A Game Theory-Based Approach for Vulnerability Analysis of a Cyber-Physical Power System
Abstract
:1. Introduction
- (1)
- A comprehensive CPPS interactive model framework is developed. The CPPS components are classified into five categories (i.e., physical nodes, cyber nodes, physical-physical links, cyber-cyber links, and cyber-physical links). The interaction between cyber components and physical components is discussed by analyzing the optimal load curtailment operation upon component failure.
- (2)
- A game-theoretic bi-level optimization model for the CPPS attacker and defender is proposed. At the upper level, the defender manages the defending resources to minimize the worst-case load loss caused by the attacks. At the lower level, the attacker decides which component (or components) to attack so that the load loss could be maximized. The hierarchical interactions between the defender and the attacker are described in a game-theoretic model.
- (3)
- The proposed model is illustrated based on a revised version of the IEEE 14-bus power system. The defender’s strategy (i.e., the distribution of the defending resources) can be viewed as the relative vulnerability index among the CPPS components. This result can be further developed to calibrate the defender’s decisions on the system.
2. Related Work
2.1. Cyber Data Attacks in CPPSs
2.2. Cyber-Physical Mutual Impacts Analysis
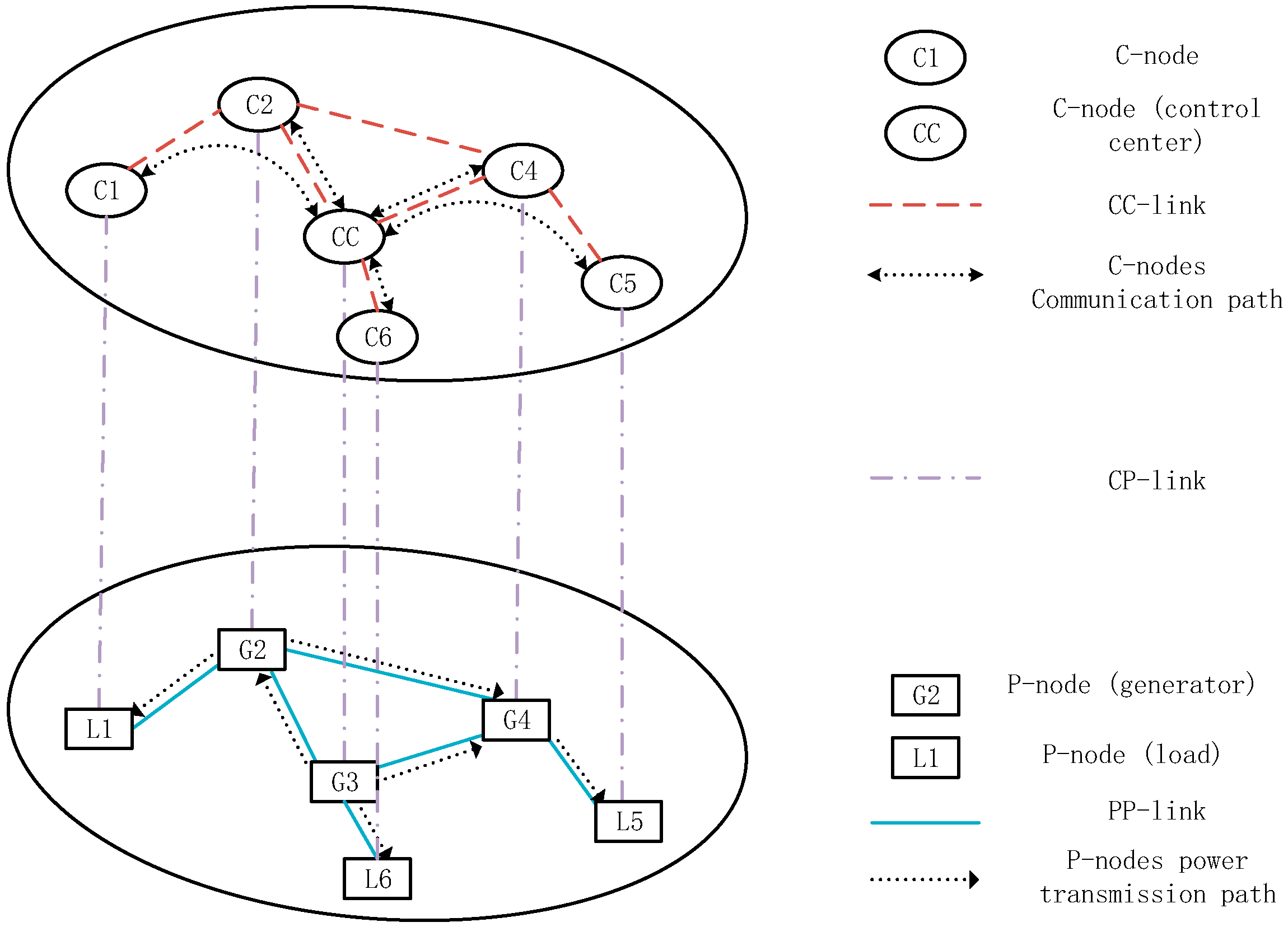
3. The CPPS Interactive Model Framework
4. CPPS Vulnerability Analysis
4.1. External Attack and Cascading Failure
- (1)
- If a CC-link fails: both C-nodes connecting to the link should verify their connection to the control center. If a C-node loses connection to the control center, it is considered to have failed.
- (2)
- If a CP-link fails: this causes the failure of both the C-node and the P-node connecting to it.
- (3)
