A Framework for Full Decentralization in Blockchain Interoperability
Abstract
1. Introduction
- A framework for decentralized blockchain interoperability is presented.
- A modified peer-to-peer (P2P) setup is presented as a communication link between two blockchains.
- The proposed P2P setup is tested to determine its computational impact.
2. Literature Review
2.1. Notary Schemes
2.2. HTLCs
2.3. Relays and Relay Chains
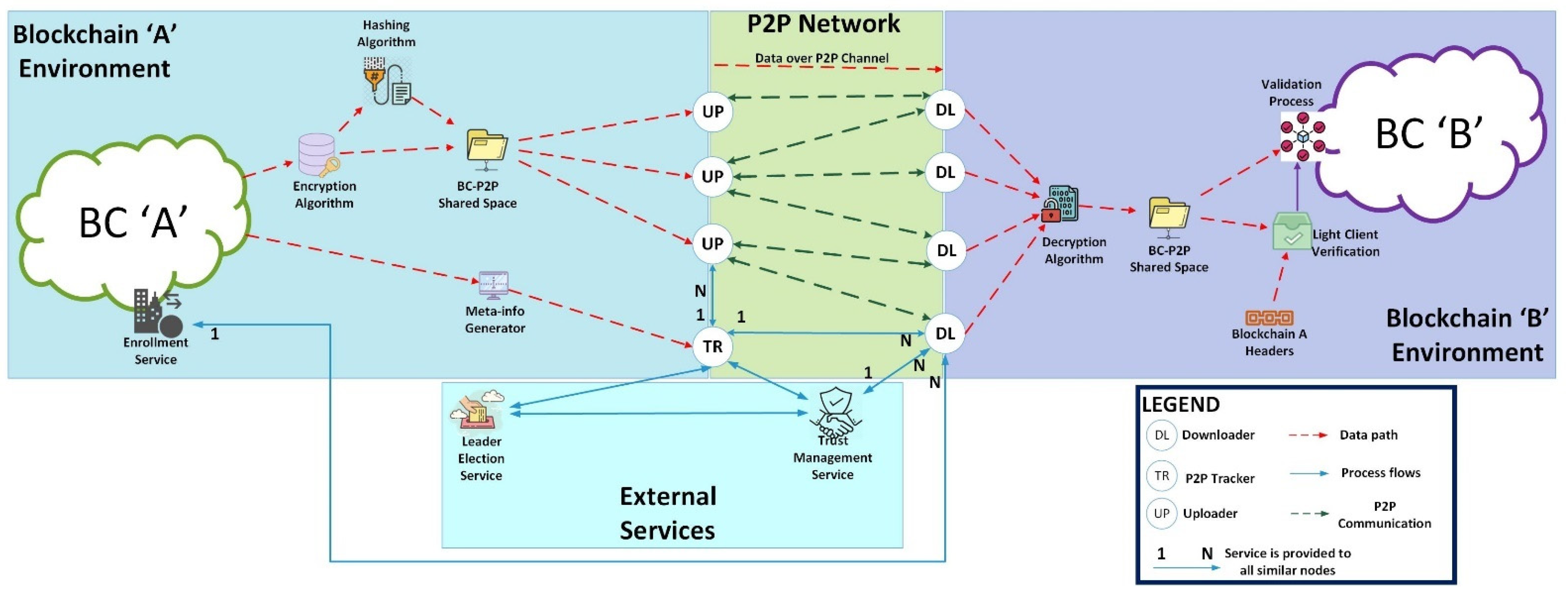
3. Proposed Framework
- Trustless: the proposed system should not rely on trusting any single entity to enable the success of interoperability. Blockchains work without trusting any single entity in the network. Eliminating the need for trust ensures that the data transferred between blockchains can be verified and validated by multiple nodes, and the destination blockchain does not depend on the trustworthiness of a single node.
- Decentralized: the proposed system should be built on a decentralized platform to ensure no single entity can dictate how interoperation is achieved. Furthermore, a decentralized system ensures multiple nodes participate in interoperation, making it easier to detect malicious nodes.
