A Study on Design Requirement Development and Satisfaction for Future Virtual World Systems
Abstract
1. Introduction
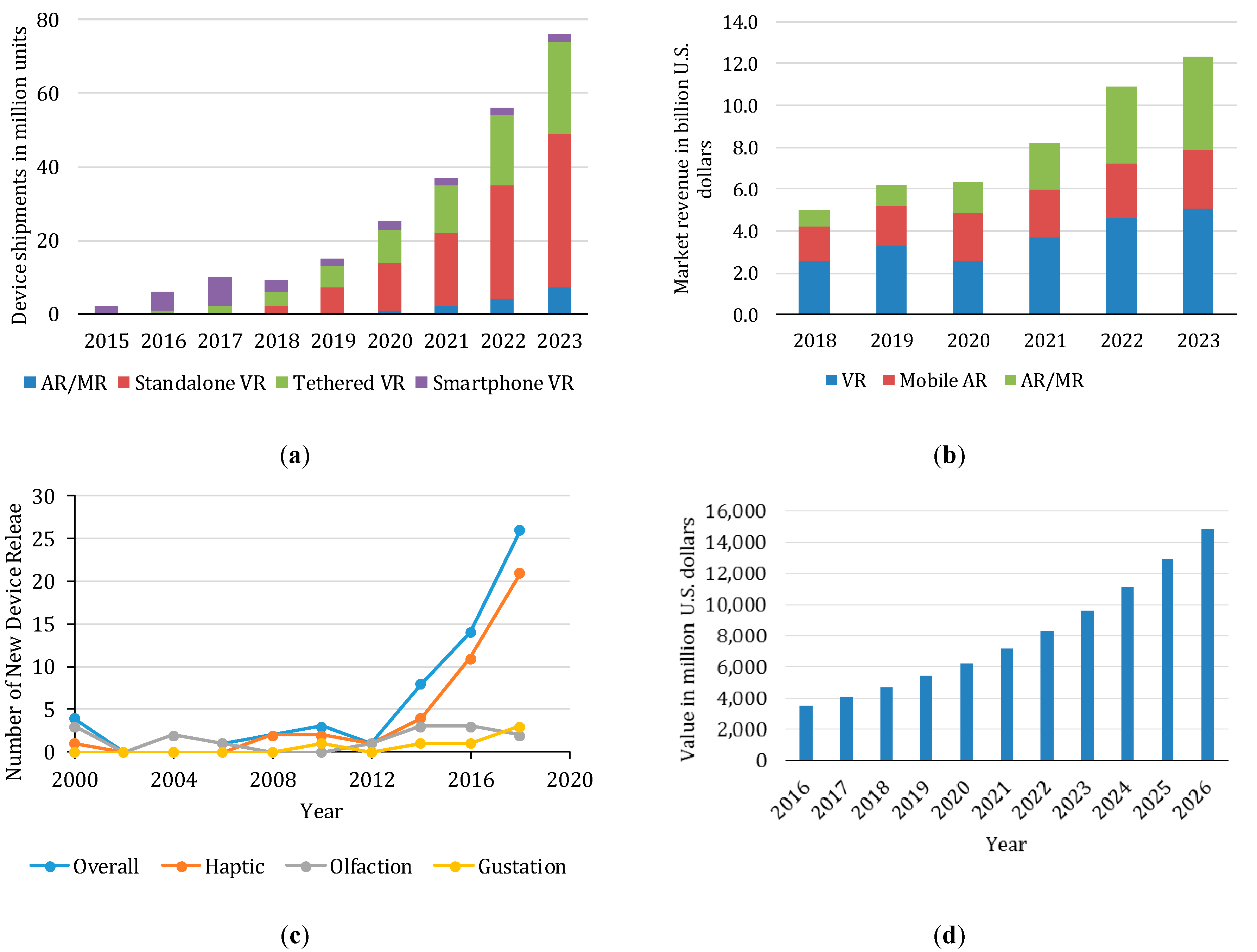
2. Trend Analysis
2.1. Mobility
2.2. Diversity
2.3. Interconnectivity
2.4. Immersion
2.5. Intelligence
2.6. Implications
3. New Requirement Space Development
3.1. Brief Introduction on Existing Requirements
3.2. Sufficiency
3.3. Reliability
3.4. Persistency
3.5. Credibility
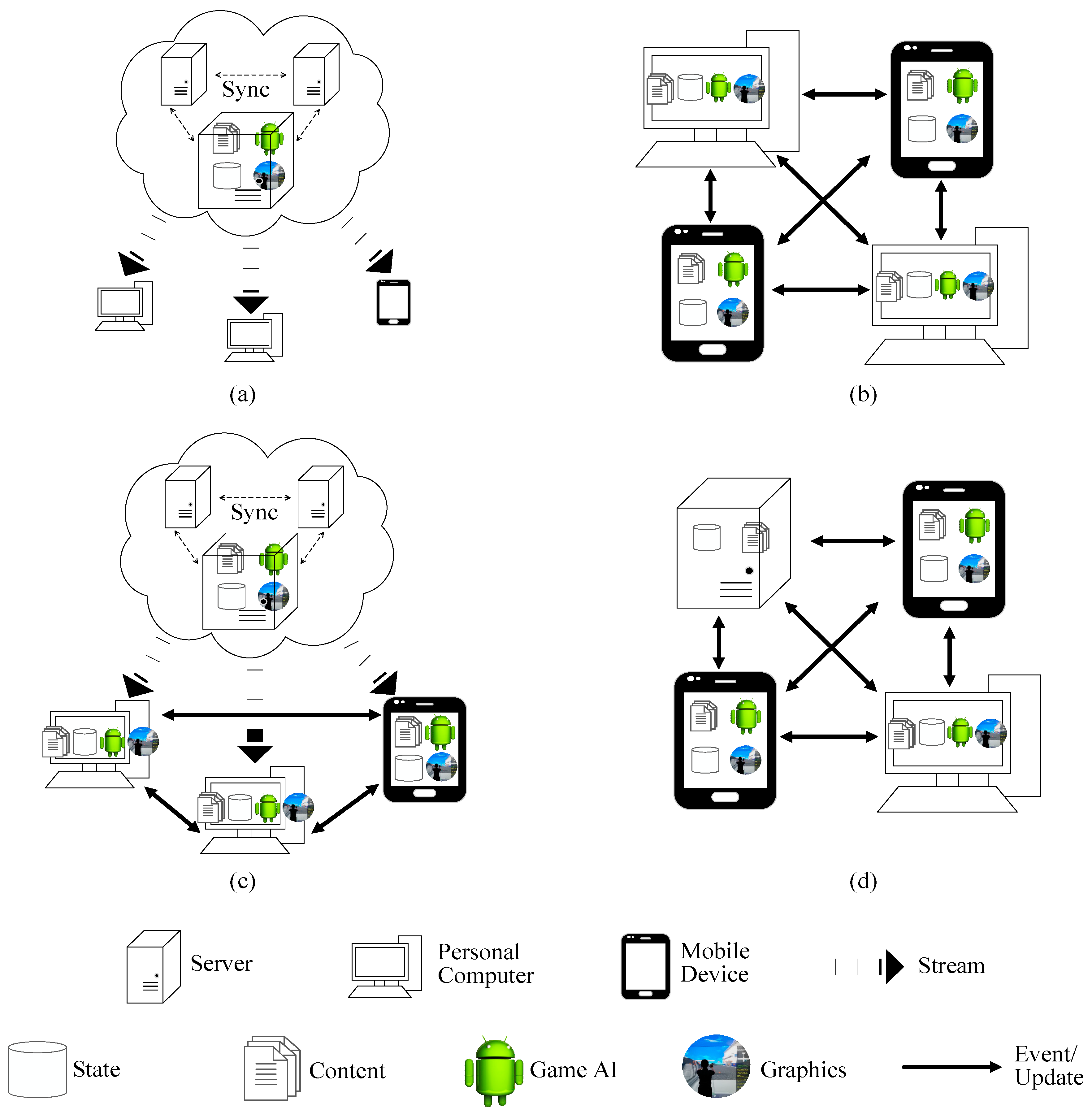
4. Virtual World Architecture Inspection
4.1. Client/Server
4.1.1. Requirement Satisfaction
4.1.2. Limitations
4.2. Peer-To-Peer
4.2.1. Requirement Satisfaction
4.2.2. Limitations
4.3. Hybrid-I
Requirement Satisfaction and Limitations
4.4. Hybrid-II
4.4.1. Requirement Satisfaction
4.4.2. Limitations
5. Discussion
5.1. Architecture Comparison
5.2. A Possible Avenue Towards Future
6. Conclusions
Supplementary Materials
Author Contributions
Funding
Conflicts of Interest
References
- Girvan, C. What is a virtual world? Definition and classification. Educ. Technol. Res. Dev. 2018, 66, 1087–1100. [Google Scholar] [CrossRef]
- Nevelsteen, K.J.L. Virtual world, defined from a technological perspective and applied to video games, mixed reality, and the Metaverse. Comput. Animat. Virtual Worlds 2018, 29, e1752. [Google Scholar] [CrossRef]
- Dionisio, J.D.N.; William, G.B., III; Gilbert, R. 3D virtual worlds and the metaverse: Current status and future possibilities. ACM Comput. Surv. 2013, 45, 1–38. [Google Scholar] [CrossRef]
- Arango-Lopez, J.; Collazos, C.A.; Velas, F.L.G.; Moreira, F. Using pervasive games as learning tools in educational contexts: A systematic review. Int. J. Learn. Technol. 2018, 13, 93–114. [Google Scholar] [CrossRef]
- Li, L.; Yu, F.; Shi, D.; Shi, J.; Tian, Z.; Yang, J.; Wang, X.; Jiang, Q. Application of Virtual Reality Technology in Clinical Medicine. Am. J. Transl. Res. 2017, 9, 3867–3880. Available online: http://www.ncbi.nlm.nih.gov/pubmed/28979666%0Ahttp://www.pubmedcentral.nih.gov/articlerender.fcgi?artid=PMC5622235 (accessed on 3 July 2020).
