Abstract
In graph theory, the study of domination sets has garnered significant interest due to its applications in network design and analysis. Consider a graph ; a subset of its vertices is a total dominating set (TDS) if, for each , there exists an edge in connecting x to at least one vertex within this subset. If the subgraph induced by the vertices outside the TDS has no edges, the set is called a total outer-independent dominating set (TOIDS). The total outer-independent domination number, denoted as , represents the smallest cardinality of such a set. Deciding if a given graph has a TOIDS with at most r vertices is an NP-complete problem. This study introduces new lower and upper bounds for and presents an exact solution approach using integer linear programming (ILP). Additionally, we develop a heuristic and a procedure to efficiently obtain minimal TOIDS.
1. Introduction
The study of domination problems constitutes a fundamental line of research within graph theory, offering both deep theoretical insights and practical applications. Over recent decades, attention in this field has grown significantly due to its wide range of applications across various scientific disciplines, including social sciences, linear algebra, computational complexity, communication networks, algorithm design, optimization problems, and complex ecosystems (see [1,2]). In this context, several domination parameters have been introduced in previous studies, often involving the combination of multiple parameters [1,3,4,5]. This paper examines a particular parameter that combines the well-known notions of independence and total domination. Furthermore, we investigate the properties of this parameter from both computational and combinatorial perspectives.
In this paper, we consider simple graphs with size and order , where A is a subset of and is a vertex. The subgraph induced by A is represented as . The symbol denotes the set of neighbors of x contained within A, formally defined as . Furthermore, represents the closed neighborhood of x within A, defined as . We also define as the cardinality of , i.e., . The degree of x is denoted as . For ease of notation, we will often use and to refer to and , respectively. The maximum degree of is defined as , and the minimum degree as . Vertices are leaf vertices if , while support vertices are any vertices adjacent to leaf vertices. and denote the sets of support and leaf vertices, respectively.
A set is an independent set of if is an edgeless graph, and , the independence number, is the size of the largest independent set in [6,7,8].
A nonempty set T is called a total dominating set (TDS) if, for every , there exists an edge such that . The total domination number, denoted by , is the smallest number of elements in any TDS of . A TDS containing exactly vertices is referred to as a -set. Since total domination cannot be defined for graphs containing isolated vertices, all graphs considered in this paper are assumed to have no isolated vertices. Please note that by the previous definitions, . For additional details on total domination, refer to [3,8,9,10,11].
If T is a TDS such that the subgraph induced by forms an independent set, then T is called a total outer-independent dominating set (TOIDS). The total outer-independent domination number, represented as , refers to the smallest cardinality of any TOIDS. A TOIDS with cardinality is called a -set. This concept was first presented in [12] and was briefly studied in [13], where it was referred to as the total co-independent domination number. Please note that by the previous definitions, , for .
If , , …, with are the connected components of a graph with , then any TOIDS of is the union of TOIDSs from each connected component , for . This is expressed in the following simple result.
Remark 1.
Let , , …, with be the components of a non-connected graph that has no isolated vertices. Then
Aligned with the previous remark, we will henceforth restrict our analysis to TOIDS in nontrivial connected graphs.
The study of TOIDS has gained considerable attention in recent years, owing to their valuable practical applications and extensive theoretical properties [4,12,13,14,15]. The objective is to identify a TOIDS with the smallest cardinality, which is an optimal total outer-independent dominating set. However, as demonstrated in [4], this problem has been proven to be -complete. A problem is considered NP-complete if it is part of the NP class (nondeterministic polynomial time), and every other NP problem can be reduced to it in polynomial time. In simpler terms, an NP-complete problem is as hard as any other problem within NP. If a polynomial-time solution is discovered for any NP-complete problem, then all problems in NP would be solvable in polynomial time. Since no polynomial-time algorithm is currently known for NP-complete problems, research often focuses on approximation algorithms, heuristics, and integer programming formulations to obtain efficient solutions for practical instances.
In [5], a polynomial-time algorithm is proposed to compute for trees. In addition, refs. [4,14,15,16] have presented various upper and lower bounds for the problem. As far as we know, no further results have been reported concerning this issue. In particular, to the best of our knowledge, no exact or approximation algorithms have been previously suggested for the TOIDS problem in general graph classes.
This paper presents new lower and upper bounds for . We also propose an exact solution approach using an integer linear programming (ILP) formulation alongside a heuristic method and a purification procedure to reduce the size of the total outer-independent dominating set produced by the heuristic. Additionally, we provide experimental results and computational analyses to assess the performance of both the ILP and heuristic methods across 500 graph instances. Our ILP approach successfully found optimal solutions for graphs with up to 9100 vertices. Specifically, we computed for the 500 graph with , which were randomly generated and can now be used as benchmarks for future research. These values and the corresponding instances are publicly available in [17]. Interestingly, in about 28.69% of the cases where the exact algorithm produced an optimal solution, the heuristic also yielded an optimal result. For the remaining instances, the average absolute error was roughly 1.012 vertices, with an average approximation ratio of 1.0032.
