A Strategy-Based Formal Approach for Fog Systems Analysis
Abstract
1. Introduction
- Low latency and location awareness: Fog computing provides location awareness by allowing fog nodes to be deployed in various places. Additionally, due to the fog proximity to end devices, it has a reduced latency while processing data.
- Geographical distribution: Unlike the centralised cloud, the fog provides dispersed services and applications that may be installed anywhere.
- Scalability: Fog provides distributed computing and storage resources that can handle such massive end devices.
- Mobility: One of the most significant features of fog systems is their capacity to connect directly to mobile devices, allowing mobility technologies.
- Interactions: Instead of the batch processing used in the cloud, fog systems enable real-time interactions between fog nodes.
- Heterogeneity: Different manufacturers create fog nodes or end devices, which come in a variety of types and must be installed according to their platforms.
- Interoperability: Fog components may interoperate with one other and perform across different domains and service providers.
- How to abstract this complex type of systems to deal with their heterogeneous, dynamical, geographically widespread, and intelligent aspects;
- What formalism is appropriate to design structural and behavioural aspects of fog systems;
- How to execute and analyse these formal models.
- First, we propose an architecture for fog systems. This architecture relies on many overlapping factors that should be considered earlier in the design phase. It focuses on the orchestration of fog elements, cloud elements, and IoT ones, in addition to communication issues between these elements by managing intra- and inter-layer communication using dedicated agents.
- Then, in the second step (Figure 1), we propose a model based on the formalism of BiAgents* (Bigraphical agents), a combination of bigraphs [10] and mobile agents [11], to model both physical and virtual aspects of complex systems. It permits also to represent its smart behaviour using the formal traces concept. The bigraphical part allows representing geographical dispersion of a fog system’s elements in addition to their heterogeneity. Besides, the dynamic behaviour of a fog system is defined by a combination of the bigraph reaction rules and agents’ states evolution.
- In the third step (Figure 1), we make a guided execution of this specification model using the Maude strategy tool [12] while implementing the different BiAgents* aspects in Maude. This execution permits a simulation of different plausible scenarios of a fog system. By using the extension of Maude with strategies, we have the ability to implement all the dimensions of a BiAgents* model.
- In the last step of our approach, we analyse formally the specified behaviours using the Maude strategy model checker.
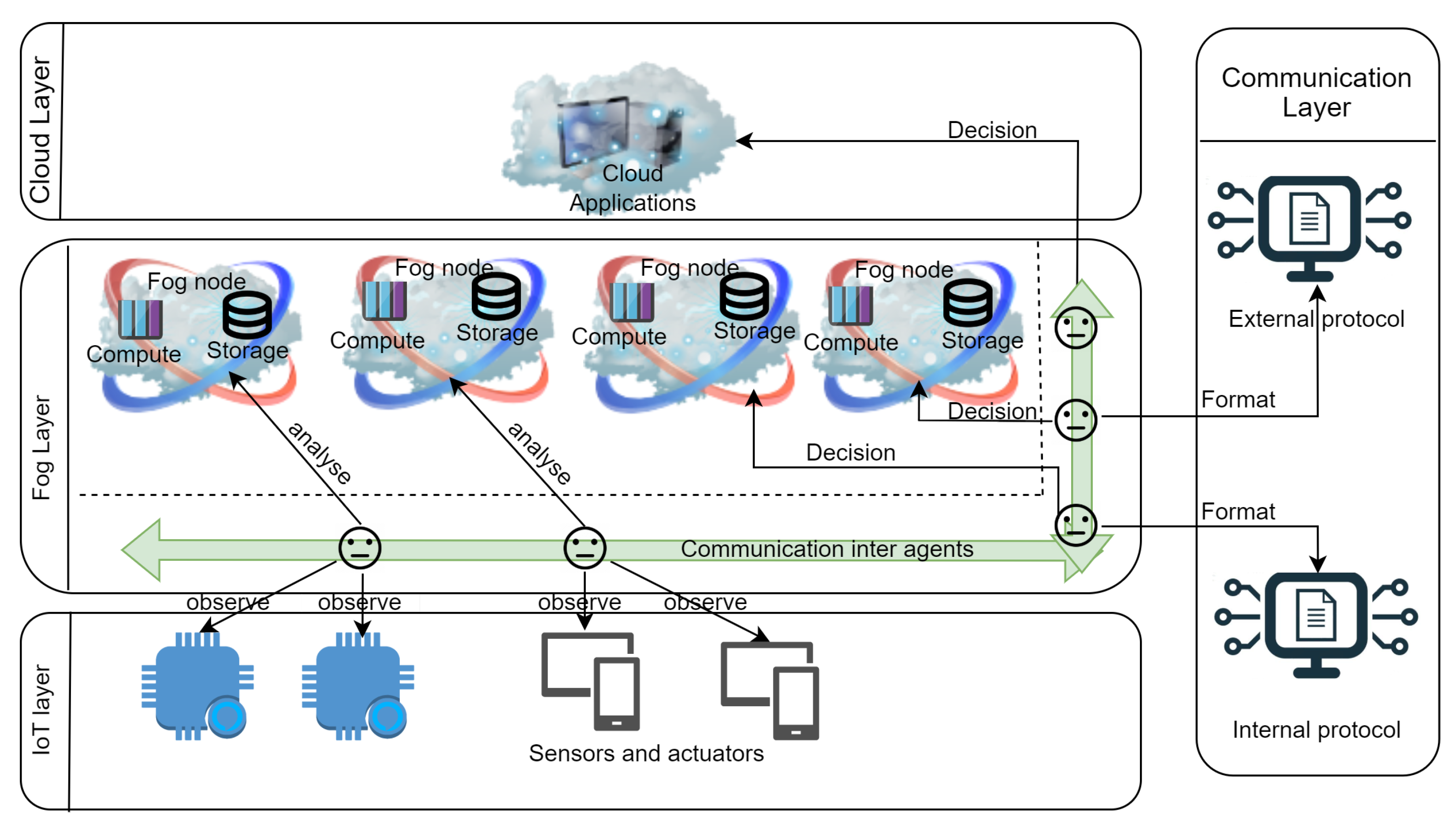
2. Cross-Layer Architecture for Fog Systems
- IoT layer:
- Physical view: represents the different sensors that capture data from the environment and actuators that have a direct impact on it.
- Interactional view: all the devices communicate data with the agents in the layer above.
