Unreachable Peers Communication Scheme in Decentralized Networks Based on Peer-to-Peer Overlay Approaches
Abstract
:1. Introduction
- Node Address: For the problem of missing trusted third-party institutions in the process of switching from centralized to decentralized networks, and the problem of wasting resources by using a network-wide consensus approach as a trust module. An algorithm for generating node addresses in overlay networks is proposed. The address information either shows or implicitly contains the logical address in the DHT, the identifier for node identification and the cryptographic seed information, and the difficulty of address generation can be adjusted according to the computing power of the whole network when generating addresses. It achieves malicious node prevention in P2P networks and data security assurance without relying on centralized trusted institutions.
- Routing: For existing decentralized network organization methods using a broadcast scheme to find nodes can cause routing bottleneck problems. A decentralized networking scheme based on overlay network containing unreachable nodes is proposed, which implements logical Node ID-based addressing routing between unreachable nodes through a DHT structured scheme. Compared with the broadcast scheme, it improves the node finding efficiency and consumes fewer resources. The entire network does not depend on trusted third-party entities, so it eliminates the performance bottleneck of centralized nodes and preserves the decentralized nature of the original network.
- Communication: For the problem that the existing scheme requires a third node of full process assistance or network-wide consensus to transmit data wasting network resources when the two end nodes communicate, the transmission model of data flow under overlay network is proposed, and the data transmission channel is established using two methods, direct connection establishment and third-node relay, according to the type of unreachable nodes at both ends. After the establishment, the two nodes can communicate freely with each other without any limitations such as the amount of data to be transmitted. The scheme in this paper can minimize the consumption of additional network resources compared to existing schemes as long as the network conditions are met.
- Evaluation: The three parts of node address generation, virtual network, and communication channel establishment are evaluated in terms of their operational effectiveness by real cluster servers, and their usability and security are verified. Compared with existing centralized and decentralized solutions, our scheme does not rely on any third-party central entity in terms of trust and data transmission, and achieves efficiency improvement in virtual networking and data transmission. It better ensures the privacy of users and realizes device democracy while taking into account the transmission efficiency.
2. Related Work
3. System Model
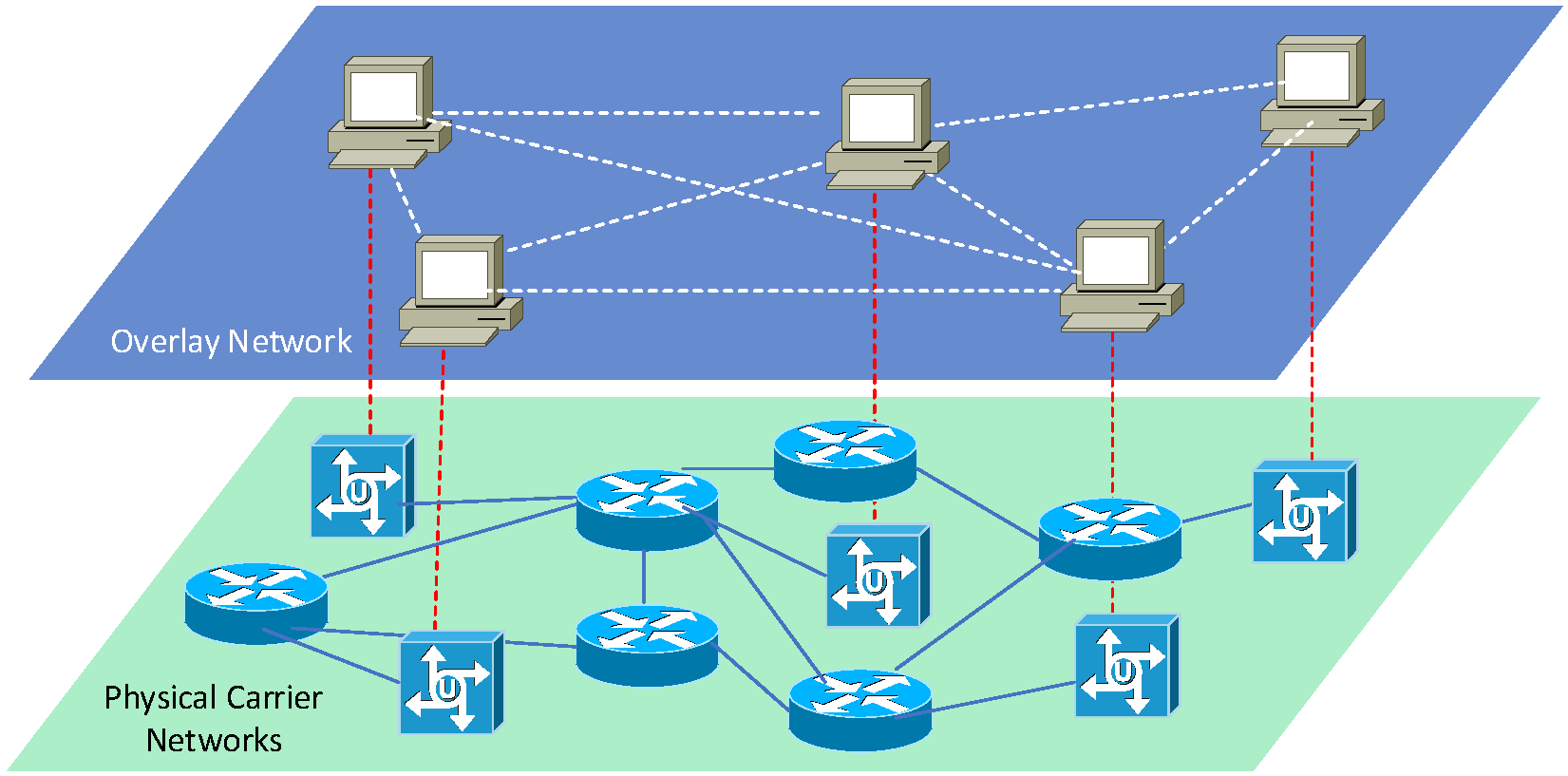
3.1. System Overview
- Reachable node: A node directly connected in the public network environment or statically mapped from the public network environment to the internet, which can passively receive packets from other nodes through the node IP address and the specified port.