- Zamora-Musa, R.; Vélez, J.; Paez-Logreira, H. Evaluating Learnability in a 3D Heritage Tour. Presence Teleoperators Virtual Environ. 2018, 26, 366–377. [Google Scholar] [CrossRef]
- Baker, E.W.; Hubona, G.S.; Srite, M. Does ‘Being There’ Matter? The Impact of Web-Based and Virtual World’s Shopping Experiences on Consumer Purchase Attitudes. Inf. Manag. 2019, 1–14. [Google Scholar] [CrossRef]
- Weiss, T.; Schiele, S. Virtual worlds in competitive contexts: Analyzing eSports consumer needs. Electron. Mark. 2013, 23, 307–316. [Google Scholar] [CrossRef]
- Castronova, E. Synthetic Worlds: The Business and Culture of Online Games; University of Chicago Press: Chicago, IL, USA, 2008. [Google Scholar]
- Lehdonvirta, V. Real-money trade of virtual assets: Ten different user perceptions. In Proceedings Digit. Arts Cult. (DAC 2005); IT Univ.: Copenhagen, Denmark, 2005; pp. 52–58. [Google Scholar]
- Adrian, A. No one knows you are a dog: Identity and reputation in virtual worlds. Comput. Law Secur. Rev. 2008, 24, 366–374. [Google Scholar] [CrossRef]
- Messinger, P.R.; Stroulia, E.; Lyons, K. Virtual worlds—Past, present, and future: New directions in social computing. Decis. Support. Syst. 2009, 47, 204–228. [Google Scholar] [CrossRef]
- Skarbez, R.; Brooks, F.P., Jr.; Whitton, M.C. A Survey of Presence and Related Concepts. ACM Comput. Surv. 2017, 50, 1–39. [Google Scholar] [CrossRef]
- Yannakakis, G.N.; Togelius, J. Artificial Intelligence and Games. In Artificial Intelligence and Games, 1st ed.; Springer: New York, NY, USA, 2018; pp. 23–25. [Google Scholar]
- Liu, H.; Bowman, M.; Chang, F. Survey of state melding in virtual worlds. ACM Comput. Surv. 2012, 44, 1–25. [Google Scholar] [CrossRef]
- Liu, H.; Bowman, M.; Adams, R.; Hurliman, J.; Lake, D. Scaling virtual worlds: Simulation requirements and challenges. In Proceedings of the 2010 Winter Simulation Conference, Baltimore, MD, USA, 5–8 December 2010; pp. 778–790. [Google Scholar] [CrossRef]
- Blackburn, J.; Kourtellis, N.; Skvoretz, J.; Ripeanu, M.; Iamnitchi, A. Cheating in Online Games: A Social Network Perspective. ACM Trans. Internet Technol. 2014, 13, 1–25. [Google Scholar] [CrossRef]
- EEDAR. Number of Mobile Gamers in the United States and Canada from 2014 to 2017. Statista—The Statistics Portal. Available online: https://www.statista.com/statistics/454381/mobile-gamers-number-north-america-device/ (accessed on 6 July 2020).
- SuperData Research. Facebook’s Social Gaming Market Revenue from 2010 to 2014 (in Billion U.S. Dollars). Statista—The Statistics Portal. Available online: https://www.statista.com/statistics/276454/worldwide-revenue-of-facebook-social-gaming-forecast/ (accessed on 6 July 2020).
- Statista. Which of the Following Devices do You Use to Play Games? Statista—The Statistics Portal. Available online: https://www.statista.com/forecasts/790476/devices-used-to-play-video-games-in-the-us (accessed on 6 July 2020).
- Statista. Share of Virtual Reality and Augmented Reality (VR and AR) Users in the United States as of 2018, by Type of Device. Statista—The Statistics Portal. Available online: https://www.statista.com/statistics/830508/us-virtual-augmented-reality-users-by-device/ (accessed on 6 July 2020).
- Context. Ranking of Purposes of Use for Virtual Reality in Europe in 2015, by Type of Audience*. Statista—The Statistics Portal. 2016. Available online: https://www.statista.com/statistics/676547/virtual-reality-preferred-purposes-of-use-in-europe-by-type-of-audience/ (accessed on 6 July 2020).
- Perkins Coie, Virtual/Augmented Reality Technology and Content Investment Focuses Worldwide in 2016 and 2018. Statista—The Statistics Portal. Available online: https://www.statista.com/statistics/829729/investments-focus-vr-augmented-reality-worldwide/ (accessed on 6 July 2020).
- Hakonen, M.; Bosch-Sijtsema, P. Virtual Worlds Enabling Distributed Collaboration. J. Virtual Worlds Res. 2014, 7. [Google Scholar] [CrossRef]
- Gautam, A.; Williams, D.; Terry, K.; Robinson, K.; Newbill, P. Mirror Worlds: Examining the Affordances of a Next Generation Immersive Learning Environment. TechTrends 2018, 62, 119–125. [Google Scholar] [CrossRef]
- Mildner, P.; John, B.; Moch, A.; Effelsberg, W. Creation of Custom-made Serious Games with User-generated Learning Content. In Proceedings of the 13th Annual Workshop on Network and Systems Support for Games, Nagoya, Japan, 4–5 December 2014; pp. 1–6. Available online: http://dl.acm.org/citation.cfm?id=2755535.2755556 (accessed on 3 July 2020).
- Guttentag, D.A. Virtual reality: Applications and implications for tourism. Tour. Manag. 2010, 31, 637–651. [Google Scholar] [CrossRef]
- Kohler, T.; Matzler, K.; Füller, J. Avatar-based innovation: Using virtual worlds for real-world innovation. Technovation 2009, 29, 395–407. [Google Scholar] [CrossRef]
- Tractica. Wearable Device Sales Revenue Worldwide from 2016 to 2022 (in Billion U.S. Dollars). Statista—The Statistics Portal. 2016. Available online: https://www.statista.com/statistics/610447/wearable-device-revenue-worldwide/ (accessed on 6 July 2020).
- Gartner, Forecast unit shipments of wearable devices worldwide from 2017 to 2019 and in 2022 (in million units), by category. Statista—The Statistics Portal. 2018. Available online: https://www.statista.com/statistics/385658/electronic-wearable-fitness-devices-worldwide-shipments/ (accessed on 6 July 2020).
- Eye Create Worlds LLC, VR for IoT—Rethinking data visualization. 2016. Available online: http://www.eyecreateworlds.com/index.php/56-vr-for-iot-and-pushing-the-limits-of-the-dk2-tracking-volume (accessed on 14 March 2019).
