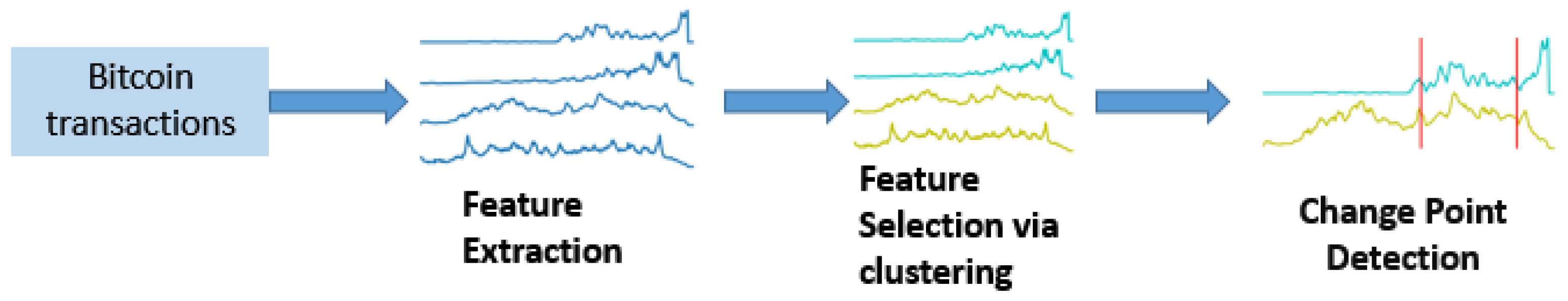
This section presents the results derived by the application of the proposed framework to two different datasets containing Bitcoin transactions that were linked to illicit activities: Pirate@40, who was involved in a high-yield investment programme (HYIP) scam, and the MintPal exchange platform that was hacked.
4.1. Experimental Setup
To showcase and evaluate the applicability of the proposed change point detection framework in identifying potential illicit addresses in Bitcoin transactions, two high profile Bitcoin entities, which involved illicit activities and their timeline was covered in news outlets, social media, and Web forums have been selected. The effectiveness of the proposed method is validated by its capability to identify statistically significant changes in the evolution of the selected time series of features at time points which can be linked to occurrences of events that may indicate the existence of illicit actions; this validation method has been followed due to the absence of ground truth about the time locations of the statistically significant changes in the time series of interest. Within a different context, a similar approach is included, for example, in
Gerlach et al. (
2019) regarding a bubble analysis of the Bitcoin to USD price dynamics from January 2012 to February 2018. Also,
Theodosiadou et al. (
2021) adopts analogous approach in the context of detecting change points in terrorism-related online content. Next, we describe the two Bitcoin entities that have been analysed.
The first entity was a user with the nickname
Pirate@403; this entity was also analysed by
Toyoda et al. (
2018b).
Pirate@40 orchestrated a kind of a Ponzi scheme—a high-yield investing programme (HYIP) scheme. Such schemes offer absurdly high interest rates in order to lure new investors, while they use new investments to pay out earlier ones.
Pirate@40 started his scheme in November 2011 gradually offering up to 7% interest per week. He mainly operated in the
www.BitcoinTalk.org (accessed on 14 July 2023) forum where he advertised the high interest rates that were promised to reach up to 11%. He progressively amassed investors until the beginning of August 2012 when he announced a reduction in the interest rate to 3.9%. Later in the same month he declared default, and as a result, he was charged for the misappropriation of about 146,000 Bitcoin out of the total 764,000 that were raised over the whole scheme’s life cycle
4. The total amount corresponded to approximately USD 4,500,000 based on the average Bitcoin price at that period.
The second entity for evaluation is the
MintPal5 cryptocurrency exchange platform; to the best of our knowledge, this entity has not been previously analysed.
MintPal provided exchange services between cryptocurrencies and fiat money. Moreover, it provided cryptocurrency wallet services for its customers that were entrusting the platform with their crypto assets.
MintPal was founded in February 2014 and gradually became a popular exchange platform that traded on multiple crypto assets (including Bitcoin). On 13 July 2014, the platform was hacked and 8,000,000 Vericoin (valued USD 2,000,000) were stolen. Notably, the Vericoin community decided to rollback the blockchain to a point before the hack, effectively annulling the stolen Vericoins. Despite that, a few months after the hack, the Mintpal platform was sold to the digital currency service provider Moolah Ltd. (London, UK). The expressed intent was to use
MintPal as the major altcoin exchange platform of Moolah. The merging of the two companies was plagued with technical difficulties, and finally, on October 2014, more than 3700 Bitcoins went missing. Unlike the first incident, in this case the stolen amount was not able to be restored, resulting in losses equivalent to USD 1,500,000 at that period. Contrary to the first hacking incident, the events on October 2014 were attributed to Moolah’s CEO, who participated in the merging of the two companies.
