A Multi-Agent Adaptive Architecture for Smart-Grid-Intrusion Detection and Prevention
Abstract
:1. Introduction
- Data-gathering device (sensor)—collecting data from systems being examined/protected;
- Detector (intrusion-detection engine)—the process that analyzes data from sensors for potential intrusions;
- Knowledge base (database)—definitions of sample attacks for use in identifying likely intrusions;
- Configuration device—mechanisms for determining current IDS settings and status;
- Response component—a mechanism for triggering actions to address likely threats detected.
2. Reference-System Architecture
- Collect information on the operation of devices that are part of the system;
- Collect and process information about users and their activity in the system;
- Define and monitor the authorization levels of smart-grid users;
- Define and monitor the roles of smart-grid components and users;
- Define access rights to devices, their settings, and the data they generate;
- Monitor data flows in the computer network;
- Generate and monitor profiles defining the typical behaviors of devices and users;
- Apply system-performance risk-assessment mechanisms;
- Take measures to reduce this risk.
3. An Approach to Deploy Software Agents in Risk Assessment and Protection of Information System Security
4. Algorithms for User- and Device-Behavior Profiling
- On-grid/off-grid—information on system operation. The on-grid installation is disabled in the event of power failure. The off-grid installation uses its own batteries for electricity storage (True/False);
- AC circuit break—AC line protection mechanism (True/False);
- DC circuit break—DC line protection mechanism (True/False)
- Energy generation—amount of energy generated (kWh);
- Energy consumption—amount of energy consumed by the user (kWh);
- AC mains voltage—determines current voltage in the power grid; on-grid requires that the inverter cut off power transfer to the smart grid in the event that a certain value is exceeded (V);
- DC mains voltage—determines voltage in the photovoltaic system or another power-generation device (V);
- Energy generated and transferred to grid—amount of energy transferred to the power grid (kW);
- Energy generated and consumed by user—amount of energy consumed by the user (kW);
- System status—determines whether the inverter is enabled or disabled (on/off) (True/False).
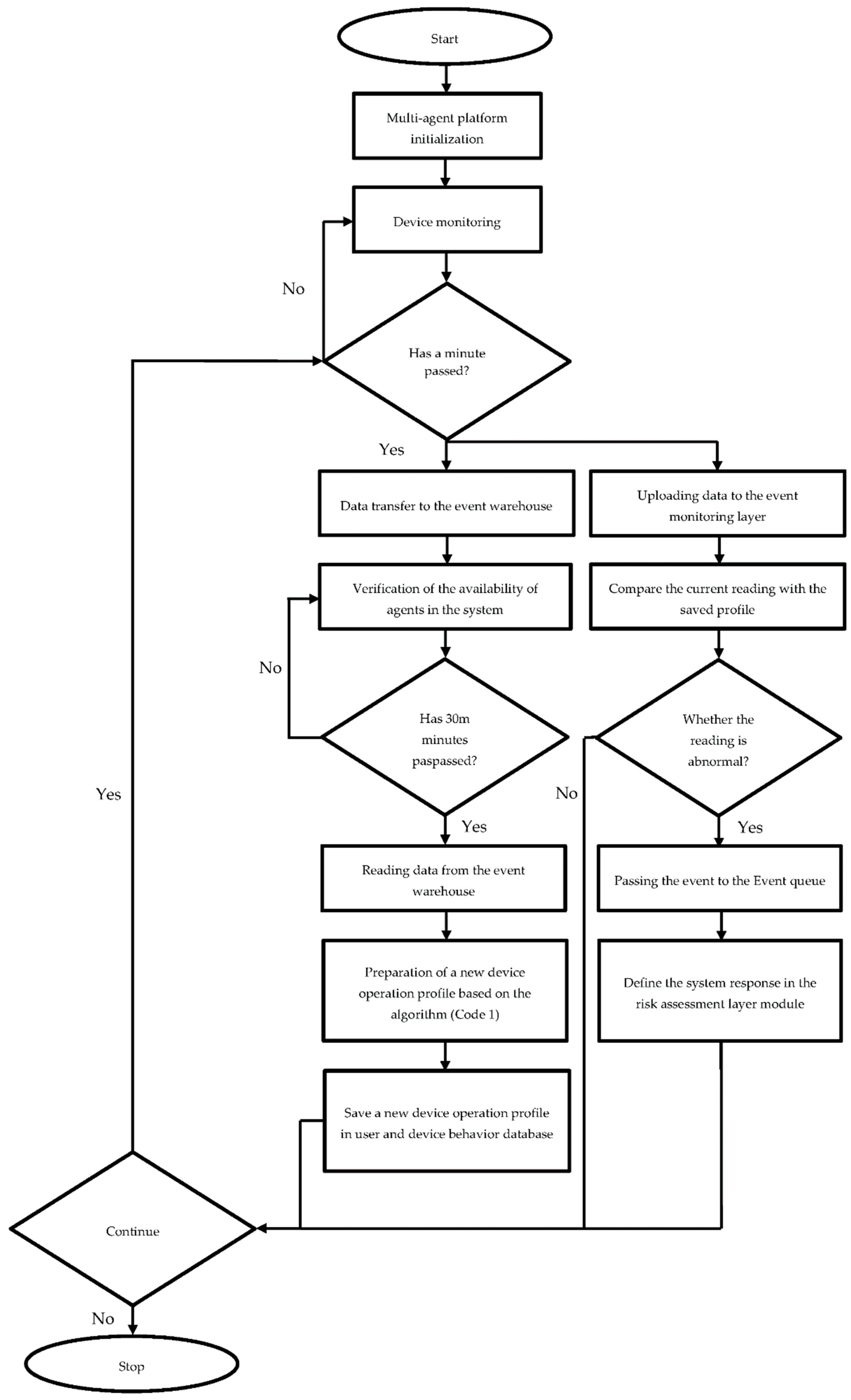
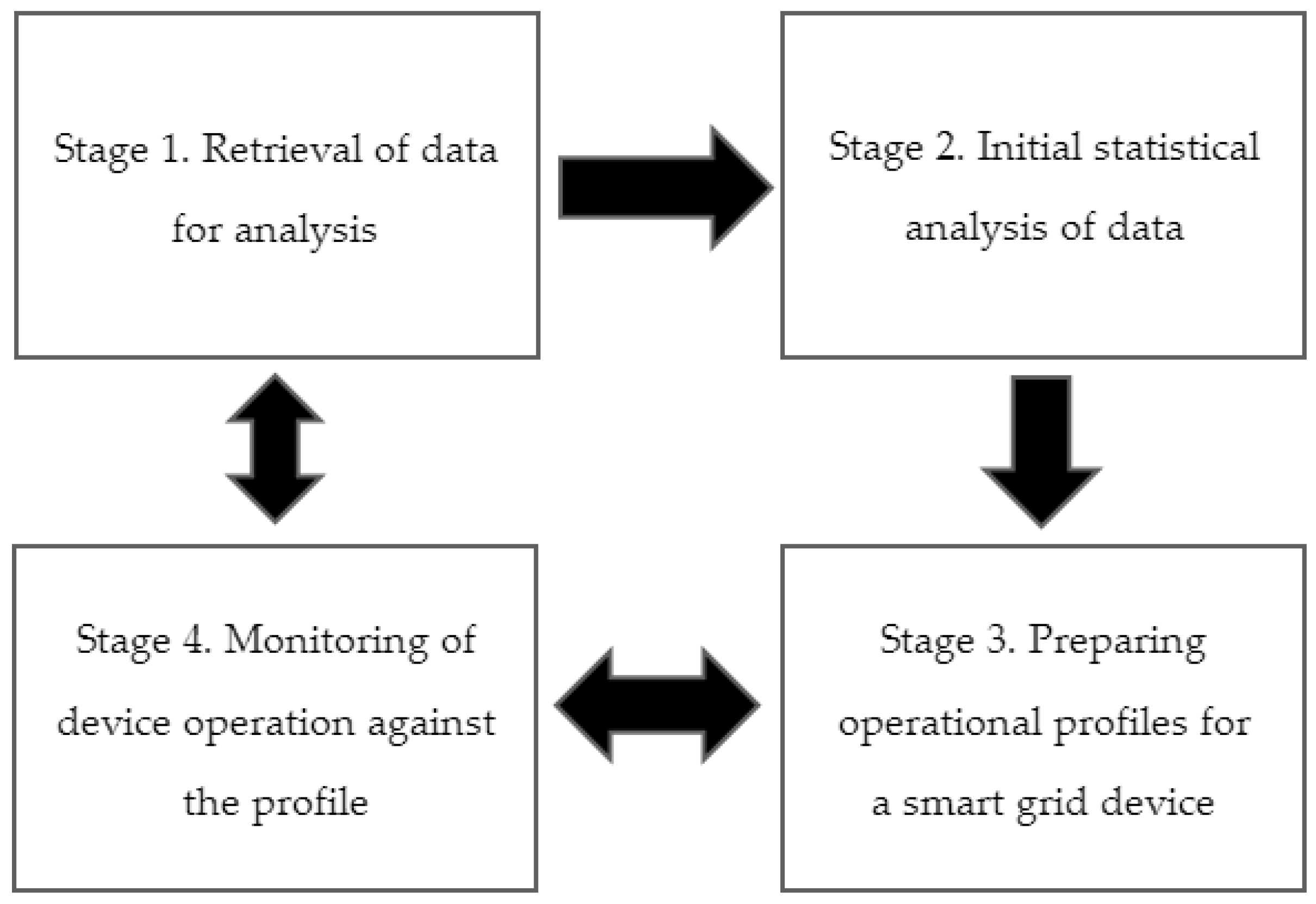
- Stage 1—data are gathered via devices that monitor electricity flows in the grid and upload the data to the server running the Open Source MQTT broker. The project uses the Eclipse Mosquitto server that integrates events implemented in the smart grid and allows for the construction of smart home systems. The data are then saved by an agent in the system database.