- Communication layer:
- Physical view: represents external and internal protocols that permit to format and root data from IoT devices to both fog and cloud applications.
- Interactional view: protocols embedded in this layer are used by associated agents to format data for either fog or the cloud.
- Fog layer:
- Physical view: depicts fog nodes responsible for critical computing, as a computing and storage.
- Virtual view: composed of intelligent agents that are responsible for managing the whole system. Each device type in the IoT layer is precisely managed by one agent, and each protocol type in the communication layer is also managed by one agent. The decisions of those agents orchestrate fog nodes and cloud applications. Each agent may observe, analyse, and interact. On the basis of at least one of these actions, the agent acts on the system elements.
- Interactional view: the interaction between agents permits all the agents to communicate between each other. On the other, agents interact with the different system’s elements nodes to analyse data and to make a decision if necessary.
- Cloud layer:
- Physical view: concerns all cloud applications involved in the system.
- Interactional view: reflects the interaction between the agent responsible for making a decision for data that must be treated in the cloud.
- Physical view: .
- Virtual view:.
- Interactional view:
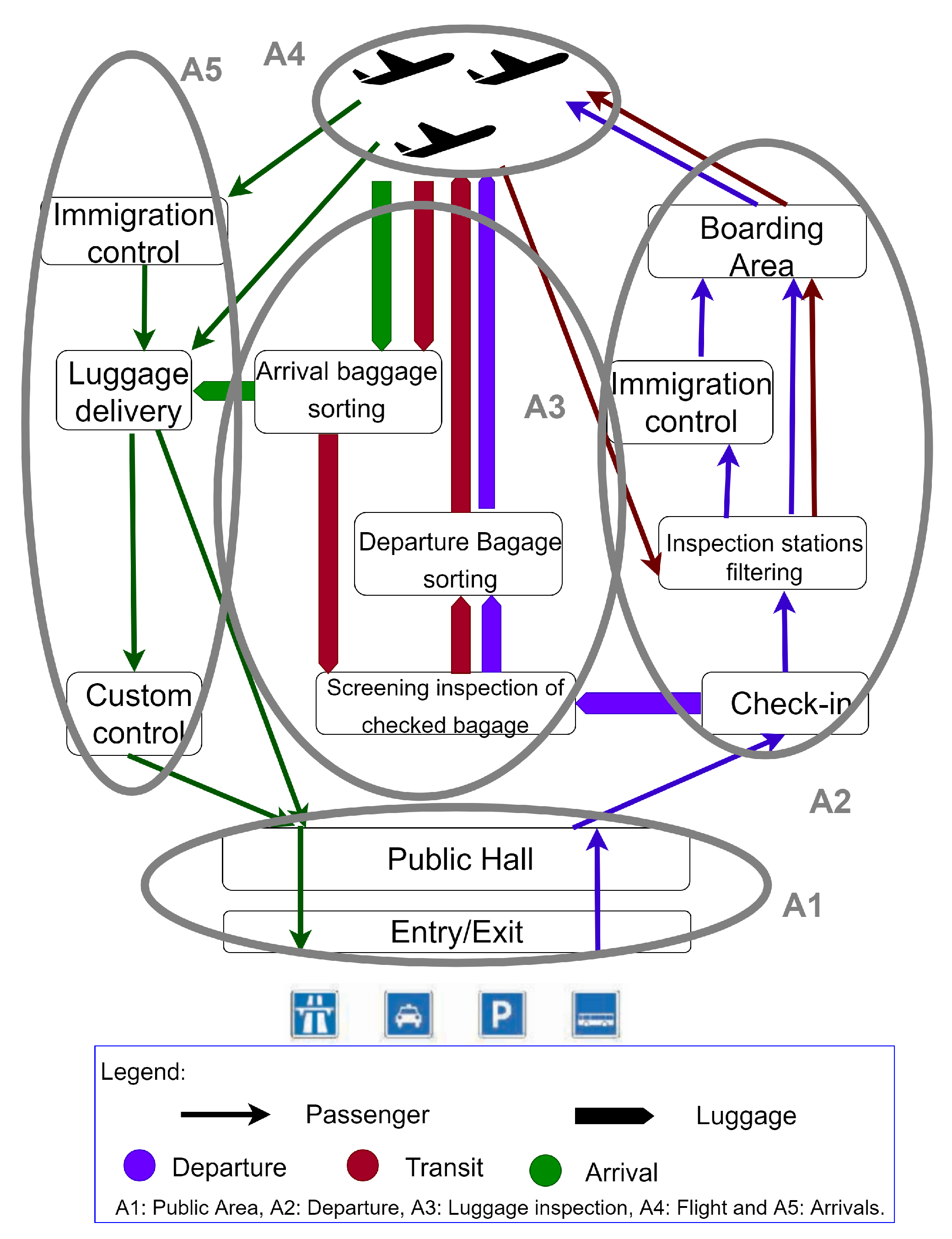
3. Motivating Case Study
- If the lines are busy (by counting the number of trays).
- If bar codes are identifiable.
- If the bags are acceptable; unacceptable bags are round-shaped with long straps and the ones tied with ropes.
- The IoT layer contains three sensors: Bag scanner, Bar-code scanner, and camera in addition to one actuator: Screen.
- The communication layer includes internal protocols that format data using the JSON format, and external protocols format data using XML. Internal protocols are responsible of the communication between layers of a system, and external ones are responsible for the communication between different systems in the network.
- The fog layer comprises two principal fog nodes: Recognition and alert fog nodes and all the agents that are hosted initially in the fog layer, scattered in the fog nodes. In this system, we define three sensor agents , , and (a sensor agent instantiation for each sensor), one fog control agent , two communication control agents and (internal and external communication), and finally one cloud control agent . Each agent manages a physical element of the architecture making a general management of the system.
- The cloud layer is defined by a cloud node responsible for analysing data and storing it.
