Modeling and Risk Analysis of Chemical Terrorist Attacks: A Bayesian Network Method
Abstract
1. Introduction
2. Related Work
- (1)
- Based on real case data and expert experience, a Bayesian network is constructed to model the risk of chemical terrorist attacks in depth.
- (2)
- We model and analyse chemical terrorist attack risk from multiple sources, such as terrorist organisations, defensive forces, and urban environments to capture the dynamic evolution of risk and propose prevention strategies.
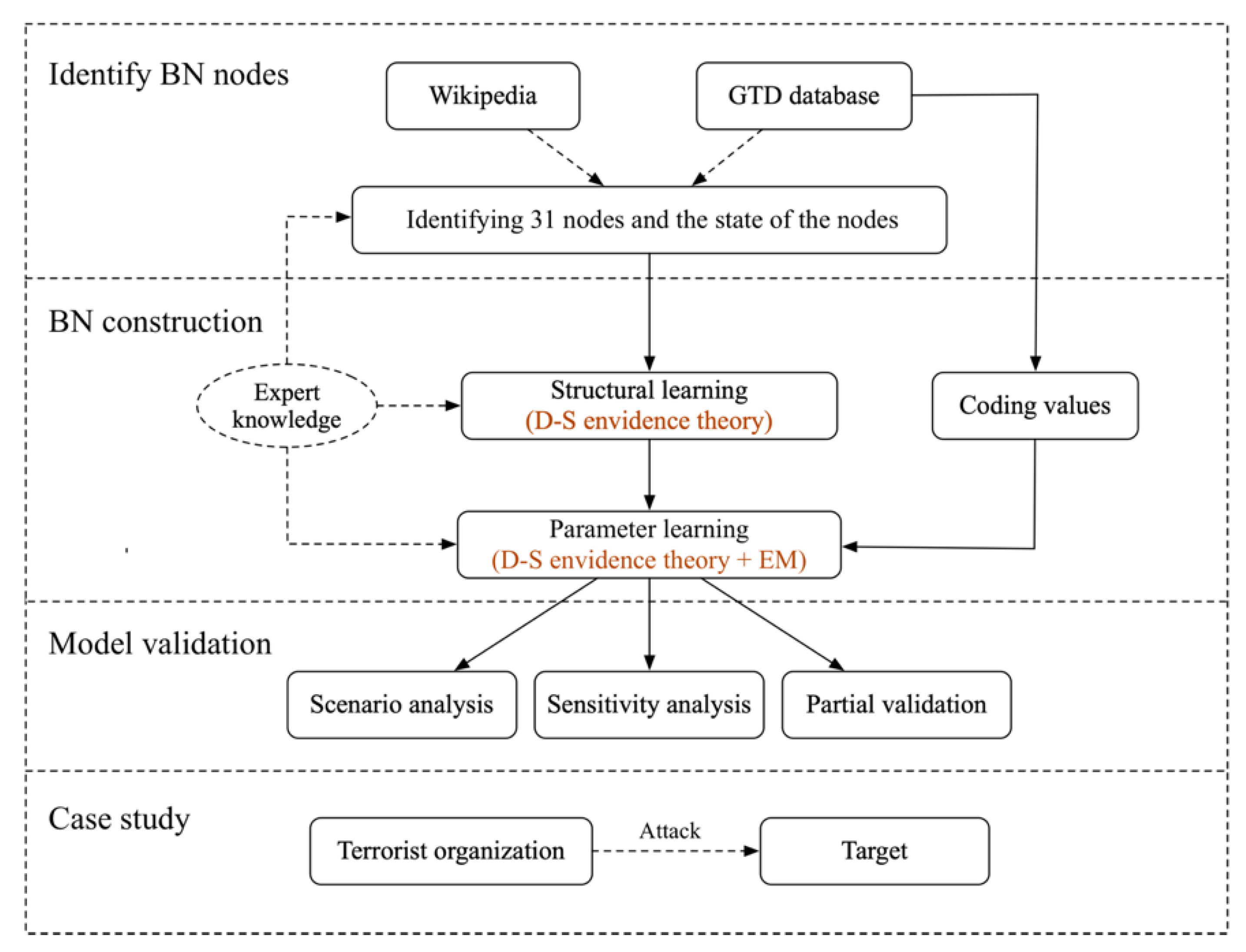
3. Bayesian Network Construction
3.1. Steps to Construct Chemical Terrorist Attack Bayesian Network
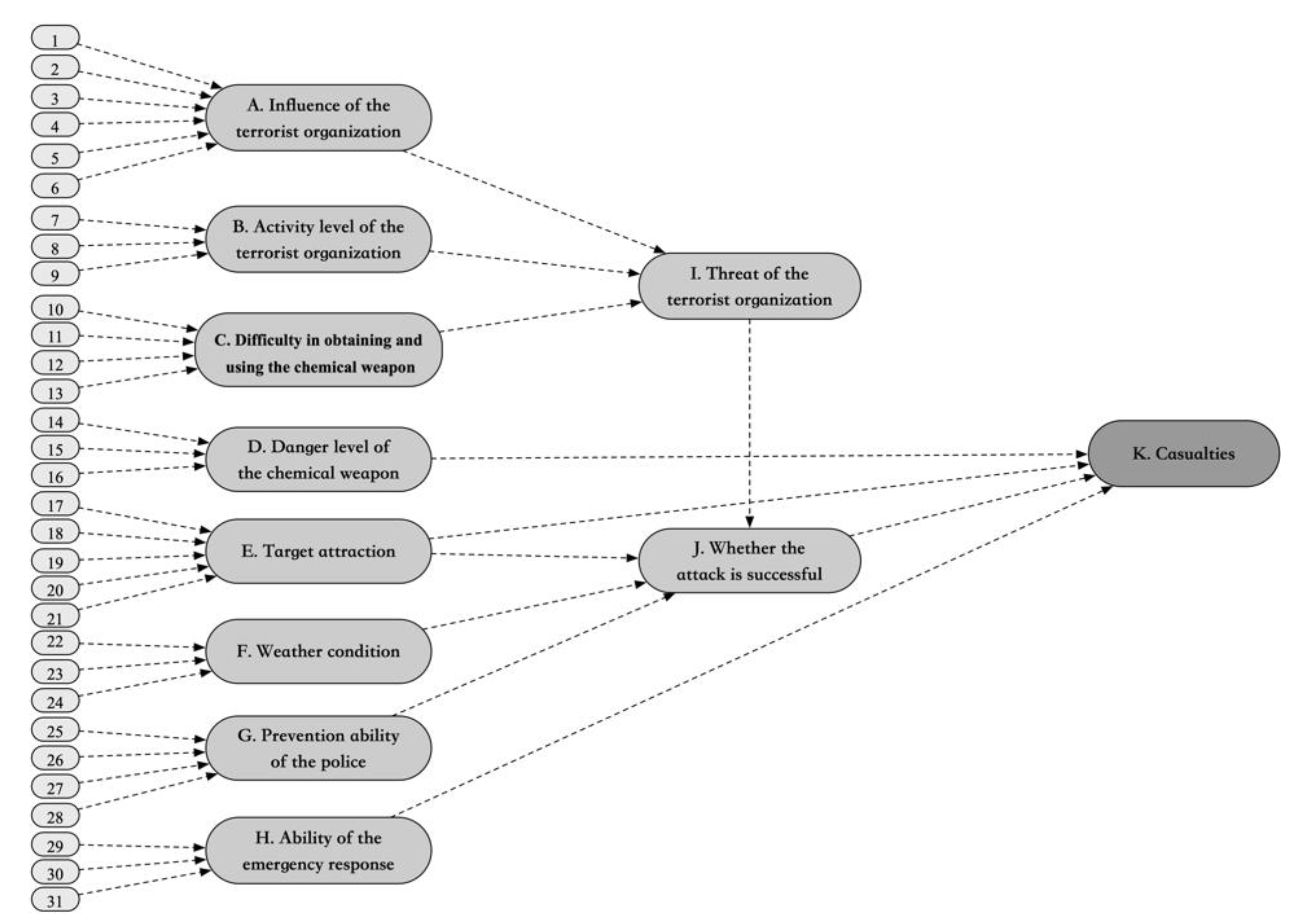
3.2. States of the Parent and Child Nodes
3.3. Determination of BN Structure
3.4. Determination of Probability Distributions of BN Nodes
3.4.1. Learning Probability Distributions Based on Samples
3.4.2. Learning Probability Distributions Based on Expert Experience
3.5. Model Validation
3.5.1. Expert Validation of Scenarios
3.5.2. Sensitivity Analysis
3.5.3. Partial Validation
- (1)
- If the prior probability of the parent node slightly decreases/increases, the posterior probability of the corresponding child node should also change accordingly.
- (2)
- The change in the probability distribution of the parent node should have a consistent impact on the child nodes.
- (3)
- The total impact of the combination of probability changes from m attributes on the value should always be greater than from the set of m − n (n ∈ m).
