1. Introduction
Building on next-generation Industrial Internet of Things (IIoT) technology, the Industrial 5.0 era aims to establish a fully interconnected industrial network system that connects humans, machines, and things [
1]. This system enables real-time acquisition, free transmission, precise analysis, and intelligent feedback of massive industrial data. With the development of IIoT, an increasing number of devices are interconnected across networks, requiring diverse data traffic to be supported in a single network simultaneously, such as high-security control, high-bandwidth AI perception, and real-time cross-domain human–machine interaction. The traditional “best-effort” mechanism of Ethernet is no longer sufficient to meet the requirements of microsecond-level synchronization and mixed deterministic transmission [
2].
Time-Triggered Ethernet (TTE) extends conventional Ethernet by incorporating time-triggering, synchronization, and redundancy mechanisms [
3,
4]. TTE can serve applications with varying latency and reliability requirements over the same physical network, providing sub-microsecond-level time synchronization and bounded transmission jitter using a global clock and offline schedule tables. TTE also supports fault tolerance and traffic isolation while remaining fully compatible with traditional Ethernet. This makes it well-suited for the stringent transmission and processing demands of industrial networks. TTE technology has gained widespread attention and recognition in the industry and is increasingly being applied in fields such as healthcare, aerospace, and automotive [
5,
6,
7,
8].
TTE classifies traffic into Time-Triggered (TT) and Event-Triggered (ET) traffic [
9], with the latter comprising Rate-Constrained (RC) and Best-Effort (BE) messages. TT traffic is transmitted according to a pre-defined schedule, ensuring deterministic latency and jitter, while ET traffic is transmitted in the gaps between TT transmissions. Consequently, the quality of the TT scheduling table directly impacts both TT traffic performance and the transmission of other traffic types, thereby influencing the overall network capacity [
10]. With the large-scale deployment of TTE, network topologies have become increasingly complex. The demand for real-time data transmission has grown substantially, resulting in greater computational complexity in solving TTE scheduling problems [
11]. Therefore, in large-scale TTE networks, how to rapidly deliver high-quality solutions tailored to specific applications and operational requirements remains a pressing challenge for TTE scheduling algorithms.
The solving of TTE scheduling tables is NP-Complete Problem (NPC). In current research and engineering applications, traditional TTE scheduling methods mainly include Satisfiability Modulo Theory (SMT) -based algorithms [
12] and Metaheuristic Algorithms (MA) [
13]. In [
14], a network-planning-based SMT solver was first proposed to generate static schedules, and its performance was validated through simulation. An incremental scheduling mechanism was also introduced, in which TT traffic is divided into multiple batches and schedules are generated sequentially using the SMT solver; however, the results yielded only feasible solutions, with limited improvement in bandwidth and time utilization. In [
15], the authors introduced the Strict Periodic Utilization (SPU) factor to quantify the scheduling difficulty of TT traffic, and TT flows are then incrementally scheduled by the SMT solver in descending order of SPU. By computing interference times between TT flows, the scale of conflict-free constraints between scheduled and unscheduled flows during incremental scheduling is reduced, thereby decreasing the number of backtracking steps. In [
16], a load-balancing strategy and distributed iterative conflict backtracking method were incorporated into the SMT framework, where message clusters were divided into smaller subsets and each subset was solved once at a time. When a subset was successfully scheduled, the results were added as new constraints to the SMT solver, improving both computational efficiency and load balance to some extent. In [
17], a Fuzzy-controlled Quantum-behaved Particle Swarm Optimization (FQPSO)-SMT algorithm was proposed, in which priorities were defined to determine the order of incremental scheduling. This method considered not only end-to-end delay but also interference between scheduled and unscheduled messages, enabling rapid resolution of collision-free and timing constraint problems for basic periodic frames, with better load balancing and bandwidth utilization than standard incremental SMT. In [
18], a hybrid scheduling technique combining Genetic Algorithm (GA) and Simulated Annealing (SA) was employed, where chromosome encoding, a penalty-based fitness function, and elite selection with POX crossover were designed, and by incorporating a simulated-annealing strategy during the mutation phase, the algorithm enhances both global and local search capabilities. However, this approach was limited to smaller network topologies and message sets, with SA parameters empirically tuned and lacking adaptive mechanisms.
Since TT messages have the highest scheduling priority in the network, the results of TTE scheduling algorithms have a significant impact on the performance of ET messages. In [
19], the paper introduced a novel Dynamic Programming Priority (DPP) algorithm designed for scheduling RC flows in TTE, which combines priority-based scheduling with dynamic programming, dividing RC flows into different priority groups. Higher-priority groups are scheduled using First input first output (FIFO) policy, while lower-priority groups leverage dynamic programming for optimal resource utilization. The algorithm also integrates an SMT solver to pre-schedule TT messages, minimizing their interference with RC flows. In [
20], the authors first employed an SMT solver to obtain an initial schedule where TT traffic is distributed as evenly as possible while satisfying inherent transmission constraints. Network calculus was then applied to verify whether RC traffic met its delay requirements; if satisfied, the scheduling process terminated with the current result, otherwise, TT flows causing excessive RC traffic delays were rescheduled until the RC traffic delay requirement was met. In [
21], a Modified Weighted Round-Robin (MWRR) scheduling algorithm based on optimal time slices was proposed. The algorithm utilizes SMT to generate an offline scheduling table for TT messages, thereby optimizing the transmission time slices for RC messages. Within these time slices, bandwidth is allocated proportionally and a deficit counter is introduced to ensure fairness, thus improving the scheduling fairness and real-time performance of different types of RC messages. In [
22], A TTE optimal scheduling technology based on rapid increment was proposed to optimize scheduling intervals to reduce RC message waiting time. By backtracking to correct multi-hop delays and adjusting the TT message schedule, the transmission performance of RC messages is improved. In [
23], a scheduling optimization method was introduced to minimize the “makespan” of TT messages, aiming to reserve the maximum possible bandwidth for RC traffic to ensure its real-time performance and stability. However, this model imposes strict constraints on link bandwidth and message periods, and its computational complexity increases sharply with the number of messages, limiting its practical applicability.
Based on the current research on TTE scheduling algorithms, several pressing issues remain when addressing large-scale TTE applications. First, due to factors such as sensor locations, service characteristics, network topology, and resource distribution, traffic loads vary significantly across different links within the same network [
24,
25]. Traditional scheduling algorithms typically employ unified global scheduling strategies without accounting for the traffic heterogeneity of different links, which reduces computational efficiency and limits the quality of the solutions. Second, in practical applications, BE messages often constitute the majority of traffic in TTE networks. Real-time and precise remote monitoring and control rely on stable BE traffic (such as image and audio) to support human–machine feedback interaction. Since BE messages have the lowest priority, the scheduling results for TT messages have the greatest impact on the performance of transmission of BE messages; however, existing optimization efforts primarily focus on the scheduling of TT and RC messages, while the impact on BE messages has not been a primary research focus. Finally, the complexity of the network topology and the number of network messages that need to be scheduled increase rapidly as the scale of the TTE network expands. The issue of the time complexity of traditional algorithms becomes increasingly critical, making it difficult to obtain feasible solutions even in certain complex scenarios [
26].
To address the above issues, this paper proposes a hybrid scheduling algorithm based on critical-link optimization for large-scale TTE. First, a TT network topology and message scheduling model is established based on large-scale network application scenarios, and the constraints of TT scheduling are analyzed and mathematically abstracted. Second, a slot-balanced scheduling algorithm based on static priority is introduced for the most critical link, in which messages on the link are first prioritized according to their periods, and then scheduled sequentially by priority. For each message, the scheduling slot is determined by searching the feasible optimal slot closest to the center of the largest TT message gap according to the distribution of already scheduled messages to achieve the most balanced time slot arrangement, thus reducing the impact of continuous TT slot allocation on delay and jitter of BE message transmission. Finally, after completing the critical link scheduling, a genetic algorithm is applied to solve the network-wide scheduling problem and the scheduling results of the critical link are used as input to the genetic algorithm. The scheduling constraints are converted into the fitness function of the genetic algorithm and optimized genetic operators are used to further improve the algorithm’s optimization capabilities. By combining static scheduling for the critical link with dynamic global scheduling based on genetic algorithm, the proposed hybrid scheduling algorithm effectively reduces computation time while improving scheduling quality.
2. Time-Triggered Ethernet Model
2.1. Network Traffic Analysis
TTE supports diverse types of data transmission, with its services built upon network-wide time synchronization. It enables the coexistence of three distinct classes of message transmission over a single physical network [
27]. TT messages are subject to strict temporal constraints. Their transmission times are determined by a pre-defined offline communication schedule and are strictly executed at scheduled time points during runtime. This schedule is cyclically repeated with a fixed duration known as the cluster cycle [
28]. RC messages are ET messages regulated through bandwidth allocation mechanisms. These messages achieve flow control and data rate limitation via the Bandwidth Allocation Gap (BAG). BE messages are also ET messages but are not subject to any timing or bandwidth constraints. Traditional Ethernet traffic falls under the BE message category.
