A Security Level Classification Method for Power Systems under N-1 Contingency
Abstract
:1. Introduction
- The proposed SLC method can assess the security level of power systems both qualitatively and quantitatively.
- Both of the power system structure and operational states are considered in the definition of comprehensive safety index (CSI) to evaluate power system security levels, where different indices, such as system margin index (SMI) and load entropy, are integrated. This will prevent any biased evaluation based only on one aspect of system structure or operational states. In addition, the defined load boundary vector (LBV) can detect the weakness in power systems and thus provides valuable reference for system operators to prevent any potential risk.
- Extended conic quadratic programming (ECQP) model is adopted to calculate TSC, where AC power flow is computed with higher precision at a reasonable polynomial computing time.
2. Calculation for TSC and LBV
2.1. Contingency Screening
2.2. TSC Calculation under AC Power Flow
2.3. ECQP Model
2.4. Load Boundary Vector
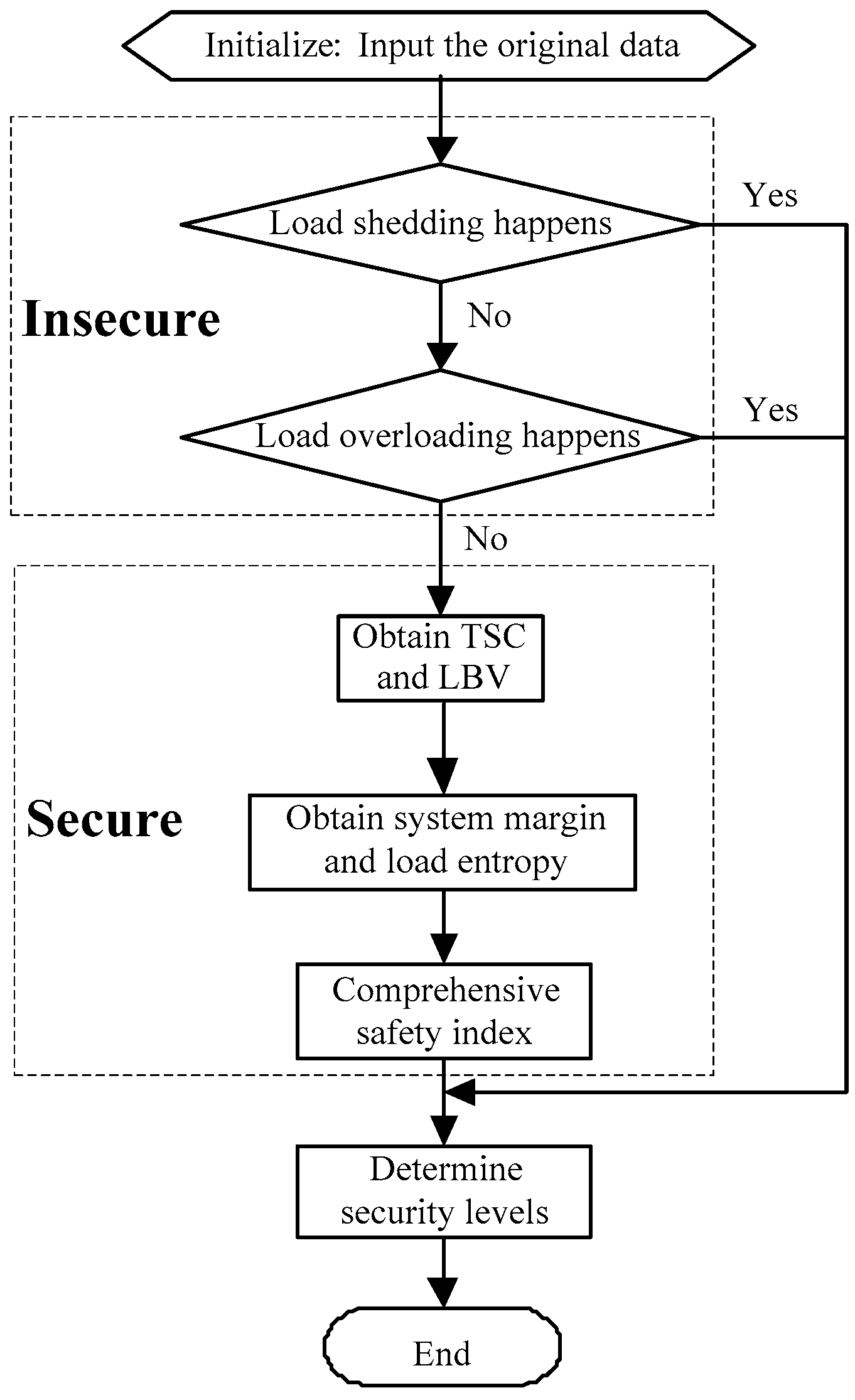
3. Security Levels Classification for Power System
3.1. General Idea
3.2. SLC for Insecure Power Systems
3.3. SLC for Secure Power Systems
3.3.1. System Margin Index
3.3.2. Load Entropy
3.3.3. Comprehensive Safety Index
3.4. SLC Principles
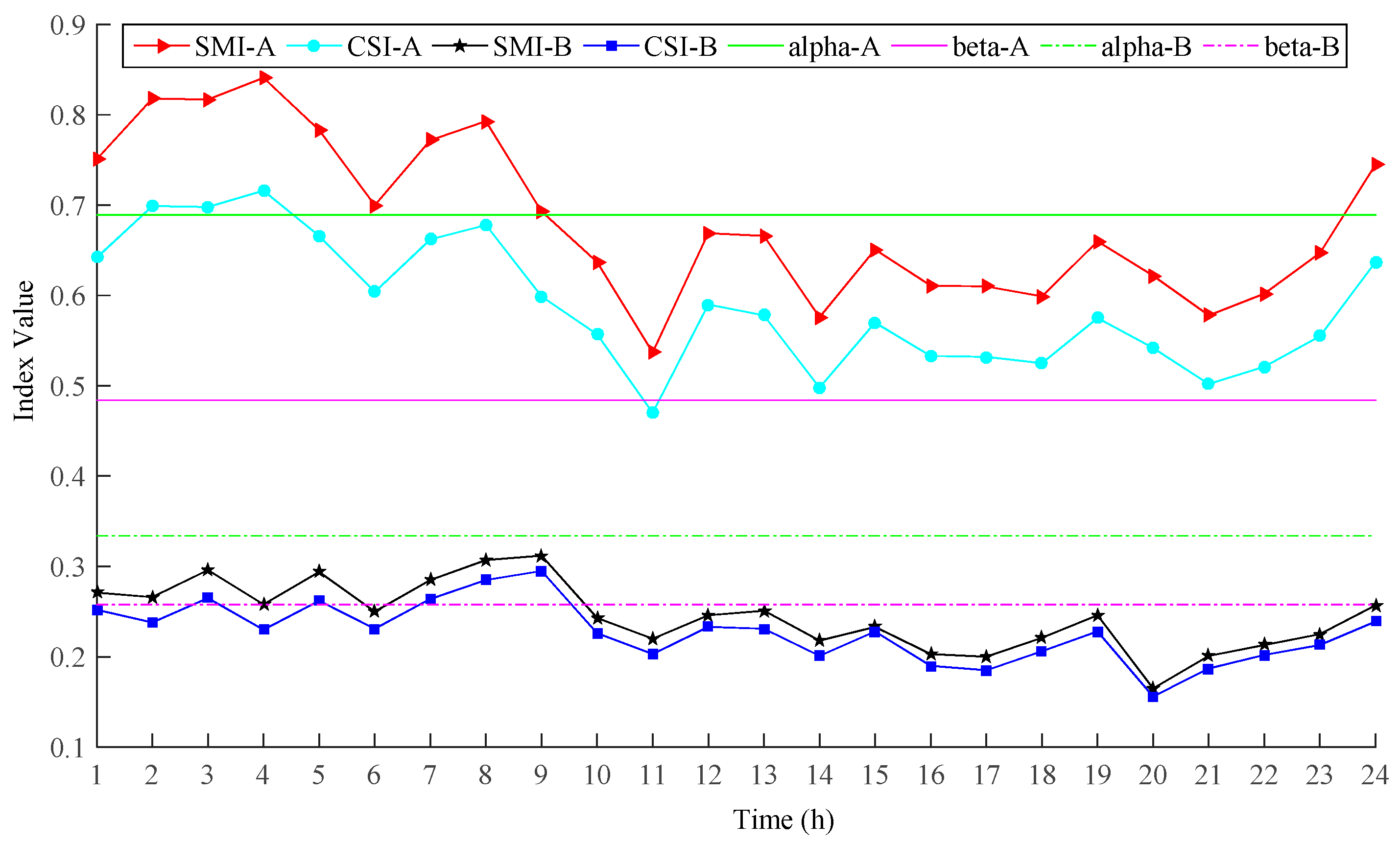
4. Case Studies
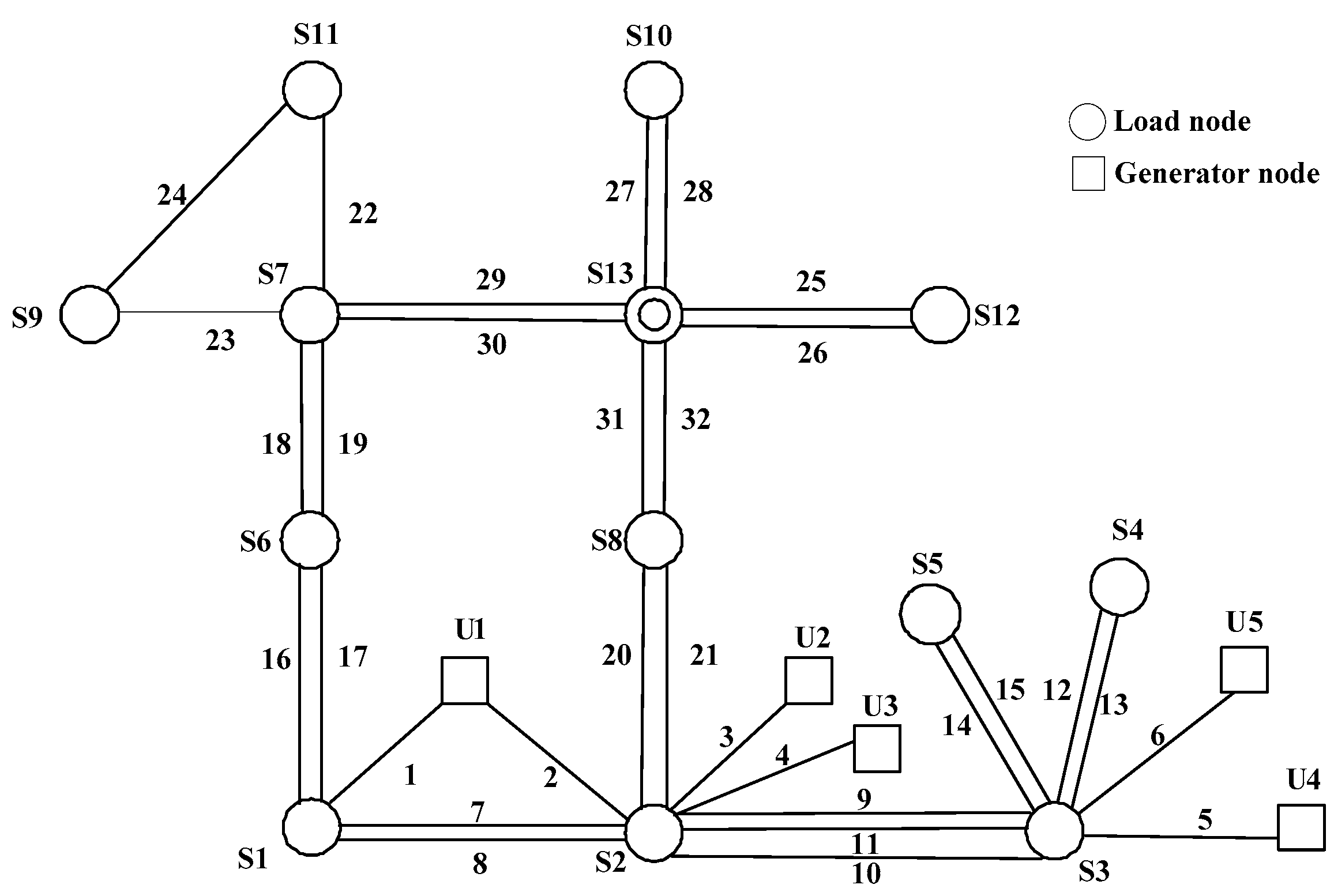
4.1. Two Modified Practical Power Systems
4.1.1. Basic Data