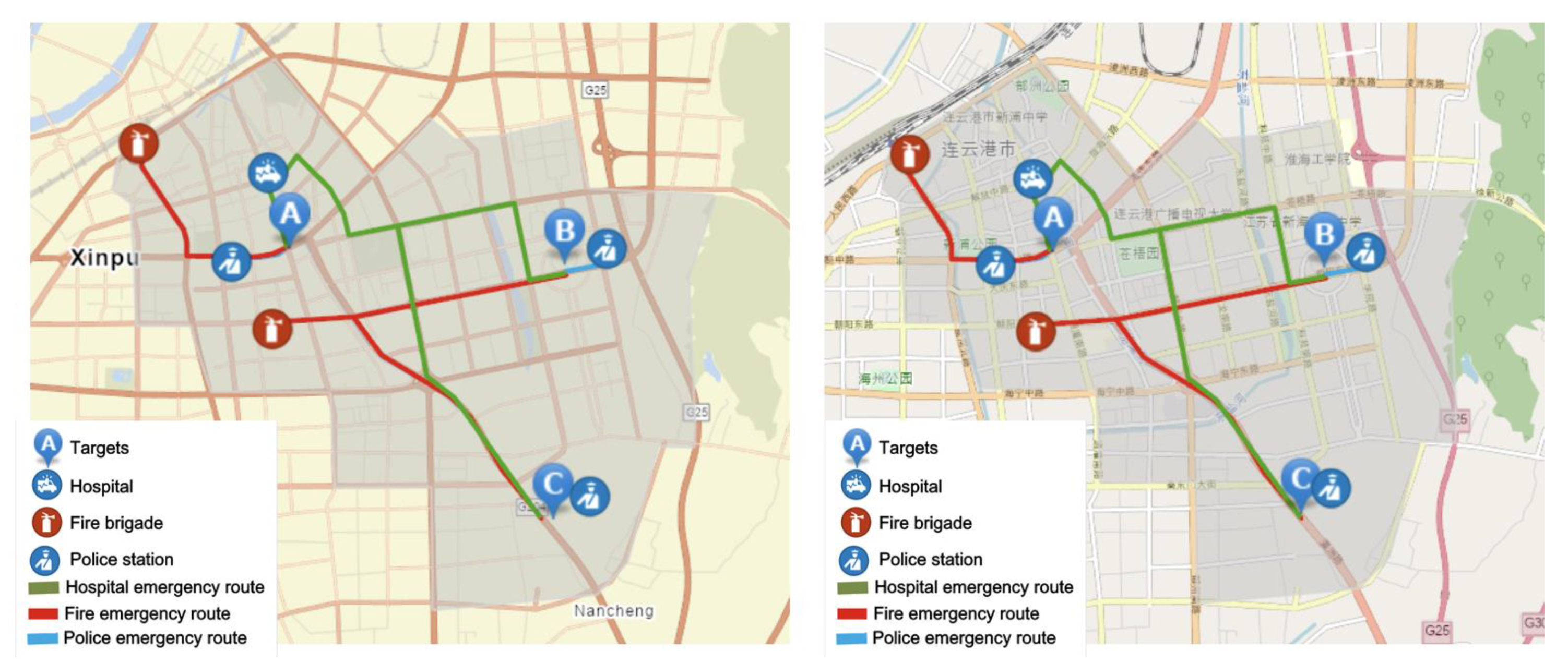
4. Case Study: Haizhou District, Lianyungang City
4.1. Target Information
4.2. Terrorist Organisation Information
4.3. Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A
- Average educational level. The average education level is divided into three categories: high, medium and low. Low means that members are mostly below primary school level, high means members include many college diplomas, doctorates, or researchers. The medium means the members have a high school education level [42].
- Technical background. There are three technical backgrounds, high, medium and low. The technical background is whether there is background knowledge related to chemistry and weapon manufacturing. With this kind of knowledge, the organisation is more dangerous [42].
- Social relations and organisational components. High-impact terrorist organisations generally have complex social relationships. Moreover, it is easier to launch attacks through complex social relations and more difficult to prevent. We manually assign the specific values by looking up information about terrorist organisations in Wikipedia and related news [42].
- Whether they have been reported recently. We look at similar terrorist attacks or attacks of the same organisation in the GTD. If the time interval is within one month, then the organisation has been reported and needs to be vigilant.
