Performance Analysis of a Novel TCP Protocol Algorithm Adapted to Wireless Networks
Abstract
1. Introduction
2. Materials and Methods
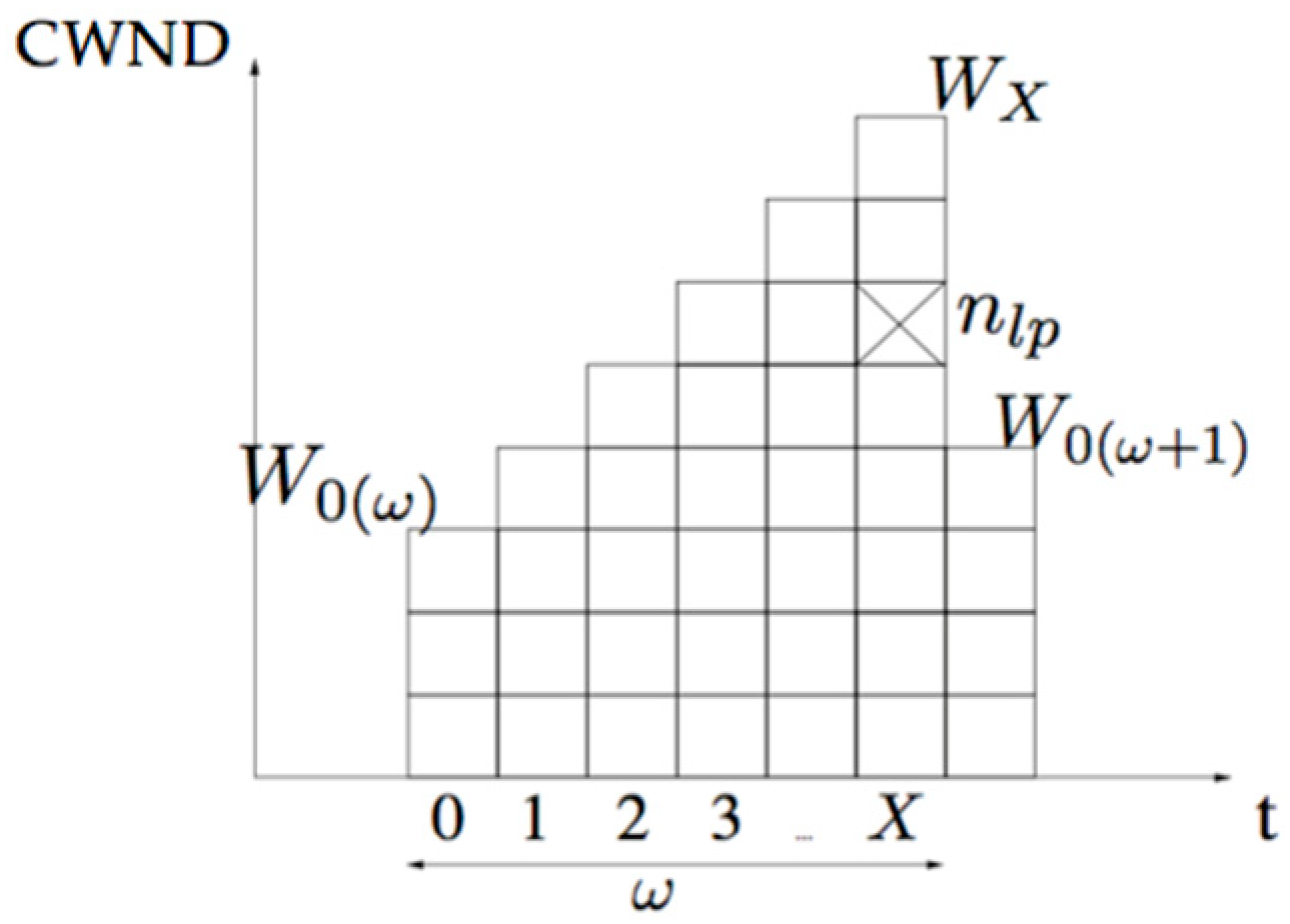
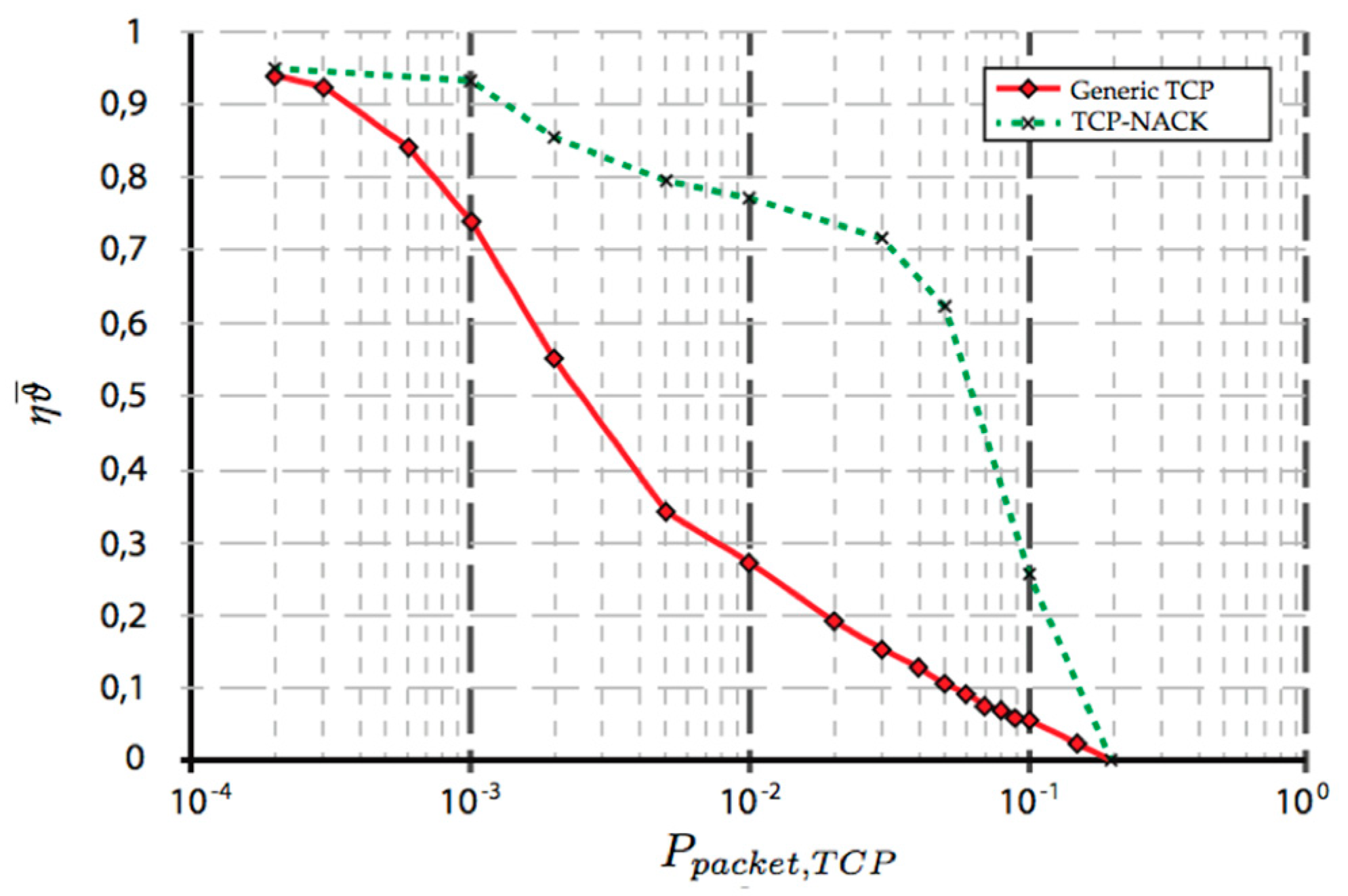
2.1. Mathematical Analysis