- Stage 2—data collected in stage 1 are processed and a set of descriptive statistics is generated. As a result, the key characteristics of the data can be determined and any irregularities detected, such as, for example, missing datasets (a fact that may be ascribed to device failure or power outage).
- Stage 3—based on the data processed in stage 2, a system profile is generated in line with the algorithm presented below (code 1). As new data streams continue to arrive, the profile is subject to ongoing adjustments and is updated on a regular basis.
- Stage 4—the profile created in previous iterations is used to monitor the grid and to detect any anomalies in the new, incoming data. Once the new data are verified against the profile, the system recalculates the profile’s parameters and updates them, and then the whole cycle is repeated.
| Algorithm 1. Simplified algorithm for a profiling agent. | |
| Code 1 ------------------------------------------------------------------------------------------------------------------------------------- | |
| E = {E1,…,En},//devices connected to the smart-grid network and devices supplied by the power system; | |
| En.producer—identifier of the energy-producing device n; | |
| En.client—identifier of the energy-consuming device n; | |
| En.time—adopted unit of time; | A |
| En.energy—amount of energy in kWh | |
| P = {P1,…Pm}—set of behavior patterns | |
| Pm = {PmEn.client,PmEn.energyMax, PmEn.energyMin, PmEn.timeFrom, PmEn.timeTo } | |
| //device-operation profiles over time; | B |
| AC.true,DC.true—correct operation confirmation; | C |
| for each En∈E do | |
| if En.time + 7 days < today do | |
| for each Pm∈P do | |
| PmEn.energyMax = null//maximum-energy consumption for the i device; | |
| PmEn.energyMin = null//minimum-energy consumption for the i device; | |
| If En.client == PmEn.client && AC.true && DC.true && En.time >= PmEn.timeFrom | |
| && En.time <= PmEn.timeTo then | |
| If En.energy > PmEn.energyMax then | |
| PmEn.energyMax = En.energy; | |
| end if | |
| If Ei.energy <Ei.energyMin then | |
| PmEn.energyMin = En.energy; | |
| end if | D |
| Pm.add(En.client,PmEn.energyMax,PmEn.energyMin,PmEn.timeFrom,PmEn.timeTo); | E |
| end if | |
| end | |
| end if | |
| end |
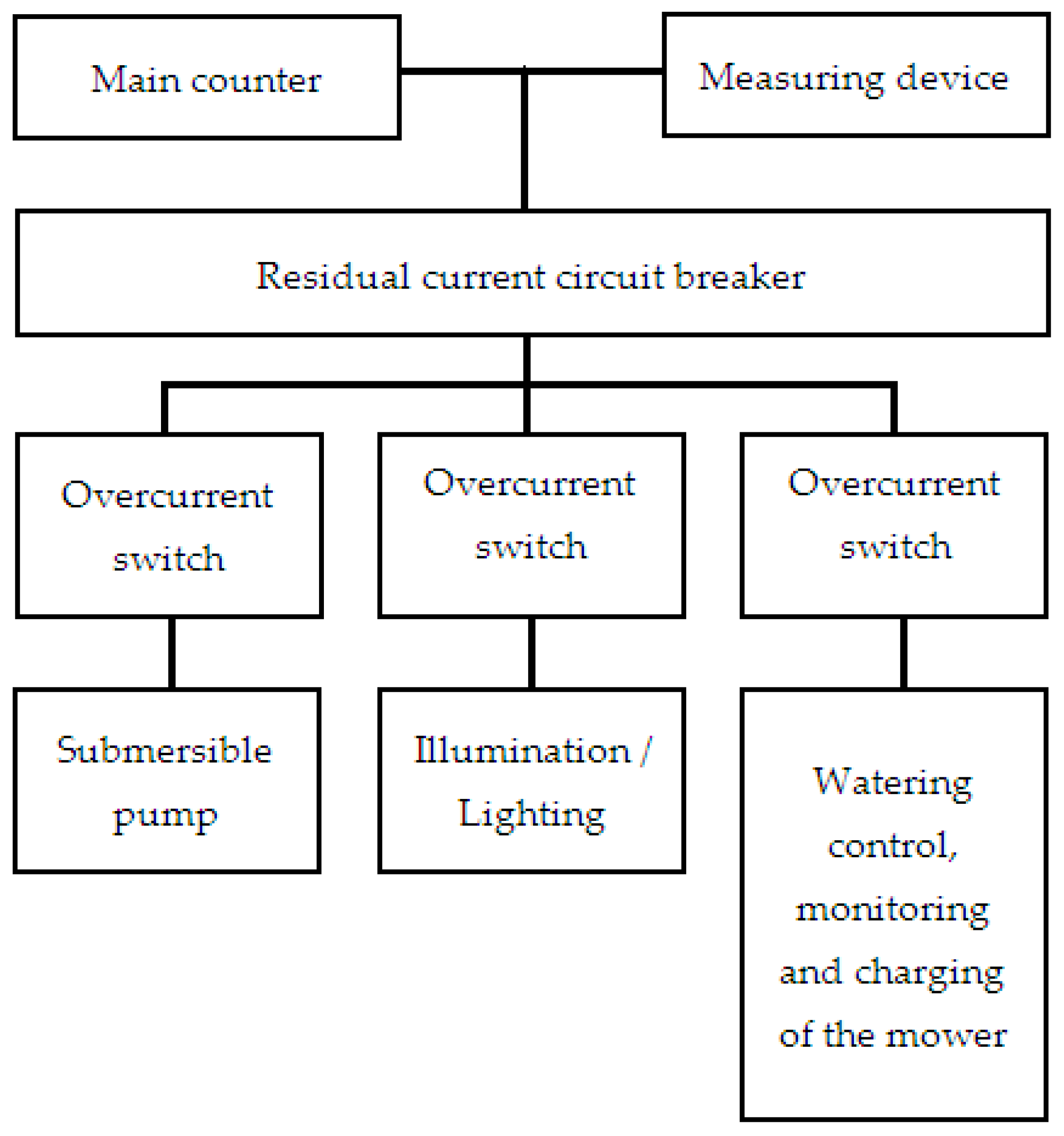
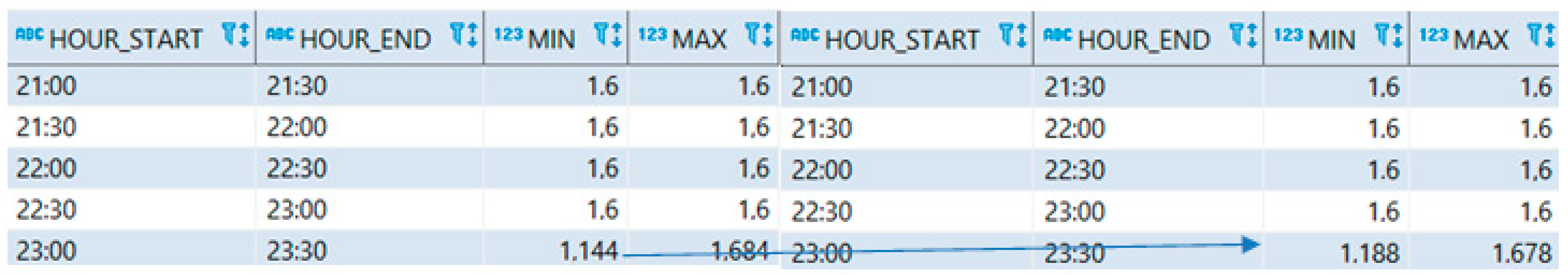
5. Application of the Proposed Architecture and Algorithm
6. Conclusions
- process automatization of user-activity profiling and supervision;
- reduction possibility of data leakage;
- scalability and efficiency improvement of the system, through the use of multiple instances of agents simultaneously performing associated tasks;
- improvements in mitigating the risks of data leakage or account-takeover fraud (i.e., taking over an employee’s login credentials as a result of phishing attacks and spamming).
