1. Introduction
In recent years, the blockchain technology has risen rapidly, which brings new business opportunities in the field of the economy and the Internet for many global financial institutions and IT companies [
1]. We can say that, if the Internet realizes the dissemination of information, then the blockchain will further realize the transmission of value, which means that the blockchain technology is one of the disruptive technologies for the next generation of the Internet. The core of the blockchain technology is the decentralized structure and the asymmetric encryption method, which ensure the security and irreparable modification of the data and solve the trust problem in the network. As the backbone technology of the future Internet, the blockchain technology has the potential to subvert the Internet infrastructure [
2]. At the same time, the application services based on the blockchain technology are characterized by large amount of data broadcasting with high frequency, so the data is frequently generated and frequently distributed to the nodes in the network, which requires better quality of service in the network, such as transmission speed. The transmission mechanism of the traditional TCP/IP network is a point-to-point transmission system [
3]. It means, when a blockchain-based application is used, it will generate great broadcast overhead and transmission delay, which has a great impact on the subsequent development of the blockchain-based applications.
There are two main directions for how to optimize the performances for the blockchain-based applications. One is based on the TCP/IP network for certain improvements and optimizations. For example, Guan wen Zhong [
4] proposed a hardware/software co-designed architecture for the proxy to accelerate the broadcast speed of the blockchain. They customize the Stratum protocol with a layer 2 broadcast mechanism instead of using TCP/IP connections. Another direction for optimization is to use a new network architecture to support the blockchain-based applications. Swapnoneel Roy [
5] chose to use NDN to support the blockchain-based applications. Tong Jin proposed BlcokNDN [
6], a bitcoin blockchain decentralized system over named data networking. They proposed a naming rules, by using the rules, the block is named an interest packet and is broadcast according to the transmission rules of the NDN network. Additionally, Guo [
7] presented BoNDN, which enables blockchain applications over NDN. In order to achieve compatibility between NDN and blockchain, they improved the blockchain data transmission process, and transmitted blocks on the network through interest broadcasting. The NDN network is very similar to the structure of the blockchain network. Both of them adopt a distributed structure and have a content-centric distribution mechanism. The information transmission mechanism of the NDN network naturally supports data distribution better than IP network. All in all, NDN provides a completely decentralized system and simplifies the system architecture. It also reduces the weak connection and the broadcast overhead. Similarly, there are some research to improve the transmission performance of NDN networks, for example, Majed investigated the existing NDN name search methods [
8], analyzed and compared common name search methods, and points out the direction of future work. In addition, Ioanna Angeliki Kapetanidou proposed a reputation-based trust method that can complement existing methods to improve the trust and security of NDN networks [
9].
In this paper, we conducted a design research and propose a blockchain information acceleration strategy based on the NDN network, where the NDN network provides fast data broadcasting services for the blockchain system. Specifically, we selected some important nodes in the network to provide them with greater bandwidth and cache to accelerate the transmission of blockchain information. We present a method to calculate the number of secondary nodes, and give the function to calculate the importance of each node, these methods are used to select appropriate nodes as secondary nodes in the network. The main contributions of this paper are as follows:
(1) We propose an information acceleration strategy combining with graph theory and probability theory, which can reduce data transmission delay and data overhead. We give the concept of secondary node and introduce its function.
(2) We jointly consider the data transmission capacity of the node, the communication weight of the node-related data link, and the degree of the node, present the concept of the importance of the node, and give a calculation method.
(3) In order to select an appropriate number of nodes as secondary nodes in the network, a calculation method is proposed based on the concept of graph theory. Combined with the real network topology, we can calculate the number of secondary nodes in the target network according to this method.
This paper is organized as follows. The background knowledge of the NDN and the blockchain technology is introduced in
Section 2. The
Section 3 introduces the system model, including network model and blockchain system model. The information acceleration transmission strategy is presented in
Section 4, and the concept of secondary nodes and the algorithm about how to select the secondary nodes are also given in this section. In
Section 5, we introduce and discuss the simulation results. In
Section 6, we summarize the work done in this paper and propose several subsequent improvements.
2. Theoretical Support
In this section, we introduce the related technologies of blockchain and NDN network, which provide theoretical support for our proposed information acceleration strategy.
The blockchain technology is a data structure that combines blocks in a chain [
10]. It is suitable for storing simple, hierarchical data that can be verified in the system. It is guaranteed by cryptography that the data cannot be falsified or forged [
11]. It enables participants to build consensus on the sequence of events and current state of the entire network transaction record [
12]. In fact, the blockchain technology is not a new technology, it is a combination of various existing technologies, such as encryption algorithms and P2P transmission, etc. They are combined with database technology to form a new way of recording, delivering, storing, and presenting data [
13]. The blockchain technology constructs a P2P self-organizing network using a distributed collective operation method under a distributed peer-to-peer network without a central control point. Through a complex verification mechanism, the blockchain database can maintain integrity, continuity and consistency. Even if some participants falsify, they cannot change the integrity of the blockchain, nor can they tamper with the data in the blockchain. A typical application of blockchain technology is the Bitcoin system. Bitcoin does not have a centralized management center, each node can freely choose to join or leave. All transaction data is opened to all nodes, and each node has the power to verify transactions and generate blocks. Bitcoin uses a proof-of-work mechanism (POW) to achieve consensus among users in the network. In the Bitcoin network, users are divided into three roles, namely miner node, wallet node, and forwarding node. The functions of the three roles will be given in
Section 3.