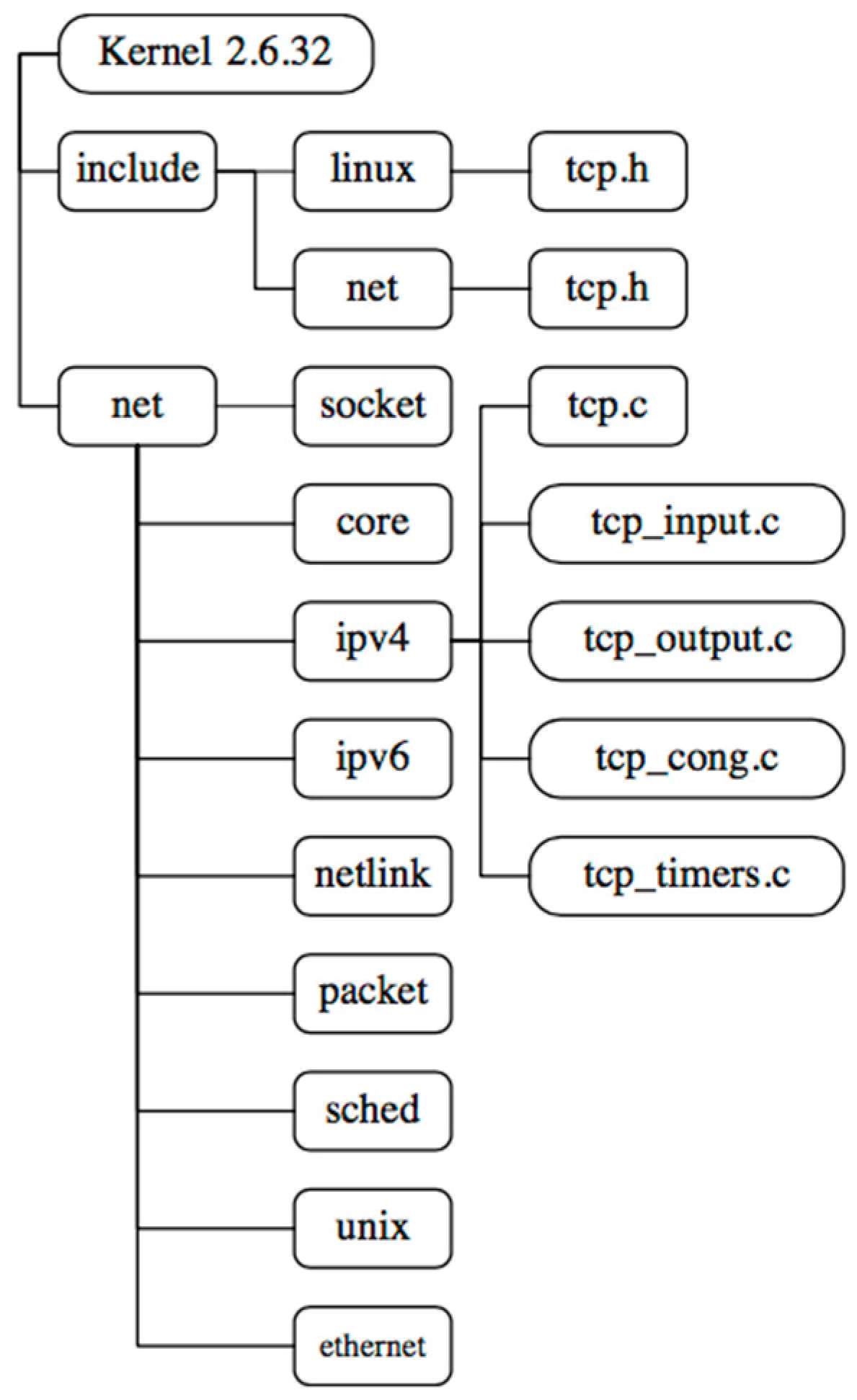
2.2. TCP-NACK Linux Implementation
2.3. TCP Sockets
2.3.1. Data Sending by TCP
- tcp_sendmsg: which copies the user space data to the Linux kernel space, then it is assigned to the “socket buffer” and divided in smaller packets.
