Evaluating Forwarding Protocols in Opportunistic Networks: Trends, Advances, Challenges and Best Practices
Abstract
:1. Introduction
2. Applications of Opportunistic Networking Protocols
3. Methodology of the Survey
4. Simulator Environments
5. Comparative Studies
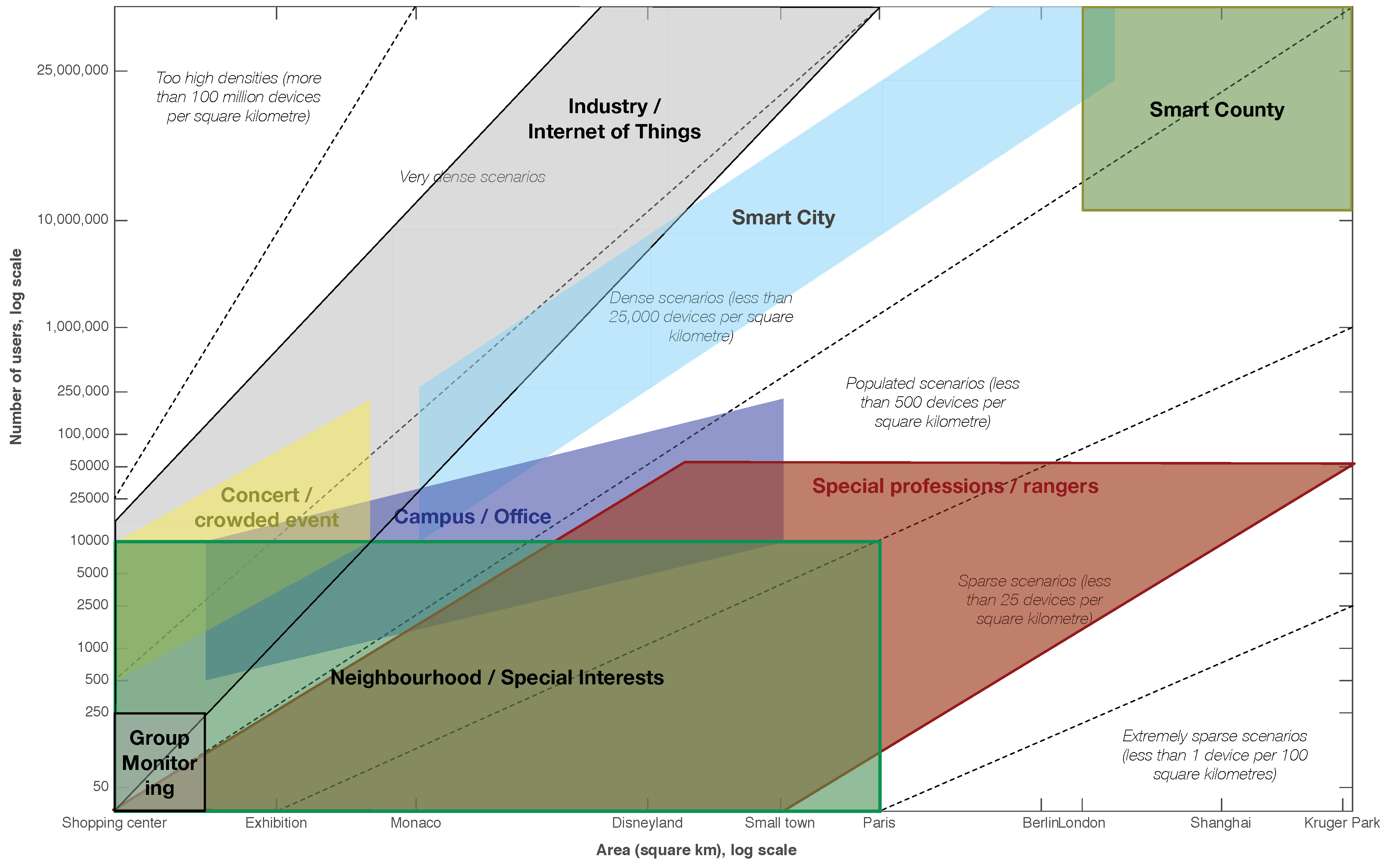
6. Scalability
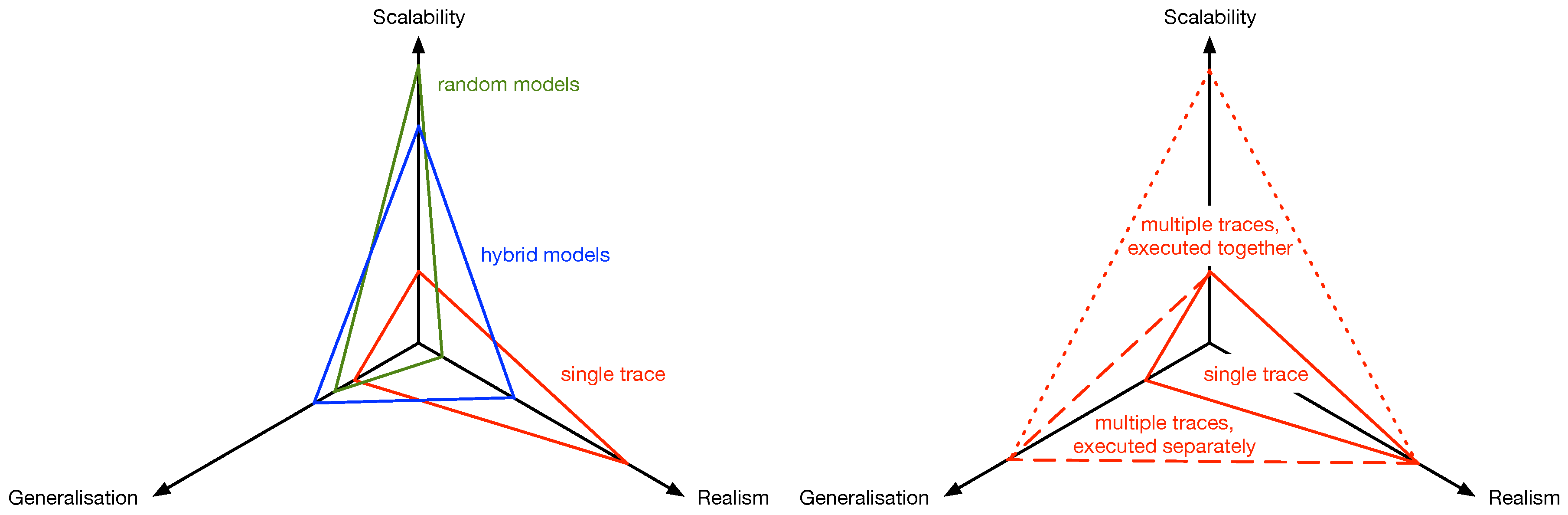
7. Mobility
- Random mobility traces use analytical models to describe the mobility of devices/people in OppNets. They are simple, fast, but very unrealistic. Examples include Random Waypoint, Random Direction, etc.