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Denning, D.E. An Intrusion-Detection Model. IEEE Trans. Softw. Eng. 1987, SE-13, 222–232. [Google Scholar] [CrossRef]
- Anderson, J.P. Computer Security Threat Monitoring and Surveillance; Technical Report; James P. Anderson Co.: Ambler, PA, USA, 1980. [Google Scholar]
- Debar, H.; Dacier, M.; Wespi, A. Towards a taxonomy of intrusion-detection systems. Comput. Netw. 1999, 31, 805–822. [Google Scholar] [CrossRef]
- Wu, S.X.; Banzhaf, W. The use of computational intelligence in intrusion detection systems: A review. Appl. Soft Comput. 2010, 10, 1–35. [Google Scholar] [CrossRef] [Green Version]
- Vasilomanolakis, E.; Karuppayah, S.; Mühlhäuser, M.; Fischer, M. Taxonomy and Survey of Collaborative Intrusion Detection. ACM Comput. Surv. 2015, 47, 1–33. [Google Scholar] [CrossRef]
- Boyles, T. CCNA Security Study Guide: Exam 640-553; John Wiley and Sons: Hoboken, NJ, USA, 2010. [Google Scholar]
- Sabahi, F.; Movaghar, A. Intrusion Detection: A Survey. In Proceedings of the 2008 Third International Conference on Systems and Networks Communications, Sliema, Malta, 26–31 October 2008; pp. 23–26. [Google Scholar] [CrossRef]
- Pez, R.; Páez, R. An Agent Based Intrusion Detection System with Internal Security. In Intrusion Detection Systems; InTech: Houston, TX, USA, 2011. [Google Scholar] [CrossRef] [Green Version]
- Peng, J.; Choo, K.-K.R.; Ashman, H. User profiling in intrusion detection: A review. J. Netw. Comput. Appl. 2016, 72, 14–27. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. An intrusion detection framework for the smart grid. In Proceedings of the Canadian Conference on Electrical and Computer Engineering, Windsor, ON, Canada, 30 April–3 May 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Gamage, T.T.; Roth, T.P.; McMillin, B.M. Confidentiality Preserving Security Properties for Cyber-Physical Systems. In Proceedings of the International Computer Software and Applications Conference, Munich, Germany, 18–22 July 2011; pp. 28–37. [Google Scholar] [CrossRef]
- Albers, P.; Camp, O.; Percher, J.-M.; Jouga, B.; Mé, L.; Puttini, R.S. Security in Ad Hoc Networks: A General Intrusion Detection Architecture Enhancing Trust Based Approaches. In Proceedings of the Wireless Information Systems (WIS 2002), Ciudad Real, Spain, 2–3 April 2002; pp. 1–12. [Google Scholar]
- Krmicek, V.; Celeda, P.; Rehak, M.; Pechoucek, M. Agent-Based Network Intrusion Detection System. In Proceedings of the 2007 IEEE/WIC/ACM International Conference on Intelligent Agent Technology, Fremont, CA, USA, 2–5 November 2007. [Google Scholar]
- Ganapathy, S.; Yogesh, P.; Kannan, A. Intelligent Agent-Based Intrusion Detection System Using Enhanced Multiclass SVM. Comput. Intell. Neurosci. 2012, 2012, 9. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Abdurrazaq, M.N.; Bambang, R.T.; Rahardjo, B. Distributed intrusion detection system using cooperative agent based on ant colony clustering. In Proceedings of the 2014 International Conference on Electrical Engineering and Computer Science (ICEECS), Kuta, Bali, Indonesia, 24–25 November 2014; pp. 109–114. [Google Scholar] [CrossRef]
- Banik, S.M.; Pena, L. Deploying agents in the network to detect intrusions. In Proceedings of the 2015 IEEE/ACIS 14th International Conference on Computer and Information Science (ICIS), Las Vegas, NV, USA, 28 June–1 July 2015; pp. 83–87. [Google Scholar] [CrossRef]