- tcp_send_skb: which organizes the data in “socket buffer” for the transmission queue, and decides whether the transmission can take place or not.
- tcp_transmit_skb: which builds the TCP header and sends the packets to the network layer.
2.3.2. Data Reception by TCP
- tcp_v4_rcv: which verifies the packet integrity, it checks if the packet is properly destined, process the transport layer checksum and removes the IP header.
- tcp_v4_do_rcv: which verifies that the received packet has a complete header and checks the current TCP connection state.
- tcp_rcv_established: If the current TCP connection state is “ESTABLISHED”, it processes the received packets and copies the data to the user space. If the packets are error-free, a fast process denominated “fast path” is executed, otherwise a “slow path” process is executed.
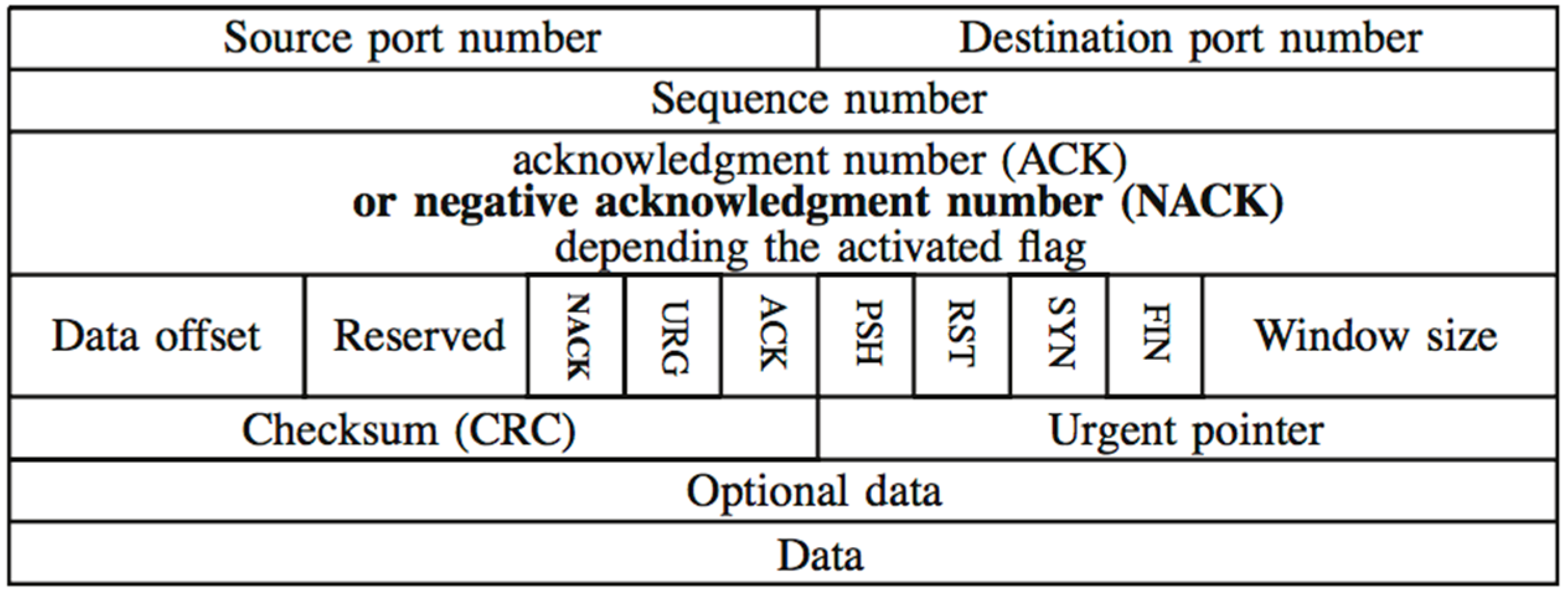
2.3.3. TCP Header Modifications
| Algorithm 1 tcphdr structure modifications for the NACK flag insertion |
| res1 = 4 bits |
| if little or big endian bitfield is used then |
| define nack = 1 bit |
| res1 = res1 - size(nack) |
| end if |
2.3.4. Sending NACK Notifications
- New tcp_send_nack function: This function, declared inside the /include/net/tcp.h file, sends NACK notifica- tions by four steps. First, it checks if the connection was restarted, if this is true, then the NACK notification is annulled. After that, it calls the skb_reserve function, that creates a socket buffer with a memory space of the maximum TCP header size. Then, the tcp_init_nondata_skb function sends the posi- tive NACK flag state and the sequence number to be retransmitted to the control buffer. Finally, the packet is transmitted to the network layer by the tcp_transmit_skb function. Algorithm 2 shows the description of the NACK sending function.
Algorithm 2 tcp_send_nack function algorithm if TCP state == close then return end if skb_reserve(maximum TCP header size) tcp_init_nondata_skb(NACK flag state, sequence number) tcp_transmit_skb() - tcp_transmit_skb modification: If the packet to be transmitted has raised the TCP_FLAG_NACK flag, the TCP confirmation number field must contain the sequence number of the corrupted packet. Algorithm 3 shows this modification.
