Abstract
Deterministic random bit generators (DRBG) play a crucial role in device security because they generate secret information cryptographic systems, e.g., secret keys and parameters. Thus, attacks on DRBGs can result in the exposure of important secret values, which can threaten the entire cryptographic system of the target Internet of Things (IoT) equipment and smart devices. In 2020, Meyer proposed a side-channel attack (SCA) method that recovers the output random bits by analyzing the power consumption traces of the NIST standard AES CTR DRBG. In addition, most algorithmic countermeasures against SCAs also utilize random numbers; thus, such vulnerabilities are more critical than other SCAs on cryptographic modules. Meyer’s attack recovers the secret random number in four stages of the attack using only the power traces, which the CTR DRBG processes in 256 blocks. We present an approach that employs a clustering algorithm to enhance Meyer’s attack. The proposed attack increases the attack success rate and recovers more information using a clustering attack in the first step. In addition, it improves the attack accuracy in the third and fourth steps using the information obtained from the clustering process. These results lead to the possibility of attacks at higher noise levels and increase the diversity of target devices for attacking the CTR DRBG. Experiments were conducted on an Atmel XMEGA128D4 processor to evaluate the effectiveness of the proposed attack method. We also introduced artificial noise into the power traces to compare the proposed attack’s performance at different noise levels. Our results demonstrate that the first step of the proposed attack achieves a higher success rate than Meyer’s attack at all noise levels. For example, at high noise levels, the difference in the success rates is up to 50%. In steps 3 and 4, an average performance improvement of 18.5% greater than Meyer’s proposed method is obtained. The proposed attack effectively extends the target to more noisy environments than previous attacks, thereby increasing the threat of SCA on CTR DRBGs.
1. Introduction
Side-Channel Attacks (SCAs) target cryptographic algorithms by analyzing the channel information from the target devices. SCAs have been used to attack embedded devices using various channel information, e.g., power consumption [1], timing [2], electromagnetic emission [3], photonic emission [4], and fault injection [5], in various platforms, including software [6,7,8] and hardware implementations [8,9,10]. In 1996, Kocher presented a timing attack for the first SCA method and recovered the secret key of public key cryptography by applying the timing attack [11]. Then, differential power analysis (DPA) [1], which is an SCA technique that uses the difference in the power consumption, correlation power analysis (CPA) [12] using Pearson’s correlation coefficients (PCC) between the actual and hypothetical power consumption, and mutual information analysis (MIA) [13] using the mutual information between the actual and hypothetical power consumption were proposed. Recently, differential deep learning analysis (DDLA) using the difference in deep learning results was proposed [14]. In addition, template attacks [15] that construct templates using a profile device, deep learning-based profiled SCA [16], and SCA using clustering algorithms were presented [17,18,19].
SCA methods have been applied to block ciphers and their modes of operation. For example, CPA and SPA have been applied to the modes of operation of AES, ECB, CBC, and CFB [20,21,22,23,24,25,26,27,28]. Note that most of these attacks require specific information, e.g., plaintexts, ciphertexts, and initial vectors; however, in 2007, Jaffe proposed a power analysis technique that can recover the master key of the AES counter (CTR) mode using 65,536 power traces without knowledge of the initial counter, input, or output of the CTR mode [26]. Then, in 2020, Meyer proposed an improved power analysis that required only 256 power traces to attack the AES CTR mode [27]. This attack causes a new attack in another application of AES. She demonstrated that the attack could be applied to the AES CTR DRBG because the required number of traces (blocks) of this attack, i.e., 256, is less than the CTR DRBG’s number of the least key life cycle traces (blocks), i.e., 4096. In 2023, Tienteu et al. presented a template attack against the AES CTR mode [28].
In Internet of Things (IoT) devices, CTR DRBG is primarily used to generate cryptographic secret information, e.g., secret keys, and protocols related to CTR DRBG, and optimal implementations in IoT environments have been studied previously [29,30,31,32]. The physical security evaluation of CTR DRBG is important relative to the security of cryptographic systems in IoT environments and is crucial from the SCA perspective. In masking and hiding [8], which are representative SCA countermeasures, secret randomness is employed, and the leakage of this randomness directly leads to the nullification of the countermeasures. However, if such SCA countermeasures are applied to DRBG, a circular problem will occur in which randomness is used to ensure the security of DRBG that generates randomness.Therefore, the physical security level should be evaluated and countermeasures should be discussed through SCA research on CTR DRBG in IoT environments by physical noise level.
From the perspective of the CTR DRBG attacker, Tienteu’s attack requires a stronger capability than Meyer’s. In addition, Tienteu’s template attack requires a profiling device that can control the DRBG’s internal state information; however, Meyer’s attack does not require a profiling device and, similar to Jaffe’s attack, only uses the power consumption to recover the internal secret value. In CTR DRBG attacks, unlike in general SCA scenarios, the number of traces an attacker can obtain is strictly limited by the DRBG’s internal state update cycle. Thus, whether an attack on a target is possible is determined by the performance of the attack method, and the attack success rate under the same conditions (e.g., the noise level and number of traces) becomes much more important than in other SCA scenarios.
This paper presents an improved SCA method for AES CTR DRBG based on Meyer’s approach. The proposed method employs a clustering algorithm and achieves a higher success rate than Meyer’s approach for all noise levels.