- Blockchain Agnostic: the proposed system should work between heterogenous blockchains without relying on their underlying frameworks. This would make it cross-blockchain compatible.
- Accountability: any action taken in the system should be traceable to the acting node. If a node acts maliciously, the actions of that node should be attributed to it, and a penalty given to that node. This requirement will help control the behavior of nodes in the network.
- Fault Tolerant: the proposed system should be able to continue functioning after the failure of some nodes. Multiple nodes should participate in the data transfer process to ensure that if some nodes fail, there will be other nodes to complete the process.
- Trustless: the use of a decentralized interface between the communicating blockchains ensures that no single node needs to be trusted. Validating by hash value and verifying data via light client verification by multiple nodes means that the operation of the system and the data being transferred do not depend on the trustworthiness of a single node.
- Decentralized: a P2P network provides a decentralized interface of communication between blockchains. The decentralized interface eliminates the need for having a centralized entity managing the interoperation process. This decentralized interface also makes the system more robust to attacks that target centralized systems.
- Blockchain Agnostic: the concept of blockchain gateways enables nodes to communicate without depending on the underlying blockchain frameworks. Communication between blockchains occurs at a level above the blockchain, removing dependency from the blockchain itself. This way, the data are retrieved and sent from the source blockchain, verified by the destination blockchain nodes and submitted to the destination in a way that is similar to how regular transactions are submitted.
- Accountability: a trust management service ensures that the actions of participating nodes are monitored and every action can be attributed to a particular node. Interactions between nodes are reported and offending nodes are given a penalty in the form of a reduction in trust score.
- Fault Tolerant: the participation of multiple nodes in the P2P network ensures that there is no single point of failure in the system. The failure of some nodes will not cause the system to fail. Multiple nodes in the network means that there are nodes always available to transfer and other nodes to receive data.
3.1. Peer-to-Peer Communication
3.2. Trust Management Service
3.3. Leader Election Algorithm
3.4. Encryption/Decryption Algorithm
3.5. Hashing Algorithm
3.6. Light Client Verification
4. Security Considerations and Theoretical Validation
4.1. Security Considerations
- DoS/DDoS Attacks: DoS/DDoS attacks attempt to disrupt the normal operation of a system by causing some nodes to go offline by flooding them with requests they cannot handle, causing them to crash. Flooding the node responsible for enabling interoperability will cause no actions to be taken as the node will be offline, preventing the transmission of data across blockchains. The P2P method of communication ensures that the flooding of some nodes will not affect the entire data transfer process, making the system resilient to these attacks.
- Sybil Attacks: a Sybil attack is an attack where an attacker creates multiple identities on the network to subvert the reputation system provided by the network. This attack is usually a pre-cursor to another attack. By managing multiple identities, the attacker can gain a larger influence on what occurs in the network. The use of light clients ensures that the participating nodes on the public blockchain are enrolled, thereby assigning a unique identity to all participants on the P2P network. Additionally, the TMS used in the architecture monitors the behavior of the nodes in the network and assigns them trust values. Nodes that exhibit malicious behavior have their trust value reduced.
- Single Point of Failure: A single point of failure in a system is a component of the system that prevents the entire system from functioning when that particular component stops functioning. The concept of blockchain gateways uses a node in a blockchain to connect to gateway nodes in other blockchains. A failure of this node means no communication between that node’s blockchain and other blockchains. We use multiple node gateways for communication to eliminate this single point of failure. The nodes in our architecture act independently, and a failure of one node does not affect the operation of the system. The use of a P2P network leader can also be a point of failure; however, a new leader is elected each time the leader fails, ensuring there is always a leader to perform the network managerial tasks.
- Man-in-the-Middle (MITM) attack: An MITM attack is where an attacker is positioned between two communicating parties and either listens in on their communication or actively attempts to subvert their communication. In this communication, an MITM may attempt to modify the data being transferred or inject malicious data as part of the data being transferred. The introduction of data encryption ensures that the data will be secured from modification in transit. Additionally, data verification by comparing hash values ensures that malicious data are not introduced in transit. As a final check, light client verification verifies the existence of all transactions received by the destination blockchain in the source blockchain. Any transaction that cannot be verified as existing on the source blockchain is discarded. This security feature ensures that only valid transactions are appended to the destination blockchain.