- ✓
- Physical part
- ✓
- Virtual part
- ✕
- Interactional and control part
- ✕
- Functional properties part
4. BiAgents* Model Specification
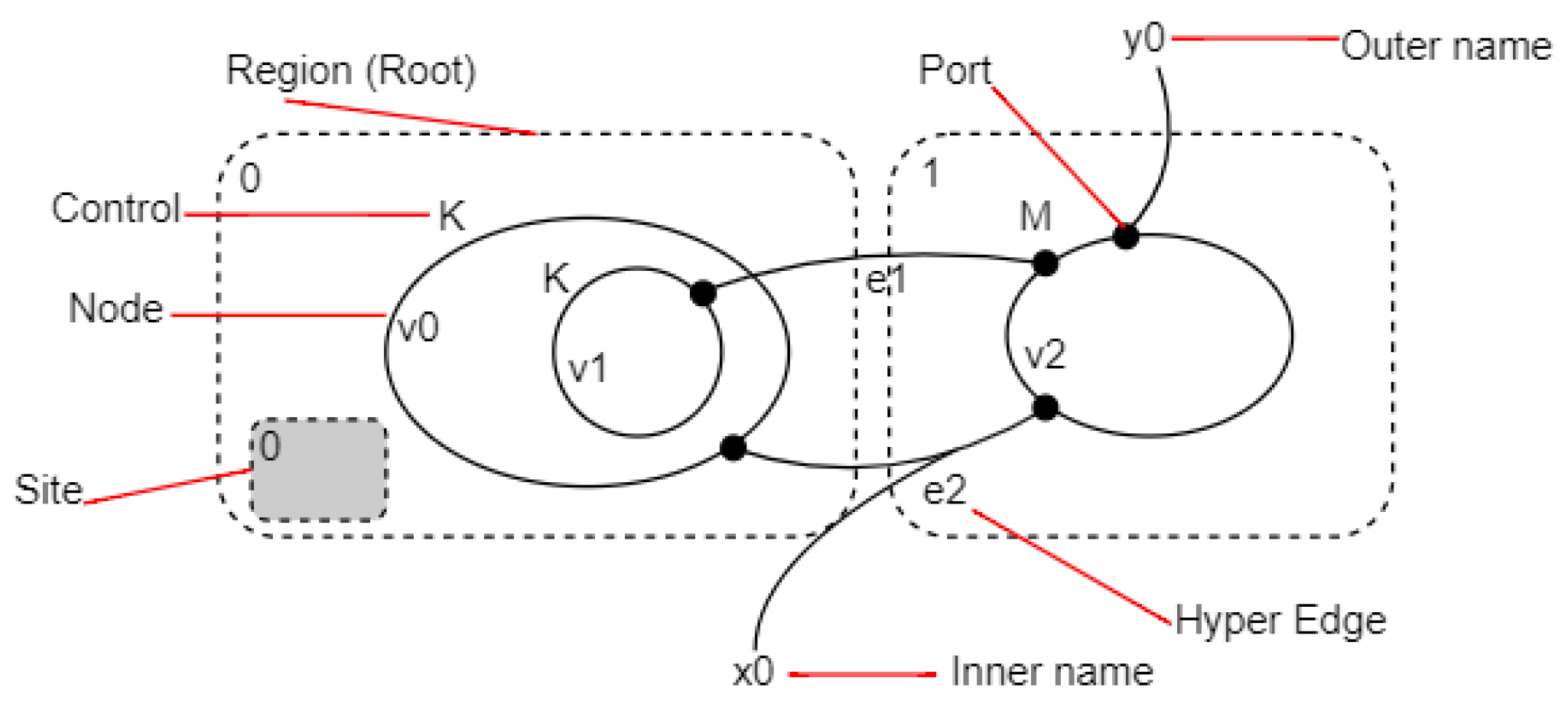
4.1. BRS Overview
4.2. Physical Part Modelling
- is the set of bigraphs representing the fog system’s states, and each bigraph represents a given state of the fog system at some point.
- is the set of labelled reaction rules modelling the different possible transitions from a fog system state to another one. The set of labels is noted .
- is the set of actions with the set of nodes of each bigraph , and each action is related to a specific node belonging to .
- represents the initial physical state of the fog system.
- F is the transition function that the model uses to reach a new state.
4.3. Virtual Part Modelling
- Observation
- –
- is the set of the different system’s states (bigraphs) that the agent observes ().
- –
- is the function of observing a system’s state using the observed bigraph and host, .
- Migration
- –
- is the host of the agent (a bigraphical node or region).
- –
- is the function of migration. agent can move from any part of the system to another, and even though the layers .
- Analysis
- –
- is the function of analysing an information .
- Decision
- –
- is the set of decisions that the agent can take after an analysis () with the set of reaction rules labels.
- Interaction
- –
- is the function of interaction between agents, using the receiver agent , the actual agent sends a message after analysis. .
- –
- is the set of messages received by the agent
- Action
- –
- is the application of a decision taken by an agent after analysis or reception of a message by another agent with the subsets set of .
- –
- is the set of reaction rules that can apply according to a node of the current bigraph; it represents the set of actions that can do in a specific part of the system .
- ; ;
- ,
- “sending to Fog”
- ;
4.4. Smart Behaviour Modelling
- : detection of an abnormal number of bags/trays
- : detection of hacking
- : data destined to analysis
- : detection of hacking
5. Execution and Formal Analysis
5.1. Maude Strategy Presentation
- A functional module implements an equational theory in an extension of order-sorted equational logic called membership equational logic. This theory is mathematically described by a pair (), where is the module’s signature that specifies the sorts, subsorts, kinds, and operators. E is the collection of equations (possibly conditional), and A is the set of equational attributes declared for some operators such as for associative, for commutative, etc.
- A system module that implements a rewrite theory as a triple (), where () is the module’s membership equational theory part, and R is a collection of possibly conditional rewrite rules.
