UAV-Based Secure Data Communication: Multilevel Authentication Perspective
Abstract
1. Introduction
- Considering that the erasing cipher is not readily cracked, the reliance on a protective mechanism with high computational security is a major consideration.
- Enormous datasets can be securely encrypted and decrypted by UAVs with less computational power.
- The third issue is that the servers store sensitive IoUAV data, making them easier for other hackers to access.
Novel Contributions
- A lightweight user authentication approach, featuring a layered authentication technique, was created as a significant contribution. This method was employed to establish a secure connection between the UAVs. The suggested approach utilizes encryption and bitwise XOR operations to ensure secure communication.
- There are four modules to evaluate security, including the pre-deployment module, user registration module, login module, and authentication module.
- Several layers of authentication are used. The first analyzer is for the server to verify the user’s identity before approving any communications. The next layer is to modify the hashing algorithm to make it resistant to different types of attacks. To obtain data from the UAV, the suggested approach made use of several authentication mechanisms, which contribute to secure communication with little latency, high throughput, and low packet loss.
- A latency of 0.099 s, throughput of 62.855 bps, and packet loss of 2.52012 s were registered as the performance metrics for the suggested approach.
2. Literature Review
3. Proposed Model
3.1. Proposed Strategy
3.1.1. Verification Process
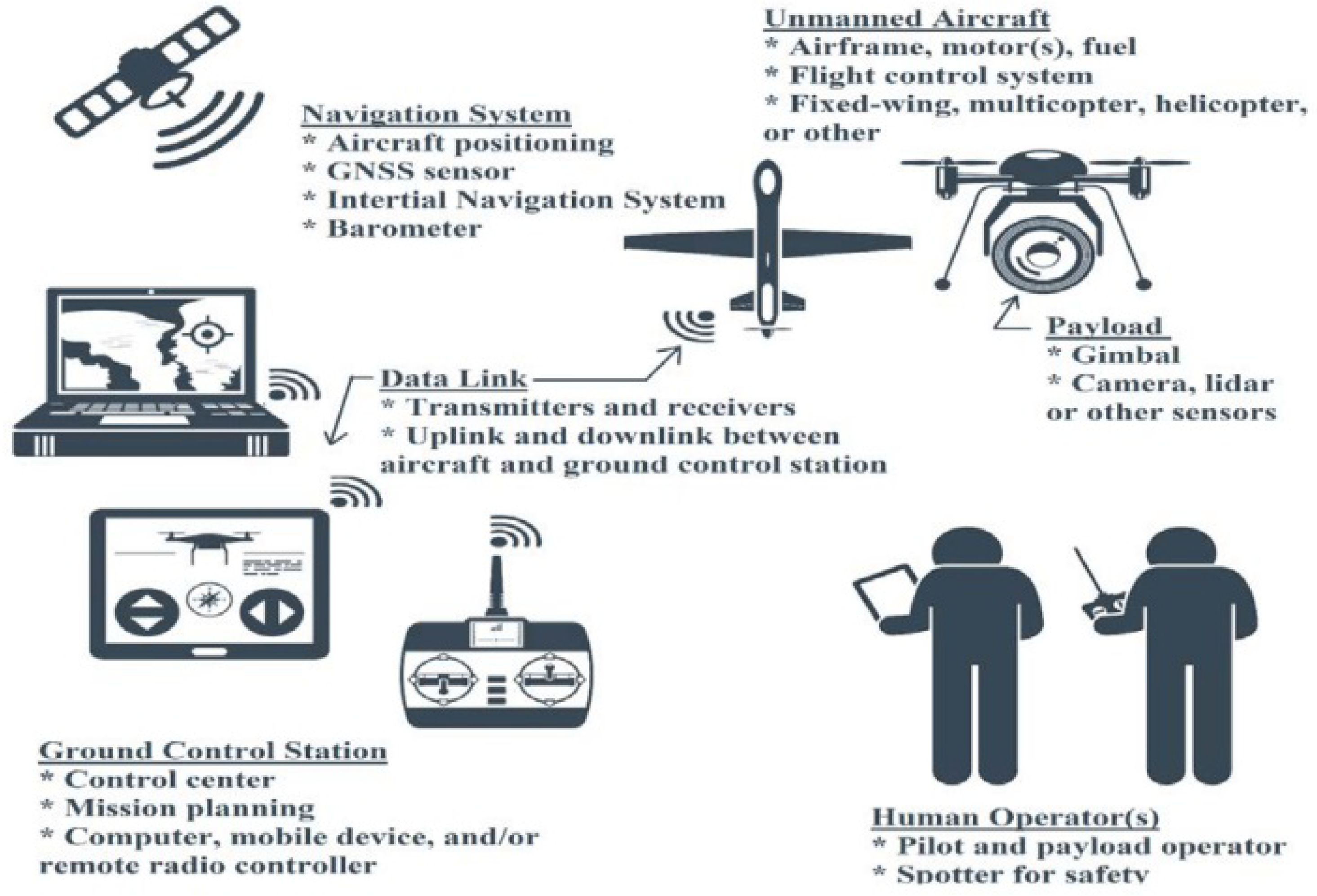
- The UAV system includes data about the UAVs that are updated in real time. Through web-related services, client apps can access the UAVs’ resources.
- Data about the individuals who will be granted access to the UAVs according to their permissions are stored in the user module.
- One of the most essential building blocks for starting conversations in a network is the communication block.
- The user authenticates the UAV by transmitting their identity, and the server verifies it.
- The login procedure is activated to reply to the service requests made by the user.
- To confirm the user, authentication is carried out between the user and the UAV.
- After user authentication, data about the user’s location are sent to the service engine.