- Unreachable node: A node that is behind one or more levels of NAT or firewall and cannot be actively accessed by other nodes through any port.
3.2. Threat Model and Assumptions
- (1)
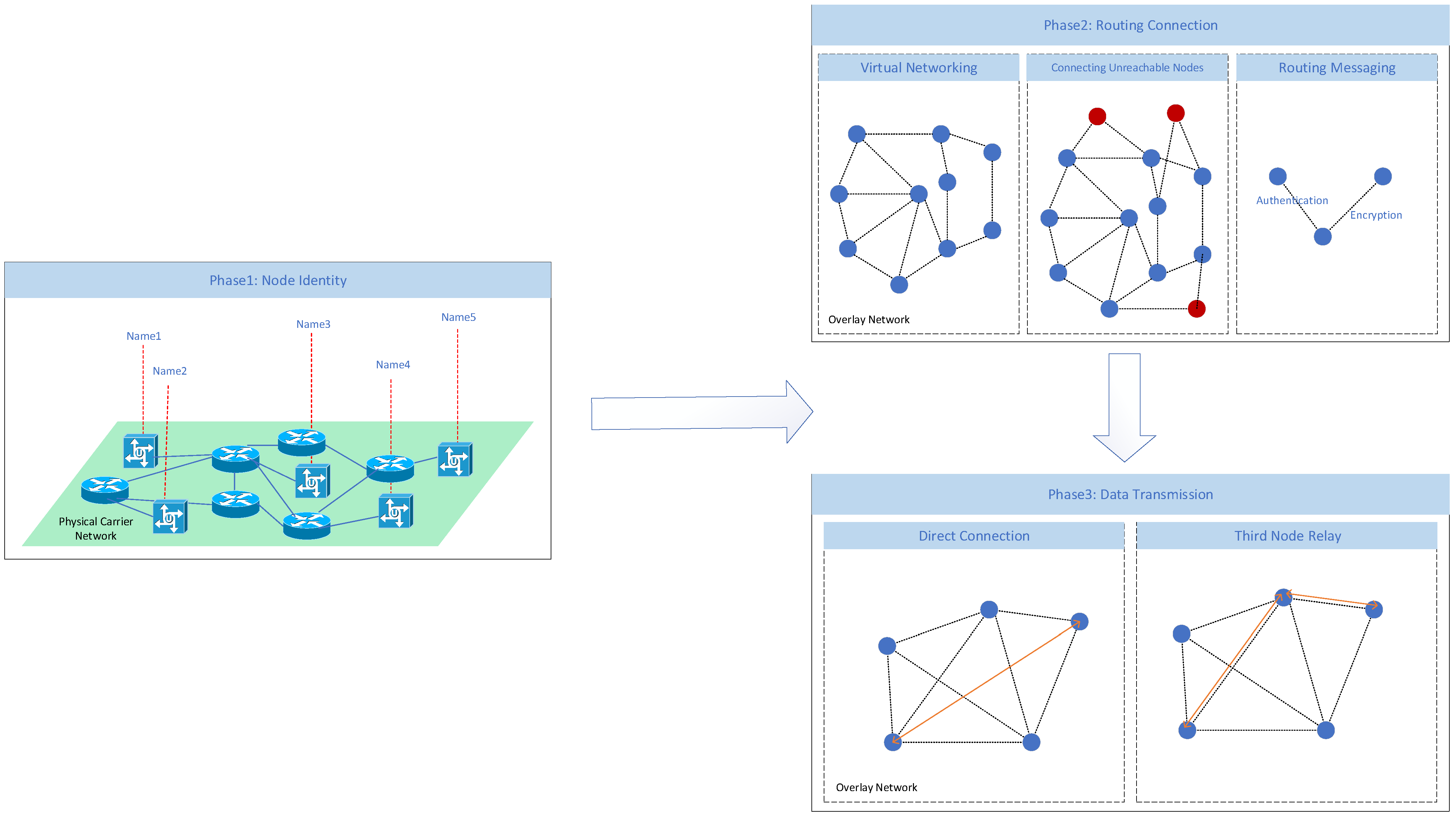
- Sybil Attack: This attack may occur in the virtual networking of second phase routing connection in Figure 4. This is an attack unique to decentralized networks, and if not prevented could lead to identity impersonation or even the entire network going down. As shown in Figure 5, there is no authentication authority in P2P networks, so it is costless for users to create nodes, which means that attackers can go to forge identities to join the network very easily. After that, they will try to obtain a large amount of node information in the network and make some malicious behaviors based on it, such as sending false node information, misleading the normal information transfer between nodes, faking the identity of normal nodes, not responding to network connection requests, etc.
