Abstract
Even though both internet-of-cloud services and biometric systems (BSs) are used worldwide, popular and expanded among public and private services, their utilization has not been extended among Greek users, and in particular within Greek HEIs. This paper aims to examine the University of the Aegean (UA) students’ perceptions, especially on BS acceptance, determining the impact of their sociodemographic characteristics toward this. An online instrument was developed based on constructs of technology acceptance models, and previous research focused on BS acceptance, including a great variety of sociodemographic variables. The authors collected 768 complete responses to explore the social and demographic attributes that impact on students’ BS acceptance through exploratory descriptive research. This study found that several UA students’ sociodemographic attributes are linked to their BS acceptance. Specifically, gender, age, study level, year of study, professional profile and fathers’ occupation are useful to determine which students’ groups are in favor of BS, while employment status, annual income and mothers’ occupation are weak toward this. Security and privacy concerns are indicated to influence users’ BS acceptance as well. This study provides a unique approach to better understanding the Greek students’ BS acceptance, with important implications for improved BS marketing in Greece in synergy with the internet-of-cloud services and their potential adoption in HEIs internal settings. It also provides developers with further knowledge for security and privacy non-functional requirements in order to increase users’ acceptance and to address these challenges within the internet of cloud.
1. Introduction
Recently, the internet of cloud has been acknowledged as one of the most evolving technologies. The interrelation between internet and cloud services has emerged because of the cloud’s attributes that directly advantage its development. However, adopting cloud services has brought new challenges, especially concerning security and privacy issues. In this regard, research in this area has to consider the synergy among other technologies, such as biometrics, in order to enhance the development of the internet of cloud. Considering that cloud and biometrics are different but significant resources on their own, when developed in combination, innovative industrial security solutions can be delivered, with several potential advantages, such as scalability, cost-effectiveness, consistency and omnipresent access to private data and services [1].
Biometrics may offer a thought-provoking frame for addressing the internet-of-cloud challenges, playing a significant role in securing a wide range of its services. In particular, an increasing development of biometric systems (BSs) has been noted, as a promising solution to address users’ accurate identification and safety [2] in several services, influencing society as well [3]. BS implementation is considered an adequate measure for providing protection against crime and cybercrime [4], while biometric recognition is indicated to be used as a scientific tool for solving criminal activities [5]. Thus, since BSs are totally dependent on handling personal information, they confront challenges compared to traditional methods of person authentication, mainly as far as public perception and social acceptance of these technologies are concerned [6]. Respectively, BS quality and reliability are dependent on users’ awareness, acceptance and satisfaction about them [3]. In this regard, a major challenge is also the providing of BS implementation in a user-friendly way [7]. Users’ issues are greatly involved in the deployment of BS, and without identifying their knowledge, insights and perceptions about BS, their installation is hardly to be achieved. If users’ beliefs and fears are not considered during elaboration, while security and privacy concerns are not addressed, then there are great possibilities for BSs to fail [5].
Users have several concerns, supporting that BSs may violate their privacy and individual rights, leading, for example, to potential fraud, identity theft, civil liberty violations and inaccuracy of data. These perceptions result in emerging conflicts among service providers and users as far as BS acceptance is concerned [4]. Therefore, both users’ acceptance and the safety issues deriving from BS deployment cannot be negotiated. It is of major importance to identify those since when these data security and privacy issues arise, the reliability of users is affected [3]. Identifying these issues, users’ willing to adopt BS in daily life is expected to be increased [5].
However, the majority of previous research that has examined various physical and behavioral biometric techniques (e.g., fingerprint, hand geometry, signature, and keystroke) has concentrated on technical factors and on the usability of its technique separately. As previous literature has already highlighted, users’ BS acceptance has not adequately been investigated [8,9,10], and deeper analysis of users’ social and demographic attributes is fragmentary or ignored. Thus, the accuracy and reliability of BSs are immensely important in contemporary crime, cybercrime protection and cyber security. Therefore, in order for these challenges, when deploying such technologies, to be addressed, holistic solutions are needed, which satisfy the users by considering the main key factors correlated with their acceptance, such as knowledge, trust, and privacy concerns [5]. Consequently, the further examining of users’ social and demographic attributes, which is lacking in previous research, will provide a deeper understanding regarding the factors that affect their BS acceptance and will lead to the development of new BS methodologies that are more user-oriented.
Considering this research gap, as well as the fact that BS adoption in Greece, both in public and private services, is still in an early stage, this paper attempts to go beyond the existing literature for the Greek cases by examining the University of the Aegean (UA) students’ case. University of the Aegean is a regional university, located in six islands, serving a large number of students, coming from all country’s regions, and therefore valuable insights can be provided that will help developers to produce new designs regarding the BS methods and techniques.
Our study aims to identify which are the students’ perceptions on the BS acceptance, by deploying exploratory research through a quantitative instrument, based on constructs of technology-acceptance models and previous research on BS acceptance. To our best knowledge, such a large-scale study on Greek users has not been elaborated yet, despite such studies having been conducted in other countries. Therefore, our survey, as a descriptive research design, targets to gain information about students’ views on the acceptance and adoption of BSs, allowing trends to be identified and analyzed and examining how different demographics respond to different variables [11]. In this regard, despite the acknowledged limitation that no further empirical analysis has been provided, we support that the data collected and analyzed in a descriptive way provide a base for further research, helping to obtain a comprehensive understanding regarding the factors which affect this. Summarizing the insights gained from the UA students, our research shows that specific social and demographic attributes, namely gender, age, study level, year of study, professional profile and fathers’ occupation are associated with students willing to use BS, while highly privacy and social concerns are indicated, contributing to the overall enhancement of the emerging literature in BS acceptance and adoption. For instance, and not surprisingly, due to unfamiliarity with BS in Greece, it is indicated that almost half of the students were not aware of BS (49%) before this survey. Among the BS-familiar students, the fingerprint (97%) and facial recognition techniques (91%) have been adopted in their daily practices, concerning specifically the unlocking of their mobile phones, while the most non-familiar technique is keystroke analysis. In particular, women (64%) consider the accurate recognition to be the most important advantage of BS deployment. Furthermore, age, employment status and father’s occupation act as differentiators regarding BS security and privacy concerns. The age group of 18–22 declares a greater concern for personal data risks (55%) compared to the rest of the groups, while all of the students (100%), working as private employees, are concerned that their registered data due to BS, can be easily accessed by third parties. University of the Aegean students are skeptical regarding services that use their biometric information due to the possibility for their security and privacy to be violated.
Despite the BS early exploitation in Greece, their use in Greek HEIs internal areas is a feasible scenario, provided that skepticism about data security and privacy protection should be taken into consideration, while the creation of technical and safety standards will be ensured. For determining and measuring the factors that affect students’ BS acceptance from their own perspective, the results show that Greek students are willing to use BS techniques if the concerns that they face can be addressed.
In this regard, our findings contribute to increasing situational awareness against BS deployment and the newly introduced cyber security and privacy threats regarding BS, helping developers to design more user-attractive, security, and privacy-oriented BS systems that satisfy users’ non-functional requirements, in order to increase their acceptance. As previous literature argues [3], issues met by the BS users should be solved instantly since BS prevalence is growing worldwide.
Furthermore, the results are beneficial for Greek HEIs, indicating the need for the development of BS training programs addressed to their students and of an improved marketing policy as well as for seizing the opportunity to upgrade their safety services, by investing in BSs that satisfy students.
The rest of the paper is organized as follows. Section 2 is divided into three subsections. The first one addresses work regarding the development of biometrics models and users’ BS acceptance within public and private services, while it presents the statement of interest and the raised research questions. The third subsection presents the research field, the methodology followed, and the implemented instrument. In Section 3, the results of our survey are outlined, indicating students’ sociodemographic profile and their perceptions regarding BS knowledge, adoption, usability, reliability and their intention of use, as well as their security, privacy and social control concerns. Section 4 discusses the main findings. Finally, Section 5 concludes our findings and raises future research directions.
2. Materials and Methods
The research study entitled “Acceptance and Adoption of Biometric Systems of the Students of the University of the Aegean” was approved by the Rector and the Vice Rector of the University of the Aegean, since the data were collected and stored anonymously, according to the Code of Ethics of the University of the Aegean.
2.1. Related Work on Biometric Systems and Users’ Acceptance
Biometric systems (BS) concern technologies that authenticate individuals’ credentials, accordingly to their biometric information. This refers to a persons’ characteristics, which do not change over time, such as fingerprints, iris or palm veins [12], as well as their behavioral characteristics, including signature, voice, keystroke and pointing, so that the procedure of identity authentication is deployed with further accuracy [10,13]. BSs are determined by specific characteristics, such as (a) universality, by which each individual owns an acknowledged feature; (b) individuality, by which each individual has a single recognition; (c) circumvention, where the identification process is changeless to deceitful samples; (d) performance, where a high accuracy is achieved in short time; and (e) collectability, where the process is easily performed [14,15]. These provide them with unique advantages. Therefore, BSs provide two main procedures: identification and the verification. Identification is more compound since it concerns not only users’ authenticating through a one-to many process of equating their information to many samples of the BS database, but also users’ identity certification [16]. The verification is considered a one-to one process by which users’ information is compared to existing samples. In general, BSs are thought to be more obtainable in comparison to other identification tools or methods [6]. Furthermore, they are considered to be among the most secure solutions for individuals’ verification [12,17] in various public or private services, such as airports, banks, communication, learning environments. Among biometric approaches, previous research [18,19] argues that the fusion of multimodal biometric techniques, in contrast to single modality ones, provides better results by using multiple combinations for users’ authentication. In this respect, several works [13,14,20,21,22,23,24,25,26], described as follows, have been developed in order to provide individuals with accurate and secure BS for several services, such as using mobile phones, health services, e-learning, airports and banking. For instance, a multimodal system for face and speech recognition, using fuzzy logic for training five images of face and speech via MATLAB, was developed by Ref. [20]. This aims at providing help for physicians to treat their patients, achieving an accuracy of 98%. Ref. [14] proposed a multimodal biometric system, focusing on a persons’ left and right palmprint images for identification, aiming at increasing accuracy and overcoming unimodal methods’ limitations by using evolutionary algorithms, such as genetic algorithms (GAS) and backtracking search algorithm (BSA). The benefits of this procedure, by choosing the relevant features concerning the increasing of the recognition accuracy (99.17) and the reducing of the feature set size, are saving runtime and highlighting the effectiveness and robustness of the proposed multimodal biometrics system compared to other unimodal ones. Ref. [21] developed a multi-biometric system for continuous student authentication within e-learning platforms, by performing a score-level fusion of different biometric responses (face, voice, touch, mouse, and keystroke), based on the device used. Ref. [22] developed a baseline gait-based authentication system (GBAS) by integrating a digital treadmill to control gait characteristics in an attack scenario. After collecting users’ walking patterns through a smartphone, they tested GBAS performance after three attack trials, utilizing five machine-learning algorithms, achieving significantly degraded performance. Ref. [23] developed an individual verification multimodal biometric method for face and speech, which provided an accuracy of 98.89%. In their latter work, [13] improved their developed algorithm, and they provided better accuracy.