- Zytniewski, M. Gossip and Ostracism in Modelling Automorphosis of Multi-agent Systems. In Complexity in Information Systems Development; Goluchowski, J., Pankowska, M., Linger, H., Barry, C., Lang, M., Schneider, C., Eds.; Lecture Notes in Information Systems and Organisation; Springer: Cham, Switzerland, 2017; Volume 22, pp. 135–150. [Google Scholar] [CrossRef]
- Stakhanova, N.; Basu, S.; Wong, J. A taxonomy of intrusion response systems. Int. J. Inf. Comput. Secur. 2007, 1, 169–184. [Google Scholar] [CrossRef] [Green Version]
- Available online: https://www.sciencedirect.com/topics/computer-science/intrusion-response-system (accessed on 24 May 2022).
- Anwar, S.; Zain, J.M.; Zolkipli, M.F.; Inayat, Z.; Khan, S.; Anthony, B.; Chang, V. From Intrusion Detection to an Intrusion Response System: Fundamentals, Requirements, and Future Directions. Algorithms 2017, 10, 39. [Google Scholar] [CrossRef] [Green Version]
- Inayat, Z.; Gani, A.; Anuar, N.B.; Khan, M.K.; Anwar, S. Intrusion response systems: Foundations, design, and challenges. J. Netw. Comput. Appl. 2016, 62, 53–74. [Google Scholar] [CrossRef]
- Rullo, A.; Serra, E.; Lobo, J. Redundancy as a Measure of Fault-Tolerance for the Internet of Things: A Review. In Policy-Based Autonomic Data Governance; Calo, S., Bertino, E., Verma, D., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2019; Volume 11550. [Google Scholar] [CrossRef]
- Aldaej, A. Enhancing Cyber Security in Modern Internet of things (IoT) Using Intrusion Prevention Algorithm for IoT (IPAI). In IEEE Access; IEEE: Piscataway, NJ, USA, 2019. [Google Scholar] [CrossRef]
- James, F. IoT Cybersecurity based Smart Home Intrusion Prevention System. In Proceedings of the 2019 3rd Cyber Security in Networking Conference (CSNet), Quito, Ecuador, 23–25 October 2019. [Google Scholar] [CrossRef]
- Rullo, A.; Bertino, E.; Sacca, D. PAST: Protocol-Adaptable Security Tool for Heterogeneous IoT Ecosystems. In Proceedings of the 2018 IEEE Conference on Dependable and Secure Computing (DSC), Kaohsiung, Taiwan, 10–13 December 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Kato, T.; Kanamori, H.; Suzuoki, Y.; Funabashi, T. Multi-Agent based Control and Protection of Power Distributed System-Protection Scheme with Simplified Information Utilization. In Proceedings of the 13th International Conference on, Intelligent Systems Application to Power Systems, Arlington, VA, USA, 6–10 November 2005. [Google Scholar] [CrossRef]
- Wan, H.; Wong, K.; Chung, C. Multi-agent application in protection coordination of power system with distributed generations. In Proceedings of the 2008 IEEE Power and Energy Society General Meeting-Conversion and Delivery of Electrical Energy in the 21st Century, Pittsburgh, PA, USA, 20–24 July 2008; pp. 1–6. [Google Scholar] [CrossRef]
- Zhu, Y.; Song, S.; Wang, D. Multiagents-based wide area protection with best-effort adaptive strategy. Int. J. Electr. Power Energy Syst. 2008, 31, 94–99. [Google Scholar] [CrossRef]
- Rahman, M.; Isherwood, N.; Oo, A. Multi-agent based coordinated protection systems for distribution feeder fault diagnosis and reconfiguration. Int. J. Electr. Power Energy Syst. 2018, 97, 106–119. [Google Scholar] [CrossRef]
- Satuyeva, B.; Sultankulov, B.; Nunna, H.S.V.S.K.; Kalakova, A.; Doolla, S. Q-Learning based Protection Scheme for Microgrid using Multi-Agent System. In Proceedings of the 2019 International Conference on Smart Energy Systems and Technologies (SEST), Porto, Portugal, 9–11 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Tian, F.; Wen, F.; Wang, X.; Xue, Y.; Salam, A. A multi-agent system based fault diagnosis for active distribution systems. In Proceedings of the 2016 IEEE Innovative Smart Grid Technologies-Asia (ISGT-Asia), Melbourne, VIC, Australia, 28 November–1 December 2016; pp. 1110–1114. [Google Scholar] [CrossRef]