4.2. Theoretical Validation
- Confidentiality: data confidentiality protects the data from unintentional or unlawful access. The data being transferred over a communication channel needs to be secured to ensure unauthorized access. Any data that are not secured could lead to third parties performing other attacks like message modification or data injection attacks. To secure the data in transit, encryption is used. This security feature protects the data from being modified or false data being injected in transit. A lightweight encryption algorithm ensures that the data are secured before transmission whilst keeping the overhead in the system low.
- Integrity: data integrity maintains the accuracy and consistency of data over their entire usage. This security feature ensures that the data are not corrupted intentionally or unintentionally whilst in transit. A hashing algorithm creates a hash of the data before transmission. A new hash of the data is then generated and compared with the original hash, and if it matches, the data are valid. Hashing is used in our architecture to ensure that the data remain consistent as they are transferred from the source blockchain to the destination blockchain.
- Availability: data availability ensures that the data are readily available to users and applications when they are required. Having many sources of data distributed over the network ensure that the data are always available. A P2P network ensures that there are multiple nodes with data and that the failure of one node does not affect availability of data over the network.
- Decentralization: decentralization ensures that no single entity has sole authority in a system. Blockchains are inherently decentralized, and this trait ensures that no single node can dictate what occurs in the network. We maintain that property by using a partially managed P2P network as the interface between the two blockchains. This network ensures that no single entity can take over and dictate how the data move through the network. The network leader that we use in the partially managed network is only responsible for network management tasks to make communication more efficient and therefore cannot dictate how the network operates. This feature keeps the network decentralized whilst enabling an efficient communication process.
5. Peer-to-Peer Setup Evaluation
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/en/bitcoin-paper (accessed on 16 June 2022).
- Habib, G.; Sharma, S.; Ibrahim, S.; Ahmad, I.; Qureshi, S.; Ishfaq, M. Blockchain Technology: Benefits, Challenges, Applications, and Integration of Blockchain Technology with Cloud Computing. Future Internet 2022, 14, 341. [Google Scholar] [CrossRef]
- Falazi, G.; Breitenbücher, U.; Daniel, F.; Lamparelli, A.; Leymann, F.; Yussupov, V. Smart Contract Invocation Protocol (SCIP): A Protocol for the Uniform Integration of Heterogeneous Blockchain Smart Contracts BT—Advanced Information Systems Engineering; Springer International Publishing: Cham, Switzerland, 2020; pp. 134–149. [Google Scholar]
- Pillai, B.; Biswas, K.; Muthukkumarasamy, V. Blockchain Interoperable Digital Objects. In Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2019; Volume 11521, pp. 80–94. [Google Scholar] [CrossRef]
- Xiong, A.; Liu, G.; Zhu, Q.; Jing, A.; Loke, S.W. A notary group-based cross-chain mechanism. Digit. Commun. Netw. 2022, 8, 1059–1067. [Google Scholar] [CrossRef]
- Hewett, N.; Lehmacher, W.; Wang, Y. Inclusive Deployment of Blockchain for Supply Chains; World Economic Forum: Cologny, Switzerland, 2019; p. 26. Available online: https://www.weforum.org/whitepapers/inclusive-deployment-of-blockchain-for-supply-chains-part-6-a-framework-for-blockchain-interoperability (accessed on 13 February 2022).
- Abdelmaboud, A.; Ahmed, A.I.A.; Abaker, M.; Eisa, T.A.E.; Albasheer, H.; Ghorashi, S.A.; Karim, F.K. Blockchain for IoT Applications: Taxonomy, Platforms, Recent Advances, Challenges and Future Research Directions. Electronics 2022, 11, 630. [Google Scholar] [CrossRef]
- Hardjono, T.; Lipton, A.; Pentland, A. Towards a Design Philosophy for Interoperable Blockchain Systems. arXiv 2018, arXiv:1805.05934. Available online: http://arxiv.org/abs/1805.05934 (accessed on 18 November 2021).