- Crowdpark, Mobile social gaming revenue worldwide from 2010 to 2014 (in billion U.S. dollars). Statista - The Statistics Portal. Available online: https://www.statista.com/statistics/248658/worldwide-mobile-social-gaming-revenue/ (accessed on 6 July 2020).
- Xania News, Value of the social online games market worldwide from 2010 to 2020, by type (in million U.S. dollars). Statista—The Statistics Portal. Available online: https://www.statista.com/statistics/558350/value-social-online-games-by-type-global/ (accessed on 6 July 2020).
- Entertainment Software Association, Essential Facts: About the computer and video game industry. 2016 Sales, Demographic and Usage Data. 2016. Available online: http://essentialfacts.theesa.com/Essential-Facts-2016.pdf (accessed on 14 March 2019).
- CCS Insight, Virtual (VR) and augmented reality (AR) device shipments worldwide from 2015 to 2023 (in million units), by product type. Statista—The Statistics Portal. 2019. Available online: https://www.statista.com/statistics/1055434/worldwide-vr-ar-device-shipments-by-product-type/ (accessed on 6 July 2020).
- SuperData, Immersive technology consumer market revenue worldwide from 2018 to 2023, by segment (in billion U.S. dollars). Statista—The Statistics Portal. 2020. Available online: https://www.statista.com/statistics/936078/worldwide-consumer-immersive-technology-market-revenue/ (accessed on 6 July 2020).
- Covaci, A.; Zou, L.; Tal, I.; Muntean, G.-M.; Ghinea, G. Is Multimedia Multisensorial? - A Review of Mulsemedia Systems. ACM Comput. Surv. 2018, 51, 1–35. [Google Scholar] [CrossRef]
- Statista. Total Value of the Haptic Technology Market in the Asia-Pacific Region in 2016 and 2017 with a Forecast up to 2026 (in Million U.S. Dollars). Statista—The Statistics Portal. Available online: https://www.statista.com/statistics/950075/asia-pacific-haptic-technology-market-value/ (accessed on 6 July 2020).
- Miikkulainen, R.; Bryant, B.D.; Cornelius, R.; Karpov, I.V.; Stanley, K.O.; Yong, C.H. Computational intelligence in games. Comput. Intell. Princ. Pract. 2006, 155–191. [Google Scholar]
- Yannakakis, G.N.; Togelius, J. A Panorama of Artificial and Computational Intelligence in Games. IEEE Trans. Comput. Intell. AI Games 2015, 7, 317–335. [Google Scholar] [CrossRef]
- Summerville, A.; Snodgrass, S.; Guzdial, M.; Holmgård, C. Procedural Content Generation via Machine Learning (PCGML). IEEE Trans. Games 2017, 10, 257–270. [Google Scholar] [CrossRef]
- Kybartas, B.; Bidarra, R. A Survey on Story Generation Techniques for Authoring Computational Narratives. IEEE Trans. Comput. Intell. AI Games 2017, 9, 239–253. [Google Scholar] [CrossRef]
- Luck, M.; Aylett, R. Applying artificial intelligence to virtual reality: Intelligent virtual environments. Appl. Artif. Intell. 2000, 14, 3–32. [Google Scholar] [CrossRef]
- Petrović, V.M. Artificial Intelligence and Virtual Worlds—Toward Human-Level AI Agents. IEEE Access 2018, 6, 39976–39988. [Google Scholar] [CrossRef]
- Arruda, L.V.R.; Mendonça, M.; Neves, F.; Chrun, I.R.; Papageorgiou, E.I. Artificial Life Environment Modeled by Dynamic Fuzzy Cognitive Maps. IEEE Trans. Cogn. Dev. Syst. 2018, 10, 88–101. [Google Scholar] [CrossRef]
- Sharma, S.; Devreaux, P.; Sree, S.; Scribner, D.; Grynovicki, J.; Grazaitis, P. Artificial intelligence agents for crowd simulation in an immersive environment for emergency response. Electron. Imaging 2019, 2019, 1–8. [Google Scholar] [CrossRef]
- Guérin, É.; Digne, J.; Galin, É. Interactive Example-Based Terrain Authoring with Conditional Generative Adversarial Networks. ACM Trans. Graph. 2017, 36, 6. [Google Scholar] [CrossRef]
- Polap, D. Voice Control in Mixed Reality. In Proceedings of the 2018 Federated Conference on Computer Science and Information Systems (FedCSIS), Poznań, Poland, 9–12 September 2018; pp. 497–500. [Google Scholar]
- Hassani, K.; Nahvi, A.; Ahmadi, A. Design and implementation of an intelligent virtual environment for improving speaking and listening skills. Interact. Learn. Environ. 2016, 24, 252–271. [Google Scholar] [CrossRef]
- Ducheneaut, N.; Yee, N.; Nickell, E.; Moore, R.J. ‘Alone Together?’: Exploring the Social Dynamics of Massively Multiplayer Online Games. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Montréal, QC, Canada, 22–27 April 2006; pp. 407–416. [Google Scholar] [CrossRef]
- Bulu, S.T. Place presence, social presence, co-presence, and satisfaction in virtual worlds. Comput. Educ. 2012, 58, 154–161. [Google Scholar] [CrossRef]
- Fernando, N.; Loke, S.W.; Rahayu, W. Mobile cloud computing: A survey. Futur. Gener. Comput. Syst. 2013, 29, 84–106. [Google Scholar] [CrossRef]
- Dinh, H.T.; Lee, C.; Niyato, D.; Wang, P. A survey of mobile cloud computing: Architecture, applications, and approaches. Wirel. Commun. Mob. Comput. 2013, 13, 1587–1611. [Google Scholar] [CrossRef]
- Barbera, M.V.; Kosta, S.; Mei, A.; Stefa, J. To offload or not to offload? The bandwidth and energy costs of mobile cloud computing. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 1285–1293. [Google Scholar] [CrossRef]
- Cai, W.; Leung, V.C.M.; Chen, M. Next Generation Mobile Cloud Gaming. In Proceedings of the 2013 IEEE Seventh International Symposium on Service-Oriented System Engineering, Redwood City, CA, USA, 25–28 March 2013; pp. 551–560. [Google Scholar] [CrossRef]
- Guo, J.; Gong, Z. Measuring virtual wealth in virtual worlds. Inf. Technol. Manag. 2011, 12, 121–135. [Google Scholar] [CrossRef]
- Hetcher, S. User-Generated Content and the Future of Copyright: Part Two—Agreements between Users and Mega-Sites Symposium Review. St. Cl. Comput. High. Technol. Law J. 2007, 24, 829–868. Available online: https://heinonline.org/HOL/P?h=hein.journals/sccj24&i=839 (accessed on 3 July 2020).
- Terry, D. Replicated Data Consistency Explained Through Baseball. Commun. ACM 2013, 56, 82–89. [Google Scholar] [CrossRef]
- Mauve, M.; Vogel, J.; Hilt, V.; Effelsberg, W. Local-lag and timewarp: Providing consistency for replicated continuous applications. IEEE Trans. Multimed. 2004, 6, 47–57. [Google Scholar] [CrossRef]
- Khan, A.M.; Chabridon, S.; Beugnard, A. Synchronization Medium: A Consistency Maintenance Component for Mobile Multiplayer Games. In Proceedings of the 6th ACM SIGCOMM Workshop on Network and System Support for Games, Melbourne, Australia, 19–20 September 2007; pp. 99–104. [Google Scholar] [CrossRef]
- Millar, J.R.; Hodson, D.D.; Peterson, G.L.; Ahner, D.K. Consistency and fairness in real-time distributed virtual environments: Paradigms and relationships. J. Simul. 2017, 11, 295–302. [Google Scholar] [CrossRef]
- Bondi, A.B. Characteristics of scalability and their impact on performance. In Proceedings of the 2nd international workshop on Software and performance, Ottawa, ON, Canada, 17–20 September 2000; pp. 195–203. [Google Scholar]
- Bezerra, C.E.B.; Geyer, C.F.R. A load balancing scheme for massively multiplayer online games. Multimed. Tools Appl. 2009, 45, 263–289. [Google Scholar] [CrossRef]
- Lee, C.Y. Understanding Security Threats in Virtual Worlds. AMCIS 2009. 2009, p. 466. Available online: http://aisel.aisnet.org/amcis2009/466 (accessed on 3 July 2020).