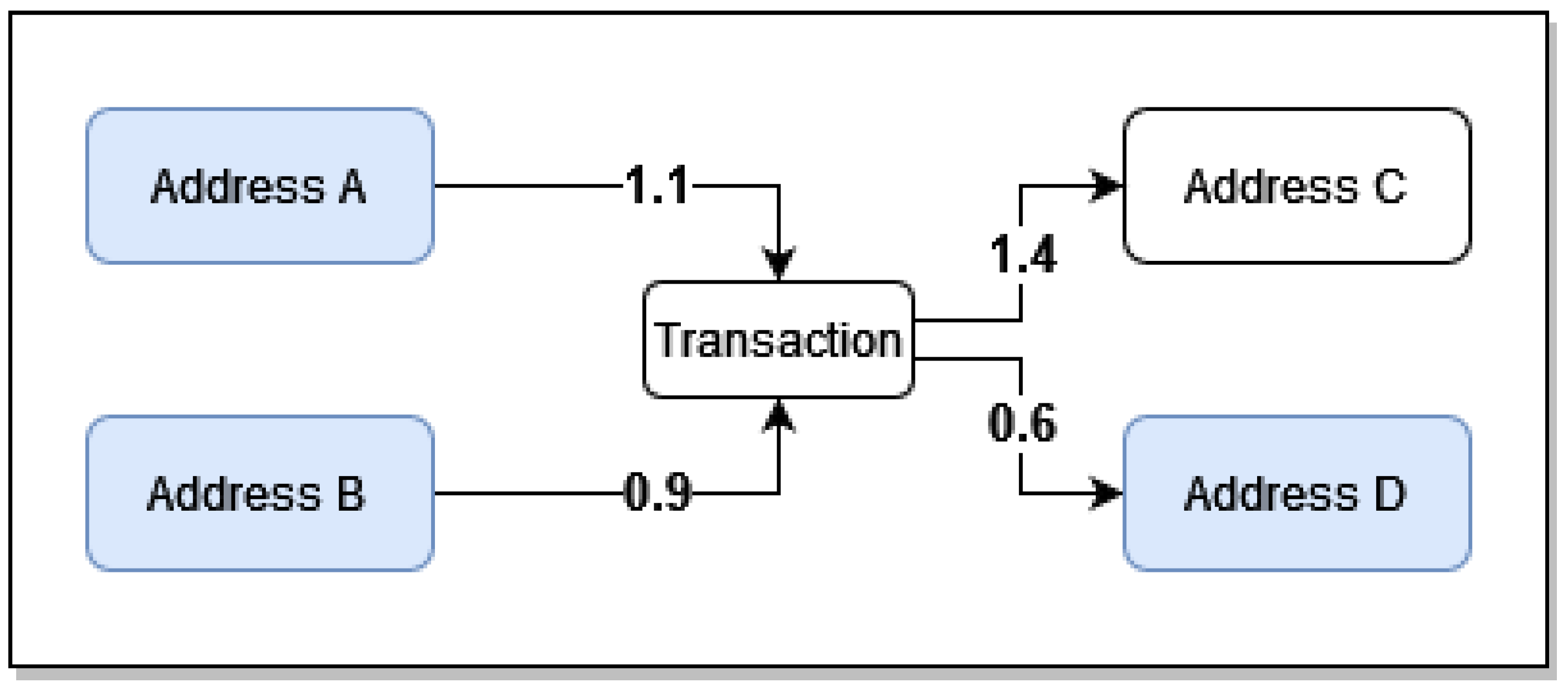
The datasets of the two entities were retrieved from the Wallet Explorer website
6, which contains lists of Bitcoin transactions for specific entities. The transactions are owner-based, meaning that multiple Bitcoin addresses are combined into a single entity (wallet). This is because one entity typically uses multiple Bitcoin addresses throughout its lifetime. For example,
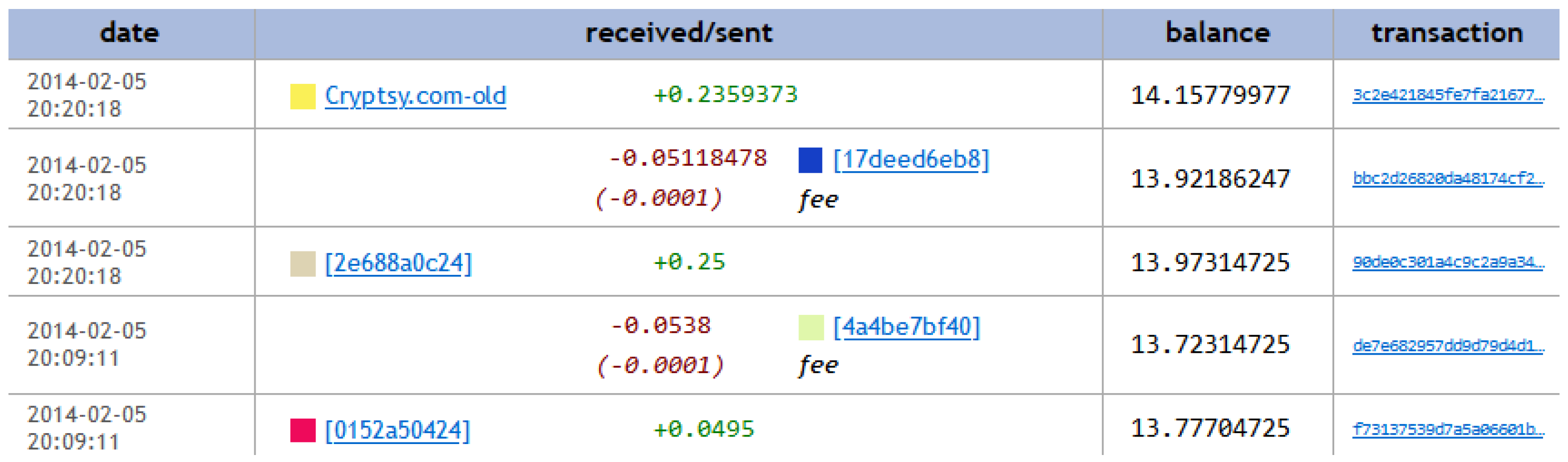
Figure 5 shows five transactions of the
MintPal entity as provided by Wallet Explorer, where the columns represent:
The timestamp of the transaction;
The ID of the spending entity;
The transacted amount;
The ID of the receiving entity;
The progressive balance;
The blockchain transaction ID.
The receiving/spending IDs are attributed by the Wallet Explorer website and they do not hold a particular importance other than to distinguish between entities. The balance changes progressively according to the transaction, starting from the bottom row and moving up. For example, the last row indicates that the MintPal entity received 0.0495 Bitcoin from the entity with ID 0152a50424 and the row above indicates that the entity MintPal sent 0.538 to 4a4be7bf40, and 0.001 was used up as a fee.
In what follows, the proposed framework is applied to the two abovementioned Bitcoin entities that were involved in illicit activities. The analysis includes the three steps described in detail in
Section 3: (a) feature extraction, where 28 features are extracted from the transaction history and their values are aggregated on a daily basis resulting in the creation of 28 time series; (b) feature selection, where the relevant time series are grouped into clusters; and (c) change point detection, where the multivariate time series created by the medoids of the formulated clusters is analysed aiming to identify statistically significant changes in it. For the implementation of the change point detection algorithm presented in
Section 3.3, the “ecp” R package has been used.
4.2. Pirate@40 HYIP Scheme
In this section the applicability of the proposed framework is illustrated and evaluated using the Pirate@40 dataset and the relevant results are presented.
Feature extraction. The features mentioned in
Table 1 are extracted from the
Pirate@40 dataset per day, resulting in the construction of 28 time series with length
(days) each, covering the period 22 from June 2011 until 26 August 2012.
Feature selection. To categorise the extracted features into homogeneous clusters so as to use the medoid time series of each class as input to the CPD algorithm, the PAM clustering algorithm is applied to the constructed time series using the DTW distance. In order to estimate the optimal number of clusters, we use the
Silhouette index for the clustering validation, selecting the number of clusters that maximises its value (see
Section 3.2); the results are presented in
Table 2 for different numbers of clusters.