Ref. [24] proposed an adaptive mechanism for user authentication on mobile phones, based on behavioral biometrics. By using a cost-based metric, they presented a method that can achieve relatively high accuracy. An android-based multimodal method, by using face and voice features, resulting in accuracy of 93.6%, was proposed by Ref. [25]. Ref. [26] provided a four-type face liveness categorization, based on motion, texture, multimodal biometric and multi-features, presenting their technical advantages and disadvantages. Regarding disadvantages, Ref. [27] supported that face recognition is hard to be realized in the case of BS low quality image technology, while privacy issues may arise since it cannot be achieved from a distance. Thus, they both Refs. [17,27] indicated the necessity of users’ actual interactions in order for the systems to be effectively deployed. Up to this point, previous literature has focused more on the BS’ technical factors, paying less attention to users’ perspectives [10,15], despite the fact that users’ intention and acceptance to use a technology is immense for the technology to be adequately adopted [28]. Ref. [15] emphatically supported that those BSs should fulfill the requirement of acceptability, namely the society’s widely acceptance for the identification method, while the role of users’ attitude toward biometric technology was overlooked [28]. Previous limited research on users’ acceptance indicates that acceptance is influenced and may be increased based on their technical interest, their identity theft concerns, the government border control initiatives, the securing basic infrastructure, and the opportunity to reduce memory requirements by replacing stored passwords [29]. More recent works, such as Ref. [3], examined users’ biometric system acceptance in Bangladesh. Ref. [8] focused on users’ acceptance for voice biometrics to an Italian international airport, while Ref. [2] work concerned Chinese tourists’ perceived intention to use biometric technology. Ref. [9] examined the possibility of airport passengers in using biometric technology in Brazilian airports and Ref. [30] indicated users’ concerns and threats to the biometric passport delivery system in Uganda. In addition, Ref. [18], acknowledging that research on behavioral biometrics continuous authentication (BBCA) technologies regarding smartphones, focused mainly on developing novel methods and techniques, conducted a survey to examine users’ views toward BBCA. Their findings indicate that the privacy concerns, reliability, trustworthiness and security of BBCA play a significant role for users, affecting greatly their intention to use such technology. Behavioral biometrics are encouraging, but also exposed to practical attack schemes, such as malware, mimic, impersonation, spoofing, replay, statistical, algorithmic and robotics attacks [7]. Furthermore, biometrics can be stored and handled without users’ consent and knowledge; they can be used for future unintended or unauthorized purposes, while they may be violated for generating more users’ information. Thus, since these technologies may provide a promising solution for increasing smartphone security, Ref. [18] highlighted the importance of addressing users’ perceptions regarding BBCA technology. Ref. [28] examined end-user acceptance within the privacy context, indicating the factors that affect users’ representations and perceptions regarding BS acceptance. These can be categorized as follows: (a) socio-demographic parameters, referring to gender, age, experience, employment, educational level, (b) reliability, referring to users’ trust on the systems, (c) usability, with reference to the easiness of procedure performance, (d) security and privacy issues, referring to users’ security and privacy concerns and (e) confidence and cultural issues, referring to users’ cultural practices. In particular, regarding the privacy concerns, one of the most used validated privacy scales in previous literature, is the concern for information privacy scale, developed by Ref. [31], which focuses on four dimensions, namely the collection, errors, secondary use, and unauthorized access to information. Emphasizing also on privacy concerns construct, authors in Ref. [32] introduced a scale to examine the control, awareness and collection of users’ personal information, while they adopted measures from other previous works, such as unauthorized secondary use, improper access, global information privacy concerns and intention to give information. In Ref. [33], focusing on internet privacy concerns, authors adopted items from Refs. [31,32] and they provided metrics for the collection, secondary usage, errors, improper access, control and awareness constructs.
Considering these works, it is acknowledged that even though BSs are increasingly widespread, users still remain wary regarding their utility since their benefits are not always apparent. Subsequently, it is immense for related research to users’ acceptance to be elaborated [10,15].
2.2. Statement of Interest and Research Questions
Taking into consideration that most of the previous works on BS focused on various physical and behavioral biometric techniques, while in users’ acceptance—a key element for BS success [15]—less attention has been given, it is of great importance for this aspect to be further examined. Thus, acceptance is a complicated notion since it includes social and organizational factors within it [34]. Previous research on users’ acceptance of new technologies, including biometrics, has used several models for further understanding of this aspect. The technology acceptance model [35] is one of the most known, focusing on users’ perceived usability (easiness and usefulness). The technology acceptance model has unfolded to be a principal one for comprehending predictors of human behavior toward the likelihood of acceptance or rejection of each technology. It presumes a mediating role of the two above-mentioned variables in a complex interrelation among system characteristics and potential system usage.
The theory of planned behavior supports that users’ behavior is determined by behavioral intentions and reasoned actions, including perceived behavioral control. It concerns an attitude–intention–behavior model, which posits that intention is determined by attitude, subjective norms, and perceived behavioral control, predicting the individual acceptance and usage of various technological features [36]. Thus, the theory of reasoned action puts an emphasis on consciously intended behaviors, and especially as far as BSs are concerned, users seem to be willing to adopt them, provided that they understand their benefits. The unified theory of acceptance and use of technology identifies four key factors, namely performance expectancy, effort expectancy, social influence and facilitating conditions, as well as four moderators, the gender, age, experience and voluntariness so that users accept new technologies, such as BSs. The performance expectancy, effort expectancy, and social influence were theorized, affecting behavioral intention to use a technology, while behavioral intention and facilitating conditions determine technology use. Moreover, various combinations of the four moderators were found to moderate various relationships, focusing on the importance of technology acceptance and use [37]. The information system success model measures systems quality and technical success, including the concepts of information quality, the semantic success via the concepts of use, user satisfaction, and individual impacts, as well as the organizational impacts via the concept of effectiveness success. These six dimensions of success are considered to be interrelated rather than independent, aiming at aiding in the understanding of the possible causal interrelationships among the dimensions of success and to provide a deeper exposition of the relationships [38]. The motivation model focuses on users’ extrinsic motivation and intrinsic motivation to examine to what depth they are willing to accept the technology, considering users’ three hierarchical stages of generality, namely, personality, life domain and state. These allow to understand intrinsic (engaging in an activity out of pleasure and satisfaction) and extrinsic motivations (engaging in an activity in order to obtain something outside the activity) more precisely [39]. Social cognitive theory supports that for interpreting users’ acceptance, behavioral, personal and environmental factors are determinants of each other [40]. However, it is important to note that the above theories/models consider either a specific limited parameter for examination, failing to pay attention to the users’ socio-demographic profile or ignore the usability facilitating factors deriving from the technology itself. Ref. [22] indicates that social and cultural differences, as well as gender, should be included as variables in models dealing with technology acceptance. Some of them are quite broadened, lacking a structural measurement, or they do not examine at all users’ security and privacy concerns, which are vital concepts for BS acceptance [30,41].
In Greece, where, to the best of our knowledge, a large-scale research regarding users’ BS acceptance is lacking, it is even more worthy to explore this issue. Consequently, questions concerning Greek users’ perceptions and familiarity with BS, as well as the socio-demographic factors that affect them to accept this type of technology, are set emphatically. Furthermore, users’ concerns regarding BS implementation are examined.
Our study focuses on the Greek University of the Aegean. Especially for Greek Universities, this type of study could be very useful since the Ministry of Education has established a new law regarding HEIs security (Law 4777/2021, F.E.K. 25/A/17-2-2021-Article 16). Toward this, the consideration of the BS adoption in order to ensure the authorized access of staff and students within HEIs internal areas would be an interesting case. The University of the Aegean is a network university, with a large student population (17.312), established in six campuses spread across six islands of the Aegean Sea, consisting of six faculties and eighteen departments. Therefore, besides the convenient access, due to its multi-faceted diversity (e.g., geographically and field of study), this research population can provide useful insight for BS acceptance. The survey is distributed to the undergraduate, postgraduate and doctoral students. In this light, the following fundamental descriptive research questions are formulated, which guide our study:
- RQ1: What are University of the Aegean students’ perceptions and familiarity regarding BS adoption and use?
- RQ2: What are the socio-demographical factors that affect University of the Aegean students’ acceptance of BS?
Our research questions aim to provide a description of many of the demographic and social variables under consideration and to assist in understanding which of them are important, while revealing current patterns regarding students’ BS acceptance and adoption.
In this regard, we aim to examine Greek users’ BS acceptance in public educational services, focusing on the perspectives of Greek students and on the role of their socio-demographic profile, going beyond previous literature, as a research need that has to be addressed.
2.3. Research Methodology
Taking into consideration the aforementioned research questions, our exploratory research aims at investigating University of the Aegean students’ perceptions regarding their BS acceptance. Constructs and significant factors from the above-mentioned technology acceptance models are adopted that being utilized in previous research for biometric systems acceptance, so as to design a more inclusive research instrument for students’ BS acceptance in HEIs in Greece. The items were based on measures derived from [3,4,12,30,41]. These are knowledge, adoption, usability, reliability, intention to use biometric systems, privacy and security concerns, confidence and social control, as well as specific demographics and social attributes of the users. Figure 1 represents the research methodology flow chart.
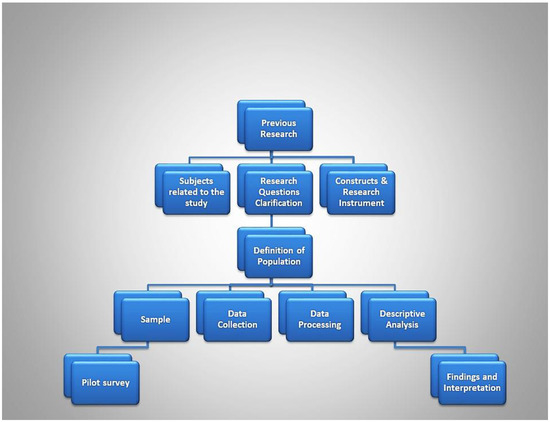
Figure 1.
Research methodology flow chart for students’ BS acceptance in Greek HEIs.