Algorithm 3tcp_transmit_skb function modification if NACK flag == 1 then TCP header <- sequence number of the corrupted packet else TCP header <- sequence number of the next expected packet end if
2.3.5. Receiving NACK Notifications
3. Results
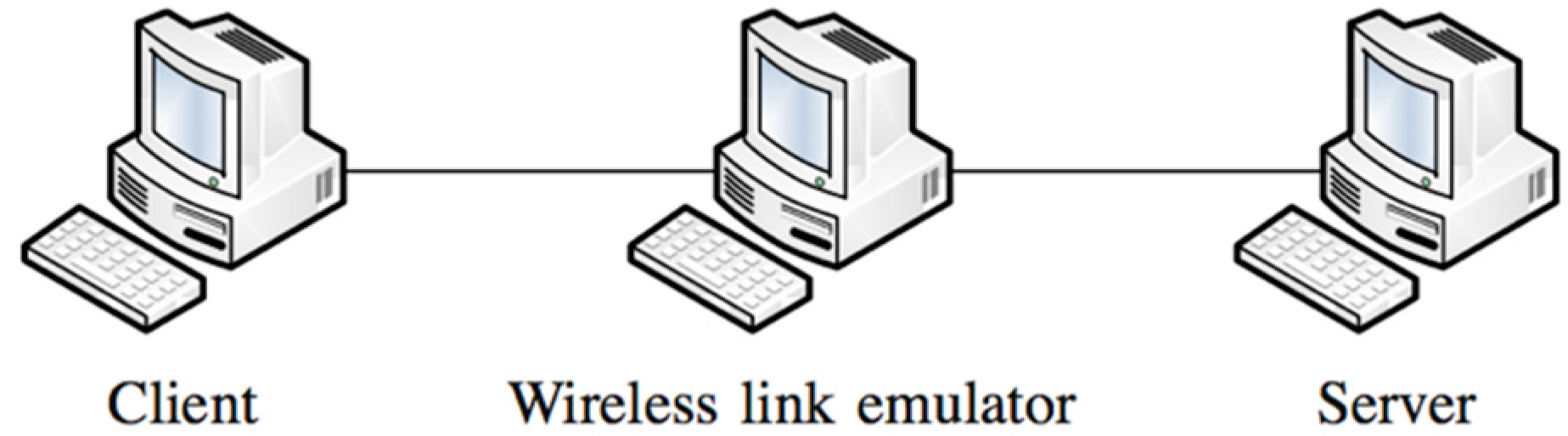
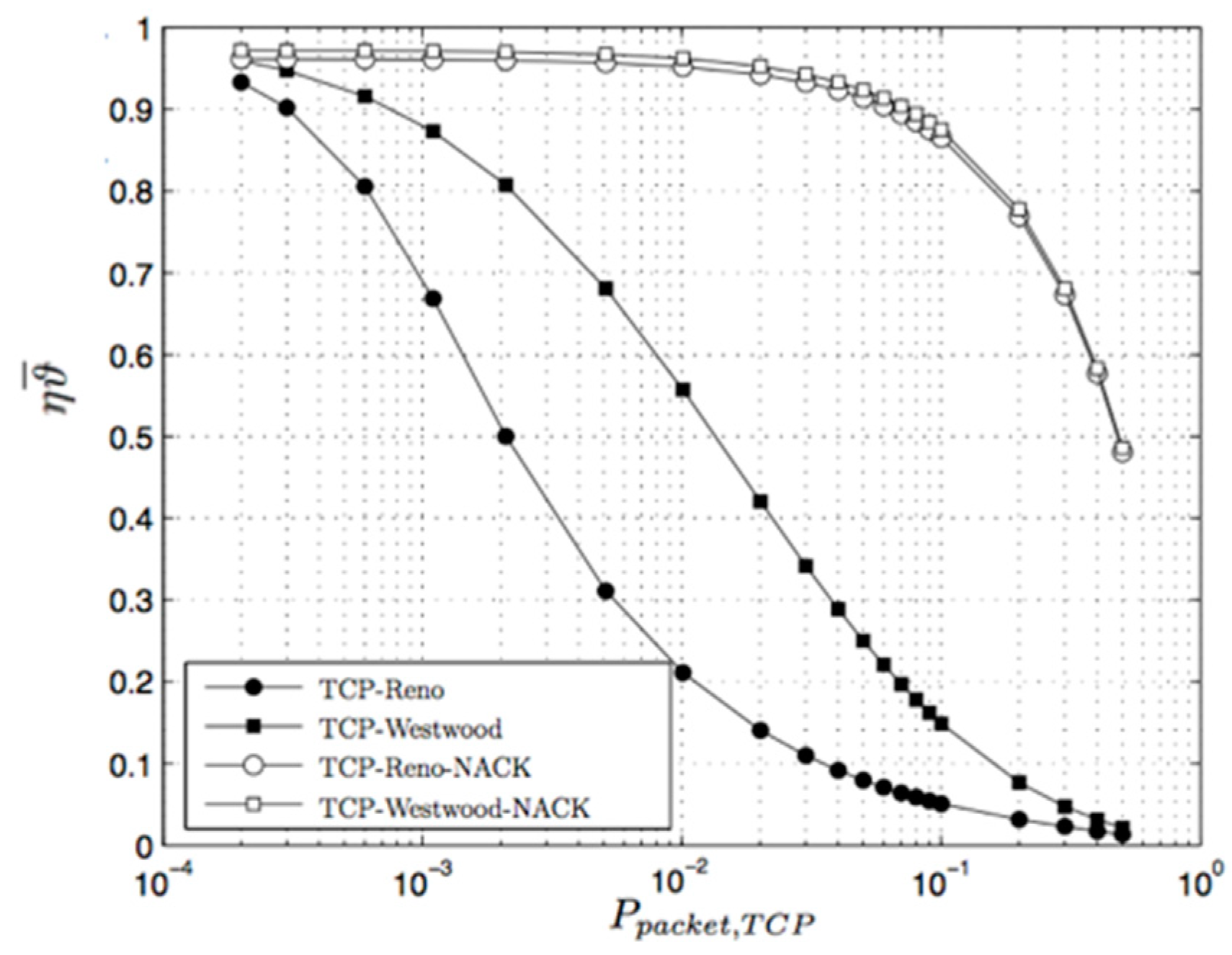
3.1. Wireless Link Emulation
- sudo tc qdisc add dev ethX root handle 1:0 tbf rate Bandwidthkbit
- sudo tc qdisc add dev ethX parent 1:1 handle 10: netem corrupt Y% delay Z
3.1.1. Iperf and Tcpprobe Configuration
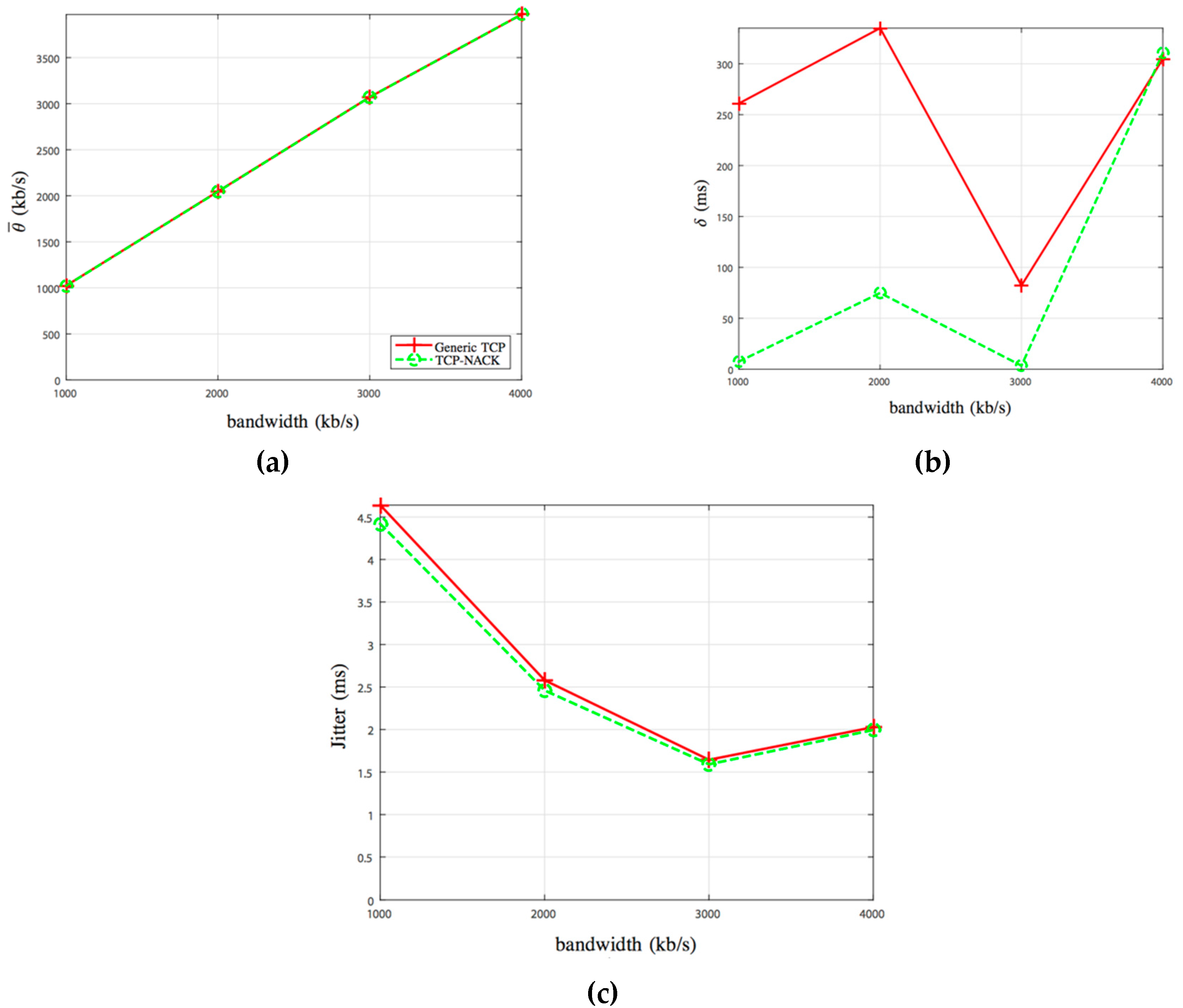
3.1.2. Evaluation
3.1.3. CWND Evaluation
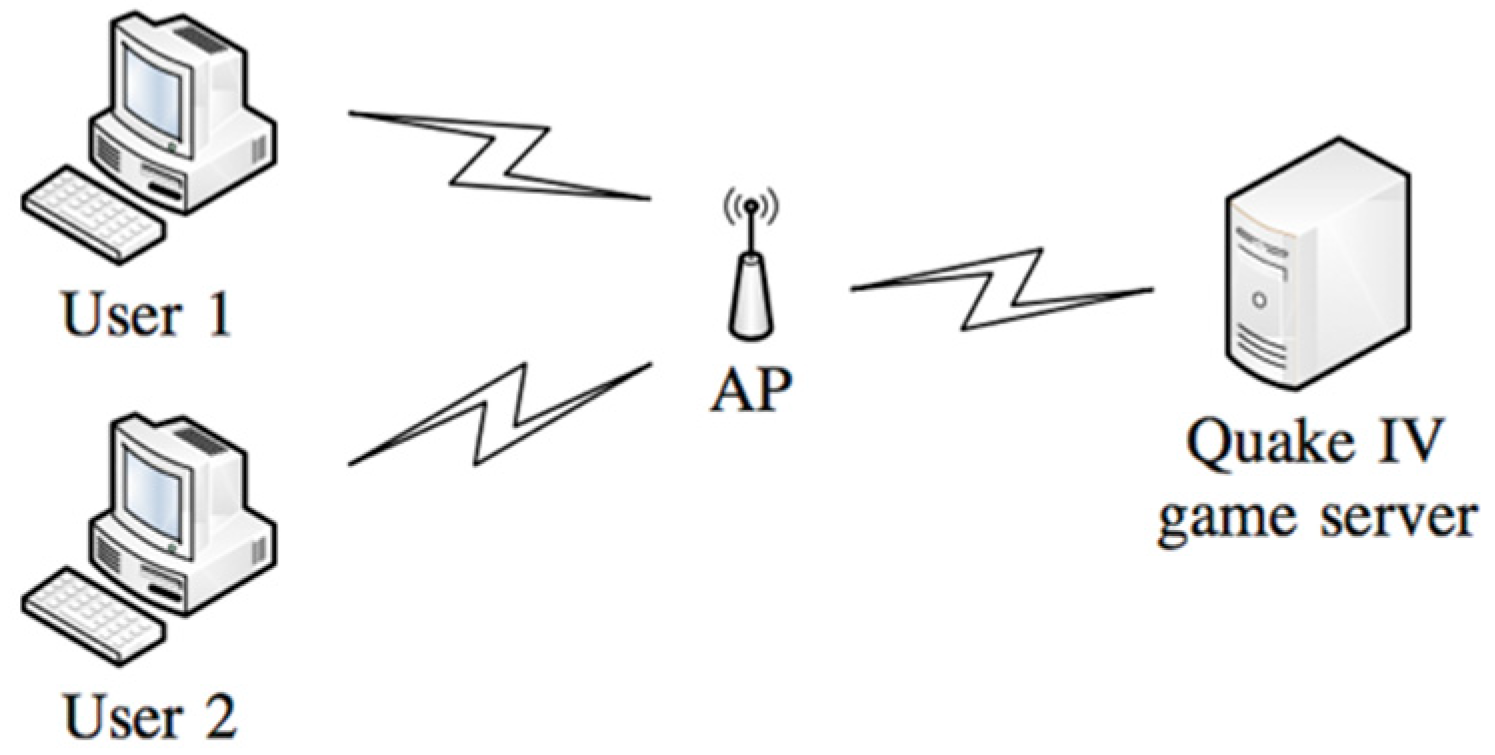
3.2. Short Distance Link Whit a Real-Time Video Game
3.2.1. Server Equipment Configuration
3.2.2. User Equipment Configuration
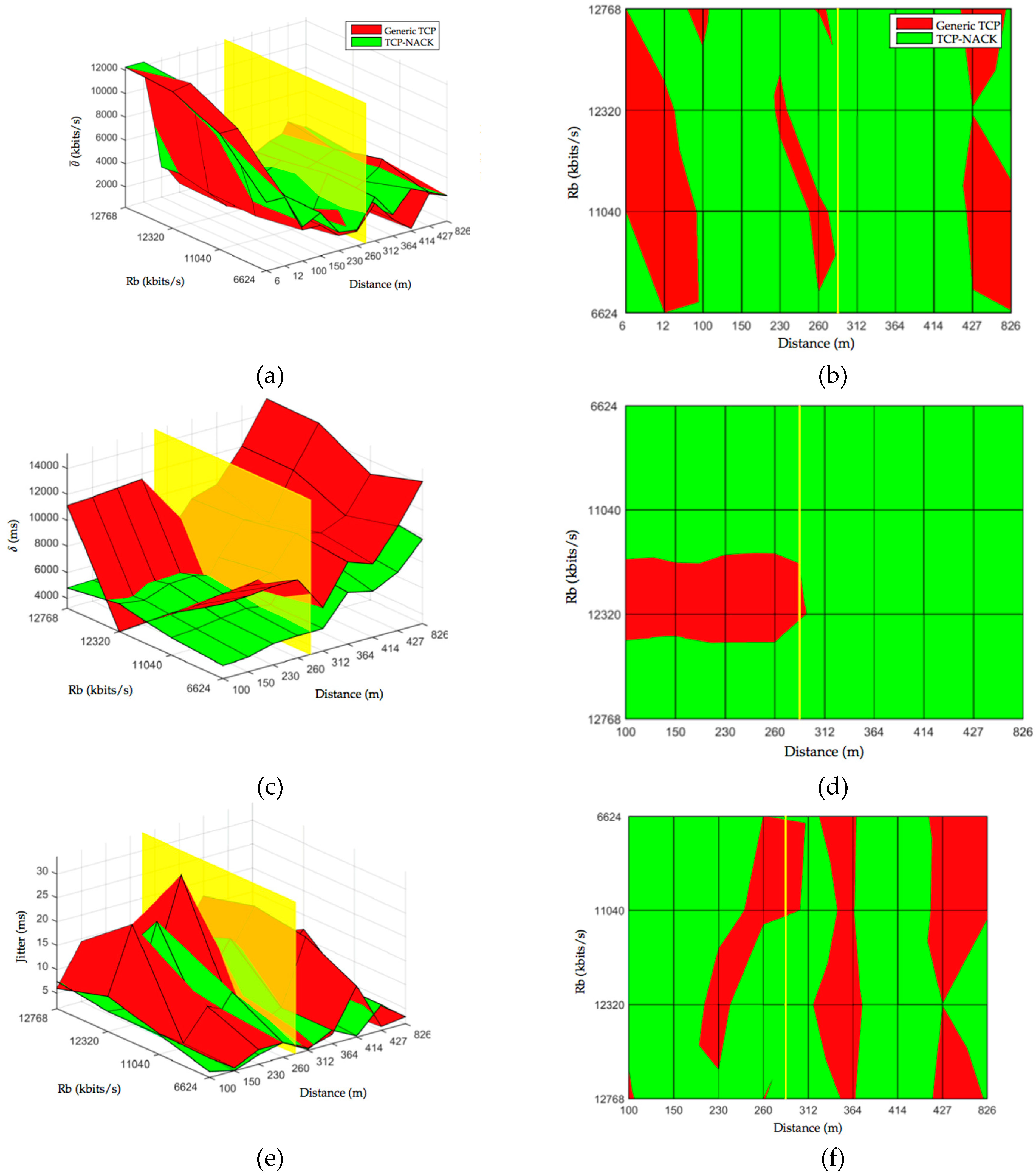
3.2.3. Short-Medium Distance Scenario
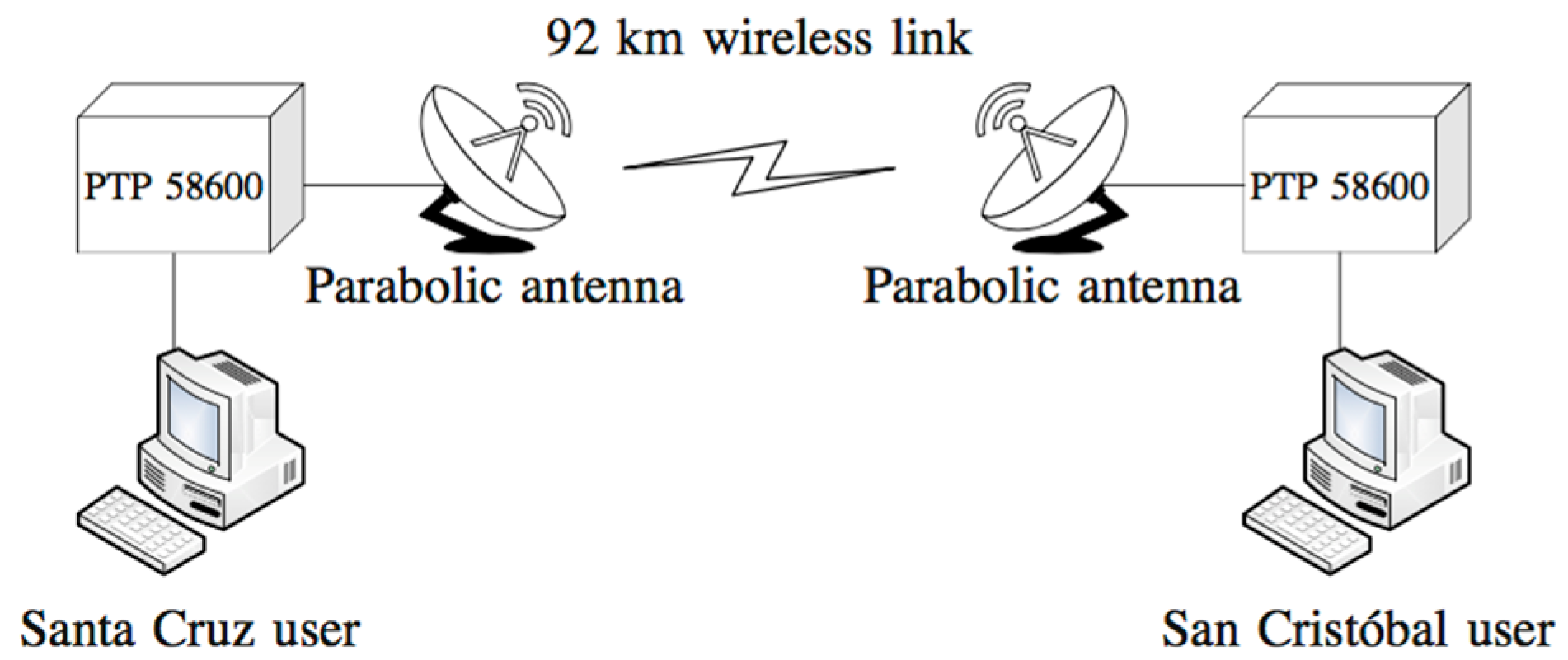
3.3. Long Distance Scenario
4. Discussion
4.1. Results from Mathematical Analysis
4.2. Results from Emulation Experiment
4.3. Results from Indoor Short Distance Experiment
4.4. Results from Outdoor Short-Medium Distance Experiment