- The service processor then uses the database to retrieve more information about the service.
| Algorithm 1 Registration and Verification Procedure |
|
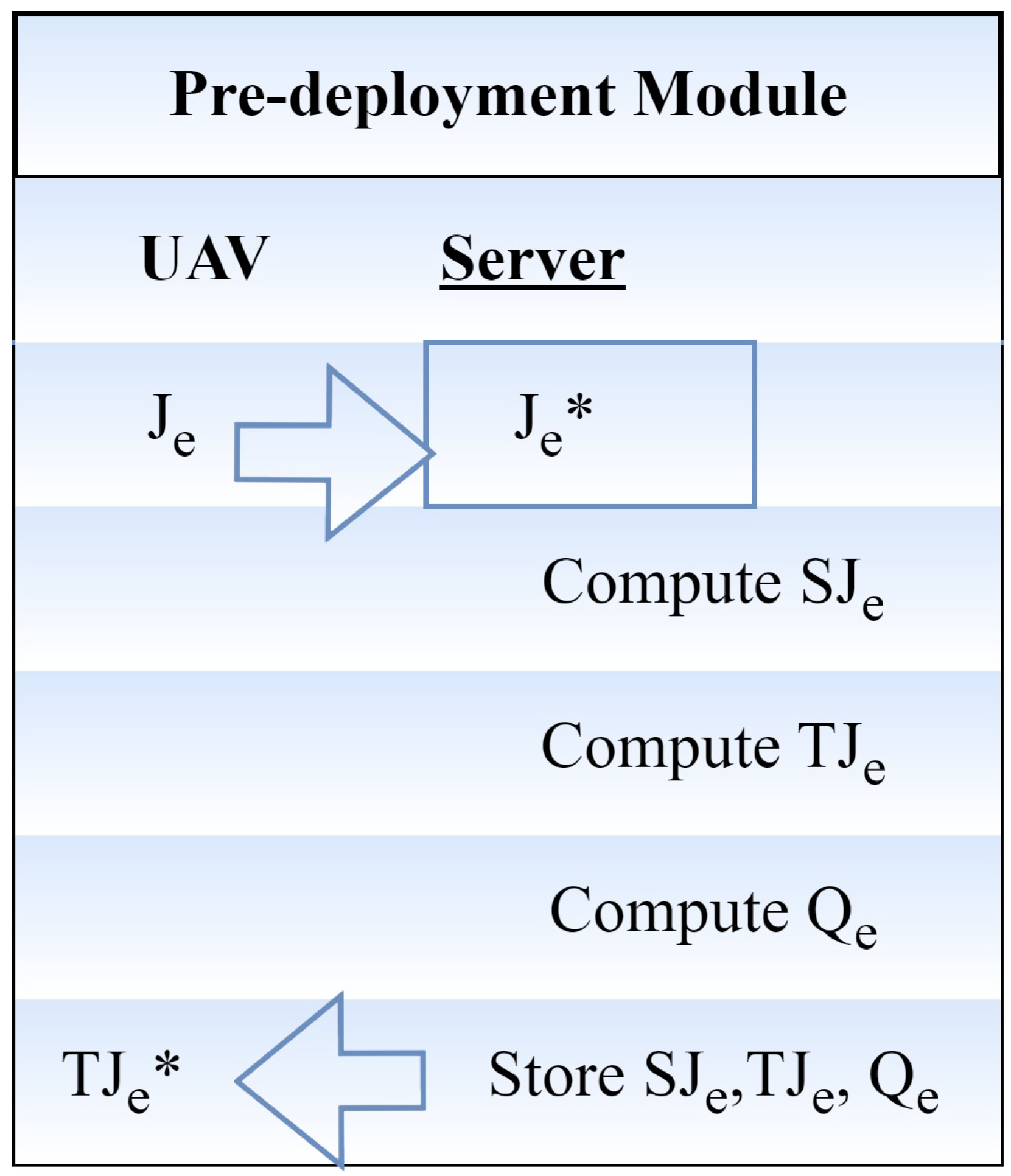
3.1.2. Initial Deployment Module
3.1.3. Registration Module
- The user selects an identity (Jv) and securely sends a message to the server (A) to request registration. When the registration request is received, the pseudo-identity of the A computer user is described asJv represents the received identity at the server side, Sv is the registration timestamp created by the user v, q is a master key, and n is the secret message.when the user’s private key is represented by qv.
- After securely sending the registration reply message to the user, server A saves the SJv, TJv, and Qv in the UAV database. After the server generates the registration reply message, the user selects password B and enters biometric Cv at the sensor. The fuzzy extractor approach is used to complete biometric verification. The fuzzy extractor method makes use of a probabilistic generation function called Gen. This function accepts the user’s biometrics Cv as input and outputs the biometric secret key of length v bits as j → 0, 1. The public parameter, H(Cv), is defined as Gen(). The information is then saved in the server’s memory. The user can still not use the server’s services, even if they have registered with the server unless the server authorizes them. The authentication procedure informs the server’s choice of the user’s permission to log.
3.1.4. Login Module
3.1.5. Authentication Module
- Connectivity: UAVs may operate in areas with limited or no network connectivity, which can make it challenging to implement traditional MFA methods that rely on real-time communication with authentication servers.
- Payload limitations: UAVs have payload limitations, which may restrict the types of hardware or software that can be carried onboard for MFA purposes.
- Environmental factors: Environmental conditions such as extreme temperatures, high altitudes, and electromagnetic interference can impact the reliability and functionality of MFA components onboard UAVs.
- Power constraints: UAVs have limited power sources, and running MFA processes may consume additional power, affecting the overall flight time and mission duration.
4. Experimental Validation
4.1. Simulation Attributes
- Latency: “Latency” refers to the overall amount of time it takes to broadcast the information. The delay is estimated in terms of computing time, energy usage, and packet loss.