This survey is based on the undergraduate, postgraduate and doctoral students of the eighteen departments of the University of the Aegean. In order to have access to a large part of the research population for the results to be able to be generalized [42], a quantitative approach was selected, and a structured questionnaire was developed. All items regarding students’ perceptions for BS acceptance and usage were compiled from previous literature, presented in Section 2. In this respect, the anonymous instrument (Appendix A) is divided into 7 sections according to the constructs that were adopted to our research design, namely knowledge, adoption, usability, reliability, intention to use BS, privacy and security concerns and confidence and social control concerns, including 38 items. The closed-ended type items are divided into: (a) dichotomy questions, allowing the respondents to choose between two answers (Yes/No); (b) Likert-scale questions (from 1 to 5) and (c) multiple choice questions. Its reliability and validity were tested in a pilot survey addressed to 150 students, preceding the main sampling, and after the instrument being revised accordingly, it received its final form. The Kuder–Richardson reliability coefficients (KR-20) index was applied to calculate the reliability for the dichotomy-type queries, while Cronbach A type was used for Likert-scale queries. Finally, a set of nine items to address the participants’ socio-demographics was included. Age groups were divided, considering that in the University of the Aegean, most of the undergraduate students belong to ages 18–21 during the four-year bachelor degrees and to 18–22 during the five year ones; most of the postgraduate students belong to the 21–35 age group; most of the PhD candidates in 31–45; and a percentage of students within all cycles of studies concerns the 46–60 age group. Besides the variables that are usually adopted (gender, age, etc.), since our survey design is a descriptive one aiming at obtaining as much information as possible in order to identify which are the critical factors and guide future work, the variables of the study of level and parents’ occupation were included.
In particular, the father’s and mother’s occupations were asked, accordingly to Ref. [43] theory, since social background impacts individuals’ practices and cultural issues. Family is one of the most important socialization agents, enhancing values which are more practical than theoretical. Parents determine all family members’ attitudes toward several life domains, as well as determining factors for information technologies acceptance and adoption [44]. Due to the influential role that parents play, which in Greece is even more observed, we believe that it is essential to identify if the parents’ occupation, as an acknowledged important variable in other domains, affects students’ willingness to accept and use BS. The identification of these factors may have the potential to further our understanding of students’ BS acceptance and could inform the development of new approaches to increase their engagement and inform future policy.
The instrument was implemented through Google forms, allowing direct distribution by email. The procedure, the purpose and the ethics of the survey were explained with clarity in the introductory note, according to the research ethics and standards [11,45]. All of the 798 provided responses were tested for completeness, and in that way, 768 were included in our survey. Data were recoded and processed through SPSS21, while they were tested by confirmatory factor analysis (CFA) and Chi-square analysis.
3. Results
From the total 17.312 questionnaires that were sent, 768 were fully answered; the survey involved 279 male students, 480 women and 6 people who declared a different gender. There was an even distribution of ages, ranging from 18 to 60, with each category accounting as follows: the age group 18–22 represented 54%, the group of 23–30 amounted to 23%, the group 31–45 to 17%, and finally the group 46–60 to 6%. The sample regarding study level was respective to the students’ total population in each study level, indicating undergraduate students as 68%, postgraduate students as 24% and PhD students as 8%. Undergraduates were also asked to record their year of study. The majority (28%) was recorded in the first year of studies, 20% in second year, 12% in third, 18% in fourth, and 12% in fifth, while 10% was studying for more than five years. Aiming to more accurately outline the participants’ socio-demographic profile, they were asked to provide their employment status. Initially, most of the students (59%) do not work in parallel with their studies. Among the 41% of them who work, half of them (50%) are private employees, and 27% are civil servants, while 20% are self-employed and 3% of them declare another category. The highest students’ proportion (44%) declares an annual income EUR <10,000, 42% ranges from EUR 10,001–25,000, while 13% indicates the EUR 25,001–55,000 category and 1% the EUR 55,001 category. As far as the students’ fathers’ occupations are concerned, most of them (29%) declared freelancer, 24% private employees, while 20% and 21% declared the categories of civil servants and pensioners, respectively. Regarding their mothers’ occupations, 22% declared private employee, while civil servants and house holding were recorded as 21%. A relatively high percentage of unemployed mothers was indicated (8%), while only 1% declared another occupation. Table 1 provides the full participants’ socio-demographics.

Table 1.
The social and demographic attributes of the respondents.
Internal consistency reliability and convergent validity [33] were used for constructs’ assessing. All constructs met the acceptable levels of composite reliability of over ≥0.7, as presented in Figure 2. Composite reliability estimations are used in order to produce the internal consistency reliability coefficient, according to the proportion of variation, explained by the test items compared to the total variance of the composite test score.
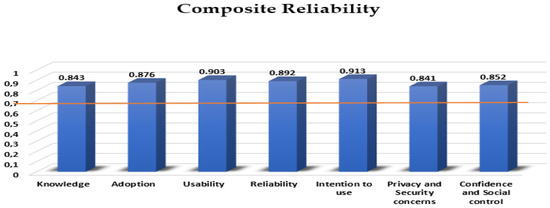
Figure 2.
Composite Reliability.
Additionally, acceptable levels of convergent validity were measured [46], presented in Figure 3, since average variance extracted was over ≥0.5, indicating that the average amount of variance in the variables of the constructs are able to provide explanations.
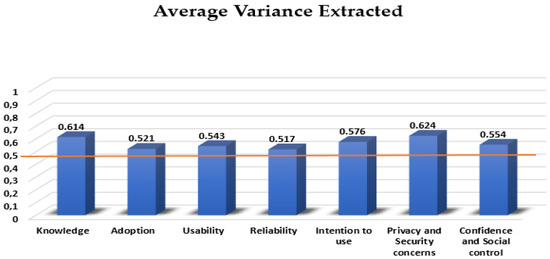
Figure 3.
Average variance extracted.
The most important findings, concerning descriptions and their interrelation, are provided as follows, according to the research design constructs. Due to the different numbers and proportions of participants in each type, (e.g., gender and level of study), in order to avoid sample unbalance in some cases, such as the study level, the normalization of the presented percentages of the participants of each type was elaborated, by weighting and summing up to 1 for each type, aiming to provide results’ explanation without bias.
In this regard, in the following subsections, according to the constructs we used, the findings are discussed, while they are summarized in Table 2 above.

Table 2.
Summary of the findings discussed.
3.1. Knowledge
The first set of questions aimed at investigating respondents’ knowledge and familiarity with BS. As far as the total sample is concerned, a small difference among participants that knew (51%) and those that were not aware of BS (49%) is indicated. Thus, the proportion (56%) of undergraduate students who did not know the BS definition before the introductory note is greater than those (44%) who did. In Figure 4, the year of study is indicated as a differentiated factor as well since higher ratings of non-familiarity are recorded among first-year students (64%), second-year students (60%), and fourth-year students (57%), showing that knowledge is not always in line with the study year. Only students over the 5th year of study declared a higher percentage of knowledge (75%). This is an unforeseen finding since young adults have been indicated to be tuning in to the new technologies at an ever-expanding level, while in our case, undergraduates and in particular the first-year ones, had less familiarity.
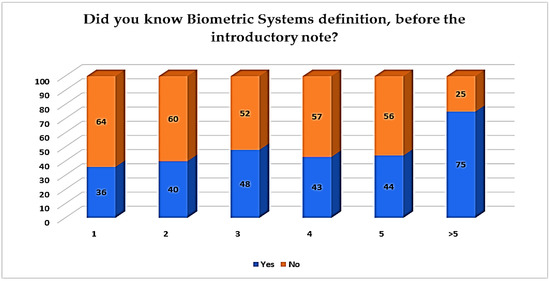
Figure 4.
Previous knowledge of BS per year study of undergraduates.
As it is presented in Figure 5, among the biometric techniques, the most popular is fingerprinting (97%), while the most non-familiar technique is keystroke analysis (79%). The face technique is also quite familiar for the majority of the students (91%), while for hand geometry and gait, low percentages of familiarity are recorded (30% and 27%, respectively). Despite the fact that the responders were asked to declare if they are familiar with any other technique, besides the eight ones that were proposed, none of them stated on this. In previous research [3], fingerprinting was also well-recognized (61.21%); however, in contrast to our findings, the DNA technique followed (60.59%). This indicates that the fingerprint technique can be the most popular one, in terms of usability.
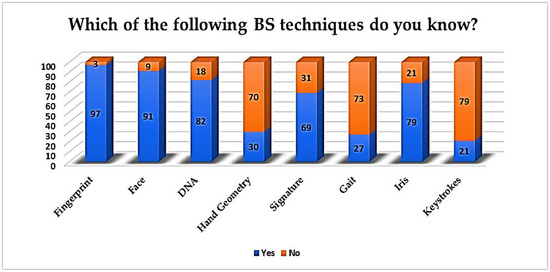
Figure 5.
Acknowledged BS techniques.
Results highlight that the 18–22 age group is more familiar with the fingerprint (52%) and face recognition (50%) techniques, indicating that age is an important factor. Thus, as it is shown in Figure 6, it is interesting to note that 2% of this group does not acknowledge fingerprinting at all, contrary to the rest ones. This indicates that, among those participants which are familiar with the BS techniques, the younger ones have a further knowledge of the most well-known techniques, supporting in this case that age goes along with technology awareness.
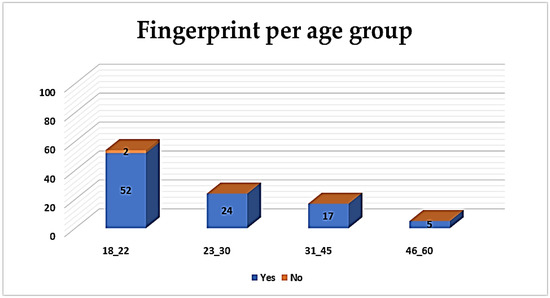
Figure 6.
Acknowledged biometric technique per age group–fingerprint.
3.2. Adoption
Despite the respondents’ knowledge level about BS, their incorporation in everyday life practices cannot be denied. In more detail, 10% of the students have adopted the fingerprint technique in daily practices, verifying why the fingerprint technique is the most popular technique. However, while facial recognition was also identified as a popular one, only 6% of them use it daily. It is important to note that the hand geometry technique is not used at all by the University of the Aegean Students, while signature, gait, iris scan and keystrokes are fragmentarily used (3%, 1%, 1%, and 1%, respectively). Furthermore, respondents were asked to declare in which daily practices they have adopted biometrics. These concern the fingerprint (57%) and facial recognition techniques (7%) for unlocking mobile phones. For other activities, such as banking or airports, the adoption is significantly lower (1–2%). In previous research [12] examining U.S. travelers’ intentions to use biometric in airports, the adoption of biometric technique of e-gates was significantly higher (Yes 24%), indicating that if services could better promote the usefulness and performance of BS techniques, these could be further adopted by users.
In Figure 7, the adoption of the most familiar technique, the fingerprint technique, per education level is presented, where a higher percentage of undergraduate students (18%) is indicated, who have not adopted it in daily life practice compared to the postgraduate and doctoral students.
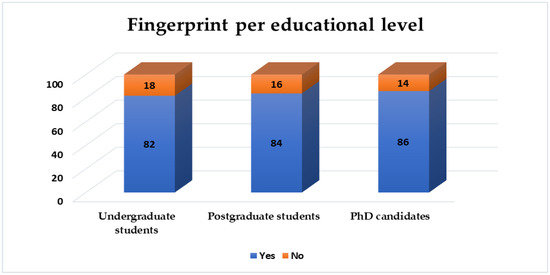
Figure 7.
Adopted biometric technique per educational level—fingerprint.