In TTE, different applications typically employ different message types according to their transmission requirements. The network performs mixed scheduling and transmission of the three message types based on an offline scheduling table. For example, in aerospace vehicle networks, critical data such as real-time control and time services are transmitted using TT messages, while status data, voice, video, and other services are transmitted using RC and BE messages. An illustration of mixed scheduling in a TTE network is shown in
Figure 1.
In TTE, since BE traffic can only be transmitted during the idle intervals of TT and RC traffic, the scheduling of TT messages increasingly impacts the performance of BE traffic as the network scales up. The significant delay and jitter experienced by BE messages can adversely affect applications relying on BE traffic, such as causing stuttering or latency in video or voice communications, as well as data congestion and packet loss. These issues, in turn, constrain the overall performance of the TTE network. Therefore, optimizing the static scheduling table of TT messages to reduce their interference with BE traffic is crucial for improving the overall performance of TTE networks.
2.2. Network Topology Model
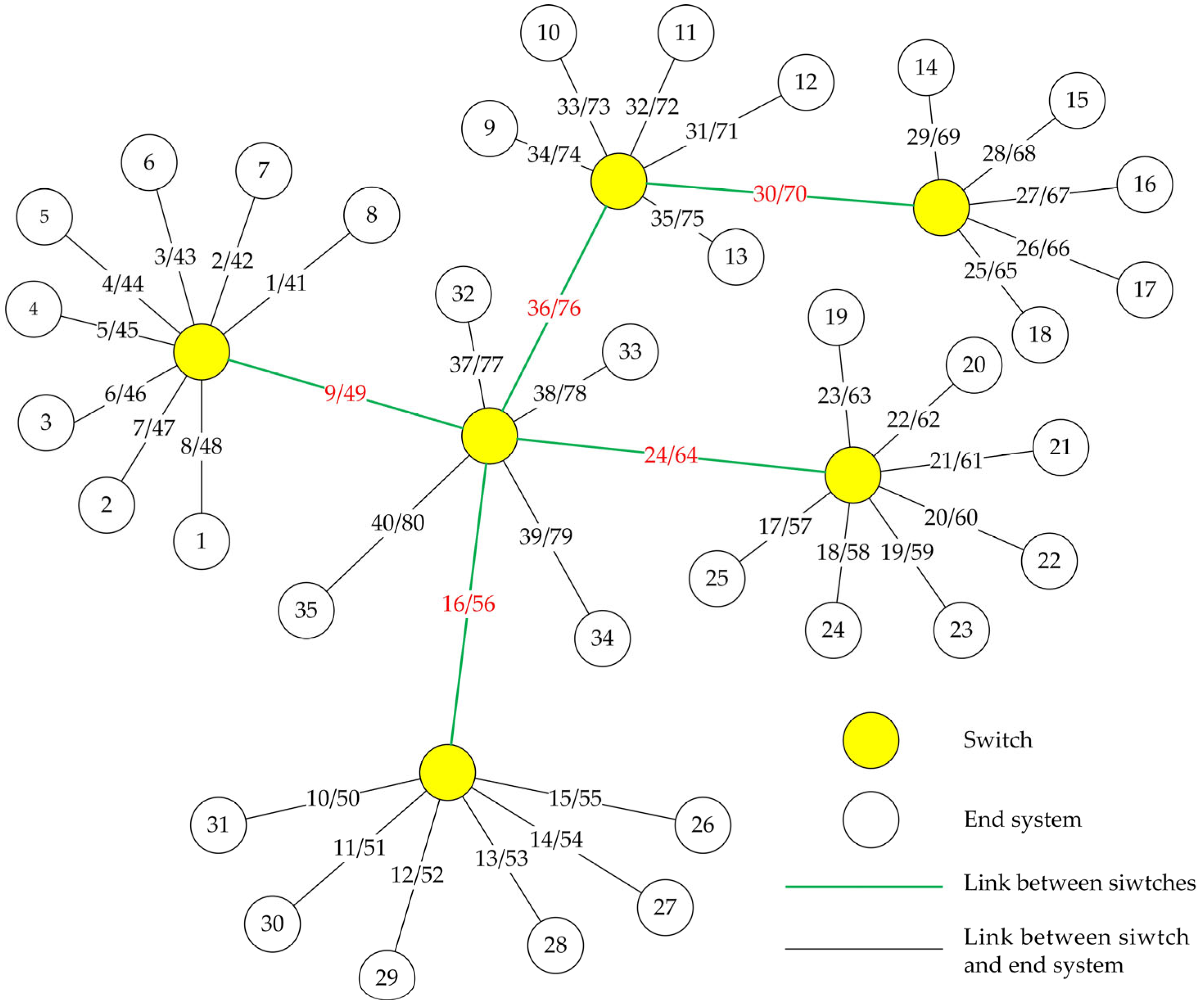
Traditional TTE networks typically employ simple topologies such as star or snowflake structures. To evaluate the performance of algorithms under large-scale and non-single-path network conditions, this study constructs a multi-hop tree topology based on a TTE network comprising 35 end systems and 6 switches. The network topology is illustrated in
Figure 2.
In the figure, circles represent network end systems or switch nodes, while the lines between nodes represent network links. The multi-hop TTE network is modeled as an undirected graph , where the vertex set (i.e., the circles in the figure) represents switches or end systems, and the edge set (i.e., the straight lines) denotes bidirectional connections between vertices. Let denote the set of all frames in the network. A vector represents the set of data links, where indicates a data link directed from vertex to vertex , and denotes the data link in the opposite direction on the same edge. Two vertices can exchange frames only if at least one of them is a switch.
2.3. Message Scheduling Model
In a TTE network, all TT frames are transmitted periodically, though the transmission periods may differ among virtual link messages. Suppose there are
messages in the network, and
denotes the transmission period of frame
. The cluster cycle, denoted as
, is defined as the least common multiple (LCM) of the periods
,
, …,
of all TT frames. The variable
represents the offset of frame
relative to the start of the cluster cycle. A schematic diagram of the TT message periodic scheduling model is shown in
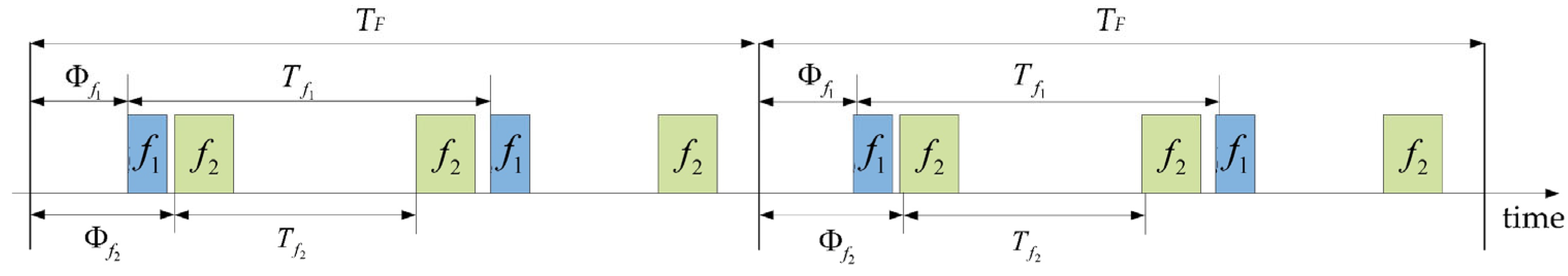
Figure 3, which illustrates two TT messages.
Figure 3 illustrates the periodic transmission characteristics of two TT messages,
and
, over two cluster cycles. As shown, within each cluster cycle, the same TT message maintains a consistent time offset relative to the start of the cycle. Since TT traffic is deterministic and periodic, once the offset of a message is determined, its transmission schedule over time can be derived based on its period. Therefore, the TT message scheduling problem can be simplified to determining the time offsets of all messages within a single cluster cycle. This leads to the construction of a static communication schedule table that ensures collision-free transmission of TT messages over the network links [
29]. After the schedule table is generated, the configuration tool encapsulates the schedule table into an image file and loads it into the local storage of each switch and end device before the network starts to run. After the schedule table is loaded, each switch and terminal transmits and receives data according to the locally stored scheduling table.
