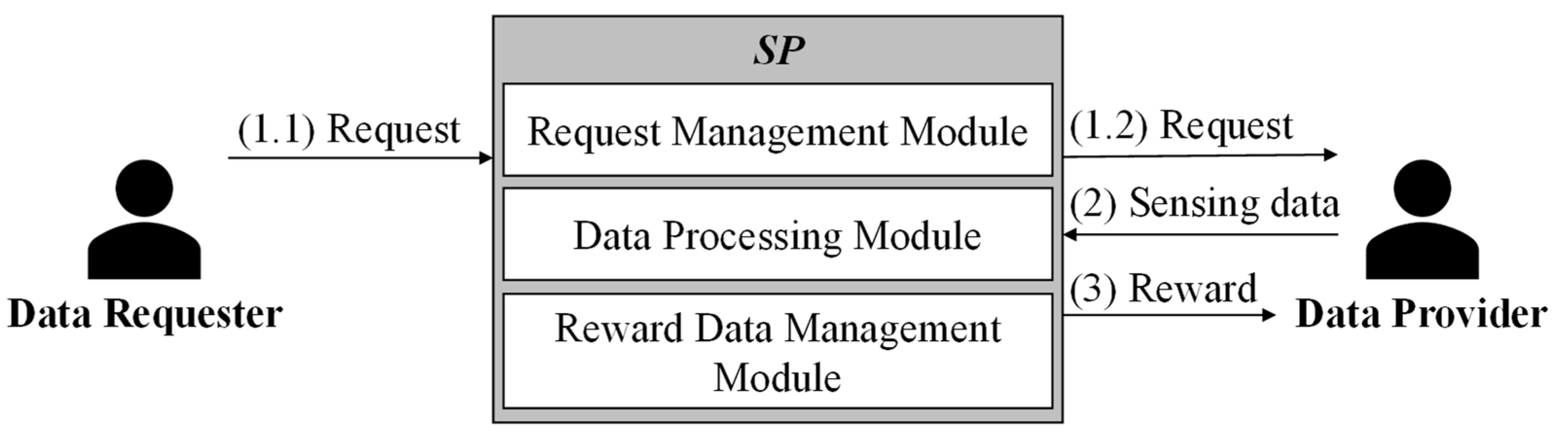
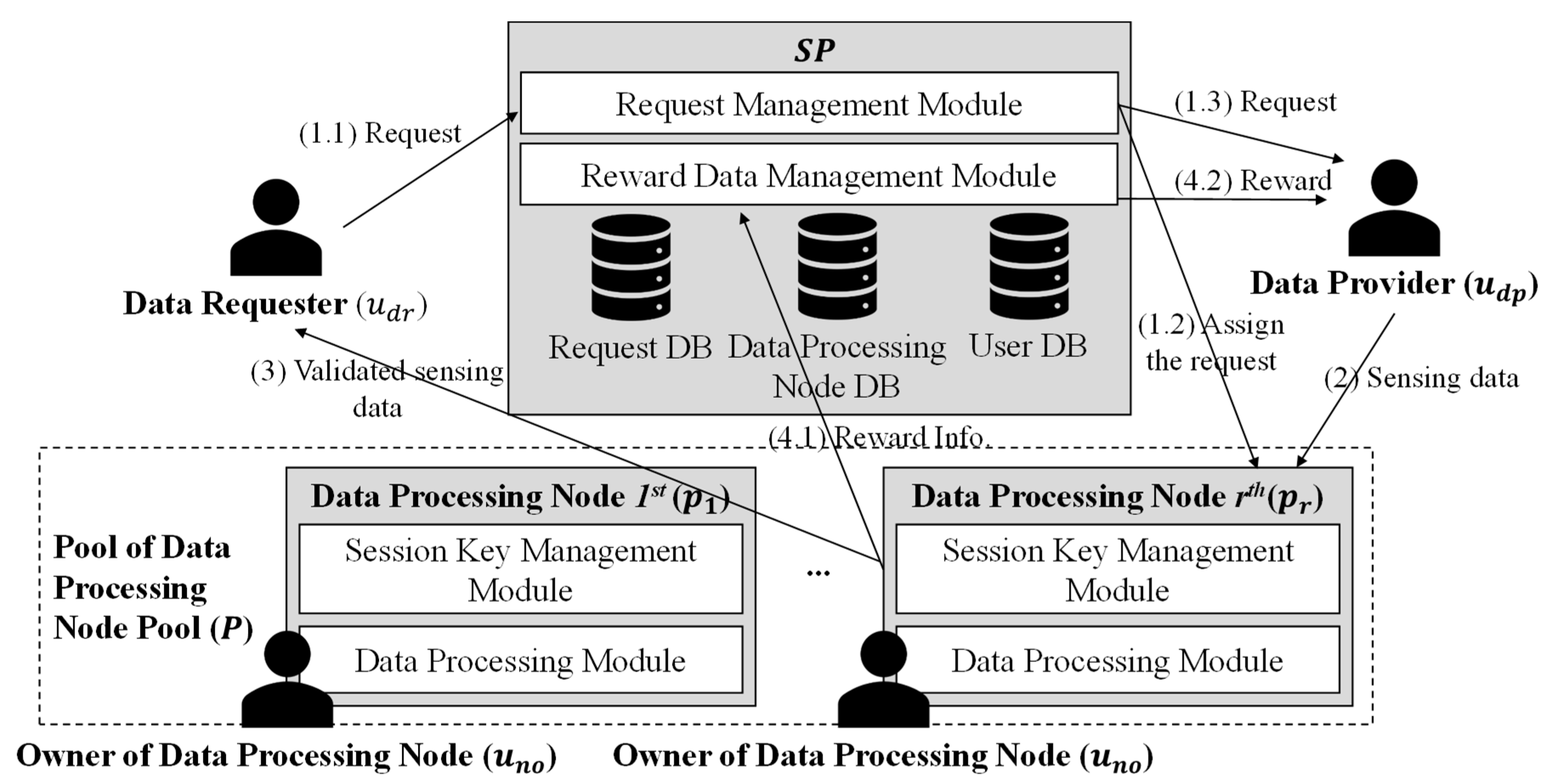