- Whether they ever launched chemical attack. We check in the GTD to see if any attacks were carried out using similar means in similar locations, or if a terrorist organisation has repeatedly carried out chemical terrorist attacks.
- Whether they made a statement or threat. Some terrorist organisations will threaten and intimidate before the attack, causing people to panic. Terrorist organisations that make such statements are often more active.
- Whether they have technical support. We look for information on terrorist organisations on the Internet and perform manual evaluations and assignments [38].
- Whether they have the capabilities of storing and transporting the chemical weapon. We manually assign values based on GTD and Wikipedia data.
- Whether they have the ability to launch the chemical attack. We manually assign values based on GTD and Wikipedia data, such as the ordinary attacks that the terrorist organisation has launched [38].
- Weapon types. By reviewing literature [3,4] and historical cases, we divide weapon types into seven types: (1) Neurotoxic agent, which is a class of agents that can damage the nervous system, mainly includes sarin, soman, and VX. People can cause poisoning through inhalation or skin absorption. Nerve agents are fast-killing, extremely lethal, and deadly. (2) Erosive poison. It is a kind of poison that can make cells and tissues necrotic and ulcerated, mainly including mustard gas and Louis gas. People cause poisoning through inhalation or skin contact. The poisoning effect is usually slow. (3) Systemic toxic agent. It is a class of poisons that can destroy the oxidative function of tissue cells, mainly includes hydrocyanic acid and cyanogen chloride. (4) Disabled poison. It is a poison that can cause mental and motor dysfunction and temporarily deprive personnel of combat effectiveness. People can cause poisoning through inhalation, and the poisoning effect is relatively rapid. (5) Choking poison. It is a type of poison that stimulates the respiratory tract and causes pulmonary oedema and suffocation, mainly includes phosgene. People can cause poisoning through inhalation, and the poisoning effect is slow. (6) Irritating poison. It is a class of poisons that can irritate the eyes, upper respiratory tract and skin, mainly includes Siez (CS), acetophenone, Adam’s gas, people can cause poisoning through inhalation and contact. (7) Corrosive objects, mainly a mixture of acid and alkali, such as nitric acid, sulfuric acid, sodium hydroxide, these poisons play a corrosive role. (8) Mixed poisons refer to a mixture of multiple poisons that cannot be accurately classified [39,42].
- Delivery method. Hu concluded that the impact of the form of emission of nuclear substances on the diffusion distribution is hugely significant [52]. For example, nuclear terrorist attacks are mostly realised by explosions, the discharge time is short, the initial velocity is large, and the diffusion distribution is broader and quicker. Chemical substances have similar characteristics. Chemicals can be released in a variety of ways, including volatilisation, water-solubility, spraying, and explosive dispersion [38].
- Chemical dose. Even small amounts of neurotoxins are still very dangerous, corrosive toxins are often more abundant. Therefore, we added the node and divide it into four categories: large, medium, small and unknown. The dose of chemical weapons directly affects the level of bomb explosions and casualties [56].
- Population density. According to the geographic information system (GIS) of the case studied, we divided population density into three levels, namely “over 1000 people/km2”, “500 to 1000 people/km2” and “less than 500 people/km2”. Population density directly affects the number of casualties caused by bomb explosions. As in the areas with high population density, the risk of serious casualties will increase [42].
- Population movement There are three types of population movement: high, medium and low. For example, the population movement in subway stations and shopping malls is high, while the level of government is medium, the level of some remote residential areas or parks is low.
- Traffic condition. Traffic condition refer to whether it is conducive to evacuation, rescue, rapid response. In transportation hubs such as railway stations, the traffic conditions are better, but in the suburbs and mountain areas, the traffic conditions are poor.
- Whether it is a high-value target. High-value locations includes: urban lifeline systems such as transportation, energy, communications, water supply and drainage; densely populated places, such as hotels, restaurants, shopping malls, bazaars, stadiums, halls, and public entertainment venues and other public gathering places; important buildings and places: such as government office buildings, stadiums, halls; the important security goal, including humanities and historical sites, the army, and public security organs [38,39,42].
- Wind speed. We have borrowed from the simulation of the risk evolution of the “dirty bomb” terrorist attack [50,52,57]. The diffusion of chemical substances is similar to the dirty bomb, so we have added wind speed and direction to the weather condition. We divide wind speed into three states according to the actual situation of the case they study, namely “less than 2 m/s”, “2 m/s to 4 m/s” and “more than 4 m/s”.
- Precipitation. Hu pointed out that wind and precipitation have a significant effect on the atmospheric diffusion of nuclear matter [52]. Chemicals have similar atmospheric diffusion characteristics. According to the precipitation of Lianyungang, there are four levels of precipitation: (1) heavy; (2) medium; (3) less; (4) very little or dry.
- Patrol. Police usually walk around to check the highly attractive locations which is more dangerous. In terms of patrol frequency of our case, there are two states:”> two times” and “<two times” [56]
- Security check. Security check are designed to detect contraband and dangerous people by inspecting people or vehicles in an area. We classify security check into yes and no [56].
- Surveillance. Surveillance means monitoring a specific area and sending images or video data to the police to assess the safety of the public. We divide monitoring into two states: “24 h coverage” and “non-24 h coverage” [56].
- Police investigation. We use “yes” and “no” to indicate whether chemical weapon attacks can be detected in advance [56].
- Hospital emergency response. The node means that after a chemical terrorist attack, emergency response measures such as rapid hospital rescue can be divided into “on time” or “delayed.”
- Fire emergency response. Fire emergency response means that after a chemical terrorist attack
- Police emergency response. Public security emergency response refers to quickly control the order of an incident and organise evacuation after a chemical terrorist attack.
- A. Influence of the terrorist organisation. Terrorist organisations with different influences have different threats. For example, ISIS has a greater influence, and its threat is also greater [38].
- B. Activity level of the terrorist organisation. The active level of a terrorist organisation has a strong relationship with his current threat level. The organisations that have repeatedly launched terrorist attacks recently are more prone to the vigilance of the defense than the terrorist organisations that have not heard of it for a long time.
- C. Difficulty in obtaining and using the chemical weapon. The difficulty of acquiring weapons determines whether terrorist organisations can launch multiple chemical weapons attacks and reflects the degree of threat [38].
- D. Danger level of the chemical weapon. Different levels of chemical weapons cause different casualties. The degree of danger is influenced by weapon type, dose, and delivery method [38].
- E. Target attraction. Different objectives have different appeal to terrorists. We divide target attraction into high, medium and low. The different targets have an impact on the success of the attack [42]. The degree of target attraction is influenced by population density, population movement, traffic condition, location, whether it is a high-value target.