The time offset of a frame within a single cluster cycle is defined as follows:
It indicates that the source node
begins transmitting the
-th frame over link
at time
after the start of the cluster cycle. According to the periodic nature of TT messages, the interval between the
-th frame and the
-th frame is equal to the frame’s period. This relationship can be expressed mathematically as follows:
An end system transmitter can send information to one or multiple receiving end systems. Therefore, in a TT network architecture, unicast, broadcast, and multicast communications can be implemented at the link layer. The data flow path
is defined as the sequence of links from the sender
to the receiver
, as shown in following:
For any frame
, its path tree is defined as
, which is the union of all data flows from the sender of frame
to each of its receivers. Accordingly, frame
can be defined by a tuple as shown in following:
In this tuple, denotes the transmission period of the frame, represents the time offset of the frame, is the frame length (in bytes), and is the path tree as defined above. Based on the previous definitions, for a given set of frames , the message scheduling table can be constructed using the set of time offsets to form a complete transmission schedule.
Since searching for time offsets in the continuous time domain is particularly complex, the continuous transmission time is discretized into natural-number-based time slots. A basic time slot unit is defined as 1 microsecond and is denoted by
. Thus, both the transmission offset and duration of each frame can be expressed in terms of time slots, which simplifies the problem. Under this assumption, the transmission duration of frame
on link
can be represented by the number of time slots
, as shown in following:
Here, represents the actual transmission duration of frame on link , and other time-related variables can be similarly expressed and simplified using this time slot representation.
Considering that the cluster cycle
is the LCM of a set of frame periods, a frame on a given virtual link may need to be scheduled multiple times within a single cluster cycle. Therefore, the number of scheduling instances is calculated as follows:
In the formula, represents the period of frame .
4. Scheduling Algorithm Based on Critical-Link Optimization
4.1. Algorithm Procedure and Analysis
4.1.1. Algorithm Procedure
The message planning and scheduling of the TTE network usually follows a two-step process. The first step is message path planning, which determines the transmission links for each message. The second step is message time-slot scheduling, which allocates transmission time slots for each message on the corresponding link. The algorithm proposed in this paper focuses on the second step and is carried out based on the following premises: the network topology structure is predetermined and does not involve dynamic topology changes; the transmission paths of all TT messages have been determined through offline planning or preset mechanisms, without considering dynamic routing adjustments, path reselection, and path distance constraints. On this basis, this study focuses on efficient slot allocation and conflict avoidance for TT messages and further optimizes the transmission performance of BE messages to improve the overall communication efficiency of the TTE network under given topology and path conditions.
To reduce the overall scheduling complexity, the heterogeneity of network links is identified, and a static scheduling algorithm is independently applied to the critical links. This approach not only shortens the computation time but also optimizes the overall transmission performance of BE messages.
For global network scheduling, due to the NP-hard nature of TTE, traditional methods are prone to local optima or excessive time consumption. Genetic algorithms, with their parallel population search and strong global increment optimization capabilities based on historical population, can quickly approximate the optimal scheduling table. Their flexible encoding makes it easy to incorporate constraints such as time windows and priorities, adapting to multi-objective optimization requirements. Therefore, a genetic algorithm is employed for global network scheduling to leverage its global optimization capability, further enhancing solution quality and reducing computation time.
Accordingly, the proposed scheduling algorithm adopts a two-stage solution strategy: the first stage focuses on scheduling of the critical link, while the second stage performs global scheduling across the network. The result of the first stage serves as an input constraint for the second stage. The overall flow of scheduling algorithm based on critical-link optimization is illustrated in
Figure 4.
First, network and traffic parameters should be obtained based on user transmission requirements, including the network topology, the length, period, duration, and transmission path of all TT messages. The LCM of all TT message periods is then calculated to determine the cluster cycle, which defines the overall scheduling duration.
Then, based on the distribution of messages across network links, the number of messages on each link, the impact of TT messages on the delay and jitter of BE messages, and the structural importance of links are evaluated. Links with high message density, high sensitivity to BE message delay and jitter, or high topological centrality can be selected as critical links. Critical links in different application scenarios can be flexibly selected based on the actual network requirements and the above factors. The detailed method for selecting critical links is described in
Section 4.1.2.
Finally, an initial population for TT message scheduling is constructed based on genetic algorithm, in which the scheduling result of the critical link are embedded as fixed genes within each individual. These genes remain unchanged throughout the evolutionary process. Once the initial population is generated, the genetic algorithm iteratively calculates fitness and applies genetic operators until a feasible solution is found, generating the final communication schedule for the TTE.
4.1.2. Critical Link Selection
Link centrality, link traffic load, and link importance are used as three indicators to evaluate link criticality. A quantitative calculation model is constructed to realize the systematic screening of critical links in the network.
Link centrality characterizes the degree of correlation between the location of the link and the location of the core node (the central node or root node in TTE network), and quantifies the topological distance between the link and the core node. The closer the link is to the core node, the higher its centrality in the data transmission path. The centrality index of a link is calculated based on its topological distance to the core node, with a value range of (0, 1]. The calculation formula is as follows:
In the formula, represents the topological distance between link and the core node, and represents the maximum topological distance to the core node in the network. When the link is directly connected to the core node, can be set to 0, and in which case = 1.
Link traffic load represents the actual message transmission pressure borne by a link. The more messages a link carries, the higher its traffic load. The ratio of the number of messages carried by a link to the total number of messages in the entire network is used as the value of link traffic load, with a maximum value of 1. The calculation formula is as follows:
In the formula, represents the actual number of messages carried by link , and represents the total number of messages in the entire network.
Link importance represents the sensitivity of a link to the delay and jitter of BE messages. If the downstream terminal nodes connected by the link (such as industrial sensors and monitoring devices) have stricter requirements on the delay and jitter of BE messages, the sensitivity of the link is higher. During network planning, the link importance of each link in the network is assigned according to application requirements, and a normalized value is used. The calculation formula is as follows:
In the formula, represents the minimum delay or jitter requirement for BE messages by the terminals associated with link , and represents the minimum delay or jitter that the network can provide for BE messages.
To realize the collaborative quantification of the three-dimensional indicators, a weighted sum model is constructed to calculate link criticality. The formula is as follows:
Among them, , , and are the weight coefficients of link centrality, link traffic load, and link importance, respectively, satisfying . has a value range of (0, 1]; the larger its value, the higher the criticality of the link. Based on the calculation results, the links with high link criticality value can be selected as critical links.
4.1.3. Algorithmic Complexity Analysis
The TTE scheduling problem is essentially a Constraint Satisfaction Problem (CSP) or a Combinatorial Optimization Problem (COP). Its core task is to search for a feasible solution within a large search space. The search space here is defined as all possible combinations of time slot offsets for all frames within the network links. Based on the TTE model introduced earlier, the searchable time domain
for any frame on a link is given by:
In this equation,
denotes a basic time slot unit,
denotes the cluster cycle. the size of the search space for a single frame on a single link is:
Suppose the network has
links, and each link carries an average of
frames. Then the total number of variables in the network is
, and the original size of the global search space is:
This paper applies a static algorithm to quickly fix the scheduling variables of a critical link before solving the global problem. Suppose this link has m frame variables. Then the total number of variables is reduced to
. Moreover, due to inter-link scheduling constraints, the fixed schedule of the critical link propagates constraints to other parts of the network, further reducing the search space. Let the average reduction ratio be
, where
. Then, the remaining search space becomes:
The relative reduction ratio of the search space is defined as:
Equation (22) shows that even if is close to 1, as long as ≥ 1, grows rapidly with and .
Additionally, after fixing the schedule of one link, the constraint propagation inherent in TTE networks significantly reduces the feasible time windows for upstream and downstream messages. This avoids potential conflicts and eliminates redundant search branches. Although these effects do not directly reduce the number of variables, they greatly improve pruning efficiency and further reduce the actual runtime.
Through the hybrid algorithm optimization proposed in this paper, although the original complexity class of the problem remains unchanged, the global search space is effectively reduced. This leads to a significant decrease in computational complexity and a substantial reduction in the runtime of the algorithm in practical applications.
4.2. Critical Link Scheduling
For the critical link, to minimize the impact of consecutive TT messages on BE traffic performance, it is necessary to reserve the maximum possible time gap after each TT message for BE transmission. This ensures that the interference of TT traffic on BE traffic in mixed transmission scenarios is reduced to a minimum—approximately the duration of a single TT frame.
From the perspective of scheduling algorithms, ensuring the determinism of critical link is particularly important, and this paper proposes a time slot balancing scheduling algorithm based on static priorities. First, messages are prioritized according to scheduling difficulty, as messages scheduled later are affected by those already scheduled; thus, messages that are more difficult to schedule should be planned first. After priority sorting is completed, messages are scheduled in descending order of priority based on predefined rules. During scheduling, according to the current time distribution of scheduled messages, the available time gaps are sorted in descending order of inter-frame intervals. Scheduling time is then searched within each gap, starting from the center and sliding outward to both sides in steps of one time slot, until a time point that satisfies the gap constraint and avoids timing conflicts is found, and this time point is then selected as the scheduling point of current message. Compared with SMT and MA, this method is rule-based, and thus the results are deterministic, and the computation time is significantly reduced.
