A Lightweight Certificateless Authenticated Key Agreement Scheme Based on Chebyshev Polynomials for the Internet of Drones
Abstract
Highlights
- We propose a novel and practical certificateless cryptographic scheme utilizing Chebyshev polynomials.
- The proposed scheme significantly reduces computational overhead compared to existing solutions. Performance evaluations and comparative analysis reveal a substantial decrease in computational costs, with our scheme requiring approximately 65% less computational effort.
- This work fills a critical research gap by establishing a practical certificateless cryptographic scheme based on Chebyshev polynomials. Beyond this novelty, it also promotes the broader application and exploration of Chebyshev polynomials within the domain of public key cryptography.
- The considerable reduction in computational overhead, particularly when compared to certificateless schemes based on elliptic curve cryptography, positions our proposed solution as a highly attractive option for resource-constrained environments (e.g., the IoD).
Abstract
1. Introduction
Contribution
- (1)
- Compared with the traditional public key cryptography mechanism, the proposed certificateless public key cryptography scheme not only improves the deployment flexibility of UAV nodes (e.g., allowing for rapid network access without pre-set certificates) but also enhances the system security by reducing the risk of key escrow.
- (2)
- To address the computational constraints of IoD nodes, we introduce Chebyshev polynomials with lower computational overhead as certificateless cryptographic operators and construct a lightweight key negotiation protocol using their semigroup property.
- (3)
- The security and performance analysis shows that the proposed scheme achieves a balance between security and resource overhead while guaranteeing IoD low-latency communication and dynamic topology adaptation.
2. Related Work
3. Preliminaries
3.1. Chebyshev Polynomial
3.2. Property
3.3. Mathematically Hard Problems
4. Our Proposal
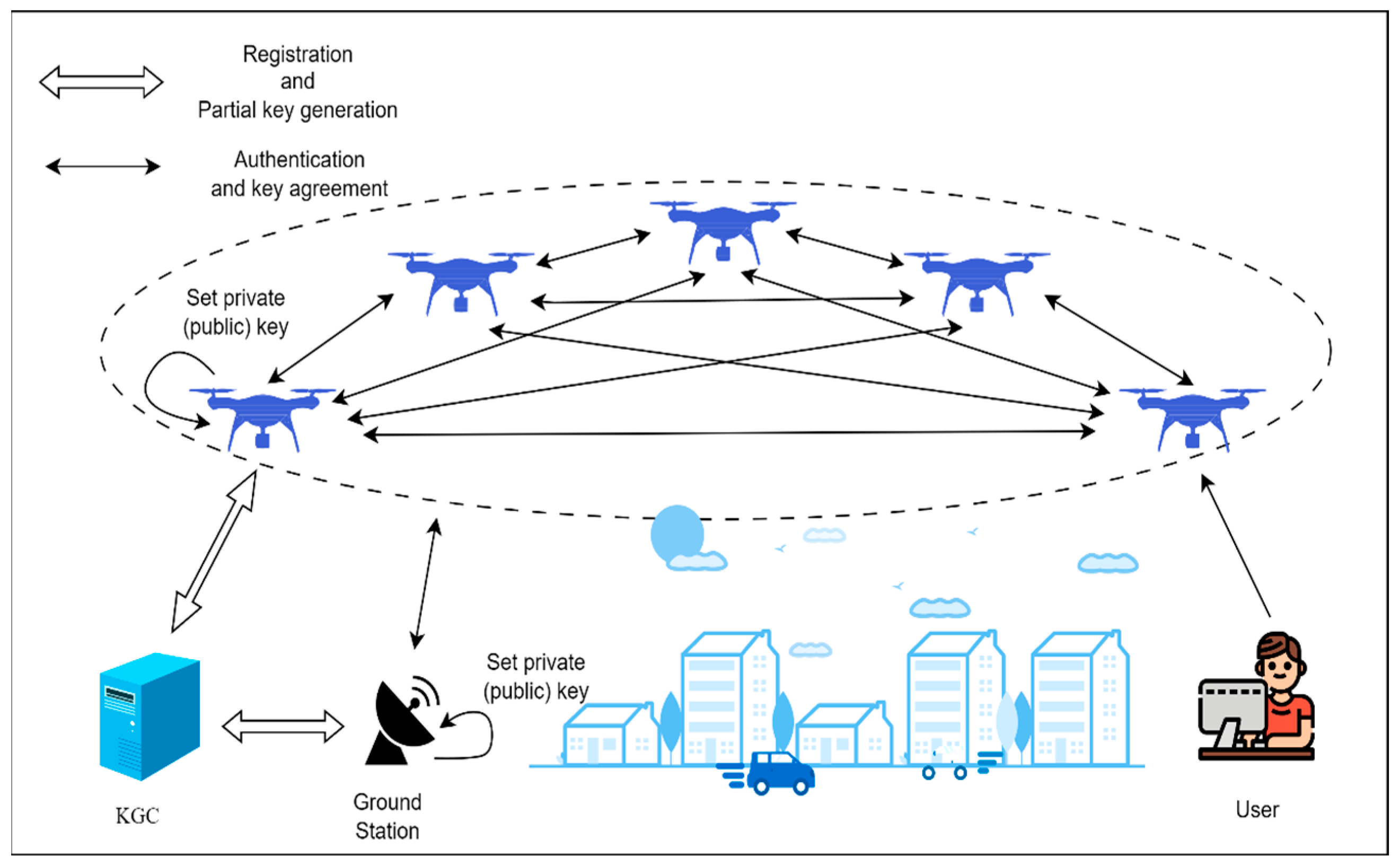
4.1. System Model
4.2. Certificateless Authenticated Key Negotiation Based on Chebyshev Polynomials
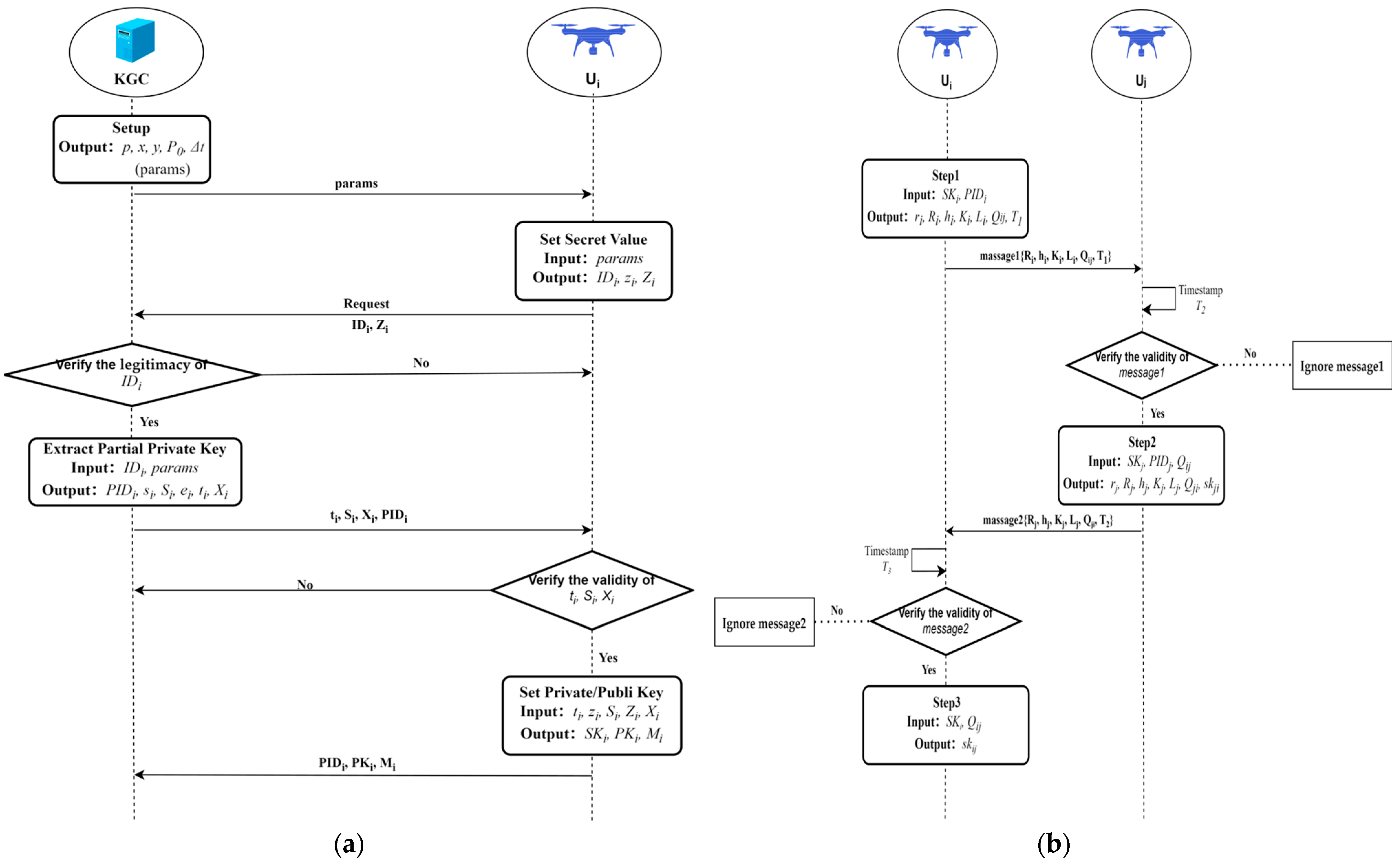
4.2.1. Setup Phase
- (1)
- KGC picks a sufficiently large prime and creates a unique identity .
- (2)
- KGC chooses as the seed of a Chebyshev polynomial and a one-way secure hash function .
- (3)
- KGC chooses a random number as the system master private key and computes the corresponding system public key .
- (4)
- KGC selects a request validity time for the system.
- (5)
- KGC publishes to each user through a secure channel and secretly keeps its private key y.
4.2.2. Authenticated Key Negotiation
- (1)
- selects a random number , calculates , and transmits a registration request containing information such as to the KGC server through a secure channel.
- (2)