- F. Weather condition. Different climatic conditions have an impact on the success of the attack [52]. Weather condition is affected by wind speed, wind direction and precipitation
- G. Prevention ability of the police. High vulnerability objectives can be easily attacked. Prevention ability of the police is affected by patrol, security check, surveillance and police investigation. Different preventive capabilities have an impact on the success of the attack [38].
- K. Casualties. Casualties are essential indicators for assessing the consequences of a chemical weapons attack. We have summarised three types of casualties in chemical terrorist attacks based on the “Safety Production Incident Report”, “Chinese Investigation and Handling Rules”: “less than ten people died or less than 50 people were injured”, “11 to 30 people died or 51 To 100 injuries “and” more than 30 dead or more than 100 injured” [38,39,42,56].
References
- Evison, D.; Hinsley, D.; Rice, P. Chemical weapons. BMJ 2002, 324, 332–335. [Google Scholar] [CrossRef] [PubMed]
- Zhiqiang, X.; Bolin, X. Counter Nuclear, Chemical, Biological Explosion Terrorism—Threat Prevention Disposal; Chemical Industry Press: Xi′an, China, 2009. [Google Scholar]
- Santos, C.; El Zahran, T.; Weiland, J.; Anwar, M.; Schier, J. Characterizing chemical terrorism incidents collected by the Global Terrorism Database, 1970–2015. Prehospital Disaster Med. 2019, 34, 385–392. [Google Scholar] [CrossRef] [PubMed]
- Sezigen, S.; Ivelik, K.; Ortatatli, M.; Almacioglu, M.; Demirkasimoglu, M.; Eyison, R.; Kunak, Z.; Kenar, L. Victims of chemical terrorism, a family of four who were exposed to sulfur mustard. Toxicol. Lett. 2019, 303, 9–15. [Google Scholar] [CrossRef] [PubMed]
- Sezigen, S.; Eyison, R.K.; Ortatatli, M.; Kilic, E.; Kenar, L. Myelosuppression and acute hematological complications of sulfur mustard exposure in victims of chemical terrorism. Toxicol. Lett. 2020, 318, 92–98. [Google Scholar] [CrossRef]
- World Health Organization. Public Health Response to Biological and Chemical Weapons—WHO Guidance; WHO: Geneva, Switzerland, 2004; Volume 4, pp. 90–96. [Google Scholar]
- Ezell, B.C.; Bennett, S.P.; Von Winterfeldt, D.; Sokolowski, J.; Collins, A.J. Probabilistic risk analysis and terrorism risk. Risk Anal. Int. J. 2010, 30, 575–589. [Google Scholar] [CrossRef]
- Greenberg, M.I.; Jurgens, S.M.; Gracely, E.J. Emergency department preparedness for the evaluation and treatment of victims of biological or chemical terrorist attack. J. Emerg. Med. 2002, 22, 273–278. [Google Scholar] [CrossRef]
- Luko, S.N. Risk management principles and guidelines. Qual. Eng. 2013, 25, 451–454. [Google Scholar] [CrossRef]
- Davis, L.E.; Melmed, A.; Krop, R. Individual Preparedness and Response to Chemical, Radiological, Nuclear, and Biological Terrorist Attacks; Rand Corporation: Santa Monica, CA, USA, 2003. [Google Scholar]
- Miller, S.E. Toxic Terror: Assessing Terrorist Use of Chemical and Biological Weapons; MIT Press: Cambridge, MA, USA, 2000. [Google Scholar]
- Beaton, R.; Murphy, S. Psychosocial responses to biological and chemical terrorist threats and events: Implications for the workplace. AAOHN J. 2002, 50, 182–189. [Google Scholar] [CrossRef]
- Marrs, T.T.; Maynard, R.L.; Sidell, F. Chemical Warfare Agents: Toxicology and Treatment; John Wiley & Sons: Hoboken, NJ, USA, 2007. [Google Scholar]
- Szinicz, L. History of chemical and biological warfare agents. Toxicology 2005, 214, 167–181. [Google Scholar] [CrossRef]
- Laurent, J.; Richter, F.; Michel, A. Management of victims of urban chemical attack: The French approach. Resuscitation 1999, 42, 141–149. [Google Scholar] [CrossRef]
- Bennett, R.L. Chemical or biological terrorist attacks: An analysis of the preparedness of hospitals for managing victims affected by chemical or biological weapons of mass destruction. Int. J. Environ. Res. Public Health 2006, 3, 67–75. [Google Scholar] [CrossRef] [PubMed]
- Reniers, G.L.; Audenaert, A. Preparing for major terrorist attacks against chemical clusters: Intelligently planning protection measures wrt domino effects. Process Saf. Environ. Prot. 2014, 92, 583–589. [Google Scholar] [CrossRef]
- Chatterjee, S.; Abkowitz, M.D. A Methodology for Modeling Regional Terrorism Risk. Risk Anal. 2011, 31, 1133–1140. [Google Scholar] [CrossRef] [PubMed]
- Piegorsch, W.W.; Cutter, S.L.; Hardisty, F. Benchmark analysis for quantifying urban vulnerability to terrorist incidents. Risk Anal. 2007, 27, 1411–1425. [Google Scholar] [CrossRef] [PubMed]
- Monroe, J.; Ramsey, E.; Berglund, E. Allocating countermeasures to defend water distribution systems against terrorist attack. Reliab. Eng. Syst. Saf. 2018, 179, 37–51. [Google Scholar] [CrossRef]
- Keeney, R.L. Modeling values for anti-terrorism analysis. Risk Anal. 2007, 27, 585–596. [Google Scholar] [CrossRef]
- Keeney, G.L.; von Winterfeldt, D. Identifying and Structuring the Objectives of Terrorists. Risk Anal. 2010, 30, 1803–1816. [Google Scholar] [CrossRef]
- Dillon, R.L.; Liebe, R.M.; Bestafka, T. Risk-Based Decision Making for Terrorism Applications. Risk Anal. 2009, 29, 321–335. [Google Scholar] [CrossRef]
- Rezazadeh, A.; Talarico, L.; Reniers, G.; Cozzani, V.; Zhang, L. Applying game theory for securing oil and gas pipelines against terrorism. Reliab. Eng. Syst. Saf. 2019, 191. [Google Scholar] [CrossRef]
- Regens, J.L.; Mould, N.; Jensen, C.J.; Graves, M.A.; Edger, D.N. Probabilistic Graphical Modeling of Terrorism Threat Recognition Using Bayesian Networks and Monte Carlo Simulation. J. Cogn. Eng. Decis. Mak. 2015, 9, 295–311. [Google Scholar] [CrossRef]
