A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices
Abstract
1. Introduction
- First, we shift our focus from IoT architecture to IoT devices. Second, the classification of IoT device security technologies has been refined. In addition, we summarize the current research, which is considered from the basic framework of vulnerability analysis, discovering the unknown vulnerability, detecting known vulnerability, and mitigating vulnerability.
- We evaluate the current research of vulnerability analysis on IoT devices. In addition, we analyze in depth the reasons that hinder the development of security technologies and point out the challenges and opportunities.
- We review the technological development context and point out future research directions for related researchers.
2. Background
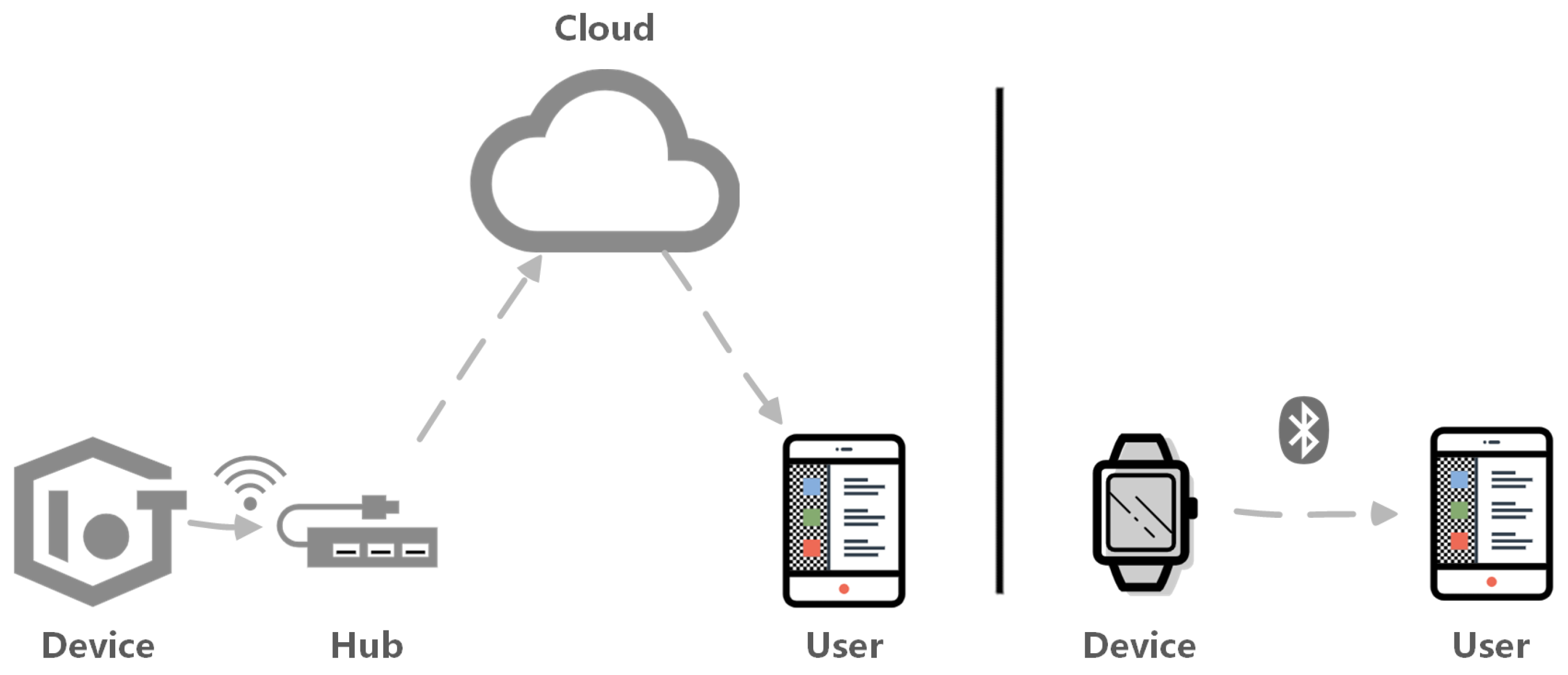
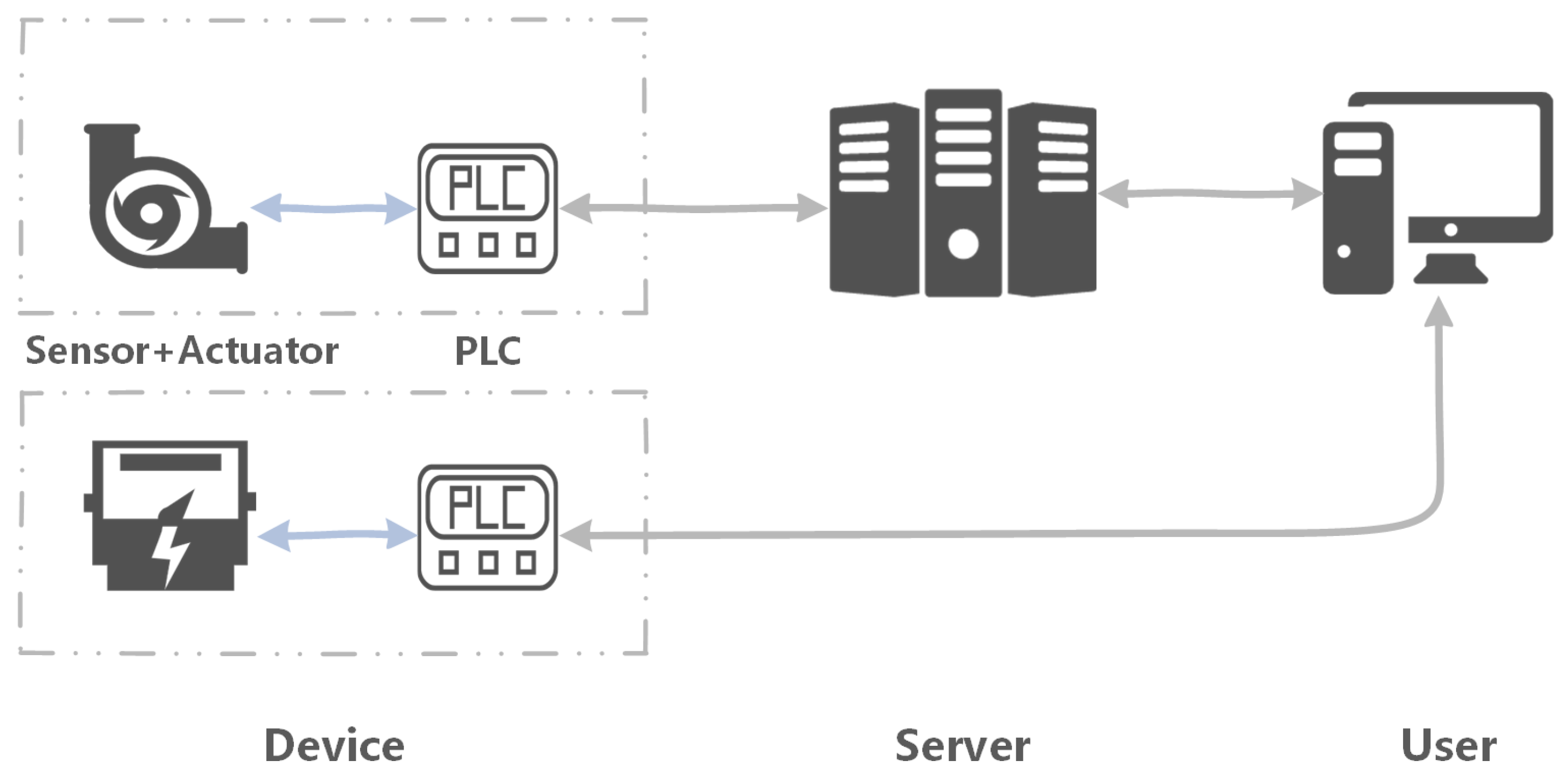
2.1. IoT Architecture
2.2. Device Composition
- (1)
- Hardware parts:
- Logic chip. For complex devices, it has an operating system so that it needs multiple logic chips or CPU. Simple embedded devices may only use a single microprocessor to run programs.
