Privacy and Security Issues in Online Social Networks
Abstract
1. Introduction
- All current online social-networking services are web-based, using an Internet connection. Contents are stored on cloud storage through a centralized access management system. These contents can be accessed from anywhere using an Internet connection and web browsers.
- OSN users need to create a public profile for social-network sites as per their predefined format. This profile information is primarily used for the authentication process to log into the social-networking site.
- Almost all existing social-networking services facilitate users in developing their social relations with other users by connecting a user’s profile with others having similar profile information.
- One interesting feature of the existing OSNs is that contents on these sites are user-generated, while OSNs use these contents for business purposes.
2. Motivation
3. Privacy and Security Threats in OSNs
3.1. Classic Threats
3.1.1. Malware
3.1.2. Phishing Attacks
3.1.3. Spam Attacks
3.1.4. Cross-Site Scripting
3.2. Modern Threats
3.2.1. Clickjacking
3.2.2. De-anonymization Attacks
3.2.3. Fake Profiles
3.2.4. Identity Clone Attacks
3.2.5. Inference Attacks
3.2.6. Information Leakage
3.2.7. Location Leakage
3.2.8. Cyberstalking
3.2.9. User Profiling
3.2.10. Surveillance
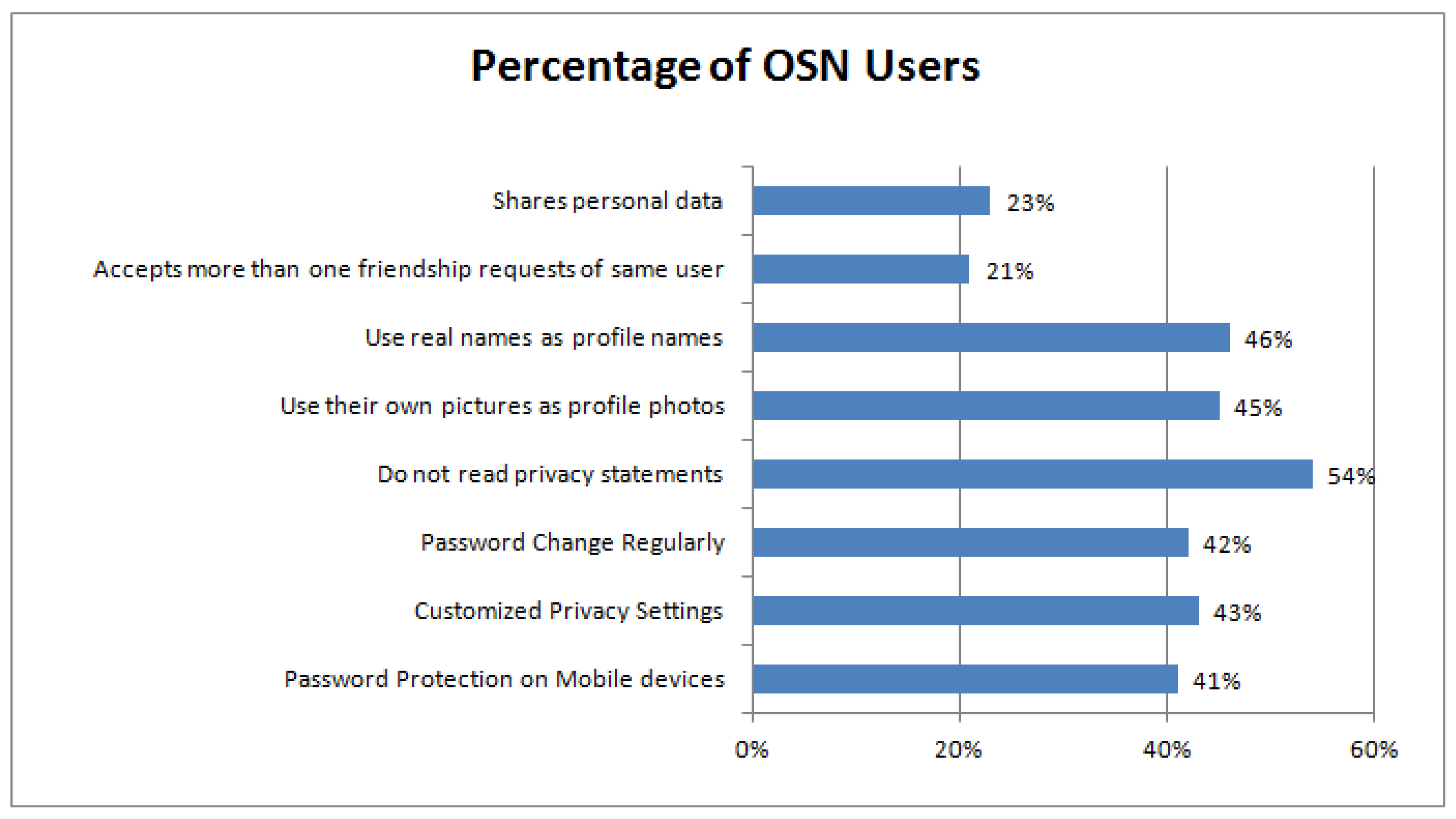
4. Results and Discussion
5. Recommendations
- Privacy settings: Regrettably, 80% of users neither check their OSNs nor know about the privacy of their profile whether they have been offered default privacy settings or adequate privacy that meets the expected level [46]. Although OSNs offer a particular level of access control to data owners via customized settings so as to hide contents from unauthorized access, the default privacy settings of almost all OSNs have restrained privacy [47]. Different social-network users keep the default security and privacy settings [48,49]. OSN users are recommended to keep customized privacy settings and take maximum advantage of the privacy-protection techniques provided by their OSNs. Similarly, users are advised to frequently revise their privacy settings because various OSNs change their privacy settings after every update.