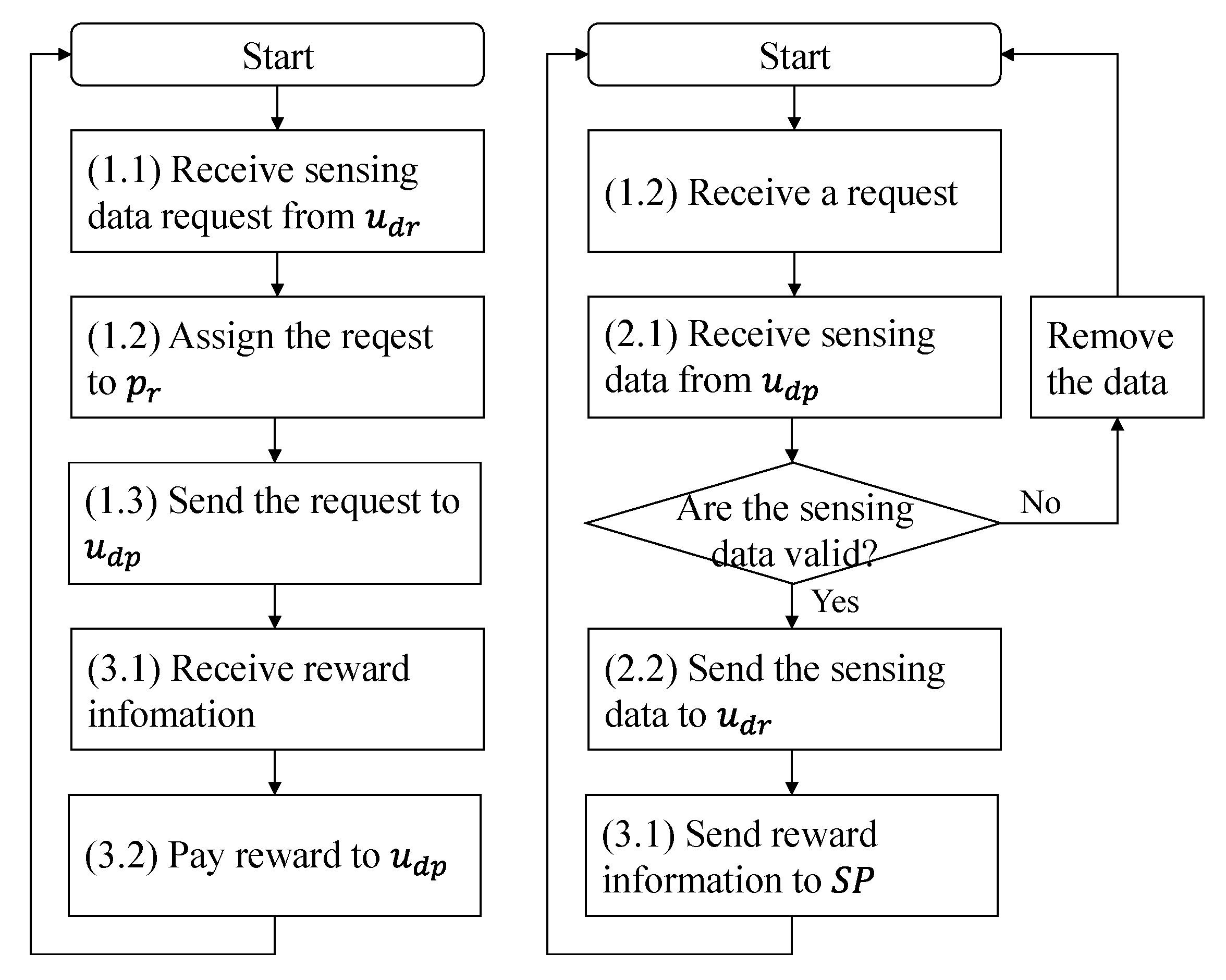
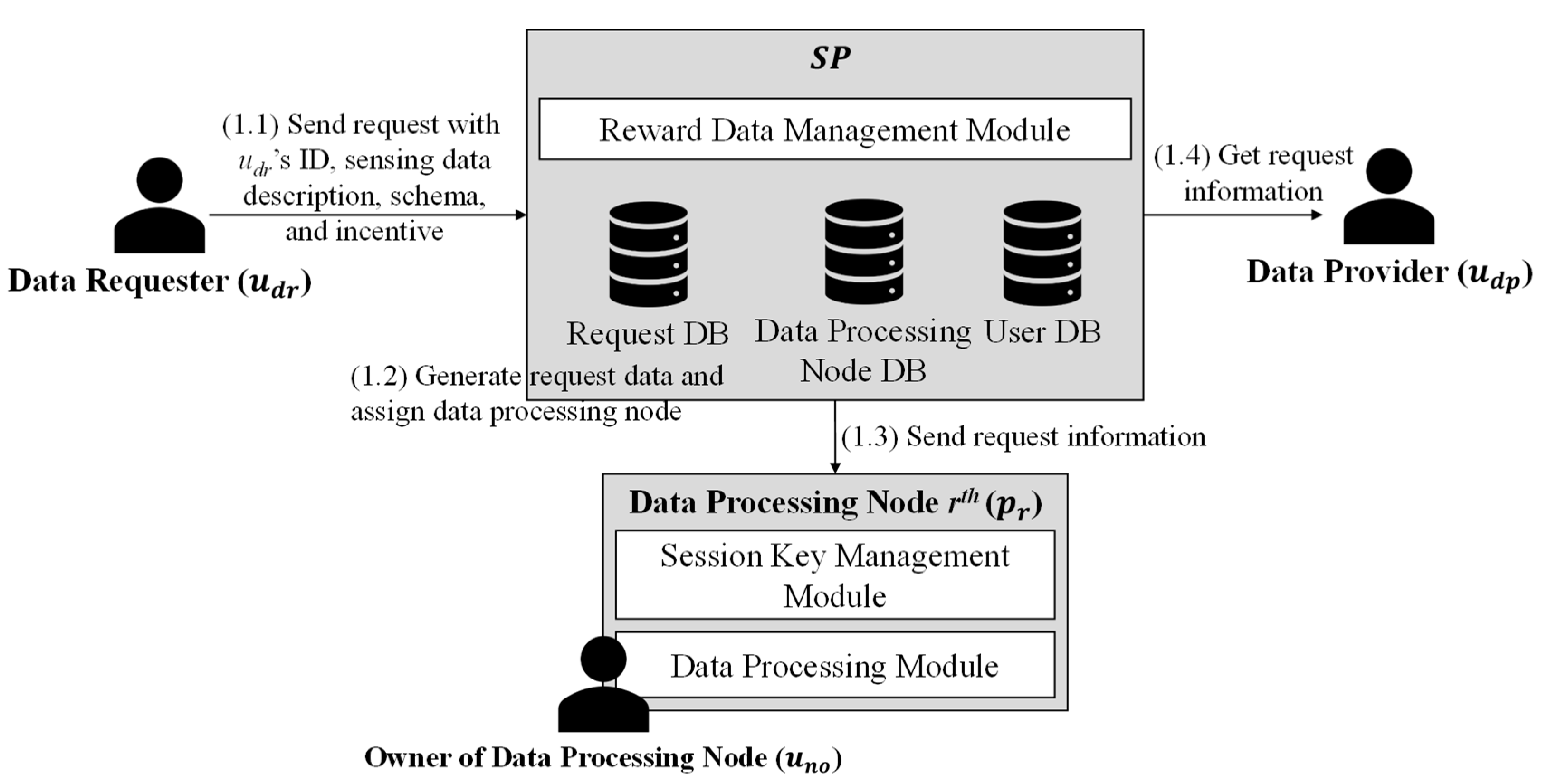
In this section, we discuss crowdsensing, lightweight messaging protocols, the Kaa IoT platform, and related work.