The results, presented in Figure 8, indicate that the employment status of 41% of the students that are working affects their adoption in daily practice. The majority of civil servants use biometric techniques as far as passport services are concerned, contrary to other categories. Private servants use keystroke analysis for authentication and for signing in banking activities on behalf of someone else, while half of the self-employed adopt biometrics within public relations activities. This finding is quite important since most of the previous studies, focused on users’ perspectives and on their demographics, did not analyze profession as a factor that impacts biometrics adoption.
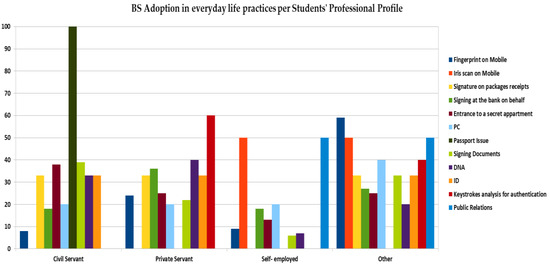
Figure 8.
BS adoption in everyday life practices per students’ professional profile.
3.3. Usability
This section outlines the respondents’ perceived usability of BS. The following results in Figure 9 draw a clear picture of users’ perception for systems’ easiness, indicating that the majority do not find any particular difficulty (easily and very easily both at 32%), while only 3% of them consider biometric techniques to be “Very Difficult” to be used. Therefore, most of them (68%) do not consider that special training is required. However, a not-ignorable proportion (32%) of them supports that training is needed. Thus, findings support that for the majority, there is no effort required for the learning and using of BS, indicating that new technology could be easily adopted since students perceived BS to be easy to be used. Previous research [41] regarding consumers’ adoption of biometric systems in restaurants validates the direct positive relationship between perceived ease of use and attitudes toward adopting and using BS.
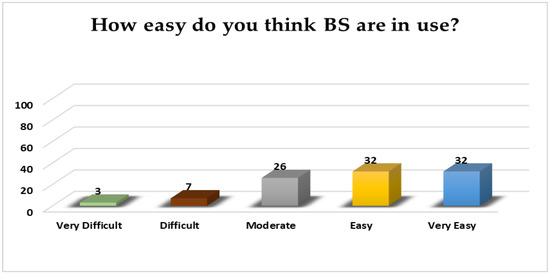
Figure 9.
BS perceived easiness.
Users were also asked to choose among the most important advantages of BS. Most of them (41%) focused on the probability of accurate identification, based on their unique characteristics, 26% on the verification speed, and 19% referred to the lack of passwords’ memorization. A proportion of 11% of them found it important that the use of a key, card or other device is not required, while 4% declared the convenience of being able to easily learn to use it. Such findings have been indicated in previous research [3], where participants cited increased ease of use (40%), increased convenience (31.2%), as well as cost savings for the users and security privileges.
Furthermore, gender seems to be differentiated. Women, in particular (64%), as shown in Figure 10, considered accurate recognition to be the most important advantage. A total of 63% of the women compared them to passwords, and they believed that the verification speed is quite important, while 62% of them focused on the absence of remembering passwords.
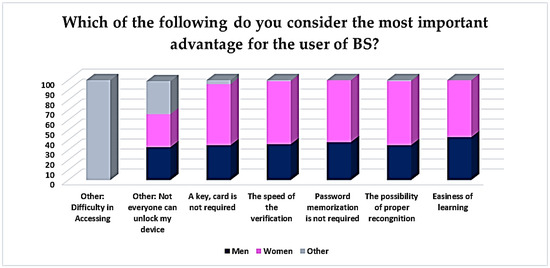
Figure 10.
BS advantages per gender.
As far as the disadvantages are concerned, the majority declared the risk of personal data breach (57%), and 21% the relatively high installation costs, while 6% of them considered the ‘long registration procedures’ to be a major disadvantage. What is striking is that, even though the risk for the personal data to be compromised was highly rated, only 5% of them declared to be concerned and fearful regarding BS use. Thus, in [4], previous research, 35.6% of the participants referred to the misuse or abuse of individual data since compromised biometric information stored in databases cannot be revoked.
Moreover, as presented in Figure 11, the age group 18–22 indicated a greater concern for personal data risks (55%) and feeling fear and anxiety (49%) compared to the rest of the groups. Equally pronounced in each age group is the disadvantage of BS high costs, with the group of 18–22 being higher (47%). Finally, it is worth noting that the respondents of the 31–45 group (36%), who declared other as the most important disadvantage focused on the uniqueness of each person to be a privilege that brings complacency to users.
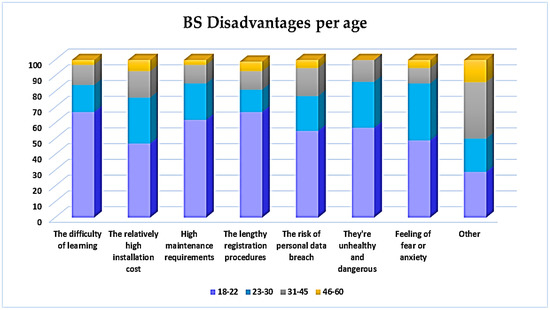
Figure 11.
BS disadvantages per age.
What is more, respondents that declared fear or anxiety as a disadvantage, were asked to justify their answers. In this respect, 22% of them declared the fear of being “registered on a server” and “access by third parties”, as well as the “obtained users’ information without their knowledge”. Similar results were indicated in [4]’s study as well, where 22% feared the selling of individual data to third parties since biometric information cannot be canceled if it is gained by a third party.
As shown in Figure 12, the employment status acts as a differentiator. In more detail, all of the participants (100%) belonging to private employees were concerned that their data, registered on a server, are easily accessed by third parties, as well as being concerned (33%) that unlike passwords, biometrics cannot be changed if they are violated.
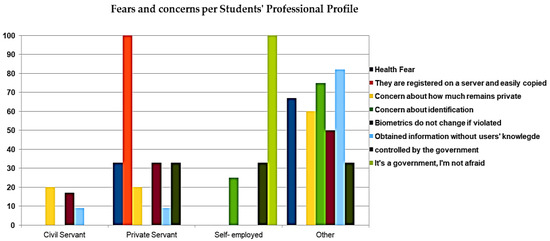
Figure 12.
Fears and concerns about BSs per students’ professional profile.
Finally, in Figure 13, the results indicate that the father’s occupation seems to act as a differentiator as well. Fifty percent of the respondents whose father is a freelancer, declared that they were more concerned about the possibility of identification, 36% of them for someone to obtain information without his/her knowledge, which could be used against them, while 40% of them were concerned with how much information remains within BSs. Furthermore, 60% among the students whose father works as a civil servant were focused on the fact that biometric information cannot be changed, contrary to passwords and codes.
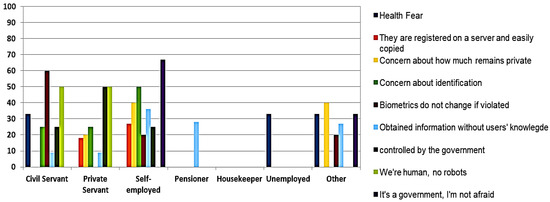
Figure 13.
Fears and concerns about BS per father’s occupation.
3.4. Reliability
This section outlines whether BSs are considered reliable. For the item “Do you consider BS as a more reliable identification method than password/PIN?” participants declared, at 38%, “very much”. Thus, the proportion who do not trust both passwords and biometric techniques is notable (10%). In Ref. [4]’s previous research, focused on the compliance of users of East Africa to passport biometric techniques, similar results came up, indicating that the majority (65.2%) of the respondents seemed to trust data encoding techniques more than a password or PIN, with 34.8%.
The results are almost identical for BS perceived security contrary to passwords/pins, as presented in Figure 14, where the majority of the participants’ declared “very” (38%) and “very much” at 23%. These support [3]’s research findings concerning users’ perspectives in Bangladesh, who believe that biometric systems can provide more security than password- or PIN-based systems (63.63%), while 10.32% of Bangladesh users totally disagreed that biometrics are secure.
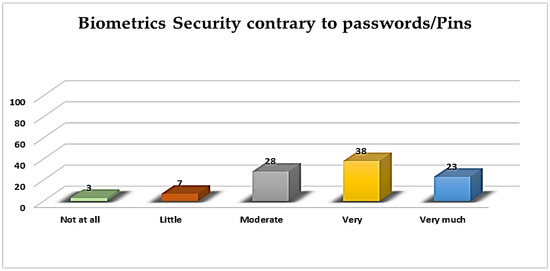
Figure 14.
BS security contrary to passwords/PINS.
The ways that individual private and sensitive information is accessed, collected, stored and handled by cloud and IoT services result in BSs being more vulnerable to identity fraud [4], so it is important to identify students’ beliefs regarding BS reliability toward this. As presented in Figure 15, the 18–22 age group (74%) states that such a solution can be reliable regarding thefts, but not adequate enough to solve the issue by itself. A small proportion is opposed (10%), belonging to the 31–45 age group. Since BSs disclose part of a users’ identity, further protection techniques should be developed in order to increase students’ intention to use them.
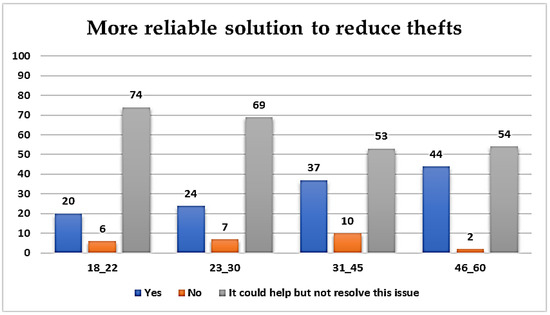
Figure 15.
BS as a reliable solution to reduce thefts.
3.5. Intention to Use Biometrics
This section reflects the intention of using BS. A total of 85% of the participants indicated that BSs have made their daily life much easier, while 15% were opposed. Since the intention to perform an action results from a mindful decision-making procedure, providing a strong prognosticator of an actual behavior, accordingly, the recorded students’ intentions indicate a highly likelihood to use BS in their every-day life practices. Thus, age and mother’s occupation seem to be the most important factors. The age group once again provides a differentiation among the other demographics. Essentially, as shown in Figure 16, the majority belongs to the group of 18–22 (90%), 83% to 23–30, 76% to 31–45 and 71% to 46–60. The results for the opposed ones are equally differentiated.
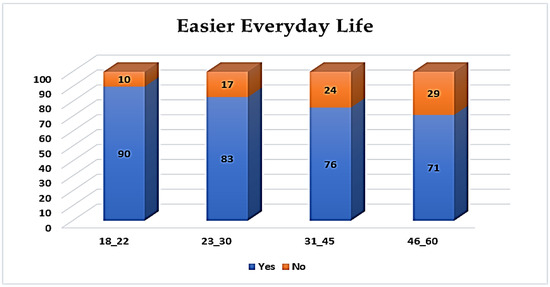
Figure 16.
Easier day life due to the BS.