With the development of the consumer Internet, TCP/IP networks have gradually exposed their shortcomings in various aspects: reliability, security, and mobility cannot meet the development needs of the network. In 2010, the National Science Foundation proposed the Named Data Networking, a novel networking architecture [
5]. The NDN regards content as the dominant entity in the network and adopts a content-based transmission architecture. There are two types of roles in the NDN, consumers and producers. There are two types of packages in the network, namely interest package and data package. The content is identified by the name [
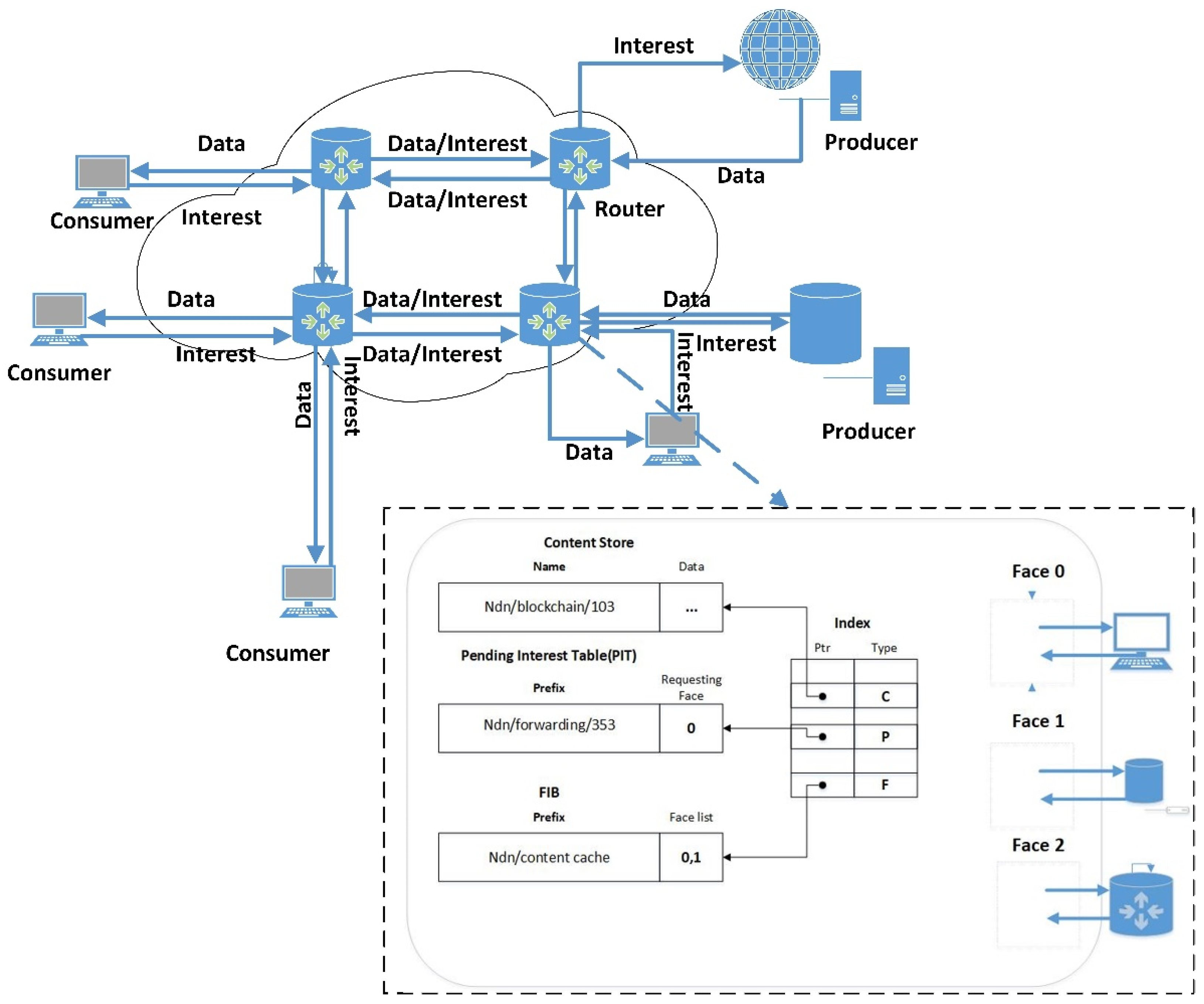
14]. If a consumer wants to request certain content, an interest packet with the corresponding name is generated, and it is forwarded through the network to the node where the content is stored. After receiving the interest packet, the node will send the corresponding Data package along the transmission path of the interest packet. Therefore, the NDN uses a receiver-driven and pull mechanism. Different from traditional IP networks, NDN nodes or routers support caching, and each node maintains three modules, which are content storage (CS), pending interest table (PIT), and forwarding information base (FIB) [
15]. After receiving the Interest packet, the router first checks whether the corresponding content is cached in the CS, if there is, it will reply directly to the data packet, if not, it will find the PIT, if the PIT has a corresponding entry, it will only record the interface that received the Interest packet without forwarding it If not, forward it according to FIB and forwarding strategy, and add corresponding PIT entry, or discard Interest packet according to relevant information. After receiving the Data packet, the router forwards it according to the information in the corresponding entry in the PIT [
16]. Since the content request has been satisfied, the router will delete the corresponding entry in the PIT after forwarding, and determine the content stored in the CS based on the caching strategy and related replacement mechanisms. Obviously, the name occupies a core position in the NDN forwarding process. There are usually two naming methods, hierarchical and flattened, and forwarding is based on the longest name prefix matching. According to the forwarding model of NDN, we can see that NDN supports multicast delivery and content distribution. The forwarding model of NDN is shown in
Figure 1.