- Real trace mobility models gather real GPS or other location data from real users and replay them in simulation. They are very realistic, easy to implement, but slow. Furthermore, gathering the traces is a very tedious task and there is no way to increase the number of nodes later. There exist a well-known database with such traces, called Crawdad (https://crawdad.org).
- Hybrid models combine both worlds by extracting statistical data or observations from real traces and then implementing a randomized model based on those. They are faster than real traces and more realistic than random models. However, they also quickly become very complex to understand and implement. It is also very hard to grasp all behavioral observations in one model. Examples for such models include SWIM (Small Worlds in Motion) [82], HCMM [83] or TRAILS [84].
- Scalability: How many nodes can a model produce/simulate? Random and hybrid mobility models are not really restricted in their scalability: as many nodes as needed can be simulated. However, traces are limited to the maximum number of nodes they have been collected for.
- Realism: How realistic is the behavior of the moving nodes? Real traces are clearly real. Random models are least realistic, while hybrid models tend to have more realistic properties.
- Generalization: How general can the results be considered? A single real trace is a snapshot and thus not representative. Analytical (random and hybrid), when used for a large number of scenarios and parameters, can be considered representative studies with statistical significance.
8. Cache Size and Traffic
9. Metrics
10. Holistic Guide to OppNets Evaluations
- Select a standard simulator. We recommend ONE or OMNeT++, as those are the most well documented and actively developed ones.
- Select OppNet protocols to compare against. They should be close in their general application scenario (destination-less or destination-oriented, etc.) and should be recent, e.g., from the last five years. Additionally, compare against optimal solutions. This combination ensures the correct positioning of the new protocols into the context of existing ones and how to progress the state of the art.
- Design a good application scenario with realistic number of nodes, traffic, cache sizes and simulation time.
- Select a good mobility model, able to cater for the application scenario and its scale. Traces (see also the discussion below) or recent hybrid mobility models are a good option. If using traces, use at least 3–5 different traces. Best, use several hybrid models and several traces.
- Explore the relevant protocol specific metrics in terms of overhead.
- Explore the parameter space of your scenario from minimum to maximum possible values. Report on confidence intervals.
11. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A

Appendix B


References
- Kurkowski, S.; Camp, T.; Colagrosso, M. MANET simulation studies: The incredibles. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2005, 9, 50–61. [Google Scholar] [CrossRef]
- Mota, V.F.; Cunha, F.D.; Macedo, D.F.; Nogueira, J.M.; Loureiro, A.A. Protocols, mobility models and tools in opportunistic networks: A survey. Comput. Commun. 2014, 48, 5–19. [Google Scholar] [CrossRef]
- Trifunovic, S.; Kouyoumdjieva, S.T.; Distl, B.; Pajevic, L.; Karlsson, G.; Plattner, B. A decade of research in opportunistic networks: Challenges, relevance, and future directions. IEEE Commun. Mag. 2017, 55, 168–173. [Google Scholar] [CrossRef]
- Pozza, R.; Nati, M.; Georgoulas, S.; Moessner, K.; Gluhak, A. Neighbor discovery for opportunistic networking in internet of things scenarios: A survey. IEEE Access 2015, 3, 1101–1131. [Google Scholar] [CrossRef]
- Chakchouk, N. A Survey on Opportunistic Routing in Wireless Communication Networks. IEEE Commun. Surv. Tutor. 2015, 17, 2214–2241. [Google Scholar] [CrossRef]
- Sobin, C.; Raychoudhury, V.; Marfia, G.; Singla, A. A survey of routing and data dissemination in delay tolerant networks. J. Netw. Comput. Appl. 2016, 67, 128–146. [Google Scholar]
- Batabyal, S.; Bhaumik, P. Mobility models, traces and impact of mobility on opportunistic routing algorithms: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 1679–1707. [Google Scholar] [CrossRef]
- Dede, J.; Förster, A.; Hernández-Orallo, E.; Herrera-Tapia, J.; Kuladinithi, K.; Kuppusamy, V.; Manzoni, P.; bin Muslim, A.; Udugama, A.; Vatandas, Z. Simulating opportunistic networks: Survey and future directions. IEEE Commun. Surv. Tutor. 2018, 20, 1547–1573. [Google Scholar] [CrossRef]
- García-Campos, J.M.; Sánchez-García, J.; Reina, D.; Toral, S.; Barrero, F. An evaluation methodology for reliable simulation based studies of routing protocols in VANETs. Simul. Model. Pract. Theory 2016, 66, 139–165. [Google Scholar] [CrossRef]
- Saloni, M.; Julien, C.; Murphy, A.L.; Picco, G.P. Lasso: A device-to-device group monitoring service for smart cities. In Proceedings of the 2017 International Smart Cities Conference (ISC2), Wuxi, China, 14–17 September 2017; pp. 1–6. [Google Scholar]
- Vahdat, A.; Becker, D. Epidemic Routing for Partially Connected Ad Hoc Netw. 2000. Technical Report CS 200006 2000, Department of Computer Science, Duke University, NC. Available online: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.34.6151 (accessed on 11 May 2019).