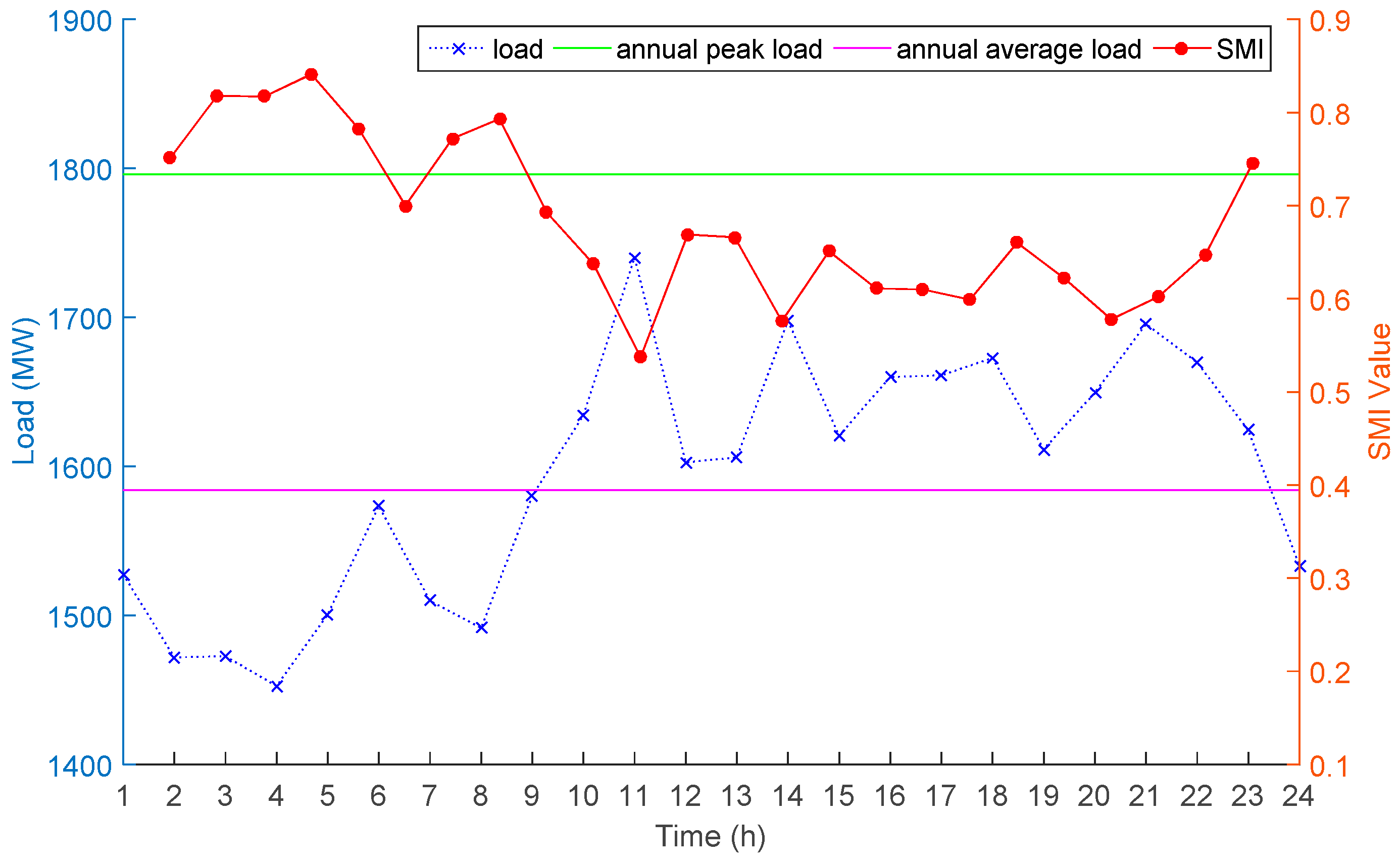
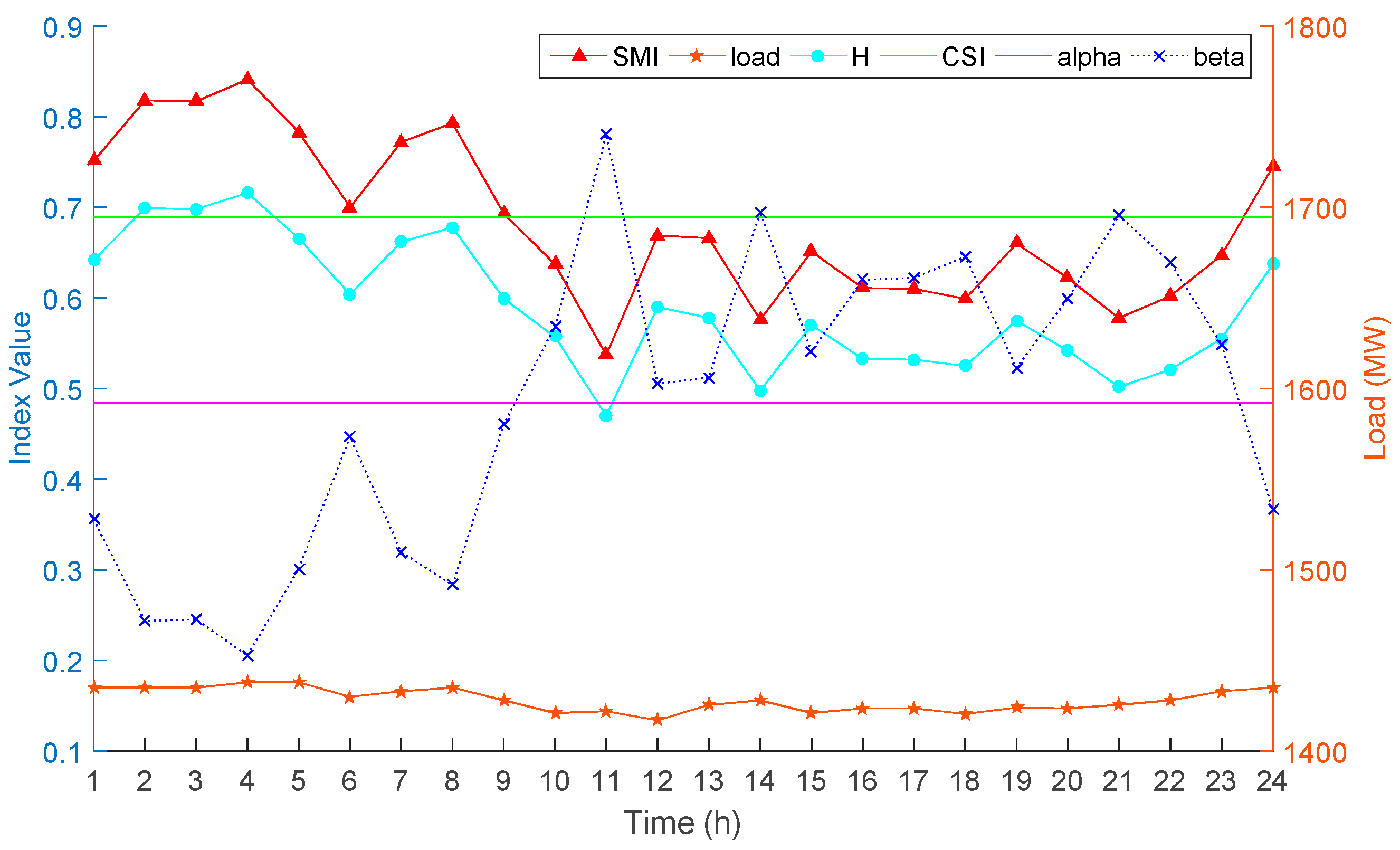
4.1.2. Simulation Results and Analysis
4.2. The IEEE-118 Bus Test System
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Srivani, J.; Swarup, K.S. Power system static security assessment and evaluation using external system equivalents. Int. J. Electr. Power Energy Syst. 2008, 30, 83–92. [Google Scholar] [CrossRef]
- Kalyani, S. Pattern analysis and classification for security evaluation in power networks. Int. J. Electr. Power Energy Syst. 2013, 44, 547–560. [Google Scholar] [CrossRef]
- Zarate, L.A.; Castro, C.A.; Ramos, J.L.M. Fast computation of voltage stability security margins using nonlinear programming techniques. IEEE Trans. Power Syst. 2006, 21, 19–27. [Google Scholar] [CrossRef]
- Estebsari, A.; Pons, E.; Huang, T.; Bompard, E. Techno-economic impacts of automatic undervoltage load shedding under emergency. Electr. Power Syst. Res. 2016, 131, 168–177. [Google Scholar] [CrossRef]
- Bompard, E.; Napoli, R.; Xue, F. Extended topological approach for the assessment of structural vulnerability in transmission networks. IET Gener. Transm. Distrib. 2010, 4, 716–724. [Google Scholar] [CrossRef]
- Preece, R.; Milanovic, J.V. Risk-based small-disturbance security assessment of power systems. IEEE Trans. Power Deliv. 2014, 30, 590–598. [Google Scholar] [CrossRef]
- Feng, Y.; Wu, W.; Zhang, B. Power system operation risk assessment using credibility theory. IEEE Trans. Power Syst. 2008, 23, 1309–1318. [Google Scholar] [CrossRef]
