Two Novel Semi-Quantum Secure Direct Communication Protocols in IoT
Abstract
1. Introduction
2. Protocol Design
2.1. Proposed Protocol (Protocol 1)
- 1.
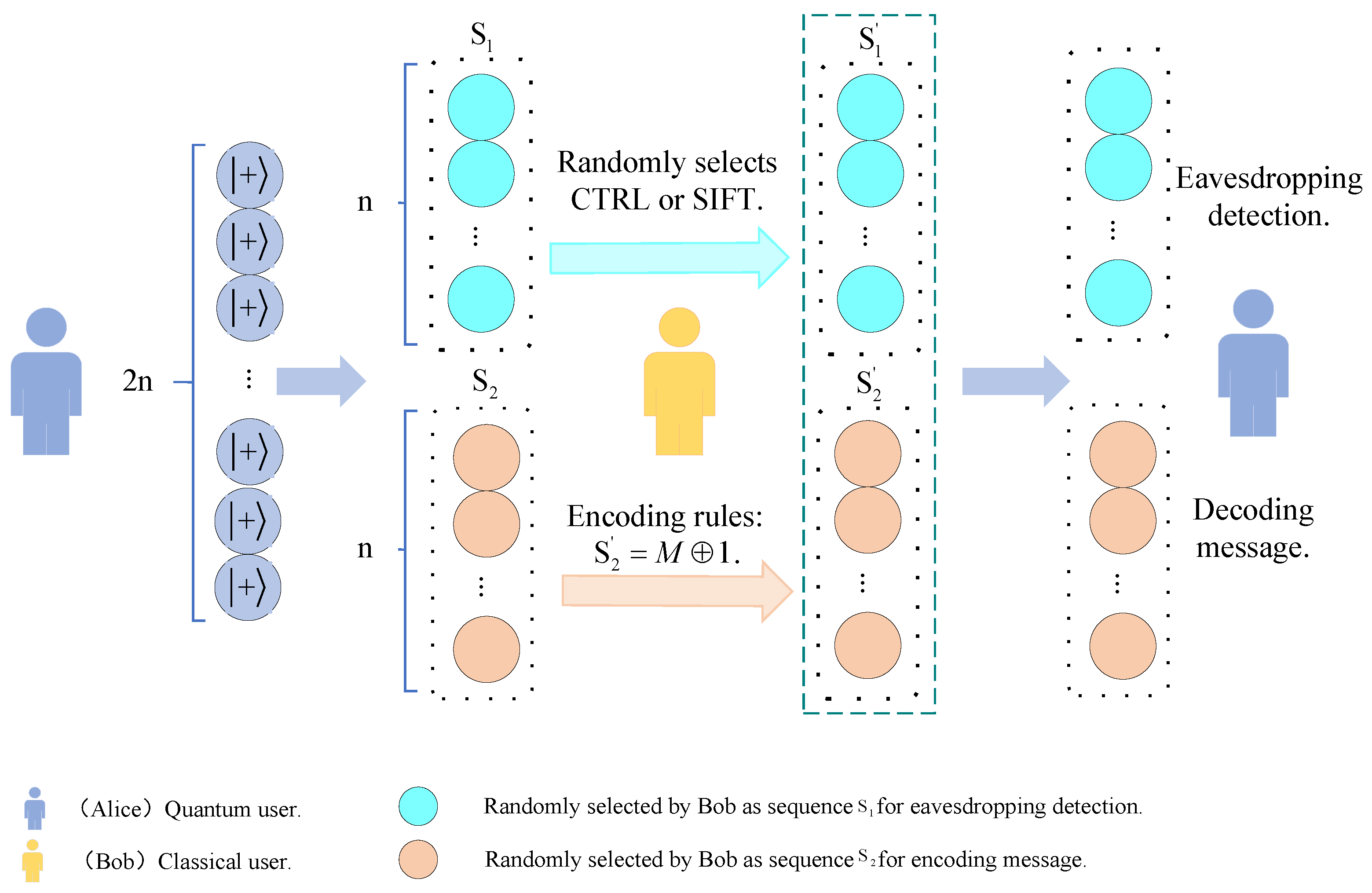
- In this paper, we propose a single-state SQSDC protocol in which quantum Alice only needs to prepare 2n single photons and sends them to Bob.