4.5. Results from Long Distance Experiment
5. Conclusion and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Xylomenos, G.; Polyzos, G.C. Internet Protocol Performance over Networks with Wireless links. IEEE Netw. 1999, 13, 55–63. [Google Scholar] [CrossRef]
- Postel, J. RFC 793—Transmission Control Protocol. Available online: https://tools.ietf.org/html/rfc793 (accessed on 4 June 2020).
- Allman, M.; Paxson, V.; Ethan, B. TCP Congestion Control. Available online: https://goo.gl/CE5m3V (accessed on 4 June 2020).
- Tian, Y.; Xu, K.; Ansari, N. TCP in wireless environments: Problems and solutions. IEEE Commun. Mag. 2005, 43, S27–S32. [Google Scholar] [CrossRef]
- Zanella, A.; Procissi, G.; Gerla, M.; Sanadidi, M.Y. TCP Westwood: Analytic model and performance evaluation. In Proceedings of the GLOBECOM’01, IEEE Global Telecommunications Conference, San Antonio, TX, USA, 25–29 November 2001; Volume 3, pp. 1703–1707. [Google Scholar]
- Ding, W.; Jamalipour, A. A New Explicit Loss Notification with Acknowledgement for Wireless TCP. In Proceedings of the 12th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, San Diego, CA, USA, 30 September–3 October 2001; Volume 1, pp. B-65–B-69. [Google Scholar]