- Memory. Provides the storage space for system and program running, ranging from a few KB to GB.
- Flash storage. The location where the IoT device firmware is stored. Part of the device’s bootloader is also stored in the flash.
- Network module. The difference between IoT devices and traditional embedded devices is that they connect to the Internet. They generally adopt wireless technology to connect to the Internet with the hub, such as access points (APs).
- Serial debug interface. The IoT device often requires means for communicating with the external world for debugging. The serial debug interface could be to send and receive commands to and from the vendor developers. One of the most commonly used interfaces is the universal asynchronous receiver/transmitter (UART).
- (2)
- Software parts:
- BootLoader. It is a small program. Before the IoT device system runs, it initializes the hardware device and loads the firmware to the boot device. Thus, it brings the system’s software and hardware environment to a suitable state to prepare the correct environment.
- Firmware. The firmware includes the operating system, file system, and service programs. Security research on IoT devices generally starts with firmware analysis.
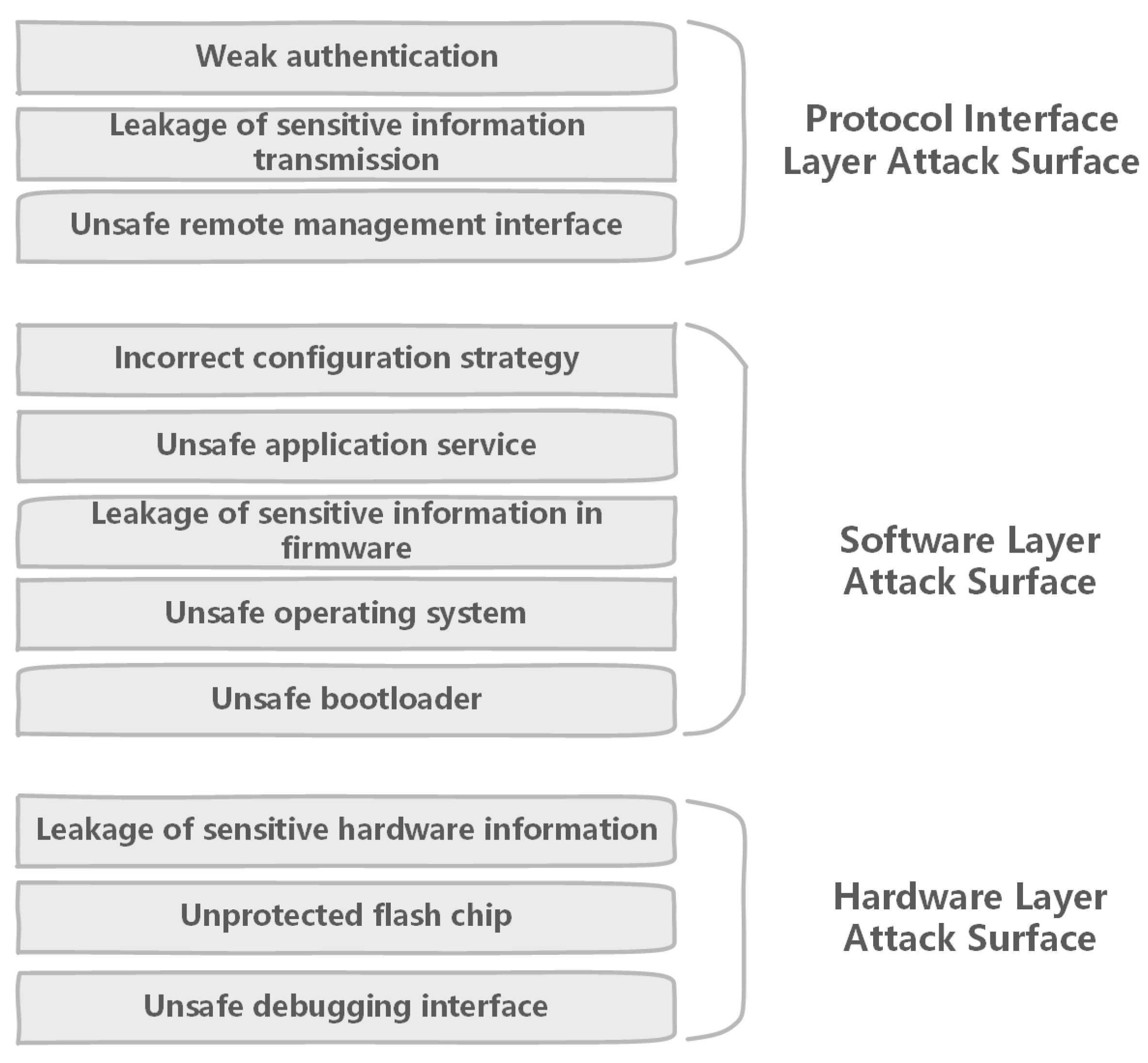
2.3. Attack Surface
2.3.1. Attack Surface on the Hardware Layer
- Unsafe debugging interface. When the IoT device is manufactured, the debug interface such as UART is left on the circuit board to facilitate the repairing. If it is no authentication or weak authentication, attackers can obtain high authority shell to modify or replace the firmware by the interface. The unsafe debugging interface is the first item on an IoT security check-list.