What is more, as shown in Figure 17, 90% of the participants, whose mother’s occupation is a private employee and unemployed, indicated that BSs have made their daily life much easier, while 10% indicated the opposite. The results for those opposed are equally varied, except for a proportion of 30%, whose mothers are retired.
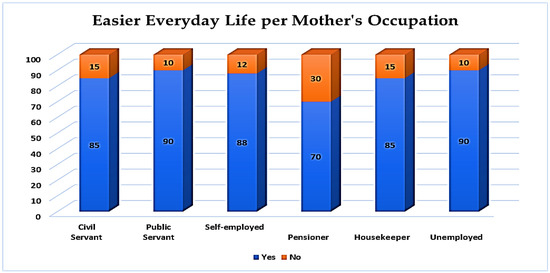
Figure 17.
Easier daily life per mother’s occupation.
As biometric systems infuse deeper into all areas of modern social life, while previous literature focused in majority on rather technical aspects of BS [41], it is important to examine in which areas the Greek students believe that BSs could be deployed in order to be broadly accepted and adopted. Regarding the services in which BSs could be integrated, participants were asked to provide a list among them. Participants seemed to be more in favor of the airport (83%) and bank (80%), while 60% supported the hospital services as well. Within education, a greater proportion (65%) indicated its approval, as presented in Figure 18.
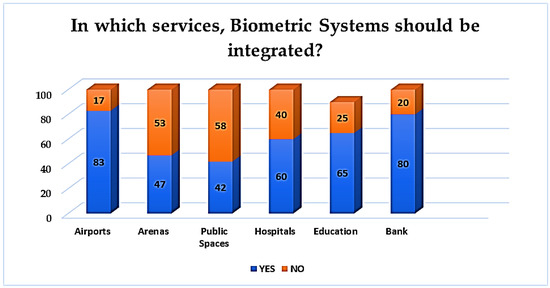
Figure 18.
BS perceived integration to services.
Furthermore, it is noted that the 31–45 age group (86%), presented in Figure 19, considers it more necessary for BS to be integrated within airport services in order to increase security measures for passengers and staff.
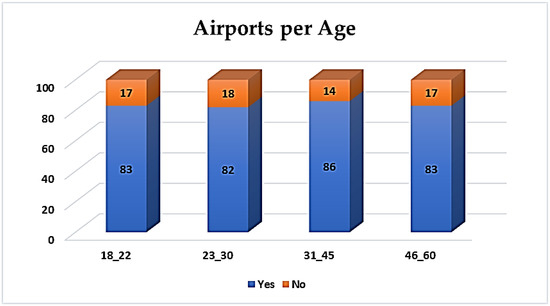
Figure 19.
BS perceived integration to services—airport per age.
The fifth-year students (86%) underline the importance of BS integration within hospitals, while 73% of the first-year students are in favor of this as well. Figure 20 fully presents these results per year of study.
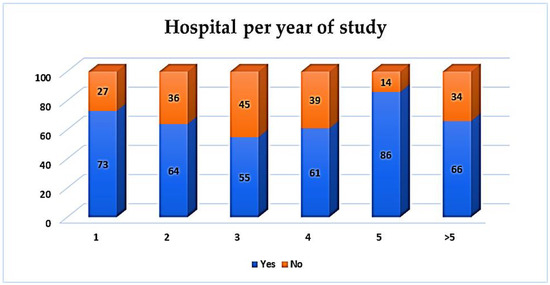
Figure 20.
BS perceived integration to services—hospital per year of study.
Among the services for which users are willing to replace previous methods with BS, travelling within or outside the EU is considered more, as reflected in Figure 21. Thus, 19% of them support that they are “not at all” willing to share their biometric information in order to increase their security level at the airport.
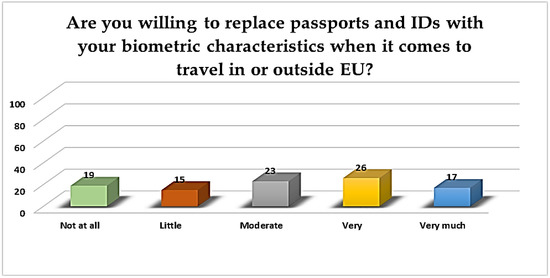
Figure 21.
BS—replacing passports with BSs.
3.6. Privacy and Security Concerns
In this section, participants were asked to rate their beliefs about the increase in the security level from potential threats due to BSs. Since BSs are relatively new in Greek society, while their capabilities to provide privacy and security protection are not well-known, it is important to understand which techniques users believe utilize their information in a harmful way in cases of privacy loss or security incidents. These representations possibly affect their intention to use them as well.
Many of them (10%) support that DNA and eye iris analysis increase security more than the others, while 9% of them consider that fingerprinting is also one of the more secure techniques. On the contrary, 8% and 7% of them, respectively, declare that typing analysis and signature recognition and pacing analysis are not very secure. In particular, 39% of the 18–22 age group considers that using fingerprinting gives them the confidence of security increasing against potential threats, unlike other biometric techniques. It is worth noting that among other demographics, only the age category shows such variations.
Furthermore, the kind of service is also important to be identified regarding the level of protection offered, considering that BS adoption in Greece is promoted in several public services. Participants were also asked to report “Which services/organizations they believe that use powerful security and identity protection methods”. In fact, the majority reported that public spaces do not (95%). Respondents believe (74%) that mobile operators, health services (75%) and airlines (66%) also do not provide secure solutions. Thus, 87% of them support that bank services use powerful methods. Figure 22 presents the respective results.
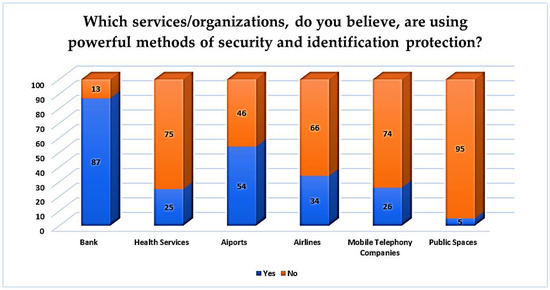
Figure 22.
Services with security and identity protection.
Employment status seems to be important among those participants who support that the mobile industry does not offer powerful security methods. In particular, civil (82%) and private servants (76%) are more confident regarding this. However, regardless of the employment category, all of them support this point of view, as presented in Figure 23.
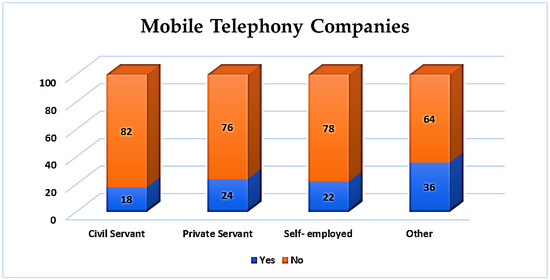
Figure 23.
Services with security and identity protection—mobile industry per students’ professional profile.
3.7. Confidence and Social Control Concerns
This section provides participants’ representations regarding confidence and social control concerns within BSs. As argued in [6], one of the most significant aspects for the successful deployment of BSs is public confidence and social acceptability. In this regard, respondents were in the majority (97%) regarding, “would you like to know how their biometrics will be used by the services”. Women supported this stronger (61%), being willing to know the following processing procedures by the services. Toward this, 83% of the participants did not trust services and their intention to use their biometrics only for verification reasons. Women were more concerned (53%) than the untrusted men (29%). It is worth noting that only “gender” provided such a difference among demographics.
One of the participants’ greatest concerns was their privacy violation, since 82% of them supported that biometrics can violate their anonymity and freedom. This was reflected mostly by women (52%), thus 10% of them did not consider it at all. Most of the participants (74%) also believed that biometric information can be easily cloned, resulting in a breach of their integrity. Equally subversive, this thesis was supported by the 46–60 age group (77%). The results for the rest of the groups are quite similar, as fully presented in Figure 24.
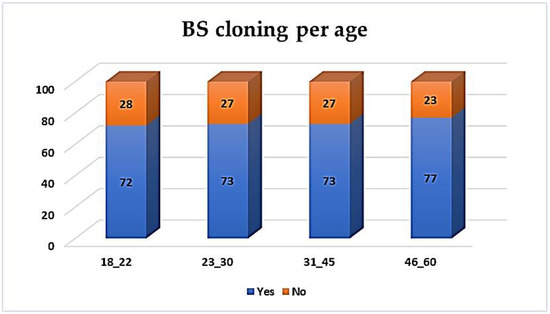
Figure 24.
BS cloning per age.
Not a significant difference was recorded among the participants who believed that biometrics may harm human rights (48%) and those who did not. Thus, the majority (28% agreement and 21% totally agreement) supports that “governments collect citizens’ biometric data for other reasons than their security”, while only 5% totally disagreed and 10% disagreed. In particular, participants belonging to “other occupation” (24%) supported that governments collect citizens’ biometric data for reasons other than their security. In this respect, participants were asked to justify this belief. Among other reasons, 15% supported that governments violate citizens’ personal information in any chance, while 6% of them, working as civil servants, supported that human rights are generally violated by the government when biometric information is requested. However, private servants (6%) declare that they are not actually aware of this. Finally, it is important to note that 7%, belonging to the 46–60 age group, as well 23% of the participants belonging to the “other occupation” group declared to prefer to be monitored by the government rather than by third parties.
4. Discussion
The main objective of this descriptive survey was to explore the University of the Aegean students’ BS acceptance, focusing on their social and demographic information and their privacy concerns that play an important role toward this in order to provide deeper insight regarding BS acceptance in Greece and in particular for Greek University students. Since similar surveys are lacking in the Greek social reality, there is a need to identify the current trends at first. Regarding this, findings are discussed and compared with previous research in other countries not on a score basis, since samples and cultural issues are varied, but as useful information before further research can be carried out. As Ref. [47] argued, users’ behavior and attitudes toward technologies are led by their mentality, so it is immensely important for designers and developers to recognize and comprehend users’ perceptions when developing and realizing such systems.
Summarizing our findings, it has emerged that most of the University of the Aegean (UA) students are familiar with the concept of BSs, and they believe that they can simplify their everyday lives. Thus, BSs are not adopted in their everyday practices to a great extent, while techniques, such as hand geometry, are not used at all. This is not the case for the fingerprint technique, which is the most popular technique, especially for mobile phones’ unlocking. This supports the previous research findings, such as Ref. [48], by which it is indicated that adults acknowledge and feel more comfortable to use the fingerprint technique, while the mobile phone industry promotes this technique more often [49].