- Buchholcz, G.; Ziegler, T.; Do, T.V. TCP-ELN: On the protocol aspects and performance of explicit loss notification for TCP over wireless networks. In Proceedings of the First International Conference on Wireless Internet, Budapest, Hungary, 10–15 July 2005; pp. 1–8. [Google Scholar]
- Cui, Y.; Wang, L.; Wang, X.; Wang, Y.; Ren, F.; Xia, S. End-to-end coding for TCP. IEEE Netw. 2016, 30, 68–73. [Google Scholar] [CrossRef]
- Caceres, R.; Iftode, L. Improving the performance of reliable transport protocols in mobile computing environments. IEEE J. Sel. Areas Commun. 1995, 13, 850–857. [Google Scholar] [CrossRef]
- Bakre, A.; Badrinath, B. Implementation and performance evaluation of indirect TCP. IEEE Trans. Comput. 1997, 46, 260–278. [Google Scholar] [CrossRef]
- Parvez, N.; Hossain, E. TCP Prairie: A sender-only TCP modification based on adaptive bandwidth estimation in wired-wireless networks. Comput. Commun. 2005, 28, 246–256. [Google Scholar] [CrossRef]
- Hung, K.L.; Bensaou, B. TCP performance optimization in multi-cell WLANs. Perform. Eval. 2011, 68, 806–824. [Google Scholar] [CrossRef]