1.1. Contribution
Figure 1 summarizes the processes of Meyer’s approach and the proposed attack. CPAs can be replaced with other non-profiled SCA methods, e.g., DPA, MIA, and DDLA, in these attack processes. We describe those based on CPA in this study. This paper presents an enhanced power analysis attack on the AES CTR DRBG that outperforms previous methods. Building on Meyer’s approach, the proposed attack method uses only 256 power traces and comprises four main steps. In step 1, we employ a clustering algorithm and an 8-bit CPA to recover 1 byte of each CTR mode IV value and the AES key. Our method recovers more information than Meyer’s attack, totaling 16 bits. The second step is the same as Meyer’s. In the third and fourth steps, we perform a more accurate CPA using the additional information obtained in the first step.
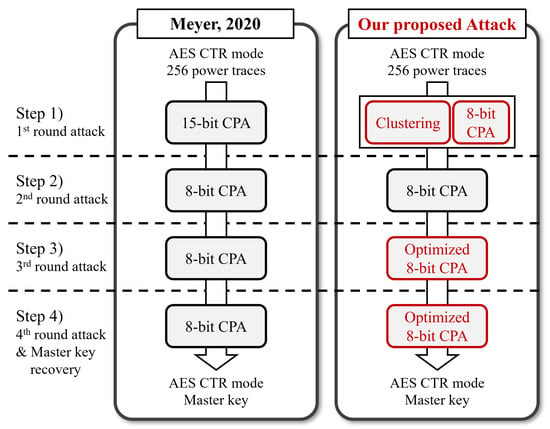
Figure 1.
Summary of Meyer’s attack [27] and the proposed attack process.
We apply the proposed and Mayer’s attacks on the Atmel XMEGA128D4 processor environment and compare their success rates. In addition, we compare the attacks at various noise levels by introducing artificial noise. The results demonstrate that the first step of the proposed attack exhibits a higher success rate than Mayer’s attack at all noise levels, particularly at high noise levels, with a success rate difference of up to 50%. Furthermore, the computational complexity of the first phase of our analysis is 128 times lower. In steps 3 and 4 of the attacks, the CPA accuracy of the proposed attack is approximately 1.18 times higher than that of Meyer’s attack.
1.2. Organization
The remainder of the paper is organized as follows. Section 2 defines the notations used in this paper and provides relevant background information, including the AES CTR mode, the CPA process, and the clustering algorithm. Section 3 summarizes Meyer’s attack. Section 4 proposes a novel attack on the AES CTR mode. Section 5 demonstrates the first step of the proposed attack on the Atmel XMEGA128D4 processor, and Section 6 compares the performance of the proposed attack with Meyer’s attack. Finally, the paper is concluded in Section 7, including a brief discussion of countermeasures.
2. Preliminaries
2.1. AES CTR Mode
AES is a 128-bit block cipher that uses a substitution-permutation network structure [33]. It offers different versions, e.g., AES-128, AES-192, and AES-256, based on the master key length. The number of rounds for AES-128, AES-192, and AES-256 is 10, 12, and 14, respectively. The AES round comprises four functions, i.e., AddRoundKeys, SubBytes, ShiftRows, and MixColumns functions.
The CTR mode is a mode of operation for the encryption and decryption of multiple blocks through a block cipher [34]. The CTR mode uses an initial nonce, and each -th block is encrypted using the exclusive or (XOR) operation with the block cipher encryption result of . Figure 2 shows the AES CTR mode of operation when the input block length is , and Figure 3 shows the AES encryption input in the CTR mode, where the black cell represents a byte that changes at each 256 AES input block in the CTR mode, and the gray cell represents a byte that toggles at most once. In the 256-block CTR mode encryption, the AES encryption inputs are expressed as follows:
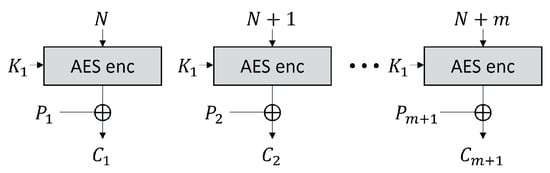
Figure 2.
AES CTR mode of operation.
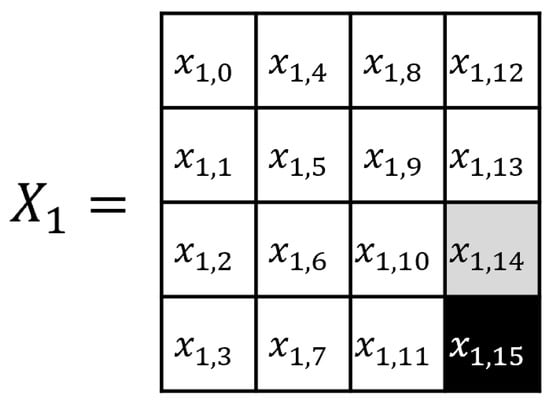
Figure 3.
AES input state in the CTR mode.
The CTR mode characteristics enable it to recover secret keys using only power traces [26]. In addition, as Meyer stated [27], attacking the CTR mode without input and output information enables the SCA scenario against the CTR DRBG.
2.2. Correlation Power Analysis
CPA is an SCA technique that recovers fixed secret values using power traces generated by the fixed secret and variable known values [12]. We first calculate the hypothetical power consumption sequence using a fixed secret value k and a variable known values. Then, we calculate the PCC between the hypothetical power consumption sequence and the actual power consumption sequence A. The formula for the PCC between A and is given as follows, where cov is the covariance and is the standard deviation of X:
In CPA, we use the absolute value of PCC for each guessed fixed secret k. We expect the highest absolute value of the PCC for the correct guessing value .
We use as a performance indicator for CPA. Here, represents the value obtained by dividing the PCC of the correct guess by the highest PCC obtained with incorrect guesses. A value greater than 1.0 indicates a successful CPA, and a higher value indicates better CPA analysis performance. The computational complexity of the CPA is determined by multiplying the number of traces, the number of points in the power trace, and the number of cases of fixed secret values.