- Upon receiving the registration request from , the KGC verifies the legitimacy of by checking it against a pre-established list of valid identities. If the provided by is present in the identity list, is allowed to register; otherwise, the registration request from is denied.
- (3)
- KGC uses the real identity of UAV to compute to generate the pseudonym .
- (4)
- KGC picks a random number , computes , , , and , then returns the through the secure channel back to .
- (5)
- receives , then calculates , , and verifies . If it holds, accept ; otherwise, ignore the message.
- (6)
- obtains the complete public/private key pair , where , .
- (7)
- precomputes , and sends through the secure channel to KGC.
4.2.3. Authentication and Key Negotiation Phase
- (1)
- chooses a random number and computes .
- (2)
- takes the current timestamp , calculates , , , , and sends to .
- (3)
- receives the message , obtains the current timestamp , checks whether is valid, and retrieves the legitimacy of the and obtains the via KGC. If any of the above conditions are not satisfied, ignores the message.
- (4)
- calculates , and verifies that , if it is valid, then continue with the following process. Otherwise, the authentication is rejected.
- (5)
- chooses the random number and computes the session key .
- (6)
- computes , , , , , and send to .
- (7)
- Receiving the message , obtains the current timestamp , checks whether is valid, and retrieves the legitimacy of and obtains via KGC. If any of the above conditions are not satisfied, ignores the message.
- (8)
- calculates , and verifies that . If it holds, computes the session key .