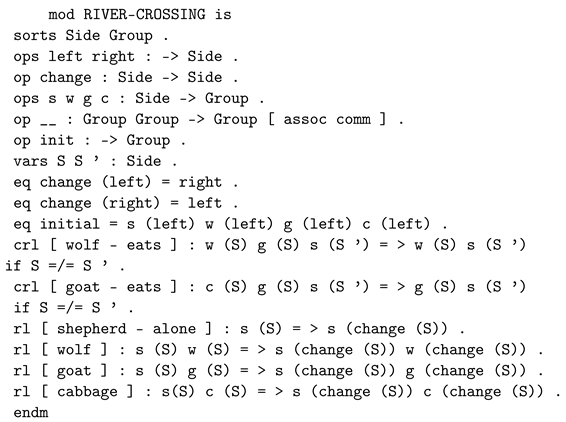

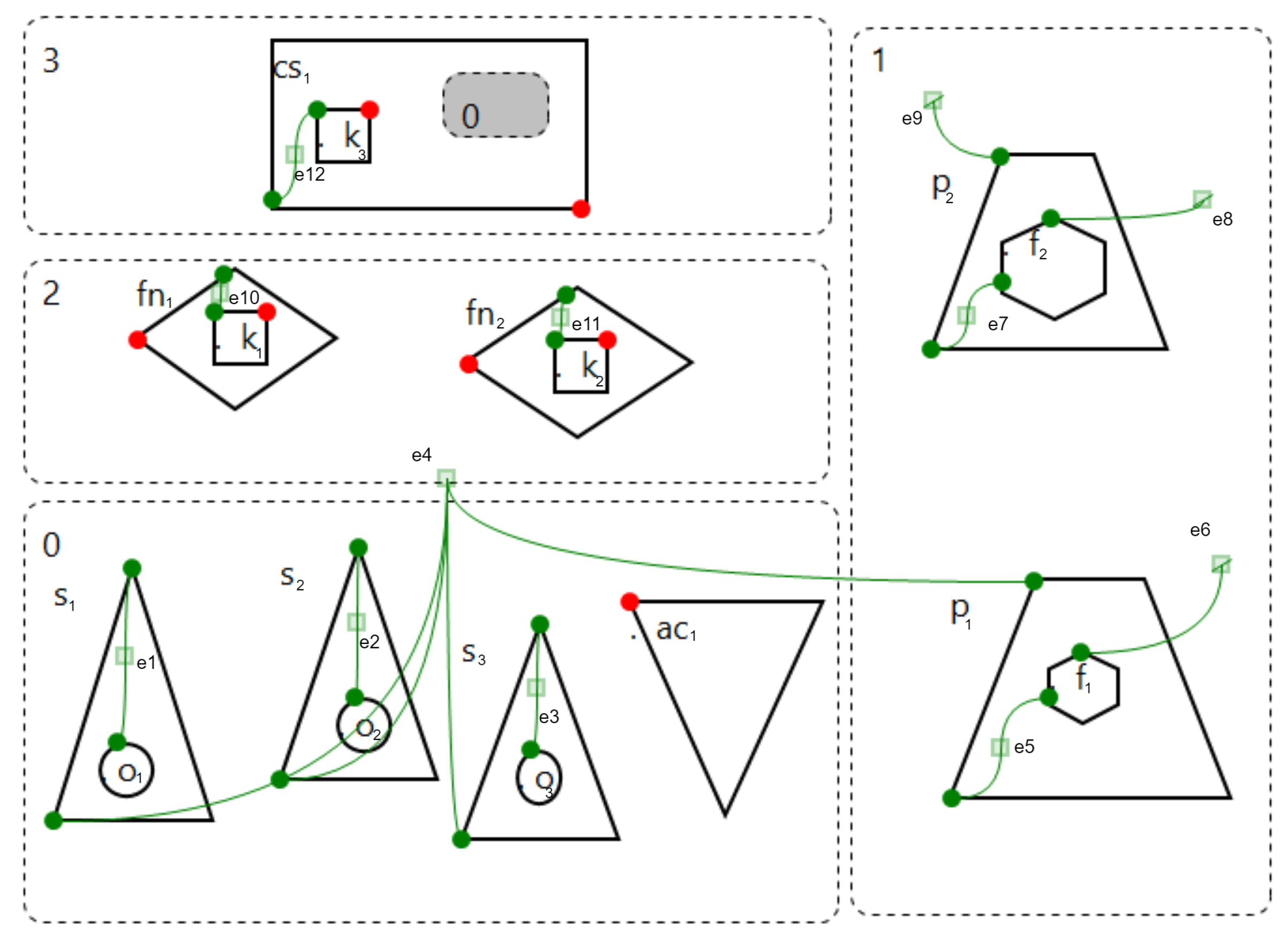
5.2. From BiAgents* to Maude Strategy
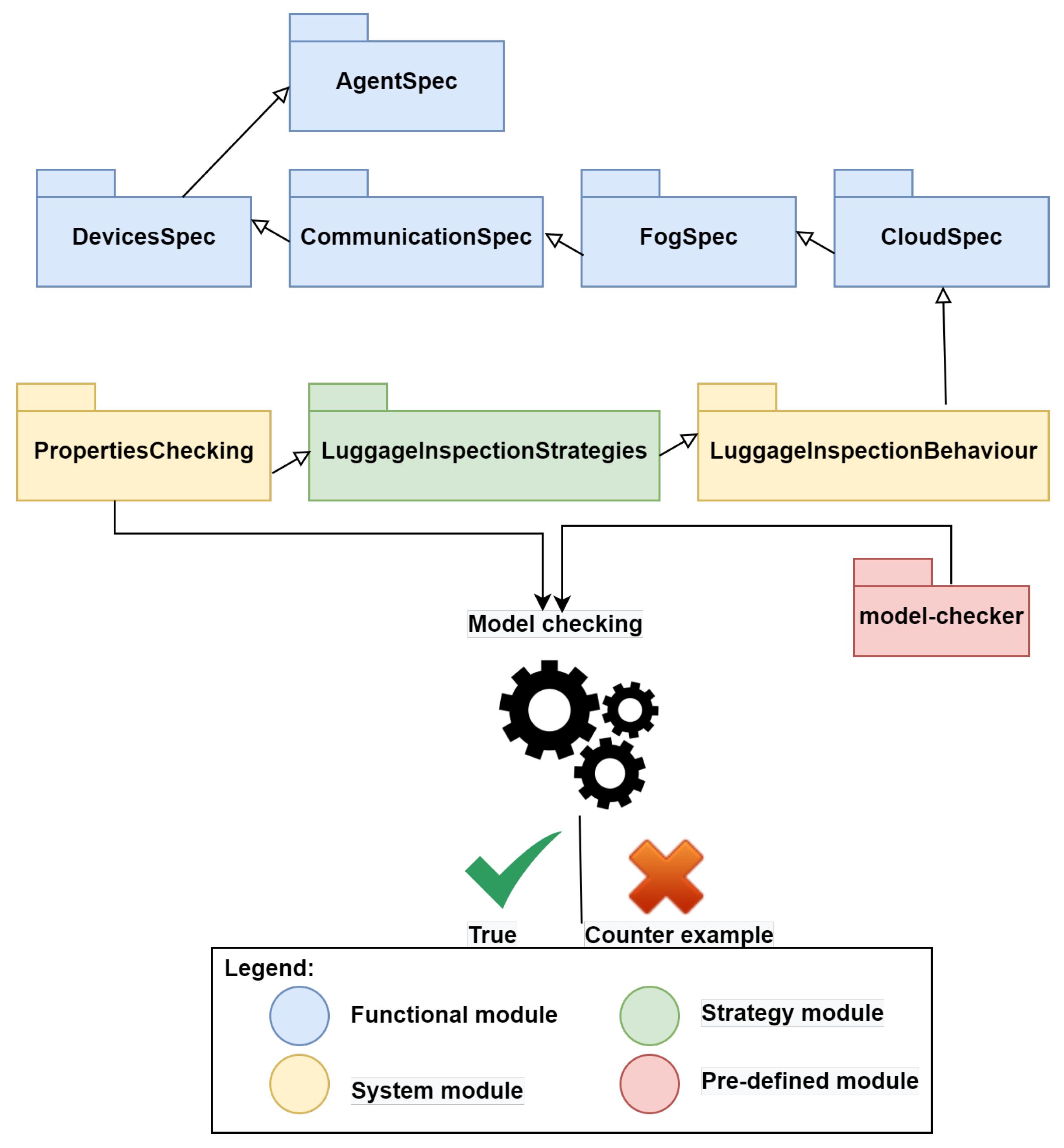
- The functional module contains five sub modules according to the agents and the four regions of the bigraphical model, named: AgentSpec, DevicesSpec, CommunicationSpec, FogSpec, and CloudSpec.