- Dubois-Ferriere, H.; Grossglauser, M.; Vetterli, M. Age matters: Efficient route discovery in mobile ad hoc networks using encounter ages. In Proceedings of the 4th ACM International Symposium on Mobile Ad Hoc Networking & Computing, Annapolis, MD, USA, 1–3 June 2003; pp. 257–266. [Google Scholar]
- Tan, K.; Zhang, Q.; Zhu, W. Shortest path routing in partially connected ad hoc networks. In Proceedings of the Global Telecommunications Conference, San Francisco, CA, USA, 1–5 December 2003; Volume 2, pp. 1038–1042. [Google Scholar]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Efficient routing in intermittently connected mobile networks: The single-copy case. IEEE/ACM Trans. Netw. 2008, 16, 63–76. [Google Scholar] [CrossRef]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and wait: An efficient routing scheme for intermittently connected mobile networks. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-Tolerant Networking, Philadelphia, PA, USA, 22–26 August 2005; pp. 252–259. [Google Scholar]
- Leguay, J.; Friedman, T.; Conan, V. Evaluating mobility pattern space routing for DTNs. arXiv 2005, arXiv:cs/0511102. [Google Scholar]
- Burgess, J.; Gallagher, B.; Jensen, D.; Levine, B.N. Maxprop: Routing for vehicle-based disruption-tolerant networks. In Proceedings of the 25th IEEE International Conference on Computer Communications, Barcelona, Spain, 23–29 April 2006; pp. 1–11. [Google Scholar]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and focus: Efficient mobility-assisted routing for heterogeneous and correlated mobility. In Proceedings of the Fifth Annual IEEE International Conference on Pervasive Computing and Communications Workshops, White Plains, NY, USA, 19–23 March 2007; pp. 79–85. [Google Scholar]
- Ramanathan, R.; Hansen, R.; Basu, P.; Rosales-Hain, R.; Krishnan, R. Prioritized epidemic routing for opportunistic networks. In Proceedings of the 1st International MobiSys Workshop on Mobile Opportunistic Networking, San Juan, Puerto Rico, 11 June 2007; pp. 62–66. [Google Scholar]
- Boldrini, C.; Conti, M.; Jacopini, J.; Passarella, A. Hibop: A history based routing protocol for opportunistic networks. In Proceedings of the 2007 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Espoo, Finland, 18–21 June 2007; pp. 1–12. [Google Scholar]
- Leontiadis, I.; Mascolo, C. GeOpps: Geographical opportunistic routing for vehicular networks. In Proceedings of the 2007 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Espoo, Finland, 18–21 June 2007; pp. 1–6. [Google Scholar]
- Nguyen, H.A.; Giordano, S.; Puiatti, A. Probabilistic routing protocol for intermittently connected mobile ad hoc network (propicman). In Proceedings of the 2007 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Espoo, Finland, 18–21 June 2007; pp. 1–6. [Google Scholar]
- Spyropoulos, T.; Turletti, T.; Obraczka, K. Utility-based message replication for intermittently connected heterogeneous networks. In Proceedings of the 2007 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Espoo, Finland, 18–21 June 2007; pp. 1–6. [Google Scholar]
- Balasubramanian, A.; Levine, B.; Venkataramani, A. DTN routing as a resource allocation problem. ACM SIGCOMM Comput. Commun. Rev. 2007, 37, 373–384. [Google Scholar] [CrossRef]
- Sandulescu, G.; Nadjm-Tehrani, S. Opportunistic DTN routing with window-aware adaptive replication. In Proceedings of the 4th Asian Conference on Internet Engineering, Pratunam, Bangkok, Thailand, 18–20 November 2008; pp. 103–112. [Google Scholar]
- Nelson, S.C.; Bakht, M.; Kravets, R. Encounter-based routing in DTNs. In Proceedings of the INFOCOM 2009, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 846–854. [Google Scholar]
- Musolesi, M.; Mascolo, C. Car: Context-aware adaptive routing for delay-tolerant mobile networks. IEEE Trans. Mob. Comput. 2009, 8, 246–260. [Google Scholar] [CrossRef]
- Daly, E.M.; Haahr, M. Social network analysis for information flow in disconnected delay-tolerant MANETs. IEEE Trans. Mob. Comput. 2008, 606–621. [Google Scholar] [CrossRef]
- Pujol, J.M.; Toledo, A.L.; Rodriguez, P. Fair routing in delay tolerant networks. In Proceedings of the INFOCOM 2009, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 837–845. [Google Scholar]
- Huang, T.K.; Lee, C.K.; Chen, L.J. Prophet+: An adaptive prophet-based routing protocol for opportunistic network. In Proceedings of the 2010 24th IEEE International Conference on Advanced Information Networking and Applications, Perth, Australia, 20–23 April 2010; pp. 112–119. [Google Scholar]
- Grasic, S.; Davies, E.; Lindgren, A.; Doria, A. The evolution of a DTN routing protocol-PRoPHETv2. In Proceedings of the 6th ACM Workshop on Challenged Networks, Las Vegas, NV, USA, 19–23 September 2011; pp. 27–30. [Google Scholar]
- Hui, P.; Crowcroft, J.; Yoneki, E. Bubble rap: Social-based forwarding in delay-tolerant networks. IEEE Trans. Mob. Comput. 2011, 10, 1576–1589. [Google Scholar] [CrossRef]
- Tie, X.; Venkataramani, A.; Balasubramanian, A. R3: Robust replication routing in wireless networks with diverse connectivity characteristics. In Proceedings of the 17th Annual International Conference on Mobile Computing and Networking, Las Vegas, NV, USA, 19–23 September 2011; pp. 181–192. [Google Scholar]