- Unprotected flash chip. Because the flash chip is often used to store firmware, it has become the focus of attention. If the chip is not read-write protected, security researchers can read the firmware for analysis or write modified firmware to bypass authentication of interface access.
2.3.2. Attack Surface on the Software Layer
- Unsafe bootloader. It is often easy to ignore the point of attack because the bootloader is a piece of code that is loaded from the chip after the device running. Its function is to initialize the device and load the firmware. Thus, it has a high risk when problems arise. For example, checkm8 [32], the Boot ROM exploit, has widely been proclaimed as the most important single exploit ever released for iPhone, iPad, Apple TV, and Apple Watch devices.
- Unsafe operating system. Due to the short development cycle and lightweight requirements of the IoT device, the kernel of the operating system is tailored, and the version is usually not up-to-date, which causes various buffer overflow problems such as privilege escalation. In addition, devices use various sensors and communication modules including a large number of drivers in the kernel. For example, the Marvell WiFi chip driver was found multiple vulnerabilities such as CVE-2019-14901, CVE-2019-14897, and CVE-2019-14896 [33]. They cause stack-based or heap-based buffer overflow in the kernel. This is also an important part of the attack surface.
- Leakage of sensitive information in firmware. Local storage of IoT devices generally uses a lightweight storage solution. Developers often ignore security and use plain text or simply encrypting data, which can easily lead to the leakage of sensitive information.
- Unsafe application service. Application services development lacks security standards. Simple and unsafe application code is compiled and used directly to speed up product development. Therefore, it is easy to introduce unknown vulnerabilities. IoT security researchers have discovered a large number of application vulnerabilities developed by manufacturers, including backdoors that are unknown for some reason.
- Incorrect configuration strategy. Services such as ssh, telnet are enabled for easy management of IoT products. There will be configuration problems. Weak authentication policies are configured by default, which allows attackers to easily obtain the shell of device. For example, Telestar Digital GmbH IoT radio devices could be exploited by remote attackers to hijack devices by telnet servers without authentication [34]. The vulnerabilities have been tracked as CVE-2019-13473 [35] and CVE-2019-13474 [36].
2.3.3. Attack Surface on the Protocol Interface Layer
- Unsafe interface of remote management. For portable management, IoT devices use remote management interfaces such as HTTP services, which bring multiple vulnerabilities such as SQL injection, Cross-site Scripting (XSS), and remote execution vulnerability.
- Leakage of sensitive information transmission. The IoT communication protocol will use weak encryption algorithms or even no encryption, which will lead to the leakage of sensitive information. For example Passwords in the Air [40], the WiFi password is transmitted in plain text when the IoT device is connected to the network.
- Weak authentication. Due to security requirements, the management of IoT devices requires authentication binding. However, a new attack surface has emerged. Attackers can bypass authentication, duplicate bind, and obtain other user’s information. The Phantom Device Attack [41] found four specific attack methods on this attack surface.
3. Vulnerability Analysis, Discovery, Detection, and Mitigation
3.1. Research on the Basic Framework of Vulnerability Analysis
3.2. Research on Vulnerability Discovery
3.2.1. Dynamic Analysis Method
3.2.2. Static Analysis Method
3.3. Research on Vulnerability Detection
3.3.1. Network Scanning Method
3.3.2. Similarity Detection Method
3.4. Research on Vulnerability Mitigation
3.4.1. Automated Patch Generation
3.4.2. Access Control Method
4. Discussion
4.1. Evaluation
4.2. Challenges
4.3. Opportunities
5. Research Directions
- AI-based vulnerability discovery and detection technology. Whether function or security, IoT and AI technologies are rapidly converging. The current AI technology is successfully used in vulnerability detection. As research progresses, it will expand to other vulnerability analysis techniques. For example, Generative Adversarial Networks (GANs) [114] have been applied in abnormal detection of IoT system behavior [115]. In the future, GANs may have a potential application in IoT vulnerability discovery because they may learn different attack scenarios to generate samples similar to a zero-day attack and provide algorithms with a set of samples beyond the existing attacks [16].
- Large-scale vulnerability analysis techniques. Complexity and heterogeneity of IoT devices hinder automation and large-scale analysis research in Section 4.2. However, this demand has been urgent in the IoT security industry. Security researchers need a cross-platform approach to overcome this problem, which is a long-term research direction.
- Automated vulnerability exploiting. To exploit the vulnerability in IoT devices and protect the device from intrusion, we need to generate PoC in an automated way. It helps to understand the hazards and causes of vulnerabilities better. With the development of the IoT field, the automation attack and defense will also become a hotspot.
- Vulnerability analysis based on a peripheral system. Through the above challenges, we found that it is aggravatingly difficult to analyze devices by static and dynamic methods directly. IoT devices are becoming more interactive. Not only will there be more and more vulnerabilities in combination with peripheral systems, but also study on peripheral system analysis methods will increase.
- Automatic generation patch of multi-platform on binary code. For some IoT vendors’ closed-source and security inaction, device firmware can not be patched in time. To this end, we need an automated repair method for cross-platform binary code vulnerabilities. The automated patch generation on the binary code level requires fully understanding the formation mechanism and the elimination condition. There will be thousands of security vulnerability templates if we rely entirely on expert domain knowledge. Thus, it is difficult to achieve a scaled and feasible solution. At the same time, the variety of operating systems and hardware architecture brings technical challenges. It is a long-term goal of the whole security field to solve the problem of the automatic generation of multi-platform binary code patches.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lueth, K.L. State of the IoT 2018: Number of IoT Devices Now at 7B—Market Accelerating. Available online: https://iot-analytics.com/state-of-the-iot-update-q1-q2-2018-number-of-iot-devices-now-7b/ (accessed on 6 December 2019).
- Rawlinson, K. Internet of Things Research Study. Available online: https://www8.hp.com/us/en/hp-news/press-release.html?id=1744676 (accessed on 6 December 2019).
- Wikipedia. Mirai(malware). Available online: https://en.wikipedia.org/wiki/Mirai_(malware) (accessed on 6 December 2019).
- Trevor, H. Internet of Things (IoT) History. Available online: https://www.postscapes.com/iot-history/ (accessed on 6 December 2019).