- The system module contains two sub modules named LuggageInspectionBehaviour and PropertiesChecking.
- The strategy module is named LuggageInspectionStrategies.
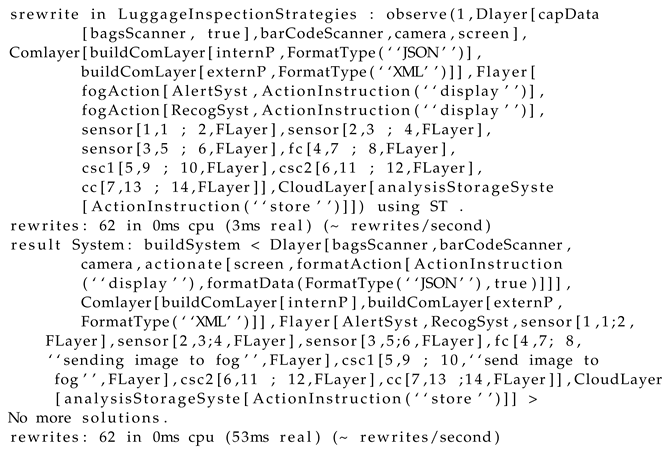
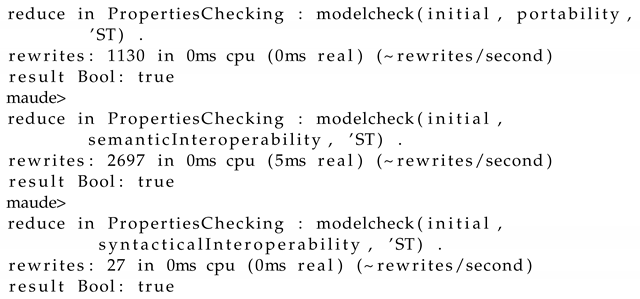
5.3. Lis Formal Analysis
gives a true result confirming the verification of portability property as for the execution of the same command with the properties of semantic and syntactic interoperability. These properties are checked to be true by the mean of the Maude strategy model-checker as given by the following code execution:reduce in PropertiesChecking : modelCheck(initial, portability, ’ST)
6. Related Work
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- IEEE Standard 1934–2018; IEEE Standard for Adoption of OpenFog Reference Architecture for Fog Computing. IEEE: Manhattan, NY, USA, 2018. [CrossRef]
- Ai, Y.; Peng, M.; Zhang, K. Edge computing technologies for Internet of Things: A primer. Digit. Commun. Netw. 2018, 4, 77–86. [Google Scholar] [CrossRef]
- Yi, S.; Hao, Z.; Qin, Z.; Li, Q. Fog computing: Platform and applications. In Proceedings of the 2015 Third IEEE Workshop on Hot Topics in Web Systems and Technologies (HotWeb), Washington, DC, USA, 12–13 November 2015; pp. 73–78. [Google Scholar]
- Mouradian, C.; Naboulsi, D.; Yangui, S.; Glitho, R.H.; Morrow, M.J.; Polakos, P.A. A comprehensive survey on fog computing: State-of-the-art and research challenges. IEEE Commun. Surv. Tutor. 2017, 20, 416–464. [Google Scholar] [CrossRef]
- Asadi, M.; Fathy, M.; Mahini, H.; Rahmani, A.M. An Evolutionary Game Approach to Safety-Aware Speed Recommendation in Fog/Cloud-Based Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2021, 1–10. [Google Scholar] [CrossRef]
- Xiao, Y.; Krunz, M. AdaptiveFog: A Modelling and Optimization Framework for Fog Computing in Intelligent Transportation Systems. IEEE Trans. Mob. Comput. 2021. [Google Scholar] [CrossRef]
- Roig, P.J.; Alcaraz, S.; Gilly, K.; Juiz, C. Modelling a Plain N-Hypercube Topology for Migration in Fog Computing. In Advances in Computing and Network Communications; Thampi, S.M., Gelenbe, E., Atiquzzaman, M., Chaudhary, V., Li, K.C., Eds.; Springer: Singapore, 2021; pp. 595–608. [Google Scholar]
- Abd Elaziz, M.; Abualigah, L.; Ibrahim, R.A.; Attiya, I. IoT Workflow Scheduling Using Intelligent Arithmetic Optimization Algorithm in Fog Computing. Comput. Intell. Neurosci. 2021, 2021, 9114113. [Google Scholar] [CrossRef] [PubMed]
- Souad, M.; Faiza, B.; Nabil, H. Formal Modeling IoT Systems on the Basis of BiAgents* and Maude. In Proceedings of the 2020 International Conference on Advanced Aspects of Software Engineering (ICAASE), Constantine, Algeria, 28–30 November 2020; pp. 1–7. [Google Scholar]
- Milner, R. The Space and Motion of Communicating Agents; Cambridge University Press: Cambridge, UK, 2009. [Google Scholar]
- Pereira, E.; Kirsch, C.; Sengupta, R. Biagentsa bigraphical agent model for structure-aware computation. Cyber-Phys. Cloud Comput. Work. Pap. CPCC Berkeley 2012, 1–13. Available online: http://cpcc.berkeley.edu/papers/paperBiagents12.pdf (accessed on 12 January 2022).