In summary, our work contributes to the understanding and advancement of the total outer-independent dominating set problem, offering insights into its structural properties and providing a practical algorithm for its computation. Section 2 explores new upper and lower bounds for and establishes relationships with other domination and independence parameters, along with an ILP formulation. Section 3 presents our heuristic, defines several graph families for which it provides an optimal solution, and outlines a purification process. Finally, Section 4 provides a detailed overview of our experimental results.
2. Bounds and Exact Results for
2.1. Bounds
A subset is a defensive k-alliance, with , if for every . The boundary of is the set . A subset is a offensive k-alliance, with , if for every . A global offensive k-alliance is an offensive k-alliance S such that . The global offensive k-alliance number of G, represented by , is the smallest size of any global offensive k-alliance in the graph G. A subset is called a powerful k-alliance if it acts as both a defensive k-alliance and an offensive -alliance. The powerful k-alliance number of G, represented by , is the minimum size of any powerful k-alliance in the graph G. A -set is a set S of cardinality such that S is a powerful k-alliance of G. Alliances in graphs have been studied extensively by many researchers. Some important results can be found in [6,18,19,20,21].
Theorem 1.
For any nontrivial graph G of order n,
Proof.
We now prove the lower bound. Let T be a -set. Observe that since T is a TDS. This fact, along with the definition of T, leads to , which is an independent set in G. It follows that for every . Hence, T is a global offensive -alliance of G. Thus, , as desired.
Next, we establish the upper bound. Let S be a -set. Since for every , we deduce that . Hence, is an independent set of G. In addition, since G is a connected graph, we obtain that . Therefore, is an independent set. Finally, from the fact that for any , we deduce that S is a total dominating set of G. Thus, S is a TOIDS of G. Therefore, . □
The bounds in Theorem 1 are tight. For example, the lower bound is attained in complete graphs and wheel graphs. On the other hand, the upper bound is attained in complete graphs and graphs belonging to , where is the family of graphs formed as follows. Let be an integer. if is formed by a cycle and k vertices adjacent to only three vertices in the cycle .
Theorem 2.
For any nontrivial graph G of size m,
Proof.
Let T be a -set. Since is an edgeless graph and T is a TDS of G, we deduce that
Which implies that . In addition, we observe that . Therefore, . Therefore, , as desired. □
The corona product of two graphs and , denoted as , is constructed by taking one instance of and replicas of , and then connecting each vertex in the ith replica of to the ith vertex of with an edge [22,23]. The bound in Theorem 2 is attained in the corona product of , where k is a positive integer and is the empty graph of k vertices.
A subset is called a 2-packing of G if for all distinct vertices . The 2-packing number of G, represented by , is the largest size of any 2-packing in G. A -set is a 2-packing of cardinality . This parameter has been studied in [24,25,26].
Theorem 3.
For any nontrivial graph G of order n,
Proof.
Let P be a -set such that is minimum among all -sets. We claim that is a TOIDS. Since P is a packing set of G, we have that P is an independent set. In addition, for any . Therefore, we only need to prove that has no isolated vertex. Let . If , then we deduce that , as desired. Now suppose that . If , then the set is a -set such that , a contradiction. Hence, , as desired. Therefore,
Next, we establish the upper bound. Observe that
From this inequality and the fact that we deduce that It follows that . □
The bounds in Theorem 3 are tight. For example, the upper bound is attained in the double-star graphs. In addition, the lower bound is attained in the corona product of , where r is a positive integer and is the empty graph of r vertices.
Proposition 1.
Let G be a nontrivial graph of order . If G is a triangle-free graph that is different from , then .
Proof.
We consider two cases.
Case 1. G is a graph with a connected structure. Suppose that G is a tree. If , then . Hence, . If , then , as desired. From now on, suppose that G has a cycle of minimum length . If , then is an independent set. Thus, . Now, suppose . Since and , it follows that . In addition, by minimality of C and since G is triangle-free, there exists such that v is adjacent to at most two nonadjacent vertices of . We assume that without loss of generality. The set is an independent set of G. Thus, we obtain that , as desired.
Case 2. G is a disconnected graph. If it consists of more than two connected components, then it is evident that . Therefore, suppose that G has two connected components, and . If , then and are complete graphs. Since , we deduce that or . As a consequence, G has a triangle, a contradiction. Hence or , which implies that , as desired. □
Consider a graph G with , and let denote its complement. For every , we denote by the vertex corresponding to v in . The complementary prism, denote by , is the graph with vertex set and edge set . Various domination parameters have been analyzed in the context of complementary prisms. For example, in [27,28,29]. Figure 1 shows a graph G and . The set of black colored vertices describes a -set.
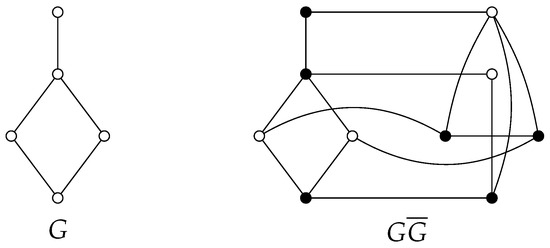
Figure 1.
Graph G and .