- Gan, G.; Lu, Z.; Jiang, J. Internet of things security analysis. In Proceedings of the International Conference on Internet Technology and Applications, Wuhan, China, 16–18 August 2011. [Google Scholar]
- Suo, H.; Wan, J.; Zou, C.; Liu, J. Security in the internet of things: A review. In Proceedings of the International Conference on Computer Science and Electronics Engineering, Hangzhou, China, 23–25 March 2012. [Google Scholar]
- Zhao, K.; Ge, L. A survey on the internet of things security. In Proceedings of the 2013 Ninth International Conference on Computational Intelligence and Security, Leshan, China, 14–15 December 2013. [Google Scholar]
- Pescatore, J.; Shpantzer, G. Securing the Internet of Things Survey; SANS Institute: Bethesda, MD, USA, 2014; pp. 1–22. [Google Scholar]
- Balte, A.; Kashid, A.; Patil, B. Security issues in Internet of things (IoT): A survey. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2018, 5, 450–455. [Google Scholar]
- Ngu, A.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, Q.Z. IoT middleware: A survey on issues and enabling technologies. IEEE Int. Things J. 2016, 4, 1–20. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in Internet-of-Things. IEEE Int. Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Net. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Zhang, Z.K.; Cho, M.C.Y.; Wang, C.W.; Hsu, C.W.; Chen, C.K.; Shieh, S. IoT security: Ongoing challenges and research opportunities. In Proceedings of the 7th IEEE International Conference on Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014. [Google Scholar]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015. [Google Scholar]
- Fernandes, E.; Rahmati, A.; Eykholt, K.; Prakash, A. Internet of things security research: A rehash of old ideas or new intellectual challenges. IEEE Secur. Priv. 2017, 15, 79–84. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.; Du, X.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. arXiv 2018, arXiv:1807.11023. Available online: https://arxiv.org/abs/1807.11023 (accessed on 6 December 2019).
- Alrawi, O.; Lever, C.; Antonakakis, M.; Monrose, F. Sok: Security evaluation of home-based iot deployments. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019. [Google Scholar]
- Xie, W.; Jiang, Y.; Tang, Y.; Ding, N.; Gao, Y. Vulnerability detection in iot firmware: A survey. In Proceedings of the IEEE 23rd International Conference on Parallel and Distributed Systems (ICPADS), Shenzhen, China, 15–17 December 2017. [Google Scholar]
- Zheng, Y.; Wen, H.; Cheng, K.; Song, Z.W.; Zhu, H.S.; Sun, L.M. A Survey of IoT Device Vulnerability Mining Techniques. J. Cyber Secur. 2019, 4, 61–75. [Google Scholar] [CrossRef]
- Samsung. Samsung SmartThings. Available online: https://www.smartthings.com/ (accessed on 6 December 2019).
- Google. Google Weave Project. Available online: https://developers.google.com/weave/ (accessed on 6 December 2019).
- Apple Inc. Apple HomeKit. Available online: http://www.apple.com/ios/home/ (accessed on 6 December 2019).
- Home, A. Home Assistant. Available online: https://www.home-assistant.io (accessed on 6 December 2019).
- Mi Inc. IoT Developer Platform. Available online: https://iot.mi.com/ (accessed on 6 December 2019).
- WiFi, A. WiFi. Available online: https://www.wi-fi.org/ (accessed on 6 December 2019).
- Zigbee, A. Zigbee. Available online: https://zigbee.org/ (accessed on 6 December 2019).
- Bluetooth Technology Website. Available online: https://www.bluetooth.com/ (accessed on 6 December 2019).
- Liu, X.; Zhou, Z.; Diao, W.; Li, Z.; Hang, K. When good becomes evil: Keystroke inference with smartwatch. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015. [Google Scholar]
- Das, A.; Borisov, N.; Caesar, M. Do you hear what i hear?: Fingerprinting smart devices through embedded acoustic components. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014. [Google Scholar]
- Vasyltsov, I.; Lee, S. Entropy extraction from bio-signals in healthcare IoT. In Proceedings of the 1st ACM Workshop on IoT Privacy, Trust, and Security, Singapore, 14 April 2015. [Google Scholar]
- McCann, D.; Eder, K.; Oswald, E. Characterising and comparing the energy consumption of side channel attack countermeasures and lightweight cryptography on embedded device. In Proceedings of the International Workshop on Secure Internet of Things (SIoT), Vienna, Austria, 21–25 September 2015. [Google Scholar]
- Stokes, P.; SentinelOne. Checkm8: 5 Things You Should Know about the New Ios Boot Rom Exploit. Available online: https://www.sentinelone.com/blog/checkm8-5-things-you-should-know-new-ios-boot-rom-exploit/ (accessed on 6 December 2019).
- MITRE Corp. Marvell WiFi. Available online: https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=+Marvell+WiFi (accessed on 6 December 2019).
- Paganini, P. Million of Telestar Digital GmbH IoT Radio Devices Can Be Remotely Hacked. Available online: https://securityaffairs.co/wordpress/91069/hacking/telestar-iot-radio-devices-hack.html (accessed on 6 December 2019).
- MITRE Corp. CVE-2019-13473. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-13473 (accessed on 6 December 2019).
- MITRE Corp. CVE-2019-13474. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-13474 (accessed on 6 December 2019).
- Costa Gondim, J.J.; de Oliveira Albuquerque, R.; Clayton Alves Nascimento, A.; García Villalba, L.J.; Kim, T.H. A methodological approach for assessing amplified reflection distributed denial of service on the internet of things. Sensors 2016, 16, 1855. [Google Scholar] [CrossRef] [PubMed]
- Wikipedia. Constrained Application Protocol. Available online: https://en.wikipedia.org/wiki/Constrained_Application_Protocol (accessed on 6 December 2019).
- UPnP Corp. UPnP Device Architecture 1.0. Available online: http://www.upnp.org/specs/arch/UPnP-arch-DeviceArchitecture-v1.0-20080424.pdf (accessed on 6 December 2019).