4.2.4. Correctness Analysis
4.3. Informal Security Analysis
4.3.1. Device Capture Attack
4.3.2. Forward Secrecy
4.3.3. Man-in-the-Middle Attack
4.3.4. Replay Attack
4.3.5. Identity Privacy Protection
4.3.6. Key Leakage Attack
4.3.7. Eavesdropping Attack
4.3.8. Impersonation Attack
4.3.9. Temporary Key Leakage Attack
4.3.10. Insider Privilege Attack
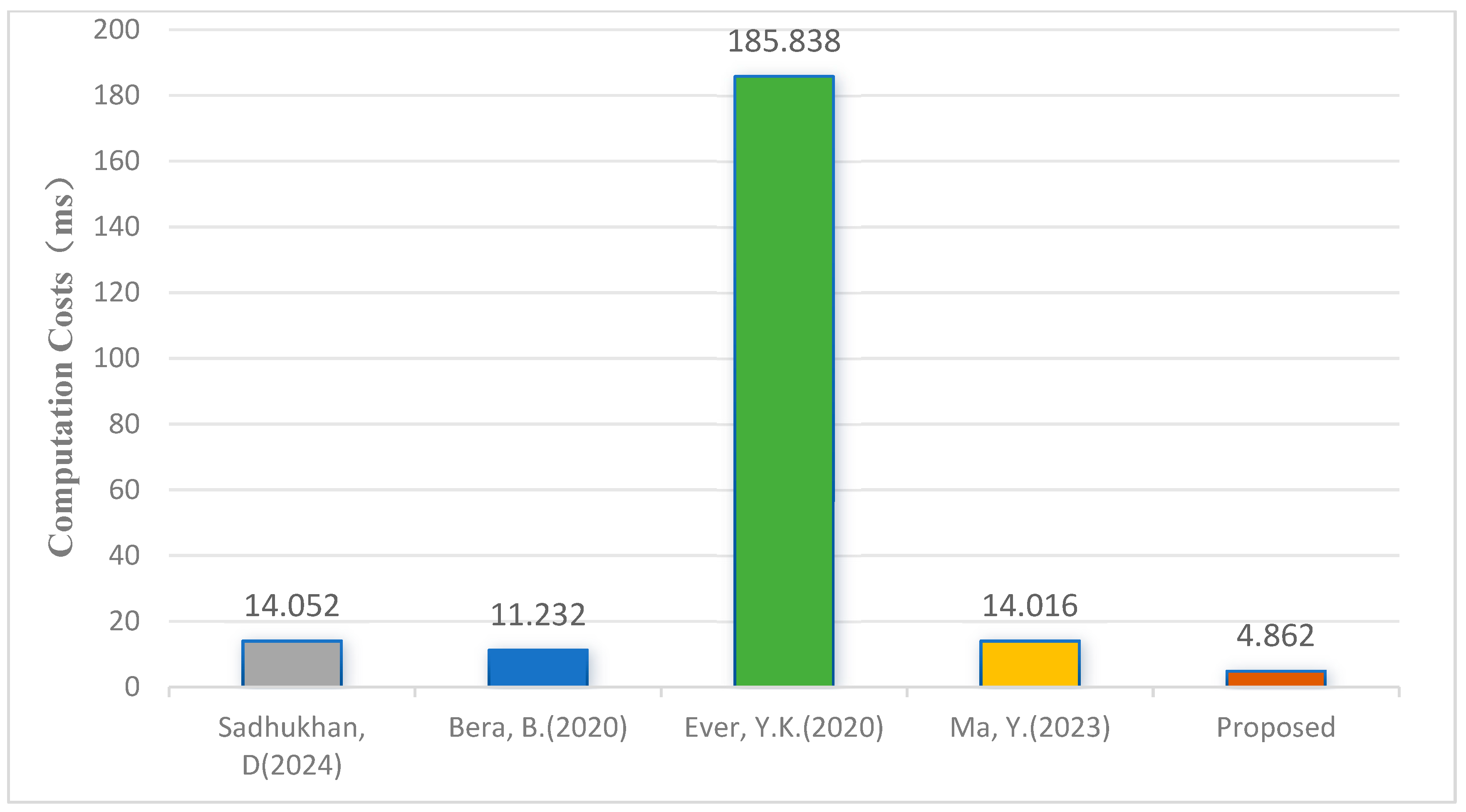
5. Performance Analysis
5.1. Scheme Computational Cost
5.2. Scheme Communication Cost
6. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| IoD | Internet of Drones |
| UAV | Unmanned Aerial Vehicle |
| IoT | Internet of Things |
| CA | Certificate Authority |
| IBC | Identity-based Cryptography |
| CL-PKC | Certificateless Public Key Cryptography |
| ECC | Elliptic Curve Cryptography |
| PUF | Physical Unclonable Functions |
| IoV | Internet of Vehicles |
| IBE | Identity-based Encryption |
| CDLP | Chebyshev Discrete Logarithm Problem |
| CDHP | Chebyshev Diffie-Hellman Problem |
| KGC | Key Generation Center |
| Notion | Meaning |
| Identifier of | |
| Timestamp | |
| Pseudonym of | |
| Private/Public key of | |
| Private/Public key of KGC | |
| cryptographic hash function | |
| large prime number | |
| Seed of Chebyshev polynomials | |
| Chebyshev polynomials | |
| Session key between and |
References
- Ganesh, Y.; Ramya, R.; Rajeshwari, H. Surveillance Drone for Landmine Detection. In Proceedings of the 2015 International Conference on Advanced Computing and Communications, Chennai, India, 18–20 September 2015; pp. 33–38. [Google Scholar]
- Flammini, F.; Naddei, R.; Pragliola, C.; Smarra, G. Towards Automated Drone Surveillance in Railways: State-of-the-Art and Future Directions. In Proceedings of the International Conference on Advanced Concepts for Intelligent Vision Systems, Lecce, Italy, 24–27 October 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 336–348. [Google Scholar]
- Gharibi, M.; Boutaba, R.; Waslander, S.L. Internet of Drones. IEEE Access 2016, 4, 1148–1162. [Google Scholar]
- Chaudhry, S.A.; Irshad, A.; Alzahrani, B.A.; Alhindi, A.; Shariq, M.; Das, A.K. TS-PAID: A Two-Stage PUF-based lightweight Authentication protocol for Internet of Drones. IEEE Access 2024, 13, 1458–1469. [Google Scholar]
- Samanth, S.; Prema, K.V.; Balachandra, M. Security in internet of drones: A comprehensive review. Cogent Eng. 2022, 9, 2029080. [Google Scholar]
- Lin, C.; He, D.; Kumar, N.; Choo, K.-K.R.; Vinel, A.; Huang, X. Security and privacy for the internet of drones: Challenges and solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar]