The following theorem provides the exact value for . For this purpose, we introduce the following family of graphs. For any integer , let denote the family consisting of complete graphs and graphs G of order k in which any two minimum independent sets and of G and , respectively, satisfy . Please note that any two minimum independent sets and of G and , respectively, satisfy .
Theorem 4.
For any nontrivial graph G with ,
Proof.
First, observe that and . Therefore, from now on we suppose that . Now, we proceed to prove that
Let D be a -set and let and . Observe that and are independent sets of G and , respectively. As a consequence,
Furthermore, if , then and cannot both be independent sets of minimum cardinality of G and , respectively. Hence, or . In any case, we obtain that
Using Equations (1) and (2), we derive that
Now we proceed to prove that
Let and be independent sets of minimum cardinality of G and (respectively) such that is minimum. Let and let . We consider the set
We claim that S is a TOIDS of . Observe that is an independent set of . Therefore, we only need to prove that has no isolated vertex. Let . If , then v is dominated by . Now suppose that . If or , then there exists such that and . As a consequence, v is dominated by . On the other hand, suppose that and . By Proposition 1 we have that , which leads to . Hence, there exists such that . In addition, we observe that . Thus, v is dominated by u, as desired. Analogously, we deduce that every is dominated by S. Therefore, S is a TOIDS of , which implies that
□
A split graph is a type of graph in which the vertex set is divided into a maximal clique K and an independent set I [30].
Proposition 2.
For any nontrivial connected split graph such that , the following statements hold.
- (i)
- I is a maximal independent set of G if and only if .
- (ii)
- I is not a maximal independent set of G if and only if .
Proof.
First, we observe that K is a TOIDS of G, which implies that . Let T be a -set such that is maximum among all -sets. If , then . If , then there exists . This implies that . It follows that
Thus,
We now move on to proving (i). Suppose that I is a maximal independent set of G. By Equation (4) we only need to prove that . Since I is a maximal independent set, every satisfies . This fact together with (3) lead to , as desired. Now, suppose that . If I is not a maximal independent set of G, then there exists such that . As a consequence, is a TOIDS of G. It follows that , a contradiction. Therefore, I is a maximal independent set of G, which completes the proof of (i). Finally, observe that (ii) is a consequence of (i) and Equation (4). □
If we remove the vertices and in the graph from Figure 2, then , and the vertex can be removed from the -set. Then, .
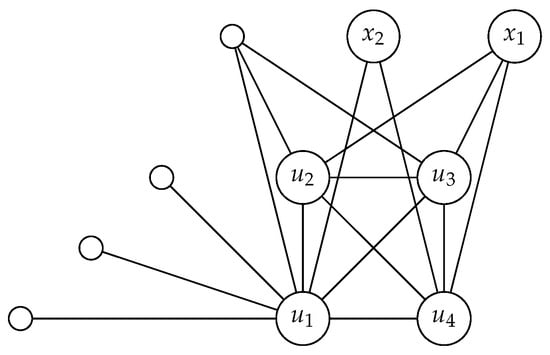
Figure 2.
A split graph with and .
A set is an independent dominating set of G if every vertex in has a neighbor in S, and S is an independent set. The independent domination number of G, represented by , is the smallest size of any independent dominating set in G. Detailed information can be found in the survey [31].
Proposition 3.
Let G be a nontrivial graph of order n and let S be a -set. The following statements hold.
- (i)
- If is a maximal independent set of G, then .
- (ii)
- If is not a maximal independent set of G, then .
Proof.
First, we proceed to prove (i). Suppose that is a maximal independent set. Please note that any vertex of S has a neighbor in . Hence, is an independent dominating set of G. Thus, , as desired.
Now, we proceed to prove (ii). Suppose that is not a maximal independent set of G. Therefore, there exists such that . Hence, is an independent set of G. Thus, , as desired. □
Now, we present the exact results for several well-known graph families, as proposed in [12,13]. These results provide valuable insights into the behavior of for specific graph structures. Furthermore, in the next subsection, we propose an ILP formulation to find a -set.
Proposition 4.
The following statements hold for any integer .
- (i)
- .
- (ii)
- .
- (iii)
- .
- (iv)
- .
- (v)
- If r is a positive integer, then .
These results contribute to a better understanding of the total outer-independent domination number in various graph families, including complete graphs, cycles, paths, and wheel graphs.
2.2. ILP Formulation
In this subsection, we propose the following ILP formulation for the problem we are studying (TOIDS). Consider a graph with order n, and its adjacency matrix is given by: if , and in the other case. Given a TOIDS T of cardinality and , our decision variables are defined in the following way:
The TOIDS problem can now be expressed as follows:
We have constraints: the n constraints of type (7) ensure that for each , at least one vertex in T is adjacent to j, while the n constraints of type (8) ensure that no vertex in has a neighbor in . Please note that in the adjacency matrix A, we define for all i. As a result, when , the term evaluates to zero, ensuring that self-loops do not affect constraints of type (7), i.e., vertices do not dominate themselves. Additionally, constraints (9) and (10) limit the search space (feasible region), ensuring that the cardinality of the generated solutions is between the lower bound L and the upper bound U. We can use the lower and upper bounds proposed in Section 2 to determine L and U. It should be noted that, in practice, the heuristic proposed in Section 3 provided a better upper bound U than the theoretical bounds for the instances analyzed.