- Li, C.; Cai, Q.; Li, J.; Liu, H.; Zhang, Y.; Gu, D.; Yu, Y. Passwords in the Air: Harvesting Wi-Fi Credentials from SmartCfg Provisioning. In Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks, Stockholm, Sweden, 18–20 June 2018. [Google Scholar]
- Zhou, W.; Jia, Y.; Yao, Y.; Zhu, L.; Guan, L.; Mao, Y.; Zhang, Y. Phantom Device Attack: Uncovering the Security Implications of the Interactions among Devices, IoT Cloud, and Mobile Apps. arXiv 2018, arXiv:1811.03241. [Google Scholar]
- Vasile, S.; Oswald, D.; Chothia, T. Breaking All the Things—A Systematic Survey of Firmware Extraction Techniques for IoT Devices. In Proceedings of the International Conference on Smart Card Research and Advanced Applications, Montpellier, France, 12–14 November 2018. [Google Scholar]
- Zaddach, J.; Bruno, L.; Francillon, A.; Balzarotti, D. AVATAR: A Framework to Support Dynamic Security Analysis of Embedded Systems’ Firmwares. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Kammerstetter, M.; Platzer, C.; Kastner, W. Prospect: Peripheral proxying supported embedded code testing. In Proceedings of the 9th ACM Symposium on Information, Computer and Communications Security, Kyoto, Japan, 3–6 June 2014. [Google Scholar]
- Koscher, K.; Kohno, T.; Molnar, D. SURROGATES: Enabling Near-Real-Time Dynamic Analyses of Embedded Systems. In Proceedings of the 9th USENIX Workshop on Offensive Technologies (WOOT 15), Washington, DC, USA, 10–11 August 2015. [Google Scholar]
- Muench, M.; Nisi, D.; Francillon, A.; Balzarotti, D. Avatar 2: A Multi-target Orchestration Platform. In Proceedings of the Workshop on Binary Analysis Research (colocated with NDSS Symposium), San Diego, CA, USA, 18 February 2018. [Google Scholar]
- Chen, D.D.; Woo, M.; Brumley, D.; Egele, M. Towards Automated Dynamic Analysis for Linux-based Embedded Firmware. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 21–24 February 2016. [Google Scholar]
- Bellard, F. QEMU, a fast and portable dynamic translator. In Proceedings of the USENIX Annual Technical Conference, Anaheim, CA, USA, 10–15 April 2005. [Google Scholar]
- Wikipedia. Fuzzing. Available online: https://en.wikipedia.org/wiki/Fuzzing (accessed on 6 December 2019).
- Wikipedia. Taint Checking. Available online: https://en.wikipedia.org/wiki/Taint_checking (accessed on 6 December 2019).
- King, J.C. Symbolic execution and program testing. Commun. ACM 1976, 19, 385–394. [Google Scholar] [CrossRef]
- Alimi, V.; Vernois, S.; Rosenberger, C. Analysis of embedded applications by evolutionary fuzzing. In Proceedings of the 2014 International Conference on High Performance Computing & Simulation (HPCS), Bologna, Italy, 21–25 July 2014. [Google Scholar]
- Kamel, N.; Lanet, J.L. Analysis of HTTP protocol implementation in smart card embedded web server. Int. J. Inf. Netw. Security (IJINS) 2013, 2, 417. [Google Scholar] [CrossRef]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental security analysis of a modern automobile. In Proceedings of the IEEE Symposium on Security and Privacy (SP), Berkeley, CA, USA, 16–19 May 2010. [Google Scholar]
- Lee, H.; Choi, K.; Chung, K.; Kim, J.; Yim, K. Fuzzing can packets into automobiles. In Proceedings of the 29th International Conference on Advanced Information Networking and Applications, Gwangiu, Korea, 24–27 March 2015. [Google Scholar]
- Wikipedia. CAN bus. Available online: https://en.wikipedia.org/wiki/CAN_bus (accessed on 6 December 2019).
- Chen, J.; Diao, W.; Zhao, Q.; Zuo, C.; Lin, Z.; Wang, X.; Lau, W.C.; Sun, M.; Yang, R.; Zhang, K. Iotfuzzer: Discovering Memory Corruptions in Iot through App-Based Fuzzing. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 18–21 February 2018. [Google Scholar]
- Costin, A.; Zarras, A.; Francillon, A. Automated dynamic firmware analysis at scale: A case study on embedded web interfaces. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016. [Google Scholar]
- Srivastava, P.; Peng, H.; Li, J.; Okhravi, H.; Shrobe, H.; Payer, M. FirmFuzz: Automated IoT Firmware Introspection and Analysis. In Proceedings of the 2nd International ACM Workshop on Security and Privacy for the Internet-of-Things, London, UK, 15 November 2019. [Google Scholar]
- Zheng, Y.; Davanian, A.; Yin, H.; Song, C.; Zhu, H.; Sun, L. FIRM-AFL: High-throughput greybox fuzzing of iot firmware via augmented process emulation. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019. [Google Scholar]
- Zalewski, M. American Fuzzy Lop. Available online: http://lcamtuf.coredump.cx/afl (accessed on 6 December 2019).
- Muench, M.; Stijohann, J.; Kargl, F.; Francillon, A.; Balzarotti, D. What You Corrupt Is Not What You Crash: Challenges in Fuzzing Embedded Devices. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 18–21 February 2018. [Google Scholar]
- Dolan-Gavitt, B.; Hodosh, J.; Hulin, P.; Leek, T.; Whelan, R. Repeatable reverse engineering with PANDA. In Proceedings of the 5th Program Protection and Reverse Engineering Workshop, Los Angeles, CA, USA, 15 December 2015. [Google Scholar]
- Costin, A.; Zaddach, J.; Francillon, A.; Balzarotti, D. A large-scale analysis of the security of embedded firmwares. In Proceedings of the 23rd USENIX Security Symposium (USENIX Security 14), San Diego, CA, USA, 20–22 August 2014. [Google Scholar]
- Davidson, D.; Moench, B.; Ristenpart, T.; Jha, S. FIE on Firmware: Finding Vulnerabilities in Embedded Systems Using Symbolic Execution. In Proceedings of the 22nd USENIX Security Symposium (USENIX Security 13), Washington, DC, USA, 14–16 August 2013. [Google Scholar]
- Celik, Z.B.; Babun, L.; Sikder, A.K.; Aksu, H.; Tan, G.; McDaniel, P.; Uluagac, A.S. KLEE: Unassisted and Automatic Generation of High-Coverage Tests for Complex Systems Programs. In Proceedings of the 8th USENIX Symposium on Operating Systems Design and Implementation(OSDI 2008), San Diego, CA, USA, 8–10 December 2008. [Google Scholar]
- Shoshitaishvili, Y.; Wang, R.; Hauser, C.; Kruegel, C.; Vigna, G. Firmalice-Automatic Detection of Authentication Bypass Vulnerabilities in Binary Firmware. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 8–11 February 2015. [Google Scholar]
- Celik, Z.B.; Babun, L.; Sikder, A.K.; Aksu, H.; Tan, G.; McDaniel, P.; Uluagac, A.S. Sensitive information tracking in commodity IoT. In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018. [Google Scholar]
- Cheng, K.; Li, Q.; Wang, L.; Chen, Q.; Zheng, Y.; Sun, L.; Liang, Z. DTaint: Detecting the taint-style vulnerability in embedded device firmware. In Proceedings of the 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Luxembourg, 25–28 June 2018. [Google Scholar]
- Cui, A.; Stolfo, S.J. A quantitative analysis of the insecurity of embedded network devices: Results of a wide-area scan. In Proceedings of the 26th Annual Computer Security Applications Conference, Austin, TX, USA, 6–10 December 2010. [Google Scholar]
- Al-Alami, H.; Ali, H.; Hussein, A.B. Vulnerability scanning of IoT devices in Jordan using Shodan. In Proceedings of the 2nd International Conference on the Applications of Information Technology in Developing Renewable Energy Processes & Systems (IT-DREPS), Amman, Jordan, 6–7 December 2017. [Google Scholar]
- Durumeric, Z.; Adrian, D.; Mirian, A.; Bailey, M.; Halderman, J.A. A search engine backed by Internet-wide scanning. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015. [Google Scholar]
- Knownsec, Inc. Zoomeye. Available online: https://www.zoomeye.org/ (accessed on 6 December 2019).