- Hardjono, T.; Lipton, A.; Pentland, A. Toward an Interoperability Architecture for Blockchain Autonomous Systems. IEEE Trans. Eng. Manag. 2020, 67, 1298–1309. [Google Scholar] [CrossRef]
- Buterin, V. Chain Interoperability. R3 Res. Pap. 2016, 9, 1–25. [Google Scholar]
- Ray, S. Blockchain Interoperability; Towards Data Science: Toronto, ON, Canada, 2018; Available online: https://towardsdatascience.com/blockchain-interoperability-33a1a55fe718 (accessed on 12 May 2022).
- Scheid, E.J.; Hegnauer, T.; Rodrigues, B.; Stiller, B. Bifröst: A Modular Blockchain Interoperability API. In Proceedings of the 2019 IEEE 44th Conference on Local Computer Networks (LCN), Osnabrueck, Germany, 14–17 October 2019; pp. 332–339. [Google Scholar]
- Gao, Z.; Li, H.; Xiao, K.; Wang, Q. Cross-chain oracle based data migration mechanism in heterogeneous blockchains. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 29 November–1 December 2020; pp. 1263–1268. [Google Scholar] [CrossRef]
- Punathumkandi, S.; Sundaram, V.M.; Panneer, P. Interoperable permissioned-blockchain with sustainable performance. Sustainability 2021, 13, 11132. [Google Scholar] [CrossRef]
- Herlihy, M. Atomic Cross-Chain Swaps. In Proceedings of the 2018 ACM Symposium on Principles of Distributed Computing, Egham, UK, 23–27 July 2018. [Google Scholar] [CrossRef]
- Miraz, M.H.; Donald, D.C. Atomic Cross-chain Swaps: Development, Trajectory and Potential of Non-monetary Digital Token Swap Facilities. arXiv 2019, arXiv:1902.04471. [Google Scholar] [CrossRef]
- Zamyatin, A.; Harz, D.; Lind, J.; Panayiotou, P.; Gervais, A.; Knottenbelt, W. XCLAIM: Trustless, Interoperable, Cryptocurrency-Backed Assets. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; pp. 193–210. [Google Scholar] [CrossRef]
- Wanchain Foundation. Wanchain: Building Super Financial Markets for the New Digital Economy. White Paper Version 0.9.1. 2018, pp. 1–34. Available online: https://www.wanchain.org/files/Wanchain-Whitepaper-EN-version.pdf (accessed on 17 February 2022).
- Barbàra, F.; Schifanella, C. MP-HTLC: Enabling blockchain interoperability through a multiparty implementation of the hash time-lock contract. Concurr. Comput. Pract. Exp. 2023, 35, e7656. [Google Scholar] [CrossRef]
- Puneeth, R.P.; Parthasarathy, G. Seamless Data Exchange: Advancing Healthcare with Cross-Chain Interoperability in Blockchain for Electronic Health Records. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 280–289. [Google Scholar] [CrossRef]
- Schulte, S.; Sigwart, M.; Frauenthaler, P.; Borkowski, M. Towards Blockchain Interoperability. In Business Process Management: Blockchain and Central and Eastern Europe Forum: BPM 2019 Blockchain and CEE Forum, Vienna, Austria, 1–6 September 2019; Lecture Notes in Business Information Processing; Springer International Publishing: Cham, Switzerland, 2019; Volume 361, pp. 3–10. [Google Scholar] [CrossRef]
- BTC RELAY. Available online: http://btcrelay.org/ (accessed on 23 June 2022).
- Wood, G. An Introduction to Polkadot. 2020. Available online: https://assets.polkadot.network/Polkadot-lightpaper.pdf (accessed on 3 October 2024).
- Verdian, G.; Tasca, P.; Paterson, C.; Mondelli, G. Quant Overledger Whitepaper. 2018. Available online: https://discovery.ucl.ac.uk/id/eprint/10179663/1/Quant-Overledger-v0.1-Whitepaper.pdf (accessed on 3 October 2024).