- (2)
- Eclipse Attack: This attack may also occur in the virtual networking of second phase routing connection in Figure 4. The eclipse attack usually has to be coupled with a Sybil attack, where the attacker adds enough fake nodes around a certain victim by appropriating the routes of nodes in the network and finding some nodes with similar addresses, thus isolating the normal nodes outside the normal P2P network, as shown in Figure 6.
- (3)
- DDoS Attack: This attack may occur in the routing messaging of second phase routing connection in Figure 4. In P2P networks, DDoS is different from the common centralized systems. The new DDoS attack does not require the establishment of a botnet to launch a large-scale attack, which is not only low-cost and powerful, but also ensures the secrecy of the attacker. In this way, if not prevented at the connection and authentication stages, it can have more serious consequences than centralized networks.
- (1)
- Man-in-the-Middle Attack: This attack may occur in the various stages of third phase data transmission in Figure 4. In a centralized network, the authentication of the communication between two parties requires the participation of an authoritative and trusted institution, which in turn ensures the security of the authentication. In a decentralized network, there are many objects that need to communicate. On the one hand, since all nodes are peer-to-peer nodes, there is no certain authoritative centralized trusted authority. On the other hand, the overhead of authentication when communicating with a large number of nodes is too high. So authentication cannot be performed in this way, making MITM attacks more likely to occur in decentralized networks.
- (2)
- Replay Attacks: Replay attacks can happen during any network communication including routed messaging and data transmission in Figure 4. In decentralized networks, replay attacks on routing messages may cause an attacker to send intercepted packets repeatedly without breaking the cryptographic security, resulting in confusing routing information in P2P networks. Replay attacks on transport messages can bring about authentication problems in the network. So it is very important for the security of routed messaging and data transmission.
- (3)
- Data Eavesdropping Attacks: This attack may occur in the various stages of third phase data transmission in Figure 4. In the case of data encryption decrypt the data by means of MITM attack. In decentralized networks due to the more complex path of data, compared to centralized networks the possibility of attackers intercepting the packets is increased. Therefore, special care should be taken in decentralized networks to prevent such attacks.
3.3. Requirements
- Turst: Since each node in the decentralized network can join at will and it is a non-trust environment, it is important to achieve mutual trust of nodes in the non-trust network and achieve identity authentication.
- Privacy: Control information, routing, data, etc. transmitted between nodes or between users are not intercepted and tampered with by other nodes.
- Security: Prevent attacks during P2P network and communication to ensure the stability and security of the whole network.
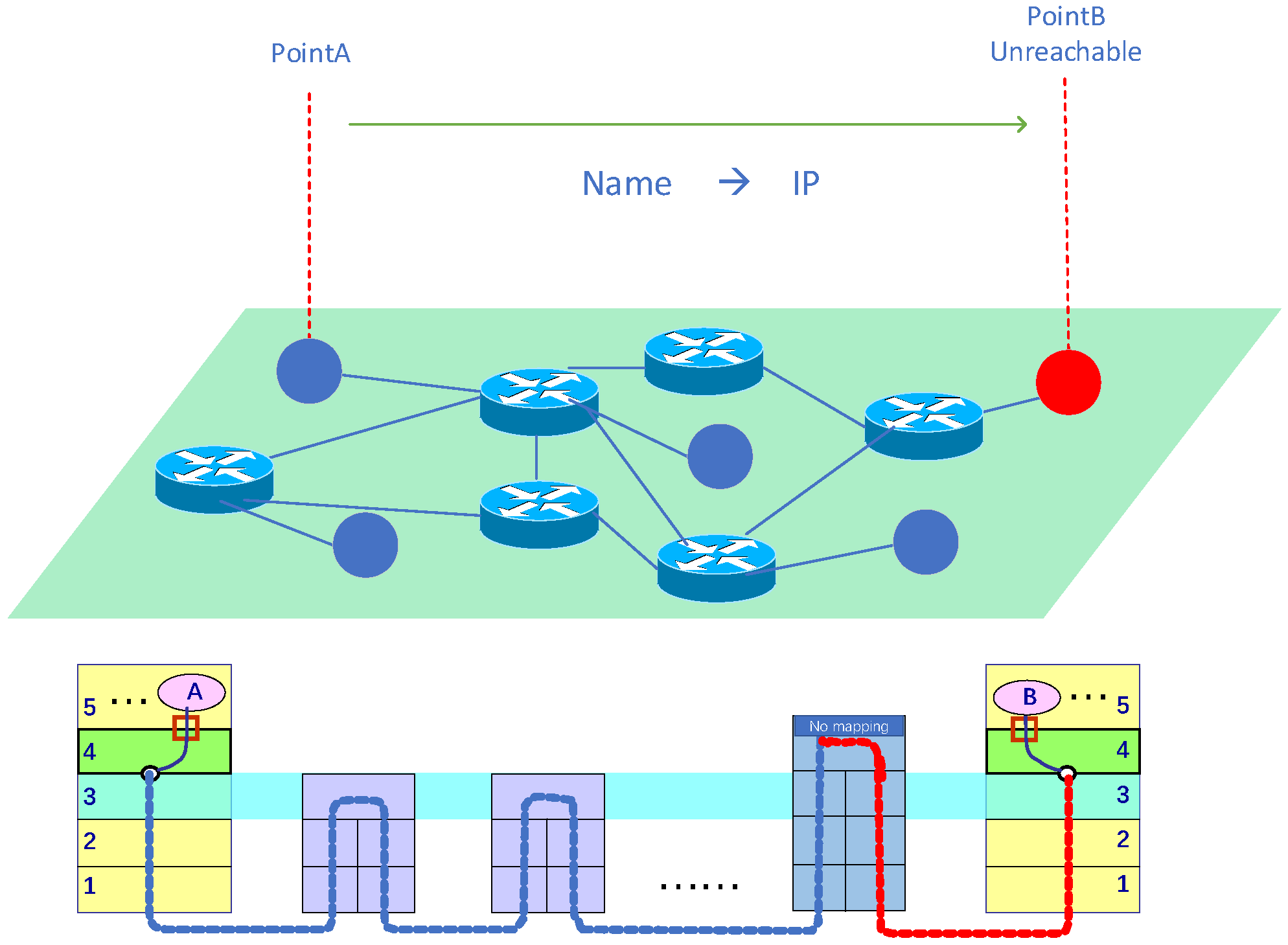
- Search Convenience: The node is found independent of its IP address, and the conditions required to find it remain unchanged when its IP address changes, enabling IP address-independent finding of unreachable nodes.