- Li, Z.; Lu, S.; Myagmar, S.; Zhou, Y. CP-Miner: A Tool for Finding Copy-paste and Related Bugs in Operating System Code. In Proceedings of the 6th Symposium on Operating System Design and Implementation (OSDI 2004), San Francisco, CA, USA, 6–8 December 2004. [Google Scholar]
- Jang, J.; Agrawal, A.; Brumley, D. ReDeBug: Finding unpatched code clones in entire os distributions. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–23 May 2012. [Google Scholar]
- Wikipedia. N-gram. Available online: https://en.wikipedia.org/wiki/N-gram (accessed on 6 December 2019).
- Myles, G.; Christian, C. K-gram based software birthmarks. In Proceedings of the 2005 ACM Symposium on Applied Computing, Santa Fe, NM, USA, 13–17 March 2005. [Google Scholar]
- Khoo, W.M.; Mycroft, A.; Anderson, R. Rendezvous: A search engine for binary code. In Proceedings of the 10th Working Conference on Mining Software Repositories, San Francisco, CA, USA, 18–19 May 2013. [Google Scholar]
- Karim, M.E.; Walenstein, A.; Lakhotia, A.; Parida, L. Malware phylogeny generation using permutations of code. J. Comput. Virol. 2005, 1, 13–23. [Google Scholar] [CrossRef]
- David, Y.; Yahav, E. Tracelet-based code search in executables. Acm Sigplan Notices 2014, 49, 349–360. [Google Scholar] [CrossRef]
- Pewny, J.; Schuster, F.; Bernhard, L.; Holz, T.; Rossow, C. Leveraging semantic signatures for bug search in binary programs. In Proceedings of the 30th Annual Computer Security Applications Conference, New Orleans, LA, USA, 8–12 December 2014. [Google Scholar]
- Allen, F.E. Control flow analysis. ACM Sigplan Notices 1970, 55, 7. [Google Scholar] [CrossRef]
- Dullien, T.; Rolles, R. Graph-based comparison of executable objects. In Proceedings of the SSTIC’05, Rennes, France, 1–3 July 2005. [Google Scholar]
- Bourquin, M.; King, A.; Robbins, E. Binslayer: Accurate comparison of binary executables. In Proceedings of the 2nd ACM SIGPLAN Program Protection and Reverse Engineering Workshop, Rome, Italy, 26 January 2013. [Google Scholar]
- Egele, M.; Woo, M.; Chapman, P.; Brumley, D. Blanket execution: Dynamic similarity testing for program binaries and components. In Proceedings of the 23rd USENIX Security Symposium (USENIX Security 14), San Diego, CA, USA, 20–22 August 2014. [Google Scholar]
- Gao, D.; Reiter, M.K.; Song, D. Binhunt: Automatically finding semantic differences in binary programs. In Proceedings of the International Conference on Information and Communications Security, Birmingham, UK, 20–22 October 2008. [Google Scholar]
- Ming, J.; Pan, M.; Gao, D. iBinHunt: Binary hunting with inter-procedural control flow. In Proceedings of the International Conference on Information Security and Cryptology, Seoul, Korea, 28–30 November 2012. [Google Scholar]
- Pewny, J.; Garmany, B.; Gawlik, R.; Rossow, C.; Holz, T. Cross-architecture bug search in binary executables. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 17–21 May 2015. [Google Scholar]
- Eschweiler, S.; Yakdan, K.; Gerhards-Padilla, E. discovRE: Efficient Cross-Architecture Identification of Bugs in Binary Code. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 21–24 February 2016. [Google Scholar]
- Chandramohan, M.; Xue, Y.; Xu, Z.; Liu, Y.; Cho, C.Y.; Tan, H.B.K. Bingo: Cross-architecture cross-os binary search. In Proceedings of the 24th ACM SIGSOFT International Symposium on Foundations of Software Engineering, Seattle, WA, USA, 13–18 November 2016. [Google Scholar]
- Feng, Q.; Zhou, R.; Xu, C.; Cheng, Y.; Testa, B.; Yin, H. Scalable graph-based bug search for firmware images. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Yan, S.; Xu, D.; Zhang, B.; Zhang, H.J.; Yang, Q.; Lin, S. Graph embedding and extensions: A general framework for dimensionality reduction. IEEE Transact. Pattern Anal. Mach. Intell. 2007, 29, 40–51. [Google Scholar] [CrossRef]
- Xu, X.; Liu, C.; Feng, Q.; Yin, H.; Song, L.; Song, D. Neural network-based graph embedding for cross-platform binary code similarity detection. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017. [Google Scholar]
- Liu, B.; Huo, W.; Zhang, C.; Li, W.; Li, F.; Piao, A.; Zou, W. αDiff: Cross-version binary code similarity detection with DNN. In Proceedings of the 33rd ACM/IEEE International Conference on Automated Software Engineering, Montpellier, France, 3–7 September 2018. [Google Scholar]
- Gao, J.; Yang, X.; Fu, Y.; Jiang, Y.; Sun, J. Vulseeker: A semantic learning based vulnerability seeker for cross-platform binary. In Proceedings of the 33rd ACM/IEEE International Conference on Automated Software Engineering, Montpellier, France, 3–7 September 2018. [Google Scholar]
- Gao, J.; Yang, X.; Fu, Y.; Jiang, Y.; Shi, H.; Sun, J. Vulseeker-pro: Enhanced semantic learning based binary vulnerability seeker with emulation. In Proceedings of the 26th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, Tallinn, Estonia, 26–30 August 2019. [Google Scholar]
- Long, F.; Rinard, M. Prophet: Automatic Patch Generation via Learning from Successful Patches. Available online: https://core.ac.uk/download/pdf/78062945.pdf (accessed on 6 December 2019).