- Balakrishnan, H.; Seshan, S.; Amir, E.; Katz, R.H. Improving TCP/IP performance over wireless networks. In Proceedings of the 1st Annual International Conference on Mobile Computing and Networking, Berkeley, CA, USA, 13–15 November 1995; pp. 2–11. [Google Scholar]
- Bhandarkar, S.; Sadry, N.E.; Reddy, A.L.; Vaidya, N.H. TCP-DCR: A Novel Protocol for Tolerating Wireless Channel Errors. IEEE Trans. Mob. Comput. 2005, 4, 517–529. [Google Scholar] [CrossRef]
- Han, K.; Lee, J.Y.; Kim, B.C. Machine-Learning based Loss Discrimination Algorithm for Wireless TCP Congestion Control. In Proceedings of the 2019 International Conference on Electronics, Information, and Communication (ICEIC), Auckland, New Zealand, 22–25 January 2019. [Google Scholar]
- Olmedo, G. Controle de Congestionamento do Protocolo TCP em Sistemas de Comunicação Sem Fio CDMA Usando Estrategia de Detecção Multiusuario, Arranjo de Antenas e Correção de Erro FEC. Ph.D. Thesis, Universidade Estadual de Campinas, Campinas, Brazil, 2008. Available online: https://goo.gl/r8tWtT (accessed on 4 June 2020).