Assume that link
is the critical link and
is its transmitting node. There are
TT messages to be scheduled on this link, with each message frame denoted as
, and the set of message frames denoted as
. The offset of each message within a cluster cycle is represented by
. To ensure the transmission performance of BE messages, a minimum time gap
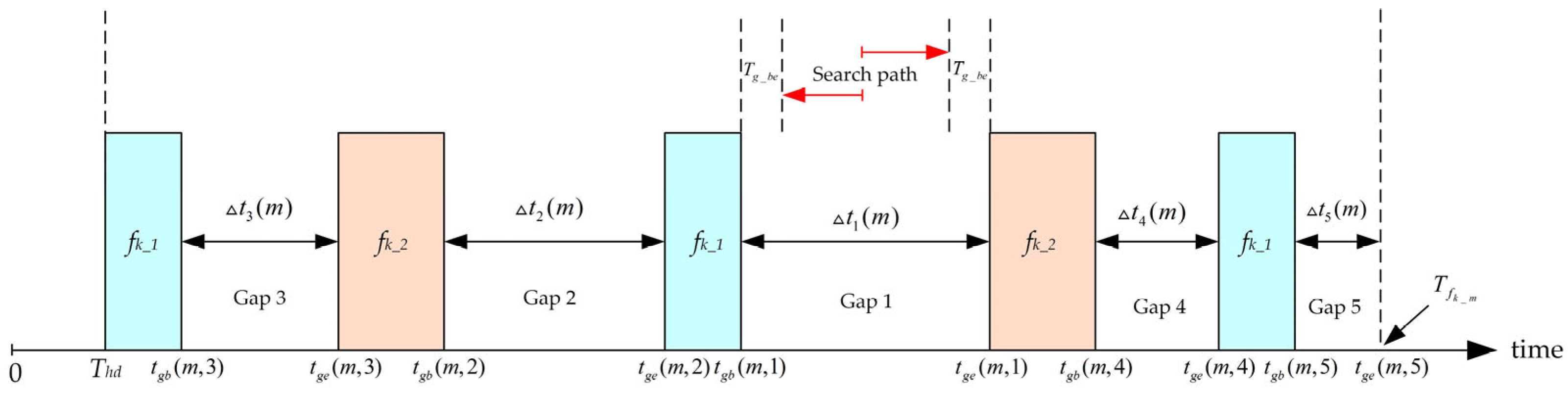
is inserted before and after each TT message, and the scheduling results should adhere to this minimum gap constraint. The schematic diagram of the scheduling algorithm is shown in
Figure 5.
The figure illustrates the scheduling process of the third message on the critical link. The first two messages result in five available time gaps. When scheduling the third message, the algorithm searches for the best solution in order from Gap 1 to Gap 5, based on descending gap size. The scheduling result of the algorithm can be expressed as follows:
In the equation, denotes the offset of the first message, denotes the offset of the -th message, and indicates the time offset of the best scheduling point obtained by the algorithms in the -th gap, relative to the start time of that gap. and represent the number of cycles in the cluster cycle of frame and , respectively. and represent the transmission duration of frame and in the link, respectively.
The detailed procedure of the time slot balancing scheduling algorithm based on static priority is as follows:
First, the messages on the critical link are sorted by priority. Since messages with shorter periods have higher temporal density and are more difficult to schedule, this paper adopts a period-based priority assignment strategy, in which messages with shorter periods are given higher scheduling priority.
The first message on the link is scheduled, and its transmission offset is directly set to the minimum forwarding delay of the switch, denoted as , as shown in Equation (23).
For the -th message on the link (), frame gap sorting is performed. Assume that the period of message is . Within the time window , suppose there are frame gaps formed by the already scheduled messages. These gaps are sorted in descending order according to the size of their intervals. After sorting, the start and end times of the gaps are denoted as , ,…, and the corresponding gap durations are , ,…, , where > > …… >
For the -th message on the link (), the frame gap for scheduling is determined. After excluding the gaps that have already been searched, the biggest remaining gap is selected as the current gap for scheduling.
For the
-th message on the link (
), the optimal scheduling time is then searched within the selected frame gap. The search starts from the center of the gap and moves outward to both sides in steps of one time slot. At each step, it checks whether all subsequent occurrences of the message within the cluster cycle satisfy the contention-free constraint described in
Section 3.2 and the minimum time gap constraint
. If a best scheduling time is found that meets these constraints, it is selected as the scheduling result, as shown in Equation (24), and the process proceeds to Step 6. If the constraints are not met, the search continues to the next time slot. If no feasible solution is found after searching the entire frame gap, the algorithm returns to Step 4.
Determine whether the scheduling result of the -th message exists in the current solution space. If it does not exist, a new solution is obtained and added to the solution space, and the process proceeds to Step 7. If the result already exists in the solution space, the algorithm returns to Step 5 to continue time slot shifting and search for the next feasible solution.
After the -th message scheduling is completed, check whether . If so, proceed to Step 8; otherwise, increment by 1 and return to Step 3.
Once all messages have been scheduled, a feasible scheduling solution for the critical link, denoted as , is obtained and added to the set of feasible solutions .
Repeat Steps (2) to (8) until the target number of solutions is reached or all feasible solutions have been exhausted, at which point the algorithm terminates.
The above algorithm is for a single critical link. If multiple critical links are identified in the network, the same algorithm process can be applied to each critical link.
4.3. Global Network Scheduling
4.3.1. Population Initialization
Before applying the genetic algorithm, an initial population must be generated, and each individual in the population must be initialized. Considering the characteristics of TTE, this paper adopts a decimal encoding scheme. Suppose there are
links and
messages to be transmitted in the network. Then, an individual in the population can be represented by an
matrix as follows:
In the matrix,
represents the time offset of frame
on link
. Since time has been simplified to time slots in the scheduling model, its value is a discrete value starting from 0 with a minimum step size of 1. If frame
does not traverse a particular link, the corresponding encoding value is set to 0, and the link is ignored during computation. The offset values
related to the critical link are brought in directly according to the critical link scheduling results in
Section 4.2, and their values remain unchanged during subsequent genetic operations.
4.3.2. Fitness Function
The objective function is designed based on the constraints of TTE, including frame period constraint, contention-free constraint, switch traversal constraint and end-to-end delay constraint, and transformed into a fitness function to construct the optimization equation. This optimization equation is subsequently used by genetic algorithm to generate a feasible scheduling table. According to the previously discussed constraints of message scheduling, we can obtain the global TT scheduling table if we determine the offset of each TT message within a single cluster cycle relative to the cycle’s starting time.
For the frame period constraint, the transmission deadline of the frame is used as the objective function. For any frame
, and for any link
in its path tree, the transmission deadline of the frame can be defined as the following objective function:
If the value of the objective function falls within the interval
, the offset of frame
on a given link is considered to meet the frame period constraint, and the corresponding penalty is assigned a value of 0. If the constraint is violated, the penalty is set to
. Based on this, the fitness function for frame
can be expressed as follows:
By summing over all TT message frames
and data links
, the overall fitness function
under the frame period constraint is obtained, as shown by the following:
- 2.
Contention-Free Constraint
For the contention-free constraint, whether a frame meets the contention-free condition is incorporated into the objective function. For any link
, whether the frames
in the link satisfy the contention-free constraint can be defined as the following objective function:
In the formula,
and
denote the sequence numbers of frames
and
on the link,
and
respectively represent the periods of frames
and
,
and
respectively represent the transmission durations of frames
and
on the link. If the value of the objective function is 1, it indicates that the transmission interval of frame
does not overlap with the transmission interval of frame
on the shared link
, meaning no resource conflict occurs and the contention-free constraint is satisfied. In this case, the corresponding penalty is set to 0. Conversely, if the objective function equals 0, it means that
and
have overlapping transmission intervals on the link
, leading to resource contention, and the associated penalty is denoted as
. Based on this, the fitness function of frame
can be expressed as follows:
Let
and
. By summing over all TT message frames
and data links
, the overall fitness function
under the non-contention constraint is obtained, as shown by the following:
- 3.