- If a PP-link fails: this influences the power flow distribution of the system, and further operations might be needed to ensure that the power flow does not exceed the line limit.
- (4)
- If a C-node fails: all CC-links and CP-links connecting to it fail.
- (5)
- If a P-node fails: the generator power output cannot be adjusted, and the load curtailment operation is invalid for the components represented by this failed P-node. Meanwhile the CP-link connecting to this P-node fails.
4.2. Optimal Load Curtailment Operation
5. The Attacker-Defender Game
5.1. Bi-Level Programming Problem
5.2. Defending Resource Distribution
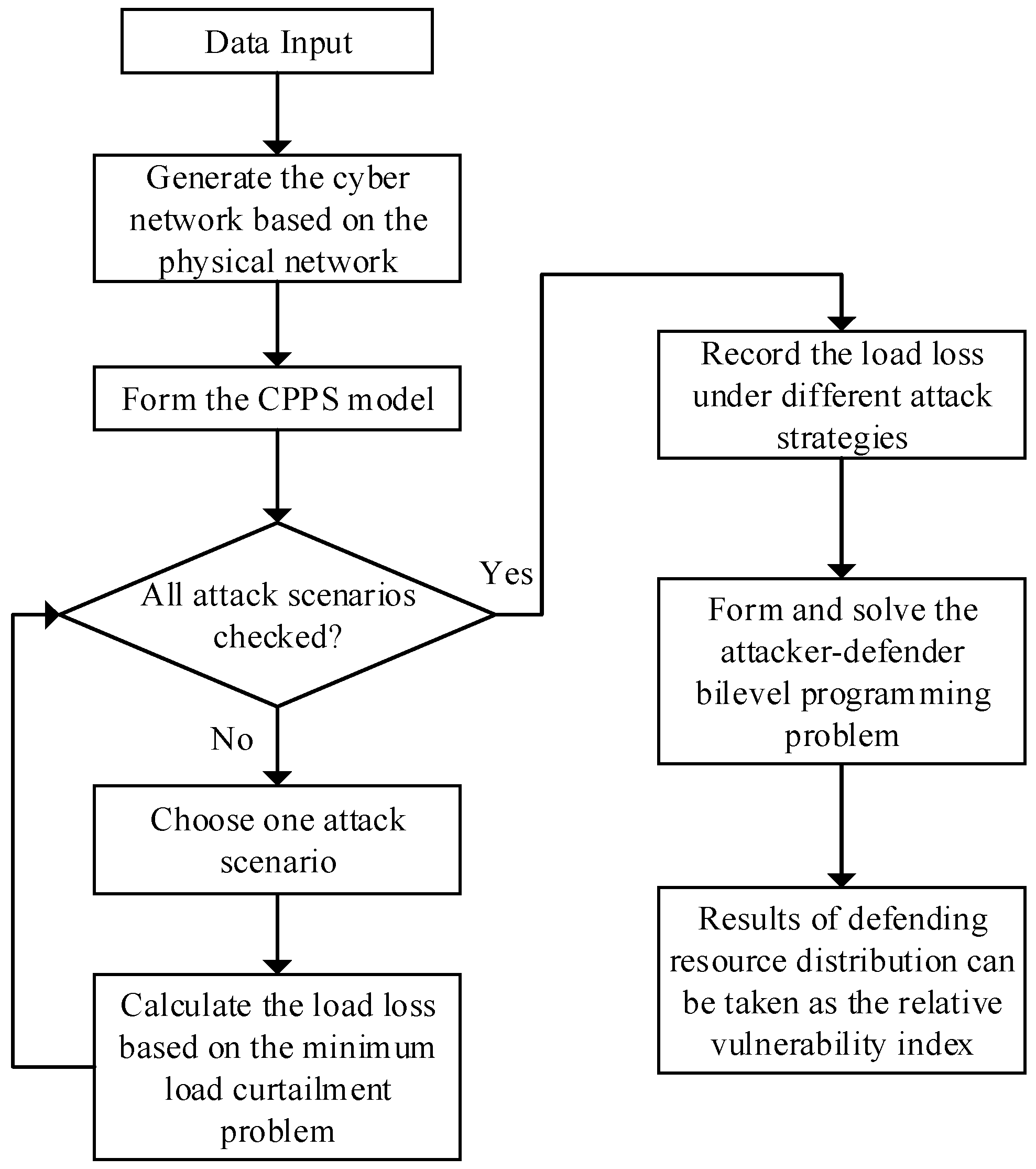
5.3. Vulnerability Assessment Procedure
- (1)
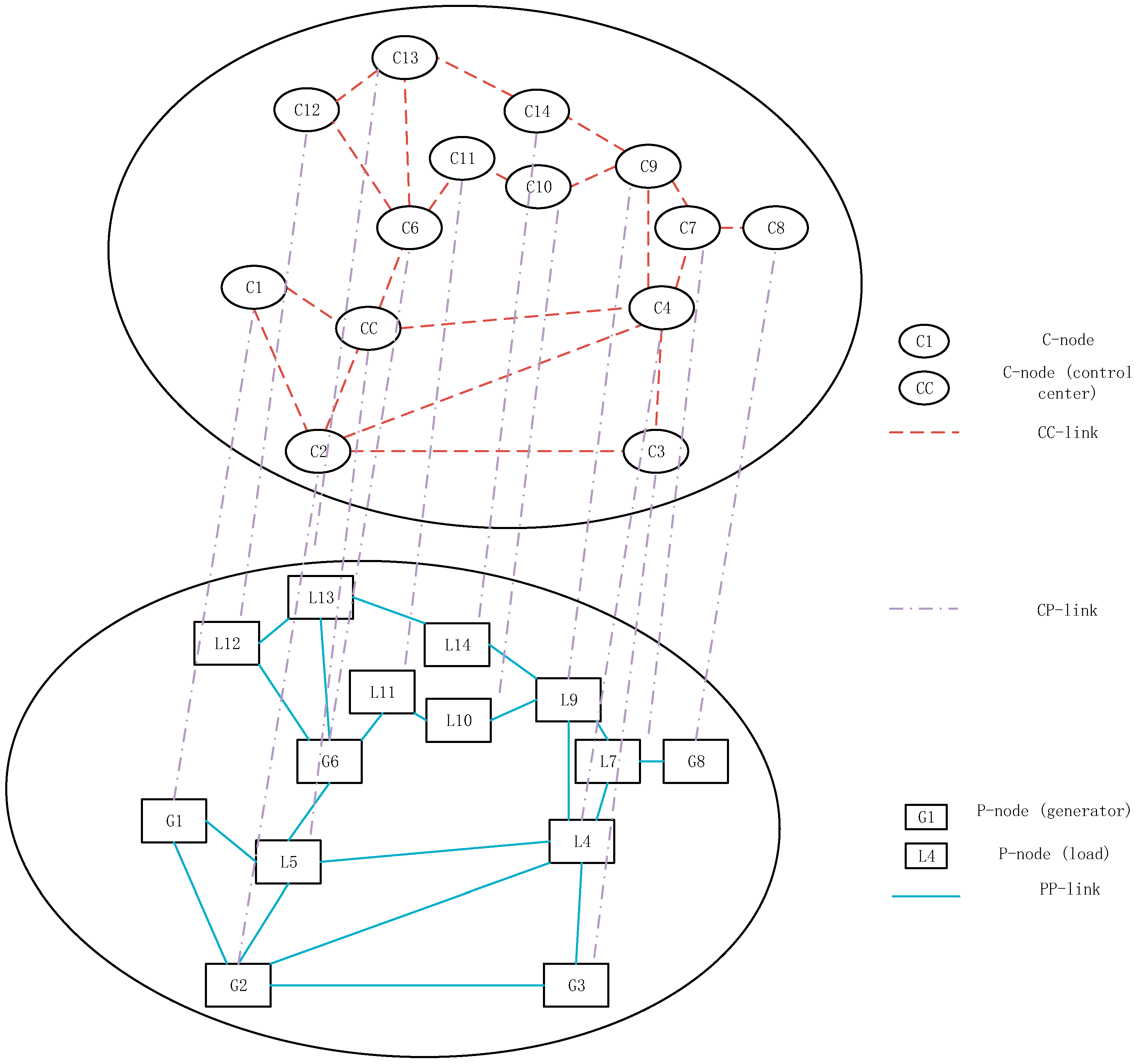
- The CPPS model is formed. The P-nodes and PP-links of the CPPS model are formed, based on the power flow model. The C-nodes and CC-links are then added, based on the one-to-one mapping rule between the P-nodes and C-nodes, and between the PP-links and CC-links, as shown in Figure 2.
- (2)
- Choose one attack scenario of the attacker to successfully compromise the components (e.g., a PP-link/a PP-link and a C-node/a PP-link and two C-nodes), and calculate the total load loss as in Equations (1)–(7).
- (3)
- Check whether all attack scenarios have been enumerated. If yes, go to Step 4, otherwise go to Step 2.
- (4)
- Formulate the bi-level optimization problem as in Equations (12)–(21).
- (5)
- The optimal defending resource distribution on the PP-links and C-nodes can be solved. Based on the result, the vulnerability of different components can be illustrated.
6. Case Studies
- (1)
- Case 1: only a PP-link is attacked, and the defender focuses on only defending PP-links;
- (2)
- Case 2: one PP-link and one C-node are attacked, and the defender aims to defend both PP-links and C-nodes;
- (3)
- Case 3: one PP-link and two C-nodes are attacked, as discussed previously; the defender also aims to defend both PP-links and C-nodes.
7. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Nomenclature
| P-node | Physical node |
| C-node | Cyber node |
| PP-link | Physical-physical link |
| CC-link | Cyber-cyber link |
| CP-link | Cyber-physical link |
| L | The collection of load in the system |
| La | The collection of controllable load in the system |
| Loff | The collection of uncontrollable load in the system |
| G | The collection of generators in the system |
| Ga | The collection of controllable generators in the system |
| Goff | The collection of uncontrollable generators in the system |
| ∆PLi | The power changed at load i (MW) |
| ∆PGj | The power changed at generator j (MW) |
| The lower limit of load i (MW) | |
| The upper limit of load i (MW) | |
| The lower limit of generator j (MW) | |
| The upper limit of generator j (MW) | |
| Pi | The real power at node i (MW) |
| ∆Pi | The change of real power at node i (MW) |
| Vi | The voltage amplitude at node i (kV) |
| θij | The angle difference of branch ij (rad) |
| ∆θij | The change of angle difference of branch ij (rad) |
| Bij | The susceptance of branch ij in the bus admittance matrix (S) |
| N | The collection of all nodes in the system |
| n | The number of nodes in the system |
| dp | The defending resource distributed to PP-links |
| dc | The defending resource distributed to C-nodes |
| a | A possible attack action |
| w | The attacker’s weight on different attack actions |
| wa | The attacker’s weight on attack action a |
| Ra | The total load curtailment when attack action a is launched (MW) |
| xa | The PP-link targeted by attack action a |
| y1a | The first C-node targeted by attack action a |
| y2a | The second C-node targeted by attack action a |
| The probability of the PP-link xa successfully compromised by the attacker | |
| The probability of the first C-node y1a successfully compromised by the attacker | |
| The probability of the second C-node y2a successfully compromised by the attacker | |
| The load curtailment when components are successfully compromised by the attacker (MW) | |
| The load curtailment when components are successfully compromised by the attacker (MW) | |
| The load curtailment when components are successfully compromised by the attacker (MW) | |
| The load curtailment when components are successfully compromised by the attacker (MW) | |
| βp | The failure coefficient of PP-links |
| βc | The failure coefficient of C-nodes |
| NPP | The number of PP-links in the system |
| NC | The number of C-nodes in the system |
| Dp | The total defending resource for PP-links |
| Dc | The total defending resource for C-nodes |
References
- Kim, K.D.; Kumar, P.R. Cyber-physical systems: A perspective at the centennial. Proc. IEEE 2012, 100, 1287–1308. [Google Scholar]
- Mamo, X.; Mallet, S.; Coste, T.; Grenard, S. Distribution automation: The cornerstone for smart grid development strategy. In Proceedings of the IEEE Power & Energy Society General Meeting, Calgary, AB, Canada, 26–30 July 2009; pp. 1–6. [Google Scholar]
- Kirschen, D.; Bouffard, F. Keeping the lights on and the information flowing. IEEE Power Energy Mag. 2009, 7, 50–60. [Google Scholar] [CrossRef]