Most of the participants consider BSs to be easy to learn and use, referring thus to the most-known ones, fingerprinting and face recognition. Their unfamiliarity with plenty of techniques, such as keystroke or hand geometry, presupposes that BS-aware training is needed, despite the fact that the majority of students believe that training is not required. Ref. [6] emphatically supports that plenty of people are still lacking information regarding the BS role and their functioning, resulting in not understanding how BSs can make their life simpler and the effective ways of identification compared to traditional methods. This has a negative impact on users’ acceptability. In this regard, BS distribution policies by private services or educational ones in Greece should not only focus on the simpler biometric techniques acknowledged by a large student population, but also on the unknown ones in order to balance knowledge and familiarity among users. Considering that UA students support that the greater BS advantage concerns accurate identification based on their unique characteristics, and the greater disadvantages concern the fear of unauthorized accessing and processing of their personal information, as well as violating their privacy by third parties, which are common ones among users worldwide [48], BS training is of great importance in order for BS acceptance to be increased within Greek HEIs. Public trust and acceptance are key parameters for the adequate deployment of BS systems, since when they are lacking, it likely leads to implementation difficulties, inconvenience, and false acceptance rates that increase distrust among users and discourage public and private services from using them in their daily function [50].
Toward this, it is also important that UA students are not fully convinced regarding BS reliability for identification, even though a large proportion of them, being tired of the plethora of passwords, supports that BSs are more reliable and safer than passwords/PINs. UA students also believe that BS utilization may reduce personal information thefts, similar to previous research [51], where American users supported that face recognition in working environments is a capable solution for this reduction. Although UA students seem to be willing to replace passwords with fingerprinting, supporting previous research findings by which UK users are indicated to want to replace codes for security and convenience reasons, this UA students’ perception needs strengthening to reduce their uncertainties and fears. It is acknowledged that users can be identified due to their unique biometric data, when they are willing to access to certain services [18]. Therefore, the UA students’ need for more reliability, security and easiness should be further considered by the responsible authorities and agencies so that their BS acceptance is enhanced not only with reference to HEIs, but also within other services. To this end, even though a proportion of UA students argues that airport and bank services could be leveraged by integrating BSs, as in previous literature [52], providing easiness and saving time, there is a more skeptical trend of a possible integration for e-banking and the replacement of passports for travelling in or out of the E.U. Consequently, in Greece, where BS technology has not been established for several years, unlike other E.U. countries, policies promoting BS should focus on students’ further information about what such adoption means and which choices they have in order for them to act knowingly.
The lack of users’ training and information is reflected in their security concerns, especially regarding the methods provided by public spaces. Participants, even though they do not adopt them in daily life, believe that fingerprinting, and DNA and iris analyses increase the safety level, compared to other techniques, against potential threats. Taking into account that users are willing to share their biometrics for improving their security [53], more secure methods are required, particularly for public spaces, such as for educational settings in Greece that are mainly public. Furthermore, bank services are considered to provide stronger biometric methods for users’ identity protection, supporting previous literature findings regarding adults’ will to embrace biometric identity within banks [48]. Thus, confidence and social control issues are highly considered by the UA students. The vast majority would like to know the subsequent processes for their obtained biometric information since students mistrust the ways in which the services will use it, supporting that it will not be used only for verification purposes, leading to privacy violations, similar to previous research findings [37,42]. According to Ref. [6], the risk of misusing and harming the integrity of personal identity, and the risk of privacy invasion as well as the social and ethical issues that derive from BS algorithmically driven actions lead the users to deny access to such systems, due to the fear of losing control over their identity. UA students focus more on private services control, rather than public, arguing their preference to be monitored by the government and not by a company for profit. On the other hand, even though previous works in the literature indicate that users believe that BSs may harm their civil liberties [54], UA students support that BSs do not violate human rights.
As far as the UA students’ sociodemographic profile concerns, the factors that are indicated to impact their BS acceptance are gender, age, study level, year of study, professional profile and fathers’ occupation. Mothers’ occupation seems to not play an important role regarding BS acceptance.
4.1. Gender
Women more strongly support than men that accurate identification, based primarily on the uniqueness of their biometric information, is the most important BS advantage, making BSs superior to passwords. Women feel more tired of password memorization, which can easily be lost, stolen or violated. Women put more emphasis on BS integration in order to safeguard their privacy protection and save time within verification processes. In particular, for bank services, women argue that they provide the most secure BS technologies, contrary to Ref. [52], where users stated that, given the high risk for data theft, bank systems do not provide high security. Furthermore, women in our research rightly want to know precisely whether their data will be used by services, since they do not trust them to use it only for verification reasons, worrying for their privacy. Men, on the other hand, are positive toward this integration with a much lower tendency to worry, arguing that BS incorporation is preferable for them only on human devices. Additionally, they do not value privacy and security issues as highly as women do. Therefore, women perceive BS advantages more easily than men, thus being more concerned about provided security and privacy protection. The need for women to ensure their protection in such services is apparent since they are likely to resist BS within services that they do not trust. Consequently, gender plays an important role in accepting BSs in Greek HEIs, inconsistent with previous work focusing on airports [9] in which this demographic was not indicated as an important one.
4.2. Age
Age is indicated to act as a great differentiator factor, impacting in multiple ways on students’ BS acceptance. Among all age groups, the 18–22 one was highlighted to be familiar enough with the popular biometric techniques, such as fingerprinting, with an emphasis on mobile unlocking, or face recognition, stating that they simplify their daily life. In particular, they argued that fingerprinting creates a high sense of security in the face of a potential threat. This shows that younger people feel more comfortable and safer using such technologies, while the previous literature is supported [9,48]. As a participant stated, “There is no longer a mobile phone without a fingerprint”, indicating as well that technology itself acts as a facilitator for BS acceptance. However, it is notable that among all age groups, the most well-known techniques were not acknowledged at all by a small proportion of students. Furthermore, the 18–22 age group believed that the most important disadvantage of BSs concerns the risk of a personal data breach, arguing that BSs are not capable of eliminating thefts but only reducing them, supporting previous literature findings. This tendency among the rest of the groups is much lower. Additionally, compared to the other age groups, the 18–22 and the 46–60 ones outline their strong concern for the possibility of their biometric information to be cloned, underlying one more disadvantage. Additionally, these groups identify the high cost of BS installation as a major disadvantage, as well. However, the majority of the 31–45 age group, considering its desire for more security at the airport services, supports that this integration is vital. Finally, regardless of their age group, participants claimed that once the services collect users’ biometric information, their privacy is automatically violated. Thus, findings interestingly indicate that the 46–60 age group supports that it is better to be monitored by the government rather than third parties or malicious companies.
4.3. Study Level
Study level can generate some interesting arguments as well for BS adoption by Greek students. Undergraduate students put particular emphasis on the adoption of fingerprinting so as to unlock their mobiles, confirming [49]’s previous research, focusing on Android 4.0+ and Iphone 5s users. However, they do not embrace hand geometry at all, while typing analysis is also not adopted by the majority. This indicates a possible trend among the biometric techniques such that they can be used within HEIs, especially under the spectrum of the new law for enhancing security.
4.4. Year of Studies
A notable proportion of first-year students did not know the BS definition before reading our introductory note. Thus, fourth-year students declared higher ignorance compared to younger years. This indicates a paradoxical finding since in general it is anticipated that the more the years of studies increase, the more students’ knowledge evolves. Additionally, first-year students are not convinced that biometric systems will change their daily lives, and thus they are not opposed to the possible replacement of passwords. Apparently, first-year students also indicate a positive perception of BS integration within hospitals, contrary to the other groups, who do not trust such technology in medical services. Therefore, the BS policies they promote should be turned to users who are skeptical or in an intermediate situation.
4.5. Professional Profile
Students, belonging to private employees, use fingerprinting to unlock their mobile phone, contrary to other employment groups. However, they argue that mobile operators do not use strong methods to provide their customers with data security. The same group is indicated to be the only one concerned about the storage of their biometric information and the probable unauthorized access by third parties. Moreover, they support that, contrary to passwords, biometrics, if violated, cannot be restored since they cannot be changed.
4.6. Father’s Occupation
Examining participants’ social background, fathers’ occupation impacts their privacy concerns. In particular, participants declaring a self-employed father are concerned about access to their biometrics information without their consent and how these will be used since they consider that if this information is digitalized, it can at any time be used for any purpose by anyone. Furthermore, the same group states a concern that biometric techniques cause health problems, supporting previous research findings [54] that are concerned about the hygiene of BS techniques and specifically about techniques such as iris analysis.
The aforementioned analysis aims at providing further understanding regarding the potential BS acceptance issues that influence University of the Aegean students. Identifying and determining these factors, awareness of the advantages and risks of using biometric technologies is increased. This is of major importance, especially for Greek HEIs in order to ensure that their potential users, mainly the students, will accept them, provided that they have undertaken the proper organizational and technical measures for effective utilization which also maintain security and privacy.
5. Conclusions
Technology acceptance, as a complex notion, is significantly differentiated among users due to several social factors that reform their views and behavior. Our survey focused on the Greek University of the Aegean Students’ BS acceptance, and in particular, on the sociodemographic attributes that influence their willingness to adopt and use BSs, since it has been underlined by previous literature [9,15] that not much research has been undertaken in this direction. Previous research, examining college students’ BS acceptance, targeted only learning activities under the spectrum of technical factors [10,21], while in Greece, such surveys are lacking even for the general population. Thus, due to the newly introduced cyber security and privacy threats regarding BS, the situational awareness, as far as their deployment is concerned, should be increased. Therefore, toward this, the identification of the prerequisites for users’ acceptance that involve their specific traits deriving from their personality, life status and habitus, as technology acceptance models indicate, is immense. Furthermore, the social factors of the users are indicated as critical ones in the privacy domain [55,56,57,58,59,60] as well, whose preservation is also significant for BS acceptance.
In this respect, our survey aims, beyond those of previous works in the literature, to expand the knowledge regarding Greek users’ BS acceptance in public and private services, attempting to gain insight through the perspectives of Greek students and the exploration of their socio-demographic profile, addressing that need, as already pointed out in the literature. As Greek users’ acceptance is the issue of focus of this research, biometric service providers can consider the indicated factors, as well as users’ concerns in order to improve their services. Furthermore, considering the new established Greek law for increasing security, adopting BSs as well within HEIs, these findings may be of major importance and help Greek public educational administrations. The adoption of such systems may be extravagant concerning their initial investment [3], and therefore Greek universities should be aware of their students’ perceptions toward this.
Our survey indicated students’ familiarity with specific biometric techniques, fingerprinting and face recognition, which are adopted for specific daily activities—mobile unlocking—in order to ensure their security. Due to their perceived benefits of accurate identification and saving time, students support that BSs should be integrated in the private bank and airport services, while they do not trust public spaces at all. This finding, indicating students’ mentality, puts forth extra challenges for Greek HEIs considered to be public spaces, highlighting that the trustworthiness of their provided biometric techniques should be increased. Several UA students’ sociodemographic attributes are indicated to impact their BS acceptance, including gender, age, study level, year of study, professional profile and fathers’ occupation. Students’ social profile influences their technological choices and therefore, an adequate marketing policy, considering these social factors, should be developed both from industry’s and universities’ leadership, in order to enhance students’ BS acceptance, by, for example, choosing the techniques that will be more easily adopted by them.