- Personal Information: Once contents are shared through any third party, there is no guarantee that these contents would be private anymore. Therefore, users are required to avoid sharing unnecessary private data on OSNs. Even though a user might understand the importance of privacy, the privacy policies provided by the OSNs often create confusion about the privacy of contents that a user shares on them [50]. For example, research found that 94% of users were sharing contents on OSNs that were intended to be private [51].
- Location Information: A number of mobile apps collect user-location information. This location information can be used by OSNs and may be provided to third parties, primarily for commercial purposes, which leads to privacy leakage. Individuals cannot use such type of location information collected by OSNs, but they often share their locations with their posts. Attackers can misuse this location information by knowing your current place. Therefore, users are recommended to not disclose their location information through OSNs in order to be safe from these potential attackers.
- Antivirus and Antispyware: An OSN is one of the leading means of communication between individuals where content distribution can be easily done [52]. Using the nature of content dissemination through OSNs, malware distribution has grown exponentially [53,54]. Malware is any type of malicious software used to disrupt user operations, illegally gather sensitive information, gain unauthorized access to private data, or inconvenience users through unwanted advertising pop-ups [55,56]. OSN users are recommended to install antivirus and antispyware software on their computers/mobile phones to counter these types of malware and spyware.
- Third-Party Applications: Third-party apps give rise to a number of privacy and security issues because their code is hosted outside the OSN and user controls. This inherently prevents the OSN and users from controlling and monitoring the app’s activities, and to take proactive measures to stop malicious penetration. Since the data are transferred out of the OSN, the utilization of user contents and their distribution is not in the control of the users [57]. Thus, they are required to uninstall third-party applications to protect their information that can go into the wrong hands.
6. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Boyd, D.M.; Ellison, N.B. Social network sites: Definition, history, and scholarship. J. Comput.-Mediat. Commun. 2007, 13, 210–230. [Google Scholar] [CrossRef]
- Obar, J.A.; Wildman, S. Social media definition and the governance challenge: An introduction to the special issue. Telecommun. Policy 2015, 39, 745–750. [Google Scholar] [CrossRef]
- Kaplan, A.M.; Haenlein, M. Users of the world, unite! The challenges and opportunities of Social Media. Bus. Horiz. 2010, 53, 59–68. [Google Scholar] [CrossRef]
- Shozi, N.A.; Mtsweni, J. Big data privacy in social media sites. In Proceedings of the 2017 IST-Africa Week Conference (IST-Africa), Windhoek, Namibia, Southern Africa, 30 May–2 June 2017; pp. 1–6. [Google Scholar]
- Nissenbaum, H. Privacy as Contextual Integrity. Wash. L. Rev. 2004, 79, 101–139. [Google Scholar]
- Davison, H.K.; Maraist, C.C.; Hamilton, R.; Bing, M.N. To Screen or Not to Screen? Using the Internet for Selection Decisions. Empl. Responsib. Rights J. 2012, 24, 1–21. [Google Scholar] [CrossRef]
- Taddicken, M. The ‘Privacy Paradox’ in the Social Web: The Impact of Privacy Concerns, Individual Characteristics, and the Perceived Social Relevance on Different Forms of Self-Disclosure. J. Comput.-Mediat. Commun. 2014, 19, 248–273. [Google Scholar] [CrossRef]
- Marwick, A.E.; Boyd, D. Networked privacy: How teenagers negotiate context in social media. New Media Soci. 2014, 16, 1051–1067. [Google Scholar] [CrossRef]
- Ashtari, S. I Know Who You Are and I Saw What You Did: Social Networks and the Death of Privacy. J. Inf. Priv. Secur. 2013, 9, 80–82. [Google Scholar] [CrossRef]