There are several advantages to choose the NDN network to support blockchain-based applications. Firstly, the NDN network is a distributed network with the key of supporting content distribution naturally, and the blockchain-based applications will also generate a large amount of data distribution and has a distributed structure Secondly, the NDN network has a content caching mechanism, and each node could distribute the information through CS to reduce overhead. Finally, the state of the NDN network node is also updated at all times. This feature coincides with the content of the network node required by the blockchain network, and could reduce the redundant data synchronization overhead, which accelerates the speed of information synchronization between blocks.
However, there are some differences between the NDN and the blockchain network. The core communication mechanism of NDN belongs to the pull type, which means the consumers send interest packets to the network proactively, and then the producers send back the data packets to the consumers. While in the blockchain network, the miners actively push information to other nodes in the network. In response to this problem, we refer to our previous research. Liu Jiang [
3] introduced the concept of PPIT, and improved the transmission architecture of the NDN network, so that we can deploy the blockchain-based applications on the NDN network.
3. System Model
In this section, we present the system model used in this article. Firstly, we assume the NDN network used in this article is a fully random network. In this network, we assume that there are N nodes, indexed by N = {1, 2, …, n}. These nodes may be servers, gateways, or mobile terminals. Since the hardware configuration of each node is different, we assume that each node has different transmission capabilities. In the same network environment, we believe that there is a positive correlation between node’s transmitting capacity and communication efficiency, we use T(i) to represent the transmission capacity of node i.
In a fully random network, there may be multiple paths between nodes i and j, and the priority of data transmission on different paths is also different. Assuming that data packets sent from node i to node j are always transmitted via node k, we think that the communication weight of the data link between node i and node k is higher, we use W(i,j) to represent the communication weight of the data link between node i and node j.
Secondly, we assume that the blockchain system used in this article is the Bitcoin system. Well known, there are three different nodes in the Bitcoin system, namely miner nodes, wallet nodes and forwarding nodes. Miner nodes are responsible for calculating the transaction results and broadcasting to the whole network, wallet nodes are responsible for generating transactions and sending information to the miners, forwarding nodes are responsible for the distribution of data in the network.
In a bitcoin network, there are three steps in a transaction from start to finish:
(1) The wallet node generates a transaction and sends the transaction information to the miner node in the network.
(2) After receiving the information, the miner node calculates the hash value corresponding to the transaction information, and the miner node that first calculates the result broadcasts the result to the whole network.
(3) All nodes receive information and change local records.
Since the time difference between the information received by each miner node and the information sent by the wallet node is much smaller than the time required for the miner node to calculate the corresponding hash value, we can consider that each node receives the information of the wallet node at the same time and starts the calculation at the same time. Therefore, when comparing network delays, we can think of the delay in completing the entire transaction as the delay announced by the miner to the entire network.
4. Findings: The Accelerating Strategy
4.1. Secondary Nodes
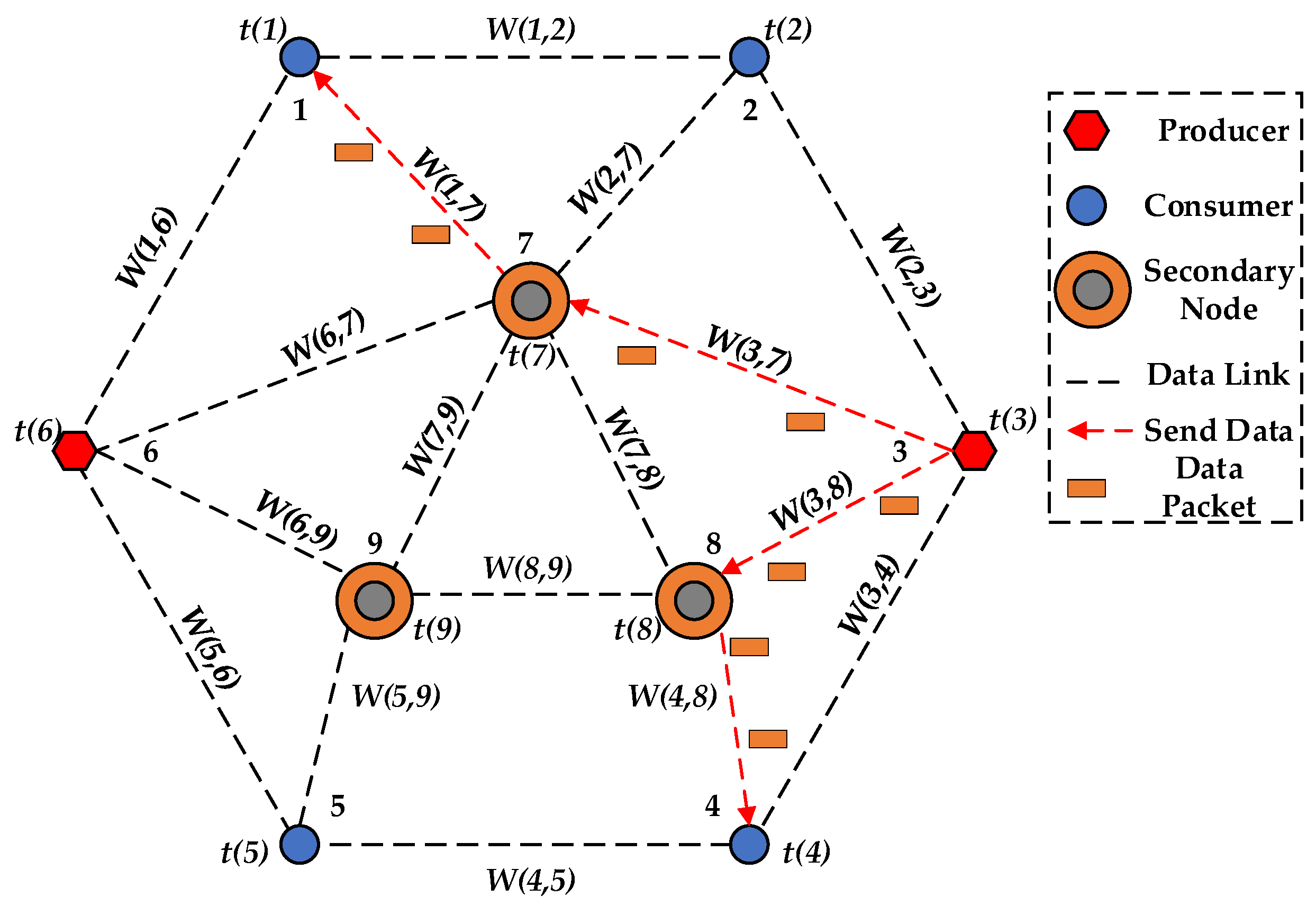
Before discussing the information acceleration transmission strategy proposed in this paper, we need to introduce the concept of the secondary node. In a random NDN network, we select some nodes to become the secondary nodes, and assign them higher bandwidth and larger cache to speed up the packet transmission in the network. These nodes usually have higher transmission capacity and communication weight, are connected to more nodes, and undertake more frequent data packet forwarding tasks, as shown in
Figure 2 (
Figure 2 does not represent the real topology network). Therefore, the secondary nodes are the routers with higher bandwidth and larger cache for storing the updating data of the producers first and pushing these data to all the receivers attending to the blockchain-based application, which is different from ordinary routers of the NDN.