- Throughput: It describes the amount of data sent across a network at any given moment. Several variables compromise the communication system’s throughput. These include the limitations of the underlying analog physical media, the available computational capacity of the system’s components, and the end-to-end users. When various protocol overheads are taken into account, the data transfer rate falls short of the maximum throughput that may be achieved. Mathematically, consider the following:
- Loss of Packet: Packet loss happens when data packets transmitted via a network do not arrive at their intended recipient. This might be because of transmission faults. Mathematically, consider the following:
- Energy Consumption: It is the quantity of power that is used up to complete a specific job. To achieve energy efficiency, the energy consumption should be kept to a minimum.
- Computation Delay: The amount of time it takes to finish a whole operation is directly proportional to the number of rules that need to be applied.
4.2. Comparative Analysis
4.2.1. One-Hundred-Fifty-Node Comparative Analysis
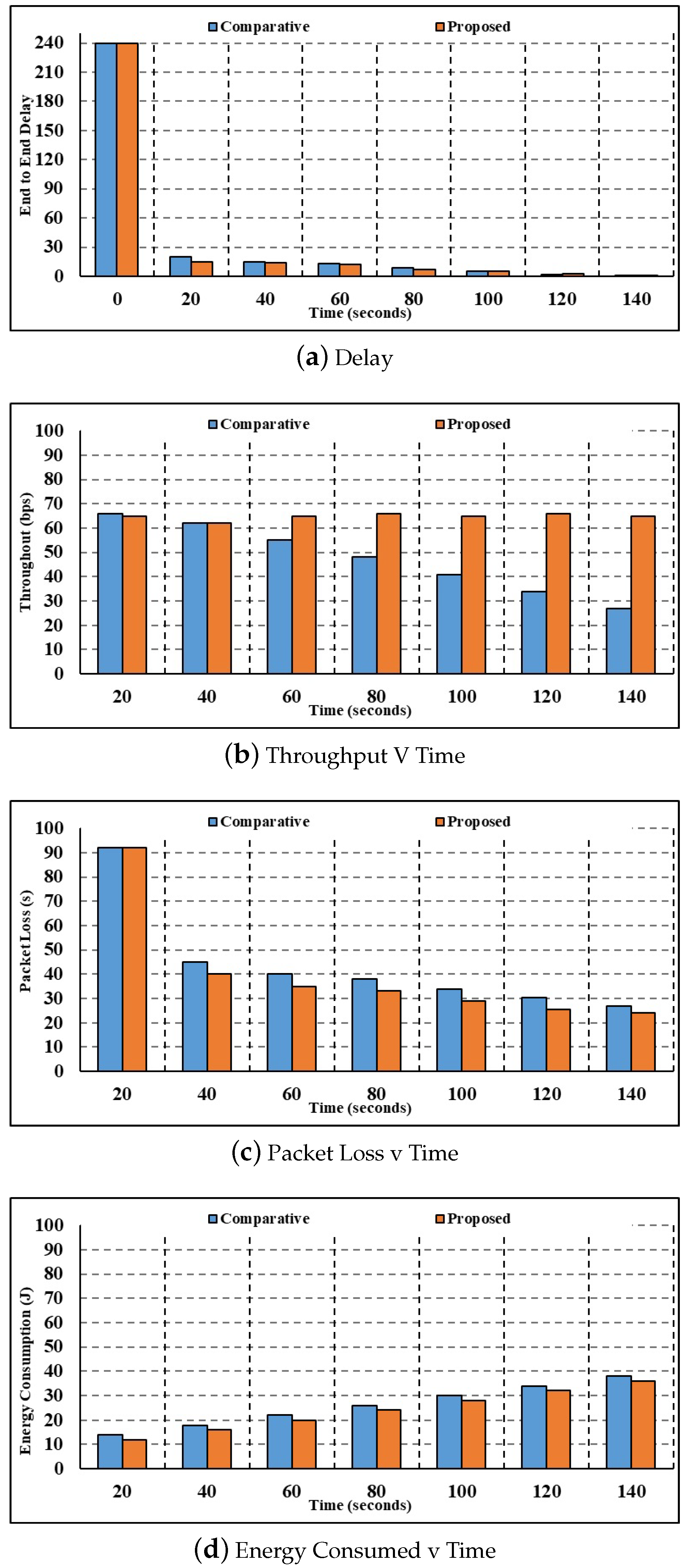
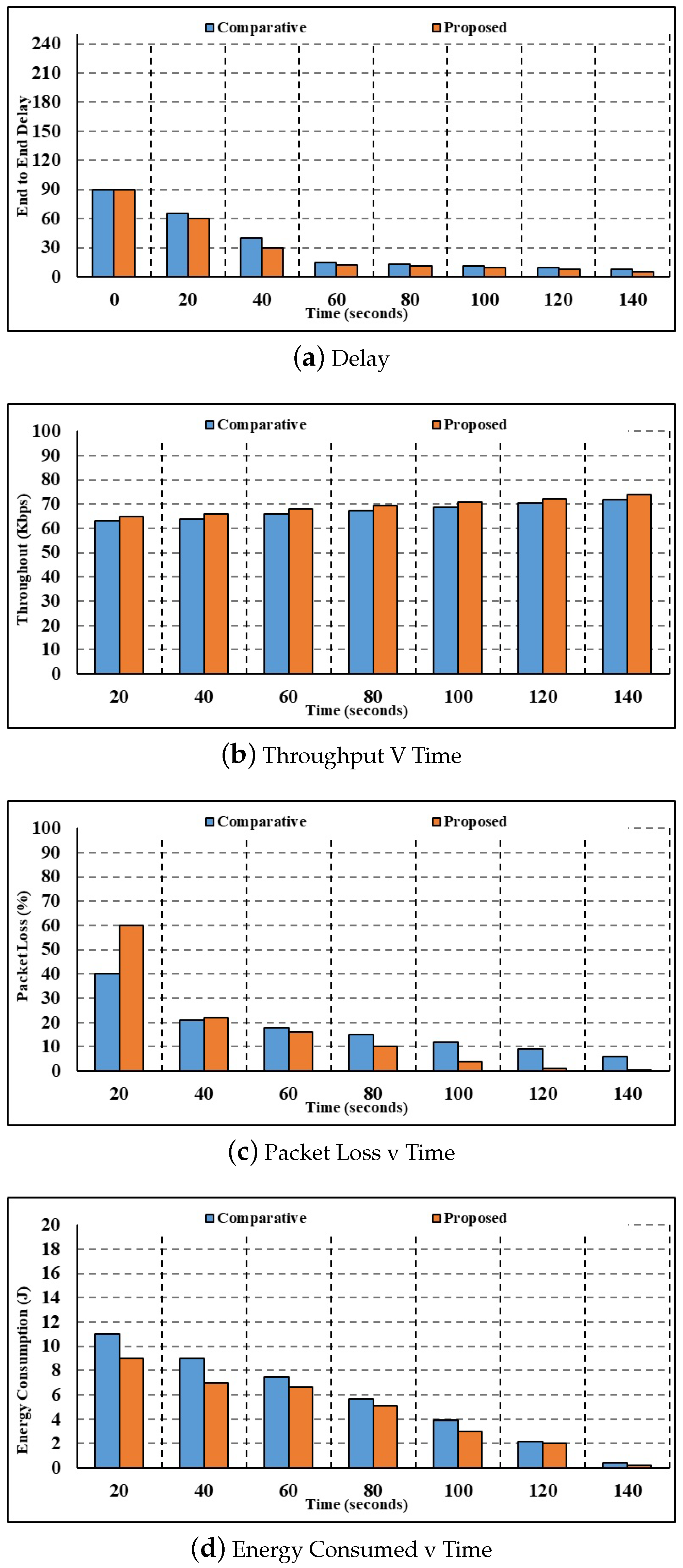
- Figure 4a depicts the results of the 150-node delay parameter investigation. When the time is 20 s, the current authentication method calculates a corresponding delay of 8.78 s, whereas the suggested multilayer authentication method computes a delay of 5.20 s. Compared to the state-of-the-art authentication and key agreement process, which takes 0.34 s, the proposed multilayer authentication process takes 0.08 s. Current authentication and key agreement have longer delays than the proposed multilayer authentication. Henceforth, the suggested multilayer authentication system has a very fast response time.