Switch Traversal Constraint
For the switch traversal constraint, the time difference between the transmissions of a TT frame on two adjacent physical paths passing through a switch node is used as the objective function. For any pair of adjacent links
, whether a frame
satisfies the switch traversal constraint can be defined as the following objective function:
Based on the periodic characteristics of TT frames, it is sufficient to satisfy the condition for only the first frame on the link; therefore, the constraint can be simplified as follows:
Based on the relationship between the constraint bounds and the offset difference, if the constraint is satisfied, the penalty is 0; otherwise, the cost value depends on the degree to which the offset deviates from the constraint—the greater the deviation, the higher the cost. Accordingly, the fitness function of frame
quantifies the deviation between the transmission of the TT data frame and the switch traversal constraint, which is defined as follows:
In the formula,
represents the minimum time a frame must be stored in the switch before being relayed, and
represents the maximum time a frame can be stored in the switch before being forwarded. By summing over all TT data frames
and all switch nodes traversed on their corresponding virtual links
, the overall fitness function
under the switch traversal constraint can be obtained, as shown in following:
- 4.
End-to-End Delay Constraint
In the case of multicast transmission, it is assumed that the upper bound of end-to-end delay is the same for all receiving nodes. Based on the constraints described in the previous section, each frame must satisfy that the difference between the offset on the destination link and the offset on the source link falls within the specified delay bound. The objective function is defined as follows:
Here,
represents the quantized value of the end-to-end delay of a traffic message under the time slot model, which is defined as the difference between the transmission offset on the destination node’s directly connected link and the transmission offset on the source node’s directly connected link. Based on the relationship between the objective function and the constraint deviation, the penalty is zero if the constraint is satisfied; otherwise, the cost depends on how much the offset deviates from the delay bound—the greater the deviation, the higher the cost. Accordingly, the fitness function for frame
is formulated as follows:
In the formula,
represents the end-to-end delay constraint time. By summing over all TT data frames
, the overall fitness function
under the end-to-end transmission delay constraint is obtained, as shown in following:
- 5.
Optimization Equation Design
By summing the fitness functions corresponding to the aforementioned constraints and assigning the respective weights, the final optimization equation of the genetic algorithm is obtained, as expressed in following:
Here, , , , and are constants that adjust the relative weight of the four different constraint-related penalty within the overall fitness function.
4.3.3. Genetic Operators
Genetic operators are the core mechanism of genetic algorithms, and they drive the algorithm to explore the search space and ultimately approximating the global optimal solution by manipulating the genes of individuals in the population. This paper optimizes the design of genetic operators for the TTE scheduling problem, including crossover, mutation, and selection.
This algorithm conducts scheduling based on messages with pre-planned transmission paths. If frames from two different transmission paths are crossovered, the transmission path of the resulting offspring will be changed from the original frames, causing individual failure. Therefore, the crossover is performed only between the same frame across different individuals, and crossover between different frames is avoided to prevent excessive divergence in the search process, which could negatively impact convergence speed. A uniform crossover strategy is adopted, in which 50% of the genes are randomly selected from two parent individuals for exchange. Considering that frame transmission must follow the sequential order of links, the resulting offsets must be re-sorted temporally after crossover to ensure that the link transmission order constraints are met.
Direct manipulation of scheduling time is the core to solving TTE scheduling problems. Therefore, a hybrid mutation mechanism combining time shifting and time swapping is adopted. In the time shifting mechanism, the scheduling time of each frame on each link within an individual is randomly increased or decreased by time slots. The value of is selected to ensure that the shifted frame still meets its period constraints. For individuals with larger fitness deviation, a larger is chosen, while for those with smaller fitness deviation, a smaller is used. In the time swapping mechanism, the scheduling times of different frames on the same link are randomly exchanged. A new scheduling table is generated, and the mutated frames are re-sorted temporally to conform to the link transmission order.
To improve convergence speed and avoid falling into local optima, a hybrid selection strategy combining parent-offspring competition and random individual competition is adopted. First, in the parent-offspring competition mechanism, both the original individual and its corresponding offspring (after crossover and mutation) are evaluated using the fitness function, and the one with the lower fitness value is selected. This approach preserves high-quality position vectors and accelerates convergence. Second, to enhance population diversity, a random individual competition mechanism is employed. A new individual is randomly generated, and its fitness is compared with that of the original individual. The one with the lower fitness value is retained. This mechanism helps the algorithm escape local optima and expand the search space.
4.3.4. Genetic Operation Process
The schedule table of the entire network is solved based on the initial population, fitness function, and genetic operators. The genetic operation process is shown in
Figure 6.
initial individuals are randomly generated to form the initial population. After initialization, the evolution stage begins. The algorithm generates new individuals through three operations: firstly, randomly generating a certain amount of new individuals to increase population diversity; secondly, randomly selecting two individuals and performing crossover operation with probability ; and thirdly, randomly selecting one individual and performing mutation operation with probability . For each of the above three operations, the fitness of the new and original individuals is compared, and the better individual is selected to enter the next generation population.
During population evolution, the algorithm directly retains a certain proportion of the individuals with higher fitness in the original population through an elite retention strategy.
After completing the genetic operation, calculate the fitness value of each individual in the next generation, and determine whether the termination condition is met. The termination condition is set to obtain a feasible solution or reach a specified solution time. If it is met, output the result and terminate the algorithm; otherwise, use the generated population as the current population and enter the next evolving stage. The entire process iteratively optimizes the population until the termination condition is met, ultimately obtaining a TTE scheduling table that meets the scheduling constraints.
4.3.5. Selection and Analysis of Algorithm Parameters
The main parameters of the genetic algorithm include the population size , the elite retention ratio , the fitness function weights , , , , the initial crossover probability , and the initial mutation probability . For the large-scale TTE network scheduling problem discussed in this paper, the parameter ranges and selection methods are analyzed and explained, along with a sensitivity analysis of these parameters under different network and message scales.
The population size affects the diversity and convergence speed of the algorithm. The population should be sufficiently large to cover the search space, but an excessively large size will increase computational overhead. For solving the TTE scheduling problem, it is recommended that be selected within a range of 50 to 600, depending specifically on the problem complexity and available computational resources. In practical applications, fine-tuning based on the algorithm’s runtime performance is also advisable. According to genetic algorithm theory, should be proportional to the size of the search space. When the network scale and message scale increase, the search space grows exponentially, and must be increased accordingly.
- 2.
Elite Retention Ratio
The elite retention ratio ensures that superior individuals are preserved for the next generation, influencing both convergence speed and diversity. An excessively high value of may lead to premature convergence, while an overly low value risks losing high-quality solutions. For solving the TTE scheduling problem, the recommended range for is between 10% and 20%. According to the theory of elitist strategies, as the network scale and message scale increase, obtaining high-quality solutions becomes more challenging; therefore, can be appropriately increased to accelerate convergence.
- 3.
Fitness Function Weights
The fitness function weights are used to balance the importance of the frame period constraint, contention-free constraint, switch traversal constraint, and end-to-end delay constraint. In practical applications, frame period constraints and contention-free constraints are the most fundamental constraints for meeting TTE schedulability, and , are usually assigned relatively high weights; the switch traversal constraint is related to the buffering limitations of switches. In practical applications, the buffering capacity of switches is relatively flexible, making it easy to meet the switch traversal constraint conditions for TT frames, so a smaller weight can be assigned to ; the end-to-end delay constraint is a fine adjustment of delay under the above three constraints, and has a smaller impact on overall TTE schedulability, so a smaller weight can also be assigned to .
For solving the TTE scheduling problem, it is recommended that the values of weights , , , and be within the range of [0.4–0.6], [0.2–0.4], [0.05–0.2], and [0.05–0.2], respectively. The values should be positive real numbers and meet the normalization conditions. As the network scale and message scale increase, constraint conflicts intensify, and the weights need dynamic adjustment. should increase with scale because delay accumulation becomes more significant in large-scale networks; should increase with scale because contention risk becomes more critical; while and will be relatively stable.
For the optimization of weight values, adjustments can be made based on the initial selected values according to the algorithm’s running results. If it is found that the optimization effect of a certain fitness function is significant while other functions change little, it indicates that the weight of that loss function may be too high, and its weight needs to be appropriately reduced, while the weights of other fitness functions need to be increased, and adjustments are repeated until the optimization effects of all fitness functions tend to be balanced.
- 4.
Crossover and Mutation Probabilities
The crossover and mutation rates control the balance between exploration and exploitation in the algorithm. An excessively high crossover rate may lead to premature convergence, while an overly low rate slows convergence. An excessively high mutation rate can destroy good solutions, while an overly low rate results in insufficient diversity. For solving the TTE scheduling problem, the recommended range for initial crossover probability is 0.6 to 0.9, and for initial mutation probability is 0.01 to 0.1. According to classical genetic algorithm theory, and should be adjusted according to problem complexity. As the scale increases and the search space expands, enhancing exploration capability becomes necessary; therefore, can be appropriately increased with scale.