- Herbert, T.F. The Linux TCP/IP Stack: Networking for Embedded Systems; Charles River Media Ed.: Needham Heights, MA, USA, 2004. [Google Scholar]
- Campbell, A.; Coulson, G.; Hutchison, D. A Quality of Service Architecture. ACM SIGCOMM Comput. Commun. Rev. 1994, 24, 6–27. [Google Scholar] [CrossRef]
- Botta, A.; Donato, D.W.; Dainotti, A.; Avallone, S.; Pescapé, A. D-ITG 2.8.1 Manual. 2013, pp. 1–35. Available online: https://goo.gl/UZPJtg (accessed on 4 June 2020).
- Hemminger, S. Network Emulation with NetEm. In Proceedings of the 6th Australia’s National Linux Conference (LCA 2005), Canberra, Australia, 18–23 April 2005; pp. 1–9. Available online: https://goo.gl/XGEHBN (accessed on 4 June 2020).
- Meyers, P. Systems and Methods for Massively Multi-Player Online Role Playing Games. U.S. Patent Application 10/754,069, 22 July 2004. Available online: https://goo.gl/BHydmL (accessed on 4 June 2020).
- Panchana, M.A. Implementación de un Escenario de Juegos en Red a Través de una Comunicación Inalámbrica con Protocolo TCP para Soportar Aplicaciones en Tiempo Real. Univ. las Fuerzas Armadas ESPE, Sangolquí, Ecuador. 2014. Available online: https://goo.gl/QpzyRN (accessed on 4 June 2020).
- Lara-Cueva, R.; Olmedo, G.; Calvopina, K. Performance evaluation of a new wireless TCP algorithm in out-door and in-door environments on WiFi and WiMAX links. In Proceedings of the 2015 CHILEAN Conference on Electrical, Electronics Engineering, Information and Communication Technologies, Santiago, Chile, 28–30 October 2016; pp. 313–318. [Google Scholar]
- Lara-Cueva, R.; Olmedo, G.; Acosta, M.; Sandoval, J. Performance evaluation of the new algorithm of the TCP protocol for a long distance wireless link in the Galapagos Islands. In Proceedings of the 2016 IEEE International Engineering Summit, II Cumbre Internacional de las Ingenierias (IE-Summit), Boca del Rio, Mexico, 2–5 March 2016; pp. 1–5. [Google Scholar]


| Parameter | Value |
|---|---|
| Bandwidth | 5000 kb/s |
| δ | 70 ms |
| Packet error probability | 0.5%, 1% and 5% |
| TCP Entity | Linux Command |
|---|---|
| Emitter (server) | iperf -c IPdirection -t time |
| Receiver (client) | iperf -s |
| Parameters | Data |
|---|---|
| Transmission model Interphase to implement Keys importation | TCP TUN .crt, .key, .ca |
| Receiver (client) | IP Direction |
| Parameters | Data |
|---|---|
| Interface Interphase to implement IP direction | dev tun ca.crt, client.crt, client.key remote 10.0.0.7 port 1194 |
| Compression | TCP |
| Packets/s | Frame Size [Bytes] | Resulting Bandwidth [kb/s] |
|---|---|---|
| 1500 2500 1000 | 512 512 1500 | 6624 11,880 12,320 |
| 1500 | 1024 | 12,768 |
| BER | Generic TCP | TCP-NACK | ||
|---|---|---|---|---|
| (Mb/s) | [%] | (Mb/s) | [%] | |
| 0.5% | 1.53 | 30.6 | 1.79 | 35.8 |
| 1% | 1.27 | 25.4 | 1.46 | 29.2 |
| 5% | 0.52 | 10.4 | 0.74 | 14.8 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Olmedo, G.; Lara-Cueva, R.; Martínez, D.; de Almeida, C. Performance Analysis of a Novel TCP Protocol Algorithm Adapted to Wireless Networks. Future Internet 2020, 12, 101. https://doi.org/10.3390/fi12060101
Olmedo G, Lara-Cueva R, Martínez D, de Almeida C. Performance Analysis of a Novel TCP Protocol Algorithm Adapted to Wireless Networks. Future Internet. 2020; 12(6):101. https://doi.org/10.3390/fi12060101
Chicago/Turabian StyleOlmedo, Gonzalo, Román Lara-Cueva, Diego Martínez, and Celso de Almeida. 2020. "Performance Analysis of a Novel TCP Protocol Algorithm Adapted to Wireless Networks" Future Internet 12, no. 6: 101. https://doi.org/10.3390/fi12060101
APA StyleOlmedo, G., Lara-Cueva, R., Martínez, D., & de Almeida, C. (2020). Performance Analysis of a Novel TCP Protocol Algorithm Adapted to Wireless Networks. Future Internet, 12(6), 101. https://doi.org/10.3390/fi12060101