Based on
Table 2, the maximum value of the Silhouette index related to the
Pirate@40 entity is achieved with the use of five clusters. Therefore, we proceed with the clustering of the extracted time series features into five groups. The formulated clusters, as well as, the medoid time series of each one of them, are presented in
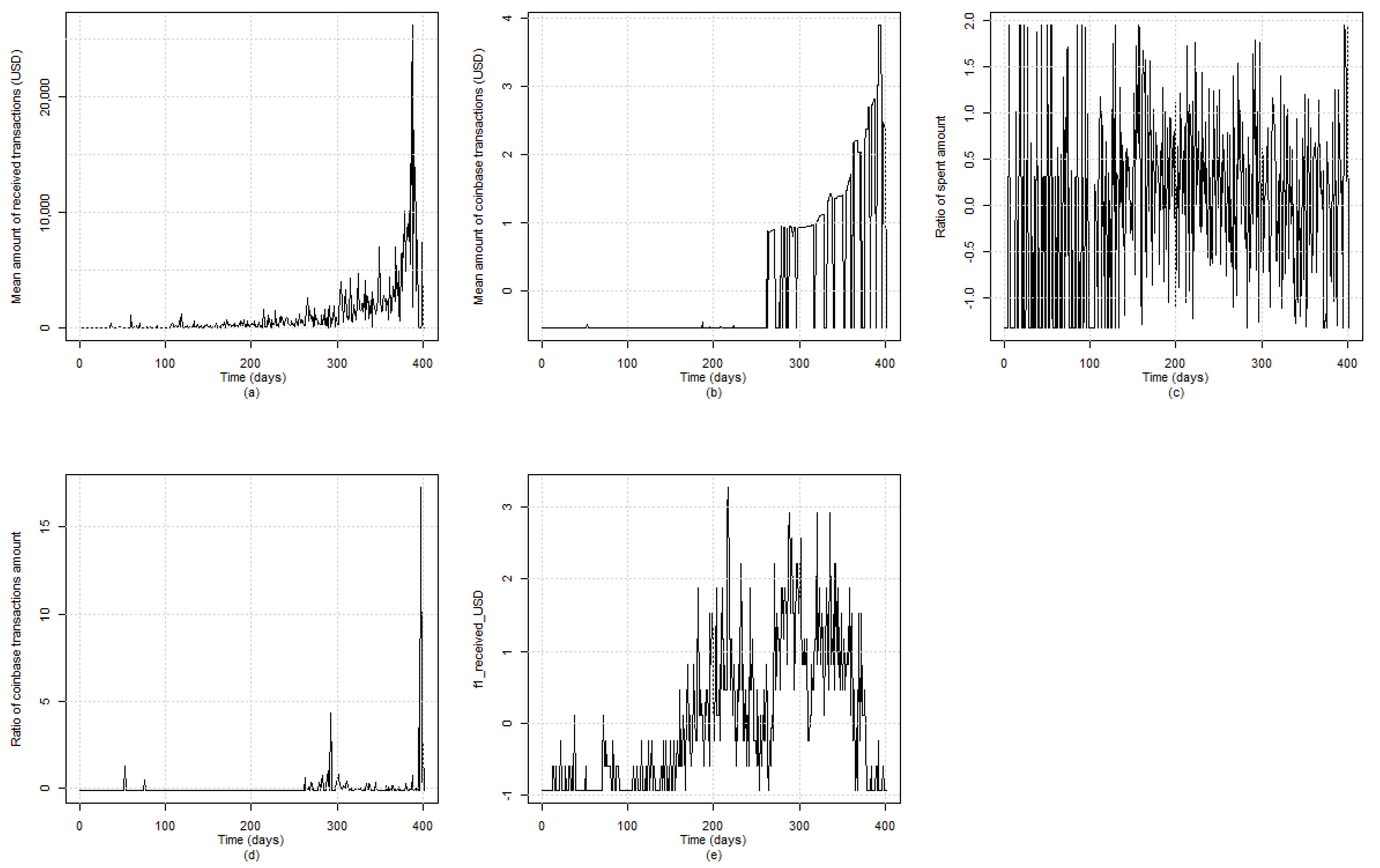
Table 3, while
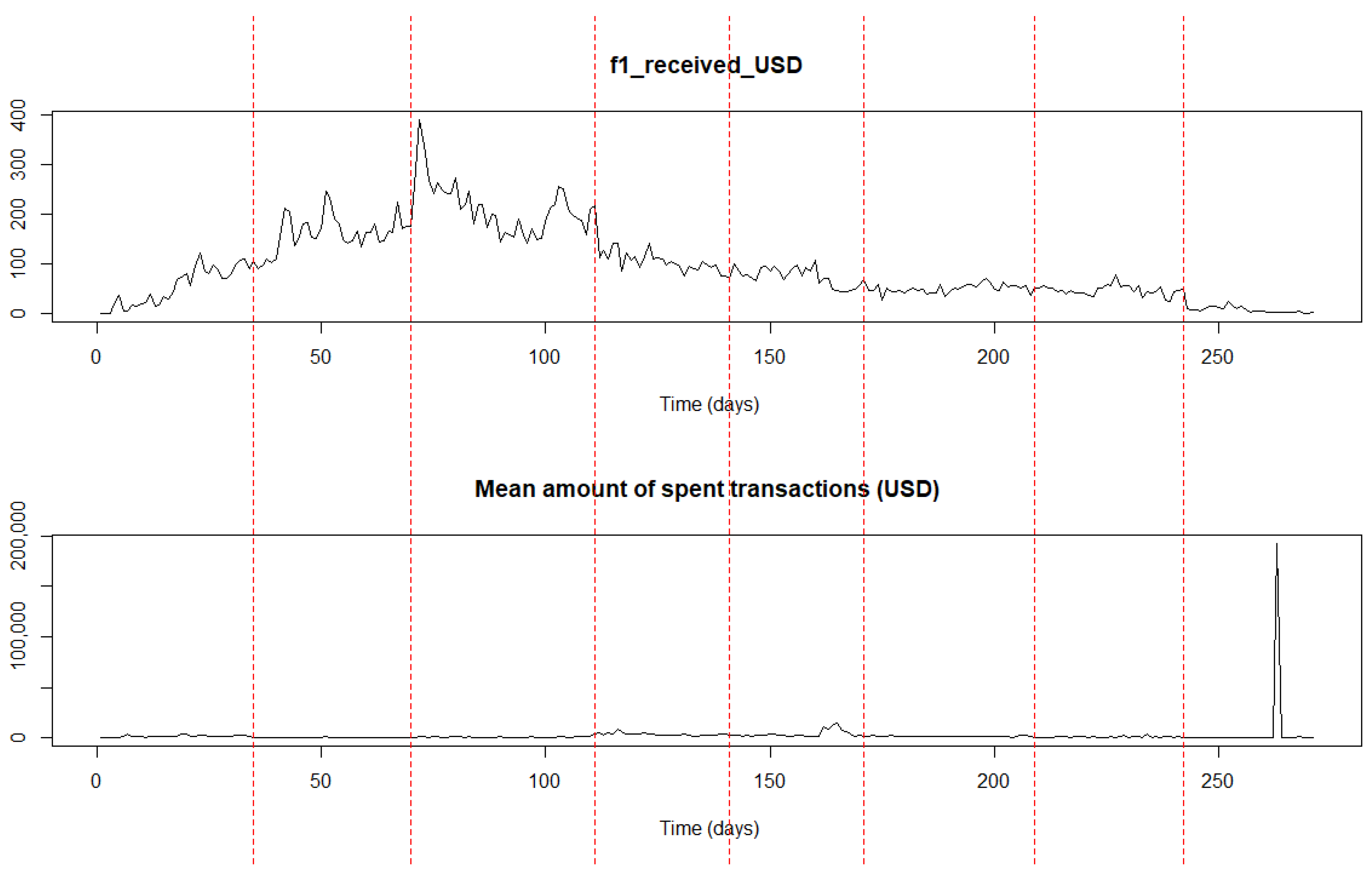
Figure 6 depicts graphically the evolution of the medoid time series.