Furthermore, contrary to previous literature [12], our survey also pointed out that several trust issues regarding users’ intention to adopt and to use BSs in public and private services are linked with their privacy and security concerns. Biometric techniques and methods are still evolving in Greece, mostly in the private domain, while students are still doubtful regarding the ways that private services using their biometric information and the possibility for their privacy to be violated. These non-technical concerns, which are also potential risks, should be confronted when implementing identity biometrical verification technologies. BS exploitation in HEIs can be achieved, provided that students, despite their security and privacy fears will be ensured that biometrics will enhance their protection, due to the organizational and technical standards that should be considered. In this regard, we support that our findings may be beneficial for both Greek HEIs and industry. Raising awareness and identifying students’ privacy and security issues will help to promote wider acceptance of the technology both organizationally and technically.
Given the constraints of internet-of-cloud services and the users’ issues for accepting and adopting biometrics, it is necessary to develop specific biometrics for the internet-of-cloud schemes that not only strengthen security and privacy, but also are user-friendly so as to embolden the public acceptance of biometrics within these services. BS developers who take into account users’ sociodemographic attributes that express higher concerns will design more attractive and safe systems that meet students’ non-functional requirements, while public Greek universities, by acknowledging the factors affecting their ender-users’ acceptability, will design effective procedures for BS deployment. Additionally, since biometric information is subject to GDPR in Europe and its privacy is strongly supported [8], universities could provide students with training programs not only for learning and using BS, but also for enhancing their privacy awareness. Our survey also enhances the literature with a further empirical association regarding BS acceptance in public and private services, with reference to Greece, also providing an opportunity for examining cultural differentiations.
Despite limitations, such as the lack of a social influence construct in our research design and the descriptive design used to determine the different characteristics of the responders regarding BS acceptance, our work provides a foundation for further analysis of the role of users’ sociodemographic profile in BS acceptance, while these attributes’ association with users’ concerns for privacy implications sets the standard for a better understanding of the users’ perspective in accepting BS. However, since biometrics for the internet of cloud is an emerging research area and security and privacy concerns are still a wider research question [30], future research should be more focused on users’ concerns and biometrics acceptance perspectives, examining the general population.
Author Contributions
Conceptualization, C.K.; Formal analysis, A.K. and C.D.; Investigation, C.D.; Supervision, C.K. and S.G.; Visualization, A.K.; Writing—original draft, A.K.; Writing—review & editing, C.K. and S.G. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Ethical review and approval were waived for this study. The study was approved by the Rector and the Vice Rector of the University of the Aegean due to the fact that the data were collected and stored anonymously, according to the Code of Ethics of the University of the Aegean.
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
| Constructs | Items |
| Knowledge | Did you know what BS are, before you read the introductory note?Responses: Yes/No |
| With which of the following Biometric techniques are you familiar?Responses (choose yes/no for each one):Fingerprint, Face recognition, DNA, hand geometry, signature, gait, iris scan, keystrokes, other | |
| Adoption | Have you adopted any of these techniques in your everyday life?Responses (you may choose yes/no for the following):Fingerprint, Face recognition, DNA, hand geometry, signature, gait, iris scan, keystrokes, other |
| If you have adopted any of them, which of the following daily activity does it concern?Response: open-ended question | |
| Usability | How easily do you think that BS are in use?Responses:1: very difficult, 2: difficult, 3: moderate, 4: easy, 5: very easy |
| Do you think their use requires a special training?Responses: Yes/No | |
| Which of the following do you consider the most import advantage for using BS?Responses:A key, card is not requiredThe speed of the verificationPassword memorization is not requiredThe possibility of proper recognitionEasiness of learningOther | |
| Which of the following do you consider the most important disadvantage while using BS?Responses:The difficulty of learningThe relatively high installation costHigh maintenance requirementsThe lengthy registration proceduresThe risk of personal data breachThey’re unhealthy and dangerousFeeling of fear or anxietyOther | |
| Provided that you feel fear when your identification is based on your biometric information, please justifyResponse: open-ended question | |
| Reliability | Do you consider BS to be a more reliable method of identification than password/PIN;Responses:1: Not at all, 2: Little, 3: moderate, 4: very, 5: very much |
| “Do you consider BS to be a more secure method of identification than password/PIN?”Responses:1: Not at all, 2: Little, 3: moderate, 4: very, 5: very much | |
| Do you consider BS to be a more reliable solution to reduce thefts than passwords/Pins?Responses:Yes, No, it could be | |
| Intention to use biometric systems | Do you think that using BS can make your everyday life easier?Responses: Yes/No |
| In which services do you think BS would be good to be integrated?Responses (you may choose yes/no for the followings):airports, arenas, public spaces, hospitals, education, bank, other | |
| To what extent do you feel ready to stop using passwords/Pins and replace them with biometric techniques?Responses:1: Not at all, 2: Little, 3: moderate, 4: very, 5: very much | |
| To what extent are you willing to adopt biometric identity for your online banking?Responses:1: Not at all, 2: Little, 3: moderate, 4: very, 5: very much | |
| To what extent are you willing to replace passports and IDs with your biometric characteristics when it comes to travel within or outside the EU?Responses:1: Not at all, 2: Little, 3: moderate, 4: very, 5: very much | |
| Is there any activity/service for which you are willing to use biometric techniques directly? Response: open-ended question | |
| Privacy and Security concerns | Does using of the following biometric techniques increase the risk of privacy invasion?Responses (you may choose yes/no for the followings):Fingerprint, Face recognition, DNA, hand geometry, signature, gait, iris scan, keystrokes, other |
| Do you believe that using BS can lead to your privacy violation?Responses: Yes/No | |
| Does using of the following biometric techniques increase the security level against potential threats?Responses (you may choose yes/no for the followings):Fingerprint, Face recognition, DNA, hand geometry, signature, gait, iris scan, keystrokes, other | |
| Which services are using powerful biometric methods to ensure security and protection of your identity?Responses (you may choose yes/no for the followings):airports, arenas, public spaces, hospitals, education, bank, other | |
| Confidence and Social control | Would you like to know how your biometric characteristics will be used in particular by the services that request them?Responses: Yes/No |
| Do you trust that biometric information obtained from the services will only be used for verification purposes?Responses: Yes/No | |
| Do you think that your biometric information can be cloned?Responses: Yes/No | |
| Do you believe that BS may violate human rights?Responses: Yes/No | |
| To what extent do you agree or disagree with the following statement “governments collect citizens’ biometric information for other uses than their security?Responses:1: Not at all, 2: Little, 3: moderate, 4: very, 5: very much |
References
- Smith, J.H.; Milberg, S.J.; Burke, S.J. Information privacy: Measuring individuals concerns about organizational practices. MIS Q. 1996, 20, 167–196. [Google Scholar] [CrossRef]
- Pai, C.; Wang, T.W.; Chen, T.S.; Cai, K.Y. Empirical study on Chinese tourists’ perceived trust and intention to use biometric technology. Asia Pac. J. Tour. Res 2018, 23, 880–895. [Google Scholar] [CrossRef]
- Siddique, S.; Yasmin, M.; Taher, T.B.; Alam, M. The Reliability and Acceptance of Biometric System in Bangladesh: Users Perspective. Int. J. Comput. Trends Technol. 2021, 69, 15–21. [Google Scholar] [CrossRef]
- Habibu, T.; Luhanga, E.T.; Sam, A.E. A study of users’ compliance and satisfied utilization of biometric application system. Inf. Secur. J. 2021, 30, 125–138. [Google Scholar] [CrossRef]
- Janahi, Y. The Impact of Internet Banking Adoption in the Kingdom of Bahrain-Overcoming Barriers to Adoption through the Use of Biometrics. Int. J. Innov. Creat. Change 2021, 15, 992–997. [Google Scholar]
- Laas-Mikko, K.; Kalvet, T.; Derevski, R.; Tiits, M. Promises, Social, and Ethical Challenges with Biometrics in Remote Identity Onboarding. In Handbook of Digital Face Manipulation and Detection; Rathgeb, C., Tolosana, R., Vera-Rodriguez, R., Busch, R., Eds.; Springer: Cham, Switzerland, 2022; pp. 437–462. [Google Scholar] [CrossRef]
- Stylios, I.; Kokolakis, S.; Thanou, O.; Chatzis, S. Behavioral biometrics & continuous user authentication on mobile devices: A survey. Inf. Fusion 2021, 66, 76–99. [Google Scholar] [CrossRef]
- Cornacchia, M.; Papa, F.; Sapio, B. User acceptance of voice biometrics in managing the physical access to a secure area of an international airport. Technol. Anal. Strateg. Manag. 2020, 32, 1236–1250. [Google Scholar] [CrossRef]
- Negri, N.A.R.; Borille, G.M.R.; Falcão, V.A. Acceptance of biometric technology in airport check-in. J. Air Transp. Manag. 2019, 81, 101720. [Google Scholar] [CrossRef]
- Levy, Y.; Ramim, M.M.; Furnell, S.M.; Clarke, N.L. Comparing intentions to use university-provided vs vendor-provided multibiometric authentication in online exams. CWIS 2011, 28, 102–113. [Google Scholar] [CrossRef]
- Babbie, E.R. The Practice of Social Research, 15th ed.; Cengage Learning: Hamshire, UK, 2021. [Google Scholar]
- Morosan, C. An empirical examination of U.S. Travelers’ intentions to use biometric e-gates in airports. J. Air Transp. Manag. 2016, 55, 120–128. [Google Scholar] [CrossRef]
- Kumar, D.; Rao, P.V. Implementing and analysing FAR and FRR for face and voice recognition (multimodal) using KNN classifier. Int. J. Intell. Unmanned Syst. 2020, 8, 55–67. [Google Scholar] [CrossRef]
- Taouche, C.; Belhadef, H. Multimodal biometric system combining left and right palmprints. Inf. Discov. Deliv. 2019, 48, 2–13. [Google Scholar] [CrossRef]
- Wojciechowska, A.; Choraś, M.; Kozik, R. The overview of trends and challenges in mobile biometrics. J. Appl. Comput. Mech. 2017, 16, 173–185. [Google Scholar] [CrossRef][Green Version]
- Buciu, I.; Gacsadi, A. Biometrics systems and technologies: A survey. Int. J. Comput. Commun. Control 2016, 11, 315–330. [Google Scholar] [CrossRef]
- Riaz, N.; Riaz, A.; Khan, S.A. Biometric template security: An overview. Sens. Rev. 2018, 38, 120–127. [Google Scholar] [CrossRef]
- Skalkos, A.; Stylios, I.; Karyda, M.; Kokolakis, S. Users’ Privacy Attitudes towards the Use of Behavioral Biometrics Continuous Authentication (BBCA) Technologies: A Protection Motivation Theory Approach. J. Cybersecur. Priv. 2021, 1, 743–766. [Google Scholar] [CrossRef]
- Buriro, A.; Crispo, B.; Del Frari, F.; Klardie, J.; Wrona, K. ITSME: Multi-Modal and Unobtrusive Behavioural User Authentication for Smartphones. In Technology and Practice of Passwords; Stajano, F., Mjølsnes, S.F., Jenkinson, G., Thorsheim, P., Eds.; Springer: Cham, Switzerland, 2016; pp. 45–61. [Google Scholar]
- Bansal, N.; Verma, A.; Kaur, I.; Sharma, D. Multimodal biometrics by fusion for security using genetic algorithm. In Proceedings of the IEEE 4th International Conference on Signal Processing, Computing and Control (ISPCC 2017), Solan, India, 21–23 September 2017. [Google Scholar] [CrossRef]
- Fenu, G.; Marras, M.; Boratto, L. A multi-biometric system for continuous student authentication in e-learning platforms. Pattern Recognit. Lett. 2018, 113, 83–92. [Google Scholar] [CrossRef]
- Kumar, R.; Phoha, V.V.; Jain, A. Treadmill attack on gait-based authentication systems. In Proceedings of the IEEE 7th International Conference on Biometrics Theory, Applications and Systems, Arlington, VA, USA, 8–11 September 2015; pp. 1–7. [Google Scholar]
- Kumar, D.; Rao, P.V. Prediction based person recognition using face and speech. Int. J. Eng. Sci. Technol. 2018, 7, 145–150. [Google Scholar] [CrossRef]
- Meng, W.; Wong, D.S. The effect of adaptive mechanism on behavioural biometric based mobile phone authentication. Inf. Manag. Comput. Secur. 2014, 22, 155–166. [Google Scholar] [CrossRef]
- Zhang, X.D.Y.; Xu, X.X. Android-based multimodal biometric identification system using feature level fusion. In Proceedings of the 2017 International Symposium on Intelligent Signal Processing and Communication Systems (ISPACS), Xiamen, China, 6–9 November 2017. [Google Scholar] [CrossRef]
- Xin, Y.; Liu, Y.; Liu, Z.; Zhu, X.; Kong, L.; Wei, D.; Chang, J. A survey of liveness detection methods for face biometric systems. Sens. Rev. 2018, 37, 346–356. [Google Scholar] [CrossRef]
- Li, L.Z.; Sajat, M.S.; Yusof, Y.; Fazea, Y.; Purba, H.S. The Design and User Acceptance of IoT-based Access and Entrance Control System Using Voice Recognition. Available online: https://www.researchgate.net/publication/349161710_The_Design_and_User_Acceptance_of_IoT-based_Access_and_Entrance_Control_System_Using_Voice_Recognition?channel=doi&linkId=602394184585158939936bf2&showFulltext=true (accessed on 22 March 2022).