- Badshah, A.; Abbas, G.; Waqas, M.; Tu, S.; Abbas, Z.H.; Muhammad, F.; Chen, S. USAF-IoD: Ultralightweight and secure authenticated key agreement framework for internet of Drones environment. IEEE Trans. Veh. Technol. 2024, 73, 10963–10977. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless Public Key Cryptography. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 30 November–4 December 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Zhang, L.; Zhu, Y.; Ren, W.; Wang, Y.; Choo, K.-K.R.; Xiong, N.N. An energy-efficient authentication scheme based on Chebyshev chaotic map for smart grid environments. IEEE Internet Things J. 2021, 8, 17120–17130. [Google Scholar]
- Cui, J.; Wang, Y.; Zhang, J.; Xu, Y.; Zhong, H. Full session key agreement scheme based on chaotic map in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2020, 69, 8914–8924. [Google Scholar]
- Bhattarai, I.; Pu, C.; Choo, K.-K.R.; Korać, D. A Lightweight and Anonymous Application-Aware Authentication and Key Agreement Protocol for the Internet of Drones. IEEE Internet Things J. 2024, 11, 19790–19803. [Google Scholar]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and analysis of secure lightweight remote user authentication and key agreement scheme in internet of drones deployment. IEEE Internet Things J. 2018, 6, 3572–3584. [Google Scholar]
- Sadhukhan, D.; Ray, S.; Dasgupta, M.; Rodrigues, J.J. CLAACS-IOD: Certificate-embedded lightweight authentication and access control scheme for Internet of Drones. Softw. Pract. Exp. 2024, 54, 1972–2006. [Google Scholar]
- Bera, B.; Chattaraj, D.; Das, A.K. Designing secure blockchain-based access control scheme in IoT-enabled Internet of Drones deployment. Comput. Commun. 2020, 153, 229–249. [Google Scholar]
- Ever, Y.K. A secure authentication scheme framework for mobile-sinks used in the internet of drones applications. Comput. Commun. 2020, 155, 143–149. [Google Scholar]
- Ma, Y.; Li, X.; Shi, W.; Cheng, Q. STCLA: An efficient certificateless authenticated key agreement scheme for the internet of vehicles. IEEE Trans. Veh. Technol. 2023, 73, 4830–4841. [Google Scholar]
- Lin, H.T.; Jhuang, W.L. Blockchain-based lightweight certificateless authenticated key agreement protocol for v2v communications in iov. IEEE Internet Things J. 2024, 11, 27744–27759. [Google Scholar]
- Tedeschi, P.; Sciancalepore, S.; Eliyan, A.; Di Pietro, R. LiKe: Lightweight certificateless key agreement for secure IoT communications. IEEE Internet Things J. 2019, 7, 621–638. [Google Scholar]
- Abbasinezhad-Mood, D.; Ostad-Sharif, A.; Mazinani, S.M.; Nikooghadam, M. Provably secure escrow-less Chebyshev chaotic map-based key agreement protocol for vehicle to grid connections with privacy protection. IEEE Trans. Ind. Inform. 2020, 16, 7287–7294. [Google Scholar]
- Pu, C.; Choo, K.K.R. Chebyshev Polynomial and Private Blockchain Based Cross-Domain Authentication Protocol for IoD Networks. In Proceedings of the 2024 IEEE 21st Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 6–9 January 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 931–936. [Google Scholar]