- Connection Efficiency: When two nodes are communicating, it is possible to quickly realize that the road has messages arriving, providing the prerequisites for establishing a connection.
- Network Adaptability: The connection of unreachable nodes can adapt to various NAT network environments to ensure the success rate of the connection, and choose the mode of third point relay in case of unsuccessful direct connection.
4. System Design
4.1. Node Identity
4.1.1. Address Generation
- Logical address: Logical address of the P2P overlay network, used for P2P network basic operations such as virtual networking and routing connections in DHT.
- Identity: The unique identity used by the node for authentication, and the node performs identity authentication in both directions before transmitting information.
- Encryption Key: The key for encrypting transmission, used to encrypt control information or routing information when transmitting.
| Algorithm 1: Routable generation algorithm in P2P overlay network |
 |
4.1.2. Authentication and Encrypted Transmission
- Public message transmission: Transferring information that can be made public in the network between two nodes, verifying each other’s nodes’ identities, signing the authenticity of messages and preventing them from being tampered with, but not from being eavesdropped. Generally only one round of interaction takes place, so no transmission channel is established.
- Confidential message transmission: Encrypted messages are delivered between two nodes, generally transmitting user data with large data volumes, so virtual encrypted channels are established to ensure the confidentiality of messages based on two-way identity authentication.
- (1)
- Node A first initiates a connection to Node B, sending its public key and .
- (2)
- Node B verifies that the and the public key sent by Node A satisfy the correspondence, as well as calculating whether satisfies the requirements in the network. Generate the random number . Sign the public key of node B and using the private key and send the data and signature to node A.
- (3)
- Node A verifies that the and the public key sent by Node B satisfy the correspondence. Verify that the signature is correct using the public key of node B. Generate a random number . Sign , , the data to be passed using the private key, and send all data and the signature to node B.
- (4)
- Node B uses the public key of node A to verify that the signature of the message sent by node A is correct, compares the sent with the random number generated by node B. The data and to be sent are signed with the public key of node B, and the data and signature are sent to node A.
- (5)
- Node A uses the public key of node B to verify that the signature of the message sent by node B is correct, and compares whether the sent is whether the random number generated by Node A.
- (1)
- Node A first initiates a connection to Node B, sending its public key and .
- (2)
- Node B verifies that the and public key sent by node A satisfy the correspondence, as well as calculates whether satisfies the requirements in the network. Generate a new elliptic curve private key , calculate based on the elliptic curve shared parameter base point G, sign the public key of node B and using the private key, and send the data with the signature result to node A.
- (3)
- Node A verifies that the NodeID and the public key sent by Node B satisfy the correspondence. Verify that the signature is correct using the public key of node B. Generate a new elliptic curve private key , compute . Compute symmetric key for DES encrypted transmission, generate vector at random. Sign and using the private key and send the data with the signature result to node B.
- (4)
- Node B uses the public key of node A to verify that the message signature from node A is correct and calculates the symmetric key used for DES encrypted transmission. At that time, node A and node B have the same DES encryption key S and vector, then use this key to encrypt the request to establish a channel command to send to node A.
- (5)
- After receiving the data, node A decrypts the data using S and . The data to be communicated can be sent to node B. The encrypted communication channel is thus established.
4.2. Virtual Networking
4.2.1. Overlay Network
4.2.2. Route Connection
- Bootstrap Node: In this system, first we need some bootstrap nodes so that nodes can join to the whole P2P network through them. We define a series of bootstrap nodes . They are all reachable nodes, . When a node wants to join the P2P network, it first connects to any bootstrap node and then integrates into the whole P2P network according to the algorithm. A total of n bootstrap nodes serve as a backup for each other and also share the pressure of network connection. The bootstrap nodes need to expose the , IP address and port number after booting so that nodes can connect to them with this information. The triad can be hard-coded in the system, or it can be dynamically updated and obtained using DNS system. Additionally, load-balanced DNS also allows for a balanced distribution of traffic across bootstrap nodes.
- K-bucket: Each reachable node has two k-buckets, which are stored in a binary tree. One of the k-buckets is used to store the logical address information of other reachable nodes, which can be used to find the nearest reachable node quickly. The definition of k-buckets and binary trees, and the update algorithm are the same as the standard Kademlia algorithm. The function is defined to store another reachable node at the reachable node.