- Eker, S.; Martí-Oliet, N.; Meseguer, J.; Verdejo, A. Deduction, strategies, and rewriting. Electron. Notes Theor. Comput. Sci. 2007, 174, 3–25. [Google Scholar] [CrossRef]
- McKendrick, J. Fog Computing: A New IoT Architecture? 2016. Available online: https://www.rtinsights.com/what-is-fog-computing-open-consortium (accessed on 12 January 2022).
- Iorga, M.; Feldman, L.; Barton, R.; Martin, M.J.; Goren, N.S.; Mahmoudi, C. Fog Computing Conceptual Model; NIST SP, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [Google Scholar]
- Kapsalis, A.; Kasnesis, P.; Venieris, I.S.; Kaklamani, D.I.; Patrikakis, C.Z. A cooperative fog approach for effective workload balancing. IEEE Cloud Comput. 2017, 4, 36–45. [Google Scholar] [CrossRef]
- Moreno-Vozmediano, R.; Montero, R.S.; Huedo, E.; Llorente, I.M. Cross-site virtual network in cloud and fog computing. IEEE Cloud Comput. 2017, 4, 46–53. [Google Scholar] [CrossRef]
- Bouheroum, A.; Benzadri, Z.; Belala, F. Towards a formal approach based on bigraphs for fog security: Case of oil and gas refinery plant. In Proceedings of the 2019 7th International Conference on Future Internet of Things and Cloud (FiCloud), Istanbul, Turkey, 26–28 August 2019; pp. 64–71. [Google Scholar]
- Marir, S.; Belala, F.; Hameurlain, N. A formal model for interaction specification and analysis in IoT applications. In Proceedings of the International Conference on Model and Data Engineering, Marrakesh, Morocco, 24–26 October 2018; pp. 371–384. [Google Scholar]
- Sales, M. The Air Logistics Handbook: Air Freight and the Global Supply Chain; Routledge: London, UK, 2013. [Google Scholar]
- da Rocha, H.; Espirito-Santo, A.; Abrishambaf, R. Semantic interoperability in the industry 4.0 using the IEEE 1451 standard. In Proceedings of the IECON 2020 the 46th Annual Conference of the IEEE Industrial Electronics Society, Singapore, 18 November 2020; pp. 5243–5248. [Google Scholar]
- Petcu, D.; Vasilakos, A.V. Portability in clouds: Approaches and research opportunities. Scalable Comput. Pract. Exp. 2014, 15, 251–270. [Google Scholar] [CrossRef][Green Version]
- Damgaard, T.C.; Birkedal, L. Axiomatizing binding bigraphs. Nord. J. Comput. 2006, 13, 58. [Google Scholar]
- Krivine, J.; Milner, R.; Troina, A. Stochastic bigraphs. Electron. Notes Theor. Comput. Sci. 2008, 218, 73–96. [Google Scholar] [CrossRef]
- Sevegnani, M.; Calder, M. BigraphER: Rewriting and analysis engine for bigraphs. In Proceedings of the International Conference on Computer Aided Verification, Toronto, ON, Canada, 17–23 July 2016; pp. 494–501. [Google Scholar]
- Grohmann, D.; Miculan, M. Directed bigraphs. Electron. Notes Theor. Comput. Sci. 2007, 173, 121–137. [Google Scholar] [CrossRef][Green Version]
- Perrone, G.; Debois, S.; Hildebrandt, T. Bigraphical refinement. arXiv 2011, arXiv:1106.4091. [Google Scholar] [CrossRef][Green Version]
- Clavel, M.; Durán, F.; Eker, S.; Lincoln, P.; Martı-Oliet, N.; Meseguer, J.; Talcott, C. Maude Manual (Version 2.1); SRI International: Menlo Park, CA, USA, 2005. [Google Scholar]
- Martí-Oliet, N.; Meseguer, J.; Verdejo, A. A rewriting semantics for Maude strategies. Electron. Notes Theor. Comput. Sci. 2009, 238, 227–247. [Google Scholar] [CrossRef]
- Cherfia, T.A.; Belala, F. Bigraphical reactive systems based approaches for modeling context-aware systems. Int. J. Adapt. Resilient Auton. Syst. (IJARAS) 2014, 5, 1–19. [Google Scholar] [CrossRef][Green Version]
- Khebbeb, K.; Hameurlain, N.; Belala, F. Formalizing and simulating cross-layer elasticity strategies in Cloud systems. Clust. Comput. 2020, 23, 1603–1631. [Google Scholar] [CrossRef]
- Laouadi, M.A.; Mokhati, F.; Seridi-Bouchelaghem, H. A formal framework for organization-centered multi-agent system specification: A rewriting logic based approach. Multiagent Grid Syst. 2017, 13, 395–419. [Google Scholar] [CrossRef]
- Metelo, A.; Braga, C.; Brandão, D. Towards the modular specification and validation of cyber-physical systems. In Proceedings of the International Conference on Computational Science and Its Applications, Melbourne, Australia, 2–5 July 2018; pp. 80–95. [Google Scholar]
- Fadlisyah, M.; Ölveczky, P.C. The HI-Maude tool. In Proceedings of the International Conference on Algebra and Coalgebra in Computer Science, Warsaw, Polan, 3–6 September 2013; pp. 322–327. [Google Scholar]
- Ölveczky, P.C. Real-Time Maude 2.3 Manual. Research Report. 2004. Available online: http://urn.nb.no/URN:NBN:no-35645 (accessed on 12 January 2022).