2.3. Clustering Algorithm
Clustering, which is an unsupervised learning algorithm, groups a dataset with similar features. Figure 4 shows a simple example, where data with similar features are clustered into red and blue groups. In the power analysis, the data correspond to a power trace, and each feature represents the power consumption at different points. The clustering results of the power traces can be used to recover the secret information. Previous studies have explored SCA using clustering techniques [17,18,19].
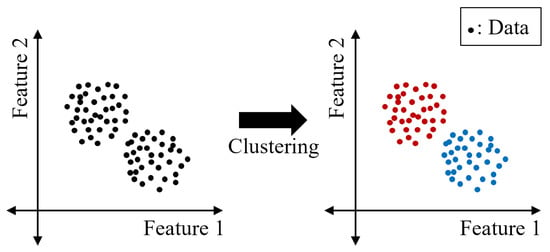
Figure 4.
Clustering example.
The widely used K-means clustering algorithm iteratively updates the means and sets the number of clusters and iterations. In this study, we employ the K-means clustering algorithm for clustering. Algorithm 1 shows the pseudocode of the K-means clustering algorithm. The computational complexity of K-means clustering is determined by multiplying the number of clusters U, iterations I, data T, and the data dimensions of the . In power analysis using K-means clustering, the number of data equal the number of the power traces, and the data dimensions equal the number of points in the power trace.
| Algorithm 1 k-means clustering algorithm |
| Input: data {}, number of clusters U, iteration I |
Output: centroid {}, cluster {}
|
3. Previous Power Analysis on AES CTR Mode
In the following, we briefly explain Meyer’s power analysis on the AES CTR mode [27]. Meyer’s attack comprises four steps and uses 256 power traces generated during the encryption of each block in the AES CTR mode. In step 1, Meyer recovered 1 byte of the first round S-Box output using a 15-bit guessing CPA. In step 2, she recovered 4 bytes of the second round S-Box outputs using an 8-bit guessing CPA based on the byte recovered in step 1. Similarly, in step 3, she recovered all third-round S-Box outputs using the 8-bit guessing CPA. Finally, in step 4, she recovered all fourth-round keys. Subsequently, she recovered the master key of the AES using the fourth-round keys.
3.1. Attack Step 1
In step 1, we focus on the black cell in Figure 5. Here, is expressed as follows:
Let and , where denotes the most significant bit, and denotes the other 7 bits. In addition, let . Then, can be expressed as follows:
Thus, for each of the 256 traces can be recovered using 15-bit guessing CPA.
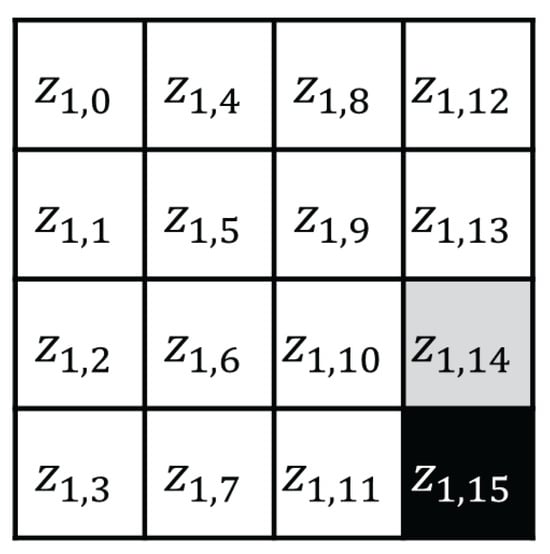
Figure 5.
AES first SubBytes output state.
3.2. Attack Step 2
In step 2 of the attack, we recover , which are the black cells in the right of Figure 6. Here, is expressed as follows.
Note that is a known variable value (recovered in step 1), and is an unknown constant value. Thus, can be recovered using 8-bit guessing CPA, and can be recovered in a similar manner.
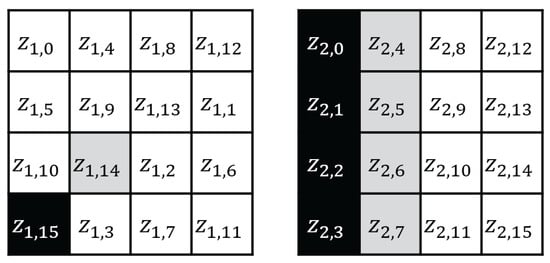
Figure 6.
AES first ShiftRows and second SubBytes output state.
3.3. Attack Step 3
In attack step 3, we recover . as follows:
Here, is a known value (recovered in step 2), and is an unknown and nonconstant value (toggled by the value). In this case, is affected by the black and gray cells (, respectively) (Figure 7) and is toggled when counter carry occurs in the addition of mod 256. Meyer only recovered 7 bits of in step 1; thus, the index of the block in which is toggled is unknown. This is an obstacle to calculating the guessing value of . In 256 traces, the values of are divided into two different fixed values, and then the value of is affected by the different fixed values. Therefore, the accuracy performance of the CPA, which analyzes 256 traces by guessing the fixed value, is reduced.