- White, G.; Porter, M.D.; Mazerolle, L. Terrorism risk, resilience and volatility: A comparison of terrorism patterns in three Southeast Asian countries. J. Quant. Criminol. 2013, 29, 295–320. [Google Scholar] [CrossRef]
- Willis, H.H.; LaTourrette, T. Using probabilistic terrorism risk modeling for regulatory benefit-cost analysis: Application to the western hemisphere travel initiative in the land environment. Risk Anal. Int. J. 2008, 28, 325–339. [Google Scholar] [CrossRef] [PubMed]
- Husmeier, D. Introduction to Learning Bayesian Networks from Data; Springer: London, UK, 2005. [Google Scholar]
- Cooper, G.F.; Herskovits, E. A Bayesian method for the induction of probabilistic networks from data. Mach. Learn. 1992, 9, 309–347. [Google Scholar] [CrossRef]
- Zerrouki, H.; Smadi, H. Bayesian Belief Network Used in the Chemical and Process Industry: A Review and Application. J. Fail. Anal. Prev. 2017, 17, 159–165. [Google Scholar] [CrossRef]
- Zhou, D.; Xu, H.; He, Y. An Unsupervised Bayesian Modelling Approach for Storyline Detection on News Articles. In Proceedings of the 2015 Conference on Empirical Methods in Natural Language Processing, Lisbon, Portugal, 17–21 September 2015; pp. 1943–1948. [Google Scholar]
- Wu, J.; Xu, S.; Zhou, R.; Qin, Y. Scenario analysis of mine water inrush hazard using Bayesian networks. Saf. Sci. 2016, 89, 239. [Google Scholar] [CrossRef]
- Zhang, C.; Wu, J.S.; Hu, X.F.; Ni, S.J. A probabilistic analysis model of oil pipeline accidents based on an integrated Event-Evolution-Bayesian (EEB) model. Process Saf. Environ. Prot. 2018, 117, 694–703. [Google Scholar] [CrossRef]
- Zhu, R.; Li, X.; Hu, X.; Hu, D. Risk Analysis of Chemical Plant Explosion Accidents Based on Bayesian Network. Sustainability 2019, 12, 1–20. [Google Scholar] [CrossRef]
- Zhang, X.; Hu, X.; Bai, Y.; Wu, J. Risk Assessment of Gas Leakage from School Laboratories Based on the Bayesian Network. Int. J. Environ. Res. Public Health 2020, 17, 426. [Google Scholar] [CrossRef]
- Argenti, F.; Landucci, G.; Reniers, G.; Cozzani, V. Vulnerability assessment of chemical facilities to intentional attacks based on Bayesian Network. Reliab. Eng. Syst. Saf. 2018, 169, 515–530. [Google Scholar] [CrossRef]
- Landucci, G.; Argenti, F.; Cozzani, V.; Reniers, G. Assessment of attack likelihood to support security risk assessment studies for chemical facilities. Process Saf. Environ. Prot. 2017, 110, 102–114. [Google Scholar] [CrossRef]
- Pate-Cornell, M.E.; Guikema, S.D. Probabilistic Modeling or Terrorist Threats: A Systems Analysis Approach to Setting Priorities Among Countermeasures. Mil. Oper. Res. 2008, 13, 89. [Google Scholar] [CrossRef]
- Wei, J.; Wang, J.; Yu, H. Terrorism threat assessment with multi-module Bayesian network. J. Univ. Chin. Acad. Sci. 2015, 32, 264–272. [Google Scholar]
- Fu, Z.; Xu, R.; Liu, W. Research on Terrorist Attack Warning Model Based on Bayesian Network. J. Catastrophol. 2016, 31, 184–189. [Google Scholar]
- LaFree, G.; Dugan, L. Introducing the global terrorism database. Terror. Political Violence 2007, 19, 181–204. [Google Scholar] [CrossRef]
- Olama, M.M.; Allgood, G.O.; Davenport, K.M.; Schryver, J.C.; Allgood, G.O.; Davenport, K.M.; Schryver, J.C. A Bayesian Belief Network of Threat Anticipation and Terrorist Motivations. In Sensors, and Command, Control, Communications, and Intelligence; Carapezza, E.M., Ed.; SPIE: Bellingham, WA, USA, 2010; Volume 7666. [Google Scholar]
- Laskey, K.B.; Suzanne, L.; Wright, E.; Mahoney, S.M. Hypothesis Management in Situation-Specific Network Construction. arXiv 2013, arXiv:1301.2287. [Google Scholar]
- Dempster, A.P. Upper and lower probabilities induced by a multivalued mapping. Ann. Math. Stat. 1967, 38, 325–339. [Google Scholar] [CrossRef]
- Yager, R.R.; Liu, L. Classic Works of the Dempster—Shafer Theory of Belief functions; Springer: Berlin/Heidelberg, Germany, 2008; Volume 219. [Google Scholar]
- Kleemann, J.; Celio, E.; Fürst, C. Validation approaches of an expert-based Bayesian Belief Network in Northern Ghana, West Africa. Ecol. Model. 2017, 365, 10–29. [Google Scholar] [CrossRef]
- Kabir, G.; Balek, N.B.C.; Tesfamariam, S. Consequence-based framework for buried infrastructure systems: A Bayesian belief network model. Reliab. Eng. Syst. Saf. 2018, 180, 290–301. [Google Scholar] [CrossRef]
- Khan, F.I.; Haddara, M. Risk-based maintenance (RBM): A new approach for process plant inspection and maintenance. Process Saf. Prog. 2004, 23, 252–265. [Google Scholar] [CrossRef]
- Johansen, I.L.; Rausand, M.; IEEE. Risk Metrics: Interpretation and Choice. In Proceedings of the 2012 IEEE International Conference on Industrial Engineering and Engineering Management, Hong Kong, China, 10–13 December 2012; pp. 1914–1918. [Google Scholar]
- Jeong, H.; Park, M.; Jeong, H.; Hwang, W.; Kim, E.; Han, M. Radiological risk assessment caused by RDD terrorism in an urban area. Appl. Radiat. Isot. 2013, 79, 1–4. [Google Scholar] [CrossRef]
- Hu, X.; Chen, P.; Tai, Y.; Mojia, S. An assessment method of radiation dose under dirty bomb terrorism based on WRF. Sci. Technol. Eng. 2017, 17, 120–124. [Google Scholar]
- Hu, X.; Li, D.; Huang, H.; Shen, S.; Bou-Zeid, E. Modeling and sensitivity analysis of transport and deposition of radionuclides from the Fukushima Dai-ichi accident. Atmos. Chem. Phys. 2014, 14, 11065–11092. [Google Scholar] [CrossRef]
- Dempster, A.P.; Laird, N.M.; Rubin, D.B. Maximum Likelihood from Incomplete Data Via the EM Algorithm. J. R. Stat. Soc. Ser. B Methodol. 1977, 39, 1–38. [Google Scholar]
- BayesFusion. GeNIe Modeler User Manuel. Available online: http://support.bayesfusion.com/docs/genie (accessed on 5 February 2017).