- Venckauskas, A.; Stuikys, V.; Damasevicius, R.; Jusas, N. Modelling of Internet of Things units for estimating security-energy-performance relationships for quality of service and environment awareness. Secur. Commun. Netw. 2016, 9, 3324–3339. [Google Scholar] [CrossRef]
- Mutlag, A.A.; Ghani, M.K.A.; Mohammed, M.A.; Lakhan, A.; Mohd, O.; Abdulkareem, K.H.; Garcia-Zapirain, B. Multi-Agent Systems in Fog–Cloud Computing for Critical Healthcare Task Management Model (CHTM) Used for ECG Monitoring. Sensors 2021, 21, 6923. [Google Scholar] [CrossRef] [PubMed]
- Murtaza, F.; Akhunzada, A.; ul Islam, S.; Boudjadar, J.; Buyya, R. QoS-aware service provisioning in fog computing. J. Netw. Comput. Appl. 2020, 165, 102674. [Google Scholar] [CrossRef]
- Chen, X.; Ding, J.; Lu, Z.; Zhan, T. An Efficient Formal Modeling Framework for Hybrid Cloud-Fog Systems. IEEE Trans. Netw. Sci. Eng. 2020, 8, 447–462. [Google Scholar] [CrossRef]
- Guo, Y.; Zhang, Z.; Guo, Y. Fog-centric authenticated key agreement scheme without trusted parties. IEEE Syst. J. 2020, 15, 5057–5066. [Google Scholar] [CrossRef]
- Sahli, H.; Ledoux, T.; Rutten, É. Modeling self-adaptive fog systems using bigraphs. In Proceedings of the International Conference on Software Engineering and Formal Methods, Oslo, Norway, 16–20 September 2019; pp. 252–268. [Google Scholar]
- Benzadri, Z.; Bouheroum, A.; Belala, F. A Formal Framework for Secure Fog Architectures: Application to Guarantee Reliability and Availability. Int. J. Organ. Collect. Intell. (IJOCI) 2021, 11, 51–74. [Google Scholar] [CrossRef]
- Khebbeb, K.; Hameurlain, N.; Belala, F. A maude-based rewriting approach to model and verify cloud/fog self-adaptation and orchestration. J. Syst. Archit. 2020, 110, 101821. [Google Scholar] [CrossRef]
- Zahra, S.; Alam, M.; Javaid, Q.; Wahid, A.; Javaid, N.; Malik, S.U.R.; Khan, M.K. Fog computing over IoT: A secure deployment and formal verification. IEEE Access 2017, 5, 27132–27144. [Google Scholar] [CrossRef]

| Layer | IoT | Communication | Fog | Cloud | |
|---|---|---|---|---|---|
| Entities | |||||
| Physical | • Bar-code scanner • Bags scanner • Camera • Screens | • Internal protocols • External protocols | • Alert system • Recognition system | • Analysis and storage cloud service | |
| Virtual | / | / | Agents: | / | |
| Interactions | • Bar-code scanner and internal protocols • Bags scanner and internal protocols • Camera and internal protocols • Bar-code scanner and external protocols • Bags scanner and External protocols • Camera and external protocols | • Internal protocols and alert system • Internal protocols and recognition system • External protocols and analysis and storage cloud service | • Alert system and screens • Recognition system and screens • and • and • and • and • and • and | • Analysis and storage Cloud service and screens | |
| CLA4Fog | BiAgents* Specification |
|---|---|
| IoT layer | Region 0 |
| • Physical view: sensors, actuators, etc. • Interactional view: connexions with communication layer | • Place graph • Link graph |
| Communication layer | Region 1 |
| • Physical view: protocols, etc. • Interactional view: connexions with fog layer and cloud layer | • Place graph • Link graph |
| Fog layer | Region 2 |
| • Physical view: Fog nodes, routers, etc. • Virtual view: agents, process, etc. • Interactional view: connexions with the other layers and communications between agents | • Place graph • Agents (observe, analyse control, migrate) • Link graph and agents (interaction) |
| Cloud layer | Region 3 |
| • Physical view: Cloud systems, apps, etc. • Interactional view: Connexions with the other layers | • Place graph • Link graph |
| LIS Element | Arity | Sort |
|---|---|---|
| IoT layer (region 0) | ||
| Bags scanner | 2 | i |
| Bar-code scanner | 2 | i |
| Camera | 2 | i |
| Screen | 1 | k |
| Captured data | 2 | e |
| Fog layer (region 1) | ||
| Alert system | 2 | f |
| Recognition system | 2 | f |
| Communication layer (region 2) | ||
| Internal communication protocol | 2 | c |
| External communication protocol | 2 | c |
| Data formats | 2 | o |
| Cloud layer (region 3) | ||
| Cloud services | 2 | a |
| Instructions | 1 | x |
| Rule | Description |
|---|---|
| All children of i nodes have sort e | |
| All children of k nodes have sort x | |
| All children of x nodes have sort o | |
| All children of o nodes have sort e | |
| All children of f nodes have sort | |
| All children of c nodes have sort | |
| All children of a nodes have sort | |
| In an x node, one port may be linked to a node | |
| In an o node one port is always linked to an e node, and the other may be linked to a node | |
| All children of a 0-region have sort in | |
| All children of a 1-region have sort c | |
| All children of a 2-region have sort f | |
| All children of a 3-region have sort a | |
| All e nodes are atomic |
| Layers | Rule Description | Algebraic Form |
|---|---|---|
| IoT → Communication | Send data to internal protocol | ((s.o)|id‖(p1.f1)|(p2.f2)|id)→(s|id)‖(p1.(f1|o))|(p2.f2)|id |
| Send data to external protocol | ((s.o)|id‖(p1.f1)|(p2.f2)|id)→(s|id)‖(p1.f1)|(p2.(f2|o))|id | |
| Communication | Delete data from internal protocol | (s|id)‖(p1.(f1|o))|(p2.f2)|id→(s|id)‖(p1.f1)|(p2.f2)|id |
| Delete data from external protocol | (s|id)‖(p1.f1)|(p2.(f2|o))|id→(s|id)‖(p1.f1)|(p2.f2)|id | |
| Format data according to internal communication protocol | (p1.(f1|o))|(p2.f2)|id→(p1.(f1.o))|(p2.f2)|id | |
| Format data according to external communication protocol | (p1.f1)|(p2.(f2|o))|id→(p1.f1)|(p2.(f2.o))|id | |
| Communication → Fog | Send formatted data to fog layer | (p1.(f1.o))|id‖(fn1.k1)|(fn2.k2)|id→p1|id‖(fn1.k1)|(fn2.k2)|(f1.o)|id |