- Vu, L.; Do, Q.; Nahrstedt, K. 3r: Fine-grained encounter-based routing in delay tolerant networks. In Proceedings of the 2011 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Lucca, Italy, 20–24 June 2011; pp. 1–6. [Google Scholar]
- Moreira, W.; Mendes, P.; Sargento, S. Opportunistic routing based on daily routines. In Proceedings of the 2012 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), San Francisco, CA, USA, 25–28 June 2012; pp. 1–6. [Google Scholar]
- Ciobanu, R.I.; Dobre, C.; Cristea, V. SPRINT: Social prediction-based opportunistic routing. In Proceedings of the 2013 IEEE 14th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Madrid, Spain, 4–7 June 2013; pp. 1–7. [Google Scholar]
- Abdelkader, T.; Naik, K.; Nayak, A.; Goel, N.; Srivastava, V. SGBR: A routing protocol for delay tolerant networks using social grouping. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 2472–2481. [Google Scholar] [CrossRef]
- Moreira, W.; Mendes, P.; Sargento, S. Social-aware opportunistic routing protocol based on user’s interactions and interests. In Proceedings of the International Conference on Ad Hoc Netw, Wroclaw, Poland, 8–10 July 2013; pp. 100–115. [Google Scholar]
- Dhurandher, S.K.; Sharma, D.K.; Woungang, I.; Bhati, S. HBPR: History based prediction for routing in infrastructure-less opportunistic networks. In Proceedings of the 2013 IEEE 27th International Conference on Advanced Information Networking and Applications (AINA), Barcelona, Spain, 25–28 March 2013; pp. 931–936. [Google Scholar]
- Ciobanu, R.I.; Marin, R.C.; Dobre, C.; Cristea, V.; Mavromoustakis, C.X. ONSIDE: Socially-aware and interest-based dissemination in opportunistic networks. In Proceedings of the 2014 IEEE Network Operations and Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014; pp. 1–6. [Google Scholar]
- Ciobanu, R.I.; Reina, D.; Dobre, C.; Toral, S.; Johnson, P. JDER: A history-based forwarding scheme for delay tolerant networks using Jaccard distance and encountered ration. J. Netw. Comput. Appl. 2014, 40, 279–291. [Google Scholar] [CrossRef]
- Dhurandher, S.K.; Sharma, D.K.; Woungang, I.; Gupta, R.; Garg, S. GAER: Genetic algorithm-based energy-efficient routing protocol for infrastructure-less opportunistic networks. J. Supercomput. 2014, 69, 1183–1214. [Google Scholar] [CrossRef]
- Dhurandher, S.K.; Borah, S.J.; Obaidat, M.S.; Sharma, D.K.; Gupta, S.; Baruah, B. Probability-based controlled flooding in opportunistic networks. In Proceedings of the 2015 12th International Joint Conference on e-Business and Telecommunications (ICETE), Colmar, France, 20–22 July 2015; Volume 6, pp. 3–8. [Google Scholar]
- Visca, J.; Baliosian, J.; Fuentes, R.A.; Cavalli, A.R. Path sampling, a robust alternative to gossiping for opportunistic network routing. In Proceedings of the 2016 IEEE 12th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), New York, NY, USA, 17–19 October 2016; pp. 1–8. [Google Scholar]
- Vendramin, A.C.K.; Munaretto, A.; Delgado, M.R.; Fonseca, M.; Viana, A.C. A social-aware routing protocol for opportunistic networks. Expert Syst. Appl. 2016, 54, 351–363. [Google Scholar] [CrossRef]
- Park, J.; Lee, J.; Kim, S.K.; Jang, K.; Yang, S.B. A forwarding scheme based on swarm intelligence and percolation centrality in opportunistic networks. Wirel. Netw. 2016, 22, 2511–2521. [Google Scholar] [CrossRef]
- Chen, H.; Lou, W. Contact expectation based routing for delay tolerant networks. Ad Hoc Netw. 2016, 36, 244–257. [Google Scholar] [CrossRef]
- Wu, J.; Wang, J.; Liu, L.; Tanha, M.; Pan, J. A data forwarding scheme with reachable probability centrality in DTNs. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Dhurandher, S.K.; Borah, S.; Woungang, I.; Sharma, D.K.; Arora, K.; Agarwal, D. EDR: An encounter and distance based routing protocol for opportunistic networks. In Proceedings of the 2016 IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, Switzerland, 23–25 March 2016; pp. 297–302. [Google Scholar]
- Rajaei, A.; Chalmers, D.; Wakeman, I.; Parisis, G. GSAF: Efficient and flexible geocasting for opportunistic networks. In Proceedings of the 2016 IEEE 17th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Coimbra, Portugal, 21–24 June 2016; pp. 1–9. [Google Scholar]
- Yu, C.; Tu, Z.; Yao, D.; Lu, F.; Jin, H. Probabilistic routing algorithm based on contact duration and message redundancy in delay tolerant network. Int. J. Commun. Syst. 2016, 29, 2416–2426. [Google Scholar] [CrossRef]
- Zhang, F.; Wang, X.; Jiang, L.; Zhang, L. Energy efficient forwarding algorithm in opportunistic networks. Chin. J. Electron. 2016, 25, 957–964. [Google Scholar] [CrossRef]
- Guan, J.; Chu, Q.; You, I. The social relationship based adaptive multi-spray-and-wait routing algorithm for disruption tolerant network. Mob. Inf. Syst. 2017, 2017, 1819495. [Google Scholar] [CrossRef]
- Zhang, H.; Wan, L.; Chen, Y.; Yang, L.T.; Peng, L. Adaptive Message Routing and Replication in Mobile Opportunistic Networks for Connected Communities. ACM Trans. Internet Technol. (TOIT) 2017, 18, 2. [Google Scholar] [CrossRef]