- Habutsu, T.; Nishio, Y.; Sasase, I.; Mori, S. A secret key cryptosystem by iterating a chaotic map. In Advances in Proceedings 10, Proceedings of the Cryptology—EUROCRYPT’91: Workshop on the Theory and Application of Cryptographic Techniques, Brighton, UK, 8–11 April 1991; Springer: Berlin/Heidelberg, Germany, 1991; Volume 547, pp. 127–140. [Google Scholar]
- Fridrich, J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 1998, 8, 1259–1284. [Google Scholar]
- Fridrich, J. Image encryption based on chaotic maps. In Proceedings of the 1997 IEEE International Conference on Systems, Man, and Cybernetics, Computational Cybernetics and Simulation, Orlando, FL, USA, 12–15 October 1997; IEEE: Piscataway, NJ, USA, 1997; Volume 2, pp. 1105–1110. [Google Scholar]
- Cui, Z.; Jin, S.; Sone, A.; Wang, X. Quantum advantages for image filtering on images with efficient encoding and lower-bounded signal-to-noise ratio. Sci. China Physics, Mech. Astron. 2024, 67, 290362. [Google Scholar]
- Zhang, Z.; Liu, J.; Hu, J.; Wang, Q.; Meißner, U.-G. Revealing the nature of hidden charm pentaquarks with machine learning. Sci. Bull. 2023, 68, 981–989. [Google Scholar]
- Cui, J.; Yu, J.; Zhong, H.; Wei, L.; Liu, L. Chaotic map-based authentication scheme using physical unclonable function for internet of autonomous vehicle. IEEE Trans. Intell. Transp. Syst. 2022, 24, 3167–3181. [Google Scholar]
- Mahmood, K.; Ghaffar, Z.; Farooq, M.; Yahya, K.; Das, A.K.; Chaudhry, S.A. A security enhanced chaotic-map based authentication protocol for internet of drones. IEEE Internet Things J. 2024, 11, 22301–22309. [Google Scholar]
- Kocarev, L.; Tasev, Z. Public-key encryption based on Chebyshev maps. In Proceedings of the 2003 International Symposium on Circuits and Systems, ISCAS ’03, Bangkok, Thailand, 25–28 May 2003; Volume 3, pp. III-28–III-31. [Google Scholar]
- Bergamo, P.; D’ARco, P.; De Santis, A.; Kocarev, L. Security of Public Key Cryptosystems based on Chebyshev Polynomials. IEEE Trans. Circuits Syst. I Regul. Pap. 2005, 52, 1382–1393. [Google Scholar]
- Kocarev, L.; Makraduli, J.; Amato, P. Public-Key Encryption based on Chebyshev Polynomials. Circuits Syst. Signal Process. 2005, 24, 497–517. [Google Scholar]
- Ning, H.; Liu, Y.; He, D. Public Key Encryption Algorithm based on Chebyshev Polynomials over Finite Fields. In Proceedings of the 8th International Conference on Signal Processing, Guilin, China, 16–20 November 2006; p. 4. [Google Scholar]
- Zhang, L. Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 2008, 37, 669–674. [Google Scholar]
- Chen, F.; Liao, X.; Xiang, T.; Zheng, H. Security analysis of the public key algorithm based on Chebyshev polynomials over the integer ring ZN. Inf. Sci. 2011, 181, 5110–5118. [Google Scholar]