4.2. The Selection Algorithm of the Secondary Nodes
Deploying the blockchain-based applications on NDN accelerates the information transmission of these applications. However, in order to further enhance the accelerating effect, we propose an information acceleration transmission strategy based on the graph theory and probability theory. In the blockchain network, the message distribution service overhead occupies a large proportion of the entire network overhead. If we select a node as secondary node, the data flowing through the node will be stored by it, and it can be sent repeatedly. When the data is sent directly by the secondary node instead of the starting point, the data transmission overhead is greatly reduced and the information transmission is accelerated.
In terms of how to choose secondary nodes to achieve more efficient information acceleration, we use the knowledge of graph theory and matrix theory to make decisions. Firstly, we use
G(
N,
T,
W) to uniquely represent an NDN network topology,
N is the node set,
T is a 1 ×
N matrix, and
T(
i) represents the transmission capacity of node
i.
W is an
N ×
N matrix,
W(
i,
j) represents the communication weight of the communication link between node
i and node
j, and
W(
i,
j) =
W(
j,
i). If
W(
i,
j) = 0, it means that there is no data link between
i and
j. Secondly, we introduce the concept of the node degree. As shown in the Equation (1) below:
where
is the path of the
sth node passing through node
i, and
R is the sum of the all paths existing in the network.
is the degree of node
i. Generally speaking, the more paths through node
i, the higher the degree of node, and the higher the importance of the node in the network. However, because the transmission capacity of each node and the communication weight between nodes are different, it is inaccurate to judge the importance of a node simply based on the number of paths connected to the node. Therefore, this paper proposes a new equation for calculating the importance of nodes.
Since the importance of a node is determined by the degree of the node, the transmission capacity of the node, and the communication weight of the node-related data link, the calculation method of the importance of the node is given by Equation (2):
where
represents the degree of node
j,
represents the transmission capacity of the node
j,
is a 1 ∗
N matrix, and
,
, and
are the weights of the three parameters respectively.
is given by Equation (3):
According to the above equation, we can calculate the importance of each node and sort it, and select the most important node as the secondary node. However, there is not only one secondary node in the network, so we need to propose how to select an appropriate number of nodes as secondary nodes. We assume that the probability of each node connecting to another node is
P (
P is given according to the network situation which will be discussed in
Section 5), and then the probability of each node connecting to
j nodes is shown in Equation (4):
According to the previous definition, we can determine that
and
are continuous values within a certain range, and because they both have physical meaning, the values of
and
will neither be very high nor very low, most will be concentrated in the common value range. Thus, we assume that the transmission capacity of the node and the communication weight of the data link follow the normal distribution. Thus, Equation (5) is given as:
where
,
,
represents the constants of the normal distribution.
Since
and
follow a normal distribution, we have Equation (6):
where
represents the constants of the normal distribution.
Then, because the (
follow the normal distribution, so its value can be within a certain range. When considering the number of secondary nodes, the influence of
and
can be ignored, and only the number of paths connected by the nodes will be considered. We set
as the probability of the node connecting more than or equal to
j nodes, so obviously there is Equation (6):
After giving a specific P, the corresponding can be calculated according to P, and an appropriate number of nodes are selected as the secondary nodes according to the value of , which are configured high bandwidth and large caches to accelerate the data transmission.
4.3. Information Acceleration Transmission Strategy
In this section, we will introduce the information acceleration strategy in detail. The core of the information accelerated transmission strategy is to calculate the importance of each node, select an appropriate number of nodes as secondary nodes according to the network situation, and give a larger bandwidth and a higher cache to help the network distribute data and reduce redundancy. Equations (2)–(7) give the calculation method of the above parameters. The specific flowchart is shown in
Figure 3. The detailed process is as follows:
Generate a topology according to the real network data. After the topology is successfully generated, the FIB table of each node is generated according to the best route routing strategy, and then run the blockchain system on each node;
Traverse the entire network according to the FIB table, and record the data interaction path between any node i and node j.
According to the traversal result, delete nodes and data links which do not interact with any other nodes in the network, and established a new topology network.
Calculate the importance of each node according to the new network topology. The calculation equation refers to Equation (2) and Equation (3).