Change point analysis. Using the medoids of each of the five clusters, we result in creating a five-dimensional time series which constitutes the input to the CPD algorithm presented in
Section 3.3. The results of the change point analysis in the multidimensional time series are presented in
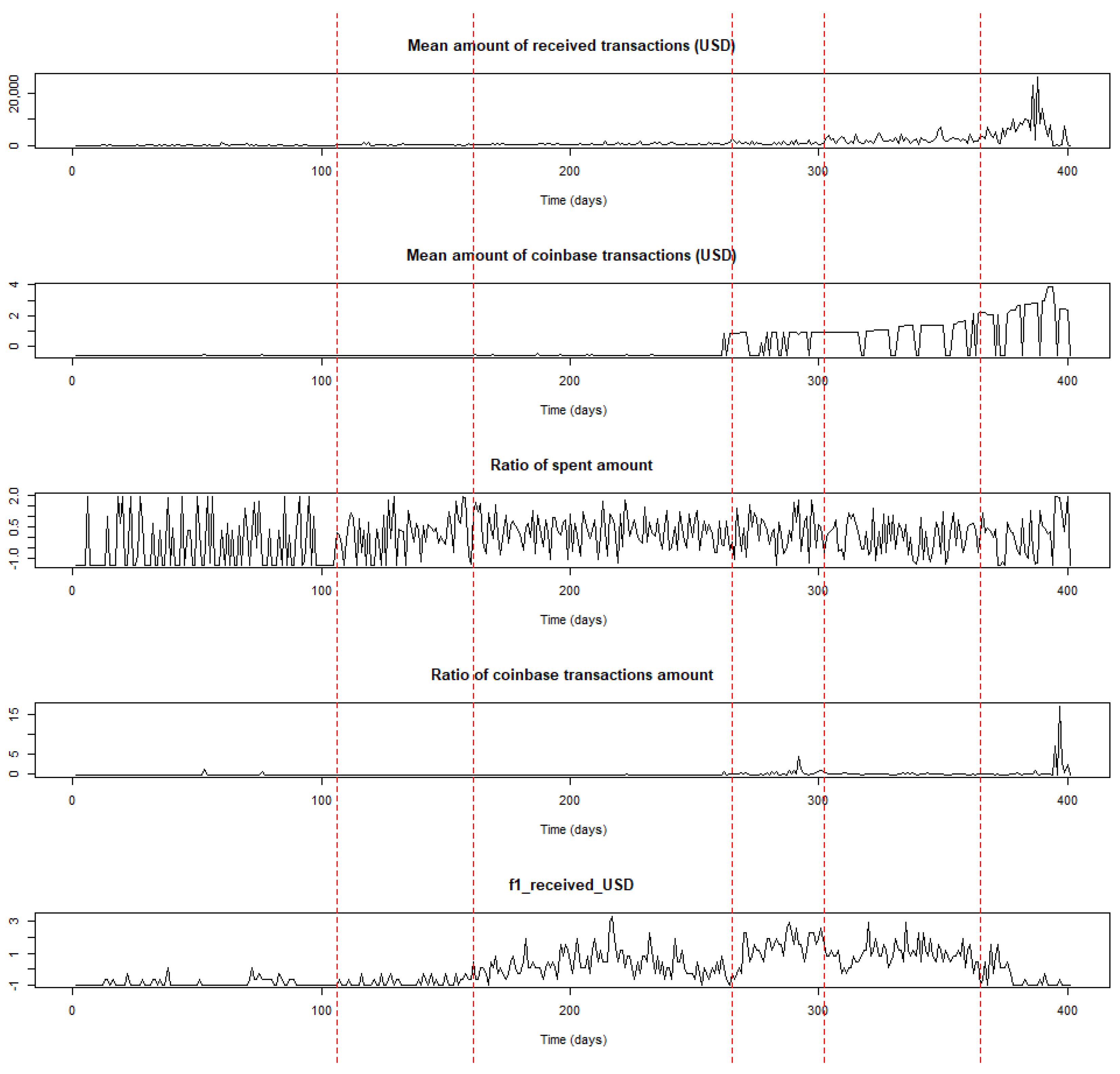
Table 4 and are depicted graphically in
Figure 7.
Some observations can be drawn by taking into account the time locations of the estimated change points and incidents (e.g., forum announcements) that occurred during the transaction period related to the
Pirate@40 wallet. The first estimated change point at time location
t = 106 (5 November 2011) signifies a period where transaction activity mainly started to occur, without intensity, though this characteristic is more obvious when considering the evolution of the time series related to the frequency of received transactions, where the range of the USD amount is greater than
and less than or equal to 10. It is noted that the time series of the number of transactions per day evolves similarly, since they both belong to the fifth cluster. This change in trend may be partially related to a major announcement that took place at the beginning of November 2011 based on the related topic in the
Bitcointalk forum where it was announced by the
Pirate@40 user that the
Bitcoin Savings & Trust will be closed down
7.