- Irdeto. Irdeto Global Gaming Survey: The Last Checkpoint for Cheating. 2018. Available online: https://www.statista.com/study/54578/cheating-in-video-gaming-report/ (accessed on 6 July 2020).
- Yahyavi, A.; Kemme, B. Peer-to-peer architectures for massively multiplayer online games: A survey. ACM Comput. Surv. 2013, 46, 1–51. [Google Scholar] [CrossRef]
- Miettinen, A.P.; Nurminen, J.K. Energy Efficiency of Mobile Clients in Cloud Computing. In Proceedings of the 2nd {USENIX} Workshop on Hot Topics in Cloud Computing, HotCloud’10, Boston, MA, USA, 22 June 2010; Available online: https://www.usenix.org/conference/hotcloud-10/energy-efficiency-mobile-clients-cloud-computing (accessed on 3 July 2020).
- Altamimi, M.; Abdrabou, A.; Naik, K.; Nayak, A. Energy Cost Models of Smartphones for Task Offloading to the Cloud. IEEE Trans. Emerg. Top. Comput. 2015, 3, 384–398. [Google Scholar] [CrossRef]
- Cai, W.; Shea, R.; Huang, C.; Chen, K.; Liu, J.; Leung, V.C.M. A survey on cloud gaming: Future of computer games. IEEE Access 2016, 4, 7605–7620. [Google Scholar] [CrossRef]
- Shen, B.; Guo, J. Uninterruptible Play in Virtual Node-based Virtual Worlds. In Proceedings of the 10th International Workshop on Immersive Mixed and Virtual Environment Systems, Las Vegas, NV, USA, 15–20 July 2018; pp. 22–27. [Google Scholar] [CrossRef]
- Brewer, E. CAP twelve years later: How the ‘rules’ have changed. Computer 2012, 45, 23–29. [Google Scholar] [CrossRef]
- Gilbert, S.; Lynch, N. Perspectives on the CAP Theorem. Computer 2012, 45, 30–36. [Google Scholar] [CrossRef]
- Abadi, D. Consistency Tradeoffs in Modern Distributed Database System Design: CAP is Only Part of the Story. Computer 2012, 45, 37–42. [Google Scholar] [CrossRef]
- Nevelsteen, K.J.L. Survey of Pervasive Games and Technologies. In A Survey of Characteristic Engine Features for Technology-Sustained Pervasive Games; Springer International Publishing: Cham, Switzerland, 2015; pp. 11–39. [Google Scholar]
- Chatzigiannakis, I.; Mylonas, G.; Akribopoulos, O.; Logaras, M.; Kokkinos, P.; Spirakis, P. The ‘Hot Potato’ Case: Challenges in Multiplayer Pervasive Games Based on Ad hoc Mobile Sensor Networks and the Experimental Evaluation of a Prototype Game. arXiv 2010, arXiv:1002.1099. Available online: https://arxiv.org/abs/1002.1099 (accessed on 3 July 2020).
- Fan, L. Solving Key Design Issues for Massively Multiplayer Online Games on Peer-to-Peer Architectures; Heriot-Watt University: Heriot-Watt, UK, 2009. [Google Scholar]
- Zhang, K.; Kemme, B. Transaction Models for Massively Multiplayer Online Games. In Proceedings of the 2011 IEEE 30th International Symposium on Reliable Distributed Systems, Madrid, Spain, 4–7 October 2011; pp. 31–40. [Google Scholar] [CrossRef]
- Gilmore, J.S.; Engelbrecht, H.A. A survey of state persistency in peer-to-peer massively multiplayer online games. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 818–834. [Google Scholar] [CrossRef]
- Nachiappan, R.; Javadi, B.; Calheiros, R.N.; Matawie, K.M. Cloud storage reliability for Big Data applications: A state of the art survey. J. Netw. Comput. Appl. 2017, 97, 35–47. [Google Scholar] [CrossRef]
- Jøsang, A.; Ismail, R.; Boyd, C. A survey of trust and reputation systems for online service provision. Decis. Support. Syst. 2007, 43, 618–644. [Google Scholar] [CrossRef]
- Li, Z.; Liao, L.; Leung, H.; Li, B.; Li, C. Evaluating the credibility of cloud services. Comput. Electr. Eng. 2017, 58, 161–175. [Google Scholar] [CrossRef]
- Bélanger, F.; Crossler, R.E. Privacy in the Digital Age: A Review of Information Privacy Research in Information Systems. MIS Q. 2011, 35, 1017–1042. Available online: http://dl.acm.org/citation.cfm?id=2208940.2208951 (accessed on 3 July 2020). [CrossRef]
- Theoharidou, M.; Papanikolaou, N.; Pearson, S.; Gritzalis, D. Privacy Risk, Security, Accountability in the Cloud. In Proceedings of the 2013 IEEE 5th International Conference on Cloud Computing Technology and Science, Bristol, UK, 2–5 December 2013; Volume 1, pp. 177–184. [Google Scholar] [CrossRef]
- Pearson, S. Strong Accountability and Its Contribution to Trustworthy Data Handling in the Information Society. In Trust Management XI; Springer: Berlin/Heidelberg, Germany, 2017; pp. 199–218. [Google Scholar] [CrossRef]
- Tietze, F.; Pieper, T.; Herstatt, C. To own or not to own: How ownership impacts user innovation–An empirical study. Technovation 2015, 38, 50–63. [Google Scholar] [CrossRef]
- Coutinho, P.; José, R. A Risk Management Framework for User-Generated Content on Public Display Systems. Adv. Human-Computer Interact. 2019, 2019, 9769246:1–9769246:18. [Google Scholar] [CrossRef]
- Cuervo, E. MAUI: Making Smartphones Last Longer with Code Offload. In Proceedings of the 8th International Conference on Mobile Systems, Applications, and Services, San Francisco, CA, USA, 15–18 June 2010; pp. 49–62. [Google Scholar] [CrossRef]
- Lin, Y.; Kemme, B.; Patino-Martinez, M.; Jimenez-Peris, R. Applying Database Replication to Multi-player Online Games. In Proceedings of the 5th ACM SIGCOMM Workshop on Network and System Support for Games, Singapore, 30–31 October 2006. [Google Scholar] [CrossRef]
- Engelbrecht, H.A.; Gilmore, J.S. Pithos: Distributed Storage for Massive Multi-User Virtual Environments. ACM Trans. Multimed. Comput. Commun. Appl. 2017, 13, 1–33. [Google Scholar] [CrossRef]
- Carlini, E.; Ricci, L.; Coppola, M. Flexible load distribution for hybrid distributed virtual environments. Futur. Gener. Comput. Syst. 2013, 29, 1561–1572. [Google Scholar] [CrossRef]
- Richerzhagen, B.; Stingl, D.; Hans, R.; Gross, C.; Steinmetz, R. Bypassing the cloud: Peer-assisted event dissemination for augmented reality games. In Proceedings of the 14-th IEEE International Conference on Peer-to-Peer Computing, London, UK, 8–12 September 2014; pp. 1–10. [Google Scholar] [CrossRef]
- Varvello, M.; Diot, C.; Biersack, E. P2P second life: Experimental validation using Kad. In Proceedings of the IEEE INFOCOM, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 1161–1169. [Google Scholar] [CrossRef]
- Amini, M.; Osanloo, F. Purpose-based Privacy Preserving Access Control for Secure Service Provision and Composition. IEEE Trans. Serv. Comput. 2018, 1. [Google Scholar] [CrossRef]
- Shen, B.; Guo, J.; Yang, Y. MedChain: Efficient Healthcare Data Sharing via Blockchain. Appl. Sci. 2019, 9, 1207. [Google Scholar] [CrossRef]