After calculating the degree of each node, obtain a p according to the network state, and substitute the p value and the degree of each node into Equations (2) and (3) to calculate the value of importance for each node. Substitute the p value into Equations (4) and (7) to calculate the value of .
According to the , an appropriate number of nodes are selected as secondary nodes to assist the blockchain network to accelerate information transmission.
Based on the execution process and operation logic of the information acceleration strategy, we present the execution pseudocode of the strategy, which is used to simulate the information acceleration strategy on the physical device. The specific pseudocode is shown in Algorithms 1.
| Algorithms 1. Pseudocode of the specific transmission strategy. |
| INPUT: network topology information |
| OUTPUT: secondary nodes |
| 1: function Information acceleration transmission strategy |
| 2: Generate FIB table according to the BestRoute policy |
| 3: Traversing the topology path according to the FIB table |
| 4: For path r |
| 5: If (Path r is an unrelated path) |
| 6: Delete path r |
| 7: end |
| 8: Generate the new topology network |
| 9: Calculate the importance of every node in the new topology network according to Equation (2) and Equation (3) |
| 10: Set the value of P |
| 11: Calculate the and according to Equation (4) and Equation (7) |
| 12: Select the appropriate number of nodes as secondary nodes based on the value of |
| 13: Set these nodes as the secondary nodes |
5. Simulation Results and Discussions
Here we use ndnSIM as our simulation tool, which is a NS3 based NDN simulator. In order to better verify the performance of the proposed acceleration strategy, we propose three simulation scenarios and compare them:
(1) Use NDN network and deploy acceleration strategy, record network latency and data overhead in a period of time.
(2) Use NDN network but do not deploy acceleration strategy, record network latency and data overhead in a period of time.
(3) Use TCP/IP network and do not deploy acceleration strategy, record network latency and data overhead in a period of time.
We constructed a network topology to simulate and observe the performance of the acceleration strategy. In the process of building the topology, we refer to the real network topology provided by ndnSIM and the topology data in some references [
17]. In a real network, the value of
P is always between 0.1 and 0.2 (as the network scale expands, the value of
P is different), so we set
P to 0.15 and calculate
as 0.15. Therefore, in the simulation network discussed below, we will calculate the importance of each node according to Equations (2) and (3), and select the top 15% of the nodes as secondary nodes. The secondary nodes will be set to have twice the bandwidth of normal nodes and 100G of cache space.
5.1. NDN Network and TCP/IP Network without Acceleration Strategy
In this section, we deploy the Bitcoin system in the NDN network and the TCP/IP network, and the two solutions use the same blockchain network topology. In this topology, there are 150 nodes, 20 of which are miner nodes, and 15 of which are wallet nodes, the remaining nodes are forwarding nodes. These nodes are connected to each other with probability P and perform data interaction.
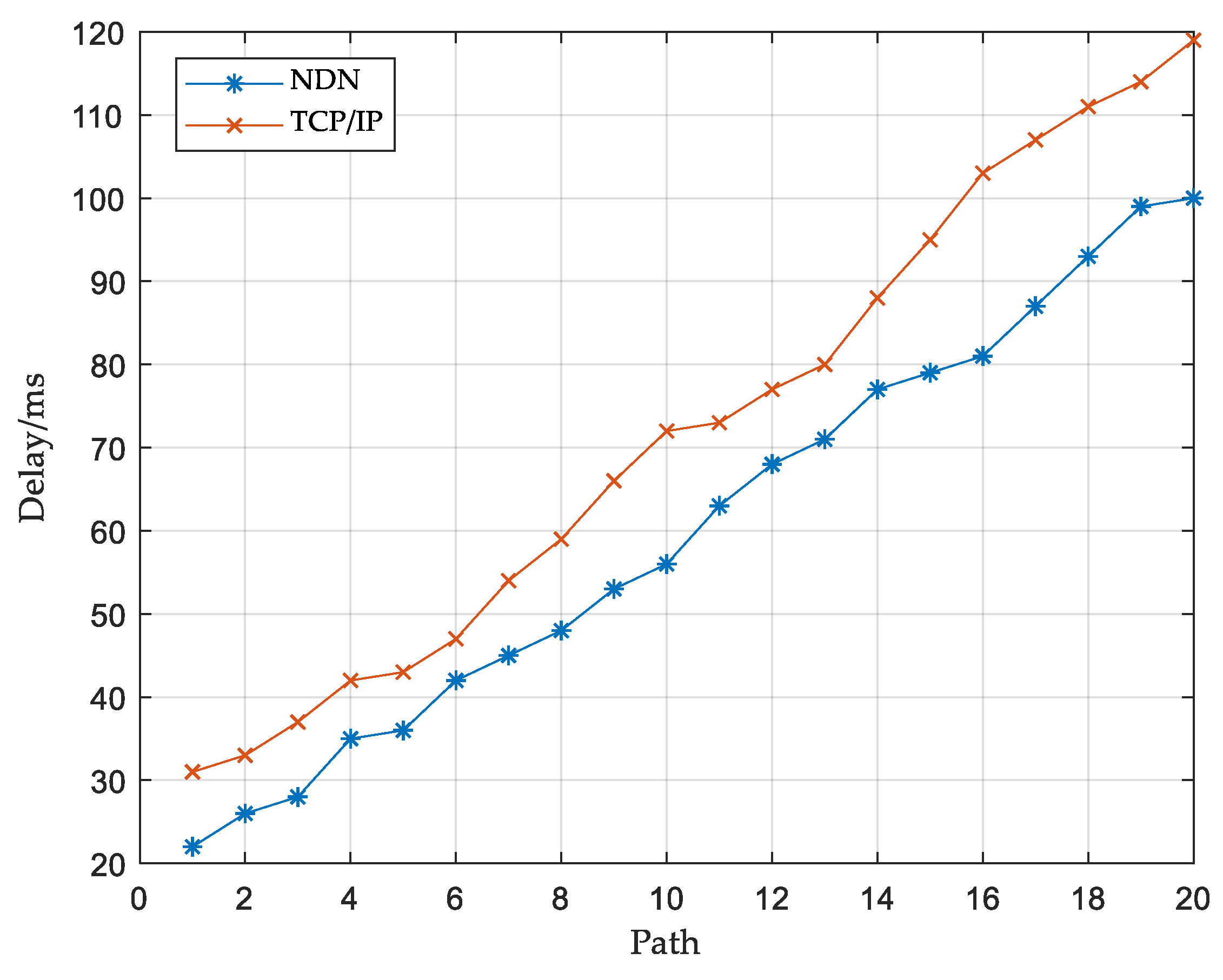
As shown in
Figure 4, we compared the transmission delay of the Bitcoin system in the NDN network and the traditional TCP/IP network. The delay/ms represents the transmission delay when a block is broadcast to a miner node. The path represents the number of miners passed by the block. It can be seen that under the same network conditions, the NDN network has better performance than the traditional TCP/IP network, which confirms the view that the NDN network is more suitable for the blockchain network. However, simply deploying the blockchain on the NDN network will not bring a more significant performance improvement, so we need to further optimize the NDN network, which will be given in the next section.