- Node joining: As mentioned earlier, the node joins the overlay network by first connecting to the bootstrap node. Then it becomes part of the network by joining to the network through the node. The joining algorithm of nodes is shown in Algorithm 2.
| Algorithm 2: Nodes (reachable nodes , unreachable nodes ) join algorithm |
 |
- Unreachable node: After joining the network, the unreachable node needs to keep alive the long connection with N nodes, in addition to executing lines 12–20 of Algorithm 2 cyclically to ensure that it is always connected to the N nodes closest to its address. When a closer node is found, the long connection to the more distant node is disconnected while contact is made with the closer node.
- Reachable node: After the reachable nodes join the network, they need to respond to the query operations of other nodes with the connection operations of unreachable nodes. In this process, the two k-buckets are split and merged in a timely manner according to the k-bucket update method described in the previous section. The long connection with the unreachable node is periodically tested for normalness, and if it is adjudged to be a deactivated node, this node is removed from the k-bucket.
4.2.3. Peer Discovery for Unreachable Node
| Algorithm 3: Nodes (reachable nodes , unreachable nodes ) lookup (discovery) algorithm |
 |
| Algorithm 4: FindPeers() procedure in reachable nodes |
 |
4.3. Communication Channels
4.3.1. Connection Directly
- (1)
- First, assume that node has already determined that node is unreachable by the method described previously, and has found a reachable node r that maintains a long connection with node , and has already established an encrypted transmission channel. When the node and the node have the intention to establish a communication channel, an initialisation message to help establish the connection is sent to the reachable node r.
- (2)
- The reachable node r receives the message and finds the long connection session of node in its own table of unreachable nodes, and sends to node a message about the wish of node to connect and an already open UDP port.
- (3)
- The node receives the message and sends a UDP packet to the open port of the reachable node r and informs the reachable node r via a long connection.
- (4)
- The reachable node r receives the UDP packet and records the IP address and port number of the source of the packet. This is the IP address and port number that the node maps to the public network, and then sends this information to the node along with an open UDP port of the reachable node r.
- (5)
- After receiving the message, node sends a UDP packet to the open port of reachable node r and informs reachable node r via a long connection.
- (6)
- Reachable node r receives a UDP packet and records the IP address and port number of the source of the packet. This is the IP address and port number that node maps to the public network and then sends this information to node .
- (7)
- The node receives it and sends a UDP packet to the IP address and port number that the node injects into the public network. Obviously this packet will not be received by because the NAT device or firewall prior to node does not have this address mapped. However, the NAT device or firewall prior to node has created a mapping for this IP address to the port. After sending the UDP packet a message is sent to the reachable node that the transmission has been completed.
- (8)
- Reachable node r receives this message and forwards it to node .
- (9)
- After receiving this message, node sends a UDP packet to the IP address and port number of node mapped to the public network.
- (10)
- At this point the node can accept the packet as it has already established a mapping in the previous NAT device or firewall. Next, a UDP packet is sent to the IP address and port number mapped to the public network by node . At this point the direct connection data channel has been successfully established.
4.3.2. Connection by Third-Node Relay
- (1)
- First, assume that node has already determined that node is unreachable by the method described previously, and has found a reachable node r that maintains a long connection with node , and has already established an encrypted transmission channel. When the node and the node have the intention to establish a communication channel, an initialisation message to help establish the connection is sent to the reachable node r.
- (2)
- Reachable node r receives the message and finds the long connection session of node in its own table of unreachable nodes and sends a message to node about the wish of node to connect.
- (3)
- Once received by the node, a transmission channel to the reachable node is established using public message transmission. At this time messages can be viewed by a third party, but are tamper-proof.
- (4)
- After the establishment of the transmission channel is complete, the reachable node r establishes a transmission channel with the node.
- (5)
- After the establishment is complete, the authentication between unreachable nodes and is started.