- Lachs, W.R. Area-Wide System Protection Scheme against Extreme Contingencies. Proc. IEEE 2005, 93, 1004–1027. [Google Scholar] [CrossRef]
- Diao, R.; Vittal, V.; Logic, N. Design of a real-time security assessment tool for situational awareness enhancement in modern power systems. IEEE Trans. Power Syst. 2010, 25, 957–965. [Google Scholar] [CrossRef]
- Xu, Y.; Dong, Z.; Zhao, J. A reliable intelligent system for real-time dynamic security assessment of power systems. IEEE Trans. Power Syst. 2012, 27, 1253–1263. [Google Scholar] [CrossRef]
- Kalyani, S.; Swarup, K.S. Classification and assessment of power system security using multiclass SVM. IEEE Trans. Syst. Man Cybern. 2011, 41, 753–758. [Google Scholar] [CrossRef]
- Abdelaziz, A.Y.; Mekhamer, S.F.; Badr, M.A.L. Probabilistic neural network classifier for static voltage security assessment of power systems. Electr. Power Compon. Syst. 2011, 40, 147–160. [Google Scholar] [CrossRef]
- Perninge, M.; Lindskog, F.; Soder, L. Importance sampling of injected powers for electric power system security analysis. IEEE Trans. Power Syst. 2012, 27, 3–11. [Google Scholar] [CrossRef]
- Zonouz, S.; Davis, C.M.; Davis, K.R.; Berthier, R.; Bobba, R.B.; Sanders, W.H. SOCCA: A Security-Oriented Cyber-Physical Contingency Analysis in Power Infrastructures. IEEE Trans. Smart Grid 2014, 5, 3–13. [Google Scholar] [CrossRef]
- Ten, C.W.; Ginter, A.; Bulbul, R. Cyber-Based Contingency Analysis. IEEE Trans. Power Syst. 2016, 31, 3040–3050. [Google Scholar] [CrossRef]