2.4. Related Work
The risk of personal information exposure in crowdsensing services discourages users from providing sensing data. This prevents the crowdsensing service from operating properly. Therefore, personal information protection is essential in crowdsensing services, and related research should be based on the possible service types.
Table 1.
Classification of crowdsensing services.
Table 1.
Classification of crowdsensing services.
| Classification Criteria | Classification |
|---|
| Vulnerability to Privacy Exposure | Resistance to Privacy Exposure |
|---|
| Request assignment entity | Centralized [15] | Distributed [16] |
| Request assignment target | Partial [17] | Overall [18] |
| Participation willingness | Push [19] | Pull [20] |
| Data providing cycle | Periodic [19] | Participatory [15] |
| Data preprocessing | Extensive [21] | Non-extensive [22] |
| Data type | Spatiotemporal [22] | Non-spatiotemporal [23] |
We classify crowdsensing services according to the classification criteria in Reference [
24], and we present threats and countermeasures against personal information disclosure in each type of service.
Table 1 shows the types of crowdsensing services according to various classification criteria. In terms of the request assignment entity, the centralized type is a method in which a central service provider assigns a request to users, and an attacker who compromises the service provider system can access sensitive personal information such as real-time user location. The distributed type is a method via which a user directly participates in a request allocation by a service provider. In contrast to the centralized type, it is difficult for a specific management entity such as a service provider to access sensitive personal information of a user. However, if a service provider or an attacker masquerades as multiple users and participates in a request assignment, it can access sensitive personal information.
In terms of the request assignment target, the partial type is a method in which a request is transmitted only to a user who can provide appropriate sensing data, considering the location and status of the user. Thus, the service provider assigning the request should monitor user location and status in real time. The overall type is a method in which a request is transmitted to all users without considering their location or state, and the service provider does not check sensitive personal information. However, the efficiency of the overall type is low because all requests should be sent to all users.
In terms of participation willingness, the push type requires that the service provider continuously communicates with the user application so that a request is directly sent to the user application. In this process, the service provider can find sensitive personal information such as real-time user location or mobile phone status. The pull type is a method in which the user directly confirms the request information disclosed by the . Therefore, as the and the user application need not communicate continuously, the risk of exposure of personal information is relatively low compared with the push type. All pull-type crowdsensing services are partial type.
In terms of the data providing cycle, the persistent type is a method in which sensing data are periodically received without user interference, and the service provider can access real-time user location and status information. The participation type is a method in which sensing data are provided according to user intention when it is determined that the risk of personal information exposure is low or when such an exposure does not become a serious problem.
Some crowdsensing services require extensive data preprocessing, as, for example, in the case of parking lot pictures for smart parking systems [
21]. If such preprocessing (e.g., removing the license plate number) is not performed by the sensing data provider, there is a risk of privacy exposure (e.g., by identifying the license plate number and revealing the location of the user). However, services that do not require extensive data processing (e.g., environmental data, such as temperature or vehicle CO
2 emissions) [
22] are less vulnerable to privacy exposure. Moreover, crowdsensing services involving spatiotemporal data (e.g., vehicle trajectory) are vulnerable in terms of location or trace privacy [
22]. Closed crowdsensing services irrelevant to spatiotemporal characteristics, such as industrial management [
23], are resistant to privacy exposure.