- 2.
- Once Bob has received all the qubits, the n particles are randomly selected from them to form the sequence , while the remaining particles constitute the sequence . For sequence , Bob randomly selects either the CTRL operation (which returns the particle to its original state without any additional processing) or the SIFT operation (which measures the particle with the Z-basis, records the measurement, and returns the particle to its original state). For sequence , Bob performs the re-prepare operation (which directly discards the particle and re-prepares a qubit) and message encoding with the following encoding rules: Bob prepares the secret messages and produces code messages . Then, is encoded into code sequence in the Z-basis and sent to Alice. If Bob wants to transmit the message “0”, he would effectively discard the original particle and prepare a state to return to Alice. If Bob wants to transmit the message “1”, he would have to effectively discard the original particle and prepare a state to return to Alice.Ultimately, the 2n particles are returned to Alice.
- 3.
- For all qubits arriving, Alice temporarily stores them all in the quantum memory and transmits an acknowledgement message to Bob, who then announces the positions of the particles in sequence , the operation performed on the particles and the measurement results of the SIFT operation. Alice receives and performs eavesdropping detection on the different operations performed by Bob. For particles where Bob performs a CTRL operation, Alice measures them directly with an X-basis, and the result must be . The particle selected by Bob for the SIFT operation is directly measured using the Z-basis, and the resulting measurements are then compared with Bob’s own measurements, which should be identical. Alice performs eavesdropping detection based on the results of the above measurements. If the error rate of the detection is higher than a threshold, the communication is abandoned and restarted; otherwise, the process continues to the next step.
- 4.
- If there is no eavesdropping, Alice performs the decoding of the message. Alice measures the qubit in the code sequence , and the results are indicated as . The decoded messages are .
2.2. Example of Proposed Protocol
- 1.
- Assume that Alice prepares 8 states and transmits them to Bob.
- 2.
- Bob receives them and randomly selects 4 for the sequence . Suppose Bob selects the 1st, 3rd, 5th, and 7th particles for the sequence . Then, the remaining 2nd, 4th, 6th, and 8th particles are sequence . In this context, it is assumed that Bob performs the operation {CTRL, CTRL, SIFT, SIFT} on the sequence for the purpose of eavesdropping detection. If we assume that Bob wishes to transmit the secret message , four particles of sequence are directly discarded. The code message . So, Bob returns {, , , }.
- 3.
- Alice receives 8 particles and sends an acknowledgement to Bob, who tells Alice the location of the particles of sequence , and the operation performed on the particles, as well as the measurements of the SIFT operation performed, and Alice performs the eavesdropping detection. For particles with direct CTRL operations, Alice measures them directly with an X-basis, and the result should be . For the particles that were selected for the SIFT operation, Alice conducts measurements using the Z-basis and compares the results with those obtained by Bob, which were expected to be identical. If there are no errors in the eavesdropping detection, the process proceeds to the next step. Otherwise, it is necessary to repeat the initial step.
- 4.
- If there is no eavesdropping, Alice directly measures remaining particles with the Z-basis, which results in {, , , }.So, Alice receives the message transmitted by Bob.
3. Security Analysis
3.1. Trojan Horse Attack
3.2. Intercept–Measure–Resend Attacks
3.3. Entangle–Measure Attack
4. Comparison
5. Protocol Extension
5.1. Extended Protocol (Protocol 2)
- 1.
- Alice prepares 2n single-photon states and sends them to Bob.
- 2.
- Once Bob has received all the qubits, the n particles are randomly selected from them to form sequence , while the remaining particles constitute sequence . For sequence , Bob randomly selects either the CTRL operation (which returns the particle to its original state without any additional processing) or the SIFT operation (which measures the particle with the Z-basis, records the measurement, and returns the particle to its original state). For sequence , Bob performs message encoding with the following encoding rules:
- (a)
- In such a scenario, should Bob wish to convey the message “00”, he would effectively discard the original particle and prepare a state to return to Alice.