- Deng, R.; Zhuang, P.; Liang, H. CCPA: Coordinated Cyber-Physical Attacks and Countermeasures in Smart Grid. IEEE Trans. Smart Grid 2017, 8, 2420–2430. [Google Scholar] [CrossRef]
- Cao, Y.; Shi, X.; Li, Y.; Tan, Y.; Shahidehpour, M.; Shi, S. A Simplified Co-simulation Model for Investigating Impacts of Cyber-Contingency on Power System Operations. IEEE Trans. Smart Grid 2017. [Google Scholar] [CrossRef]
- Kumar, R.S.; Mathew, A.T. Online static security assessment module using artificial neural networks. IEEE Trans. Power Syst. 2013, 28, 4328–4335. [Google Scholar] [CrossRef]
- Bompard, E.; Estebsari, A.; Huang, T.; Fulli, G. A framework for analyzing cascading failure in large interconnected power systems: A post-contingency evolution simulator. Int. J. Electr. Power Energy Syst. 2016, 81, 12–21. [Google Scholar] [CrossRef]
- Ma, L.; Jia, B.; Lu, Z.; Cao, L. Research on security classification of transmission network considering static security and real-time power supply capacibility. Trans. China Electr. Soc. 2014, 29, 229–237. [Google Scholar]
- Saric, A.T.; Stankovic, A.M. Model uncertainty in security assessment of power systems. IEEE Trans. Power Syst. 2005, 20, 1398–1407. [Google Scholar] [CrossRef]
- Michael, E.K.; Nicholas, G.M.; Costas, D.V. Maximizing power-system loadability in the presence of multiple binding complementarity constraints. IEEE Trans. Circuits Syst. 2007, 54, 1775–1787. [Google Scholar] [CrossRef]
- Díaz, G. Maximum loadability of droop regulated microgrids-formulation and analysis. IET Gener. Transm. Distrib. 2013, 7, 175–182. [Google Scholar] [CrossRef]