- Figure 4b shows the results of the throughput parameter study with 150 nodes. While the throughput estimated using the current authentication and key agreement method is 61.60 bps for 40 s, the throughput estimated using the proposed multilevel authentication method is 64.20 bps. In comparison to the current authentication and key agreement throughput of 52.41 bps, the suggested multilayer authentication has a throughput of 62.74 bps for 100 s. The reduced throughput calculated by the suggested approach proves that the technique is very efficient at handling the data packets.
- Figure 4c shows that the results of the investigation are expressed as a packet loss parameter with 150 nodes. At 60 s, the current authentication and key agreement method calculates a packet loss value of 3.72, whereas the proposed multilevel authentication method calculates a packet loss value of 2.66. In comparison to the current authentication and key agreement, the packet loss values calculated by the proposed multilayer authentication are 2.41. Minimal packet loss is an indication of how efficiently the suggested method processes packets and reduces packet loss.
- Figure 4d shows the study in terms of the energy consumption parameter. Compared to the proposed multilayer authentication, which uses 16.79 J of energy for 100 s, the present authentication and key agreement uses 17.09 J. After 108 s, the suggested multilayer authentication uses 17.70 J of energy, compared to 19.63 J for the current authentication and key agreement. As a result, the suggested approach uses far less energy than the current one.
4.2.2. Three-Hundred-Node Comparative Analysis
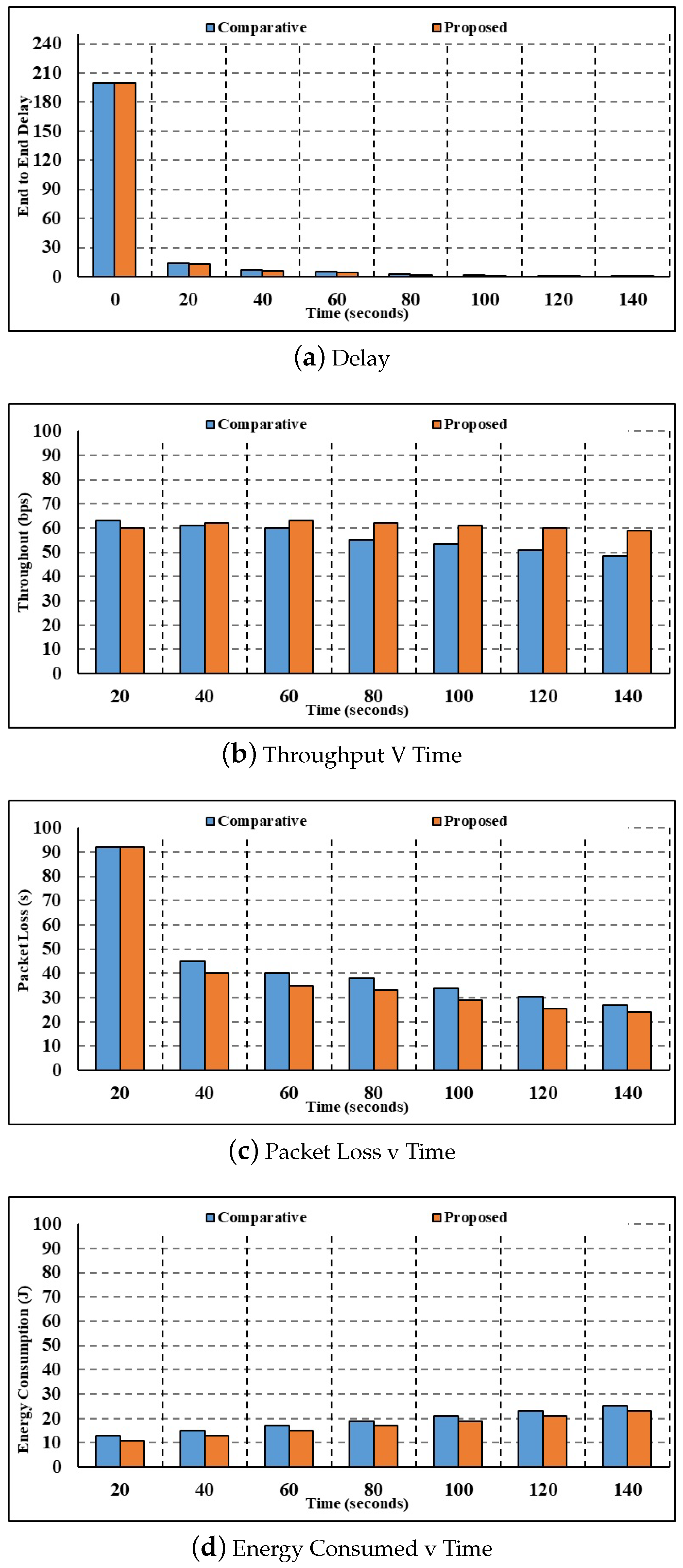
- Figure 5a shows the results of the investigation for the delay parameter with 300 nodes. The current authentication and key agreement method calculate a corresponding delay value of 9.59 s for 20 s, whereas the proposed multilayer authentication method only takes 7.32 s. In comparison to the current authentication and key agreement delay of 1.46 s, the delay values calculated by the proposed multilayer authentication for 100 s are 1.38s.