- Li, Y.; Bartos, R. Interaction based routing algorithm for opportunistic mobile social networks. In Proceedings of the 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017; pp. 492–497. [Google Scholar]
- Yu, X.; Liu, Z. Message forwarding strategy with fuzzy mechanism in opportunistic network. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017; pp. 309–314. [Google Scholar]
- Jia, W.; Chen, Z.; Zhao, M. Effective information transmission based on socialization nodes in opportunistic networks. Comput. Netw. 2017, 129, 297–305. [Google Scholar]
- Zhao, R.; Wang, X.; Zhang, L.; Lin, Y. A social-aware probabilistic routing approach for mobile opportunistic social networks. Trans. Emerg. Telecommun. Technol. 2017, 28, e3230. [Google Scholar] [CrossRef]
- Zhang, L.; Wang, X.; Lu, J.; Ren, M.; Duan, Z.; Cai, Z. A novel contact prediction-based routing scheme for DTNs. Trans. Emerg. Telecommun. Technol. 2017, 28, e2889. [Google Scholar] [CrossRef]
- Zhou, H.; Leung, V.C.; Zhu, C.; Xu, S.; Fan, J. Predicting temporal social contact patterns for data forwarding in opportunistic mobile networks. IEEE Trans. Veh. Technol. 2017, 66, 10372–10383. [Google Scholar] [CrossRef]
- Ma, H.; Wu, H.; Zheng, G.; Ji, B.; Li, J. FARS: A Fairness-aware Routing Strategy for Mobile Opportunistic Networks. KSII Trans. Internet Inf. Syst. 2018, 12, 1992–2008. [Google Scholar] [CrossRef]
- Borah, S.J.; Dhurandher, S.K.; Woungang, I.; Kandhoul, N.; Rodrigues, J.J. An Energy-Efficient Location Prediction-Based Forwarding Scheme for Opportunistic Networks. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Liu, K.; Chen, Z.; Wu, J.; Xiao, Y.; Zhang, H. Predict and Forward: An Efficient Routing-Delivery Scheme Based on Node Profile in Opportunistic Networks. Future Internet 2018, 10, 74. [Google Scholar] [CrossRef]
- Baek, K.; Seo, D.; Chung, Y. An Improved Opportunistic Routing Protocol Based on Context Information of Mobile Nodes. Appl. Sci. 2018, 8, 1344. [Google Scholar] [CrossRef]
- Tao, J.; Wu, H.; Shi, S.; Hu, J.; Gao, Y. Contacts-aware opportunistic forwarding in mobile social networks: A community perspective. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Ciobanu, R.I.; Reina, D.G.; Dobre, C.; Toral, S.L. Context-adaptive forwarding in mobile opportunistic networks. Ann. Telecommun. 2018, 73, 559–575. [Google Scholar] [CrossRef]
- Papapetrou, E.; Likas, A. Cluster-based Replication: A Forwarding Strategy for Mobile Opportunistic Networks. In Proceedings of the 2018 IEEE 19th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Chania, Greece, 12–15 June 2018. [Google Scholar]
- Sajid, A.; Hussain, K. Rule Based (Forward Chaining/Data Driven) Expert System for Node Level Congestion Handling in Opportunistic Network. Mob. Netw. Appl. 2018, 23, 446–455. [Google Scholar] [CrossRef]
- Sharma, D.K.; Dhurandher, S.K.; Agarwal, D.; Arora, K. kROp: K-Means clustering based routing protocol for opportunistic networks. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 1289–1306. [Google Scholar] [CrossRef]
- Sharma, D.K.; Kukreja, D.; Aggarwal, P.; Kaur, M.; Sachan, A. Poisson’s probability-based Q-Routing techniques for message forwarding in opportunistic networks. Int. J. Commun. Syst. 2018, 31, e3593. [Google Scholar] [CrossRef]
- Sharma, D.K.; Dhurandher, S.K.; Woungang, I.; Srivastava, R.K.; Mohananey, A.; Rodrigues, J.J. A machine learning-based protocol for efficient routing in opportunistic networks. IEEE Syst. J. 2018, 12, 2207–2213. [Google Scholar] [CrossRef]
- Lenando, H.; Alrfaay, M. EpSoc: Social-Based Epidemic-Based Routing Protocol in Opportunistic Mobile Social Network. Mob. Inf. Syst. 2018, 2018, 6462826. [Google Scholar] [CrossRef]
- Lin, Y.; Chen, Z.; Wu, J.; Wang, L. An Opportunistic Network Routing Algorithm Based on Cosine Similarity of Data Packets between Nodes. Algorithms 2018, 11, 119. [Google Scholar] [CrossRef]
- Madoery, P.G.; Raverta, F.D.; Fraire, J.A.; Finochietto, J.M. Routing in Space Delay Tolerant Networks under Uncertain Contact Plans. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Keränen, A.; Ott, J.; Kärkkäinen, T. The ONE Simulator for DTN Protocol Evaluation. In Proceedings of the 2nd International Conference on Simulation Tools and Techniques, Rome, Italy, 2–6 March 2009; pp. 55:1–55:10. [Google Scholar]
- Varga, A. The OMNET++ discrete event simulation system. In Proceedings of the European Simulation Multiconference; SCS—European Publishing House: Prague, Czech Republic, 2001; pp. 319–324. [Google Scholar]
- Riley, G.F.; Henderson, T.R. The ns-3 network simulator. In Modeling and Tools for Network Simulation; Springer: Berlin, Germany, 2010; pp. 15–34. [Google Scholar]
- Ciobanu, R.I.; Marin, R.C.; Dobre, C. MobEmu: A Framework to Support Decentralized Ad-Hoc Networking. In Modeling and Simulation in HPC and Cloud Systems; Kołodziej, J., Pop, F., Dobre, C., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 87–119. [Google Scholar] [CrossRef]
- Papanikos, N.; Akestoridis, D.G.; Papapetrou, E. Adyton: A Network Simulator for Opportunistic Networks. 2015. Available online: https://github.com/npapanik/Adyton (accessed on 24 December 2018).
