Intrusion Detection for in-Vehicle Communication Networks: An Unsupervised Kohonen SOM Approach
Abstract
1. Introduction
- An anomaly-based IDS implemented using unsupervised learning to identify intrusions on an in-vehicle communication network, in particular, a CAN bus. At the state of the art level, this is the first work which tests an unsupervised Kohonen SOM network as an anomaly detector in the automotive domain.
- A novel distance-based procedure to integrate Kohonen SOM network and k-means algorithm, which greatly improves accuracy in detecting attack messages compared to the traditional procedure. Moreover, the proposed method significantly reduces false negative rate, which assumes a great importance in attack detection for in-vehicle CAN buses. Its value should be very low to ensure the safety of the vehicle.
- The proposed method was tested on real car-hacking data, including DoS, spoofing the drive gear, spoofing the RPM gauge, and fuzzy attacks. Data were obtained by logging CAN traffic via the OBD-II port from a real vehicle while message injection attacks were being performed. The performance of the proposed method was shown via computing evaluation metrics.
- The proposed method was performed with remarkable results both using single datasets only containing one type of attack and also merging all types of attack into a unique dataset.
- Most of the studies in the literature propose IDSs only able to detect periodic attacks but not aperiodic violations. The proposed method reveals remarkable performance in detecting both periodic and aperiodic intrusions.
2. Related Works
3. Control Area Network (CAN)