5. Evaluation
5.1. Address Generation Evaluation
5.2. P2P Network Simulation Method
5.3. Network Evaluation
5.3.1. Virtual Network Evaluation
5.3.2. Communication Channels Establish Evaluation
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Leiner, B.M.; Cerf, V.G.; Clark, D.D.; Kahn, R.E.; Kleinrock, L.; Lynch, D.C.; Postel, J.; Roberts, L.G.; Wolff, S. A brief history of the Internet. ACM SIGCOMM Comput. Commun. Rev. 2009, 39, 22–31. [Google Scholar] [CrossRef]
- Sharma, N.; Shamkuwar, M.; Singh, I. The history, present and future with IoT. In Internet of Things and Big Data Analytics for Smart Generation; Springer: Berlin/Heidelberg, Germany, 2019; pp. 27–51. [Google Scholar]
- Gumrukcu, E.; Arsalan, A.; Muriithi, G.; Joglekar, C.; Aboulebdeh, A.; Zehir, M.A.; Papari, B.; Monti, A. Impact of Cyber-attacks on EV Charging Coordination: The Case of Single Point of Failure. In Proceedings of the 2022 4th Global Power, Energy and Communication Conference (GPECOM), Buenos Aires, Argentina, 26–28 February 2020; IEEE: New York, NY, USA, 2022; pp. 506–511. [Google Scholar]
- Stark, E.; Sleevi, R.; Muminovic, R.; O’Brien, D.; Messeri, E.; Felt, A.P.; McMillion, B.; Tabriz, P. Does certificate transparency break the web? Measuring adoption and error rate. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; IEEE: New York, NY, USA, 2019; pp. 211–226. [Google Scholar]
- Li, B.; Lin, J.; Li, F.; Wang, Q.; Li, Q.; Jing, J.; Wang, C. Certificate transparency in the wild: Exploring the reliability of monitors. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 2505–2520. [Google Scholar]
- Chen, F.; Duan, H.; Zheng, X.; Jiang, J.; Chen, J. Path Leaks of HTTPS Side-Channel by Cookie Injection. In Proceedings of the International Workshop on Constructive Side-Channel Analysis and Secure Design, Singapore, 23–24 April 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 189–203. [Google Scholar]
- Oukemeni, S.; Rifà-Pous, H.; Puig, J.M.M. Privacy analysis on microblogging online social networks: A survey. ACM Comput. Surv. (CSUR) 2019, 52, 1–36. [Google Scholar] [CrossRef] [Green Version]
- Mare, S.; Girvin, L.; Roesner, F.; Kohno, T. Consumer smart homes: Where we are and where we need to go. In Proceedings of the 20th International Workshop on Mobile Computing Systems and Applications, Santa Cruz, CA, USA, 27–28 February 2019; pp. 117–122. [Google Scholar]
- Pouwelse, J.; Garbacki, P.; Epema, D.; Sips, H. The bittorrent p2p file-sharing system: Measurements and analysis. In International Workshop on Peer-to-Peer Systems; Springer: Berlin/Heidelberg, Germany, 2005; pp. 205–216. [Google Scholar]
- Honigsberg, P.J. The evolution and revolution of Napster. USFL Rev. 2001, 36, 473. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 September 2022).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Dai, W.; Dai, C.; Choo, K.K.R.; Cui, C.; Zou, D.; Jin, H. SDTE: A secure blockchain-based data trading ecosystem. IEEE Trans. Inf. Forensics Secur. 2019, 15, 725–737. [Google Scholar] [CrossRef]
- Kalbantner, J.; Markantonakis, K.; Hurley-Smith, D.; Akram, R.N.; Semal, B. P2PEdge: A Decentralised, Scalable P2P Architecture for Energy Trading in Real-Time. Energies 2021, 14, 606. [Google Scholar] [CrossRef]
- Zheng, S.; Pan, L.; Hu, D.; Li, M.; Fan, Y. A blockchain-based trading platform for big data. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; IEEE: New York, NY, USA, 2020; pp. 991–996. [Google Scholar]
- Ma, X.; Ma, J.; Li, H.; Jiang, Q.; Gao, S. ARMOR: A trust-based privacy-preserving framework for decentralized friend recommendation in online social networks. Future Gener. Comput. Syst. 2018, 79, 82–94. [Google Scholar] [CrossRef]
- Jiang, L.; Zhang, X. BCOSN: A blockchain-based decentralized online social network. IEEE Trans. Comput. Soc. Syst. 2019, 6, 1454–1466. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Zhong, X.; Wang, J.; Li, X. On mapping of address and port using translation. Int. J. Inf. Comput. Secur. 2019, 11, 214–232. [Google Scholar] [CrossRef]
- Ibhaze, A.E.; Okoyeigbo, O.; Samson, U.A.; Obba, P.; Okakwu, I.K. Performance evaluation of IPv6 and IPv4 for future technologies. In Proceedings of the Future of Information and Communication Conference, San Francisco, CA, USA, 5–6 March 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 15–22. [Google Scholar]
- Zander, S.; Wang, X. Are we there yet? IPv6 in Australia and China. ACM Trans. Internet Technol. (TOIT) 2018, 18, 1–20. [Google Scholar] [CrossRef]
- Hamarsheh, A.; Abdalaziz, Y.; Nashwan, S. Recent impediments in deploying IPv6. Adv. Sci. Technol. Eng. Syst. 2021, 6, 336–341. [Google Scholar] [CrossRef]
- Egevang, K.; Francis, P. The IP Network Address Translator (NAT); RFC 1631; Internet Engineering Task Force (IETF): Fremont, CA, USA, 1994. [Google Scholar]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Henningsen, S.; Florian, M.; Rust, S.; Scheuermann, B. Mapping the interplanetary filesystem. In Proceedings of the 2020 IFIP Networking Conference (Networking), Paris, France, 22–25 June 2020; pp. 289–297. [Google Scholar]