- Breslau, L.; Estrin, D.; Yu, H.; Fall, K.; Floyd, S.; Heidemann, J.; Helmy, A.; Huang, P.; McCanne, S.; Varadhan, K.; et al. Advances in network simulation. Computer 2000, 59–67. [Google Scholar] [CrossRef]
- Udugama, A.; Förster, A.; Dede, J.; Kuppusamy, V.; Bin Muslim, A. OPS—An Opportunistic Networking Protocol Simulator for OMNeT++. In Proceedings of the International OMNeT++ Summit, Bremen, Germany, 7–8 September 2017. [Google Scholar]
- Stefa, J.; Mei, A. Swim: A simple model to generate small mobile worlds. In Proceedings of the IEEE INFOCOM Conference, San Diego, CA, USA, 24–31 July 2009. [Google Scholar]
- Boldrini, C.; Passarella, A. HCMM: Modelling Spatial and Temporal Properties of Human Mobility Driven by Users’ Social Relationships. Comput. Commun. 2010, 33, 1056–1074. [Google Scholar] [CrossRef]
- Förster, A.; Bin Muslim, A.; Udugama, A. TRAILS—A Trace-Based Probabilistic Mobility Model. In Proceedings of the 21st ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems (MSWIM), Montreal, QC, Canada, 28 October–2 November 2018. [Google Scholar]
- Hernández-Orallo, E.; Cano, J.C.; Calafate, C.T.; Manzoni, P. FALCON: A new approach for the evaluation of opportunistic networks. Ad Hoc Netw. 2018, 81, 109–121. [Google Scholar] [CrossRef]


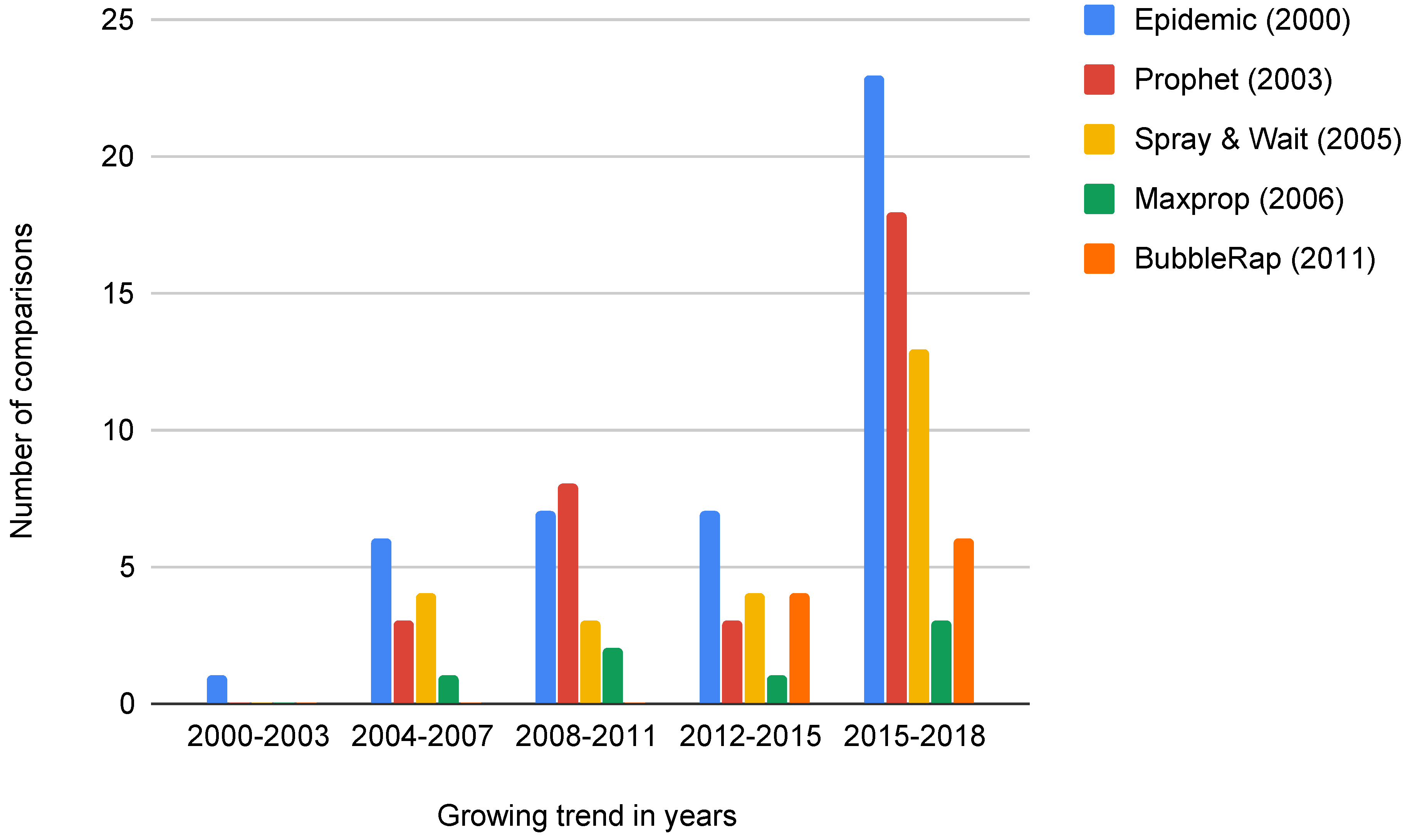



| Protocol | Year of Publication | Concise Description |
|---|---|---|
| Epidemic Routing [11] | 2000 | Flooding of all the messages to all the neighbors. |
| Fresh [12] | 2003 | Nodes having the most recent encounters with destination are chosen as forwarders. |
| SEPR [13] | 2003 | Nodes with the shortest expected path length to the destination are selected as forwarders. |
| Seek and Focus [14] | 2004 | Randomized forwarding and Utility-based forwarding are used based on encounter rates. |
| Spray and Wait [15] | 2005 | Controlled-replication. Spraying L copies of message M to relays and holding the final copy until the destination node is met. |
| MobySpace [16] | 2005 | Nodes having similar mobility pattern to the destination node. |
| Maxprop [17] | 2006 | Estimating highest delivery likelihood of neighbors to the destination based on frequency of encounters with the destination. |
| Spray and Focus [18] | 2007 | Spraying message copies to the neighbors and utility forwarding |
| Prioritized ER [19] | 2007 | Estimation of routing cost to destination and prioritization of packet bundles to transmit based on routing cost. |
| HiBop [20] | 2007 | Contact history and stored context information about neighbors are used for selection of forwarders. |
| Geo-Opps [21] | 2007 | Using geographic location of the destination and prior known route schedules of destination and encountered neighbors. |
| Propicman [22] | 2007 | Estimating the probability of meeting the destination by sending probes to two hop neighbors. |
| Utility-based Spraying [23] | 2007 | Nodes choose between different utilities such as most mobile first, most social first, etc. for selection of relays. |
| Rapid [24] | 2007 | Adaptive replication of copies based on a chosen utility metric such as minimizing average delivery latency, minimizing maximum latency, etc. |
| ORWAR [25] | 2008 | Controlled-replication such as spray and wait routing combined with prioritization of messages by choosing required utility metrics. |
| EBR [26] | 2009 | Replication-based and selection of forwarders based on the number of encounters with the destination. |
| CAR [27] | 2009 | Evaluating and predicting context information such as mobility locally and by sending updates to neighborhood, using delivery predictability for relay selection. |
| SimBetTs [28] | 2009 | Relay selection based on social analysis on betweenness centrality, similarity index and strength of ties between nodes. |
| FairRoute [29] | 2009 | Tie strength and social status of nodes to assist in forwarding decisions. |
| Prophet+ [30] | 2010 | Enhancements to delivery predictability by considering node’s buffer, power, location, popularity along with the delivery predictability obtained from prophet. |
| Prophet v2 [31] | 2011 | Fine-grained encounter rates by taking into account the unsuccessful intermittent connections, thus increasing the reliability of delivery predictability. |