To accelerate the convergence speed of the algorithm, an adaptive parameter tuning method was adopted for the crossover and mutation probabilities, which are tuned according to the following formula:
In the formula, represents the dynamic crossover probability, represents the dynamic mutation probability, and represents the initial hyperparameter, represents the maximum fitness value in the population, represents the average fitness value in the population, represents the fitness value of the parent with higher fitness among the two parents before the crossover operation, and represents the fitness value of the individual after the mutation operation.
5. Simulation and Analysis
5.1. Simulation Parameters and Algorithms
In the simulation network, five different types of TT messages are configured. Based on the message periods, the cluster cycle of the network is set to 30,000 time slots. The detailed configuration of the messages is shown in
Table 1.
According to the scheduling characteristics of TTE, the greater the number of time slots occupied by TT messages on a link, the higher the scheduling complexity. To quantify the scheduling difficulty of a link, a link scheduling pressure parameter is defined. This parameter is expressed as the ratio between the number of time slots occupied by TT messages on the link within a cluster cycle and the total number of time slots in that period. The link scheduling pressure
of link
can be calculated as follows:
In the formula,
represents the cluster cycle,
denotes the number of cycles of frame
within the cluster cycle, and
represents the set of all frames in the critical link. To thoroughly evaluate the scheduling performance of the proposed algorithm under varying scheduling pressures, eight simulation conditions are designed based on different network load levels. These conditions cover a range of scheduling pressure levels on the link, with the number of frames and link scheduling pressure configured for each case shown in
Table 2.
The simulation adopts the network topology shown in
Figure 2, which includes 35 end systems and 6 switches, totaling 41 network nodes. Frame forwarding behavior occurs only at the switches. The communication links between nodes are represented by straight lines; since the network uses full-duplex bidirectional links, each direct connection represents two separate links. The two numbers on each line indicate the link IDs in both directions. There are 80 links in total across the network. To verify the scalability of the algorithm, the network scale was further increased based on the aforementioned basic network topology, and the configurations of the three resulting simulation network topologies are shown in
Table 3.
Taking topology 1 as an example, assume that nodes 26–31 have relatively high latency and jitter requirements for BE messages, therefore link 16 associated with them also has high link importance. Meanwhile, due to the direct connection to the central root node, link 16 has the highest link centrality. Finally, we configured link 16 with frames according to
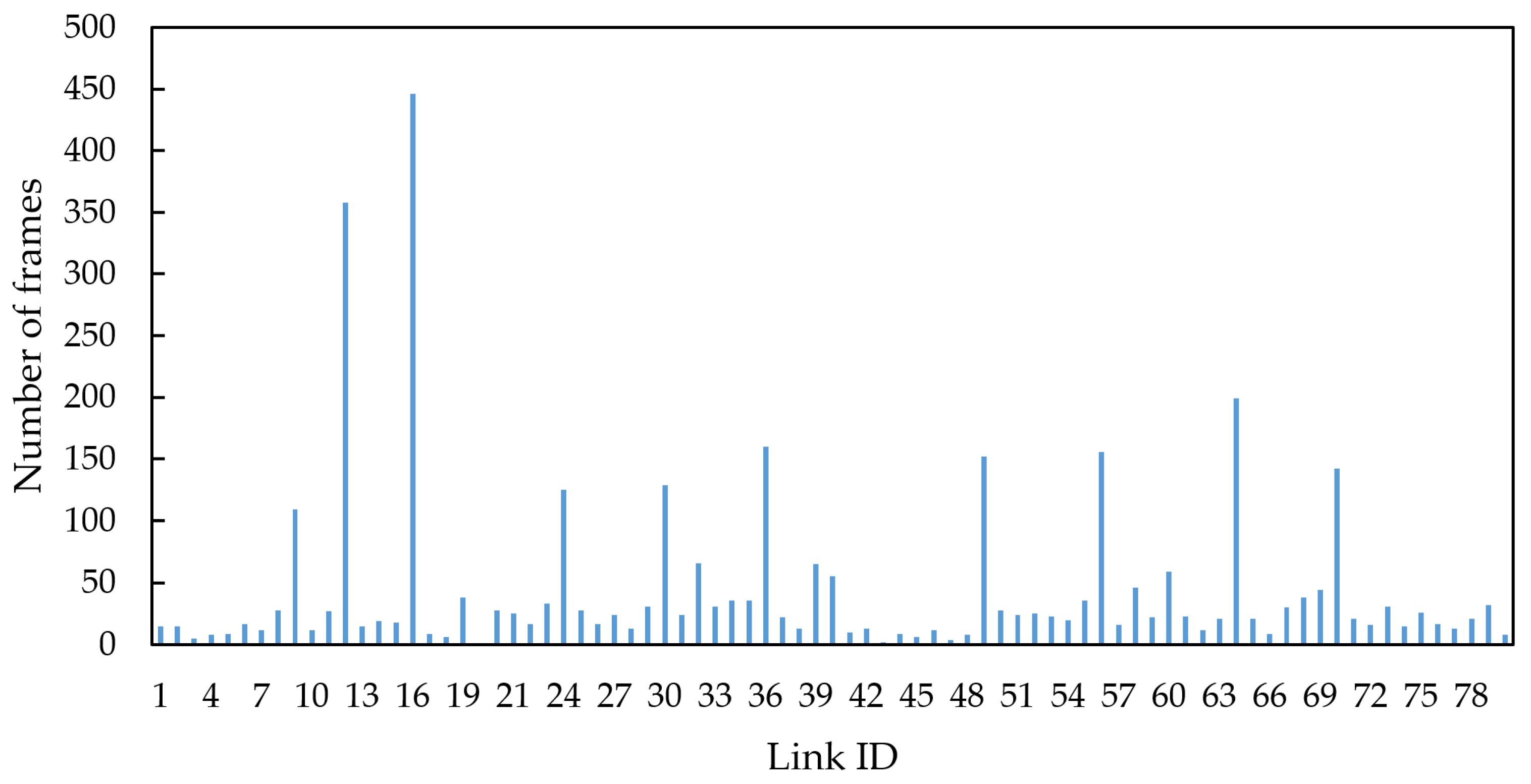
Table 2, which has a relatively high link traffic load. The link criticality of each link was calculated, and the link with the highest criticality, link 16, was ultimately selected as the critical link for simulation. The frame distribution across each link under condition 5 and topology 1 is shown in
Figure 7.
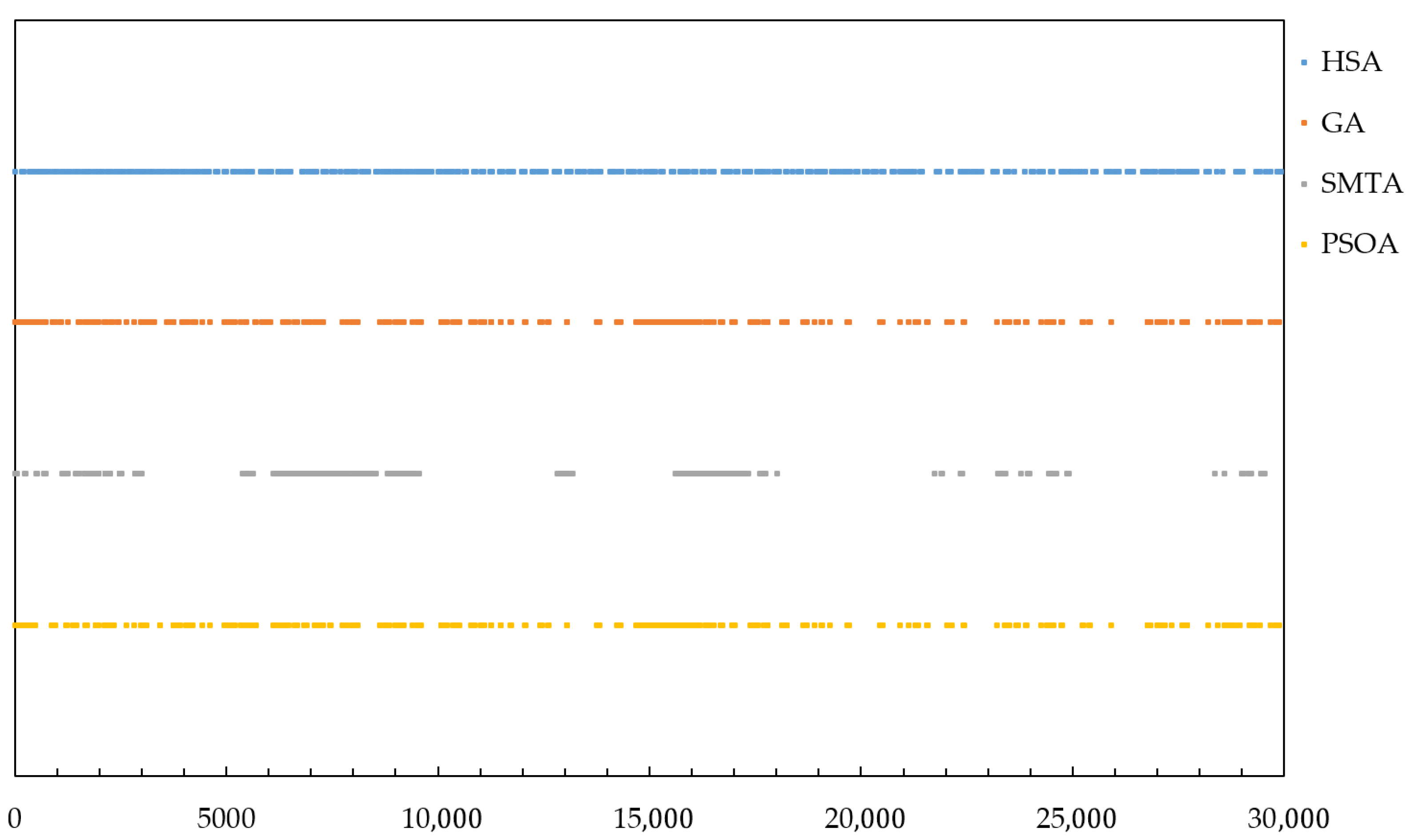
It can be observed that among the 80 links, there is a significant variation in the frame distribution. Links connected to switch nodes carry more frames compared to those connected to end nodes. Link 16 has the highest frame count and is identified as the critical link in this simulation.