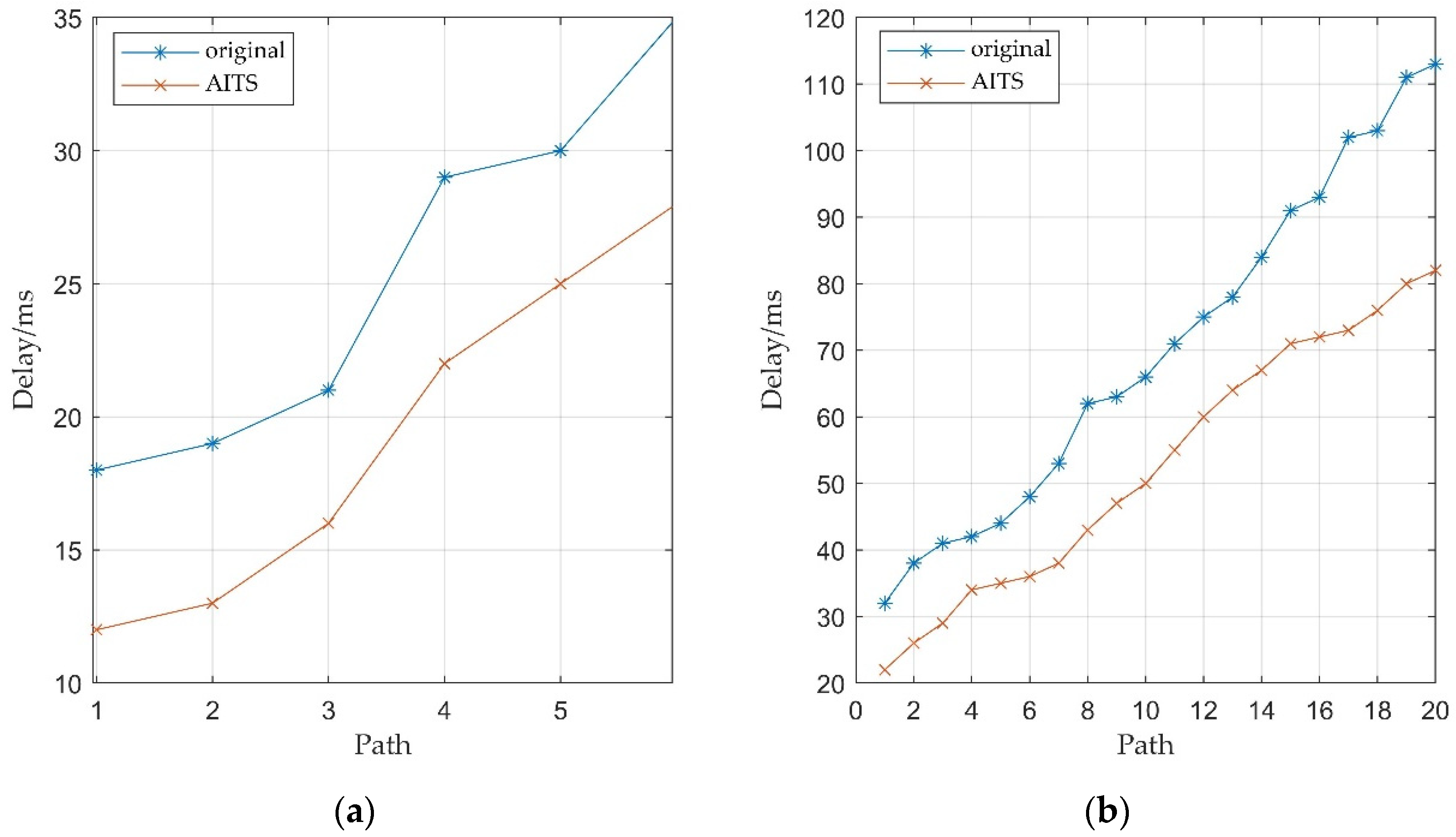
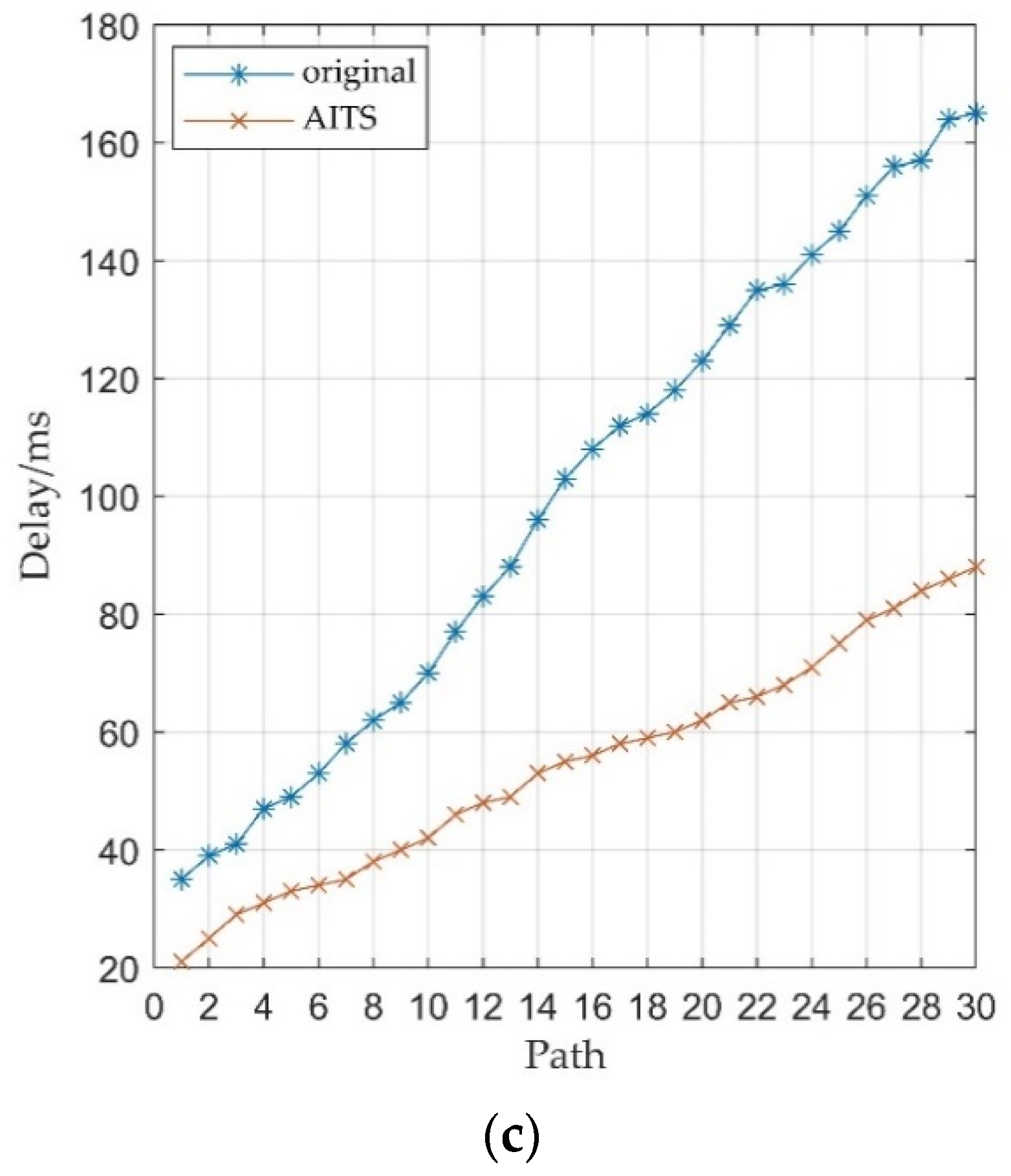
5.2. NDN Network with Acceleration Strategy
In this section, we will introduce an acceleration strategy to optimize the NDN net-work, and compare the performance of the Bitcoin system before and after the acceleration strategy is introduced. The network topology used in this section is the same as the previous one. In the previous simulation, we set
P = 0.15 based on the real network data, and calculated the number of secondary nodes based on the
P value. However, there are peaks and underestimations of traffic in the network, the value of
P will also change and affect the number of secondary nodes. Because changes in the number of secondary nodes can affect the performance of the AITS strategy, we selected a set of
P values for simulation experiments and compared them with the original network, the value of these
P has a 5% fluctuation relative to the real network value, as shown in
Figure 5. The original algorithm in
Figure 5,
Figure 6 and
Figure 7 represents that the blockchain uses the NDN network for information transmission, but no additional information acceleration strategy is applied. It can be seen that in complex networks, as the transmission path in the network becomes longer, the node receiving delay increases significantly, but the use of the AITS strategy (accelerated information transmission strategy) can significantly reduce this delay. The simulation results show that compared with the original algorithm, the AITS strategy can significantly reduce the transmission delay, and the reduction is determined by the number of secondary nodes, the higher the
P value, the higher the number of secondary nodes in the network, and the better the performance of the AITS strategy.
Whether it has good scalability is also an important factor in evaluating the information acceleration strategy proposed in this paper. In order to prove the scalability of the AITS strategy, we designed a set of simulation experiments. We created three sets of simulation networks, the first group has 20 nodes, of which six are miner nodes; the second group has 150 nodes, of which 20 are miner nodes; the third group has 250 nodes, of which 30 are Miner nodes. These three sets of simulation networks are all established in the same way and have the same external parameters: all nodes in the network are connected with each other with probability
P, and interact with each other according to their roles. In each network, the number of secondary nodes is 15% of the number of network nodes. The simulation results are shown in
Figure 6. It can be seen that the AITS strategy has good performance no matter whether the network is simple or complex, and as the network scale becomes larger, AITS performs better in a complex network environment. The simulation results further prove the superiority of the AITS strategy proposed in this paper in complex environments.