- Jones, B.; Jenkinson, I.; Yang, Z.; Wang, J. The use of Bayesian network modelling for maintenance planning in a manufacturing industry. Reliab. Eng. Syst. Saf. 2010, 95, 267–277. [Google Scholar] [CrossRef]
- Tang, Z.; Li, Y.; Hu, X.; Wu, H. Risk Analysis of Urban Dirty Bomb Attacking Based on Bayesian Network. Sustainability 2019, 11, 206. [Google Scholar] [CrossRef]
- Jeong, H.-J.; Hwang, W.-T.; Kim, E.-H.; Han, M.H. Radiological risk assessment for an urban area: Focusing on an air contamination event. Ann. Nucl. Energy 2010, 37, 791–797. [Google Scholar] [CrossRef]
- Zhang, J.; Shen, S.; Yang, R. Asymmetric information in combating terrorism: Is the threat just a bluff? Tsinghua Sci. Technol. 2010, 15, 604–612. [Google Scholar] [CrossRef]
- Sandler, T.; Daniel, G.; Arce, M. Terrorism & game theory. Simul. Gaming 2003, 34, 319–337. [Google Scholar] [CrossRef]
- Cox, J.; Louis, A. Some limitations of “Risk= Threat× Vulnerability× Consequence” for risk analysis of terrorist attacks. Risk Anal. Int. J. 2008, 28, 1749–1761. [Google Scholar] [CrossRef]
- Pan, H.; Page, J.; Zhang, L.; Cong, C.; Ferreira, C.; Jonsson, E.; Näsström, H.; Destouni, G.; Deal, B.; Kalantari, Z. Understanding interactions between urban development policies and GHG emissions: A case study in Stockholm Region. Ambio 2019, 1–15. [Google Scholar] [CrossRef] [PubMed]
- Pan, H.; Deal, B. Reporting on the performance and usability of planning support systems—Towards a common understanding. Appl. Spat. Anal. Policy 2020, 13, 137–159. [Google Scholar] [CrossRef]



| No. | Nodes | States of Bayesian Nodes |
|---|---|---|
| 1 | Religious background | (1) Cult terrorism; (2) Islamic terrorism; (3) Christian terrorism; (4) Jewish terrorism; (5) Other |
| 2 | Region of the perpetrator | (1) Middle East and North Africa; (2) Europe; (3) Americas; (4) South and Southeast Asia; (5) East and Central Asia; (6) Central and North Africa |
| 3 | Number of members | (1) Less than 50 people; (2) 50–500 people; (3) 500–5000 people; (4) More than 5000 people |
| 4 | Average educational level | (1) High; (2) Medium; (3) Low |
| 5 | Technical background | (1) High level; (2) Middle level; (3) Low level |
| 6 | Social relations and organisational components | (1) Complex and diverse; (2) Medium; (3) Single |
| 7 | Whether they have been reported recently | (1) Yes; (2) No; (3) Unknown |
| 8 | Whether they ever launched chemical attack | (1) Yes; (2) No |
| 9 | Whether they made a statement or threat | (1) Yes; (2) No |
| 10 | Source of chemical weapon | (1) Self-made; (2) Occupied inventory or armory; (3) Steal from elsewhere; (4) Black market |
| 11 | Whether they have technical support | (1) Yes; (2) No |
| 12 | Whether they have the capabilities of storing and transporting the chemical weapon | (1) Yes; (2) No |
| 13 | Whether they have the ability to launch the chemical attack | (1) Yes; (2) No |
| 14 | Weapon types | (1) Irritant agent; (2) Erosive agent; (3) Systemic poison; (4) Neurotoxic agent; (5) Asphyxiating agent; (6) Acid and alkali corrosive weapons; (7) Mixed Poison; (8) Unknown |
| 15 | Delivery method | (1) Volatile; (2) Water-soluble; (3) Spraying; (4) Explosive dispersion; (5) Send by post; (6) Unknown |
| 16 | Chemical dose | (1) Large; (2) Medium; (3) Little; (4) Unknown |
| 17 | Population density | (1) >1000/km2; (2) 500–1000/km2; (3) <500/km2 |
| 18 | Population movement | (1) High; (2) Medium; (3) Low |
| 19 | Traffic condition | (1) Good; (2) Bad |
| 20 | Location | (1) Residential area; (2) Commercial area; (3) Open space |
| 21 | Whether it is a high-value target | (1) Yes; (2) No |
| 22 | Wind speed | (1) ≤2 m / s; (2) 2 m / s ~ 4 m / s; (3) > 4 m / s |
| 23 | Wind direction | (1) Upwind; (2) Downwind |
| 24 | Precipitation | (1) Heavy; (2) Medium; (3) Less; (4) Minimal or dry |
| 25 | Patrol | (1) More than 2 times; (2) Less than 2 times |
| 26 | Security check | (1) Yes; (2) No |
| 27 | Surveillance | (1) 24 h; (2) Non-24 h |
| 28 | Police investigation | (1) Yes; (2) No |
| 29 | Hospital emergency response | (1) On time; (2) Delay |
| 30 | Fire emergency response | (1) On time; (2) Delay |
| 31 | Police emergency response | (1) On time; (2) Delay |
| A | Influence of the terrorist organisation | (1) Large; (2) Medium; (3) Small |
| B | Activity level of the terrorist organisation | (1) Inactive; (2) Active; (3) Very active |