- Miltgen, C.; Popovic, A.; Oliveira, T. Determinants of end-user acceptance of biometrics: Integrating the "Big 3" of technology acceptance with privacy context. Decis. Support Syst. 2013, 56, 103–114. [Google Scholar] [CrossRef]
- Levine, B.N.; Reiter, M.K.; Wang, C.; Wright, M.K. Timing attacks in low-latency mix-based systems. In Financial Cryptography; Juels, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 251–265. [Google Scholar]
- Habibu, T.; Luhanga, E.T.; Sam, A. Evaluation of users’ knowledge and concerns of biometric passport systems. Data 2019, 4, 58. [Google Scholar] [CrossRef]
- Malhotra, N.; Kim, S.; Agarwal, J. Internet users’ information privacy concerns: The construct, the scale, and a causal model. Inf. Syst. Res. 2004, 15, 336–355. [Google Scholar] [CrossRef]
- Hong, W.; Thong, J.Y. Internet privacy concerns: An integrated conceptualization and four empirical studies. MIS Q. 2013, 37, 275–298. [Google Scholar] [CrossRef]
- Kalkbrenner, M.T. Alpha, Omega, and H Internal Consistency Reliability Estimates: Reviewing These Options and When to Use Them. Couns. Outcome Res. Eval. 2021, 12, 1–12. [Google Scholar] [CrossRef]
- Wang, L.Y.; Lew, S.L.; Lau, S.H. An empirical study of students’ intention to use cloud e-learning in higher education. Int. J. Emerg. Technol. 2020, 15, 19–38. [Google Scholar] [CrossRef]
- Marangunić, N.; Granić, A. Technology acceptance model: A literature review from 1986 to 2013. Univers. Access Inf. Soc. 2015, 14, 81–95. [Google Scholar] [CrossRef]
- Seyal, A.H.; Turner, R. A study of executives’ use of biometrics: An application of theory of planned behaviour. Behav. Inf. Technol. 2013, 32, 1242–1256. [Google Scholar] [CrossRef]
- Venkatesh, V.; Thong, J.Y.; Xu, X. Unified theory of acceptance and use of technology: A synthesis and the road ahead. J. Assoc. Inf. Syst. 2016, 17, 328–376. [Google Scholar] [CrossRef]
- DeLone, W.H.; McLean, E.R. The DeLone and McLean model of information systems success: A ten-year update. J. Manag. Inf. Syst. 2003, 19, 9–30. [Google Scholar] [CrossRef]
- Vallerand, R. Toward a hierarchical model of intrinsic and extrinsic motivation. Adv. Exp. Soc. Psychol. 1997, 29, 271–360. [Google Scholar] [CrossRef]
- Onywoki, B.; Opiyo, E. A Framework for the Adoption of Biometric ATM Authentication in the Kenyan Banks. Available online: http://erepository.uonbi.ac.ke/bitstream/handle/11295/73528/Onywoki%20_Biometric%20ATM%20authentication%20.pdf?sequence=1 (accessed on 9 November 2022).
- Morosan, C. Customers’ adoption of biometric systems in restaurants: An extension of the technology acceptance model. J. Hosp. Mark. Manag. 2011, 20, 661–690. [Google Scholar] [CrossRef]
- Chalikias, Μ.; Lalou, P.; Manolessou, A. Research Methodology and Introduction to Statistical Data Analysis via IBM SPSS STATISTICS. 2015. Available online: https://repository.kallipos.gr/handle/11419/5075 (accessed on 12 July 2021).
- Bourdieu, P. Distinction: A Social Critique of the Judgement of Taste, 2nd ed.; Harvard University Press: Cambridge, MA, USA, 1987. [Google Scholar]
- Powell, L.M.; Wimmer, H. Parental perceptions and recommendations of computing majors: A technology acceptance model approach. Inf. Syst. Educ. J. 2017, 15, 29. [Google Scholar]
- Rea, L.M.; Parker, R.A. Designing and Conducting Survey Research: A Comprehensive Guide, 3rd ed.; John Wiley & Sons: Jossey-Bass, CA, USA, 2014. [Google Scholar]
- Ahmad, S.; Zulkurnain, N.N.A.; Khairushalimi, F.I. Assessing the Validity and Reliability of a Measurement Model in Structural Equation Modeling (SEM). Br. J. Math. Comput. Sci. 2016, 15, 1–8. [Google Scholar] [CrossRef]
- Volkamer, M.; Renaud, K. Mental models—General introduction and review of their application to human-centred security. In Number Theory and Cryptography; Fischlin, M., Katzenbeisser, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 255–280. [Google Scholar]
- Keough, E.; Muir, S. UK Now Ready for Biometric Banking. Experian. 2016. Available online: https://www.experianplc.com/media/news/2016/uk-now-ready-for-biometric-banking/ (accessed on 22 July 2021).
- Bhagavatula, R.; Ur, B.; Iacovino, K.; Kywe, S.M.; Cranor, L.F.; Savvides, M. Biometric authentication on iphone and android: Usability, perceptions, and influences on adoption. In Proceedings of the Workshop on Usable Security, (USEC 2015), San Diego, CA, USA, 8 February 2015. [Google Scholar] [CrossRef]
- Tiits, M.; Kalvet, T.; Laas-Mikko, K. Social acceptance of epassports. In Proceedings of the International Conference of the Biometrics Special Interest Group (BIOSIG), IEEE, Darmstadt, Germany, 10–12 September 2014; pp. 1–6. [Google Scholar]
- Lee, T.Z.; Bong, D.B. Face and palmprint multimodal biometric system based on bit-plane decomposition approach. In Proceedings of the IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW, 2016), Nantou, Taiwan, 27–29 May 2016. [Google Scholar] [CrossRef]
- Santa, I. Biometric Technology Enjoys Strong Support from Consumers, Says CTA|Business Wire. 2016. Available online: https://www.businesswire.com/news/home/20160330006149/en/Biometric-?-Technology-?-Enjoys-?-Strong-?-Support-?-Consumers-?-CTA (accessed on 22 July 2021).
- Doyle, J. Accenture Research Shows Citizen Support for Biometrics to Facilitate Travel and Secure Borders Accenture Newsroom. 2014. Available online: https://newsroom.accenture.com/industries/health-public-service/accenture-research-shows-citizen-support-for-use-of-biometrics-to-facilitate-travel-and-secure-borders.htm (accessed on 15 July 2021).
- El-Abed, M.; Giot, R.; Hemery, B.; Rosenberger, C. Evaluation of biometric systems: A study of users’ acceptance and satisfaction. Int. J. Biometr. 2012, 4, 265–290. [Google Scholar] [CrossRef]
- Vgena, K.; Kitsiou, A.; Kalloniatis, C.; Gritzalis, S. Determining the Role of Social Identity Attributes to the Protection of Users’ Privacy in Social Media. Future Internet 2022, 14, 249. [Google Scholar] [CrossRef]
- Vgena, K.; Kitsiou, A.; Kalloniatis, C. Understanding the role of users’ socio-location attributes and their privacy implications on social media. Inf. Comput. Secur. 2022, 30, 705–729. [Google Scholar] [CrossRef]
- Kitsiou, A.; Tzortzaki, E.; Kalloniatis, C.; Gritzalis, S. Identifying Privacy Related Requirements for the Design of Self-Adaptive Privacy Protections Schemes in Social Networks. Future Internet 2021, 13, 23. [Google Scholar] [CrossRef]
- Vgena, K.; Kitsiou, A.; Kalloniatis, C.; Kavroudakis, D.; Gritzalis, S. Toward Addressing Location Privacy Issues: New Affiliations with Social and Location Attributes. Future Internet 2019, 11, 234. [Google Scholar] [CrossRef]
- Kitsiou, A.; Tzortzaki, E.; Kalloniatis, C.; Gritzalis, S. Self Adaptive Privacy in Cloud Computing Environments: Identifying the Major Socio-Technical Concepts. In CyberICPS 2020 6th Workshop on Security of Industrial Control Systems and Cyber-Physical Systems in Conjunction with 25th European Symposium on Research in Computer Security (ESORICS); LNCS Lecture Notes in Computer Science; Katsikas, S.K., Cuppens, F., Cuppens, N., Lambrinoudakis, C., Eds.; Springer: Guildford, UK, 2020; Volume 12501, pp. 117–132. [Google Scholar]
- Kitsiou, A.; Tzortzaki, E.; Kalloniatis, C.; Gritzalis, S. Measuring Users’ Socio- contextual Attributes for Self-adaptive Privacy Within Cloud-Computing Environments. In International Conference on Trust and Privacy in Digital Business; Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 12395 LNCS; Springer: Berlin/Heidelberg, Germany, 2020; pp. 140–155. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).