4. Theoretical Background
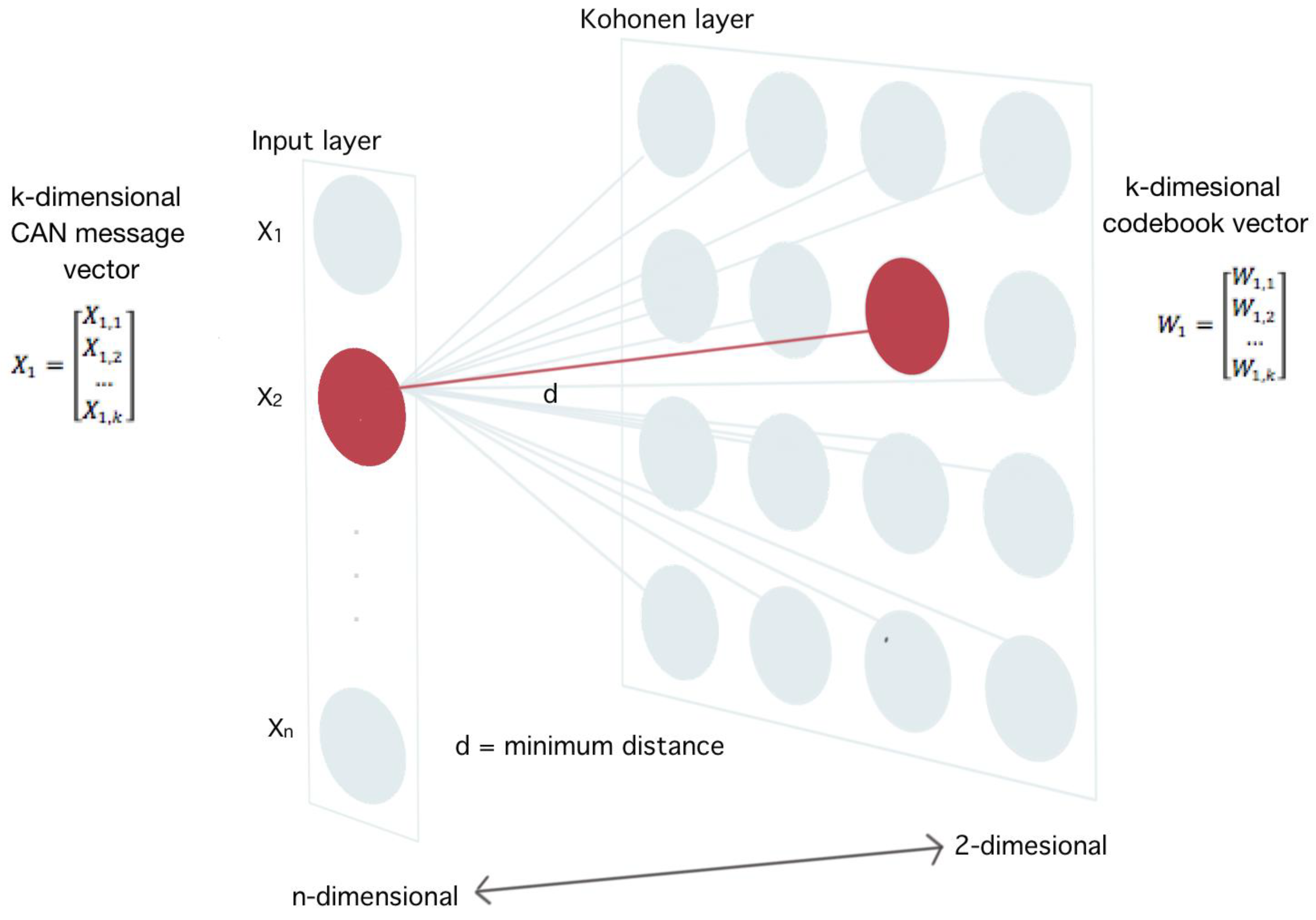
4.1. Unsupervised SOM Neural Network
| Algorithm 1: Kohonen SOM algorithm. |
 |
4.2. K-Means Clustering Algorithm
| Algorithm 2: K-means algorithm. |
 |
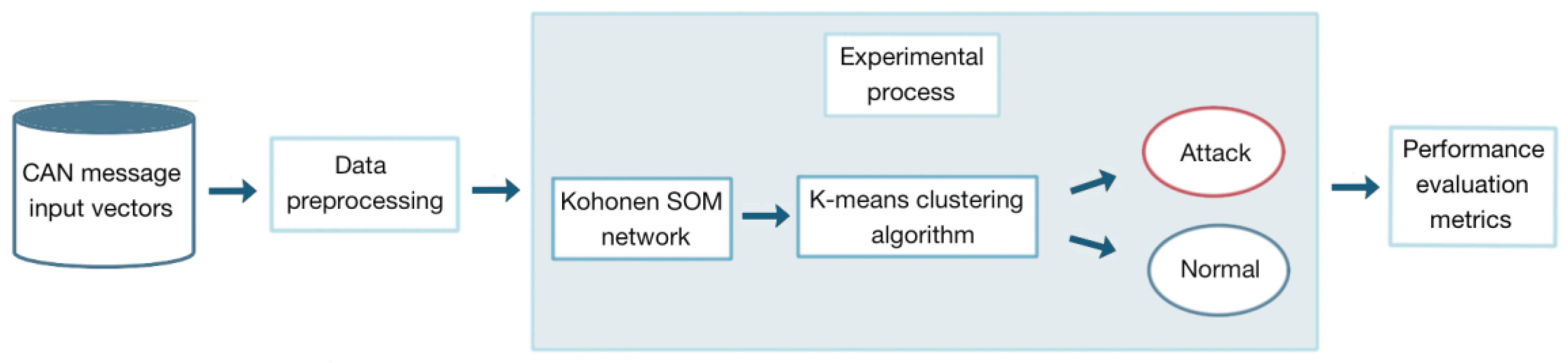
5. Materials and Methods
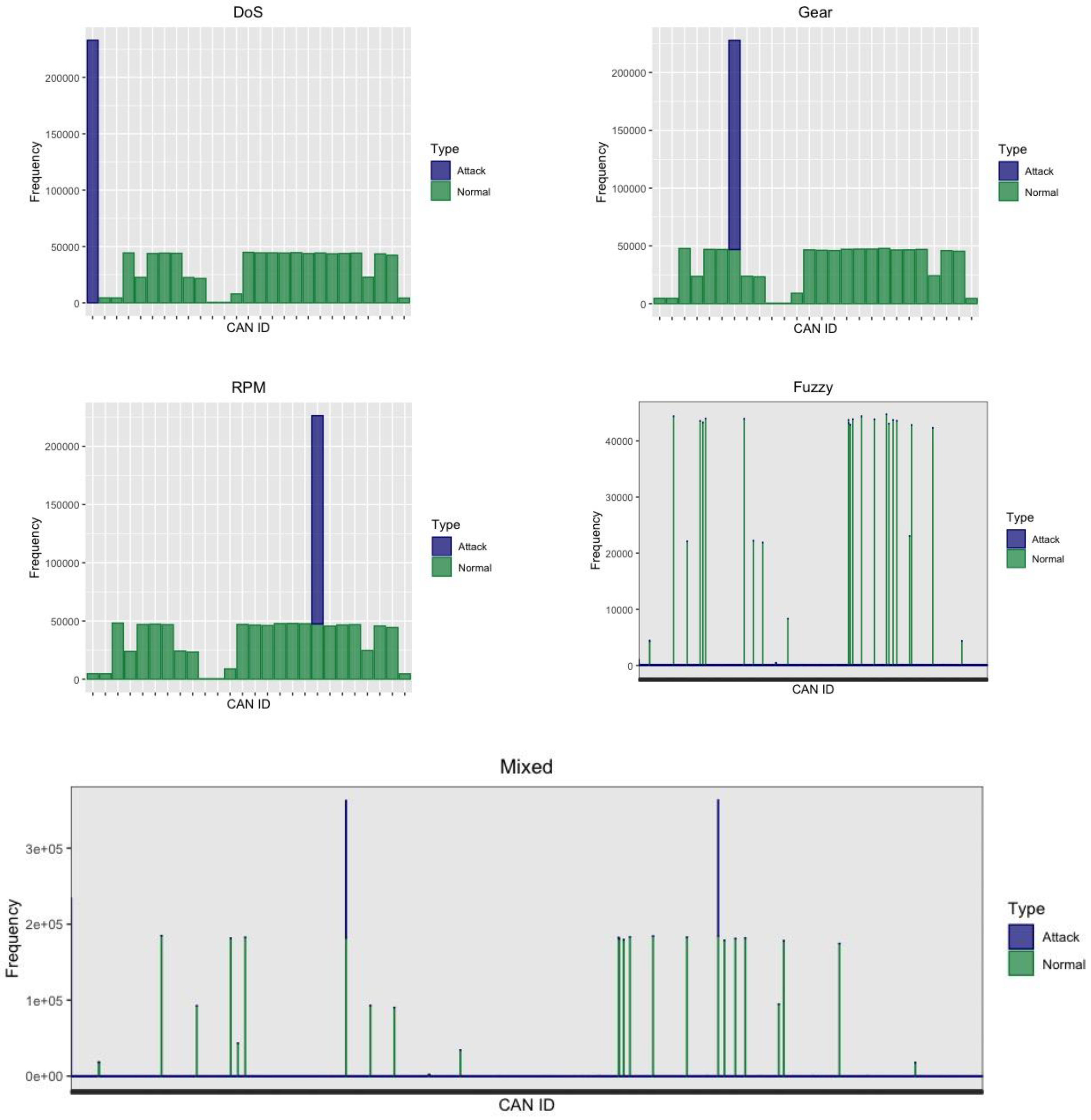
- Data pre-processing: Data were pre-processed in order to be given input to the network. We analyzed open source car hacking data including different kinds of attack messages. In particular, we considered four different datasets containing DoS attacks, spoofing the drive gear, spoofing the RPM gauge, and fuzzy attacks. Data are available at [53].
- Experimental process: We tested the proposed method based on a novel procedure to integrate the Kohonen SOM network with a k-means algorithm in order to improve the performance of the model in terms of accuracy in detection of attack messages and reduction of false negative rate. We also compared the proposed method with the traditional procedure. Both methods were tested, first, on each attack dataset separately, and then on the mixed dataset.
- Evaluation of the performances of the models.
5.1. Dataset Pre-Processing
5.2. System Architecture
- Input CAN message data vectors were weighted depending on their frequency in the whole traffic dataset, since the nature of attack and normal messages sent in the CAN bus differs in terms of structure and frequency.
- Distances between weighted input CAN vectors and neurons in the Rx map were computed training the Kohonen SOM network.
- Distances were used as input of the k-means algorithm.