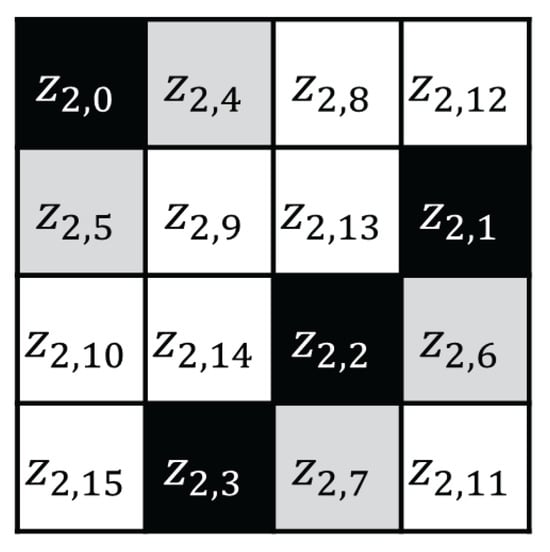
Figure 7.
AES second ShiftRows output state.
Meyer discussed three cases, i.e., the best, average, and worst cases, for step 3 CPA. The best case does not involve the toggle (i.e., ), resulting in no interference to the CPA. The worst case occurs when the toggle occurs in approximately 128 traces, i.e., when . In this case, approximately half of the traces contribute noise to the CPA, thereby causing a significant reduction in its success rate. Meyer also proposed a CPA method that uses either the front 128 or back 128 traces to avoid a significant reduction in the CPA performance. However, CPA using 128 traces results in a reduced success rate, particularly in the best or average cases. In other words, each CPA method proposed by Meyer results in reduced CPA performance in some instances. can be recovered using 8-bit guessing CPA using the 256-trace or 128-trace.
3.4. Attack Step 4
In step 4, we recover the and AES master keys. can be calculated using recovered in step 3. can then be recovered using 8-bit guessing CPA 16 times. Here, similar to step 3, the CPA accuracy performance decreases. Finally, the master key of the AES can be calculated using .
4. Our Proposed Power Analysis on AES CTR Mode
This section proposes the power analysis for the AES CTR mode. The proposed attack comprises four steps and uses 256 power traces, the same as Meyer’s attack. However, in contrast to Meyer’s approach, we introduce a clustering algorithm in step 1 to recover more information more accurately. In step 1, while Meyer recovered 7 bits of the input and key, we recover the 1-byte input by clustering, and then the 1-byte key is recovered through 8-bit guessing CPA. Note that step 2 remains the same as in Meyer’s attack. Finally, we improve the 8-bit guessing CPA in steps 3 and 4 using the additional information obtained in step 1.
4.1. Attack Step 1
The first step is crucial in both Meyer’s attack and the proposed attack. If the first step fails, all subsequent steps of the attack will also fail. In addition, the first step is the most complex in terms of the computation and the attack complexity.
Rather than using 15-bit guessing CPA, we perform a single clustering attack and a single 8-bit guessing CPA. The clustering process divides the 256 power traces into two clusters and recovers using the results. We then guess the 8-bit and perform CPA on to recover (Equation (4)). This result recovers rather than . Theoretically, the 15-bit guessing CPA has a lower attack success rate than the 8-bit guessing CPA; thus, the success rate of the clustering attack is very important in the proposed attack. We describe the clustering attack method and several ways to improve the attack success rate.
Here, we focus on the byte of the AES state being toggled (i.e., the gray cells in the AES state figures). We defined the toggled byte as the byte to be toggled when it causes carry in , i.e., the gray cell in the AES state figures. The toggled bytes contain , and others. Figure 8 shows an example of the 256-block encryption of the AES CTR mode when and . We use the difference in the power consumptions of the toggled byte. In Figure 8, the forward 173 blocks have different power consumptions with the backward 83 blocks in computing the toggled byte. If we can classify the power consumption into two groups, we can recover the value, and the clustering algorithm is one of the solutions that classify the power consumption into two groups. Here, the clustering algorithm is used to determine the power consumption of the toggled bytes (i.e., the gray cells in the AES state figures). Note that the type of analysis result varies depending on the following two cases.
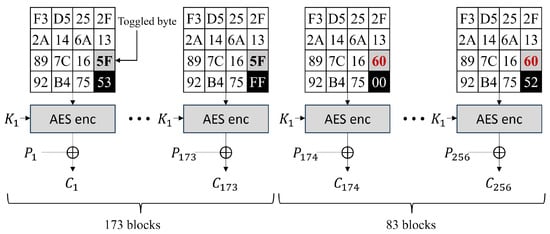
Figure 8.
Example of 256-block encryption and toggled byte of CTR mode.
Case 1.
The toggled bytes remain constant in the front and back traces. Therefore, we predict that the power consumption while operating the toggled byte of the front traces and the back traces will exhibit significantly different distributions. Here, if we can successfully cluster the front and back traces, then backwards, we can recover using the clustering results.
Case 2.
Note that the toggled bytes are constant in all 256 traces; thus, the power consumption while operating the toggled byte of all 256 traces will exhibit the same distributions. Therefore, applying a clustering algorithm will not yield clear clustering results. However, backwards, we can know that through the unclear clustering results.
In addition, we can recover using the clustering results of the 256 traces. However, if the value of is close to 0 or 255, the clustering accuracy may be affected by the number of data in each set, and this limitation can be overcome using an optimized clustering algorithm or data augmentation technique, e.g., adding copies of the 0th and 255th power traces to the dataset. The data in this attack possess characteristics that can optimize the clustering process. First, the 256 traces are always clustered into two classes. Second, consecutive data points fall into the same cluster before and after the toggle point. Third, the toggled bytes exist within the AES traces at multiple points in time. Note that the first and second characteristics simplify the clustering problem and imply the existence of a more optimized clustering algorithm for this problem. The third characteristic allows securing more data features, which means that the clustering success rate can be improved through multiple feature information even in a higher noise environment. Thus, the attack can be improved by applying a clustering algorithm that uses these data characteristics effectively. In the experiments conducted in this study (Section 5), we employed power traces for part of the toggled bytes and non-modified K-means clustering, which outperformed both the 8-bit and 15-bit guessing CPA.