3. Heuristic Algorithm
Now, we present our heuristic for approximating a total outer-independent dominating set. This heuristic is divided into two stages: Stage 1 follows a greedy methodology to find a TOIDS, and Stage 2 consists of a purification procedure that delivers a minimal TOIDS. Stage 1 is further divided into two fundamental parts: the first part constructs a total dominating set, and the second part updates this set to ensure that its complement is independent.
We need a few definitions to describe our heuristic. We denote by the TOIDS formed by the heuristic in iteration h. The dominated set in iteration h is denoted by ; this vertex set is formed by the vertices that have at least one neighbor in . Please note that in the final iteration of Stage 1, the set is an independent set. Finally, denotes the vertex set that has no neighbors in in iteration h, i.e., .
In general, our heuristic is a greedy algorithm that runs over several iterations. The iterative process in Stage 1 is guaranteed to converge, as in each iteration, a vertex is selected from and added to , reducing the size of or . Since these sets are subsets of , the number of iterations is at most n, ensuring termination in a finite number of steps. Below, we provide a detailed description of our heuristic.
First, we select two vertices where u is the vertex with the highest degree in and v is its neighbor with the highest number of neighbors not dominated by u. Thus, initially , and . Notice that these are disjoint sets and .
Remark 2.
The sets , and are disjoint and .
Lemma 1.
If then and is a minimum total dominating set.
Proof.
By Remark 2 and , it follows immediately that . This implies that all vertices in have a neighbor in . Please note that by the construction of the algorithm, . Since , then is minimum, a TDS cannot contain fewer than two vertices. □
A direct consequence of the previous lemma is the following observation.
Remark 3.
If and is an independent set, then is a minimum TOIDS.
The initial sets are updated iteratively at each iteration , resulting in the current sets of vertices , , and , where is the partial total outer-independent dominating set. Each iteration begins if or is not an independent set. In the first iterative part of Stage 1, for each iteration, we choose a vertex such that is as large as possible. Then, we add v to , i.e., . Please note that v is chosen to maximize the number of adjacent vertices among those that do not yet have neighbors in . At this point, the sets and are updated accordingly.
In the second iterative part of Stage 1, each iteration runs if the set is not yet an independent set. Thus, we choose a vertex such that is as large as possible, then we add u to , i.e., . Please note that u is the vertex that has the most neighbors in . At this point, the sets and are updated accordingly.
At the end of Stage 1, we obtain a TOIDS of the graph G in . Up to this point, the algorithm may have included redundant vertices in . Therefore, in Stage 2, we proceed to apply a purification procedure that yields a minimal TOIDS of G. The purification procedure is described in Section 3. The pseudo-code for the heuristic is shown as follows (see Algorithm 1).
| Algorithm 1 Heuristic TOID |
|
Theorem 5.
Stage 1 of the Heuristic TOID runs in at most iterations, taking time.
Proof.
The total number of iterations in the loops of Stage 1 is bounded by . Please note that the bound is reached for the graph and . Then, Stage 1 performs iterations.
In iteration , for each vertex , the neighborhood is determined by summing all the entries equal to 1 in the row associated with vertex u. The selection of the maximum takes time. Similarly, for each vertex , the value is computed by summing all the entries equal to 1 in the row corresponding to vertex v, provided that the entries for vertex u are not both 1.
In each iteration, , is calculated for every vertex by counting all the 1 entries in the row corresponding to that vertex, if the entries are simultaneously 1 in . Similarly, is calculated for every vertex . Given that each row consists of n entries and there are fewer than n rows to check, the computation of or , along with the selection of the maximum, requires time. Following the same idea, we can determine if the set is independent if, for every vertex , it holds that .
Please note that and . Therefore, the total number of iterations in the loops of Stage 1 is bounded by n. Hence, Stage 1 finds a total outer-independent dominating set in time. □
Proposition 5.
Let G be a connected split graph with maximum clique K and independent set I. Then, the Heuristic TOID finds an optimal solution for the graph G if, in iteration i of the second iterative part of Stage 1, there is no vertex such that .
Proof.
Clearly, every vertex in K has a higher degree than the vertices in . Then, in iteration , Heuristic TOID will select the vertices such that is maximized, forming the set . Since dominates all the vertices in K, and is an independent set, in every iteration of the first iterative part of Stage 1, is a vertex in with the largest number of undominated neighbors in , and is updated as . The first iterative part stops when all the vertices in are dominated.
If , then is an independent set, and the second iterative part of Stage 1 is skipped, proceeding directly to Stage 2. If there exists a vertex such that , the procedure removes this vertex from the set and returns a set with vertices. Otherwise, the cardinality of cannot be reduced, and . In either case, by the proof of Proposition 2, this is an optimal solution.
If , then is not an independent set and has vertices from K in . Please note that these r vertices form a graph. Therefore, in the second iterative part of Stage 1, since in every iteration , there is no vertex such that , vertices from the set are removed from and added to to ensure that becomes an independent set. Then, . The current set does not allow purification by the proof of Proposition 2, and is an optimal solution. □
Purify Procedure
In Theorem 2.3 of [13], Soner et al. demonstrate that:
Lemma 2.