- Henze, M.; Matzutt, R.; Hiller, J.; Mühmer, E.; Ziegeldorf, j.; van der Giet, J. Practical Data Compliance for Cloud Storage. In Proceedings of the 2017 IEEE International Conference on Cloud Engineering (IC2E), Vancouver, BC, Canada, 4–7 April 2017; pp. 252–258. [Google Scholar] [CrossRef]
- Zhou, M.; Leenders, M.A.A.M.; Cong, L.M. Ownership in the virtual world and the implications for long-term user innovation success. Technovation 2018, 78, 56–65. [Google Scholar] [CrossRef]
- Kim, J.; Chung, H.; Lee, M.; Chang, Y.; Jung, J.; Shin, P. Design of user-centric semantic rights model for validation of user-generated content. Cluster Comput. 2016, 19, 1261–1273. [Google Scholar] [CrossRef]
- Ma, Z.; Jiang, M.; Gao, H.; Wang, Z. Blockchain for digital rights management. Futur. Gener. Comput. Syst. 2018, 89, 746–764. [Google Scholar] [CrossRef]
- Cai, W.; Chen, M.; Leung, V.C.M. Toward Gaming as a Service. IEEE Internet Comput. 2014, 18, 12–18. [Google Scholar] [CrossRef]
- Chi, F.; Wang, X.; Cai, W.; Leung, V.C.M. Ad-Hoc Cloudlet Based Cooperative Cloud Gaming. IEEE Trans. Cloud Comput. 2018, 6, 625–639. [Google Scholar] [CrossRef]
- Ghaffari, M.; Hariri, B.; Shirmohammadi, S.; Ahmed, D.T. A Dynamic Networking Substrate for Distributed MMOGs. IEEE Trans. Emerg. Top. Comput. 2015, 3, 289–302. [Google Scholar] [CrossRef]
- Diaconu, R.; Keller, J. Kiwano: Scaling virtual worlds. In Proceedings of the Winter Simulation Conference, Washington, DC, USA, 11–14 December 2017; pp. 1836–1847. [Google Scholar] [CrossRef]
- Ricci, L.; Genovali, L.; Carlini, E.; Coppola, M. AOI-cast in distributed virtual environments: An approach based on delay tolerant reverse compass routing. Concurr. Comput. 2015, 27, 2329–2350. [Google Scholar] [CrossRef]
- Mönch, C.; Grimen, G.; Midtstraum, R. Protecting Online Games Against Cheating. In Proceedings of the 5th ACM SIGCOMM Workshop on Network and System Support for Games, Singapore, 30–31 October 2006. [Google Scholar] [CrossRef]
- Laurens, P.; Paige, R.F.; Brooke, P.J.; Chivers, H. A Novel Approach to the Detection of Cheating in Multiplayer Online Games. In Proceedings of the 12th IEEE International Conference on Engineering Complex Computer Systems (ICECCS 2007), Auckland, New Zealand, 11–14 July 2007; pp. 97–106. [Google Scholar] [CrossRef]
- Goodman, J.; Verbrugge, C. A Peer Auditing Scheme for Cheat Elimination in MMOGs. In Proceedings of the 7th ACM SIGCOMM Workshop on Network and System Support for Games, Worcester, MA, USA, 21–22 October 2008; pp. 9–14. [Google Scholar] [CrossRef]
- Schuster, S.; Weis, T. Enforcing Game Rules in Untrusted P2P-based MMVEs. In Proceedings of the 4th International ICST Conference on Simulation Tools and Techniques; 2011; pp. 288–295. Available online: http://dl.acm.org/citation.cfm?id=2151054.2151106 (accessed on 3 July 2020).
- Webb, S.; Soh, S.; Lau, W. RACS: A referee anti-cheat scheme for P2P gaming. In Proceedings of the 17th international workshop on Network and operating systems support for digital audio and video; 2007; pp. 34–42. Available online: http://hdl.handle.net/20.500.11937/32304 (accessed on 3 July 2020).
- Flores, H.; Hui, P.; Tarkoma, S.; Li, Y.; Srirama, S.; Buyya, R. Mobile code offloading: From concept to practice and beyond. IEEE Commun. Mag. 2015, 53, 80–88. [Google Scholar] [CrossRef]
- Shi, S.; Hsu, C.-H. A Survey of Interactive Remote Rendering Systems. ACM Comput. Surv. 2015, 47, 1–29. [Google Scholar] [CrossRef]
- Lin, Y.; Shen, H. CloudFog: Leveraging Fog to Extend Cloud Gaming for Thin-Client MMOG with High Quality of Service. IEEE Trans. Parallel Distrib. Syst. 2017, 28, 431–445. [Google Scholar] [CrossRef]
- Gunes, M.H.; Yuksel, M.; Ceker, H. A blind processing framework to facilitate openness in smart grid communications. Comput. Networks 2015, 86, 14–26. [Google Scholar] [CrossRef]
- Wang, H. Anonymous Data Sharing Scheme in Public Cloud and Its Application in E-Health Record. IEEE Access 2018, 6, 27818–27826. [Google Scholar] [CrossRef]
- Li, J.; Lin, X.; Zhang, Y.; Han, J. KSF-OABE: Outsourced Attribute-Based Encryption with Keyword Search Function for Cloud Storage. IEEE Trans. Serv. Comput. 2017, 10, 715–725. [Google Scholar] [CrossRef]
- Wang, B.; Li, B.; Li, H. Oruta: Privacy-preserving public auditing for shared data in the cloud. IEEE Trans. Cloud Comput. 2014, 2, 43–56. [Google Scholar] [CrossRef]
- Stolfo, S.J.; Salem, M.B.; Keromytis, A.D. Fog Computing: Mitigating Insider Data Theft Attacks in the Cloud. In Proceedings of the 2012 IEEE Symposium on Security and Privacy Workshops, San Francisco, CA, USA, 24–25 May 2012; pp. 125–128. [Google Scholar] [CrossRef]
- Kasapakis, V.; Gavalas, D. Pervasive gaming: Status, trends and design principles. J. Netw. Comput. Appl. 2015, 55, 213–236. [Google Scholar] [CrossRef]
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, A.; Rajarajan, M. A survey on security issues and solutions at different layers of Cloud computing. J. Supercomput. 2013, 63, 561–592. [Google Scholar] [CrossRef]
- Sarathy, R.; Robertson, C.J. Strategic and Ethical Considerations in Managing Digital Privacy. J. Bus. Ethics 2003, 46, 111–126. [Google Scholar] [CrossRef]
- Dougherty, C. Bragg v. Linden: Virtual Property Rights Litigation. E-Commerce Law Policy 2007, Volume 9, 1–5. Available online: http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1092284 (accessed on 3 July 2020).
- DRyu, M. United States District Court Northern District of California; Evans v. Linden Research, Inc., 2014; Volume C-11–01078, pp. 1–9. Available online: https://casetext.com/case/evans-v-linden-research-12 (accessed on 3 July 2020).
- George, C.; Scerri, J. Web 2.0 and user-generated content: Legal challenges in the new frontier. J. Inf. Law Technol. 2007, 12, 1–22. Available online: http://www2.warwick.ac.uk/fac/soc/law/elj/jilt/2007_2/george_scerri/george_scerri.pdf (accessed on 3 July 2020).
- Knutsson, B.; Lu, H.; Xu, W.; Hopkins, B. Peer-to-peer support for massively multiplayer games. In Proceedings of the IEEE INFOCOM 2004, Hong Kong, China, 7–11 March 2004; Volume 1, pp. 96–107. [Google Scholar] [CrossRef]
- Buyukkaya, E.; Abdallah, M.; Simon, G. A survey of peer-to-peer overlay approaches for networked virtual environments. Peer-to-Peer Netw. Appl. 2013, 8, 276–300. [Google Scholar] [CrossRef]
- Bhagwan, R.; Tati, K.; Cheng, Y.C.; Savage, S.; Voelker, G.M. Total Recall: System Support for Automated Availability Management. In Proceedings of the NSDI; 2004; p. 25. Available online: http://portal.acm.org/citation.cfm?id=1251175.1251200 (accessed on 3 July 2020).