- Fire, M.; Goldschmidt, R.; Elovici, Y. Online social networks: Threats and solutions. IEEE Commun. Surv. Tutor. 2014, 16, 2019–2036. [Google Scholar] [CrossRef]
- Heymann, P.; Koutrika, G.; Garcia-Molina, H. Fighting spam on social web sites: A survey of approaches and future challenges. IEEE Internet Comput. 2007, 11, 36–45. [Google Scholar] [CrossRef]
- Everett, C. Social media: Opportunity or risk? Comput. Fraud Secur. 2010, 2010, 8–10. [Google Scholar] [CrossRef]
- Alarm, S.; El-Khatib, K. Phishing Susceptibility Detection through Social Media Analytics. In Proceedings of the 9th International Conference on Security of Information and Networks, Newark, NJ, USA, 20–22 July 2016; pp. 61–64. [Google Scholar]
- Nithya, V.; Pandian, S.L.; Malarvizhi, C. A survey on detection and prevention of cross-site scripting attack. Int. J. Secur. Appl. 2015, 9, 139–152. [Google Scholar] [CrossRef]
- Baltazar, J.; Costoya, J.; Flores, R. The Real Face of Koobface: The Largest Web 2.0 Botnet Explained. Trend Micro Threat Research. 2009. Available online: https://www.trendmicro.de/cloud-content/us/pdfs/security-intelligence/white-papers/wp_the-real-face-of-koobface.pdf (accessed on 21 October 2018).
- Alghamdi, B.; Watson, J.; Xu, Y. Toward detecting malicious links in online social networks through user behavior. In Proceedings of the IEEE/WIC/ACM International Conference on Web Intelligence Workshops, Omaha, NE, USA, 13–16 October 2016; pp. 5–8. [Google Scholar]
- Protalinski, E. Chinese Spies Used Fake Facebook Profile to Friend Nato Officials. Available online: https://www.zdnet.com/article/chinese-spies-used-fake-facebook-profile-to-friend-nato-officials/ (accessed on 21 October 2018).
- Dvorak, J.C. LinkedIn Account Hacked. Available online: https://www.pcmag.com/article2/0,2817,2375983,00.asp (accessed on 1 November 2018).
- Miller, S. Sen. Grassley’s Twitter Account Hacked by SOPA Protesters. Available online: https://abcnews.go.com/blogs/politics/2012/01/sen-grassleys-twitter-account-hacked-by-sopa-protesters/ (accessed on 1 November 2018).
- Vishwanath, A. Getting phished on social media. Decis. Support Syst. 2017, 103, 70–81. [Google Scholar] [CrossRef]
- Fire, M.; Katz, G.; Elovici, Y. Strangers intrusion detection-detecting spammers and fake profiles in social networks based on topology anomalies. Human J. 2012, 1, 26–39. [Google Scholar]
- Egele, M.; Stringhini, G.; Kruegel, C.; Vigna, G. Towards detecting compromised accounts on social networks. IEEE Trans. Dependable Secure Comput. 2017, 14, 447–460. [Google Scholar] [CrossRef]
- Grier, C.; Thomas, K.; Paxson, V.; Zhang, M. @spam: The underground on 140 characters or less. In Proceedings of the 17th ACM conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 27–37. [Google Scholar]
- Gao, H.; Hu, J.; Wilson, C.; Li, Z.; Chen, Y.; Zhao, B.Y. Detecting and characterizing social spam campaigns. In Proceedings of the 10th ACM SIGCOMM Conference on Internet Measurement, Melbourne, Australia, 1–3 November 2010; pp. 35–47. [Google Scholar]
- Thomas, K.; Grier, C.; Ma, J.; Paxson, V.; Song, D. Design and evaluation of a real-time URL spam filtering service. In Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, 22–25 May 2011; pp. 447–462. [Google Scholar]
- Gao, H.; Chen, Y.; Lee, K.; Palsetia, D.; Choudhary, A.N. Towards Online Spam Filtering in Social Networks. In Proceedings of the 19th Annual Network & Distributed System Security Symposium, San Diego, CA, USA, 5–8 February 2012; pp. 1–16. [Google Scholar]
- Gupta, S.; Gupta, B.B. Cross-Site Scripting (XSS) attacks and defense mechanisms: Classification and state-of-the-art. Int. J. Syst. Assur. Eng. Manag. 2017, 8, 512–530. [Google Scholar] [CrossRef]
- Faghani, M.R.; Nguyen, U.T. A study of XSS worm propagation and detection mechanisms in online social networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1815–1826. [Google Scholar] [CrossRef]
- Lundeen, R.; Ou, J.; Rhodes, T. New Ways Im Going to Hack Your Web APP. Black Hat Abu Dhabi. Available online: https://www.blackhat.com/html/bh-ad-11/bh-ad-11-archives.htmlLundeen (accessed on 1 November 2018).