Let T be a TOIDS. T is a minimal set if and only if, for each vertex , one of the following conditions holds:
- (i)
- There exists a vertex such that .
- (ii)
- There exists a vertex that is adjacent to x.
Following these ideas, the objective of this subsection is to propose a purification procedure that yields a minimal total outer-independent domination set (see Algorithm 2). Below are two definitions that we will use in the purification procedure. The private neighborhood of a vertex , denoted by , is given by
A vertex in is referred to as a private neighbor of x. These definitions are equivalent to condition in Lemma 2.
Please note that all vertices in the set formed in this way satisfy one of the conditions proposed in Lemma 2, making it a minimal total outer-independent dominating set for the graph G. Using similar reasoning as in the proof of Theorem 5, it follows that the purification procedure can be executed in time .
Theorem 6.
Purify runs in at most k iterations, and its time complexity is .
| Algorithm 2 Purify |
|
4. Experimental Results
This section provides an overview of our computational analysis. We implemented the ILP formulation and Heuristic TOID in C++ using the CPLEX library, both running on a Windows 11 operating system for 64-bit architecture. The experiments were conducted on a personal computer equipped with an Intel Core i7-9750H processor (2.6 GHz) and 16 GB of DDR4 RAM. Our algorithm was tested on a set of 500 benchmark instances from [17,32,33].
Since no benchmark instances for the TOIDS problem previously existed, we used optimal values from CPLEX alongside established upper and lower bounds to evaluate heuristic performance. While our computational experiments provide valuable insights into the performance of the proposed heuristic and ILP formulation, some limitations should be considered. First, since no standard benchmark instances existed for this problem, the generated dataset may not fully represent the characteristics of real-world graphs. Second, computational constraints limited the exact resolution of larger instances using CPLEX, which may affect the evaluation of the heuristic’s performance in such cases. Finally, further experiments on graphs from real-world applications would be necessary to assess the generalizability of our approach beyond the tested instances.
Table 1 presents the values of for 39 instances out of the 500 analyzed using CPLEX. These instances were randomly selected from the full dataset. Additionally, T and represent the solutions provided by our heuristic in Stages 1 and 2, respectively. The values of shown in Table 1 can be compared with the solutions obtained by the heuristic. This comparison enables an assessment of the accuracy and effectiveness of the heuristic in estimating for the analyzed instances.

Table 1.
Comparison of with heuristic solutions.
Figure 3 presents a comparison between the solutions produced by our Heuristic TOID and the optimal values obtained by CPLEX for instances with up to 9100 vertices. Our heuristic successfully found the optimal solution in 28.69% of the instances. For the cases where the optimal solution was not achieved, the average absolute error was approximately 1.012 vertices.
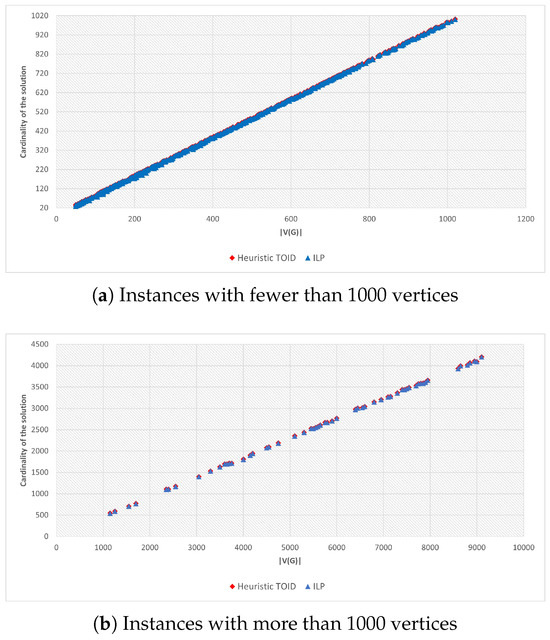
Figure 3.
Approximation results vs. .
Figure 4 shows the approximation ratio of our heuristic in those instances where the optimal solution was not found. For these instances, the minimum approximation ratio was 1.00028, the maximum was 1.05555, and the average was 1.0032. Figure 4 also reveals a clear trend toward reducing the approximation ratio as the number of vertices increases. This result highlights the strong performance of our heuristic in terms of approximation ratio for instances with a larger number of vertices. The low approximation ratios demonstrate the high quality of our heuristic in efficiently providing near-optimal solutions.
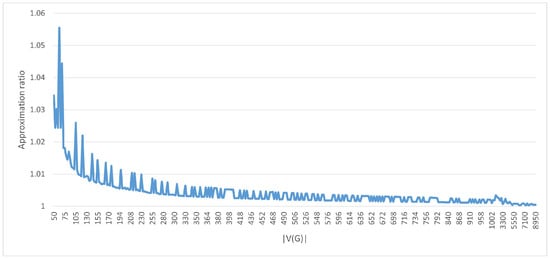
Figure 4.
Approximation Ratio.