- Ye, N.; Chen, Q. An anomaly detection technique based on a chi-square statistic for detecting intrusions into information systems. Qual. Reliab. Eng. Int. 2001, 17, 105–112. [Google Scholar] [CrossRef]
- Ling, L.; Song, S.; Manikopoulos, C. Windows NT User Profiling for Masquerader Detection. In Proceedings of the 2006 IEEE International Conference on Networking, Sensing and Control, Ft. Lauderdale, FL, USA, 23–25 April 2006. [Google Scholar] [CrossRef]
- Revett, K. A bioinformatics based approach to user authentication via keystroke dynamics. Int. J. Control Autom. Syst. 2009, 7, 7–15. [Google Scholar] [CrossRef]
- Pannell, G.; Ashman, H. Anomaly detection over user profiles for intrusion detection. In Proceedings of the 8th Australian Information Security Management Conference, Perth, Australia, 30 November 2010. [Google Scholar]
- Gupta, S.; Kumar, P.; Abraham, A. A Profile Based Network Intrusion Detection and Prevention System for Securing Cloud Environment. Int. J. Distrib. Sens. Netw. 2013, 9, 364575. [Google Scholar] [CrossRef] [Green Version]
- Zytniewski, M.; Stanek, S. Software agents supporting the security of IT systems handling personal information. J. Decis. Syst. 2020, 29, 285–300. [Google Scholar] [CrossRef]





| Types of Agents Used | IDS/IPS System Architecture | Agent Platform Used | Simulation | Role of Agent System |
|---|---|---|---|---|
| Monitoring agent, control agent, supervisor agent | None | Information unavailable | Yes | Ground and line fault |
| Management agent, relay agents, distributed-generator agents and equipment agents | None | JADE | No | Coordination of communication in the system |
| Communication-control agent, network-topology analysis agent, impedance-matrix-computation agent, adaptive-setting-calculation agent, relay agent, mobile-management agent, network-monitoring agent | Dispatching Center, SDH-based Intranet, Station | Information unavailable | Yes | Adaptive-relay settings calculation |
| Relay agent, configuration agent | Multi-agent-communication layer, data-acquisition layer (PMU), physical-power-grid model | JADE | Yes | System reconfiguration, relay coordination |
| Smart agent (circuit-breaker agents), master agent | Agent, environment | JADE | Yes | Phase-fault detection |
| Bus agents | Multi-agent layer, physical layer | JADE | Yes | Fault diagnosis |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kisielewicz, T.; Stanek, S.; Zytniewski, M. A Multi-Agent Adaptive Architecture for Smart-Grid-Intrusion Detection and Prevention. Energies 2022, 15, 4726. https://doi.org/10.3390/en15134726
Kisielewicz T, Stanek S, Zytniewski M. A Multi-Agent Adaptive Architecture for Smart-Grid-Intrusion Detection and Prevention. Energies. 2022; 15(13):4726. https://doi.org/10.3390/en15134726
Chicago/Turabian StyleKisielewicz, Tomasz, Stanislaw Stanek, and Mariusz Zytniewski. 2022. "A Multi-Agent Adaptive Architecture for Smart-Grid-Intrusion Detection and Prevention" Energies 15, no. 13: 4726. https://doi.org/10.3390/en15134726
APA StyleKisielewicz, T., Stanek, S., & Zytniewski, M. (2022). A Multi-Agent Adaptive Architecture for Smart-Grid-Intrusion Detection and Prevention. Energies, 15(13), 4726. https://doi.org/10.3390/en15134726