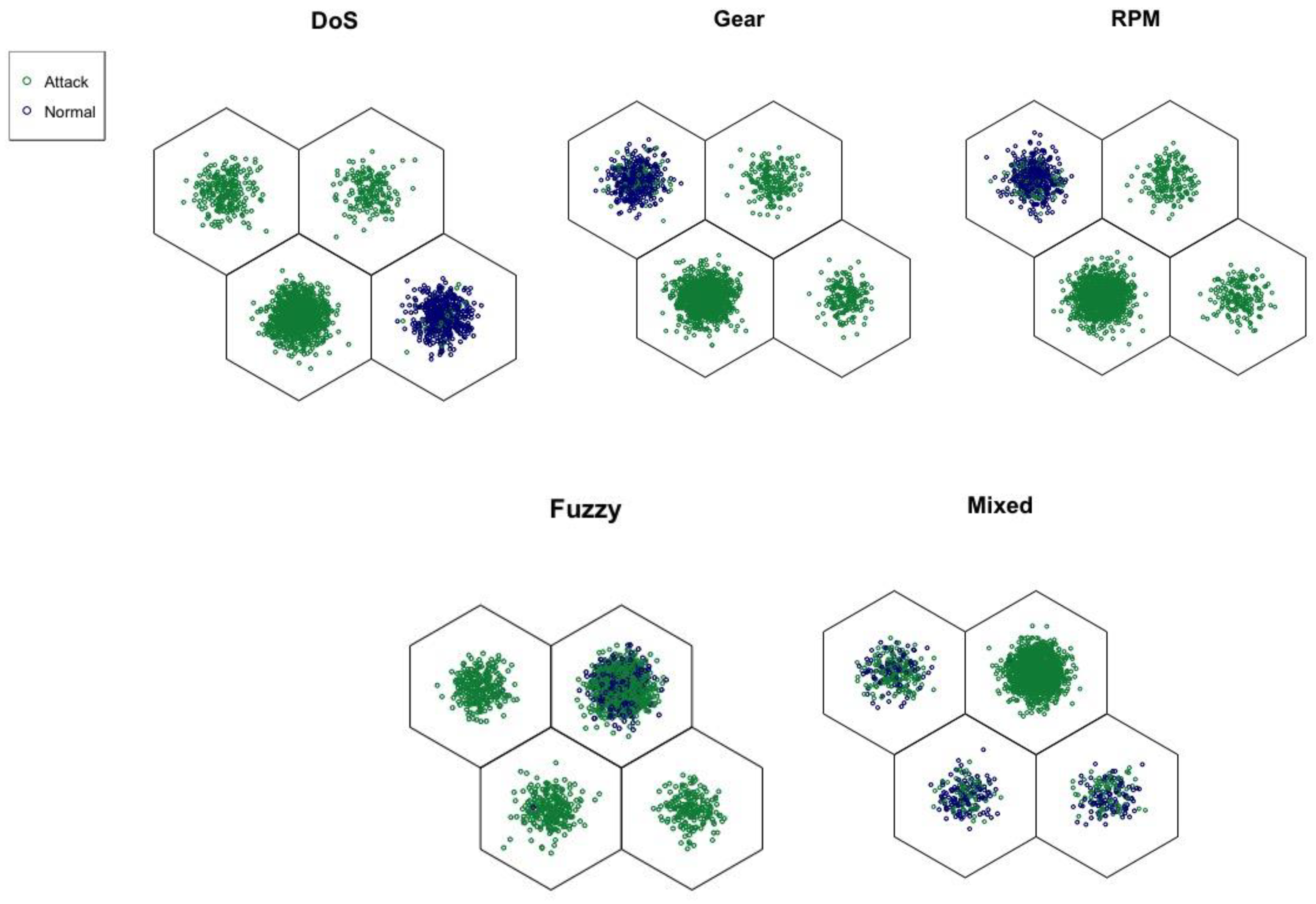
- The k-means algorithm was implemented to classify input vectors in two clusters based on their distance to the corresponding winning neurons’ BMU.
| Algorithm 3: SOMK-D algorithm. |
 |
| Algorithm 4: SOMK-D algorithm. |
 |
5.3. Performance Evaluation Metrics
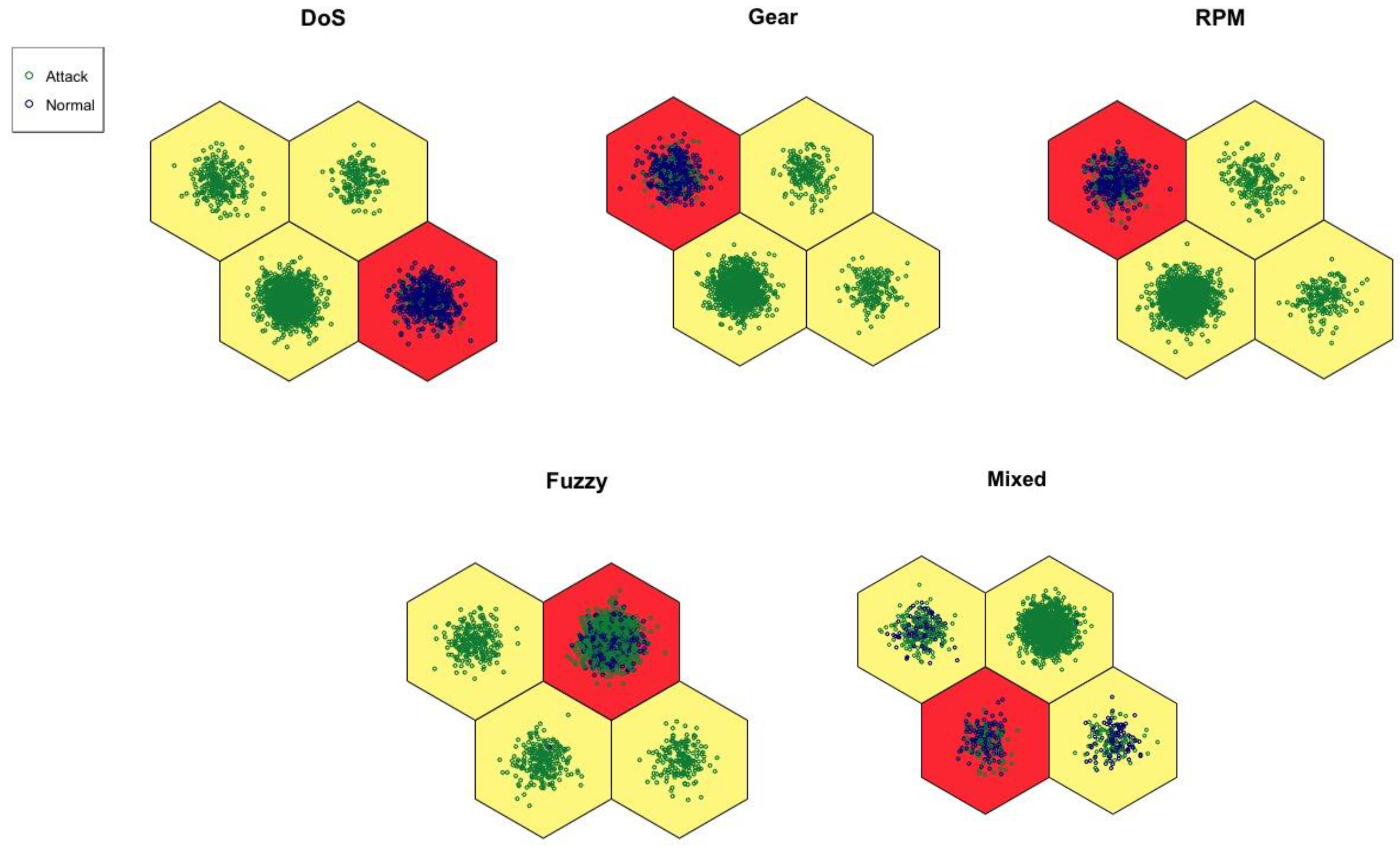
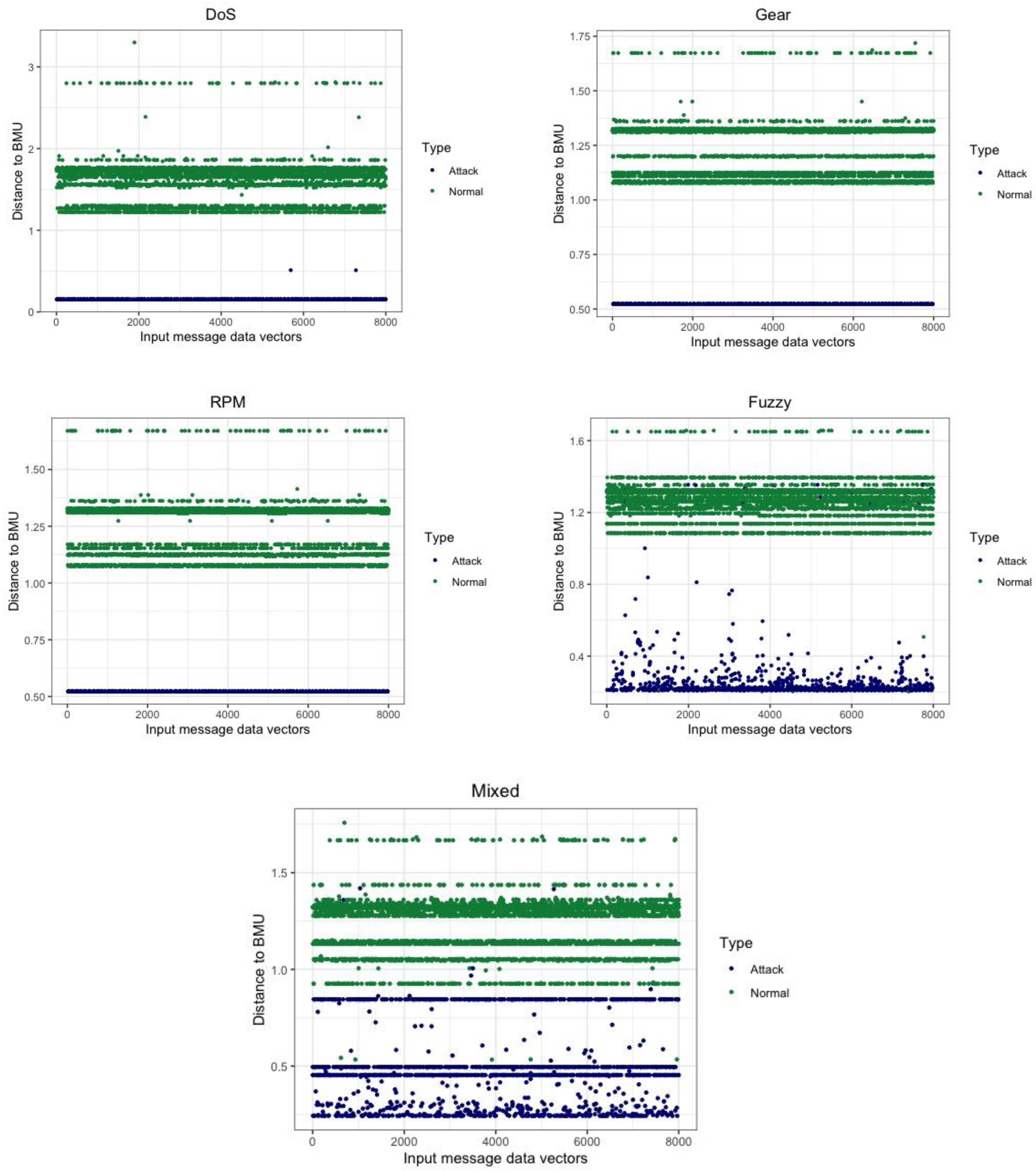
6. Results and Discussion
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Vasudev, H.; Das, D.; Vasilakos, A.V. Secure message propagation protocols for IoVs communication components. Comput. Electr. Eng. 2020, 82, 106555. [Google Scholar] [CrossRef]
- Du, R.; Santi, P.; Xiao, M.; Vasilakos, A.V.; Fischione, C. The Sensable City: A Survey on the Deployment and Management for Smart City Monitoring. IEEE Commun. Surv. Tutorials 2019, 21, 1533–1560. [Google Scholar] [CrossRef]
- Barletta, V.; Caivano, D.; DiMauro, G.; Nannavecchia, A.; Scalera, M. Managing a Smart City Integrated Model through Smart Program Management. Appl. Sci. 2020, 10, 714. [Google Scholar] [CrossRef]
- Baldassarre, M.T.; Barletta, V.S.; Caivano, D. Smart Program Management in a Smart City. In Proceedings of the 2018 AEIT International Annual Conference; Institute of Electrical and Electronics Engineers (IEEE), Bari, Italy, 3–5 October 2018; pp. 1–6. [Google Scholar]
- Zhou, J.; Dong, X.; Cao, Z.; Vasilakos, A.V. Secure and Privacy Preserving Protocol for Cloud-Based Vehicular DTNs. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1299–1314. [Google Scholar] [CrossRef]
- Baldassarre, M.T.; Barletta, V.; Caivano, D.; Scalera, M. Integrating security and privacy in software development. Softw. Qual. J. 2020, 1–32. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A.V. Security and Privacy for Cloud-Based IoT: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Challa, S.; Das, A.K.; Gope, P.; Kumar, N.; Wu, F.; Vasilakos, A.V. Design and analysis of authenticated key agreement scheme in cloud-assisted cyber–physical systems. Futur. Gener. Comput. Syst. 2020, 108, 1267–1286. [Google Scholar] [CrossRef]
- Sommer, F.; Duerrwang, J.; Kriesten, R. Survey and Classification of Automotive Security Attacks. Information 2019, 10, 148. [Google Scholar] [CrossRef]
- Caivano, D. Continuous Software Process Improvement through Statistical Process Control. In Proceedings of the Ninth European Conference on Software Maintenance and Reengineering; Institute of Electrical and Electronics Engineers (IEEE), Manchester, UK, 21–23 March 2005; pp. 288–293. [Google Scholar]
- Baldassarre, M.T.; Boffoli, N.; Caivano, D.; Visaggio, G. Managing Software Process Improvement (SPI) through Statistical Process Control (SPC). Intell. Tutor. Syst. 2004, 3009, 30–46. [Google Scholar]