- (b)
- If Bob wants to convey the message “01”, he would effectively discard the original particle and prepare a state to return to Alice.
- (c)
- If Bob wishes to convey message “10”, it is necessary to measure the original particle with the Z-basis and record the result (assuming that the measurement is 0), returning an identical state (returning a ) to Alice.
- (d)
- If Bob wants to pass on message “11”, he measures the original particle with the Z-basis and records the result (assuming that the measurement is 0), returning an opposite state (returning a ) to Alice.
Ultimately, the 2n particles are returned to Alice. - 3.
- Alice receives all the particles and transmits an acknowledgement message to Bob, who then transmits the position of the particles in sequence , the operation performed on the particles and the measurement results of the SIFT operation. Alice receives and performs eavesdropping detection on the different operations performed by Bob. For particles where Bob performs a CTRL operation, Alice measures them directly with an X-basis, and the result must be . The particle selected by Bob for the SIFT operation is directly measured using the Z-basis, and the resulting measurements are then compared with Bob’s own measurements, which should be identical. Alice performs eavesdropping detection based on the results of the above measurements. If the error rate of the detection is higher than a threshold, the communication is abandoned and restarted; otherwise, the process continues to the next step.
- 4.
- If there is no eavesdropping, Bob is informed that the channel is secure. Bob informs Alice the location of the remaining particles in which the measurement operation has been performed and the result of the measurement. Alice performs the decoding of the message.
- (a)
- For particles that are not measured, Alice measures them directly with the Z-basis. If the measurement result is , the secret message delivered by Bob is “00”.
- (b)
- For particles that are not measured, Alice measures them directly with the Z-basis. If the measurement result is , the secret message delivered by Bob is “01”.
- (c)
- In the case of the particles for which Bob performs measurements, Alice conducts measurements with the Z-basis. The measurements should then be compared with those made by Bob. If the results of this comparison are identical, the secret message delivered by Bob is “10”.
- (d)
- In the case of the particles for which Bob performs measurements, Alice conducts measurements with the Z-basis. The measurements should then be compared with those made by Bob. If the results of this comparison are different, the secret message delivered by Bob is “11”.
5.2. Example of Proposed Extended Protocol
- 1.
- Assume that Alice prepares 8 states and transmits them to Bob.
- 2.
- Bob receives them and randomly selects 4 for the sequence . Suppose Bob selects the 1st, 3rd, 5th, and 7th particles for the sequence . Then, the remaining 2nd, 4th, 6th, and 8th particles are sequence . In this context, it is assumed that Bob performs the operation {CTRL, SIFT, CTRL, SIFT} on the sequence for the purpose of eavesdropping detection. If we assume that Bob wishes to deliver the secret message {00, 01, 10, 11}, the first of the four particles of sequence is directly discarded, returning a ; the second particle is directly discarded, returning a ; the third particle is measured with a Z-basis (assuming that the measurement is 0), and the result is recorded to return an identical state (returning a ); and the fourth particle is measured with a Z-basis (assuming the measurement is 0), and recording the measurement returns an opposite state (returning a ). So, for the sequence, Bob returns {, , , }.
- 3.
- Alice receives 8 particles and sends an acknowledgement to Bob, who tells Alice the location of the particles of sequence , and the operation performed on the particles, as well as the measurements of the SIFT operation performed, and Alice performs the eavesdropping detection. For particles with direct CTRL operations, Alice measures them directly with an X-basis, and the result should be . For the particles that were subjected to the SIFT operation, Alice conducts measurements using the Z-basis and compares the results with those obtained by Bob, which were expected to be identical. If there are no errors in the eavesdropping detection, the process proceeds to the next step. Otherwise, it is necessary to repeat the initial step.
- 4.