- Shen, B.; Guo, J. Virtual Net: A Decentralized Architecture for Interaction in Mobile Virtual Worlds. Wirel. Commun. Mob. Comput. 2018, 2018, 9749187:1–9749187:24. [Google Scholar] [CrossRef]
- Hu, S.Y.; Huang, T.H.; Chang, S.C.; Sung, W.L.; Jiang, J.R.; Chen, B.Y. FLoD: A framework for peer-to-peer 3D streaming. In Proceedings of the IEEE INFOCOM 2007—26th IEEE International Conference on Computer Communications, Barcelona, Spain, 6–12 May 2007; pp. 2047–2055. [Google Scholar] [CrossRef]
- Çevikbaş, Ş.B.; İşler, V. Phaneros: Visibility-based framework for massive peer-to-peer virtual environments. Comput. Animat. Virtual Worlds 2019, 30, e1808. [Google Scholar] [CrossRef]
- Cruz, J.P.; Kaji, Y.; Yanai, N. RBAC-SC: Role-Based Access Control Using Smart Contract. IEEE Access 2018, 6, 12240–12251. [Google Scholar] [CrossRef]
- Lee, J. BIDaaS: Blockchain Based ID As a Service. IEEE Access 2018, 6, 2274–2278. [Google Scholar] [CrossRef]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Futur. Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Neisse, R.; Steri, G.; Nai-Fovino, I. A Blockchain-based Approach for Data Accountability and Provenance Tracking. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–10. [Google Scholar] [CrossRef]
- Vogel, M. Final Fantasy XV Pocket Edition HD Review. Nintendo Life. 2018. Available online: http://www.nintendolife.com/reviews/switch-eshop/final_fantasy_xv_pocket_edition_hd (accessed on 26 May 2019).
- Gillham, N. Final Fantasy XV: Pocket Edition Review. GodisaGeek. 2018. Available online: https://www.godisageek.com/reviews/final-fantasy-xv-pocket-edition-review/ (accessed on 26 May 2019).
- Carlini, E.; Coppola, M.; Ricci, L. Integration of P2P and clouds to support massively multiuser virtual environments. In Proceedings of the 2010 9th Annual Workshop on Network and Systems Support for Games, NetGames 2010, Taipei, Taiwan, 16–17 November 2010; pp. 1–6. [Google Scholar] [CrossRef]
- Flintham, M.; Benford, S.; Anastasi, R.; Hemmings, T.; Crabtree, A. Where On-line Meets on the Streets: Experiences with Mobile Mixed Reality Games. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Ft. Lauderdale, FL, USA, 5–10 April 2003; pp. 569–576. [Google Scholar] [CrossRef]
- Bujari, A.; de Giovanni, L.; Palazzi, C.E. Optimal configuration of active and backup servers for augmented reality cooperative games. Concurr. Comput. Pract. Exp. 2018, 30, e4454. [Google Scholar] [CrossRef]
- Cai, W.; Leung, V.C.M.; Hu, L. A Cloudlet-Assisted Multiplayer Cloud Gaming System. Mob. Networks Appl. 2014, 19, 144–152. [Google Scholar] [CrossRef]
- Najaran, M.T.; Krasic, C. Scaling online games with adaptive interest management in the cloud. In Proceedings of the 2010 9th Annual Workshop on Network and Systems Support for Games, Taipei, Taiwan, 16–17 November 2010; pp. 1–6. [Google Scholar] [CrossRef]