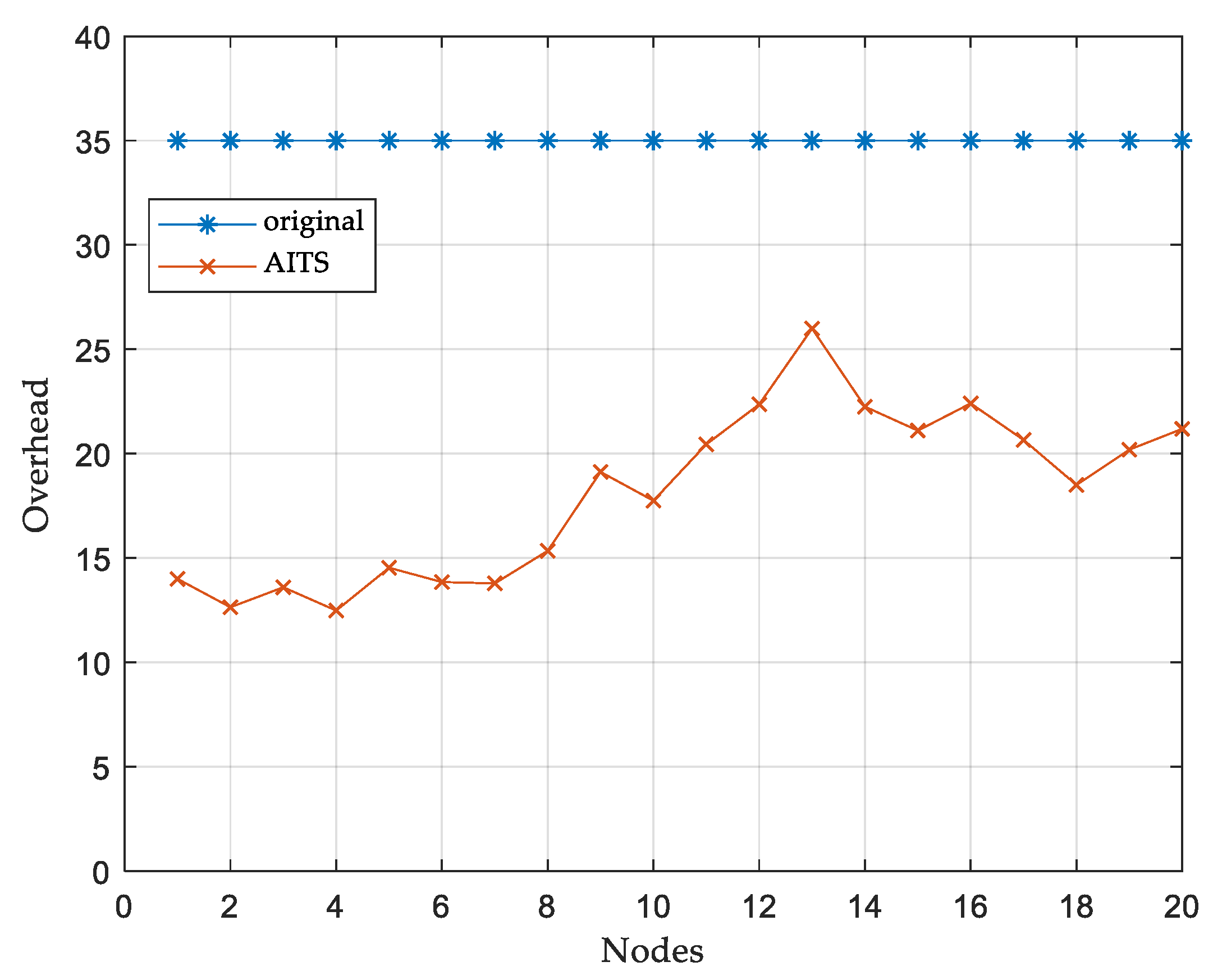
Another advantage of the AITS strategy is reducing the data overhead, which means reducing the redundant transmission of the data. Since the secondary node stores the data packets sent by the miner node, it distributes directly from the secondary node to the destination when it needs to distribute to another node on the path, which reduces a large amount of data overhead. We select 20 miner nodes to observe the packet overhead sent when it broadcasts information to the entire network. As shown in
Figure 7, after the introduction of the AITS strategy, the data overhead of all miner nodes has been significantly reduced, the reduction depends on the distance between the miner node and the secondary node. The closer to the secondary node, the fewer data packets are repeatedly requested, and the data overhead is reduced. The simulation results proved this. The simulation results proved the excellent performance of AITS in reducing data overhead in complex network conditions.
6. Conclusions
Due to the architectural characteristics of the blockchain, when running blockchain programs on the traditional network, it will generate great broadcast overhead and transmission delay, which has a great impact on the subsequent development of the blockchain-based applications. In this paper, we mainly focused on deploying the blockchain-based applications on NDN and realizing the acceleration of information transmission. In order to speed up the information transmission speed of the blockchain system and reduce data overhead, we have selected some more important nodes in the network as secondary nodes, giving them more bandwidth and cache to speed up the transmission of information. We present a method to calculate the number of secondary nodes, and give the function to calculate the importance of each node, these methods are used to select appropriate nodes as secondary nodes in the network. We designed multiple simulation schemes to verify the performance of the AITS strategy under the NDN network. The simulation results show that in complex networks, our AITS method has superior performance in accelerating information transmission and reducing data overhead. In addition, the more secondary nodes in the network, the better the performance of the AITS strategy.
In the future, we focus on the information acceleration transmission strategies in more complex blockchain scenarios, such as data transmission services between multiple blockchains.