- Zhang, S.; Cheng, H.; Zhang, L. Probabilistic evaluation of available load supply capability for distribution system. IEEE Trans. Power Syst. 2013, 28, 3215–3225. [Google Scholar] [CrossRef]
- Hu, Z.; Wang, X. Efficient computation of maximum loading point by load flow method with optimal multiplier. IEEE Trans. Power Syst. 2008, 23, 804–806. [Google Scholar] [CrossRef]
- Kong, T.; Cheng, H.; Wang, J.; Li, Y.; Wang, S. United urban power grid planning for network structure and partition scheme based on bi-level multi-objective optimization with genetic algorithm. Proc. CSEE 2009, 29, 59–66. [Google Scholar] [CrossRef]
- Shu, H.; Hu, Z.; Liu, Z. Online evaluation of utmost power supply ability of urban power system and its application. Power Syst. Technol. 2008, 32, 46–50. [Google Scholar] [CrossRef]
- Xiao, J.; Liu, S.; Li, Z.; Li, F. Loadability formulation and calculation for interconnected distribution systems considering N-1 security. Int. J. Electr. Power Energy Syst. 2016, 77, 70–76. [Google Scholar] [CrossRef]
- Xiao, J.; Liu, S.; Li, Z.; Wang, C. Model of total supply capability for distribution network based on power flow calculation. Proc. CSEE 2014, 34, 5516–5524. [Google Scholar] [CrossRef]
- Xiao, J.; Li, F.; Gu, W. Total supply capability and its extended indices for distribution systems: Definition, model calculation and applications. IET Gener. Transm. Distrib. 2011, 5, 869–876. [Google Scholar] [CrossRef]