- Alice informs Bob that the channel is secure, and Bob tells Alice which of the remaining particles have been measured, in this case particles 3 and 4, and that the measurements are {0, 0}. Alice directly measures the particles that were not previously measured (i.e., the 1st and 2nd particles) using the Z-basis. A measurement of “0” for the first particle results in a message of “00” from Bob, and a measurement of “1” for the second particle results in a message of “01” from Bob. For the particles for which Bob performs measurements (i.e., the 3rd and 4th particles), Alice conducts measurements directly with the Z-basis, which results in {0, 1}, and then compares them with Bob’s measurements of {0, 0}, revealing that the third particle has the same result for the comparison, which results in Bob delivering a message of “10”, and the fourth particle has a different result for the comparison, which results in Bob delivering a message of “11”. So, Alice receives the message {00, 01, 10, 11} delivered by Bob.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Al-Mohammed, H.A.; Yaacoub, E. On The Use of Quantum Communications for Securing IoT Devices in the 6G Era. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Virtual, 14–23 June 2021. [Google Scholar]
- Fu, Y.; Li, D.; Hua, X.; Jiang, Y.; Zhu, Y.; Zhou, J.; Yang, X.; Tan, Y. A Scheme for Quantum Teleportation and Remote Quantum State Preparation of IoT Multiple Devices. Sensors 2023, 23, 8475. [Google Scholar] [CrossRef] [PubMed]
- Shi, R.H.; Fang, X.Q. Quantum Scheme for Privacy-Preserving Range MAX/MIN Query in Edge-Based Internet of Things. IEEE Trans. Netw. Serv. Manag. 2024. early access. [Google Scholar] [CrossRef]
- Shor, P. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on the Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Grover, L.K. A fast quantum-mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996. [Google Scholar]
- Bennett, C.H. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Bangalore, India, 10–12 December 1984. [Google Scholar]
- French, J.A.; Kanner, A.M.; Bautista, J.; Abou-Khalil, B.; Browne, T.; Harden, C.L.; Theodore, W.H.; Bazil, C.; Stern, J.; Schachter, S.C.; et al. Efficacy and Tolerability of the New Antiepileptic Drugs, II: Treatment of Refractory Epilepsy. Report of the TTA and QSS Subcommittees of the American Academy of Neurology and the American Epilepsy Society. Epilepsia 2004, 45, 410–423. [Google Scholar] [CrossRef] [PubMed]
- Tian, Y.; Wang, J.; Bian, G.; Chang, J.; Li, J. Dynamic Multi-Party to Multi-Party Quantum Secret Sharing based on Bell States. Adv. Quantum Technol. 2024, 7, 2400116. [Google Scholar] [CrossRef]
- Mizutani, A.; Tamaki, K.; Ikuta, R.; Yamamoto, T.; Imoto, N. Measurement-device-independent quantum key distribution for Scarani-Acin-Ribordy-Gisin 04 protocol. Sci. Rep. 2014, 4, 5236. [Google Scholar]
- Yang, Z.; Shi, Q.; Cheng, T.; Wang, X.; Zhang, R.; Yu, L. A security-enhanced authentication scheme for quantum-key-distribution (QKD) enabled Internet of vehicles in multi-cloud environment. Veh. Commun. 2024, 48, 100789. [Google Scholar] [CrossRef]
- Wu, W.Q.; Zhou, G.L.; Zhao, Y.X.; Zhang, H. New Quantum Private Comparison Protocol Without a Third Party. Int. J. Theor. Phys. 2020, 59, 1866–1875. [Google Scholar] [CrossRef]
- Liu, W.; Wang, Y.B.; Cui, W. Quantum Private Comparison Protocol Based on Bell Entangled States. Commun. Theor. Phys. 2012, 57, 583. [Google Scholar]