- Carter, C.; Rhalibi, A.E.; Merabti, M.; Bendiab, A.T. Hybrid Client-Server, Peer-to-Peer framework for MMOG. In Proceedings of the 2010 IEEE International Conference on Multimedia and Expo, Suntec City, Singapore, 19–23 July 2010; pp. 1558–1563. [Google Scholar] [CrossRef]
- DAhmed, T.; Shirmohammadi, S.; de Oliveira, J.C. A hybrid P2P communications architecture for zonal MMOGs. Multimed. Tools Appl. 2009, 45, 313–345. [Google Scholar] [CrossRef]
- Carlini, E.; Ricci, L.; Coppola, M. Integrating centralized and peer-to-peer architectures to support interest management in massively multiplayer on-line games. Concurr. Comput. 2015, 27, 3362–3382. [Google Scholar] [CrossRef]
- Kavalionak, H.; Carlini, E.; Ricci, L.; Montresor, A.; Coppola, M. Integrating peer-to-peer and cloud computing for massively multiuser online games. Peer-to-Peer Netw. Appl. 2015, 8, 301–319. [Google Scholar] [CrossRef]
- Lua, E.K.; Crowcroft, J.; Pias, M.; Sharma, R.; Lim, S. A survey and comparison of peer-to-peer overlay network schemes. IEEE Commun. Surv. Tutor. 2005, 7, 72–93. [Google Scholar] [CrossRef]
- Flexera Software. Challenges of Using Cloud Computing Worldwide as of 2019. Statista—The Statistics Portal. Available online: https://www.statista.com/statistics/511283/worldwide-survey-cloud-computing-risks/ (accessed on 6 July 2020).
- Oualha, N.; Leneutre, J.; Roudier, Y. Verifying remote data integrity in peer-to-peer data storage: A comprehensive survey of protocols. Peer-to-Peer Netw. Appl. 2012, 3, 231–243. [Google Scholar] [CrossRef]
- Matsumoto, K.; Okabe, Y. A Collusion-Resilient Hybrid P2P Framework for Massively Multiplayer Online Games. In Proceedings of the 2017 IEEE 41st Annual Computer Software and Applications Conference (COMPSAC), Turin, Italy, 4–8 July 2017; Volume 2, pp. 342–347. [Google Scholar] [CrossRef]
- Shen, B.; Guo, J. Efficient Peer-to-peer Content Sharing for Learning in Virtual Worlds. J. Univers. Comput. Sci. 2019, 25, 465–488. [Google Scholar]
- Shen, B.; Guo, J.; Li, L.X. Cost optimization in persistent virtual world design. Inf. Technol. Manag. 2018, 19, 155–169. [Google Scholar] [CrossRef]
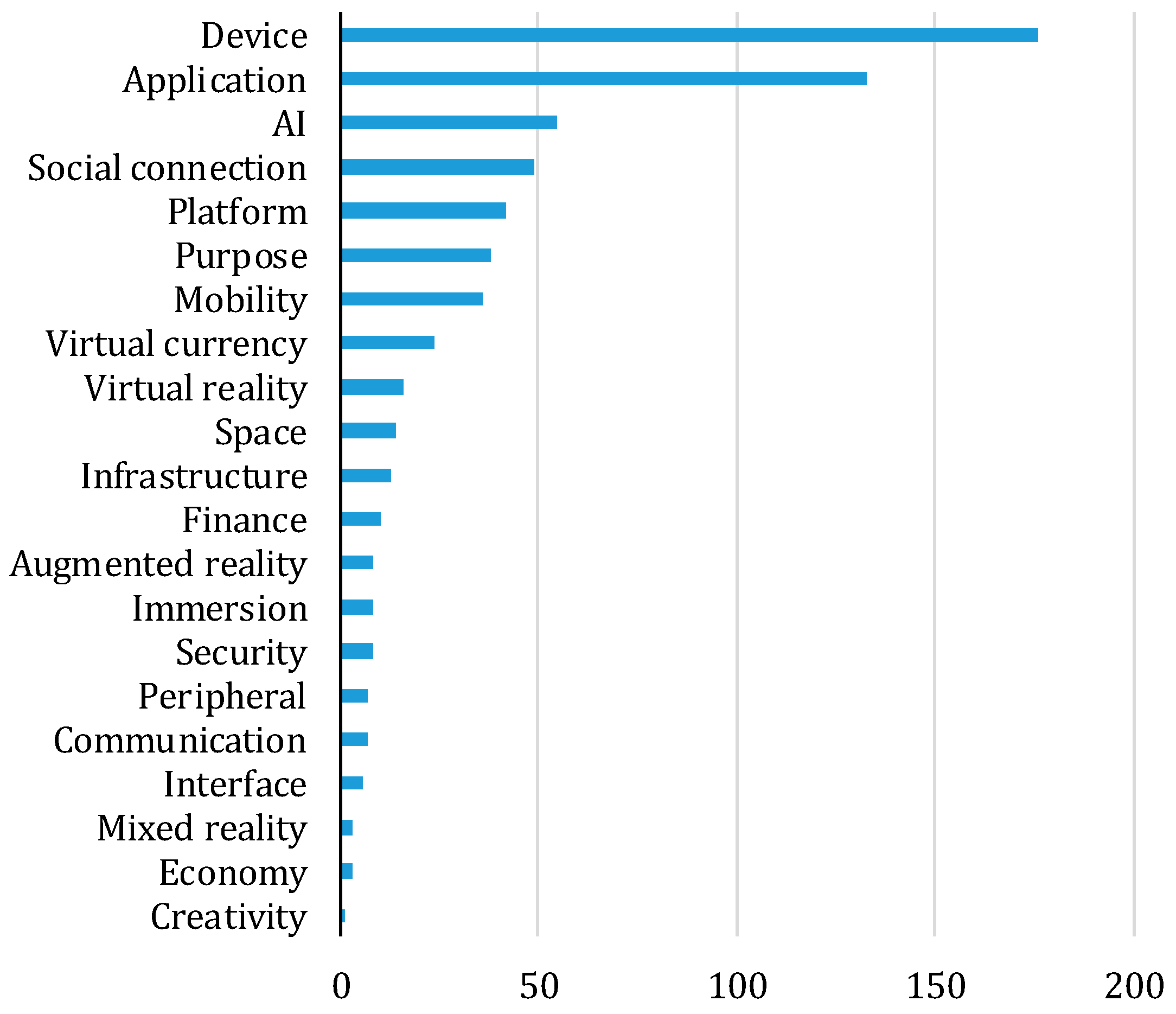
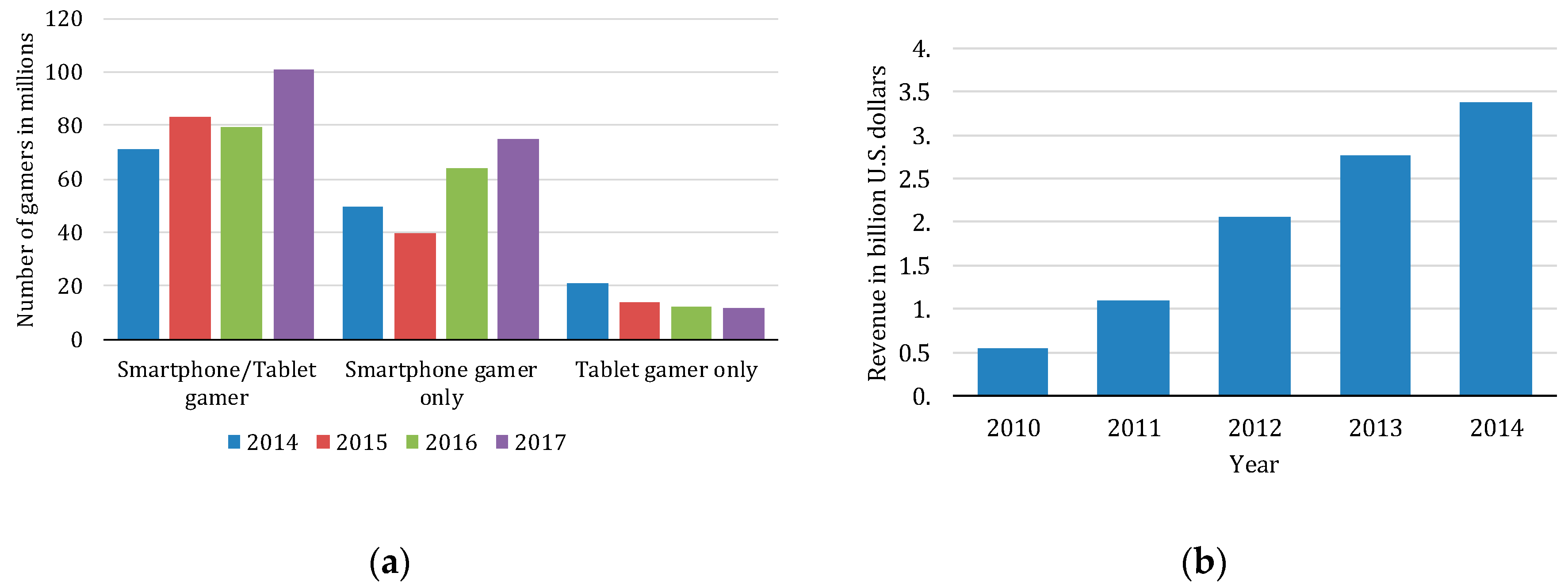
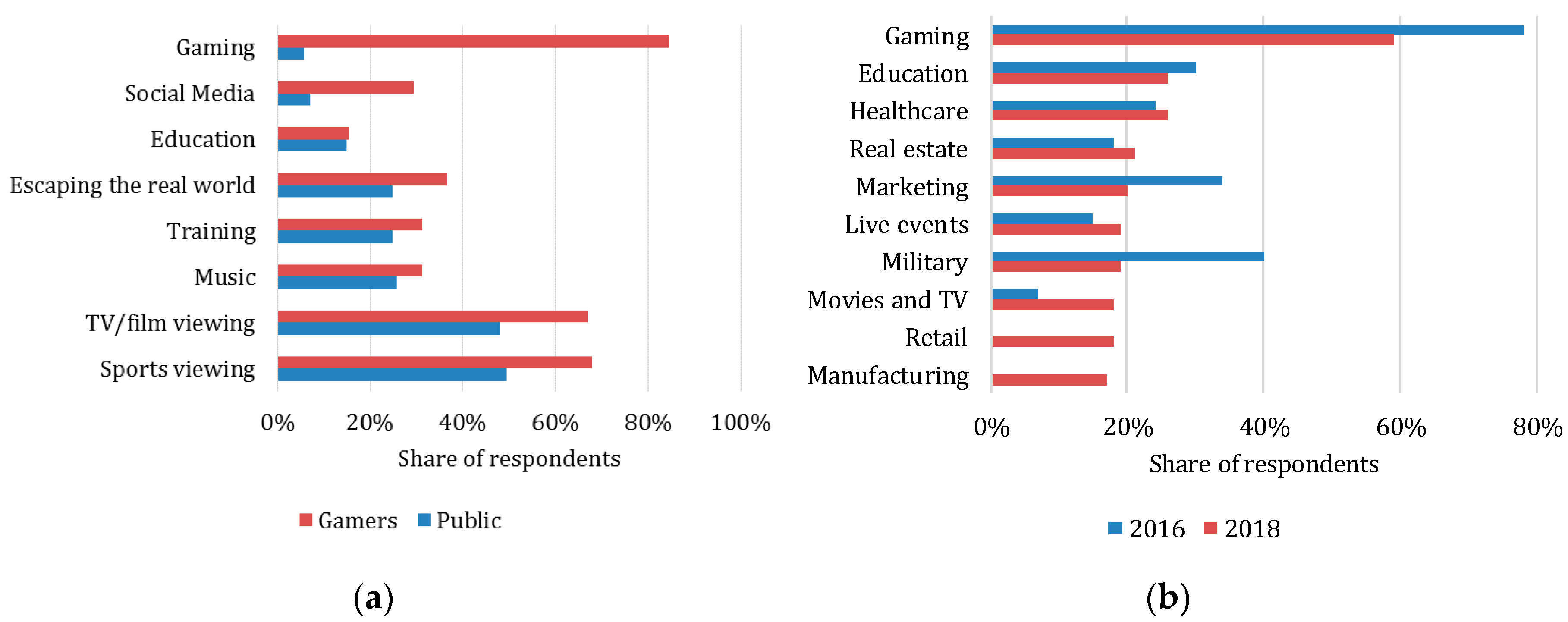
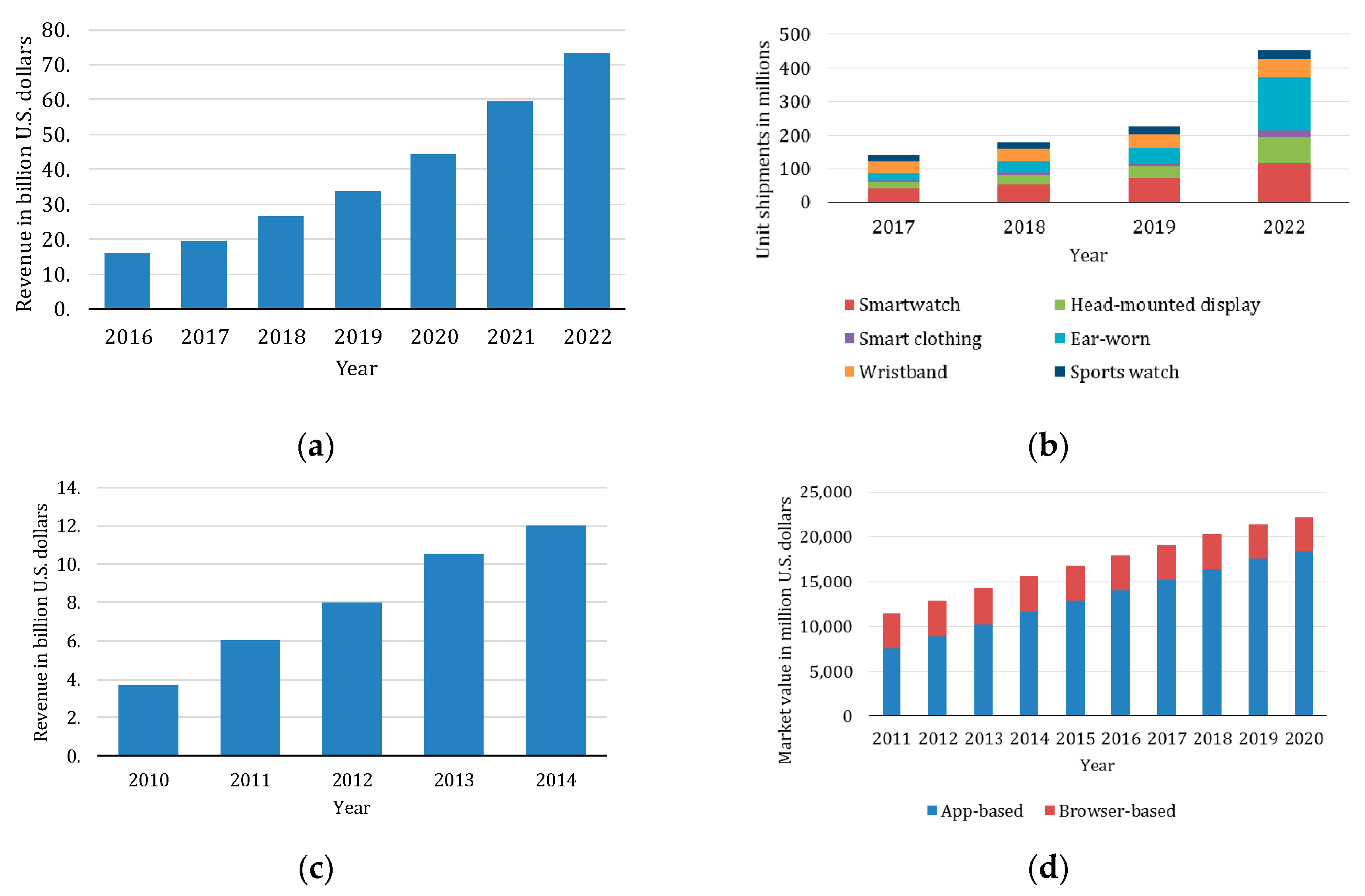
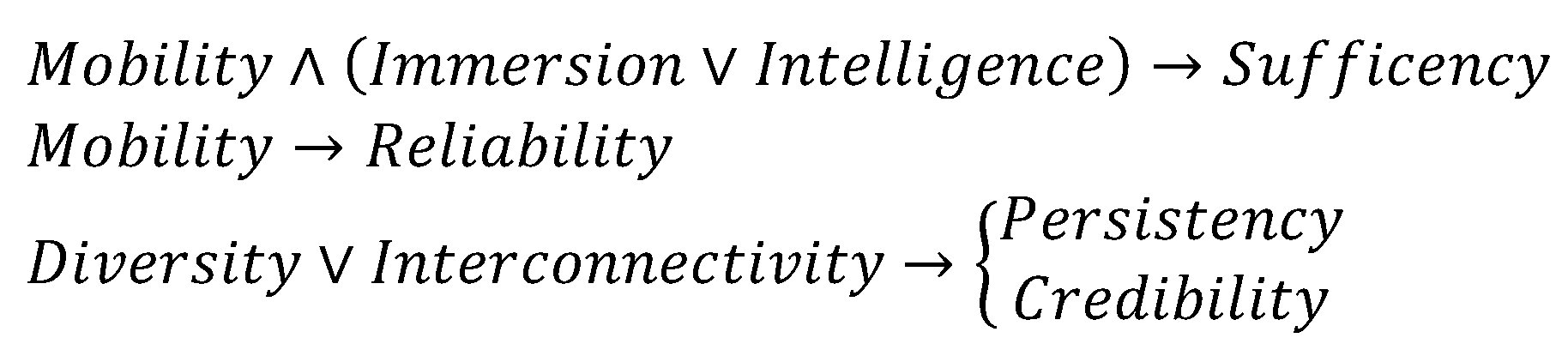

| Requirement | Design Issue | C/S | Hybrid-I | P2P | Hybrid-II |
|---|---|---|---|---|---|
| Sufficiency | Energy Efficiency | Energy trade-off [67] | |||
| QoS/QoE | MAUI [87] | ||||
| Reliability | Reliability | Database replication [88] | Database replication [88] | Pithos [89] | Backup virtual node [90] |
| Persistency | State Persistency | Centralized control [91] | State Action Manager [90] | ||
| Content Persistency | Kad [92] | ||||