- Long, F.; Rinard, M. Automatic patch generation by learning correct code. In Proceedings of the 43rd Annual ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, St. Petersburg, FL, USA, 20–22 January 2016. [Google Scholar]
- Long, F.; Amidon, P.; Rinard, M. Automatic inference of code transforms for patch generation. In Proceedings of the 11th Joint Meeting on Foundations of Software Engineering, Paderborn, Germany, 4–8 September 2017. [Google Scholar]
- Le Goues, C.; Nguyen, T.; Forrest, S.; Weimer, W. Genprog: A generic method for automatic software repair. IEEE Trans. Soft. Eng. 2011, 38, 54–72. [Google Scholar] [CrossRef]
- Kim, D.; Nam, J.; Song, J.; Kim, S. Automatic patch generation learned from human-written patches. In Proceedings of the International Conference on Software Engineering, San Francisco, CA, USA, 18–26 May 2013. [Google Scholar]
- Zhang, Y.; Chen, Y.; Bao, C.; Xia, L.; Zhen, L.; Lu, Y.; Wei, T. Adaptive kernel live patching: An open collaborative effort to ameliorate android n-day root exploits. In Proceedings of the Black Hat USA, Las Vegas, NA, USA, 30 July–4 August 2016. [Google Scholar]
- DARPA. Cyber Grand Challenge. Available online: https://www.darpa.mil/program/cyber-grand-challenge (accessed on 6 December 2019).
- Shoshitaishvili, Y.; Bianchi, A.; Borgolte, K.; Cama, A.; Corbetta, J.; Disperati, F.; Dutcher, A.; Grosen, J.; Grosen, P.; Machiry, A.; et al. Mechanical phish: Resilient autonomous hacking. IEEE Secur. Priv. 2018, 16, 12–22. [Google Scholar] [CrossRef]
- Shoshitaishvili, Y.; Weissbacher, M.; Dresel, L.; Salls, C.; Wang, R.; Kruegel, C.; Vigna, G. Rise of the hacrs: Augmenting autonomous cyber reasoning systems with human assistance. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017. [Google Scholar]
- Nguyen-Tuong, A.; Melski, D.; Davidson, J.W.; Co, M.; Hawkins, W.; Hiser, J.D.; Morris, D.; Nguyen, D.; Rizzi, E. Xandra: An Autonomous Cyber Battle System for the Cyber Grand Challenge. IEEE Secur. Priv. 2018, 16, 42–51. [Google Scholar] [CrossRef]
- Fernandes, E.; Jung, J.; Prakash, A. Security analysis of emerging smart home applications. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Fernandes, E.; Paupore, J.; Rahmati, A.; Simionato, D.; Conti, M.; Prakash, A. Flowfence: Practical data protection for emerging iot application frameworks. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016. [Google Scholar]
- Jia, Y.J.; Chen, Q.A.; Wang, S.; Rahmati, A.; Fernandes, E.; Mao, Z.M.; Prakash, A. ContexloT: Towards Providing Contextual Integrity to Appified IoT Platforms. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 26 February–1 March 2017. [Google Scholar]
- Rahmati, A.; Fernandes, E.; Eykholt, K.; Prakash, A. Tyche: A risk-based permission model for smart homes. In Proceedings of the IEEE Cybersecurity Development (SecDev), Cambridge, MA, USA, 30 September–2 October 2018. [Google Scholar]
- Tian, Y.; Zhang, N.; Lin, Y.H.; Wang, X.; Ur, B.; Guo, X.; Tague, P. Smartauth: User-centered authorization for the internet of things. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017. [Google Scholar]
- Lee, S.; Choi, J.; Kim, J.; Cho, B.; Lee, S.; Kim, H.; Kim, J. FACT: Functionality-centric access control system for IoT programming frameworks. In Proceedings of the 22nd ACM on Symposium on Access Control Models and Technologies, Indianapolis, IN, USA, 21–23 June 2017. [Google Scholar]
- Cui, A.; Costello, M.; Stolfo, S. When firmware modifications attack: A case study of embedded exploitation. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 24–27 February 2013. [Google Scholar]
- Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative adversarial nets. In Proceedings of the Advances in Neural Information Processing Systems 27 (NIPS 2014), Montreal, QC, Canada, 8–13 December 2014. [Google Scholar]
- Hiromoto, R.E.; Haney, M.; Vakanski, A. A secure architecture for IoT with supply chain risk management. In Proceedings of the 9th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Bucharest, Romania, 21–23 September 2017. [Google Scholar]

| Ref. | Architecture Support | Simulation Type | ||
|---|---|---|---|---|
| ARM | MIPS | x86 | ||
| Avatar [43] | √ | Semi-simulation | ||
| Prospect [44] | √ | Semi-simulation | ||
| Surrogate [45] | √ | Semi-simulation | ||
| Avatar2 [46] | √ | Semi-simulation | ||
| Firmadyne [47] | √ | √ | Full simulation | |
| Category | Ref. | Target | Technology | Types of Finding Vulnerabilities | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Dynamic Analysis | Alimi [52] | Smart Card | Fuzzing | Logic Vulnerability | |||||||
| Kamel [53] | Smart Card | Fuzzing | Logic Vulnerability | ||||||||
| Kosche [54] | Smart Car | Fuzzing | Weak Access Control | ||||||||
| Lee [55] | Smart Car | Fuzzing | Weak Access Control | ||||||||
| IoTFuzzer [57] | Smart Home | Fuzzing | BO, NPD | ||||||||
| Costin [58] | Router | Fuzzing | CI, XSS, CSRF, SQL Injection | ||||||||
| FirmFuzz [59] | Smart Home | Fuzzing | BO, NPD, CI, XSS | ||||||||
| Firm-AFL [60] | Smart Home | Fuzzing | BO, NPD | ||||||||
| Static Analysis | Costin2014 [64] | Binary code | Fuzzy hash | Weak Authentication, Backdoor | |||||||
| FIE [65] | Binary code | Symbolic execution | BO | ||||||||