The execution time of CPLEX and the heuristic varies depending on the density of the analyzed instances. In our analysis, graph density is defined as . Figure 5a,b compare the time taken by CPLEX to find with the time taken by the heuristic to find a feasible solution, considering graph density. Figure 5a shows the execution time for instances with a density of less than . For these instances, CPLEX performed better; on average, it was approximately times faster than the heuristic. CPLEX successfully solved instances of this type with up to 9100 vertices. However, for instances with more than 9100 vertices, CPLEX ran out of available memory on the system and failed to find the optimal solution. Whereas the heuristic was not constrained by memory capacity, successfully solving instances with more than 14,000 vertices. Figure 5b shows the execution time for instances with a density greater than . For these instances, the heuristic outperformed CPLEX, being approximately times faster on average. CPLEX was able to solve instances of this type with up to 1100 vertices, while the heuristic successfully solved instances with up to 14,100 vertices in less than two hours without reaching the memory limit (see BD4_xx instances in Table 1). In instances where the heuristic identified the optimal solution, i.e., a -set, regardless of the instance density, the heuristic was, on average, 594 times faster than CPLEX. These findings, along with the excellent approximation ratios shown in Figure 4, emphasize the critical role of heuristics in solving large-scale problems that are computationally infeasible for exact methods.
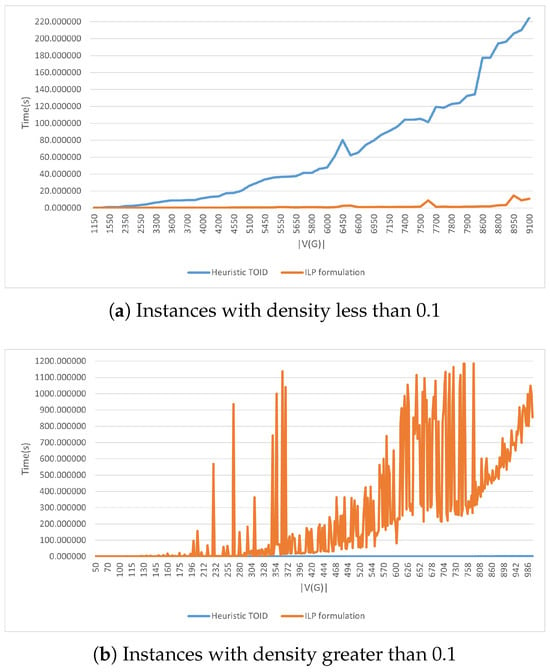
Figure 5.
Time ILP formulation vs. Heuristic TOID.
The results reported for our heuristic include the purification stage (Stage 2). The purification process proved effective in practice, as illustrated in Figure 6. In this figure, and represent the number of vertices in the TOIDS before and after purification, respectively. In 99.59% of the analyzed instances, Stage 1 did not yield minimal TOIDS, i.e., Stage 1 produced TOIDS with redundant vertices. The purification process in Stage 2 of our heuristic exhibited different behaviors depending on the graph density. For graphs with a density lower than 0.1, an average of 191.68 vertices were removed, with a minimum of 28 and a maximum of 316. In these instances, on average, 6.81% of the vertices provided by Stage 1 were eliminated. In contrast, for graphs with a density greater than 0.1, the purification process had a significantly smaller impact. The average number of vertices removed was only 2.80, with a minimum of 0 and a maximum of 5. In these cases, the purification step reduced, on average, only 1.09% of the vertices provided by Stage 1. These results highlight that the purification procedure is notably more effective in sparse graphs, where a larger proportion of vertices can be removed, while in denser graphs, the final solution remains almost unchanged after Stage 2.
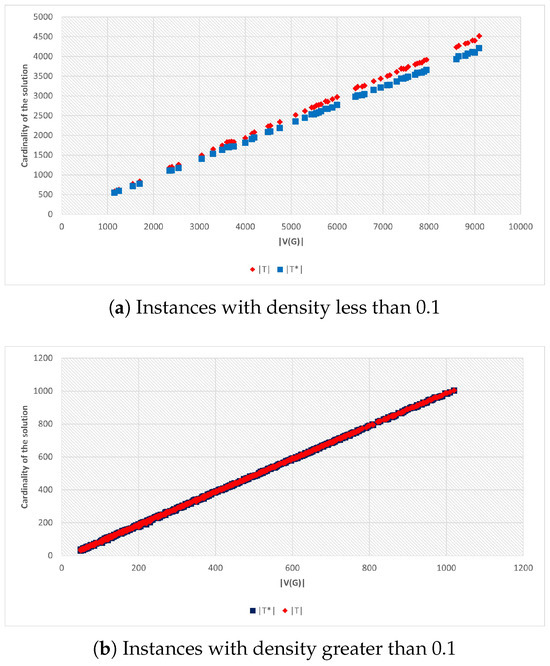
Figure 6.
Stage 1 vs. Stage 2 of Heuristic TOID.
Figure 7a,b display boxplots illustrating the distribution of purified vertices in graphs with varying densities. The box represents the interquartile range (IQR), encompassing the central 50% of the data. The line within the box marks the median, which is the middle value. The whiskers represent the range of data that is not considered outliers, while any points outside this range are considered outliers. In Figure 7a, which corresponds to graphs with a density of 0.1 or higher, we observe that the purified vertices are concentrated between 0 and 3. This suggests that the number of purified vertices is generally low in high-density graphs, indicating a better quality of the solution delivered by Stage 1. However, Stage 2 is still needed to guarantee a minimal TOIDS.