- Ding, X.; Zhang, L.; Wan, Z.; Gu, M. A brief survey on de-anonymization attacks in online social networks. In Proceedings of the IEEE International Conference on Computational Aspects of Social Networks (CASoN 2010), Taiyuan, China, 26–28 September 2010; pp. 611–615. [Google Scholar]
- Gulyás, G.G.; Simon, B.; Imre, S. An Efficient and Robust Social Network De-anonymization Attack. In Proceedings of the Workshop on Privacy in the Electronic Society, Vienna, Austria, 24 October 2016; pp. 1–11. [Google Scholar]
- Wani, M.A.; Jabin, S.; Ahmad, N. A sneak into the Devil’s Colony-Fake Profiles in Online Social Networks. Available online: https://arxiv.org/ftp/arxiv/papers/1705/1705.09929.pdf (accessed on 29 October 2018).
- Perlroth, N. Fake Twitter Followers Become Multimillion-Dollar Business. The New York Times. 9 April 2013. Available online: https://bits.blogs.nytimes.com/2013/04/05/fake-twitter-followers-becomes-multimillion-dollar-business/?_php=true&_type=blogs&ref=technology&_r=0 (accessed on 1 November 2018).
- Kharaji, M.Y.; Rizi, F.S.; Khayyambashi, M.R. A New Approach for Finding Cloned Profiles in Online Social Networks. arXiv, 2014; arXiv:1406.7377. [Google Scholar]
- Lewis, J. How spies used Facebook to Steal NATO Chief’s Details. The Telegraph, 20 March 2012. [Google Scholar]
- Heatherly, R.; Kantarcioglu, M.; Thuraisingham, B. Preventing private information inference attacks on social networks. IEEE Trans. Knowl. Data Eng. 2013, 25, 1849–1862. [Google Scholar] [CrossRef]
- Viswanath, B.; Bashir, M.A.; Crovella, M.; Guha, S.; Gummadi, K.P.; Krishnamurthy, B.; Mislove, A. Towards Detecting Anomalous User Behavior in Online Social Networks. In Proceedings of the USENIX Security Symposium, San Diego, CA, USA, 20–22 August 2014; pp. 223–238. [Google Scholar]
- Torabi, S.; Beznosov, K. Privacy Aspects of Health Related Information Sharing in Online Social Networks. In Proceedings of the 2013 USENIX Conference on Safety, Security, Privacy and Interoperability of Health Information Technologies, Washington, DC, USA, 12 August 2013; p. 3. [Google Scholar]
- Scism, L.; Maremont, M. Insurers Test Data Profiles to Identify Risky Clients. The Wall Street Journal, 20 November 2010. [Google Scholar]
- Humphreys, L. Mobile social networks and social practice: A case study of Dodgeball. J. Comput.-Mediat. Commun. 2007, 13, 341–360. [Google Scholar] [CrossRef]
- D’Ovidio, R.; Doyle, J. A study on cyberstalking: Understanding investigative hurdles. FBI Law Enforc. Bull. 2003, 72, 10–17. [Google Scholar]
- Burke Winkelman, S.; Oomen-Early, J.; Walker, A.D.; Chu, L.; Yick-Flanagan, A. Exploring Cyber Harassment among Women Who Use Social Media. Univers. J. Public Health 2015, 3, 194–201. [Google Scholar] [CrossRef]
- Ali, S.; Rauf, A.; Islam, N.; Farman, H.; Khan, S. User Profiling: A Privacy Issue in Online Public Network. Sindh Univ. Res. J. (Sci. Seri.) 2017, 49, 125–128. [Google Scholar]
- Fuchs, C.; Trottier, D. Towards a theoretical model of social media surveillance in contemporary society. Commun. Eur. J. Commun. Res. 2015, 40, 113–135. [Google Scholar] [CrossRef]
- Gross, R.; Acquisti, A. Information revelation and privacy in online social networks. In Proceedings of the 2005 ACM workshop on Privacy in the Electronic Society, Alexandria, VA, USA, 7–10 November 2005; pp. 71–80. [Google Scholar]
- Zhang, W.; Al Amin, H. Privacy and security concern of online social networks from user perspective. In Proceedings of the International Conference on Information Systems Security and Privacy (ICISSP2015), ESEO, Angers, Loire Valley, France, 9–11 February 2015; pp. 246–253. [Google Scholar]
- Carminati, B.; Ferrari, E.; Heatherly, R.; Kantarcioglu, M.; Thuraisingham, B. Semantic web-based social network access control. Comput. Secur. 2011, 30, 108–115. [Google Scholar] [CrossRef]
- Strater, K.; Richter, H. Examining privacy and disclosure in a social networking community. In Proceedings of the 3rd Symposium on Usable Privacy and Security, Pittsburgh, PA, USA, 18–20 July 2007; pp. 157–158. [Google Scholar]
- Miltgen, C.L.; Peyrat-Guillard, D. Cultural and generational influences on privacy concerns: A qualitative study in seven European countries. Eur. J. Inf. Syst. 2014, 23, 103–125. [Google Scholar] [CrossRef]
- Fletcher, D. How Facebook Is Redefining Privacy. Available online: http://content.time.com/time/magazine/article/0,9171,1990798,00.html (accessed on 10 November 2018).