- Using 300 nodes, Figure 5b shows the throughput parameter analysis. The current authentication and key agreement method calculate a throughput value of 60.06 bps for 20 s, whereas the suggested multilayer authentication method achieves a throughput of 63.50 bps. In comparison to the current authentication and key agreement throughput of 48.21 bps, the throughput figures estimated by the proposed multilayer authentication for 100 s are 61.44 bps.
- Figure 5c shows the results of the investigation with 300 nodes, broken down per packet loss parameter. At a time of 20 s, the packet loss calculated using the current authentication and key agreement method is 6.15 s, whereas the packet loss calculated using the suggested multilayer authentication method is 5.82 s. In comparison to the current authentication and key agreement, the packet loss values calculated by the proposed multilayer authentication for 100 s are 3.71 s.
- Figure 5d shows the study in terms of the energy consumption parameter. Current authentication and key agreement use 16.03 J of energy for 100 s, while the suggested multilayer authentication consumes 17.11 J. Comparing the energy consumption of current authentication and key agreement at 17.55 J for 110 s to that of suggested multilayer authentication, the latter results in 15.45 J. As a result, the suggested approach uses far less energy.
4.2.3. Six-Hundred-Node Comparative Analysis
- Figure 6a illustrates the study on the delay parameter. The suggested multilayer authentication approach calculates a delay of 12.04 s when the time is 90 s, whereas the present method’s comparable delay is 16.46 s. The suggested multilevel authentication method calculates delay values of 8.45 s for 100 s, whereas the present authentication and key agreement method computes a delay of 14.73 s.
- Figure 6b shows the results of the throughput parameter study with 600 nodes. There is a significant difference between the throughput values obtained using the current authentication and key agreement method (61.53 bps) and the suggested multilevel authentication method (63.73 bps) at a time of 22 s. Compared to the current authentication and key agreement throughput of 66.15 bps, the throughput values estimated by the proposed multilayer authentication are 68.34 bps for 75 s.
- Figure 6c shows the results of the investigation with 600 nodes, broken down per packet loss parameter. There is a discrepancy between the packet loss values calculated using the current authentication and key agreement method (16.57 s) and the proposed multilevel authentication method (14.32 s) at a time of 55 s. Compared to the current authentication and key agreement, the packet loss values calculated by the proposed multilayer authentication are 10.01 s for 105 s. As a result of the suggested strategy’s fast processing of packets and mitigation of packet loss, the suggested technique has very little packet loss.
- Figure 6d displays the results of the investigation concerning the energy consumption parameter. The current authentication and key agreement method uses 12.88 J of energy for 30 s, whereas the suggested multilayer authentication method uses 9.97 J. While current authentication uses 18.51 J of energy and key agreement uses 17.51 J for 80 s, the suggested multilayer authentication uses 17.51 J. Therefore, in comparison to the current way, the suggested strategy is superior and has less energy use.
4.3. Discussion
- Denial of Service (DoS) Attacks: Attackers may attempt to overwhelm the system with a high volume of illegitimate requests, disrupting communication and coordination. This could potentially lead to a loss of control over UAVs and operational disruptions. Implementing rate limiting, traffic filtering, and employing redundant communication channels can help to mitigate the impact of DoS attacks and ensure continuity of operations.
- Man-in-the-Middle (MitM) Attacks: Unauthorized entities could intercept and manipulate communication between UAVs and the IoT system, compromising data integrity and security. Implementing end-to-end encryption, digital signatures, and mutual authentication can help to prevent and detect MitM attacks, ensuring the integrity and confidentiality of data transmission.
- Unauthorized Access: Robust authentication mechanisms should be in place to prevent unauthorized access attempts, such as strong user authentication and access control policies. Implementing multifactor authentication, role-based access control, and regular security audits can help to prevent unauthorized access and protect sensitive information.
- Data Tampering: To prevent data tampering, data integrity checks, cryptographic hashing, and secure transmission protocols should be employed to detect and prevent unauthorized modifications to transmitted data. Implementing data validation mechanisms, digital signatures, and secure communication protocols can help to ensure the integrity of data transmitted between UAVs and the IoT system.