| C | Difficulty in obtaining and using the chemical weapon | (1) Low; (2) Medium; (3) High |
| D | Danger level of the chemical weapon | (1) High; (2) Medium; (3) Low |
| E | Target attraction | (1) High; (2) Medium; (3) Low |
| F | Weather condition | (1) Favorable; (2) Unfavorable |
| G | Prevention ability of the police | (1) High; (2) Medium; (3) Low |
| H | Ability of the emergency response | (1) High; (2) Medium; (3) Low |
| I | Threat of the terrorist organisation | (1) Large; (2) Medium; (3) Small |
| J | Whether the attack is successful | (1) Yes; (2) No |
| K | Casualties | (1) Minor (0 to 10 deaths or 0 to 50 injuries); (2) Medium (11 to 30 deaths or 50 to 100 injuries); (3) Major (more than 30 deaths or more than 100 injuries) |
| Nodes | Experts’ Opinion | Calculated Results | |||||
|---|---|---|---|---|---|---|---|
| Hospital Emergency Response | Fire Emergency Response | Police Emergency Response | m1(1,2,3) | m2(1,2,3) | m3(1,2,3) | m4(1,2,3) | m(1,2,3) |
| (1) On time | (1) On time | (1) On time | (0.9,0.09,0.01) | (0.9,0.05,0.05) | (0.9,0.08,0.02) | (0.95,0.04,0.01) | (1,0,0) |
| (1) On time | (1) On time | (2) Delay | (0.4,0.35,0.25) | (0.75,0.15,0.1) | (0.5,0.3,0.2) | (0.8,0.15,0.05) | (0.979,0.019,0.002) |
| (1) On time | (2) Delay | (1) On time | (0.3,0.3,0.4) | (0.7,0.2,0.1) | (0.4,0.3,0.3) | (0.7,0.2,0.1) | (0.925,0.057,0.019) |
| (1) On time | (2) Delay | (2) Delay | (0.03,0.17,0.8) | (0.5,0.3,0.2) | (0.1,0.3,0.6) | (0.2,0.5,0.3) | (0.008,0.208,0.784) |
| (2) Delay | (1) On time | (1) On time | (0.45,0.25,0.3) | (0.6,0.2,0.2) | (0.45,0.3,0.25) | (0.7,0.2,0.1) | (0.950,0.034,0.017) |
| (2) Delay | (1) On time | (2) Delay | (0.05,0.2,0.75) | (0.4,0.3,0.3) | (0.15,0.3,0.55) | (0.15,0.35,0.5) | (0.007,0.092,0.902) |
| (2) Delay | (2) Delay | (1) On time | (0.05,0.2,0.75) | (0.3,0.25,0.45) | (0.07,0.3,0.63) | (0.1,0.3,0.6) | (0.001,0.034,0.965) |
| (2) Delay | (2) Delay | (2) Delay | (0.01,0.09,0.9) | (0.01,0.01,0.98) | (0.01,0.09,0.9) | (0.01,0.04,0.95) | (0,0,1) |
| No | Parent Nodes | Extreme Worst | Extreme Best |
|---|---|---|---|
| 1 | Religious background | Islamic terrorism | Jewish terrorism |
| 2 | Region of the perpetrator | Middle East and North Africa | Central and North Africa |
| 3 | Number of members | More than 5000 people | Less than 50 people |
| 4 | Average educational level | High | Low |
| 5 | Technical background | High level | Low level |
| 6 | Social relations and organisational components | Complex and diverse | Single |
| 7 | Whether they have been reported recently | Yes | No |
| 8 | Whether they ever launched chemical attack | Yes | No |
| 9 | Whether they made a statement or threat | Yes | No |
| 10 | Source of chemical weapon | Self-made | Steal from elsewhere |
| 11 | Whether they have technical support | Yes | No |
| 12 | Whether they have the capabilities of storing and transporting the chemical weapon | Yes | No |
| 13 | Whether they have the ability to launch the chemical attack | Yes | No |
| 14 | Weapon types | Irritant agent | Acid and alkali corrosive weapons |
| 15 | Delivery method | Explosive dispersion | Spraying |
| 16 | Chemical dose | Large | Little |
| 17 | Population density | >1000/km2 | <500/km2 |
| 18 | Population movement | High | Low |
| 19 | Traffic condition | Good | Bad |
| 20 | Location | Commercial area | Open space |
| 21 | Whether it is a high-value target | Yes | No |
| 22 | Wind speed | >4 m/s | ≤2 m/s |
| 23 | Wind direction | Downwind | Upwind |
| 24 | Precipitation | Minimal or dry | Many |
| 25 | Patrol | Less than 2 times | More than 2 times |
| 26 | Security check | No | Yes |
| 27 | Surveillance | Non-24 h | 24 h |
| 28 | Police investigation | No | Yes |
| 29 | Hospital emergency response | Delay | On time |
| 30 | Fire emergency response | Delay | On time |
| 31 | Police emergency response | Delay | On time |
| G | Prevention ability of the police | High: 0% Medium: 0% Low: 100% | High: 100% Medium: 0% Low: 0% |
| H | Ability of the emergency response | High: 0% Medium: 0% Low: 100% | High: 100% Medium: 0% Low: 0% |
| I | Threat of the terrorist organisation | Large: 54% Medium: 23% Small: 23% | Large: 35% Medium: 34% Small: 32% |
| J | Whether the attack is successful | Yes: 86% No: 14% | Yes: 0% No: 100% |
| K | Casualties | Minor: 24% Medium: 16% Major: 59% | Minor: 100% Medium: 0% Major: 0% |