- Ju, W.; Li, Y. Identification of critical lines and nodes in power grid based on maximum flow transmission contribution degree. Autom. Electr. Power Syst. 2012, 36, 6–12. [Google Scholar] [CrossRef]
- Dwivedi, A.; Yu, X. A maximum-flow-based complex network approach for power system vulnerability analysis. IEEE Trans. Ind. Electron. 2013, 9, 81–88. [Google Scholar] [CrossRef]
- Jabr, R. A conic quadratic format for the load flow equations of meshed networks. IEEE Trans. Power Syst. 2007, 22, 2285–2286. [Google Scholar] [CrossRef]
- The MOSEK Optimization Tools Version 3.2 (Revision 8), Denmark. Available online: http://www.mosek.com (accessed on 8 August 2017).
- Power Grid Operation Standards. China. 2015. Available online: http://www.safehoo.com/Standard/Trade/Electric/201608/452584.shtml (accessed on 2 November 2017).
- The Matpower Simulation Package. 2016. Available online: http://www.pserc.cornell.edu/matpower/ (accessed on 6 November 2017).
| Ranking | Contingencies | SPI |
|---|---|---|
| 1 | U1 | 0.129 |
| 2 | U4, U5, L5, L6 | 0.094 |
| 3 | U2, U3, L3, L4 | 0.093 |
| 4 | L23 | 0.027 |
| 5 | L22 | 0.025 |
| 6 | L26 | 0.009 |
| 7 | L27, L28, L29, L30, L14, L15 | 0.003 |
| 8 | L3, L4 | 0.002 |
| 9 | L9, L10, L24, L31, L32 | 0.001 |
| 10 | Others | Near to zero |
| Substation No. | ECQP | NR | Error/% | |
|---|---|---|---|---|
| P | V/p.u. | V/p.u. | ||
| S1 | 281.94 | 0.980929 | 0.980949 | 0.002039 |
| S2 | 354.26 | 0.986529 | 0.986545 | 0.001622 |
| S3 | 354.16 | 0.986707 | 0.986726 | 0.001926 |
| S4 | 111.52 | 0.983807 | 0.983827 | 0.002033 |
| S5 | 111.33 | 0.983728 | 0.983748 | 0.002033 |