- Identity Spoofing: Employing strong identity verification methods and secure communication channels can help to prevent identity spoofing attacks. Implementing certificate-based authentication, biometric authentication, and secure token exchange can help to mitigate the risk of identity spoofing attacks.
- Registry Manipulation: Implementing secure registry management practices, such as access controls, audit trails, and tamper-evident logging, can help to prevent unauthorized manipulation of the IoUAV registry. Employing secure registry management practices, such as access controls, audit trails, and regular integrity checks, can help to prevent unauthorized manipulation of the IoUAV registry.
4.4. Security Validation
4.5. Limiting Aspects
- Scalability: The scalability of the proposed model may not have been thoroughly addressed. As the number of UAVs and users increases, the system’s ability to handle a larger load of registrations, logins, and authentications may become a challenge.
- Connectivity and Latency: The model’s effectiveness may be limited in scenarios with intermittent connectivity or high latency as real-time communication and authentication could be compromised.
- User Experience: The user registration and login process may introduce complexities for UAV operators, potentially affecting the overall user experience and operational efficiency.
- Maintenance and Updates: The long-term maintenance and update process for the IoUAV registry and authentication modules should be considered to ensure ongoing security and reliability.
Uav-Related Limiting Aspects
- Flight Performance: The model should account for the specific flight performance requirements of UAVs, including stability, maneuverability, and payload capacity.
- Regulatory Compliance: Compliance with aviation regulations, airspace restrictions, and licensing requirements is crucial for UAV operations.
- Environmental Adaptability: The model should consider the adaptability of UAVs to diverse environmental conditions, including weather, temperature, and terrain.
- Mission-specific Considerations: Addressing the unique requirements of different UAV missions, such as surveillance, mapping, delivery, or search and rescue.
4.6. Application Deployment Scenarios
- Industrial Sector: The model can be deployed in industrial environments where UAVs are used for tasks such as infrastructure inspection, inventory management, and surveillance. The security and coordination provided by the proposed model can enhance operational efficiency and safety in industrial settings.
- Emergency Response: Deploying the model in emergency response scenarios, such as search and rescue operations or disaster management, can enable secure and coordinated communication among UAVs and ground personnel, facilitating effective response efforts.
- Agriculture: In agricultural applications, the model can be utilized for coordinating UAVs involved in crop monitoring, pesticide spraying, and irrigation management. The secure communication facilitated by the model can help to optimize agricultural operations.
- Urban Planning and Infrastructure Development: The proposed model can be deployed in urban planning and infrastructure development projects where UAVs are used for surveying, mapping, and construction monitoring. It can ensure secure data transmission and coordination among multiple UAVs involved in such projects.
- Remote Sensing and Environmental Monitoring: Environments such as remote sensing missions, environmental monitoring, and wildlife conservation can benefit from the secure communication and coordination provided by the proposed model, enabling effective data collection and analysis by UAVs.
5. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- AL-Dosari, K.; Fetais, N. A New Shift in Implementing Unmanned Aerial Vehicles (UAVs) in the Safety and Security of Smart Cities: A Systematic Literature Review. Safety 2023, 9, 64. [Google Scholar] [CrossRef]
- Abegaz, M.S.; Abishu, H.N.; Yacob, Y.H.; Ayall, T.A.; Erbad, A.; Guizani, M. Blockchain-Based Resource Trading in Multi-UAV-Assisted Industrial IoT Networks: A Multi-Agent DRL Approach. IEEE Trans. Netw. Serv. Manag. 2023, 20, 166–181. [Google Scholar] [CrossRef]
- Alhafnawi, M.; Bany Salameh, H.A.; Masadeh, A.; Al-Obiedollah, H.; Ayyash, M.; El-Khazali, R.; Elgala, H. A Survey of Indoor and Outdoor UAV-Based Target Tracking Systems: Current Status, Challenges, Technologies, and Future Directions. IEEE Access 2023, 11, 68324–68339. [Google Scholar] [CrossRef]
- Aljumah, A.; Ahanger, T.A.; Ullah, I. Heterogeneous Blockchain-Based Secure Framework for UAV Data. Mathematics 2023, 11, 1348. [Google Scholar] [CrossRef]
- Bakirci, M.; Ozer, M.M. Surveillance, Reconnaissance and Detection Services for Disaster Operations of IoT-Based eVTOL UAVs with Swarm Intelligence. In Proceedings of the 2023 11th International Symposium on Digital Forensics and Security (ISDFS), Chattanooga, TN, USA, 11–12 May 2023. [Google Scholar]