| Parent Nodes | Scenario 1 | Scenario 2 | Scenario 3 | Scenario 4 |
|---|---|---|---|---|
| Whether the attack is successful | Yes: 46% No: 54% | Yes: 46% No: 54% | Yes: 51% No: 49% | Yes: 24% No: 76% |
| Casualties | Minor: 69% Medium: 27% Major: 4% | Minor: 61% Medium: 16% Major: 23% | Minor: 66% Medium: 29% Major: 5% | Minor: 84% Medium: 14% Major: 2% |
| Value of Nodes 25–28 | Casualties | Patrol | Security Check | Surveillance | Police Investigation |
|---|---|---|---|---|---|
| yes | minor | 78% | 90% | 77% | 88% |
| medium | 12% | 5% | 13% | 6% | |
| major | 10% | 5% | 10% | 6% | |
| no | minor | 65% | 66% | 61% | 71% |
| medium | 20% | 19% | 22% | 16% | |
| major | 15% | 15% | 17% | 13% |
| Value of Nodes 25–28 | Whether the Attack is Successful | Patrol | Security Check | Surveillance | Police Investigation |
|---|---|---|---|---|---|
| yes | yes | 28% | 13% | 30% | 16% |
| no | 72% | 87% | 70% | 84% | |
| no | yes | 47% | 45% | 52% | 39% |
| no | 53% | 55% | 48% | 61% |
| Parent Nodes | Target A | Target B | Target C |
|---|---|---|---|
| Population density | > 1000/km2 | 500–1000/km2 | <500/km2 |
| Population movement | High | Medium | Low |
| Traffic condition | Good | Good | Bad |
| Location | Commercial area | Residential area | Open space |
| Whether it is a high-value target | Yes | Yes | No |
| Patrol | More than 2 times | More than 2 times | Less than 2 times |
| Security check | No | Yes | No |
| Surveillance | 24 h | 24 h | Non-24 h |
| Police investigation | No | Yes | No |
| Hospital emergency response | On time | Delay | Delay |
| Fire emergency response | On time | On time | Delay |
| Police emergency response | On time | On time | Delay |
| Parent Nodes | Organisation 1 | Organisation 2 | Organisation 3 |
|---|---|---|---|
| Religious background | Islamic terrorism | Christian terrorism | Cult terrorism |
| Region of the perpetrator | Middle East and North Africa | Europe | East and Central Asia |
| Number of members | More than 5000 people | 50–500 people | Less than 50 people |
| Average educational level | Middle | Low | High |
| Technical background | Middle level | Low level | High level |
| Social relations and organisational components | Complex and diverse | Medium | Single |
| Whether they have been reported recently | Yes | No | No |
| Whether they ever launched chemical attack | Yes | No | No |
| Whether they made a statement or threat | Yes | No | No |
| Source of chemical weapon | Occupied inventory or armory | Steal from elsewhere | Self-made |
| Whether they have technical support | No | No | Yes |
| Whether they have the capabilities of storing and transporting the chemical weapon | Yes | No | Yes |
| Whether they have the ability to launch the chemical attack | Yes | No | No |
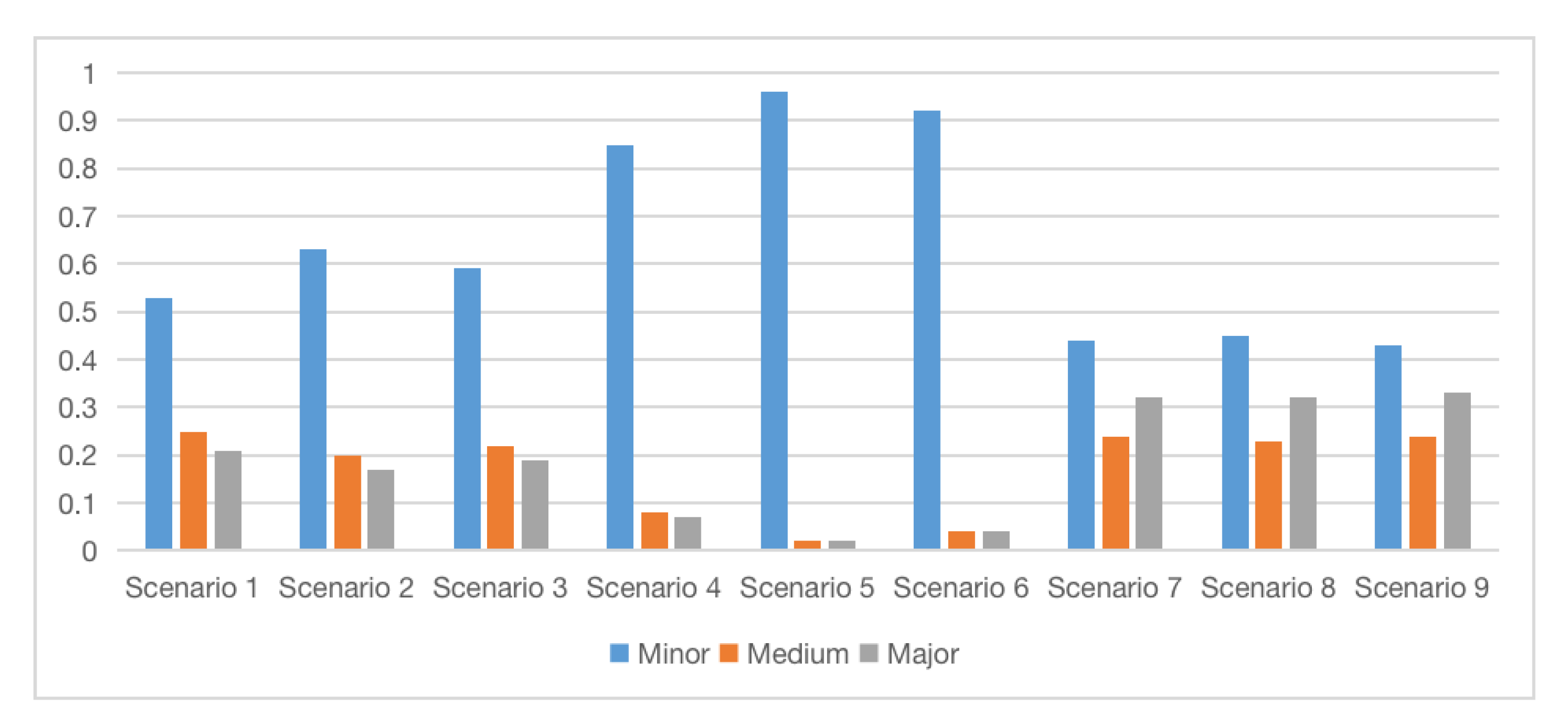
| Scenario | Description | Scenario | Description | Scenario | Description |
|---|---|---|---|---|---|
| Scenario 1 | Organisation 1 Target A | Scenario 4 | Organisation 1 Target B | Scenario 7 | Organisation 1 Target C |
| Scenario 2 | Organisation 2 Target A | Scenario 5 | Organisation 2 Target B | Scenario 8 | Organisation 2 Target C |
| Scenario 3 | Organisation 3 Target A | Scenario 6 | Organisation 3 Target B | Scenario 9 | Organisation 3 Target C |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, R.; Hu, X.; Li, X.; Ye, H.; Jia, N. Modeling and Risk Analysis of Chemical Terrorist Attacks: A Bayesian Network Method. Int. J. Environ. Res. Public Health 2020, 17, 2051. https://doi.org/10.3390/ijerph17062051
Zhu R, Hu X, Li X, Ye H, Jia N. Modeling and Risk Analysis of Chemical Terrorist Attacks: A Bayesian Network Method. International Journal of Environmental Research and Public Health. 2020; 17(6):2051. https://doi.org/10.3390/ijerph17062051
Chicago/Turabian StyleZhu, Rongchen, Xiaofeng Hu, Xin Li, Han Ye, and Nan Jia. 2020. "Modeling and Risk Analysis of Chemical Terrorist Attacks: A Bayesian Network Method" International Journal of Environmental Research and Public Health 17, no. 6: 2051. https://doi.org/10.3390/ijerph17062051
APA StyleZhu, R., Hu, X., Li, X., Ye, H., & Jia, N. (2020). Modeling and Risk Analysis of Chemical Terrorist Attacks: A Bayesian Network Method. International Journal of Environmental Research and Public Health, 17(6), 2051. https://doi.org/10.3390/ijerph17062051