- Tram, H. Technical and operation considerations in using smart metering for outage management. In Proceedings of the IEEE PES Transmission and Distribution Conference and Exposition, Chicago, IL, USA, 21–24 April 2008; pp. 1–3. [Google Scholar]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 ukraine blackout: Implications for false data injection attacks. IEEE Trans. Power Syst. 2016, 32, 3317–3318. [Google Scholar] [CrossRef]
- Susuki, Y.; Koo, T.J.; Ebina, H.; Yamazaki, T.; Ochi, T.; Uemura, T.; Hikihara, T. A hybrid system approach to the analysis and design of power grid dynamic performance. Proc. IEEE 2012, 100, 225–239S. [Google Scholar] [CrossRef]
- Yampolskiy, M.; Horvath, P.; Koutsoukos, X.D.; Xue, Y.; Sztipanovits, J. Taxonomy for description of cross-domain attacks on CPS. In Proceedings of the 2nd ACM International Conference on High Confidence Networked Systems, Philadelphia, PA, USA, 9–11 April 2013; pp. 135–142. [Google Scholar]
- Yampolskiy, M.; Horváth, P.; Koutsoukos, X.D.; Xue, Y.; Sztipanovits, J. A language for describing attacks on cyber-physical systems. Int. J. Crit. Infrastruct. Prot. 2015, 8, 40–52. [Google Scholar] [CrossRef]
- Petnga, L.; Xu, H. Security of unmanned aerial vehicles: dynamic state estimation under cyber-physical attacks. In Proceedings of the 2016 International Conference on Unmanned Aircraft Systems (ICUAS), Arlington, VA, USA, 7–10 June 2016; pp. 811–819. [Google Scholar]
- Li, Y.; Shi, L.; Cheng, P.; Chen, J.; Quevedo, D.E. Jamming attacks on remote state estimation in cyber-physical systems: A game-theoretic approach. IEEE Trans. Autom. Control 2015, 60, 2831–2836. [Google Scholar] [CrossRef]
- Mo, Y.; Chabukswar, R.; Sinopoli, B. Detecting integrity attacks on SCADA systems. IEEE Trans. Control Syst. Technol. 2014, 22, 1396–1407. [Google Scholar]
- Mo, Y.; Sinopoli, B. Secure estimation in the presence of integrity attacks. IEEE Trans. Autom. Control 2015, 60, 1145–1151. [Google Scholar] [CrossRef]
- Fawzi, H.; Tabuada, P.; Diggavi, S. Secure estimation and control for cyber-physical systems under adversarial attacks. IEEE Trans. Autom. Control 2014, 59, 1454–1467. [Google Scholar] [CrossRef]
- Pasqualetti, F.; Carli, R.; Bullo, F. A distributed method for state estimation and false data detection in power networks. In Proceedings of the 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm), Brussels, Belgium, 17–20 October 2011; pp. 469–474. [Google Scholar]
- Mo, Y.; Garone, E.; Casavola, A.; Sinopoli, B. False data injection attacks against state estimation in wireless sensor networks. In Proceedings of the 49th IEEE Conference on Decision and Control (CDC), Atlanta, GA, USA, 15–17 December 2010; pp. 5967–5972. [Google Scholar]
- Li, Y.; Quevedo, D.E.; Dey, S.; Shi, L. A game-theoretic approach to fake-acknowledgment attack on cyber-physical systems. IEEE Trans. Signal Inf. Proc. Netw. 2017, 3, 1–11. [Google Scholar] [CrossRef]
- Poisel, R. Modern Communications Jamming: Principles and Techniques; Artech House: Norwood, MA, USA, 2011. [Google Scholar]
- Zhang, H.; Cheng, P.; Shi, L.; Chen, J. Optimal DoS attack scheduling in wireless networked control system. IEEE Trans. Control Syst. Technol. 2016, 24, 843–852. [Google Scholar] [CrossRef]