- Baldassarre, M.T.; Barletta, V.S.; Caivano, D.; Raguseo, D.; Scalera, M. Teaching cyber security: The hack-space integrated model, CEUR Workshop Proceedings. In ITASEC; University of BariAldo Moro: Bari, Italy, 2019; Volume 2315. [Google Scholar]
- Lokman, S.F.; Othman, A.T.; Abu-Bakar, M.-H. Intrusion detection system for automotive Controller Area Network (CAN) bus system: A review. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 184. [Google Scholar] [CrossRef]
- Carsten, P.; Andel, T.R.; Yampolskiy, M.; McDonald, J.T. In-Vehicle Networks. In Proceedings of the 10th Annual Cyber and Information Security Research Conference on - CISR ’15; Association for Computing Machinery (ACM), London, UK, 6–8 April 2015; pp. 1–8. [Google Scholar]
- Gmiden, M.; Gmiden, M.H.; Trabelsi, H. An intrusion detection method for securing in-vehicle CAN bus. In Proceedings of the 2016 17th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA); Institute of Electrical and Electronics Engineers (IEEE), Sousse, Tunisia, 19–21 December 2016; pp. 176–180. [Google Scholar]
- Young, C.; Zambreno, J.; Olufowobi, H.; Bloom, G. Survey of Automotive Controller Area Network Intrusion Detection Systems. IEEE Des. Test 2019, 36, 48–55. [Google Scholar] [CrossRef]
- Qu, X.; Yang, L.; Guo, K.; Ma, L.; Sun, M.; Ke, M.; Li, M. A Survey on the Development of Self-Organizing Maps for Unsupervised Intrusion Detection. Mob. Netw. Appl. 2019, 1–22. [Google Scholar] [CrossRef]
- Yao, X.Q.; Tang, G.; Hu, X. Method for recognizing mechanical status of container crane motor based on SOM neural network. In IOP Conference Series: Materials Science and Engineering; IOP: London, UK, 2018; Volume 435, p. 12009. [Google Scholar]
- Wu, Y.; Yan, P.F. A study on structural adapting self-organizing neural network. Acta Electron. Sin. 1999, 27, 56–59. [Google Scholar]
- Wan, Q.; Wang, C.; Feng, Z.Y.; Ye, J.F. Review of K-means clustering algorithm. Electron. Des. Eng. 2012, 20, 21–24. [Google Scholar]
- Feyereisl, J.; Aickelin, U. Self-Organising Maps in Computer Security. arXiv Preprint 2016, arXiv:1608.01668. [Google Scholar]
- Ling, T.; Chong, L.; Jingming, X.; Jun, C. Application of Self-organizing Feature Map Neural Network Based on K-means Clustering in Network Intrusion Detection. Comput. Mater. Contin. 2019, 61, 275–288. [Google Scholar] [CrossRef]
- Huai-Bin, W.; Hong-Liang, Y.; Zhi-Jian, X.; Zheng, Y. A Clustering Algorithm Use SOM and K-Means in Intrusion Detection. In Proceedings of the 2010 International Conference on E-Business and E-Government; Institute of Electrical and Electronics Engineers (IEEE), Guangzhou, China, 7–9 May 2010; pp. 1281–1284. [Google Scholar]
- Dhanabal, L.; Shantharajah, S.P. A Study on NSL-KDD Dataset for Intrusion Detection System Based on Classification Algorithms. Int. J. Adv. Res. Comput. Commun. Eng. 2015, 4, 446–452. [Google Scholar] [CrossRef]