The period between the second estimated change point at time location
t = 161 (30 December 2011) and the third one at
t = 265 (12 April 2012) appears to have an increasing trend, especially when considering the time series related to the ratio out amount and the frequency of the received transactions where the values of the USD amount lie between
and 10. Subsequently, it can be argued that the estimated change point at
t = 161 signifies an upward change related to the transactions activity; this may be linked to the opening of the website of
Pirate@40’s HYIP that occurred in December 2011, according to the related topic in the
Bitcointalk forum
8, and may have triggered such an intense activity.
Regarding the period between
t = 265 (12 April 2012) and the fourth estimated change point at
t = 302 (19 May 2012), it can be argued that a more intense activity in transactions is identified compared to the previous period. In this case, time location
t = 265 signals the initialisation of a more intense upward trend in the transactions activity which could be partially justified by the fact that on 10 April 2012
Pirate@40 changed their scheme name
9; this may have contributed to the continuation of the upward trend in a more intense way.
Commenting on the period between
t = 302 (19 May 2012) and the fifth estimated change point at
t = 365 (21 July 2012), it can be argued that the related time series appear to have a stable trend at a high level; this means that the fourth estimated change point at
t = 302 indicates the initialisation of a period with stable trend in transactions activity. Finally, the last period starting at
t = 365 (21 July 2012) until the wallet was defunct (26 August 2012), indicates the existence of a decreasing trend related to the medoid time series of the fifth cluster, and an increasing one in the remaining medoids. This may be partially linked to the fact that during July 2012
Pirate@40 changed its interest rate down from 7% to 5%
10.
Overall, based on the findings derived from the application of the proposed method to the Pirate@40 case, it can be concluded that the estimated change points in the time series of interest partially align with time instances of events that may have impacted its transaction activity.
4.3. The MintPal Exchange Platform
In this section, the applicability of the proposed framework is illustrated using the MintPal dataset.
Feature extraction. The features mentioned in
Table 1 are extracted from
MintPal dataset per day, resulting in the construction of 28 time series with length
(days) each, spanning the period from 2 February 2014 until 31 October 2014.
Feature selection. Similarly to the
Pirate@40 case, we categorise the extracted features into clusters using the PAM clustering method with the DTW distance, and the optimal number of clusters is selected using the
Silhouette index; the values of this index for different number of clusters are presented in
Table 5.
The maximum value of the
Silhouette index is achieved with the use of two clusters, and therefore, we proceed with the clustering of the extracted time series features into two groups.
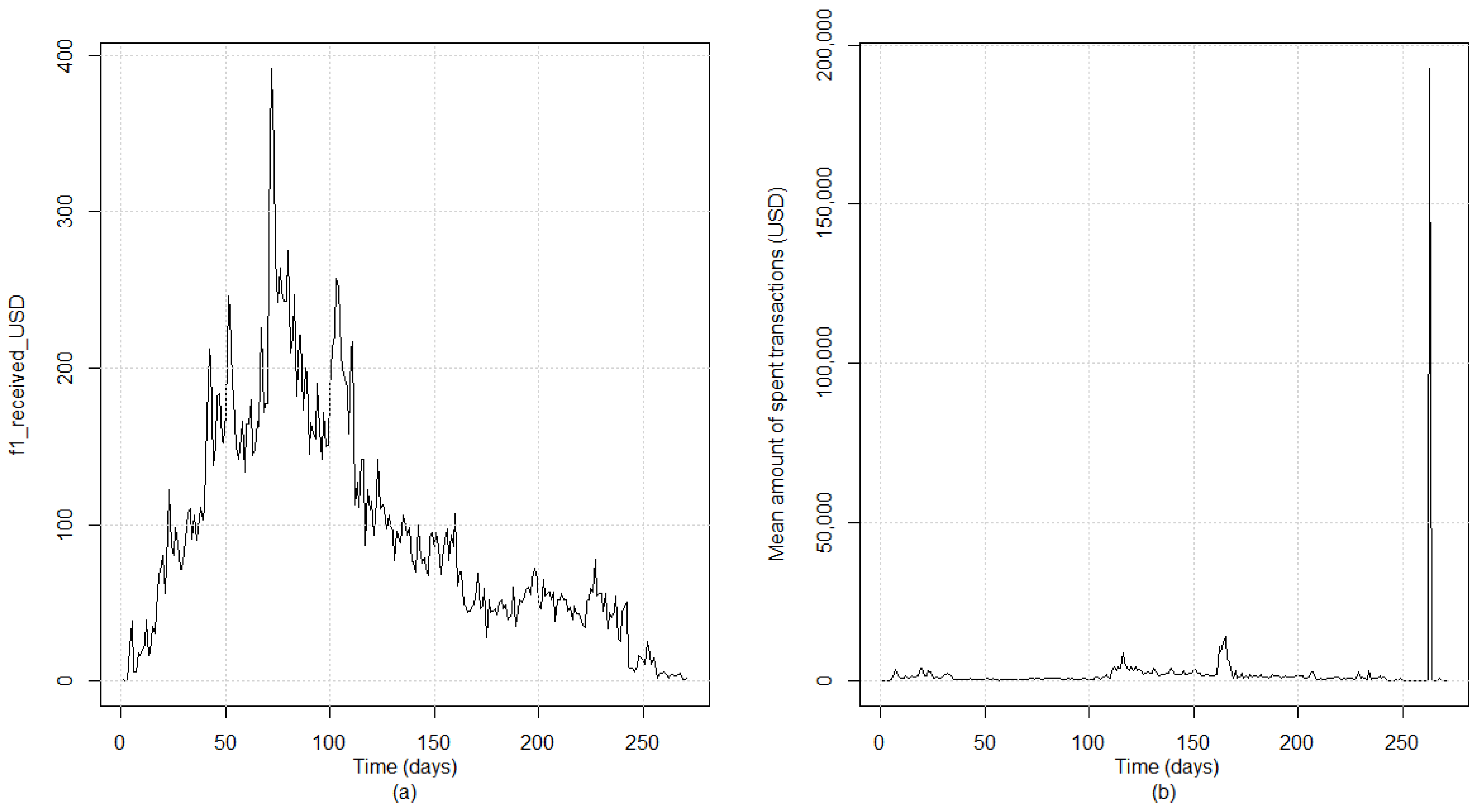