| BubbleRap [32] | 2011 | Social and structural properties such as centrality and community metrics are used to select forwarders. |
| R3 [33] | 2011 | Estimates end-to-end delays of different paths to the destination and selects the path with best replication gain, uses adaptive replication. |
| 3R [34] | 2011 | Estimates encounter probability by prediction of fine-grained regular encounters pertaining to a time window in a given day. |
| dLife [35] | 2012 | Daily routines of users are used to increase the accuracy of predicting future social contacts. |
| Sprint [36] | 2013 | Predicting the future contacts over a given time by analyzing the mobility patterns and using additional information on social contacts. |
| SGBR [37] | 2013 | Identifying social groups based on frequent and longer contact durations, social properties used to route packets between different communities. |
| Scorp [38] | 2013 | Prediction of probability of encounters having content-specific interests among the neighbors with similar social interests and daily routines. |
| HBPR [39] | 2013 | Exchange of location updates between nodes and predicting the direction of future movements to find shortest paths to the destination. |
| Onside [40] | 2014 | Community identification based on similar social interests and exchange of interests table between nodes to chose forwarders. |
| JDER [41] | 2014 | Targets high reachability by giving preference to selecting nodes connected to multiple communities (cut-nodes) as forwarders. |
| GAER [42] | 2014 | Genetic algorithm based next hop selection, distance between mean of home locations of neighbors to destination along with a fitness function is used to select forwarders. |
| PRoWait [43] | 2015 | Uses delivery predictability of Prophet to select forwarders combined with spray and wait routing. |
| Pathsampling [44] | 2016 | Learns network topology by using probes sent along with the beacons and selects forwarders based on estimated end-to-end delivery probability. |
| CGrAnt [45] | 2016 | Local information, situational information and domain information is used to select forwarders. |
| ABCON [46] | 2016 | Relay nodes are selected by the number of encountered neighbors. |
| EER [47] | 2016 | Calculates expected encounter value for every neighbor by using contact durations and frequent contacts which determines the forwarders and the number of copies. |
| RPC [48] | 2016 | Estimates reachability probability computed considering centrality measure and encounters rates, which is used in selecting forwarders. |
| EDR [49] | 2016 | Encounter rates with the destination and estimated distance to the destination are used to select forwarders. |
| GSAF [50] | 2016 | Destination dependent identifier is used to spray messages to forwarders. After the message is in the locality of the destination, it is flooded to all neighbors. |
| HPR [51] | 2016 | Delivery predictability of nodes with spraying is the forwarding strategy. |
| E2FA [52] | 2016 | Delivery predictability of nodes and buffer utility are used for choosing forwarders. |
| Multi-S&W Routing [53] | 2017 | Spray and wait routing with next hop selection based on weighted sum of betweenness centrality, friendship index and similarity index. |
| FGAR [54] | 2017 | Adaptive replication and forwarding based on contact prediction and success probability of delivery between contacts in a given time interval. |
| IBR [55] | 2017 | Effects of interactions between nodes in terms of popularity without detection of communities is the forwarding strategy. |
| FC-DFCM [56] | 2017 | Relationship strength of node pairs and contact durations are used in selection of forwarders. |
| EIMCT [57] | 2017 | Social network based contact durations are considered for forwarding decisions. |
| SAPR [58] | 2017 | Social characteristics of nodes and their mobility are the factors for making forwarding decisions. |
| CPR [59] | 2017 | Prediction-based routing decision considering statistical contact information, contact transitivity and instant contact information. |
| TCCB [60] | 2017 | Temporal social contact patterns and temporal centrality prediction are used to select forwarders. |
| FARS [61] | 2018 | Fairness based routing involving weighted factors of contact duration, residual buffer and historical amount of delivered data. |