| Fog | Create instruction in the recognition system | (fn1.k1)|(fn2.k2)|(f1.o)|id→(fn1.(k1.(f1.o)))|(fn2.k2)|id |
| Create instruction in the alert system | (fn1.k1)|(fn2.k2)|(f1.o)|id→(fn1.k1)|(fn2.(k2.(f1.o)))|id | |
| Fog → IoT | Send instruction from the recognition system to the actuator | ac1|id‖fn1.(k1.(f1.o)))|(fn2.k2)|id→(ac1.(k1.(f1.o)))|id‖fn1|(fn2.k2)|id |
| Send instruction from the alert system to the actuator | ac1|id‖(fn1.k1)|(fn2.(k2.(f1.o)))|id→(ac1.(k2.(f1.o)))|id‖(fn1.k1)|fn2|id | |
| Communication → Cloud | Send formatted data to the cloud layer | (p2.(f2.o))|id‖(cs1.(k3|d1))|id→p2|id‖(cs1.(k3|d1)|(f2.o))|id |
| Cloud | Create instruction in the analysis and storage system | (cs1.(k3|d1)|(f2.o))|id→(cs1.((k3.(f2.o))|d1))|id |
| Cloud → IoT | Send instruction from the cloud to the actuator | ac1|id‖(cs1.((k3.(f2.o))|d1))|id→(ac1.(k3.(f2.o)))|id‖(cs1.d1)|id |
| Possible LIS Behaviour | Trace Definition |
|---|---|
| Send data to internal communication protocol | |
| Send data to external communication protocol | |
| Treatment of captured data destined to fog nodes | |
| Trigger action according to the recognition system | |
| Trigger action according to the alert system | |
| Treatment of captured data destined to cloud systems | |
| Trigger action according to the analysis system | |
| Detection of hacking the fog nodes | |
| Detection of hacking the cloud systems |
| Traces Projections on Agents |
|---|
| Projection on |
or or |
| Projection on |
| Projection on |
| Projectionon |
| Projection on |
| Projection on |
| Projection on |
| Projection on |
| Projection on |
| BiAgents* Model | Maude Strategy Specification |
|---|---|
| Physical Structure | |
| Sorting discipline | sorts Agent Sensor Actuator Action DLayer ComLayer Protocol Flayer ClLayer. |
| Reaction rules | Conditional rewrite rules of the form: crl [rewrite-rule-name] : term term’ if condition. Rewrite rules of the form: rl [rewrite-rule-name] : term term’ |
| Parent function | Operation of the form: op parent [_,_] : Parent Child Parent. |
| Virtual Structure | |
| Agents’ behaviour | op observe (_,_) : Nat Host System. op analyse (_,_) : Nat Data Bool. op interaction (_,_,_) : Nat Nat String System. op mgrt(_,_,_) : Nat Host Host System. crl [action] : term term’ if decision. |
| Smart behaviour Traces | |
| Global Traces | Composed Strategy with operators(| ; ...) strat ST @ System. sd ST (ST1 | ST2 | ... | ST9) *. |
| Projections | Defined Simple Strategies strat ST1 @ System. strat S1 @ System. ... ST1 (S1 ; S11 ; S41 ; S411). S1 (observation1 ; migration1). ... |
| Property | Comments | LTL Definition |
|---|---|---|
| Portability of data | Captured data must have the ability to move through the different elements of the system | |
| Syntactical Interoperability | Data must be formatted after capture and this format must be understandable by the treatment nodes of the system and actuators. | |
| Semantic interoperability | Any transmitted information in many types of systems and sub systems must be a meaningful information (a meaningful information is an information that can be analysed by an agent |
| Predicate | Definition |
|---|---|
| Data are hosted in a sensor | |
| Data are hosted in a communication protocol | |
| Data are hosted in the alert fog node | |
| Data are hosted in the recognition fog node | |
| Data are hosted in a cloud system | |
| Data are hosted in an actuator | |
| Format is hosted in alert fog node’s action | |
| Format is hosted in recognition fog node’s action | |
| Format is hosted in cloud system’s action | |
| Format is hosted in action that is hosted in actuator | |
| Sensor agent 1 analyses information | |
| Sensor agent 2 analyses information | |
| Sensor agent 3 analyses information | |
| Internal communication security control agent analyses format of information | |
| External communication security control agent analyses format of information | |
| Fog control agent analyses information | |
| Cloud control agent analyses information |
| Approaches | Formalism | Modelling | Simulation/ Analysis | Genericity | ||
|---|---|---|---|---|---|---|
| Physical | Virtual | Behavioural | ||||
| Venckauskas et al., 2016 [35] | FAMILIAR DSL | ✕ | ✕ | ✓ | SPLOT | ✓ |
| Mutlag et al., 2021 [36] | Multi-agents system | ✕ | ✓ | ✓ | iFogSim | ✕ |
| Murtaza et al., 2020 [37] | Timed automata | ✕ | ✓ | ✓ | iFogSim/ UPPAL Model checker | ✓ |
| Chen et al., 2020 [38] | Process algebra (PEPA) | ✓ | ✓ | ✕ | Stochastic simulation | ✓ |
| Guo et al., 2020 [39] | Process algebra (ROR) | ✕ | ✕ | ✓ | ROR | ✕ |
| Sahli et al., 2019 [40] | BRS | ✓ | ✕ | ✓ | ✕ | ✓ |
| Benzadri et al., 2021 [41] | CA-BRS | ✓ | ✓ | ✓ | Maude | ✕ |
| Khebbeb et al., 2020 [42] | Rewriting logic | ✓ | ✕ | ✓ | Maude | ✓ |
| Zahra et al., 2017 [43] | High-level petri nets | ✓ | ✕ | ✕ | Z3 for SMT | ✕ |
| This work | BiAgents* | ✓ | ✓ | ✓ | Maude strategy | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Marir, S.; Belala, F.; Hameurlain, N. A Strategy-Based Formal Approach for Fog Systems Analysis. Future Internet 2022, 14, 52. https://doi.org/10.3390/fi14020052
Marir S, Belala F, Hameurlain N. A Strategy-Based Formal Approach for Fog Systems Analysis. Future Internet. 2022; 14(2):52. https://doi.org/10.3390/fi14020052
Chicago/Turabian StyleMarir, Souad, Faiza Belala, and Nabil Hameurlain. 2022. "A Strategy-Based Formal Approach for Fog Systems Analysis" Future Internet 14, no. 2: 52. https://doi.org/10.3390/fi14020052
APA StyleMarir, S., Belala, F., & Hameurlain, N. (2022). A Strategy-Based Formal Approach for Fog Systems Analysis. Future Internet, 14(2), 52. https://doi.org/10.3390/fi14020052