- Liu, Z.; Xiang, Y.; Shi, J.; Gao, P.; Wang, H.; Xiao, X.; Wen, B.; Hu, Y.C. Hyperservice: Interoperability and programmability across heterogeneous blockchains. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 549–566. [Google Scholar] [CrossRef]
- Frauenthaler, P.; Sigwart, M.; Spanring, C.; Schulte, S. Testimonium: A Cost-Efficient Blockchain Relay. arXiv 2020, arXiv:2002.12837. [Google Scholar] [CrossRef]
- Bentov, I.; Ji, Y.; Zhang, F.; Breidenbach, L.; Daian, P.; Juels, A. Tesseract: Real-Time Cryptocurrency Exchange Using Trusted Hardware. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 1521–1538. [Google Scholar]
- Jin, H.; Dai, X.; Xiao, J. Towards a novel architecture for enabling interoperability amongst multiple blockchains. In Proceedings of the 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS), Vienna, Austria, 2–6 July 2018; pp. 1203–1211. [Google Scholar] [CrossRef]
- Fynn, E.; Bessani, A.; Pedone, F. Smart Contracts on the Move. In Proceedings of the 2020 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Valencia, Spain, 29 June–2 July 2020; pp. 233–244. [Google Scholar] [CrossRef]
- Belchior, R.; Vasconcelos, A.; Correia, M.; Hardjono, T. HERMES: Fault-tolerant middleware for blockchain interoperability. Future Gener. Comput. Syst. 2022, 129, 236–251. [Google Scholar] [CrossRef]
- Darshan, M.; Amet, M.; Srivastava, G.; Crichigno, J. An Architecture That Enables Cross-Chain Interoperability for Next-Gen Blockchain Systems. IEEE Internet Things J. 2023, 10, 18282–18291. [Google Scholar] [CrossRef]
- Karumba, S.; Jurdak, R.; Kanhere, S.S.; Sethuvenkatraman, S. BAILIF: A Blockchain Agnostic Interoperability Framework. In Proceedings of the 2023 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Dubai, United Arab Emirates, 1–5 May 2023; pp. 1–9. [Google Scholar] [CrossRef]
- Hardjono, T. Blockchain Gateways, Bridges and Delegated Hash-Locks. arXiv 2021, arXiv:2102.03933. Available online: http://arxiv.org/abs/2102.03933 (accessed on 5 May 2022).
- Liu, Z.; Xiang, Y.; Shi, J.; Gao, P.; Wang, H.; Xiao, X.; Wen, B.; Li, Q.; Hu, Y.C. Make Web3.0 Connected. IEEE Trans. Dependable Secur. Comput. 2021, 19, 2965–2981. [Google Scholar] [CrossRef]
- Evangelista, P.; Amaral, M.; Miers, C.; Goya, W.; Simplicio, M.; Carvalho, T.; Souza, V. EbitSim: An enhanced BitTorrent simulation using OMNeT++ 4. In Proceedings of the 2011 IEEE 19th Annual International Symposium on Modelling, Analysis, and Simulation of Computer and Telecommunication Systems, Singapore, 25–27 July 2011; pp. 437–440. [Google Scholar] [CrossRef]
- Toole, R.; Vokkarane, V. BitTorrent Architecture and Protocol; University of Massachusetts Dartmouth: Dartmouth, MA, USA, 2006; pp. 1–6. Available online: https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=be5aaaec88323f3a6e1c63033cca92095b2972ac (accessed on 3 October 2024).
