Heuristic Optimal Scheduling for Road Traffic Incident Detection Under Computational Constraints
Abstract
:1. Introduction
- This study introduces a heuristic optimal configuration and scheduling method for traffic anomaly detection, designed to maximize the efficiency of traffic event detection. By calculating the weighted event feature value for each camera to represent its detection efficiency, the method dynamically adjusts camera resource allocation based on detection requirements. This adaptive dynamic scheduling approach effectively addresses the limitations of static allocation models, avoiding resource wastage or insufficiency and enhancing overall detection performance.
- An innovative cyclic elimination mechanism is introduced. This process identifies and removes low-performing cameras based on their detection efficiency within each cycle, and resources are redistributed from inactive cameras. This mechanism facilitates the continuous optimization of resource utilization across multiple cycles, thereby enhancing the flexibility and adaptability of computational resource scheduling.
2. Related Work
3. Methodology
3.1. Preliminaries
- Temporal Attribute t: This refers to the specific time at which a traffic incident occurs. To facilitate data analysis, traffic incident data are often segmented into time windows T, that is, traffic incident data statistics are processed every T hour.
- Type Attribute l: This refers to the specific category of a traffic incident, such as pedestrians on highways, traffic congestion, and abnormal parking:where M denotes the number of traffic incident types.
- Spatial Attribute s: This refers to the specific geographic location where a traffic incident occurs. In this study, the approximate location of the incident is determined by utilizing the geographic coordinates of the monitoring camera:where N denotes the number of traffic surveillance cameras on the highway.
3.2. Overall Efficiency of Traffic Incident Detection
- To simplify the analysis, it is assumed, without loss of generality, that the computational cost of each traffic incident detection algorithm is the same across all cameras. This means that deploying any type of algorithm on any camera incurs the same computational overhead, denoted by r. Assuming that all cameras can deploy M types of incident detection algorithms, the maximum number of surveillance cameras that can be deployed using all M types of incident detection algorithms is n . In addition, a status value of 1 is assigned to surveillance cameras if they have deployed detection algorithms, while those without such algorithms are assigned a value of 0.
- Based on prior knowledge, such as business requirements or expert evaluation, the significance of the j-th type of incident is defined by , where ; denotes the number of j-type traffic incidents detected by the i-th camera.
- The weighted sum of the numbers of various abnormal incidents detected by each camera within a time window T is defined as follows:where denotes the number of algorithms deployed on the i-th camera and denotes the effective incident detection efficiency of the i-th camera.
- Furthermore, the average effective incident detection efficiency of all cameras with deployed algorithms is defined as the OETID for this time window and is calculated as follows:where denotes the number of cameras. This study aims to maximize the OETID within computational constraints, with a specific focus on maximizing the average number of effective incident detections. To accomplish this objective, the following function can be derived:
3.3. Proposed Method
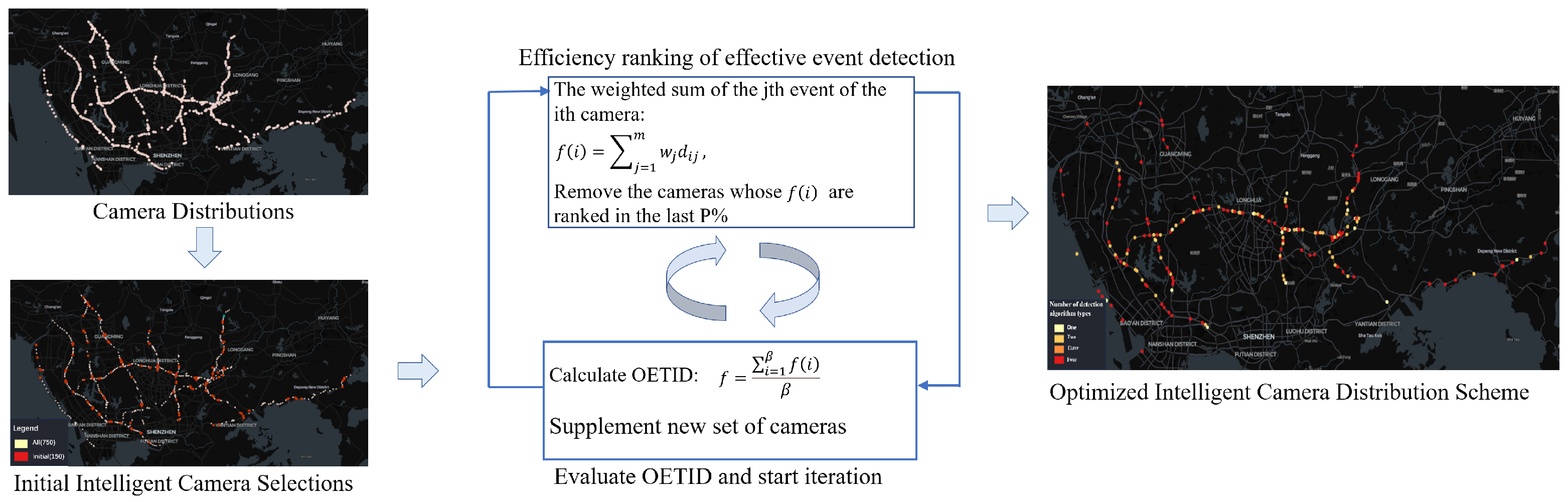
- Set a time window T (e.g., 00:00–06:00). Based on prior knowledge or expert experience, heuristically and randomly select n cameras from the initial N cameras during the first round. Deploy all M types of detection algorithms on each selected camera, ensuring that all computational resources are fully allocated. This is calculated as: . Additionally, mark all cameras that have been configured with algorithms as 1.