- Algehawi, M.B.; Samsudin, A. Certificateless Public Key Encryption (CL-PKE) Scheme Using Extended Chebyshev Polynomial over the Finite Field Z p. Malays. J. Math. Sci. 2015, 9, 53. [Google Scholar]
- Tan, S.Y.; Chin, J.J.; Mohamad, M.S. Security and efficiency analysis of a certificateless encryption scheme based on Chebyshev polynomial. In Proceedings of the International Conference on Frontiers of Communications, Kuala Lumpur, Malaysia, 3–5 November 2014. [Google Scholar]
- Shakiba, A.; Hooshmandasl, M.R.; Meybodi, M.A. Cryptanalysis of multiplicative coupled cryptosystems based on the Chebyshev polynomials. Int. J. Bifurc. Chaos 2016, 26, 1650112. [Google Scholar]
- Lee, T.F.; Huang, Y.C. Efficient Extended Chaotic Map-Based IBE for Industrial Environment. IEEE Access 2022, 10, 71278–71283. [Google Scholar]
- Long, Y.; Peng, C.; Tan, W.; Chen, Y. Blockchain-Based Anonymous Authentication and Key Management for Internet of Things With Chebyshev Chaotic Maps. IEEE Trans. Ind. Inform. 2024, 20, 7883–7893. [Google Scholar]
- Abdelfatah, R.I.; Abdal-Ghafour, N.M.; Nasr, M.E. Secure VANET authentication protocol (SVAP) using Chebyshev chaotic maps for emergency conditions. IEEE Access 2021, 10, 1096–1115. [Google Scholar]
- Farash, M.S.; Attari, M.A. Cryptanalysis and improvement of a chaotic map-based key agreement protocol using Chebyshev sequence membership testing. Nonlinear Dyn. 2014, 76, 1203–1213. [Google Scholar] [CrossRef]
| Notation | Description | Cost |
|---|---|---|
| Time of one-way hash operation | ≈0.002 ms | |
| Time of a bilinear pairing | ≈30.034 ms | |
| Time of an EC point multiplication | ≈1.400 ms | |
| Time of an EC point addition | ≈0.006 ms | |
| Time of a Chebyshev polynomial computation | ≈0.485 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Z.; Ju, Z.; Zhao, H.; Wei, Z.; Lan, G. A Lightweight Certificateless Authenticated Key Agreement Scheme Based on Chebyshev Polynomials for the Internet of Drones. Sensors 2025, 25, 4286. https://doi.org/10.3390/s25144286
Li Z, Ju Z, Zhao H, Wei Z, Lan G. A Lightweight Certificateless Authenticated Key Agreement Scheme Based on Chebyshev Polynomials for the Internet of Drones. Sensors. 2025; 25(14):4286. https://doi.org/10.3390/s25144286
Chicago/Turabian StyleLi, Zhaobin, Zheng Ju, Hong Zhao, Zhanzhen Wei, and Gongjian Lan. 2025. "A Lightweight Certificateless Authenticated Key Agreement Scheme Based on Chebyshev Polynomials for the Internet of Drones" Sensors 25, no. 14: 4286. https://doi.org/10.3390/s25144286
APA StyleLi, Z., Ju, Z., Zhao, H., Wei, Z., & Lan, G. (2025). A Lightweight Certificateless Authenticated Key Agreement Scheme Based on Chebyshev Polynomials for the Internet of Drones. Sensors, 25(14), 4286. https://doi.org/10.3390/s25144286