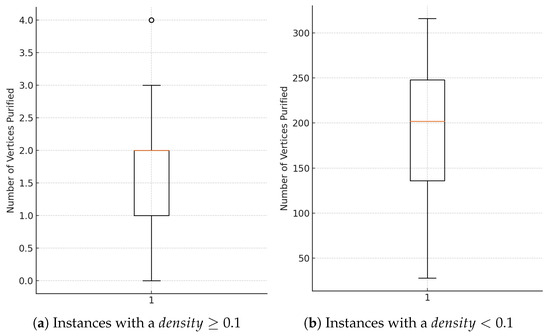
Figure 7.
Distribution of the number of purified vertices.
In contrast, Figure 7b, representing graphs with very low density (almost trees), shows a much wider spread in the values. The number of purified vertices is significantly higher, ranging from 28 to 316 vertices. This indicates that in low-density graphs, where the structure is more dispersed and less connected, the purification process has a much more significant impact. In these cases, it is more likely that many redundant or non-essential vertices can be removed. In summary, Stage 1 of our heuristic tends to be more effective in higher-density graphs, while it faces greater challenges in very low-density graphs.
5. Conclusions
In this work, we introduced new lower and upper bounds for and presented both an ILP formulation and a heuristic algorithm for addressing the total outer-independent domination problem. As no prior algorithm had been developed for this specific problem, we utilized the optimal solutions generated by CPLEX for our ILP model as a basis for evaluating the performance of our heuristic. Our experiments employed well-established benchmark instances originally designed for the classical domination problem. CPLEX successfully solved 500 of these instances, which included graphs with up to 9100 vertices. In addition, our heuristic consistently produced high-quality solutions for the same benchmarks, achieving an average error of 1.012 vertices across all tested instances. We also identified certain families of graphs where our heuristic guarantees optimal solutions. Looking ahead, we believe this research can be extended to tackle more complex variants of domination problems, such as k-tuple domination, secure domination, alliance domination, and total outer k-independent domination, opening new lines of research.
In addition to the results presented in this paper, several open problems remain related to . One significant direction for future research is the study of this parameter in the context of various graph operators and transformations. Specifically, the behavior of under graph product operators (e.g., corona product, lexicographic product) and graph transformations (e.g., edge contractions, vertex deletions) remains largely unexplored. Investigating these operators could provide valuable insights and inspire further research in domination theory. Moreover, a comparative analysis with existing domination parameters across various graph families would offer deeper insights into the advantages and limitations of . Such comparisons could highlight the applicability of in relation to well-established parameters, including the powerful k-alliance number, 2-packing number, global offensive k-alliance number, independence number, and independent domination number. Exploring these areas will not only expand our understanding of but could also reveal new relationships between domination parameters in different graph families. We believe that addressing these open problems will significantly contribute to the theory of domination in graphs and inspire future research in this area.
Author Contributions
Conceptualization, P.B., E.P.I. and J.L.S.-S.; methodology, E.P.I., I.R.V. and J.L.S.-S.; software, E.P.I.; validation, E.P.I. and I.R.V.; formal analysis, P.B., E.P.I. and J.L.S.-S.; investigation, E.P.I., I.R.V. and J.L.S.-S.; data curation, E.P.I.; writing—original draft preparation, E.P.I., I.R.V. and J.L.S.-S.; writing—review and editing, P.B., E.P.I. and J.L.S.-S.; visualization, E.P.I. and J.L.S.-S.; supervision, P.B. and J.L.S.-S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data are available at DOI: https://dx.doi.org/10.17632/rr5bkj6dw5.9.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| TDS | Total Dominating Set |
| TOIDS | Total Outer-Independent Dominating Set |
| ILP | Integer Linear Programming |
| RAM | Random Access Memory |
References
- Gupta, P. Domination in graph with application. Indian J. Res 2013, 2, 115–117. [Google Scholar]
- Farber, M. Applications of Linear Programming Duality to Problems Involving Independence and Domination; Simon Fraser University, Computing Science: Burnaby, BC, Canada, 1981. [Google Scholar]
- Henning, M.A. A survey of selected recent results on total domination in graphs. Discret. Math. 2009, 309, 32–63. [Google Scholar] [CrossRef]
- Cabrera Martínez, A.; Hernández Mira, F.A.; Sigarreta Almira, J.M.; Yero, I.G. On computational and combinatorial properties of the total co-independent domination number of graphs. Comput. J. 2019, 62, 97–108. [Google Scholar] [CrossRef]