- De La Hoz, E.; De La Hoz, E.; Ortiz, A.; Ortega, J.; Martínez-Álvarez, A. Feature selection by multi-objective optimisation: Application to network anomaly detection by hierarchical self-organising maps. Knowl.-Based Syst. 2014, 71, 322–338. [Google Scholar] [CrossRef]
- Palomo, E.J.; Domínguez, E.; Luque, R.M.; Muñoz, J.; Luque-Baena, R.M. Network Security Using Growing Hierarchical Self-Organizing Maps. Intell. Tutor. Syst. 2009, 5495, 130–139. [Google Scholar]
- Ippoliti, D.; Zhou, X. A-GHSOM: An adaptive growing hierarchical self organizing map for network anomaly detection. J. Parallel Distrib. Comput. 2012, 72, 1576–1590. [Google Scholar] [CrossRef]
- Zhang, Y.; Bu, W.; Su, C.; Wang, L.; Xu, H. Intrusion detection method based on improved growing hierarchical self-organizing map. Trans. Tianjin Univ. 2016, 22, 334–338. [Google Scholar] [CrossRef]
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity challenges in vehicular communications. Veh. Commun. 2020, 23, 100214. [Google Scholar] [CrossRef]
- Liang, L.; Ye, H.; Li, G.Y. Toward Intelligent Vehicular Networks: A Machine Learning Framework. IEEE Internet Things J. 2019, 6, 124–135. [Google Scholar] [CrossRef]
- Ye, H.; Liang, L.; Li, G.Y.; Kim, J.; Lu, L.; Wu, M.; Li, Y. Machine Learning for Vehicular Networks: Recent Advances and Application Examples. IEEE Veh. Technol. Mag. 2018, 13, 94–101. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Baldassarre, M.T.; Barletta, V.; Caivano, D.; Scalera, M. Privacy Oriented Software Development; Springer Science and Business Media LLC: Berlin, Germany, 2019; pp. 18–32. [Google Scholar]
- Bezemskij, A.; Loukas, G.; Gan, D.; Anthony, R.J. Detecting Cyber-Physical Threats in an Autonomous Robotic Vehicle Using Bayesian Networks. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData); Institute of Electrical and Electronics Engineers (IEEE), Exeter, UK, 21–23 June 2017; pp. 98–103. [Google Scholar]
- Kang, M.-J.; Kang, J.-W. A Novel Intrusion Detection Method Using Deep Neural Network for In-Vehicle Network Security. In Proceedings of the 2016 IEEE 83rd Vehicular Technology Conference (VTC Spring); Institute of Electrical and Electronics Engineers (IEEE), Nanjing, China, 15–18 May 2016; pp. 1–5. [Google Scholar]
- Taylor, A.; Leblanc, S.P.; Japkowicz, N. Anomaly Detection in Automobile Control Network Data with Long Short-Term Memory Networks. In Proceedings of the 2016 IEEE International Conference on Data Science and Advanced Analytics (DSAA); Institute of Electrical and Electronics Engineers (IEEE), Montreal, QC, Canada, 17–19 October 2016; pp. 130–139. [Google Scholar]
- Kalash, M.; Rochan, M.; Mohammed, N.; Bruce, N.D.B.; Wang, Y.; Iqbal, F. Malware Classification with Deep Convolutional Neural Networks. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS); Institute of Electrical and Electronics Engineers (IEEE), Paris, France, 26–28 February 2018; pp. 1–5. [Google Scholar]