| S6 | 138.43 | 0.979961 | 0.979974 | 0.001327 |
| S7 | 249.15 | 0.981523 | 0.981537 | 0.001426 |
| S8 | 357.10 | 0.987960 | 0.987975 | 0.001518 |
| S9 | 180.56 | 0.963821 | 0.963822 | 0.000104 |
| S10 | 63.46 | 0.978277 | 0.978281 | 0.000409 |
| S11 | 63.38 | 0.978233 | 0.978237 | 0.000409 |
| S12 | 200.19 | 0.958037 | 0.958074 | 0.003862 |
| S13 | 200.28 | 0.964930 | 0.964936 | 0.000622 |
| Substation No. | ECQP | LP | ||
|---|---|---|---|---|
| P | V/p.u. | P | V/p.u. | |
| S1 | 281.94 | 0.980929 | 274.69 | 0.982400 |
| S2 | 354.26 | 0.986529 | 149.81 | 0.989605 |
| S3 | 354.16 | 0.986707 | 360.00 | 0.989589 |
| S4 | 111.52 | 0.983807 | 120.00 | 0.986474 |
| S5 | 111.33 | 0.983728 | 120.00 | 0.986383 |
| S6 | 138.43 | 0.979961 | 154.39 | 0.980101 |
| S7 | 249.15 | 0.981523 | 25.00 | 0.978929 |
| S8 | 357.10 | 0.987960 | 300.13 | 0.989723 |
| S9 | 180.56 | 0.963821 | 235.07 | 0.947094 |
| S10 | 63.46 | 0.978277 | 100.00 | 0.965383 |
| S11 | 63.38 | 0.978233 | 100.00 | 0.965268 |
| S12 | 200.19 | 0.958037 | 400.00 | 0.929790 |
| S13 | 200.28 | 0.964930 | 360.91 | 0.931195 |
| sum | 2665.76 | -- | 2700 | -- |
| Ranking | SPI Values | Contingencies | Number of Contingencies |
|---|---|---|---|
| 1 | [0.07, 1.0] | -- | 0 |
| 2 | [0.06, 0.07) | G89, G69 | 2 |
| 3 | [0.05, 0.06) | G80, G10, L9–10, L8–9 | 4 |
| 4 | [0.04, 0.05) | G66, G65 | 2 |
| 5 | [0.03, 0.04) | G26, G100, G49 | 3 |
| 6 | [0.02, 0.03) | G25, G61, G59 | 3 |
| 7 | [0.01, 0.02) | G12, G54, L92–102, G46, G103, G92, G111, G31, L110–111, G40, G1, L110–111, L8–5, G42 | 14 |