- Banerjee, A.; Gupta, S.K.; Gupta, P.; Sufian, A.; Srivastava, A.; Kumar, M. UAV-IoT collaboration: Energy and time-saving task scheduling scheme. Int. J. Commun. Syst. 2023, 36, e5555. [Google Scholar] [CrossRef]
- Chapnevis, A.; Bulut, E. Delay Optimal UAV Trajectory Planning for Secure Data Collection from Mobile IoT Networks. In Proceedings of the 2023 IEEE International Conference on Industrial Technology (ICIT), Orlando, FL, USA, 4–6 April 2023. [Google Scholar]
- Chelloug, S.A.; Alkanhel, R.; Aziz, A.; Muthanna, M.S.A.; Muthanna, A. Secured Reliable Communication Through Authentication and Optimal Relay Selection in Blockchain Enabled Cellular IoT Networks. IEEE Access 2023, 11, 122368–122386. [Google Scholar] [CrossRef]
- Safwan, H.; Iqbal, Z.; Amin, R.; Khan, M.A.; Alhaisoni, M.; Alqahtani, A.; Kim, Y.J.; Chang, B. An IoT Environment Based Framework for Intelligent Intrusion Detection. CMC Comput. Mater. Contin. 2023, 75, 2365–2381. [Google Scholar] [CrossRef]
- Goyal, N.; Sharma, S.; Rana, A.K.; Tripathi, S.L. (Eds.) Internet of Things: Robotic and Drone Technology; CRC Press: Boca Raton, FL, USA, 2022. [Google Scholar]
- Chen, C.L.; Deng, Y.Y.; Zhu, S.; Tsaur, W.J.; Weng, W. An IoT and blockchain based logistics application of UAV. Multimed. Tools Appl. 2024, 83, 655–685. [Google Scholar] [CrossRef]
- Tianyi, L.; Riaz, S.; Xuande, Z.; Mirza, A.; Afzal, F.; Iqbal, Z.; Khan, M.A.; Alhaisoni, M.; Alqahtani, A. Federated learning based nonlinear two-stage framework for full-reference image quality assessment: An application for biometric. Image Vis. Comput. 2022, 128, 104588. [Google Scholar] [CrossRef]
- Chulerttiyawong, D.; Jamalipour, A. Sybil Attack Detection in Internet of Flying Things-IoFT: A Machine Learning Approach. IEEE Internet Things J. 2023, 10, 12854–12866. [Google Scholar] [CrossRef]
- Alsubai, S.; Alqahtani, A.; Sha, M.; Almadhor, A.; Abbas, S.; Mughal, H.; Gregus, M. Privacy Preserved Cervical Cancer Detection Using Convolutional Neural Networks Applied to Pap Smear Images. Comput. Math. Methods Med. 2023, 2023, 9676206. [Google Scholar] [CrossRef] [PubMed]
- Do, D.T.; Le, C.B.; Vahid, A.; Mumtaz, S. Antenna Selection and Device Grouping for Spectrum-Efficient UAV-Assisted IoT Systems. IEEE Internet Things J. 2023, 10, 8014–8030. [Google Scholar] [CrossRef]
- Dong, C.; Zhou, J.; An, Q.; Jiang, F.; Chen, S.; Pan, L.; Liu, X. Optimizing Performance in Federated Person Re-Identification through Benchmark Evaluation for Blockchain-Integrated Smart UAV Delivery Systems. Drones 2023, 7, 413. [Google Scholar] [CrossRef]
- Han, L.; Xun, Y.; Liu, J.; Benslimane, A.; Zhang, Y. DP-Authentication: A novel deep learning based drone pilot authentication scheme. Hoc Networks 2023, 147, 103180. [Google Scholar] [CrossRef]
- He, X.; Chen, Q.; Tang, L.; Wang, W.; Liu, T.; Li, L.; Liu, Q.; Luo, J. Federated Continuous Learning Based on Stacked Broad Learning System Assisted by Digital Twin Networks: An Incremental Learning Approach for Intrusion Detection in UAV Networks. IEEE Internet Things J. 2023, 10, 19825–19838. [Google Scholar] [CrossRef]
- Khoshafa, M.H.; Ngatched, T.M.N.; Gadallah, Y.; Ahmed, M.H. Securing LPWANs: A Reconfigurable Intelligent Surface (RIS) Assisted UAV Approach. IEEE Wirel. Commun. Lett. 2023, 1, 158–162. [Google Scholar] [CrossRef]
- Saini, H.K.; Jain, K. Heuristics to Secure IoT-Based Edge-Driven UAV; IGI Global: Hershey, PA, USA, 2023; pp. 283–301. [Google Scholar]
- Nguyen, S.Q.; Le, A.T.; Le, C.B.; Tin, P.T.; Kim, Y.H. Exploiting User Clustering and Fixed Power Allocation for Multi-Antenna UAV-Assisted IoT Systems. Sensors 2023, 23, 5537. [Google Scholar] [CrossRef] [PubMed]
- Tsou, Y.C.; Chou, R.H.; Chen, Y.J. A High-security Internet of Drones Design by Integrating Physical-layer Key Generation and Blockchain. In Proceedings of the 2023 International Conference on Consumer Electronics—Taiwan, Pingtung, Taiwan, 17–19 July 2023; pp. 351–352. [Google Scholar]
- Restivo, R.D.; Dodson, L.C.; Wang, J.; Tan, W.; Liu, Y.; Wang, H.; Song, H. GPS Spoofing on UAV: A Survey. In Proceedings of the IEEE INFOCOM 2023—IEEE Conference on Computer Communications Workshops, Hoboken, NJ, USA, 20 May 2023. [Google Scholar]
- Nasr-Azadani, M.; Abouei, J.; Plataniotis, K.N. Distillation and Ordinary Federated Learning Actor-Critic Algorithms in Heterogeneous UAV-Aided Networks. IEEE Access 2023, 11, 44205–44220. [Google Scholar] [CrossRef]
- Zhang, S.; Shi, Z.; Liu, J. Joint Trajectory Design and Resource Allocation for Secure Air-ground Integrated IoT Networks. IEEE Internet Things J. 2023, 10, 20458–20471. [Google Scholar] [CrossRef]
- Li, S.; Cheng, X.; Huang, X.; Otaibi, S.A.; Wang, H. Cooperative Conflict Detection and Resolution and Safety Assessment for 6G Enabled Unmanned Aerial Vehicles. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2183–2198. [Google Scholar] [CrossRef]
- Yin, Z.; Cheng, N.; Song, Y.; Hui, Y.; Li, Y.; Luan, T.H.; Yu, S. UAV-assisted Secure Uplink Communications in Satellite-supported IoT: Secrecy Fairness Approach. IEEE Internet Things J. 2023. [Google Scholar] [CrossRef]