- Zhang, H.; Cheng, P.; Shi, L.; Chen, J. Optimal denial-of-service attack scheduling with energy constraint. IEEE Trans. Autom. Control 2015, 60, 3023–3028. [Google Scholar] [CrossRef]
- Zhu, M.; Martínez, S. On the performance analysis of resilient networked control systems under replay attacks. IEEE Trans. Autom. Control 2014, 59, 804–808. [Google Scholar] [CrossRef]
- Deng, R.; Zhuang, P.; Liang, H. CCPA: coordinated cyber-physical attacks and countermeasures in smart grid. IEEE Trans. Smart Grid 2017, 8, 2420–2430. [Google Scholar] [CrossRef]
- Li, Z.; Shahidehpour, M.; Alabdulwahab, A.; Abusorrah, A. Bi-level model for analyzing coordinated cyber-physical attacks on power systems. IEEE Trans. Smart Grid 2016, 7, 2260–2272. [Google Scholar] [CrossRef]
- Soltan, S.; Yannakakis, M.; Zussman, G. Power grid state estimation following a joint cyber and physical attack. IEEE Trans. Control Netw. Syst. 2018, 5, 499–512. [Google Scholar] [CrossRef]
- Xin, S.; Guo, Q.; Sun, H.; Zhang, B.; Wang, J.; Chen, C. Cyber-physical modeling and cyber-contingency assessment of hierarchical control systems. IEEE Trans. Smart Grid 2015, 6, 2375–2385. [Google Scholar] [CrossRef]
- Ilic, M.D.; Xie, L.; Khan, U.A.; Moura, J.M. Modeling of future cyber-physical energy systems for distributed sensing and control. IEEE Trans. Syst. Man Cybern. Part A Syst. Hum. 2010, 40, 825–838. [Google Scholar] [CrossRef]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic cascade of failures in interdependent networks. Nature 2010, 464, 1025. [Google Scholar] [CrossRef]
- Vespignani, A. Complex networks: The fragility of interdependency. Nature 2010, 464, 984. [Google Scholar] [CrossRef]
- Falahati, B.; Fu, Y.; Wu, L. Reliability assessment of smart grid considering direct cyber-power interdependencies. IEEE Trans. Smart Grid 2012, 3, 1515–1524. [Google Scholar] [CrossRef]
- Falahati, B.; Fu, Y. Reliability assessment of smart grids considering indirect cyber-power interdependencies. IEEE Trans. Smart Grid 2014, 5, 1677–1685. [Google Scholar] [CrossRef]
- Bard, J.F. Practical Bi-Level Optimization: Algorithms and Applications; Springer Science & Business Media: Berlin, Germany, 2013. [Google Scholar]
- Zimmerman, R.D.; Murillo-Sánchez, C.E.; Thomas, R.J. MATPOWER: Steady-State Operations, Planning and Analysis Tools for Power Systems Research and Education. IEEE Trans. Power Syst. 2011, 26, 12–19. [Google Scholar] [CrossRef]

| PP-Link | Load Loss by Different Attack Actions (MW) and the Extra Percentage (%) | ||||
|---|---|---|---|---|---|
| PP (Case 1) | PP + C (Case 2) | % | PP + C + C (Case 3) | % | |
| 1-2 | 14.5088 | 14.5088 | 0 | 17.1003 | 17.86 |
| 1-5 | 5.4097 | 6.2701 | 15.9 | 6.5704 | 21.46 |
| 2-3 | 0 | 0 | 0 | 0 | 0 |
| 2-4 | 72.2991 | 74.5461 | 3.11 | 76.3861 | 5.65 |
| 2-5 | 21.2526 | 23.8454 | 12.20 | 24.7432 | 16.42 |
| 3-4 | 0 | 0 | 0 | 0 | 0 |
| 4-5 | 20.6592 | 21.6079 | 4.59 | 22.8152 | 10.44 |
| 4-7 | 18.1528 | 18.2292 | 0.42 | 18.2611 | 0.60 |
| 4-9 | 8.046 | 8.1913 | 1.81 | 8.238 | 2.39 |
| 5-6 | 6.3524 | 6.8563 | 7.93 | 7.15 | 12.56 |