| ELPFR-MC [62] | 2018 | Energy-aware routing based on node’s residual energy, location prediction and delivery probability. |
| Predict and Forward [63] | 2018 | Next hop selection based on node profiles and attributes along with historical encounters to calculate delivery probability. |
| IoR [64] | 2018 | Average time since the message generation, average distance travelled in hops and delivery predictability of ProPhet are used to select forwarders. |
| CAOF [65] | 2018 | Relay selection is based on node’s activeness to meet nodes in its own community and different communities within a bounded time. |
| CAF [66] | 2018 | Adaptive weighted combination of friendship index, similarity index, centrality, contact strength and trust to find the suitable relays. |
| CbR [67] | 2018 | Nodes belonging to clusters with good delivery capability are preferred than just the node’s utility value. |
| RBES [68] | 2018 | Congestion level at a node and contact history of nodes are together used for forwarding strategy. |
| kROp [69] | 2018 | Partition of neighbors to clusters and next hop is determined by an evaluation function to find the cluster with optimal delivery capability. |
| PBQ [70] | 2018 | Delivery probability is calculated by Poisson based distribution along with consideration of node’s daily routines and mobility patterns. |
| MLProph [71] | 2018 | Enhanced delivery predictability of ProPhet with machine learning by considering node’s popularity, power consumption, speed, location and frequently encountered nodes. |
| EPSoc [72] | 2018 | Social-based epidemic routing where degree centrality of nodes is used for next hop selection. |
| CoSim [73] | 2018 | Cosine similarity of the data packets between nodes are used to find the similarity of the nodes which in turn are used to forward messages. |
| CGR [74] | 2018 | Replication based on scheduled contact patterns with predetermined network prediction. |
| Protocol | Extremely Sparse: 1’Device per km | Sparse: 1–25 Devices per km | Populated: 26–500 Devices per km | Dense: 501–25,000 Devices per km | Very Dense: 25,001–1 Million Devices per km | Extremely Dense: 100 Million Devices or More per km |
|---|---|---|---|---|---|---|
| Epidemic | x | x | x | |||
| Seek and Focus | x | x | ||||
| Spray and Wait | x | x | x | x | ||
| Maxprop | x | x | ||||
| Spray and Focus | x | x | ||||
| Prioritized Epidemic | x | |||||
| CAR | x | x | ||||
| HiBop | x | |||||
| GeoOpps | x | |||||
| Propicman | x | |||||
| Utility Based | x | x | ||||
| Rapid | x | |||||
| ORWAR | x | |||||
| EBR | x | |||||
| SimBeTs | x | |||||
| Prophet | x | x | x | |||
| BubbleRap | x | x | ||||
| dLife | x | |||||
| Sprint | x | |||||
| Scorp | x | |||||
| HBPR | x | |||||
| GAER | x | |||||
| CPR | x | |||||
| Prowait | x | |||||
| CGrAnt | x | |||||
| GSAF | x | x | ||||
| PathSampling | x | |||||
| ABCON | x | |||||
| EER | x | |||||
| RPC | x | |||||
| EDR | x | |||||
| HPR | x | |||||
| FC-DFCM | x | |||||
| EIMST | x | x | ||||
| SAPR | x | |||||
| CAF | x | |||||
| CoSim | x | |||||
| ELPFR-MC | x | |||||
| FARS | x | |||||
| IoR | x | |||||
| kRoP | x | |||||
| MLProph | x | |||||
| PBQ Routing | x | |||||
| PnF | x |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kuppusamy, V.; Thanthrige, U.M.; Udugama, A.; Förster, A. Evaluating Forwarding Protocols in Opportunistic Networks: Trends, Advances, Challenges and Best Practices. Future Internet 2019, 11, 113. https://doi.org/10.3390/fi11050113
Kuppusamy V, Thanthrige UM, Udugama A, Förster A. Evaluating Forwarding Protocols in Opportunistic Networks: Trends, Advances, Challenges and Best Practices. Future Internet. 2019; 11(5):113. https://doi.org/10.3390/fi11050113
Chicago/Turabian StyleKuppusamy, Vishnupriya, Udaya Miriya Thanthrige, Asanga Udugama, and Anna Förster. 2019. "Evaluating Forwarding Protocols in Opportunistic Networks: Trends, Advances, Challenges and Best Practices" Future Internet 11, no. 5: 113. https://doi.org/10.3390/fi11050113
APA StyleKuppusamy, V., Thanthrige, U. M., Udugama, A., & Förster, A. (2019). Evaluating Forwarding Protocols in Opportunistic Networks: Trends, Advances, Challenges and Best Practices. Future Internet, 11(5), 113. https://doi.org/10.3390/fi11050113