- Lan, X.; Tang, X.; Zhang, R.; Lin, W.; Han, Z. UAV-Assisted Computation Offloading Toward Energy-Efficient Blockchain Operations in Internet of Things. IEEE Wirel. Commun. Lett. 2023, 12, 1469–1473. [Google Scholar] [CrossRef]
- Ma, Z.; Zhang, J. Efficient, Traceable and Privacy-Aware Data Access Control in Distributed Cloud-Based IoD Systems. IEEE Access 2023, 11, 45206–45221. [Google Scholar] [CrossRef]
- Moshayedi, A.J.; Roy, A.S.; Taravet, A.; Liao, L.; Wu, J.; Gheisari, M. A Secure Traffic Police Remote Sensing Approach via a Deep Learning-Based Low-Altitude Vehicle Speed Detector through UAVs in Smart Cites: Algorithm, Implementation and Evaluation. Future Transp. 2023, 3, 189–209. [Google Scholar] [CrossRef]
- Zhou, S.; Huang, X.; Obaidat, M.S.; Alzahrani, B.A.; Han, X.; Kumari, S.; Chen, C.M. Transferability of Adversarial Attacks on Tiny Deep Learning Models for IoT Unmanned Aerial Vehicles. IEEE Internet Things J. 2023. [Google Scholar] [CrossRef]
- Wei, M.; Xu, K. Multi-Task Matching Mechanism Design for UAV-assisted MEC Network with Blockchain. IEEE Access 2023. [Google Scholar] [CrossRef]
- Perumalla, S.; Chatterjee, S.; Siva Kumar, A.P. Secure communication using multilevel authentication strategy in Internet of Drones. Concurr. Comput. Pract. Exp. 2023, 35, e7667. [Google Scholar] [CrossRef]
- Pu, C.; Wall, A.; Choo, K.K.R.; Ahmed, I.; Lim, S. A lightweight and privacy-preserving mutual authentication and key agreement protocol for Internet of Drones environment. IEEE Internet Things J. 2022, 9, 9918–9933. [Google Scholar] [CrossRef]

| References | [29] | [30] | [31] | [32] | [23] | [22] | [33] | Proposed |
|---|---|---|---|---|---|---|---|---|
| UAV | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
| Data Analysis | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 |
| Data Repository | 1 | 1 | 1 | 1 | 0 | 0 | 1 | 1 |
| Quantification | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 1 |
| Security | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
| Authentication | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 1 |
| IoT | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
| Numerical | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 1 |
| Latency | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 |
| Energy Efficacy | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 |
| Symbolic Representation | Description |
|---|---|
| e | UAV node |
| A | Server Module |
| n | Secret Message |
| J | Identity Value |
| SJ | Relative Identity Value |
| T | Server Module |
| Q | Polynomial Identity Value |
| S | Registration Timestamp |
| v | User |
| q | Private Key |
| H | Public attribute |
| C | Fingerprint |
| h | Random Number |
| O | Output measures |
| S. No. | Attribute | Measure |
|---|---|---|
| 1 | Energy | 25 J |
| 2 | Power (Transmission) | 0.833 W |
| 3 | Power (Receiving) | 0.0637 W |
| 4 | Power (Idle) | 0.064 W |
| 5 | Power (Sense) | 0.0164 W |
| Metric | Node Count | State-of-the-Art Technique | Proposed Technique |
|---|---|---|---|
| Latency | 150 | 1.365 | 0.958 |
| Latency | 300 | 1.986 | 1.458 |
| Latency | 600 | 3.995 | 3.255 |
| Throughput | 150 | 62.621 | 69.26 |
| Throughput | 300 | 50.262 | 56.654 |
| Throughput | 600 | 79.265 | 90.15 |
| Loss of Packet | 150 | 4.586 | 3.215 |
| Loss of Packet | 300 | 6.658 | 3.654 |
| Loss of Packet | 600 | 10.245 | 8.854 |
| Consumed Energy | 150 | 20.265 | 17.659 |
| Consumed Energy | 300 | 18.255 | 15.265 |
| Consumed Energy | 600 | 20.999 | 18.658 |
| Computation Delay | 150 | 2.958 | 2.82 |
| Computation Delay | 300 | 2.145 | 1.92 |
| Computation Delay | 600 | 3.958 | 3.45 |
| Parameter | [13] | [34] | [33] | Proposed |
|---|---|---|---|---|
| Precision | 88.44% | 89.23% | 91.27% | 94.46% |
| Specificity | 87.02% | 89.22% | 92.33% | 96.97% |
| Precision | 87.44% | 89.46% | 91.07% | 94.56% |
| Sensitivity | 86.49% | 89.64% | 91.95% | 96.54% |
| F-Measure | 86.96% | 89.26% | 90.45% | 95.69% |
| Root Relative Squared Error (RRSE) | 6.67 ± 0.38% | 6.64 ± 0.68% | 6.64 ± 0.33% | 2.23 ± 0.66% |
| Root Mean Square Error (RMSE) | 6.42 ± 0.03% | 5.03 ± 0.37% | 4.89 ± 0.23% | 2.35 ± 0.37% |
| Relative Absolute Error (RAE) | 5.66 ± 0.43% | 6.63 ± 0.66% | 7.21 ± 0.19% | 4.11 ± 0.22% |
| Mean Absolute Error (MAE) | 6.09 ± 0.03% | 7.22 ± 0.72% | 7.78 ± 0.27% | 4.43 ± 0.42% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aljumah, A. UAV-Based Secure Data Communication: Multilevel Authentication Perspective. Sensors 2024, 24, 996. https://doi.org/10.3390/s24030996
Aljumah A. UAV-Based Secure Data Communication: Multilevel Authentication Perspective. Sensors. 2024; 24(3):996. https://doi.org/10.3390/s24030996
Chicago/Turabian StyleAljumah, Abdullah. 2024. "UAV-Based Secure Data Communication: Multilevel Authentication Perspective" Sensors 24, no. 3: 996. https://doi.org/10.3390/s24030996
APA StyleAljumah, A. (2024). UAV-Based Secure Data Communication: Multilevel Authentication Perspective. Sensors, 24(3), 996. https://doi.org/10.3390/s24030996






