Han, Z.; Vucetic, B.; Li, Y. Physical-layer security in distributed wireless networks using matching theory. IEEE Trans. Inf. Forensics Secur. 2013, 8, 717–732. [Google Scholar] [CrossRef]
- Lv, L.; Zhou, F.; Chen, J.; Al-Dhahir, N. Secure Cooperative Communications With an Untrusted Relay: A NOMA-Inspired Jamming and Relaying Approach. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3191–3205. [Google Scholar] [CrossRef]
- Perera, T.D.P.; Jayakody, D.N.K. Analysis of time-switching and power-splitting protocols in wireless-powered cooperative communication system. Phys. Commun. 2018, 31, 141–151. [Google Scholar] [CrossRef]
- Nguyen, N.P.; Duong, T.Q.; Ngo, H.Q.; Hadzi-Velkov, Z.; Shu, L. Secure 5G wireless communications: A joint relay selection and wireless power transfer approach. IEEE Access 2016, 4, 3349–3359. [Google Scholar] [CrossRef]
- Lu, X.; Wang, P.; Niyato, D.; Kim, D.I.; Han, Z. Wireless Networks With RF Energy Harvesting: A Contemporary Survey. IEEE Commun. Surv. Tutor. 2015, 17, 757–789. [Google Scholar] [CrossRef] [Green Version]
- Tran, T.N.; Voznak, M. Adaptive multiple access assists multiple users over multiple-input-multiple-output non-orthogonal multiple access wireless networks. Int. J. Commun. Syst. 2021, 10, e4803. [Google Scholar] [CrossRef]
- Men, J.; Ge, J.; Zhang, C. Performance analysis of nonorthogonal multiple access for relaying networks over Nakagami-m fading channels. IEEE Trans. Veh. Technol. 2016, 66, 1200–1208. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