- Xin, X.; Ding, L.; Zhang, T.; Yang, Q.; Li, C. Provably secure arbitrated-quantum signature. Quantum Inf. Process. 2022, 21, 390. [Google Scholar] [CrossRef]
- Shi, R.H.; Li, Y.F. Quantum private set intersection cardinality protocol with application to privacy-preserving condition query. IEEE Trans. Circuits Syst. Regul. Pap. 2022, 69, 2399–2411. [Google Scholar] [CrossRef]
- Long, G.L.; Liu, X.S. Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. 2002, 65, 032302. [Google Scholar] [CrossRef]
- Deng, F.G.; Long, G.L.; Liu, X.S. Two-step quantum direct communication protocol using the Einstein–Podolsky-Rosen pair block. Phys. Rev. A 2003, 68, 113–114. [Google Scholar] [CrossRef]
- Long, G.L.; Deng, F.G.; Wang, C.; Li, X.H.; Wen, K.; Wang, W.Y. Quantum secure direct communication and deterministic secure quantum communication. Front. Phys. China 2007, 2, 251–272. [Google Scholar] [CrossRef]
- Pan, D.; Song, X.T.; Long, G. Free-space quantum secure direct communication: Basics, progress, and outlook. Adv. Devices Instrum. 2023, 4, 0004. [Google Scholar] [CrossRef]
- Sheng, Y.B.; Zhou, L.; Long, G.L. One-step quantum secure direct communication. Sci. Bull. 2021, 67, 367–374. [Google Scholar] [CrossRef]
- Boyer, M.; Kenigsberg, D.; Mor, T. Quantum Key Distribution with Classical Bob. Phys. Rev. Lett. 2007, 99, 140501. [Google Scholar] [CrossRef]
- Tian, Y.; Li, J.; Chen, X.B.; Ye, C.Q.; Li, H.J. An efficient semi-quantum secret sharing protocol of specific bits. Quantum Inf. Process. 2021, 20, 217. [Google Scholar] [CrossRef]
- He, Z.; Lou, X. Security analysis and improvement in a semi-quantum private comparison without pre-shared key. Quantum Inf. Process. 2023, 22, 150. [Google Scholar] [CrossRef]
- Lian, J.Y.; Ye, T.Y. Hybrid protocols for multi-party semiquantum private comparison, multiplication and summation without a pre-shared key based on d-dimensional single-particle states. EPJ Quantum Technol. 2024, 11, 1–24. [Google Scholar] [CrossRef]
- Han, S.; Huang, Y.; Mi, S.; Qin, X.; Wang, J.; Yu, Y.; Wei, Z.; Zhang, Z. Proof-of-principle demonstration of semi-quantum key distribution based on the Mirror protocol. EPJ Quantum Technol. 2021, 8, 21. [Google Scholar] [CrossRef]
- Ye, T.Y.; Geng, M.J.; Xu, T.J.; Chen, Y. Efficient semiquantum key distribution based on single photons in both polarization and spatial-mode degrees of freedom. Quantum Inf. Process. 2022, 21, 123. [Google Scholar] [CrossRef]
- Zou, X.; Qiu, D. Three-step semiquantum secure direct communication protocol Science China Physics. Mech. Astron. 2014, 57, 1696–1702. [Google Scholar] [CrossRef]
- Gu, J.; Lin, P.H.; Hwang, T. Double C-NOT attack and counterattack on Three-step semi-quantum secure direct communication protocol. Quantum Inf. Process. 2018, 17, 182. [Google Scholar] [CrossRef]
- Wang, M.M.; Liu, J.L.; Gong, L.M. Semiquantum secure direct communication with authentication based on single-photons. Int. J. Quantum Inf. 2019, 17, 1950024. [Google Scholar] [CrossRef]
- Rong, Z.; Qiu, D.; Zou, X. Two single-state semi-quantum secure direct communication protocols based on single photons. Int. J. Mod. Phys. B 2020, 34, 2050106. [Google Scholar] [CrossRef]
- Rong, Z.; Qiu, D.; Zou, X. Semi-Quantum Secure Direct Communication Using Entanglement. Int. J. Theor. Phys. 2020, 59, 1807–1819. [Google Scholar] [CrossRef]