To validate the effectiveness of the proposed algorithm, three scheduling algorithms are selected for comparison: the SMT algorithm (SMTA), the Genetic Algorithm (GA), the Particle Swarm Optimization Algorithm (PSOA) and the proposed Hybrid Scheduling Algorithm (HSA) based on critical-link optimization. Both SMTA and PSOA are based on industrial standard algorithms. GA is the global scheduling algorithm proposed in this paper, with relevant parameters consistent with those of the HSA based on critical link optimization. The weights , , , of the fitness function of the genetic algorithm are set to 0.54, 0.32, 0.08, 0.06, respectively, the population size is set to 350, the elite retention ratio is set to 20%, the initial crossover probability is set to 0.8, and the initial mutation probability is set to 0.08.
The simulation experiments were conducted on a system equipped with an Intel® Core™ i9-12900H CPU and 32 GB of RAM (Intel Corporation, Santa Clara, CA, USA). The scheduling algorithms were implemented using MATLAB R2016a, and comparative simulations were performed on the PyCharm Community Edition 2023.2.3 development platform.
5.2. Calculation Time and Success Rate of Solution
Three algorithms were used to solve the TTE scheduling tables under three topologies and eight different conditions, and each algorithm was run 10 times under each condition. If a feasible solution could not be found within 2 h, the run was considered a failure and the simulation was terminated. For the SMT solver, a random seed was set and heuristic search was enabled to ensure the randomness of each solving process. The running results of three algorithms under eight conditions are summarized in
Table 4.
In
Table 4, each cell contains two values: the average calculation time (in seconds) and the success rate of obtaining a feasible solution. A dash (“–”) indicates that no solution was found within the 2 h time limit.
The comparison shows that in large-scale network TT scheduling, the SMTA has the longest calculation time, which grows rapidly with the increase in message volume, while its success rate continuously declines. Under all three network topologies, there are cases where the SMTA rarely produces feasible results. Since SMTA relies on exhaustive search, while GA and PSOA iteratively optimizes along constraint convergence directions, their solving times are relatively shorter than that of SMTA, and their success rates are higher. However, as message scale increases, there are cases where no solution can be found for GA under all three topologies, and for PSOA under topologies 2 and 3. Compared to SMTA, GA and PSOA, the proposed HSA consistently achieves the shortest solving times across all conditions and succeeds in all topologies. This improvement stems from combining the critical link algorithm with a global genetic algorithm, which enhances the efficiency of scheduling on key links and overall solution quality, making it better suited for large-scale message transmission in complex topologies.
5.3. Degree of Balance in Message Scheduling
Since the scheduling balance of TT messages directly affects the performance of BE messages, the scheduling balance achieved by the three algorithms is compared using the formula defined as follows:
Here,
denotes the time interval between any two TT messages,
represents the total number of message intervals, and
denotes the average message interval. The calculated degree of balance ranges from 0 to 1, where a larger value indicates higher balance. The average scheduling balance of the three algorithms under eight conditions is shown in
Figure 8.
The comparison of scheduling balance above shows that HSA consistently achieves higher balance than the SMTA, GA and PSOA across all conditions. As the message scale increases, the SMTA, GA and PSOA exhibit a significant decline in balance, whereas the HSA maintains a relatively stable balance level. This stability results from the HSA’s use of a slot-balanced scheduling algorithm for the critical link during the initial static scheduling phase, which ensures an even distribution of TT message intervals on the critical link. Additionally, due to the periodic nature of TT messages, this balanced distribution on the critical link propagates throughout the entire network, thereby optimizing overall network balance.
Taking condition 5 under topology 1 as an example, the Gantt charts of TT frames of link 16 generated by the three algorithms are shown in
Figure 9.
Figure 9 shows that the message scheduling obtained by the SMTA exhibits high randomness, resulting in the most uneven slot distribution and clearly causing greater delay and jitter for BE messages. The GA and PSOA produces a relatively more uniform message distribution compared to SMTA. The proposed HSA achieves the most optimal slot distribution, with well-spaced intervals between TT messages, minimizing the impact on BE message transmission performance.
5.4. BE Message Transmission Performance
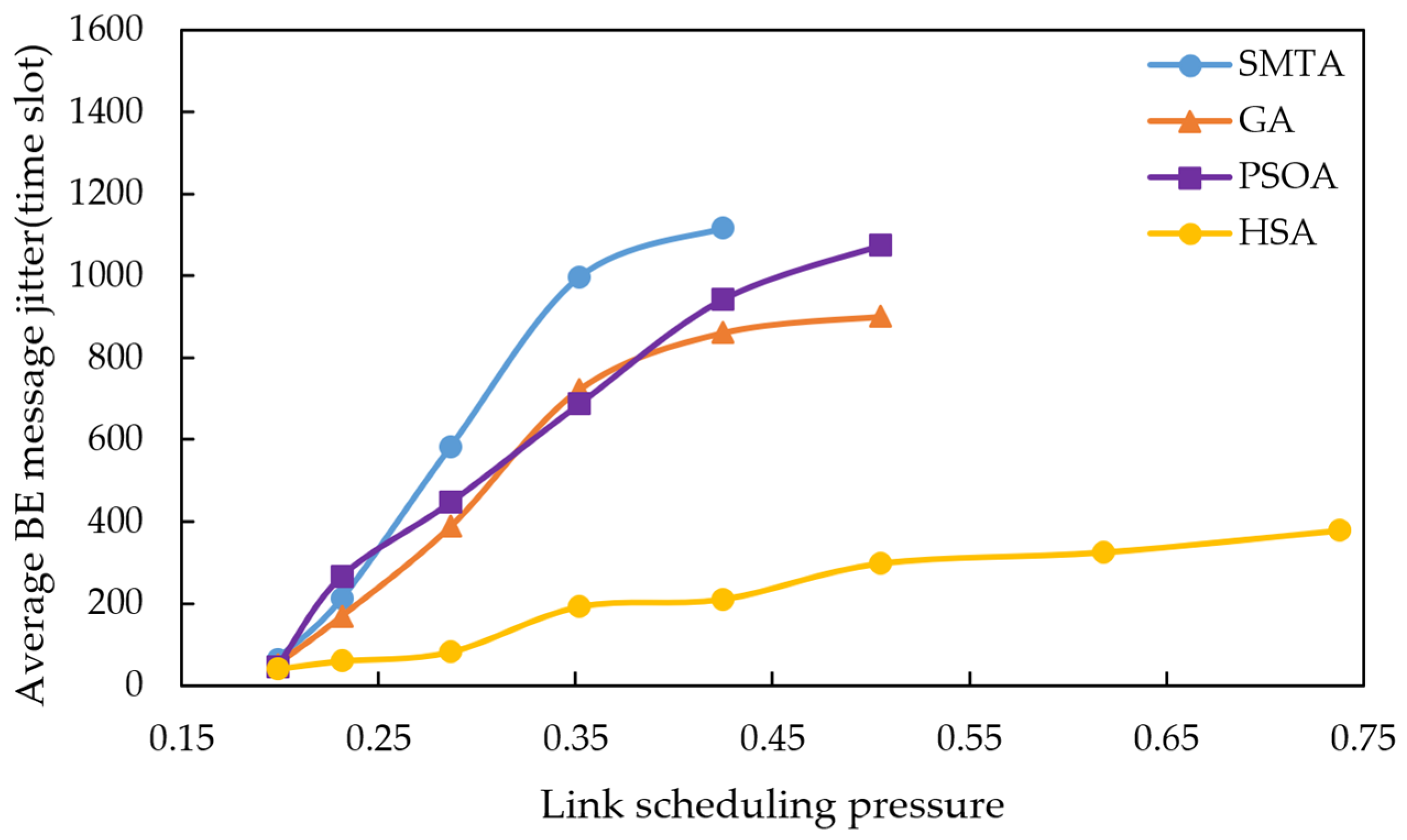
Using the scheduling results described above, a simulation of network message transmission performance was conducted. Four hundred BE messages were randomly generated from network nodes, and their transmission delays were recorded at the receivers. To simulate random network traffic, the arrival process of BE messages is set to a Poisson process and the packet-size distribution is set to log-normal distribution. The average BE message delay under the eight conditions for different algorithms are shown in
Figure 10,
Figure 11 and
Figure 12, with the corresponding average jitter presented in
Figure 13,
Figure 14 and
Figure 15.