| Firmalice [67] | Binary code | Symbolic execution | Backdoor | ||||||||
| SainT [68] | APP | Static Taint analysis | Data Leakage | ||||||||
| DTaint [69] | Binary code | Static Taint analysis | BO, CI | ||||||||
| Component | Ref. | Attack Surface | Technical Requirement | Architecture Support | OS Support | With AI | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Simulation | Debugging Interface | Netwrok Traffic | Firmware (Binary) | Source Code | Cloud (APP) | ARM | MIPS | X86 | Other | Linux | Vxworks | Windows | Android | ||||
| Basic Framework | Avatar, 2014 [43] | S | √ | √ | √ | √ | √ | ||||||||||
| Prospect, 2014 [44] | S | √ | √ | √ | √ | ||||||||||||
| Surrogate, 2015 [45] | S | √ | √ | √ | √ | √ | |||||||||||
| Avatar2, 2018 [46] | S | √ | √ | √ | √ | √ | |||||||||||
| Firmadyne, 2016 [47] | S, P1 | √ | √ | √ | √ | √ | |||||||||||
| Dynamic Analysis | Alimi, 2014 [52] | P1 | √ | √ | |||||||||||||
| Kamel, 2013 [53] | P1 | √ | √ | ||||||||||||||
| Koscher, 2010 [54] | S | √ | √ | ||||||||||||||
| Lee, 2015 [55] | S | √ | √ | ||||||||||||||
| IoTFuzzer, 2018 [57] | S, P1 | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| Costin, 2016 [58] | P1 | √ | √ | √ | √ | √ | |||||||||||
| FirmFuzz, 2019 [59] | S, P1 | √ | √ | √ | √ | √ | |||||||||||
| FIRM-AFL, 2019 [60] | S, P1 | √ | √ | √ | √ | √ | |||||||||||
| Static Analysis | Costin, 2014 [64] | S, P1 | √ | √ | √ | √ | √ | ||||||||||
| FIE, 2013 [65] | S | √ | √ | ||||||||||||||
| Firmalice, 2015 [67] | S | √ | √ | √ | √ | ||||||||||||
| SainT, 2018 [68] | S, P1 | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| DTaint, 2018 [69] | S | √ | √ | √ | √ | ||||||||||||
| Network Scanning | Cui, 2010 [70] | S, P | √ | √ | √ | √ | √ | √ | √ | √ | √ | ||||||
| Shodan [71] | S, P | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| Censys, 2015 [72] | S, P | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| Zoomeye [73] | S, P | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| Similarit Detection | CP-Miner, 2004 [74] | S | √ | √ | √ | ||||||||||||
| ReDeBug, 2012 [75] | S | √ | √ | √ | |||||||||||||
| Rendezvous, 2013 [78] | S | √ | √ | √ | |||||||||||||
| Karim, 2005 [79] | S | √ | √ | √ | |||||||||||||
| Tracelet-based, 2014 [80] | S | √ | √ | √ | |||||||||||||
| TEDEM, 2014 [81] | S | √ | √ | √ | √ | ||||||||||||
| BinDiff, 2005 [83] | S | √ | √ | √ | √ | √ | √ | ||||||||||
| Binslayer, 2013 [84] | S | √ | √ | √ | |||||||||||||
| Egele, 2014 [85] | S | √ | √ | √ | |||||||||||||
| BinHunt, 2008 [86] | S | √ | √ | √ | |||||||||||||
| iBinHunt, 2012 [87] | S | √ | √ | √ | |||||||||||||
| Multi-MH, 2015 [88] | S | √ | √ | √ | √ | √ | |||||||||||
| DiscovRE, 2016 [89] | S | √ | √ | √ | √ | √ | √ | √ | |||||||||
| BinGo, 2016 [90] | S | √ | √ | √ | √ | √ | √ | ||||||||||
| Genius, 2016 [91] | S | √ | √ | √ | √ | √ | √ | ||||||||||
| Xu, 2017 [93] | S | √ | √ | √ | √ | √ | √ | ||||||||||
| Diff, 2018 [94] | S | √ | √ | √ | √ | √ | √ | ||||||||||
| VulSeeker, 2018 [95] | S | √ | √ | √ | √ | √ | √ | ||||||||||
| VulSeeker-Pro, 2018 [95] | S | √ | √ | √ | √ | √ | √ | ||||||||||
| Automated Patch Generation | Long, 2015 [97] | S | √ | √ | |||||||||||||
| Long, 2016 [98] | S | √ | √ | ||||||||||||||
| Long, 2017 [99] | S | √ | √ | ||||||||||||||
| GenProg, 2011 [100] | S | √ | √ | ||||||||||||||
| Kim, 2013 [101] | S | √ | √ | ||||||||||||||
| AdaptKpatch, 2016 [102] | S | √ | √ | √ | |||||||||||||
| Shoshitaishvili, 2017 [105] | S | √ | √ | √ | |||||||||||||
| Shoshitaishvili, 2018 [104] | S | √ | √ | √ | |||||||||||||
| Xandra, 2018 [106] | S | √ | √ | √ | |||||||||||||
| Access Control | Flowfence, 2016 [108] | P | √ | √ | √ | √ | √ | √ | √ | √ | √ | ||||||
| ContexIoT, 2017 [109] | P | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| Tyche, 2018 [108,110] | P | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| Flowfence, 2016 [108] | P | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| SmartAuth, 2017 [111] | P | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | ||||||
| FACT, 2017 [112] | P | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| Category | Name | T1 | T2 | T3 | T4 |
|---|---|---|---|---|---|
| Challenges | Complexity and heterogeneity of device | √ | √ | √ | √ |
| Limitations of device resources | √ | √ | √ | ||
| Closed-source measures | √ | √ | √ | √ | |
| Opportunities | Application of AI technology | √ | √ | √ | |
| Dependency of third-party and open source code | √ | √ | √ | ||
| Development of peripheral systems | √ | √ |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, M.; Zhuge, J.; Cao, M.; Shi, Z.; Jiang, L. A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices. Future Internet 2020, 12, 27. https://doi.org/10.3390/fi12020027
Yu M, Zhuge J, Cao M, Shi Z, Jiang L. A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices. Future Internet. 2020; 12(2):27. https://doi.org/10.3390/fi12020027
Chicago/Turabian StyleYu, Miao, Jianwei Zhuge, Ming Cao, Zhiwei Shi, and Lin Jiang. 2020. "A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices" Future Internet 12, no. 2: 27. https://doi.org/10.3390/fi12020027
APA StyleYu, M., Zhuge, J., Cao, M., Shi, Z., & Jiang, L. (2020). A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices. Future Internet, 12(2), 27. https://doi.org/10.3390/fi12020027