- Yang, Y.F.; Duan, L.Z.; Qiu, T.R.; Xie, X.M.; Duan, W.Y. Multi-party semi-quantum secure direct communication using Greenberger–Horne–Zeilinger states. Quantum Inf. Process. 2022, 21, 324. [Google Scholar] [CrossRef]
- Guo, H.; Li, Y.; Wei, J.; Tang, J.; Wang, J. Multi-party semi-quantum secure direct communication based on GHZ states. Chin. J. Quantum Electron. 2023, 40, 738. [Google Scholar]
- Xu, L.C.; Chen, H.Y.; Zhou, N.R.; Gong, L.H. Multi-party semi-quantum secure direct communication protocol with cluster states. Int. J. Theor. Phys. 2020, 59, 2175–2186. [Google Scholar] [CrossRef]
- Tian, Y.; Zhang, N.; Chang, J.; Li, J. Three-party semi-quantum secure direct communication based on two communication models. Phys. Scr. 2024, 99, 095110. [Google Scholar] [CrossRef]
- Zhang, M.H.; Li, H.F.; Xia, Z.Q.; Feng, X.Y.; Peng, J.Y. Semiquantum secure direct communication using EPR pairs. Quantum Inf. Process. 2017, 16, 117. [Google Scholar] [CrossRef]
- Yan, L.; Sun, Y.; Chang, Y.; Zhang, S.; Wan, G.; Sheng, Z. Semi-quantum protocol for deterministic secure quantum communication using Bell states. Quantum Inf. Process. 2018, 17, 315. [Google Scholar] [CrossRef]
- Xie, C.; Li, L.; Situ, H.; He, J. Semi-quantum Secure Direct Communication Scheme Based on Bell States. Int. J. Theor. Phys. 2018, 57, 1881–1887. [Google Scholar] [CrossRef]
- Sun, Y.; Yan, L.; Chang, Y.; Zhang, S.; Shao, T.; Zhang, Y. Two semi-quantum secure direct communication protocols based on Bell states. Mod. Phys. Lett. A 2019, 34, 1950004. [Google Scholar] [CrossRef]
- Li, X.H.; Deng, F.G.; Zhou, H.Y. Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 2006, 74, 361. [Google Scholar] [CrossRef]
- Deng, F.G.; Li, X.H.; Zhou, H.Y.; Zhang, Z.J. Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 2005, 72, 440–450. [Google Scholar] [CrossRef]




| Protocol | Efficiency (%) |
|---|---|
| Zou et al.’s protocol [26] | 18.2 |
| Gu et al.’s protocol [27] | 9.1 |
| Rong et al.’s protocol 1 [29] | 14.3 |
| Rong et al.’s protocol 2 [29] | 7.7 |
| Proposed protocol | 28.57 |
| Protocol | Quantum State | Efficiency (%) |
|---|---|---|
| Zou et al.’s protocol [26] | Single-photon | 18.2 |
| Zhang et al.’s protocol [35] | Bell states | 15.4 |
| Yan et al.’s protocol [36] | Bell states | 18.2 |
| Xie et al.’s protocol [37] | Bell states | 20 |
| Sun et al.’s protocol 1 [38] | Bell states | 10 |
| Sun et al.’s protocol 2 [38] | Bell states | 20 |
| Rong et al.’s protocol [30] | Bell states | 16.7 |
| Rong et al.’s protocol [30] | GHZ states | 12.5 |
| Guo et al.’s protocol [32] | GHZ states | 17.65–22.22 |
| Xu et al.’s protocol [33] | Cluster states | 18.5 |
| Proposed protocol | Single-photon | 28.57 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, Y.; Zhang, N.; Li, J. Two Novel Semi-Quantum Secure Direct Communication Protocols in IoT. Sensors 2024, 24, 7990. https://doi.org/10.3390/s24247990
Tian Y, Zhang N, Li J. Two Novel Semi-Quantum Secure Direct Communication Protocols in IoT. Sensors. 2024; 24(24):7990. https://doi.org/10.3390/s24247990
Chicago/Turabian StyleTian, Yuan, Nanyijia Zhang, and Jian Li. 2024. "Two Novel Semi-Quantum Secure Direct Communication Protocols in IoT" Sensors 24, no. 24: 7990. https://doi.org/10.3390/s24247990
APA StyleTian, Y., Zhang, N., & Li, J. (2024). Two Novel Semi-Quantum Secure Direct Communication Protocols in IoT. Sensors, 24(24), 7990. https://doi.org/10.3390/s24247990