Next, with the knowledge of through , we can recover , using 8-bit guessing CPA. The difference from Meyer’s attack is that we know the exact toggle point, i.e., , and this advantage is exploited in the CPA of attack steps 3 and 4.
4.2. Attack Step 2
In step 1, we recovered additional information about toggled bytes (gray cells). However, the target values of step 2 are not related to the toggled bytes. Therefore, we follow the same attack described in Section 3.2.
4.3. Attack Step 3
is expressed in Equation (7). Here, we have recovered all 8 bits of in step 1, so we know exactly when is toggled, unlike Section 3.3. Thus, we can divide the 256 traces into two sets based on the value. We can prevent the degradation of CPA accuracy performance due to traces acting as noise mentioned in Section 3.3 by performing CPA on traces classified with the same value of . Although we still do not know the value of , we optimize the CPA by using the maximum number of traces for which is fixed, thereby minimizing the accuracy degradation.
Meyer’s approach performs well with 256-trace CPA in the best case () and with 128-trace CPA in the worst case (). On the other hand, our optimized CPA method always uses the maximum number of traces about a fixed value, so it is optimized for all cases. For example, when , Meyer’s 256-trace CPA has 64 traces acting as noise. However, in the proposed attack, we can perform optimized CPA without any traces acting as noise in CPA by using only 192 traces with fixed as the same value. Similarly, we can recover via the optimized 8-bit guessing CPA.
4.4. Attack Step 4
In step 4, we perform 8-bit guessing CPA on to recover and the AES master key. As discussed in Section 3.4, the CPA target is calculated from ; thus, the same CPA accuracy degradation as in step 3 occurs. As described in Section 4.3, we can perform the optimized CPA using the maximum number of traces in which is fixed.
5. Experimental Results for the Proposed Clustering Attack
This section describes the experimental results for the clustering attack of the proposed attack first step.
Figure 9 shows the experimental setup used to measure the power traces from the Atmel XMEGA target using ChipWhisperer-Lite. Table 1 shows the details of the experimental setup. We selected this setting with a low noise level and added artificial noise to evaluate the attack success rate at various noise levels. This section discusses the attacks performed at the default noise level, and Section 6 discusses the attacks performed at various noise levels. We experimentally verified the effectiveness of the proposed clustering attack described in Section 4.1. The attack was performed by collecting power consumption while encrypting 256 blocks using the AES-128 CTR mode on the Atmel XMEGA128D4 processor.
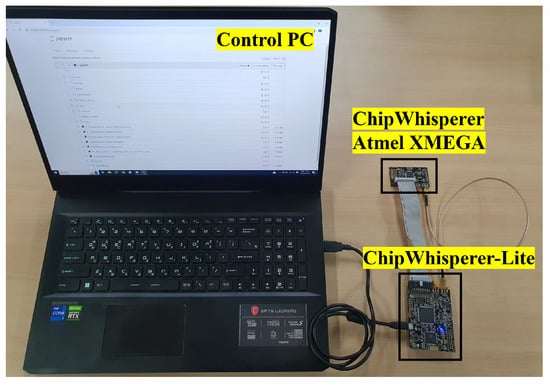
Figure 9.
Experimental setup.

Table 1.
Experimental environment.
Figure 10 shows the power trace during AES execution from the first to the fifth round. As discussed in Section 4.1, the power consumption suitable for clustering is the part where the toggled byte is manipulated. The first and second rounds involve the toggled bytes in the AddRoundKey, SubBytes, ShiftRows, and Mixcolumns operations. In these experiments, we used a power consumption range of 4400–4500 points, which is part of the second round of the SubBytes operation. Here, we employed the K-means clustering algorithm with two clusters and one iteration.
Figure 10.
Power trace of AES for five rounds.
Figure 11 shows the clustering results for 256 traces with , where the x-axis represents the trace index, and the y-axis represents the corresponding cluster number assigned to each trace. The graph shows a toggled point at the 128th trace. Thus, we can recover as .
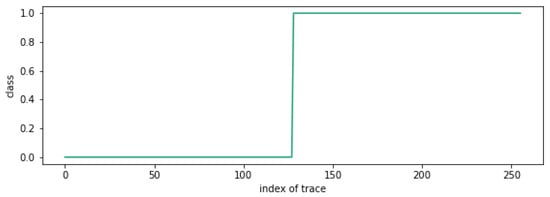
Figure 11.
Clustering attack result when .
Figure 12 shows the clustering results for 256 traces with . As can be seen, the clustering result is unclear. Therefore, we can recover as .
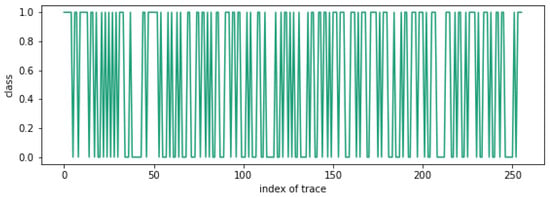
Figure 12.
Clustering attack result when .
6. Comparison of Previous and Proposed Attacks
In this section, we compare the proposed attack with Meyer’s attack. Regarding step 1 of the attack, we compare the attack success rate based on the noise level and computational complexity. In addition, we compare the CPA accuracy performance for steps 3 and 4 of the attack.