- Lin, Z.; Shi, Y.; Xue, Z. IDSGAN: Generative Adversarial Networks for Attack Generation against Intrusion Detection. arXiv 2018, arXiv:1809.02077. [Google Scholar]
- Torres, J.M.; Comesaña, C.I.; García-Nieto, P.J. Review: Machine learning techniques applied to cybersecurity. Int. J. Mach. Learn. Cybern. 2019, 10, 2823–2836. [Google Scholar] [CrossRef]
- Song, H.M.; Woo, J.; Kim, H.K. In-vehicle network intrusion detection using deep convolutional neural network. Veh. Commun. 2020, 21, 100198. [Google Scholar] [CrossRef]
- Olufowobi, H.; Young, C.; Zambreno, J.; Bloom, G. SAIDuCANT: Specification-Based Automotive Intrusion Detection Using Controller Area Network (CAN) Timing. IEEE Trans. Veh. Technol. 2020, 69, 1484–1494. [Google Scholar] [CrossRef]
- Cook, J.A.; Freudenberg, J.S. Controller Area Network (CAN). EECS461 2008, 1–8. [Google Scholar]
- Chen, S.-H.; Lin, C.-H.R. Evaluation of DoS Attacks on Vehicle CAN Bus System. In Proceedings of the Human Centred Intelligent Systems; Springer Science and Business Media LLC: Berlin, Germany, 2018; pp. 308–314. [Google Scholar]
- Barbieri, N. Fuel prices and the invention crowding out effect: Releasing the automotive industry from its dependence on fossil fuel. Technol. Forecast. Soc. Chang. 2016, 111, 222–234. [Google Scholar] [CrossRef]
- Ciaburro, G.; Venkateswaran, B. Neural Networks with R: Smart Models Using CNN, RNN, Deep Learning, and Artificial Intelligence Principles, Packt Publishing Ltd.: Birmingham, UK, 2017; ISBN 978-1-78839-787-2.
- Akinduko, A.A.; Mirkes, E.M. Initialization of Self-Organizing Maps: Principal Components Versus Random Initialization. A Case Study. arXiv preprint 2012, arXiv:1210.5873 . [Google Scholar]
- Shamsuddin, S.M.; Zainal, A.; Mohd Yusof, N. Multilevel Kohonen Network Learning For Clustering Problems. J. Inf. Commun. Technol. 2008, 7, 1–25. [Google Scholar]
- Wehrens, R.; Buydens, L.M. Self- and Super-organizing Maps in R: The kohonen Package. J. Stat. Softw. 2007, 21, 1–19. [Google Scholar] [CrossRef]
- Kohonen, T. Self-Organizing Map; Springer: Berlin/Heidelberg, Germany, 2001; Volume 30. [Google Scholar]
- Wehrens, R.; Kruisselbrink, J. Flexible Self-Organizing Maps in kohonen 3.0. J. Stat. Softw. 2018, 87, 1–18. [Google Scholar] [CrossRef]
- Vasighi, M.; Kompany-Zareh, M. Classification ability of self organizing maps in comparison with other classification methods. Commun. Math. Comput. Chem. 2013, 70, 29–44. [Google Scholar]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN based Intrusion Detection System for In-Vehicle Network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST); Institute of Electrical and Electronics Engineers (IEEE), Belfast, UK, 28–30 August 2018; pp. 1–6. [Google Scholar]
- Car-Hacking Dataset - Hacking and Countermeasure Research Lab. Available online: http://ocslab.hksecurity.net/Datasets/CAN-intrusion-dataset. (accessed on 27 November 2019).