| Credibility | Secure Access | Policy-based access control [93] | Blockchain-based access control [94] | ||
| Regulation | Data compliance [95] | N.A. | |||
| Ownership | User representative [96] | ||||
| DRM | License Server [97] | DRMChain [98] | |||
| Content Moderation | Content approval or social accountability [86] | ||||
| Consistency | Causality | Local-lag and timewarp [59] | |||
| Perceptive Consistency | |||||
| Scalability | World Scalability | Cloud gaming [99] | Cloudlet [100] | Red-Black [101] | Cloud resources [90] |
| Hotspot Scalability | KIWANO [102] | Peer-assisted [91] | AOI-cast [103] | Virtual server transfer [90] | |
| Security | Cheating Prevention | Cryptographic measures [104] | |||
| Cheating Detection | Behavior monitoring [105] | IRS [106] | Mutual verification [107] | RACS [108] | |
| Requirement | Feature | C/S | P2P | Hybrid-I | Hybrid-II | Virtual Net |
|---|---|---|---|---|---|---|
| Sufficiency | Lightweight Device Support | Code offload, Cloud gaming | No | Code offload, Cloud gaming | No | Code offload |
| Reliability | Connect Failure Tolerance | No | No | No | No | Replicated Connection |
| Replica consistency | Yes | No guarantee | Yes | No guarantee | Yes | |
| Content persistency | Content lost due to platform failure | Likely | Unlikely | Likely | Unlikely | Unlikely |
| Credibility | Transparency to Compliance | No | Yes | No | Yes | Yes |
| Content Ownership | Separated | User-owned | Separated | User-owned | User-owned | |
| Platform Owner’s Liability for illegal content | Yes | No | Yes | No | No | |
| DRM Violation Traceability | No | Yes | No | Yes | Possible | |
| Scalability | Scalability Cost to Application Provider | High | Low | Moderate | Moderate to low | Moderate to low |
| Cheating-prevention | Client-side Code Tampering | Highly secure | Vulnerable | Highly secure | Vulnerable | Moderately secure |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shen, B.; Tan, W.; Guo, J.; Cai, H.; Wang, B.; Zhuo, S. A Study on Design Requirement Development and Satisfaction for Future Virtual World Systems. Future Internet 2020, 12, 112. https://doi.org/10.3390/fi12070112
Shen B, Tan W, Guo J, Cai H, Wang B, Zhuo S. A Study on Design Requirement Development and Satisfaction for Future Virtual World Systems. Future Internet. 2020; 12(7):112. https://doi.org/10.3390/fi12070112
Chicago/Turabian StyleShen, Bingqing, Weiming Tan, Jingzhi Guo, Hongming Cai, Bin Wang, and Shuaihe Zhuo. 2020. "A Study on Design Requirement Development and Satisfaction for Future Virtual World Systems" Future Internet 12, no. 7: 112. https://doi.org/10.3390/fi12070112
APA StyleShen, B., Tan, W., Guo, J., Cai, H., Wang, B., & Zhuo, S. (2020). A Study on Design Requirement Development and Satisfaction for Future Virtual World Systems. Future Internet, 12(7), 112. https://doi.org/10.3390/fi12070112