6.1. Comparison of Attack Step 1
6.1.1. Attack Success Rate
Gaussian noise with an average of 0 was added to the experimental data described in Section 5. These data, were then used as the experimental data to compare the attack success rate based on the noise level. Here, Gaussian noise with a random multiple of the sample standard deviation was added for each point. Figure 13 shows a power trace with the added Gaussian noise, where the noise level is set to nine times the standard deviation of the sample for each time point derived from the power trace discussed in Section 5.
Figure 13.
Power trace of AES for five rounds with inserted Gaussian noise.
We selected and defined that the clustering attack was successful when the class was first changed at the index of 128. We also defined the CPA as successful when the correct guess had the highest correlation coefficient. We determined that step 1 of the proposed attack was successful when the clustering attack and 8-bit CPA were both successful.
To compare the success rate of step 1 of the proposed attack, we generated 256 power traces for each noise level, repeated this process ten times, and conducted an attack on each dataset. For the clustering attack, we used the power trace of the range of 4400–4500 points, which corresponds to the SubBytes operation in the second round. For CPA, we used a data point range of 1000–3200, encompassing the SubBytes to Mixcolumns operations in the first round.
Figure 14 compares the success rate of step 1 of each attack according to the noise level. The noise level indicates the number of times the standard deviation of the inserted Gaussian noise was equal to that of the sample of the existing power trace. As can be seen, Meyer’s attack exhibits a significant decline at noise level 6, and its success rate is 0% at noise level 10. However, the success rate of the proposed attack decreases at noise level 7, and its success rate is 20% at noise level 10. In particular, the success rate of the proposed attack in step 1 is higher than that of Meyer’s attack by a maximum of 50% at high noise levels (i.e., noise levels 7 and 8).
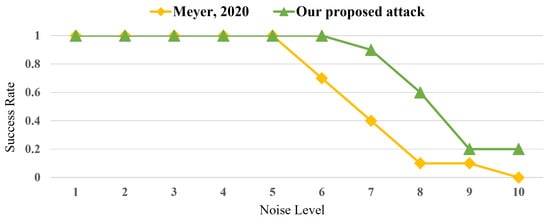
Figure 14.
Success rate result of step 1 of Meyer’s attack [27] and the proposed attack according to the noise level.
6.1.2. Attack Complexity
Step 1 of Meyer’s attack performs a 15-bit guessing CPA and has the highest computational complexity among all steps. In contrast, step 1 of the proposed attack performs clustering and 8-bit guessing CPA. The computational complexity of the CPA and K-means clustering algorithm are described in Section 2.2 and Section 2.3, respectively. The number of cases of the fixed secret values is in the n-bit guessing CPA, and the number of clusters U is fixed to 2 in this attack. In addition, if the number of traces is T, the number of points is P, and the number of clustering iterations is I, the computational complexity of step 1 of each attack can be determined as follows:
If the number of iterations is set to 1, as in the experiments described in Section 5 and Section 6.1.1, the computational complexity of step 1 in the proposed attack is approximately 1/128 that of Meyer’s attack.
6.2. Comparison on Steps 3 and 4 of the Attack
Meyer proposed two types of CPA using 128 or all 256 traces [27]; however, in contrast, the proposed attack enables the recovery of all bits of in step 1, which allows us to perform CPA using the maximum number of traces where the unknown value is fixed.
Figure 15 compares the , which represents the CPA performance, between Meyer’s and the proposed CPA in steps 3 and 4, using the experimental environment described in Table 1. Here, we performed CPA and computed the for values of 0, 64, 128, and 192. Note that our optimized CPA employs the maximum number of traces where the unknown value is fixed; thus, our CPA exhibited the highest in all cases. On average, the of the CPA using 256 traces was 2.03, that of CPA using 128 traces was 1.98, and the optimized CPA had a value of 2.37. As a result, the optimized CPA demonstrated an average performance improvement of 18.5% compared to the method proposed by Meyer.
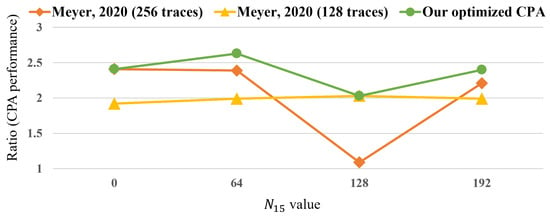
Figure 15.
Performance of Meyer’s CPA [27] and the optimized CPA in steps 3 and 4 of the attack.
7. Conclusions
This paper has proposed an improved power analysis method for the AES CTR mode based on Meyer’s previous approach. In addition, we have demonstrated the effectiveness of the proposed attack method based on actual experiments. In a high-noise experimental environment, we found that the proposed attack outperforms Meyer’s attack, achieving up to a 50% higher success rate in the first stage, and the computational complexity was reduced. The CPA performance improved by approximately 18.5% in steps 3 and 4 of the attack. In addition, the clustering process in the proposed attack can be optimized further using the characteristics of the AES CTR mode. These results demonstrate that the proposed attack extended the target device to more noisy environments than previous attacks, thereby increasing the threat of SCAs on the CTR DRBG.
As described in the literature [27], these attacks (the proposed attack and Meyer’s attack) were designed to target the CTR mode, which uses addition as a counter and thus can not be applied to the CTR mode using a linear-feedback shift register (LFSR) as a counter. In addition, the limitation of the request size of CTR DRBG can provide resistance for these attacks by reducing the number of traces for the attack. However, these attacks arise from the relationship between each counter block; thus, the CTR mode with an LFSR counter and the limitation of the request size could still be susceptible to as-yet undiscovered attacks. Conservatively, we expect that it would be more effective from a security perspective to employ a counter that makes it difficult to guess the relevance of each counter block, e.g., a hash function.