- Zhou, A.; Li, Z.; Shen, Y. Anomaly Detection of CAN Bus Messages Using A Deep Neural Network for Autonomous Vehicles. Appl. Sci. 2019, 9, 3174. [Google Scholar] [CrossRef]
- Nakayama, K.; Matsuo, Y. MIGSOM: A SOM Algorithm for Large Scale Hyperlinked Documents Inspired by Neuronal Migration. Intell. Tutor. Syst. 2014, 8421, 79–94. [Google Scholar]
- Han, K.; Weimerskirch, A.; Shin, K. Automotive Cybersecurity for In-Vehicle Communication. IQT Q. 2014, 6, 22–25. [Google Scholar]


| Field | CAN Message | Bits (Length) | Description |
|---|---|---|---|
| SOF | CAN 2.0A | 1 | The Start of Frame (SOF) indicates the start of a new message and the single bit must be dominant as it is used for synchronizing all nodes |
| CAN 2.0B | 1 | ||
| Identifier | CAN 2.0A | 11 | The identifier establishes the priority of the message: the lower the value, the higher its priority |
| CAN 2.0B | 11 | This identifier is the first part, which is used in both the standard and extended frames | |
| Identifier extended | CAN 2.0A | - | - |
| CAN 2.0B | 18 | In CAN 2.0B Extended, the identifier is comprised of 11 bits Base ID and 18 bits Extended ID | |
| RTR | CAN 2.0A | 1 | The single remote transmission request (RTR) bit is dominant when information is required from another node. All nodes receive the request, but the identifier determines the specified node. The responding data is also received by all nodes and used by any node interested. In this way, all data being used in a system is uniform [43] |
| CAN 2.0B | 1 | ||
| SRR | CAN 2.0A | - | - |
| CAN 2.0B | 1 | The Substitute Remote Request (SRR) must be recessive and used in the extended frame | |
| IDE | CAN 2.0A | - | - |
| CAN 2.0B | 1 | The Identifier Extension (IDE) must be recessive for extended format and dominant for standard format | |
| Reserved r0 | CAN 2.0A | - | - |
| CAN 2.0B | 1 | Reversed bit must be dominant for standard format | |
| Reserved r0, r1 | CAN 2.0A | 2 | Bits must be dominant |
| CAN 2.0B | 2 | Bits must be recessive for extended format | |
| DLC | CAN 2.0A | 4 | The data length code (DLC) contains the number of data bytes |
| CAN 2.0B | 4 | ||
| Data Field | CAN 2.0A | 64 | The actual payload data which can be up to 64 bits |
| CAN 2.0B | 64 | ||
| CRC | CAN 2.0A | 15 | Cyclic Redundancy Check (CRC) contains the checksum of the previous data for error detection |
| CAN 2.0B | 15 | ||
| CRC Delimiter | CAN 2.0A | 1 | The single bit must be recessive |
| CAN 2.0B | 1 | ||
| ACK | CAN 2.0A | 1 | Acknowledge ensures (ACK) that all nodes involved in the message receive everything correctly and in case of error, the transmitter is immediately alerted to send the data packets again. The transmitter sends recessive, the receiver asserts dominant |
| CAN 2.0B | 1 | ||
| ACK Delimiter | CAN 2.0A | 1 | The single bit must be recessive |
| CAN 2.0B | 1 | ||
| EOF | CAN 2.0A | 7 | End of Frame (EOF) denotes the end of a current CAN message. Bits must be recessive |
| CAN 2.0B | 7 |
| Timestamp | CanID | DLC | D0 | D1 | D2 | D3 | D4 | D5 | D6 | D7 | Label |
|---|---|---|---|---|---|---|---|---|---|---|---|
| 1478193191230940 | 04f0 | 8 | 0 | 0 | 0 | 80 | 0 | 67 | d1 | 13 | R |
| 1478193191234870 | 05f0 | 2 | 1 | 0 | R | ||||||
| …. | … | … | … | … | … | … | … | … | … | … | … |
| 1478193191271620 | 043f | 8 | 1 | 45 | 60 | ff | 6b | 0 | 0 | 0 | T |
| 1478193191272270 | 316 | 8 | 5 | 23 | 70 | 9 | 23 | 21 | 0 | 70 | R |
| …. | … | … | … | … | … | … | … | … | … | … | … |
| Input X Layer | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| Input X CAN Message Vector | DLC | 04f0 | 05f0 | 043f | … | 00080067d113 | 14560ff6b000 | … | Time |
| X1 | 1 | 1 | 0 | 0 | … | 0 | 0 | … | 0.27 |
| X2 | 0.1 | 0 | 0 | 1 | … | 0 | 1 | … | 0.84 |
| X3 | 1 | 0 | 1 | 0 | … | 1 | 0 | … | 0.97 |
| … | … | … | … | … | … | … | … | … | … |
| Xn | 0.5 | 0 | 0 | 0 | … | 0 | 0 | 0.01 | |
| Dataset | Type | Min | Median | Mean | Max | Standard Deviation |
|---|---|---|---|---|---|---|
| DoS | Attack | 0.15 | 0.15 | 0.26 | 2.39 | 0.34 |
| Normal | 1.22 | 1.74 | 1.67 | 3.30 | 0.20 | |
| Spoofing gear | Attack | 0.52 | 0.52 | 0.65 | 1.13 | 0.24 |
| Normal | 1.08 | 1.32 | 1.28 | 1.72 | 0.10 | |
| Spoofing RPM | Attack | 0.52 | 0.52 | 0.65 | 1.13 | 0.25 |
| Normal | 1.07 | 1.32 | 1.28 | 1.67 | 0.10 | |