| 8 | [0.073, 0.01) | L109–110, L71–73, L68–116, L86–87, L60–61, L110–112, and Other generators | 38 |
| 9 | [0, 0.005) | Others lines | 175 |
| Load Node | Assigned Capacity | Capacity in Obtained LBV | Difference (%) |
|---|---|---|---|
| 53 | 316.32 | 155.85 | 50.73 |
| 52 | 41.87 | 22.13 | 47.15 |
| 45 | 188.40 | 102.68 | 45.50 |
| 102 | 414.01 | 240.60 | 41.89 |
| 47 | 507.05 | 305.49 | 39.75 |
| 41 | 309.35 | 196.78 | 36.39 |
| 43 | 179.10 | 120.00 | 33.00 |
| 57 | 223.29 | 157.92 | 29.28 |
| 58 | 174.44 | 136.60 | 21.69 |
| 14 | 241.90 | 200.66 | 17.05 |
| 109 | 267.48 | 226.48 | 15.33 |
| 48 | 248.87 | 236.06 | 5.15 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, Z.; He, L.; Zhang, D.; Zhao, B.; Zhang, J.; Zhao, H. A Security Level Classification Method for Power Systems under N-1 Contingency. Energies 2017, 10, 2055. https://doi.org/10.3390/en10122055
Lu Z, He L, Zhang D, Zhao B, Zhang J, Zhao H. A Security Level Classification Method for Power Systems under N-1 Contingency. Energies. 2017; 10(12):2055. https://doi.org/10.3390/en10122055
Chicago/Turabian StyleLu, Zhigang, Liangce He, Dan Zhang, Boxuan Zhao, Jiangfeng Zhang, and Hao Zhao. 2017. "A Security Level Classification Method for Power Systems under N-1 Contingency" Energies 10, no. 12: 2055. https://doi.org/10.3390/en10122055
APA StyleLu, Z., He, L., Zhang, D., Zhao, B., Zhang, J., & Zhao, H. (2017). A Security Level Classification Method for Power Systems under N-1 Contingency. Energies, 10(12), 2055. https://doi.org/10.3390/en10122055