Table 6 presents the clusters and the medoid time series for each one of them, while
Figure 8 showcases the evolution of the medoids over time.
Change point analysis. Using the medoids of each of the two clusters, we result in creating a two-dimensional time series which constitutes the input of the CPD algorithm presented in
Section 3.3. The results of the change point analysis in the multidimensional time series are presented in
Table 7 and are depicted graphically in
Figure 9.
Similarly to the
Pirate@40 case, some observations could be drawn regarding the
MintPal crypto exchange platform. The period between the first estimated change point at
t = 35 (9 March 2014) and the second one at
t = 70 (13 April 2014) depicts a more intense upward trend related to the transaction activity compared to the previous one; this characteristic is more obvious especially when considering the time series of the frequency of the received transactions where the values of the USD amount are greater than
and less than or equal to 10. It is also mentioned that the time series of the number of transactions per day evolves similarly, since both features belong to the first cluster. In other words, time location
t = 35 initiates a period with a more intense upward trend in the extracted features. This could be attributed partially to two facts: (a)
MintPal was founded in February 2014 (See Note 5 above) and consequently there was a gradual increase in transactions since then, and (b) a new cryptocurrency was added in
MintPal in early March 2014
11 that may have boosted the transaction activity.
Regarding the period between time locations
t = 70 (13 April 2014) and
t = 111 (24 May 2014), it could be argued that a stable trend at high level is depicted, especially in the medoid time series of the second cluster. This means that the high transaction activity continues from the previous period and stabilises. The high engagement related to a tweet commenting on the addition of the
BlackCoin in
MintPal constitutes an indication of this high interest (See Note 11 above). In the remaining periods formulated by the estimated change points, either a decreasing trend is depicted related to the medoid time series of the first cluster and an increasing one in the medoid of the second cluster, respectively (e.g., during the period between
t = 111 (24 May 2014) and
t = 141 (23 June 2014), or a stable one at a low level is depicted in both cases (e.g., during the period between
t = 171 (23 July 2014) and
t = 209 (30 August 2014). These identified trends may be partially related to a series of events that may have triggered the change in the transaction activity in
MintPal, like the attack it faced on 13 July 2014
12, the fact that it was purchased by the digital currency services provider Moopay late July 2014
13, and the technical issues that were raised due to the relaunch of
MintPal exchange early October 2014
14.
The findings obtained from applying the proposed change point detection framework in the MintPal dataset are similar with the results of the first one in the Pirate@40 entity. These similarities suggest that the framework could successfully identify links between time instances and events that may influence the transaction activity.