- Kermarrec, A.M.; Taïani, F. Want to scale in centralized systems? Think P2P. J. Internet Serv. Appl. 2015, 6, 16. [Google Scholar] [CrossRef]
- Androutsellis-Theotokis, S.; Spinellis, D. A survey of peer-to-peer content distribution technologies. ACM Comput. Surv. 2004, 36, 335–371. [Google Scholar] [CrossRef]
- Krishnan, M.A.; Shankar, C.G.; Raj, S.A.; Ragavan, A. Peer to Peer File Sharing by Blockchain Using IOT. Int. J. Sci. Res. Sci. Eng. Technol. 2017, 2, 91–94. [Google Scholar]
- Pourebrahimi, B.; Bertels, K.; Vassiliadis, S. A Survey of Peer-to-Peer Networks. In Proceedings of the 16th Annual Workshop on Circuits, Systems and Signal Processing, Rome, Italy, 20–22 June 2024. [Google Scholar]
- Mekouar, L.; Iraqi, Y.; Boutaba, R. Reputation-Based Trust Management in Peer-to-Peer Systems: Taxonomy and Anatomy; Springer: Boston, MA, USA, 2010. [Google Scholar]
- Balhara, S.; Khanna, K. Leader Election Algorithms in Distributed Systems. Int. J. Comput. Sci. Mob. Comput. 2014, 3, 374–379. [Google Scholar]
- Ongaro, D.; Ousterhout, J. In search of an understandable consensus algorithm. In Proceedings of the 2014 USENIX Annual Technical Conference (USENIX ATC), Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- Mahto, D.; Khan, D.A.; Yadav, D.K. Security analysis of elliptic Curve cryptography and RSA. In Proceedings of the World Congress on Engineering 2016, London, UK, 29 June–1 July 2016; Lecture Notes in Engineering and Computer Science. Volume 2223, pp. 419–422. [Google Scholar]
- Amara, M.; Siad, A. Elliptic Curve Cryptography and its applications. In Proceedings of the International Workshop on Systems, Signal Processing and Their Applications, WoSSPA, Tipaza, Algeria, 9–11 May 2011; pp. 247–250. [Google Scholar] [CrossRef]
- Prashant, P. Pittalia A Comparative Study of Hash Algorithms in Cryptography. Int. J. Comput. Sci. Mob. Comput. 2019, 8, 147–152. Available online: https://ijcsmc.com/docs/papers/June2019/V8I6201928.pdf (accessed on 5 June 2022).
- Thomas, C.G.; Jose, R.T. A Comparative Study on Different Hashing Algorithms. Int. J. Innov. Res. Comput. Commun. Eng. (An ISO Certif. Organ.) 2015, 3297, 170–175. Available online: www.ijircce.com (accessed on 7 June 2022).
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G.; Van Keer, R.; Viguier, B. KangarooTwelve: Fast hashing based on KECCAK-p. In Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2018; Volume 10892, pp. 400–418. [Google Scholar] [CrossRef]
- Wright, C.S. Merkle Trees and SPV. 2019. Available online: https://craigwright.net/blog/bitcoin-blockchain-tech/merkle-trees-and-spv/ (accessed on 19 June 2022).
- Wright, C.S. On Merkle Trees. 2019. Available online: https://craigwright.net/wp-content/uploads/2019/11/On-Merkle-Trees_CSW.pdf (accessed on 19 June 2022).






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kotey, S.D.; Tchao, E.T.; Agbemenu, A.S.; Ahmed, A.-R.; Keelson, E. A Framework for Full Decentralization in Blockchain Interoperability. Sensors 2024, 24, 7630. https://doi.org/10.3390/s24237630
Kotey SD, Tchao ET, Agbemenu AS, Ahmed A-R, Keelson E. A Framework for Full Decentralization in Blockchain Interoperability. Sensors. 2024; 24(23):7630. https://doi.org/10.3390/s24237630
Chicago/Turabian StyleKotey, Seth Djanie, Eric Tutu Tchao, Andrew Selasi Agbemenu, Abdul-Rahman Ahmed, and Eliel Keelson. 2024. "A Framework for Full Decentralization in Blockchain Interoperability" Sensors 24, no. 23: 7630. https://doi.org/10.3390/s24237630
APA StyleKotey, S. D., Tchao, E. T., Agbemenu, A. S., Ahmed, A.-R., & Keelson, E. (2024). A Framework for Full Decentralization in Blockchain Interoperability. Sensors, 24(23), 7630. https://doi.org/10.3390/s24237630