In addition, attacks targeting hardware implementations, such as those on FPGAs or ASICs, remain an open area for future research. Both Meyer’s and our proposed attacks operate with only 256 power traces in a non-profiled setting, requiring the success of all four steps to fully recover secret information. In practice, however, hardware implementations (e.g., FPGAs, ASICs) typically exhibit higher noise levels than MCUs, making such attacks more difficult to succeed. Therefore, to perform practical attacks on hardware implementations of CTR DRBG, future research should explore conditions that allow for profiling or access to a larger number of power traces, as demonstrated in Tienteu’s work. Additionally, since hardware implementations tend to conform more closely to the Hamming distance leakage model, adapting the attack logic to accommodate this characteristic is also expected to be necessary.
Author Contributions
J.H.: Conceptualization, methodology, software, validation, formal analysis, investigation, resources, data curation, writing—original draft preparation, writing—review and editing, visualization, project administration; D.-G.H.: Writing—review and editing, supervision, funding acquisition. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Korea Research Institute for defense Technology planning and advancement (KRIT)—Grant funded by Defense Acquisition Program Administration (DAPA) (KRIT-CT-23-005).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original traces and noisy traces used in our demonstrations are available from the following link: https://drive.google.com/file/d/1O6vo7QFC13HIWwCKl0ss0VE6ksCNgzwN/view (accessed on 28 May 2025).
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| SCA | Side-Channel Attack |
| CPA | Correlation Power Analysis |
| CTR | Counter |
| DRBG | Deterministic Random Bit Generator |
Notations
The notations used in this paper are defined as follows:
| ⊕ | Exclusive OR operator |
| ≪ | Shift operator in 8-bit |
| · | AES field multiplication operator |
| AES S-Box function | |
| i | Round index |
| j | Byte index |
| i-th round input 16 bytes | |
| i-th round input j-th byte | |
| i-th round key 16 bytes | |
| i-th round key j-th byte | |
| i-th round SubBytes output 16 bytes | |
| i-th round SubBytes output j-th byte | |
| N | Nonce value 16 bytes of CTR mode |
| Nonce value j-th byte of CTR mode | |
| Counter value of CTR mode |
References
- Kocher, P.C.; Jaffe, J.; Jun, B. Differential Power Analysis. In Proceedings of the Advances in Cryptology—CRYPTO ’99, 19th Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; Wiener, M.J., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 1999; Volume 1666, pp. 388–397. [Google Scholar] [CrossRef]
- Moradi, A.; Mischke, O.; Paar, C. One Attack to Rule Them All: Collision Timing Attack versus 42 AES ASIC Cores. IEEE Trans. Comput. 2013, 62, 1786–1798. [Google Scholar] [CrossRef]
- Zhang, P.; Den, G.; Zhao, Q.; Chen, K. Em frequency domain correlation analysis on cipher chips. In Proceedings of the 2009 First International Conference on Information Science and Engineering, Nanjing, China, 26–28 December 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 1729–1732. [Google Scholar]
- Krämer, J.; Nedospasov, D.; Schlösser, A.; Seifert, J. Differential Photonic Emission Analysis. In Proceedings of the Constructive Side-Channel Analysis and Secure Design—4th International Workshop, COSADE 2013, Paris, France, 6–8 March 2013; Revised Selected Papers. Prouff, E., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2013; Volume 7864, pp. 1–16. [Google Scholar] [CrossRef]
- Blömer, J.; Seifert, J. Fault Based Cryptanalysis of the Advanced Encryption Standard (AES). In Proceedings of the Financial Cryptography, 7th International Conference, FC 2003, Guadeloupe, French West Indies, 27–30 January 2003; Revised Papers. Wright, R.N., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2003; Volume 2742, pp. 162–181. [Google Scholar] [CrossRef]
- Moabalobelo, P.T. Differential Power Analysis of an AES Software Implementation. Master’s Thesis, University of Johannesburg, Johannesburg, South Africa, 2013. [Google Scholar]
- Aigner, M.; Oswald, E. Power Analysis Tutorial. Technical Report, TU Graz. 2000. Available online: https://cs.ru.nl/E.Poll/hw/dpa_tutorial.pdf (accessed on 27 May 2025).