- Madejski, M.; Johnson, M.; Bellovin, S.M. A study of privacy settings errors in an online social network. In Proceedings of the IEEE International Conference on Pervasive Computing and Communications Workshops, Lugano, Switzerland, 19–23 March 2012; pp. 340–345. [Google Scholar]
- Penni, J. The future of online social networks (OSN): A measurement analysis using social media tools and application. Telemat. Inform. 2017, 34, 498–517. [Google Scholar] [CrossRef]
- Boshmaf, Y.; Muslukhov, I.; Beznosov, K.; Ripeanu, M. Design and analysis of a social botnet. Comput. Netw. 2013, 57, 556–578. [Google Scholar] [CrossRef]
- Makridakis, A.; Athanasopoulos, E.; Antonatos, S.; Antoniades, D.; Ioannidis, S.; Markatos, E.P. Understanding the behavior of malicious applications in social networks. IEEE Netw. 2010, 24, 14–19. [Google Scholar] [CrossRef]
- Tam, K.; Feizollah, A.; Anuar, N.B.; Salleh, R.; Cavallaro, L. The evolution of android malware and android analysis techniques. ACM Comput. Surv. 2017, 49, 76. [Google Scholar] [CrossRef]
- Provos, N.; McNamee, D.; Mavrommatis, P.; Wang, K.; Modadugu, N. The Ghost in the Browser: Analysis of Web-based Malware. In Proceedings of the First Workshop on Hot Topics in Understanding Botnets (HotBots’07), Cambridge, MA, USA, 10 April 2007; p. 4. [Google Scholar]
- Chaabane, A.; Ding, Y.; Dey, R.; Kaafar, M.A.; Ross, K.W. A Closer Look at Third-Party OSN Applications: Are They Leaking Your Personal Information? In Proceedings of the 15th International Conference on Passive and Active Network Measurement, Los Angeles, CA, USA, 10–11 March 2014; pp. 235–246. [Google Scholar]
| OSN | Total Active Users in Millions |
|---|---|
| 2047 | |
| YouTube | 1500 |
| 1200 | |
| 938 | |
| 700 | |
| 328 | |
| Skype | 300 |
| Viber | 260 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, S.; Islam, N.; Rauf, A.; Din, I.U.; Guizani, M.; Rodrigues, J.J.P.C. Privacy and Security Issues in Online Social Networks. Future Internet 2018, 10, 114. https://doi.org/10.3390/fi10120114
Ali S, Islam N, Rauf A, Din IU, Guizani M, Rodrigues JJPC. Privacy and Security Issues in Online Social Networks. Future Internet. 2018; 10(12):114. https://doi.org/10.3390/fi10120114
Chicago/Turabian StyleAli, Shaukat, Naveed Islam, Azhar Rauf, Ikram Ud Din, Mohsen Guizani, and Joel J. P. C. Rodrigues. 2018. "Privacy and Security Issues in Online Social Networks" Future Internet 10, no. 12: 114. https://doi.org/10.3390/fi10120114
APA StyleAli, S., Islam, N., Rauf, A., Din, I. U., Guizani, M., & Rodrigues, J. J. P. C. (2018). Privacy and Security Issues in Online Social Networks. Future Internet, 10(12), 114. https://doi.org/10.3390/fi10120114