- Wang, L.; Pustogarov, I. Towards better understanding of bitcoin unreachable peers. arXiv 2017, arXiv:1709.06837. [Google Scholar]
- Baset, S.A.; Schulzrinne, H. An analysis of the skype peer-to-peer internet telephony protocol. arXiv 2004, arXiv:cs/0412017. [Google Scholar]
- Saldamli, G.; Upadhyay, C.; Jadhav, D.; Shrishrimal, R.; Patil, B.; Tawalbeh, L. Improved gossip protocol for blockchain applications. Clust. Comput. 2022, 25, 1915–1926. [Google Scholar] [CrossRef]
- Silvano, W.F.; Marcelino, R. Iota Tangle: A cryptocurrency to communicate Internet-of-Things data. Future Gener. Comput. Syst. 2020, 112, 307–319. [Google Scholar] [CrossRef]
- Guidi, B.; Michienzi, A.; Ricci, L. A libP2P Implementation of the Bitcoin Block Exchange Protocol. In Proceedings of the 2nd International Workshop on Distributed Infrastructure for Common Good, Virtual Event Canada, 6–10 December 2021; pp. 1–4. [Google Scholar]
- Petit-Huguenin, M.; Salgueiro, G.; Rosenberg, J.; Wing, D.; Mahy, R.; Matthews, P. Session Traversal Utilities for NAT (STUN); RFC 8489; IETF: Wilmington, DE, USA, 2020. [Google Scholar]
- Reddy, T.; Johnston, A.; Matthews, P.; Rosenberg, J. Traversal Using Relays around NAT (TURN): Relay Extensions to Session Traversal Utilities for NAT (STUN); RFC 8656; IETF: Wilmington, DE, USA, 2020. [Google Scholar]
- Wing, D.; Cheshire, S.; Boucadair, M.; Penno, R.; Selkirk, P. Port Control Protocol (PCP); Technical Report; IETF: Wilmington, DE, USA, 2013. [Google Scholar]
- Boucadair, M.; Penno, R.; Wing, D. Universal Plug and Play (Upnp) Internet Gateway Device-Port Control Protocol Interworking Function (IGD-PCP IWF); RFC 6970; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2013. [Google Scholar]
- Kfoury, E.F.; Gomez, J.; Crichigno, J.; Bou-Harb, E.; Khoury, D. Decentralized distribution of PCP mappings over blockchain for end-to-end secure direct communications. IEEE Access 2019, 7, 110159–110173. [Google Scholar] [CrossRef]
- Patsonakis, C.; Samari, K.; Kiayiasy, A.; Roussopoulos, M. On the practicality of a smart contract PKI. In Proceedings of the 2019 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPCON), Newark, CA, USA, 4–9 April 2019; pp. 109–118. [Google Scholar]
- Ali, M.; Nelson, J.; Shea, R.; Freedman, M.J. Blockstack: A global naming and storage system secured by blockchains. In Proceedings of the 2016 USENIX Annual Technical Conference (USENIX ATC 16), Denver, CO, USA, 22–24 June 2016; pp. 181–194. [Google Scholar]
- Cheshire, S.; Krochmal, M. Nat Port Mapping Protocol (Nat-Pmp); Technical Report; IETF: Wilmington, DE, USA, 2013. [Google Scholar]
- Xia, W.; Wen, Y.; Foh, C.H.; Niyato, D.; Xie, H. A survey on software-defined networking. IEEE Commun. Surv. Tutor. 2014, 17, 27–51. [Google Scholar] [CrossRef]
- Wang, H.C.; Chen, C.; Lu, S.H. An sdn-based nat traversal mechanism for end-to-end iot networking. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; IEEE: New York, NY, USA, 2019; pp. 1–4. [Google Scholar]
- Subratie, K.; Figueiredo, R. Towards island networks: SDN-enabled virtual private networks with peer-to-peer overlay links for edge computing. In Proceedings of the International Conference on Internet and Distributed Computing Systems, Tokyo, Japan, 11–13 October 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 122–133. [Google Scholar]
- Kavalionak, H.; Payberah, A.H.; Montresor, A.; Dowling, J. Natcloud: Cloud-assisted nat-traversal service. In Proceedings of the 31st Annual ACM Symposium on Applied Computing, Pisa, Italy, 4–8 April 2016; pp. 508–513. [Google Scholar]
- Garcia, B.; Gortazar, F.; Lopez-Fernandez, L.; Gallego, M.; Paris, M. WebRTC testing: Challenges and practical solutions. IEEE Commun. Stand. Mag. 2017, 1, 36–42. [Google Scholar] [CrossRef]
- Novo, O. Making constrained things reachable: A secure IP-agnostic NAT traversal approach for IoT. ACM Trans. Internet Technol. (TOIT) 2018, 19, 1–21. [Google Scholar] [CrossRef]
- Saka, R.; Uehara, M. Web API-based NAT traversal in managed network blocks. In Proceedings of the Conference on Complex, Intelligent, and Software Intensive Systems, Matsue, Japan, 4–6 July 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 660–669. [Google Scholar]
- Kim, G.; Kim, J.; Lee, S. An SDN based fully distributed NAT traversal scheme for IoT global connectivity. In Proceedings of the 2015 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 28–30 October 2015; IEEE: New York, NY, USA, 2015; pp. 807–809. [Google Scholar]
- Hansen, H.V.; Goebel, V.; Plagemann, T. DevCom: Device communities for user-friendly and trustworthy communication, sharing, and collaboration. Comput. Commun. 2016, 85, 14–27. [Google Scholar] [CrossRef]
- Ford, B. UIA: A Global Connectivity Architecture for Mobile Personal Devices. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2008. [Google Scholar]
- Ding, D.; Conti, M.; Figueiredo, R. SAND: Social-aware, network-failure resilient, and decentralized microblogging system. Future Gener. Comput. Syst. 2019, 93, 637–650. [Google Scholar] [CrossRef]