- Mangard, S.; Oswald, E.; Popp, T. Power Analysis Attacks—Revealing the Secrets of Smart Cards; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Smith, K.J., Jr. Methodologies for Power Analysis Attacks on Hardware Implementations of AES; Rochester Institute of Technology: Rochester, NY, USA, 2009. [Google Scholar]
- Petrvalsky, M.; Drutarovsky, M.; Varchola, M. Differential power analysis of advanced encryption standard on accelerated 8051 processor. In Proceedings of the 2013 23rd International Conference Radioelektronika (RADIOELEKTRONIKA), Pardubice, Czech Republic, 16–17 April 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 334–339. [Google Scholar]
- Kocher, P.C. Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems. In Proceedings of the Advances in Cryptology—CRYPTO ’96, 16th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 1996; Koblitz, N., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 1996; Volume 1109, pp. 104–113. [Google Scholar] [CrossRef]
- Brier, E.; Clavier, C.; Olivier, F. Correlation Power Analysis with a Leakage Model. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2004: 6th International Workshop, Cambridge, MA, USA, 11–13 August 2004; Joye, M., Quisquater, J., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2004; Volume 3156, pp. 16–29. [Google Scholar] [CrossRef]
- Gierlichs, B.; Batina, L.; Tuyls, P.; Preneel, B. Mutual Information Analysis. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2008, 10th International Workshop, Washington, DC, USA, 10–13 August 2008; Oswald, E., Rohatgi, P., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2008; Volume 5154, pp. 426–442. [Google Scholar] [CrossRef]
- Timon, B. Non-Profiled Deep Learning-based Side-Channel attacks with Sensitivity Analysis. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 107–131. [Google Scholar] [CrossRef]
- Chari, S.; Rao, J.R.; Rohatgi, P. Template Attacks. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2002, 4th International Workshop, Redwood Shores, CA, USA, 13–15 August 2002; Revised Papers. Kaliski, B.S., Koç, ç.K., Paar, C., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2002; Volume 2523, pp. 13–28. [Google Scholar] [CrossRef]
- Zeman, V.; Martinasek, Z. Innovative Method of the Power Analysis. Radioengineering 2013, 22, 586–594. [Google Scholar]
- Batina, L.; Gierlichs, B.; Lemke-Rust, K. Differential cluster analysis. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Lausanne, Switzerland, 6–9 September 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 112–127. [Google Scholar]
- Nascimento, E.; Chmielewski, Ł. Applying horizontal clustering side-channel attacks on embedded ECC implementations. In Proceedings of the International Conference on Smart Card Research and Advanced Applications, Lugano, Switzerland, 13–15 November 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 213–231. [Google Scholar]
- Sim, B.Y.; Park, A.; Han, D.G. Chosen-ciphertext clustering attack on CRYSTALS-KYBER using the side-channel leakage of Barrett reduction. IEEE Internet Things J. 2022, 9, 21382–21397. [Google Scholar] [CrossRef]
- Mangard, S. A Simple Power-Analysis (SPA) Attack on Implementations of the AES Key Expansion. In Proceedings of the Information Security and Cryptology—ICISC 2002, 5th International Conference, Seoul, Republic of Korea, 28–29 November 2002; Revised Papers. Lee, P.J., Lim, C.H., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2002; Volume 2587, pp. 343–358. [Google Scholar] [CrossRef]
- Kocher, P.C.; Jaffe, J.; Jun, B.; Rohatgi, P. Introduction to differential power analysis. J. Cryptogr. Eng. 2011, 1, 5–27. [Google Scholar] [CrossRef]
- Belaïd, S.; Fouque, P.A.; Gérard, B. Side-Channel Analysis of Multiplications in GF (2128) Application to AES-GCM. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Kolkata, India, 10–14 December 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 306–325. [Google Scholar]
- Jayasinghe, D.; Ragel, R.G.; Ambrose, J.A.; Ignjatovic, A.; Parameswaran, S. Advanced modes in AES: Are they safe from power analysis based side channel attacks? In Proceedings of the 32nd IEEE International Conference on Computer Design, ICCD 2014, Seoull, Republic of Korea, 19–22 October 2014; IEEE Computer Society: Piscataway, NJ, USA, 2014; pp. 173–180. [Google Scholar] [CrossRef]
- Fahd, S.; Afzal, M.; Abbas, H.; Iqbal, M.M.W.; Waheed, S. Correlation power analysis of modes of encryption in AES and its countermeasures. Future Gener. Comput. Syst. 2018, 83, 496–509. [Google Scholar] [CrossRef]
- Ebina, K.; Ueno, R.; Homma, N. Side-Channel Analysis Against SecOC-Compliant AES-CMAC. IEEE Trans. Circuits Syst. II Express Briefs 2023, 70, 3772–3776. [Google Scholar] [CrossRef]
- Jaffe, J. A First-Order DPA Attack Against AES in Counter Mode with Unknown Initial Counter. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2007, 9th International Workshop, Vienna, Austria, 10–13 September 2007; Paillier, P., Verbauwhede, I., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2007; Volume 4727, pp. 1–13. [Google Scholar] [CrossRef]
- Meyer, L.D. Recovering the CTR_DRBG state in 256 traces. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2020, 2020, 37–65. [Google Scholar] [CrossRef]
- Tienteu, M.; Smith, E.; Santillan, E.M.; Kornegay, K.T.; Harvey, P.; Toutsop, O.; Yimer, T.; Morris, V.; Wandji, K. Template Attack Against AES in Counter Mode with Unknown Initial Counter. In Proceedings of the 13th IEEE Annual Computing and Communication Workshop and Conference, CCWC 2023, Las Vegas, NV, USA, 8–11 March 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 525–533. [Google Scholar] [CrossRef]
- Hayati, N.; Ramli, K.; Windarta, S.; Suryanegara, M. A Novel Secure Root Key Updating Scheme for LoRaWANs Based on CTR_AES DRBG 128. IEEE Access 2022, 10, 18807–18819. [Google Scholar] [CrossRef]
- Kim, Y.; Seo, S.C. Efficient Implementation of AES and CTR_DRBG on 8-Bit AVR-Based Sensor Nodes. IEEE Access 2021, 9, 30496–30510. [Google Scholar] [CrossRef]
- Kietzmann, P.; Schmidt, T.C.; Wählisch, M. A Guideline on Pseudorandom Number Generation (PRNG) in the IoT. ACM Comput. Surv. 2022, 54, 1–38. [Google Scholar] [CrossRef]
- Prada-Delgado, M.Á.; Baturone, I.; Dittmann, G.; Jelitto, J.; Kind, A. PUF-derived IoT identities in a zero-knowledge protocol for blockchain. Internet Things 2020, 9, 100057. [Google Scholar] [CrossRef]
- NIST FIPS PUB 197; Advanced Encryption Standard. NIST: Gaithersburg, MD, USA, 2001.
- Dworkin, M.J. Sp 800-38a 2001 Edition. Recommendation for Block Cipher Modes of Operation: Methods and Techniques; NIST: Gaithersburg, MD, USA, 2001. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).