| Fuzzy | Attack | 0.20 | 1.31 | 1.08 | 1.66 | 0.43 |
| Normal | 1.09 | 1.09 | 1.14 | 1.26 | 0.05 | |
| Mixed | Attack | 0.24 | 1.32 | 1.20 | 1.76 | 0.27 |
| Normal | 0.94 | 1.12 | 1.04 | 1.12 | 0.09 |
| Dataset | Training Set (%) | |||||
|---|---|---|---|---|---|---|
| Accuracy | Precision | Recall | F1 | FNR | ||
| DoS | SOMK-C | 97.78 | 90.88 | 100.00 | 95.22 | 0.00 |
| CI (95%) | 97.45–98.10 | 90.25–91.51 | 100.00–100.00 | 94.75–95.69 | 0.00–0.00 | |
| SOMK-D | 100.00 | 100.00 | 100.00 | 100.00 | 0.00 | |
| CI (95%) | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 0.00–0.00 | |
| Spoofing gear | SOMK-C | 95.60 | 79.70 | 100.00 | 88.70 | 0.00 |
| CI (95%) | 95.15–96.05 | 78.82–80.58 | 100.00–100.00 | 88.01–89.40 | 0.00–0.00 | |
| SOMK-D | 100.00 | 100.00 | 100.00 | 100.00 | 0.00 | |
| CI (95%) | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 0.00–0.00 | |
| Spoofing RPM | SOMK-C | 95.49 | 79.04 | 100.00 | 88.29 | 0.00 |
| CI (95%) | 95.03–95.94 | 78.14–79.93 | 100.00–100.00 | 87.59–89.00 | 0.00–0.00 | |
| SOMK-D | 100.00 | 100.00 | 100.00 | 100.00 | 0.00 | |
| CI (95%) | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 0.00–0.00 | |
| Fuzzy | SOMK-C | 73.20 | 0.46 | 0.20 | 0.28 | 99.80 |
| CI (95%) | 72.23–74.17 | 0.32–0.61 | 0.10–0.30 | 0.16–0.39 | 99.70–99.80 | |
| SOMK-D | 99.58 | 99.66 | 98.07 | 98.86 | 1.93 | |
| CI (95%) | 99.43–99.72 | 99.54–99.79 | 97.77–98.37 | 98.63–99.09 | 1.63–2.23 | |
| Mixed | SOMK-C | 82.55 | 61.76 | 27.91 | 38.45 | 72.09 |
| CI (95%) | 81.72–83.38 | 60.69–62.82 | 26.93–28.90 | 37.38–39.51 | 71.10–73.07 | |
| SOMK-D | 99.86 | 99.68 | 99.62 | 99.65 | 0.38 | |
| CI (95%) | 99.78–99.94 | 99.56–99.80 | 99.48–99.75 | 99.52–99.78 | 0.25–0.52 | |
| Dataset | Test Set (%) | |||||
|---|---|---|---|---|---|---|
| Accuracy | Precision | Recall | F1 | FNR | ||
| DoS | SOMK-C | 97.85 | 91.21 | 100.00 | 95.40 | 0.00 |
| CI (95%) | 97.22–98.49 | 89.97–92.45 | 100.00–100.00 | 94.48–96.32 | 0.00–0.00 | |
| SOMK-D | 100.00 | 100.00 | 100.00 | 100.00 | 0.00 | |
| CI (95%) | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 0.00–0.00 | |
| Spoofing gear | SOMK-C | 95.50 | 79.36 | 100.00 | 88.49 | 0.00 |
| CI (95%) | 94.59–96.41 | 77.58–81.13 | 100.00–100.00 | 87.09–89.89 | 0.00–0.00 | |
| SOMK-D | 100.00 | 100.00 | 100.00 | 100.00 | 0.00 | |
| CI (95%) | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 0.00–0.00 | |
| Spoofing RPM | SOMK-C | 95.75 | 80.41 | 100.00 | 89.14 | 0.00 |
| CI (95%) | 94.87–96.63 | 78.68–82.15 | 100.00–100.00 | 87.78–90.51 | 0.00–0.00 | |
| SOMK-D | 100.00 | 100.00 | 100.00 | 100.00 | 0.00 | |
| CI (95%) | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 100.00–100.00 | 0.00–0.00 | |
| Fuzzy | SOMK-C | 72.55 | 0.00 | 0.00 | - | 100.00 |
| CI (95%) | 70.59–74.51 | 0.00–0.00 | 0.00–0.00 | – | 100.00–100.00 | |
| SOMK-D | 99.40 | 98.92 | 97.87 | 98.39 | 2.13 | |
| CI (95%) | 99.06–99.74 | 98.47–99.37 | 97.23–98.50 | 97.84–98.94 | 1.50–2.77 | |
| Mixed | SOMK-C | 87.01 | 61.05 | 38.41 | 47.15 | 61.59 |
| CI (95%) | 85.53–88.48 | 58.92–63.19 | 36.28–40.54 | 44.97–49.34 | 59.46–63.72 | |
| SOMK-D | 97.60 | 86.29 | 100.00 | 92.64 | 0.00 | |
| CI (95%) | 96.93–98.27 | 84.78–87.79 | 100.00–100.00 | 91.49–93.78 | 0.00–0.00 | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Barletta, V.S.; Caivano, D.; Nannavecchia, A.; Scalera, M. Intrusion Detection for in-Vehicle Communication Networks: An Unsupervised Kohonen SOM Approach. Future Internet 2020, 12, 119. https://doi.org/10.3390/fi12070119
Barletta VS, Caivano D, Nannavecchia A, Scalera M. Intrusion Detection for in-Vehicle Communication Networks: An Unsupervised Kohonen SOM Approach. Future Internet. 2020; 12(7):119. https://doi.org/10.3390/fi12070119
Chicago/Turabian StyleBarletta, Vita Santa, Danilo Caivano, Antonella Nannavecchia, and Michele Scalera. 2020. "Intrusion Detection for in-Vehicle Communication Networks: An Unsupervised Kohonen SOM Approach" Future Internet 12, no. 7: 119. https://doi.org/10.3390/fi12070119
APA StyleBarletta, V. S., Caivano, D., Nannavecchia, A., & Scalera, M. (2020). Intrusion Detection for in-Vehicle Communication Networks: An Unsupervised Kohonen SOM Approach. Future Internet, 12(7), 119. https://doi.org/10.3390/fi12070119