- Aslanoglou, C.; Konstantopoulos, M.; Chondros, N.; Roussopoulos, M. Take Back your Friends with DCS: A Decentralized Connectivity Service for private social communication apps. In Proceedings of the 2020 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Oxford, UK, 3–6 August 2020; IEEE: New York, NY, USA, 2020; pp. 133–138. [Google Scholar]
- Kfoury, E.; Khoury, D. Securing natted iot devices using ethereum blockchain and distributed turn servers. In Proceedings of the 2018 10th International Conference on Advanced Infocomm Technology (ICAIT), Stockholm, Sweden, 12–15 August 2018; IEEE: New York, NY, USA, 2018; pp. 115–121. [Google Scholar]
- Keizer, N.V.; Ascigil, O.; Psaras, I.; Pavlou, G. Rewarding relays for decentralised nat traversal using smart contracts. In Proceedings of the Twenty-First International Symposium on Theory, Algorithmic Foundations, and Protocol Design for Mobile Networks and Mobile Computing, Virtual, 11–14 October 2020; pp. 309–314. [Google Scholar]
- Kamel, M.; Ligeti, P.; Nagy, A.; Reich, C. Distributed Address Table (DAT): A decentralized model for end-to-end communication in IoT. Peer-Netw. Appl. 2022, 15, 178–193. [Google Scholar] [CrossRef]
- Maymounkov, P.; Mazieres, D. Kademlia: A peer-to-peer information system based on the xor metric. In Proceedings of the International Workshop on Peer-to-Peer Systems, Cambridge, MA, USA, 7–8 March 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 53–65. [Google Scholar]
- Soni, D.; Makwana, A. A survey on mqtt: A protocol of internet of things (iot). In Proceedings of the International Conference on Telecommunication, Power Analysis and Computing Techniques (ICTPACT-2017), Chennai, India, 6–8 April 2017; Volume 20, pp. 173–177. [Google Scholar]
- Tariq, M.A.; Khan, M.; Raza Khan, M.T.; Kim, D. Enhancements and challenges in coap—A survey. Sensors 2020, 20, 6391. [Google Scholar] [CrossRef]
- Rais, R.N.B.; Abdelmoula, M.; Turletti, T.; Obraczka, K. Naming for heterogeneous networks prone to episodic connectivity. In Proceedings of the 2011 IEEE Wireless Communications and Networking Conference, Cancun, Mexico, 28–31 March 2011; IEEE: New York, NY, USA, 2011; pp. 1091–1096. [Google Scholar]

















| Group | Number | Time | Average Time of per Time | 8 bit ‘0’ | 16 bit ‘0’ |
|---|---|---|---|---|---|
| 1 | 1000 | 605 s | 0.605 s | 47 | 1 |
| 2 | 1000 | 653 s | 0.653 s | 53 | 3 |
| 3 | 1000 | 589 s | 0.589 s | 43 | 0 |
| 4 | 1000 | 621 s | 0.621 s | 55 | 2 |
| 5 | 1000 | 660 s | 0.660 s | 62 | 5 |
| Item | Numerical Value (HEX) |
|---|---|
| Maximum | 0xffffb1931c879140b7561882a8953cb7abef14f3 |
| Minimum | 0x502a121f6e286d8eda6c1a0f411bdf07e5d3 |
| Average | 0x801e79cb28bc725f94b84c200bb522dc4ef9efe0 |
| Variance | 0x1.54f215601abd8E+80 |
| NAT Traversal Capability | Decentralized | Centralized Authority | Central Bottlenecks | Additional Deployments | Encryption and Authentication Security Dependencies | User Autonomy | Transmission Security | |
|---|---|---|---|---|---|---|---|---|
| Centric solutions [54,55] | Yes | No | Yes | Yes | Yes | CA Institutions | No | Centralized institutional customization |
| Decentralized naming systems [36,46,47,56] | No | Yes | No | —— | —— | —— | Yes | —— |
| Decentralized solutions in this paper | Yes | Yes | No | No | No | Cryptographic algorithms and decentralization | Yes | Forced |
| Decentralized Node Organization | Flooding Bottlenecks | Centralized Organizations/Institutions | User Autonomy/ Device Democracy | Peer-To-Peer Data Channels | CA Trusted Institutions | Connection Method | NAT Traversal Capability | Dependent on ISP Device Support | |
|---|---|---|---|---|---|---|---|---|---|
| Keizer et al. [51] | Unstructured | Existence | No | Yes | Can be established | —— | Relay | Reliance on relay method | No |
| Kamel et al. [52] | Structured | Not existence | Yes | No | Cannot be established | Need | Message | Dependent message mechanism | No |
| Decentralized PCP and decentralized SDN [34,45] | Unstructured | Existence | No | Yes | Can be established | —— | Direct connection | Reliance on ISP device protocols | Yes |
| Decentralized solutions in this paper | Structured | Not existence | No | Yes | Can be established | No need | Direct and Relay | No reliance on other | No |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, G.; Wang, C.; Wang, H. Unreachable Peers Communication Scheme in Decentralized Networks Based on Peer-to-Peer Overlay Approaches. Future Internet 2022, 14, 290. https://doi.org/10.3390/fi14100290
Li G, Wang C, Wang H. Unreachable Peers Communication Scheme in Decentralized Networks Based on Peer-to-Peer Overlay Approaches. Future Internet. 2022; 14(10):290. https://doi.org/10.3390/fi14100290
Chicago/Turabian StyleLi, Gengxian, Chundong Wang, and Huaibin Wang. 2022. "Unreachable Peers Communication Scheme in Decentralized Networks Based on Peer-to-Peer Overlay Approaches" Future Internet 14, no. 10: 290. https://doi.org/10.3390/fi14100290
APA StyleLi, G., Wang, C., & Wang, H. (2022). Unreachable Peers Communication Scheme in Decentralized Networks Based on Peer-to-Peer Overlay Approaches. Future Internet, 14(10), 290. https://doi.org/10.3390/fi14100290