In conclusion, distributed, overall, pull, participatory, non-extensive-preprocessing, and non-spatiotemporal crowdsensing services are advantageous compared to centralized, partial, push, periodic, extensive-preprocessing, and spatiotemporal services in terms of privacy protection. It is more difficult for attackers to access sensitive personal information in distributed crowdsensing services than in centralized because this information is processed by multiple users. The overall crowdsensing service sends requests to all users instead of checking user location, status, and so on; thus, it does not experience personal information exposure problems caused by user monitoring. The pull crowdsensing service does not experience personal information exposure problems caused by continuous communication because users check requests directly, and no continuous communication with the service provider is required. In the participatory crowdsensing service, users provide sensing data voluntarily. Thus, if personal information exposure occurs, users can respond immediately by, for example, removing this information or discontinuing participation. We consider these architecture and service types in the design of a crowdsensing system that is resistant to privacy exposure.
The authors in Reference [
19] proposed a participatory crowdsensing system using smartphones. The service provider transmits a request to all user applications, and users may respond to the request of their choice. A user can reduce the risk of personal information exposure by providing only selected sensing data to the service provider. However, the central service provider handles all stages of data collection, including request allocation and data processing, so that the personal information of a specific user can be inferred from the data provided by multiple users. In this paper, we propose a system for reducing the risk of personal information exposure in participatory crowdsensing by applying distributed crowdsensing in which users participate in data processing.
The authors in Reference [
25] proposed a partial crowdsensing system for road condition monitoring. The application continuously transmits user location information to the service provider. To obtain road condition information at a certain location, the service provider sends a request only to the user at that location; thus, this method is highly efficient. However, as the
continuously collects the location information of all users, the risk of personal information exposure is high. In the present study, to reduce this in a partial crowdsensing system, we use a pull method whereby requests are not allocated to users by the service provider, but rather a user application selects whether to display a request.
We propose a distributed crowdsensing system of pull, partial, and participation type that exhibits relatively low personal information exposure risk, and we implement it using the Kaa IoT platform, CoAP light messaging protocol, and MongoDB.
On the other hand, the proposed mechanism separates the sensing data processing from the reward payment processing in order to preserve the privacy in the data processing by the service provider in the crowdsensing system. Basically, mechanisms to prevent privacy leakage were studied [
26,
27]. AnonySense [
26] is a privacy preservation mechanism through
k-anonymity against the system (i.e., it is difficult to link any report to a specific user within a set of
k users based on the location or timestamp) and
l-anonymity against the applications (i.e., at least
l reports are combined together before the aggregate is revealed to the application). The
L-diversity system [
27] obfuscates data to satisfy
L-diversity, which means that a set of the same attribute value must have at least
L sensitive information to complement
K-anonymity vulnerability. AnonySense assumes that mobile nodes trust the registration authority (RA), and
L-diversity also assumes the operation of a centralized system. However, internal attack against RA in AnonySense or the centralized
L-diversity system could collapse the privacy preservation. Moreover, it is hard to design the reward management mechanism for the crowdsensing system in the AnonySense and
L-diversity system with
k- anonymity, and the data quality of both systems could go down due to the aggregation of
l reports or the obfuscated data for
L-diversity.
Researches on privacy protection in crowdsensing environments were also performed using various technologies [
28,
29,
30]. The authors in Reference [
28] utilized the fog computing technology and, thus, tried to improve the efficiency of blocking privacy leakage by external attackers through fog nodes installed by service provider. Fog nodes collect sensing data and perform data aggregation However, the service provider system is still able to know the exact location of users, and the compromised fog nodes enable the privacy exposure of sensing data. The authors in Reference [
29] proposed a crowdsensing system capable of protecting personal information by grouping users using blockchain technology. They tried to secure user anonymity by assigning multiple users to one blockchain node. However, due to the characteristics of the blockchain, there would be a delay in data transmission and reward payment because the transaction speed is lower than that of a general network. The authors in Reference [
30] intended to provide anonymity by grouping participants in participant bidding to protect personal information exposed from bids in auction-based crowdsensing systems. Similar to the data processing nodes of our proposed mechanism, the selection of participants through group bidding is passed to the third party and, thus, bid information is protected against the service provider. However, since the third party is fixed and data collected by the service provider is still delivered to the data user, there is a vulnerability to an internal attack on this part. The data processing load is concentrated because the service provider performs data processing. Consequently, many mechanisms were proposed to prevent the exposure of personal information by external attacks. There are not many techniques considering the possibility that a service provider is malicious or compromised. In our proposed mechanism, the service provider does not play any role other than the platform provider, and an external attacker must steal a large number of data processing nodes in order to steal personal information in our proposed system.