| 6-11 | 9.4161 | 9.4161 | 0 | 9.4161 | 0 |
| 6-12 | 7.2594 | 7.2594 | 0 | 7.2594 | 0 |
| 6-13 | 29.325 | 31.976 | 9.04 | 32.2755 | 10.06 |
| 7-8 | 28.073 | 29.7059 | 5.82 | 30.0918 | 7.19 |
| 8-9 | 29.07 | 29.0721 | 0.0072 | 29.0753 | 0.018 |
| 9-10 | 6.5541 | 6.5541 | 0 | 6.5541 | 0 |
| 9-14 | 9.3228 | 9.3228 | 0 | 9.3228 | 0 |
| 10-11 | 2.7341 | 2.7341 | 0 | 2.7342 | 0.0048 |
| 12-13 | 0 | 0 | 0 | 0 | 0 |
| 13-14 | 5.756 | 5.756 | 0 | 5.756 | 0 |
| PP-Link | Defending Resource | C-Node | Defending Resource |
|---|---|---|---|
| 1-2 | 0.7126 | 1 | 0 |
| 1-5 | 0 | 2 | 0.0001 |
| 2-3 | 0 | 3 | 0 |
| 2-4 | 1.6066 | 4 | 0.8996 |
| 2-5 | 0.9401 | 5 | 0 |
| 3-4 | 0 | 6 | 0 |
| 4-5 | 0.9222 | 7 | 0 |
| 4-7 | 0.8445 | 8 | 0 |
| 4-9 | 0.3081 | 9 | 1.9131 |
| 5-6 | 0.1133 | 10 | 1.9394 |
| 6-11 | 0.4216 | 11 | 0 |
| 6-12 | 0.2232 | 12 | 0 |
| 6-13 | 1.1329 | 13 | 1.0694 |
| 7-8 | 1.0954 | 14 | 1.1781 |
| 8-9 | 1.113 | ||
| 9-10 | 0.1364 | ||
| 9-14 | 0.4145 | ||
| 10-11 | 0 | ||
| 12-13 | 0 | ||
| 13-14 | 0.0157 |
| PP-Link | Load Loss by Different Attack (MW) and the Extra Percentage (%) | ||||
|---|---|---|---|---|---|
| PP (Case 1) | PP + C (Case 2) | % | PP + C + C (Case 3) | % | |
| 1-2 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 1-5 | 5.4097 | 5.5575 | 2.73 | 5.6107 | 3.72 |
| 2-3 | 0 | 0 | 0 | 0 | 0 |
| 2-4 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 2-5 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 3-4 | 0 | 0 | 0 | 0 | 0 |
| 4-5 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 4-7 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 4-9 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 5-6 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 6-11 | 5.642 | 5.6549 | 0.23 | 5.6657 | 0.42 |
| 6-12 | 5.642 | 5.6549 | 0.23 | 5.6657 | 0.42 |
| 6-13 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 7-8 | 5.642 | 5.6549 | 0.23 | 5.6661 | 0.43 |
| 8-9 | 5.642 | 5.6549 | 0.23 | 5.6658 | 0.42 |
| 9-10 | 5.642 | 5.6549 | 0.23 | 5.6656 | 0.42 |
| 9-14 | 5.642 | 5.6549 | 0.23 | 5.6655 | 0.42 |
| 10-11 | 2.7341 | 2.7341 | 0 | 2.7342 | 0.0036 |
| 12-13 | 0 | 0 | 0 | 0 | 0 |
| 13-14 | 5.642 | 5.6549 | 0.23 | 5.6657 | 0.42 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, K.; Wen, F.; Tseng, C.-L.; Chen, M.; Yang, Z.; Zhao, H.; Shang, H. A Game Theory-Based Approach for Vulnerability Analysis of a Cyber-Physical Power System. Energies 2019, 12, 3002. https://doi.org/10.3390/en12153002
Chen K, Wen F, Tseng C-L, Chen M, Yang Z, Zhao H, Shang H. A Game Theory-Based Approach for Vulnerability Analysis of a Cyber-Physical Power System. Energies. 2019; 12(15):3002. https://doi.org/10.3390/en12153002
Chicago/Turabian StyleChen, Keren, Fushuan Wen, Chung-Li Tseng, Minghui Chen, Zeng Yang, Hongwei Zhao, and Huiyu Shang. 2019. "A Game Theory-Based Approach for Vulnerability Analysis of a Cyber-Physical Power System" Energies 12, no. 15: 3002. https://doi.org/10.3390/en12153002
APA StyleChen, K., Wen, F., Tseng, C.-L., Chen, M., Yang, Z., Zhao, H., & Shang, H. (2019). A Game Theory-Based Approach for Vulnerability Analysis of a Cyber-Physical Power System. Energies, 12(15), 3002. https://doi.org/10.3390/en12153002