- Li, Z.; Shao, Z.; Lang, F.; Zhang, X.; Liu, J.B. Computational complexity of outer-independent total and total Roman domination numbers in trees. IEEE Access 2018, 6, 35544–35550. [Google Scholar] [CrossRef]
- Rodríguez-Velázquez, J.A.; Sigarreta, J.M. Global offensive alliances in graphs. Electron. Notes Discret. Math. 2006, 25, 157–164. [Google Scholar] [CrossRef]
- Rodriguez, J.M.; Sigarreta, J.M. Bounds on Gromov hyperbolicity constant in graphs. Proc.-Math. Sci. 2012, 122, 53–65. [Google Scholar] [CrossRef]
- Martinez, A.C.; Mira, F.A.H.; Almira, J.M.S.; Yero, I.G. A note on total co-independent domination in trees. Contrib. Discret. Math. 2024, 19, 184–195. [Google Scholar] [CrossRef]
- Henning, M. Total Domination in Graphs; Springer Monographs in Mathematics; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Bermudo, S.; Hernández-Gómez, J.C.; Sigarreta, J.M. On the total k-domination in graphs. Discuss. Math. Graph Theory 2017, 38, 301–317. [Google Scholar] [CrossRef]
- Sigarreta, J.M. Total domination on some graph operators. Mathematics 2021, 9, 241. [Google Scholar] [CrossRef]
- Krzywkowski, M. A lower bound on the total outer-independent domination number of a tree. Comptes Rendus Math. 2011, 349, 7–9. [Google Scholar] [CrossRef]
- Soner, N.; Murthy, B.D.; Deepak, G. Total co-independent domination in graphs. Appl. Math. Sci 2012, 6, 6545–6551. [Google Scholar]
- Mojdeh, D.A.; Peterin, I.; Samadi, B.; Yero, I.G. On three outer-independent domination related parameters in graphs. Discret. Appl. Math. 2021, 294, 115–124. [Google Scholar] [CrossRef]
- Cabrera-Martıneza, A. Total outer-independent domination in regular graphs. Filomat 2024, 38, 6581–6586. [Google Scholar] [CrossRef]
- Martínez, A.C.; García, S.C.; Peterin, I.; Yero, I.G. The total co-independent domination number of some graph operations. Rev. Unión Matemática Argent. 2022, 63, 153–168. [Google Scholar] [CrossRef]
- Parra Inza, E. Random Graph. Mendeley Data 2025, V9. [Google Scholar] [CrossRef]
- Hedetniemi, S.; Hedetniemi, S.; Kristiansen, P. Alliances in graphs. J. Combin. Math. Combin. Comput 2004, 48, 157–177. [Google Scholar]
- Brigham, R.C.; Dutton, R.D.; Haynes, T.W.; Hedetniemi, S.T. Powerful alliances in graphs. Discret. Math. 2009, 309, 2140–2147. [Google Scholar] [CrossRef]
- Ouazine, K.; Slimani, H.; Tari, A. Alliances in graphs: Parameters, properties and applications—A survey. AKCE Int. J. Graphs Comb. 2018, 15, 115–154. [Google Scholar] [CrossRef]
- Rodríguez-Velázquez, J.A.; Yero, I.G.; Sigarreta, J.M. Defensive k-alliances in graphs. Appl. Math. Lett. 2009, 22, 96–100. [Google Scholar] [CrossRef]
- Carballosa, W.; Rodríguez, J.M.; Sigarreta, J.M. Hyperbolicity in the corona and join of graphs. Aequationes Math. 2015, 89, 1311–1327. [Google Scholar] [CrossRef]
- Hernández-Gómez, J.C.; Méndez-Bermúdez, J.; Rodríguez, J.M.; Sigarreta, J.M. Harmonic index and harmonic polynomial on graph operations. Symmetry 2018, 10, 456. [Google Scholar] [CrossRef]
- Henning, M.A. Packing in trees. Discret. Math. 1998, 186, 145–155. [Google Scholar] [CrossRef]
- Clark, L. Perfect domination in random graphs. J. Combin. Math. Combin. Comput 1993, 14, 173–182. [Google Scholar]
- Bermudo, S.; Fernau, H.; Sigarreta, J.M. The differential and the Roman domination number of a graph. Appl. Anal. Discret. Math. 2014, 8, 155–171. [Google Scholar] [CrossRef]
- Haynes, T.W.; Henning, M.A.; Van Der Merwe, L.C. Domination and total domination in complementary prisms. J. Comb. Optim. 2009, 18, 23–37. [Google Scholar] [CrossRef]
- Kazemi, A.P. k-Tuple Total Domination in Complementary Prisms. Int. Sch. Res. Not. 2011, 2011, 681274. [Google Scholar] [CrossRef][Green Version]
- Méndez, J.; Reyes, R.; Rodríguez, J.M.; Sigarreta, J.M. Geometric and topological properties of the complementary prism networks. Math. Methods Appl. Sci. 2023, 46, 9555–9575. [Google Scholar] [CrossRef]
- Bertossi, A.A. Dominating sets for split and bipartite graphs. Inf. Process. Lett. 1984, 19, 37–40. [Google Scholar] [CrossRef]
- Goddard, W.; Henning, M.A. Independent domination in graphs: A survey and recent results. Discret. Math. 2013, 313, 839–854. [Google Scholar] [CrossRef]
- Parra Inza, E. Random Graph BD4. Mendeley Data 2025, V1. [Google Scholar] [CrossRef]
- Parra Inza, E. Random Graph BD5. Mendeley Data 2025, V1. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).