The figures indicate that as the message scale increases, the BE message delay and jitter resulting from the scheduling table of SMTA, GA and PSOA grow significantly, whereas those from the HSA remain substantially lower. For instance, under topology 1 and condition 5, the average BE message delay with the HSA is reduced by 87.9% compared to SMTA, by 71.8% compared to GA, and by 68.1% compared to PSOA. Similarly, the average BE message jitter with the HSA decreases by 81.1% relative to SMTA, by 75.6% relative to GA, and by 77.7% relative to PSOA.
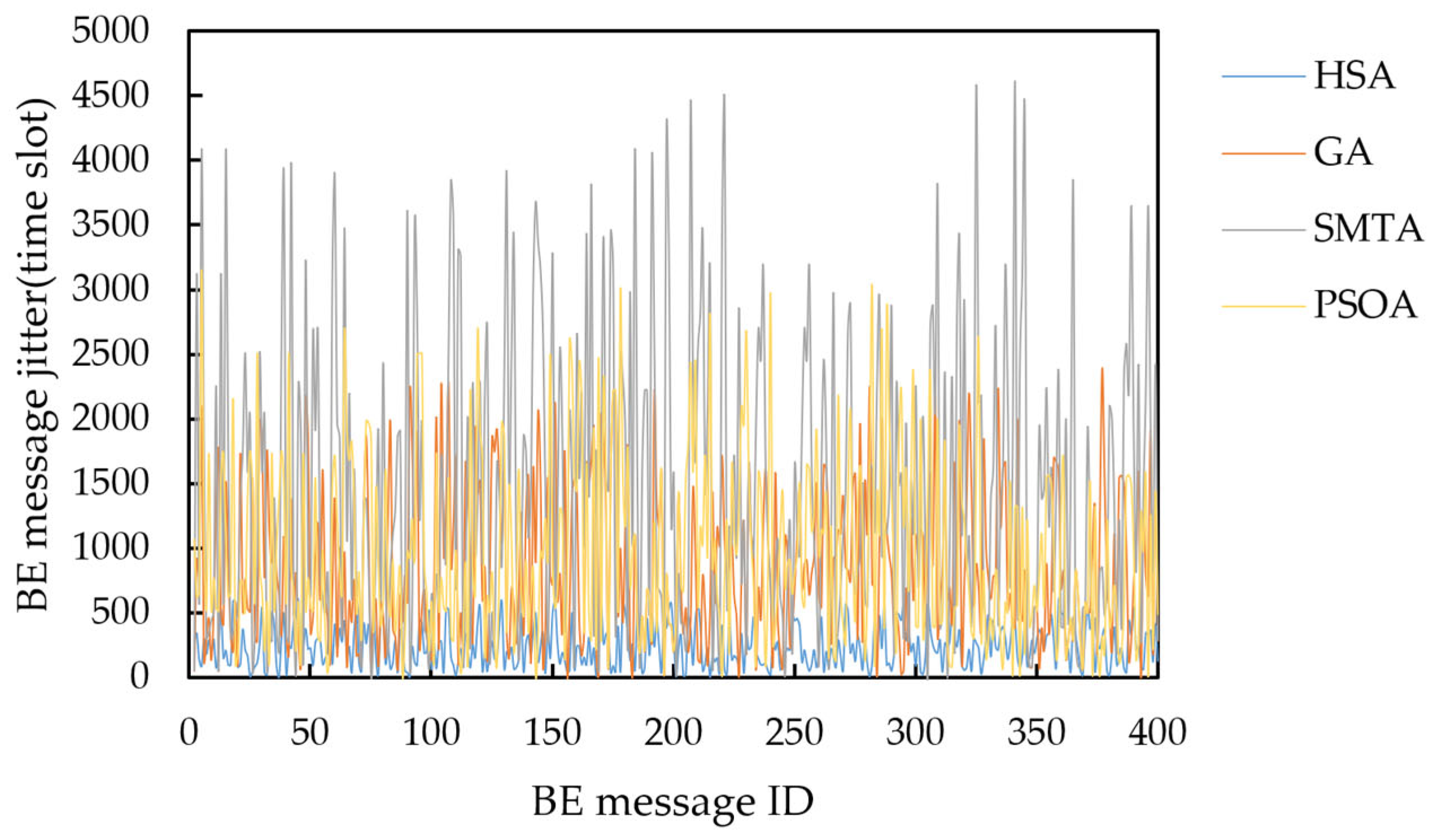
Taking topology 1 and condition 5 as an example, the delay distribution of four hundred BE messages under the scheduling results of the three algorithms is shown in
Figure 16, and the jitter distribution is shown in
Figure 17.
The figure shows that the scheduling results from the SMTA, GA and PSOA exhibit significant fluctuations in BE message transmission delay due to the “back-to-back” arrangement of numerous TT messages. Specifically, the SMTA’s maximum delay and jitter are 4970 and 4689 time slots, respectively; the GA’s maximum delay and jitter are 2800 and 2391 time slots respectively; and the PSOA’s maximum delay and jitter are 3585 and 3151 time slots respectively. In contrast, the HSA employs static scheduling based on slot balancing on the critical link, producing deterministic schedules that facilitate rapid BE message transmission through gaps between TT messages. As a result, HSA achieves the lowest message delays, with a maximum delay of 980 time slots and a maximum jitter of 598 time slots. This demonstrates that the HSA significantly reduces BE message transmission delay and jitter.
6. Conclusions
This paper addresses the scheduling demands of large-scale TTE by constructing a representative large-scale TTE network topology and establishing a TTE message scheduling model. The scheduling constraints of TTE messages are analyzed, and a critical-link optimized scheduling algorithm for large-scale TTE is proposed. The algorithm adopts a two-step approach: first, it applies a static priority–based slot-balanced scheduling algorithm on critical links; then, it incorporates the critical link results as fixed genes in the initial population of a genetic algorithm to perform global network scheduling. This method optimizes both the solving process and the results. As the network message volume increases, the algorithm improves the success rate, reduces solving time, and effectively minimizes the impact of TT messages on BE message transmission performance, making it well-suited for large-scale TTE scheduling scenarios. The following conclusions can be drawn:
Compared to traditional algorithms that apply the same solving method to all links, this work identifies link heterogeneity by locating critical links within the network topology and applies a distinct static solving algorithm specifically for these critical links, thereby improving solving efficiency. Additionally, the use of slot-balanced scheduling on critical links effectively reduces the impact of the scheduling results on BE message performance.
Compared to the conventional SMT algorithm used in engineering applications, this paper employs a genetic algorithm to solve the global network scheduling table. It abstracts network constraints into a mathematical model and constructs a scheduling framework with effective fitness functions and genetic operators. Leveraging the genetic algorithm’s strong global search capability and parallel computing advantages, the approach accelerates convergence and enhances scheduling performance.
Simulation results demonstrate that, in large-scale TTE environments, the proposed algorithm achieves higher solving success rates and shorter solving times compared to traditional methods. Additionally, it effectively reduces BE message transmission delay and jitter, making it more suitable for dense message scheduling in large-scale, complex network topologies.
Despite the insights provided, several limitations merit mention. Firstly, the algorithm we proposed is a static solution and offline scheduling algorithm. In industrial networks, there may be application scenarios where network topology or traffic changes dynamically. Future work will focus on the incremental or online scheduling methods of TTE. Secondly, the algorithm proposed in this paper is based on the premise that the transmission path of messages has been pre-determined. Factors such as path selection, path backup, and path distance constraints in path planning also affect the scheduling results of messages [
30]. In subsequent work, we will continue to study the joint optimization of message path planning and message scheduling.