- Calculate the effective event detection efficiency of each camera with deployed algorithms over a cycle (e.g., one week). For all cameras with deployed algorithms, if , it indicates that the j-th type of algorithm is no longer deployed on the i-th camera. Consequently, the freed-up computational resources can be reallocated to other relevant event types on different cameras, thereby maximizing the utilization of limited computational resources.
- Sort the obtained effective event detection efficiencies in descending order. Remove the cameras corresponding to the bottom (where P denotes a specified value, typically in the range (0, 20]), and calculate the remaining computational resources , where denotes the number of cameras with the deployed detection algorithms. Furthermore, calculate the OETID for the top cameras.
- Enter the next cycle. Select cameras (where denotes the ceiling function) from those marked as 0, and deploy all M types of detection algorithms on each selected camera to ensure that all remaining computational resources are fully allocated. Mark these cameras as 1. Use steps (2) and (3) to calculate the OETID for the top cameras in this cycle (where denotes the OETID for cycle C).
- If the designated number of cycles is reached or all cameras are marked as 1, complete the optimization, exit the loop, and terminate the iteration. After the algorithm iteration is concluded, sort the obtained weighted event feature values in descending order and remove the cameras corresponding to the bottom of effective event detection efficiency. To maximize the utilization of computational resources, the saved computational resources can be dynamically allocated by relevant personnel based on experience and urgency of tasks.
- In the next time window T (e.g., 06:00–12:00), repeat steps (1)–(5) until all time windows T are fully optimized.
| Algorithm 1 Pseudo Code of Dynamic Computing Resource Allocation |
|
4. Experimental Analysis
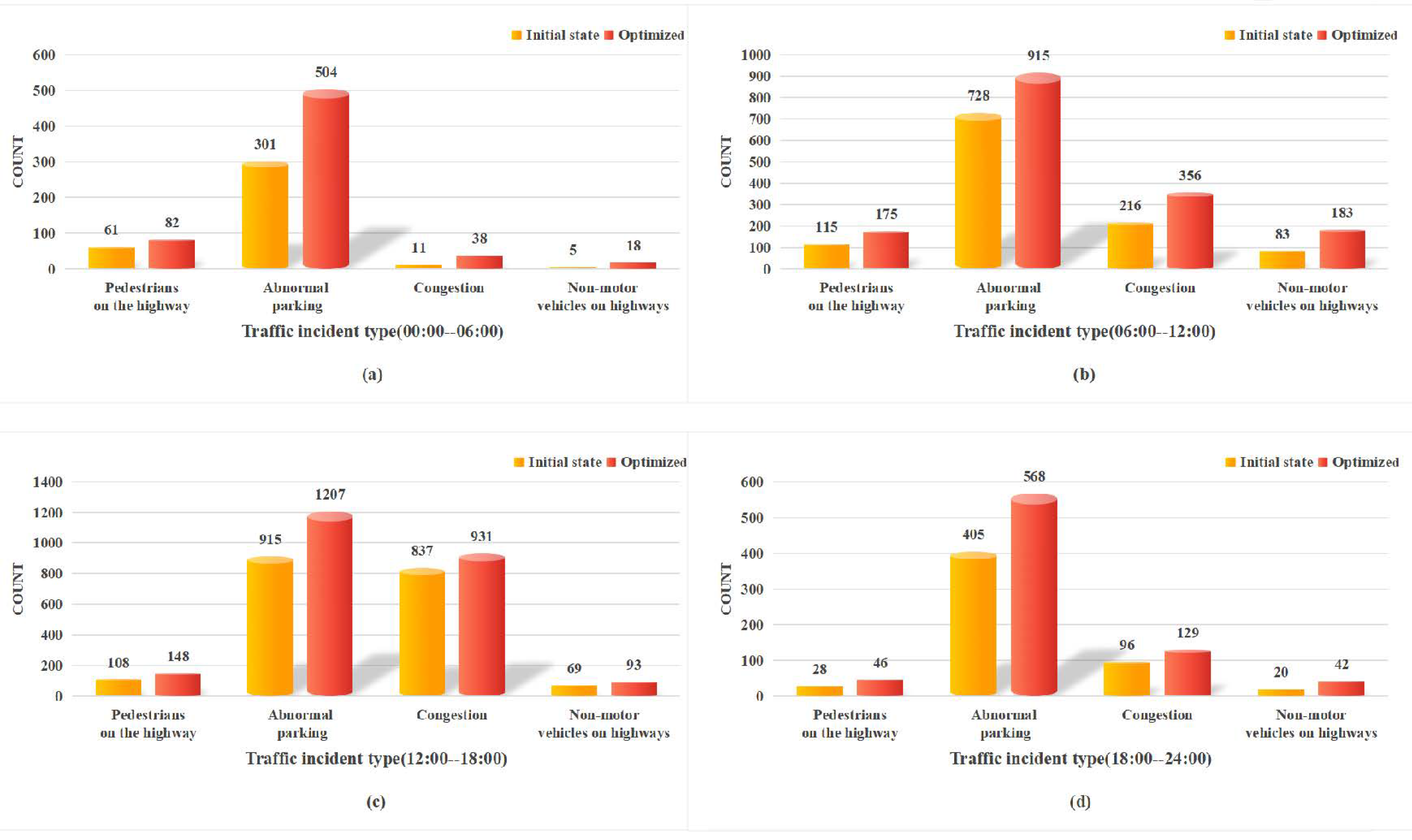
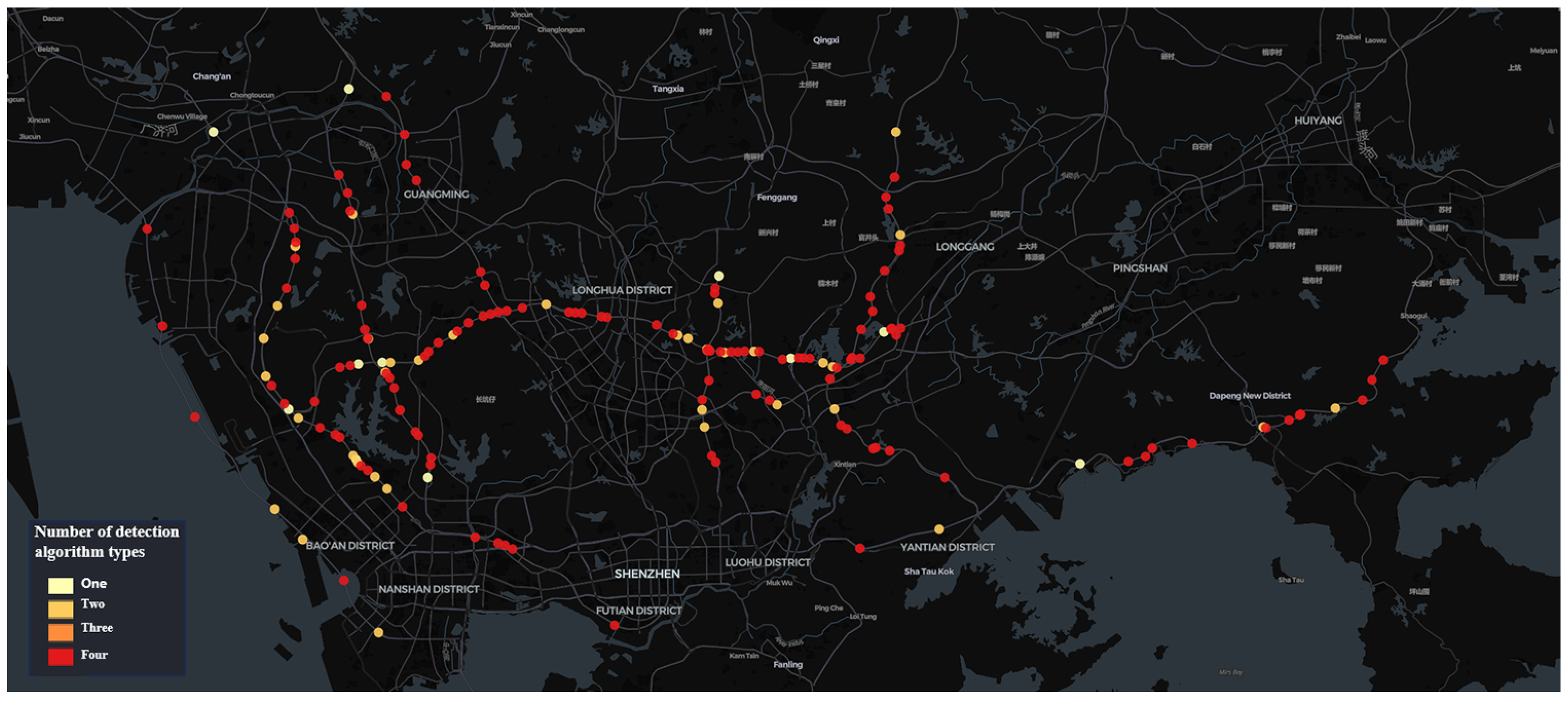
4.1. Data and Processing
4.2. Data Evaluation Metrics
4.3. Experimental Results and Analysis
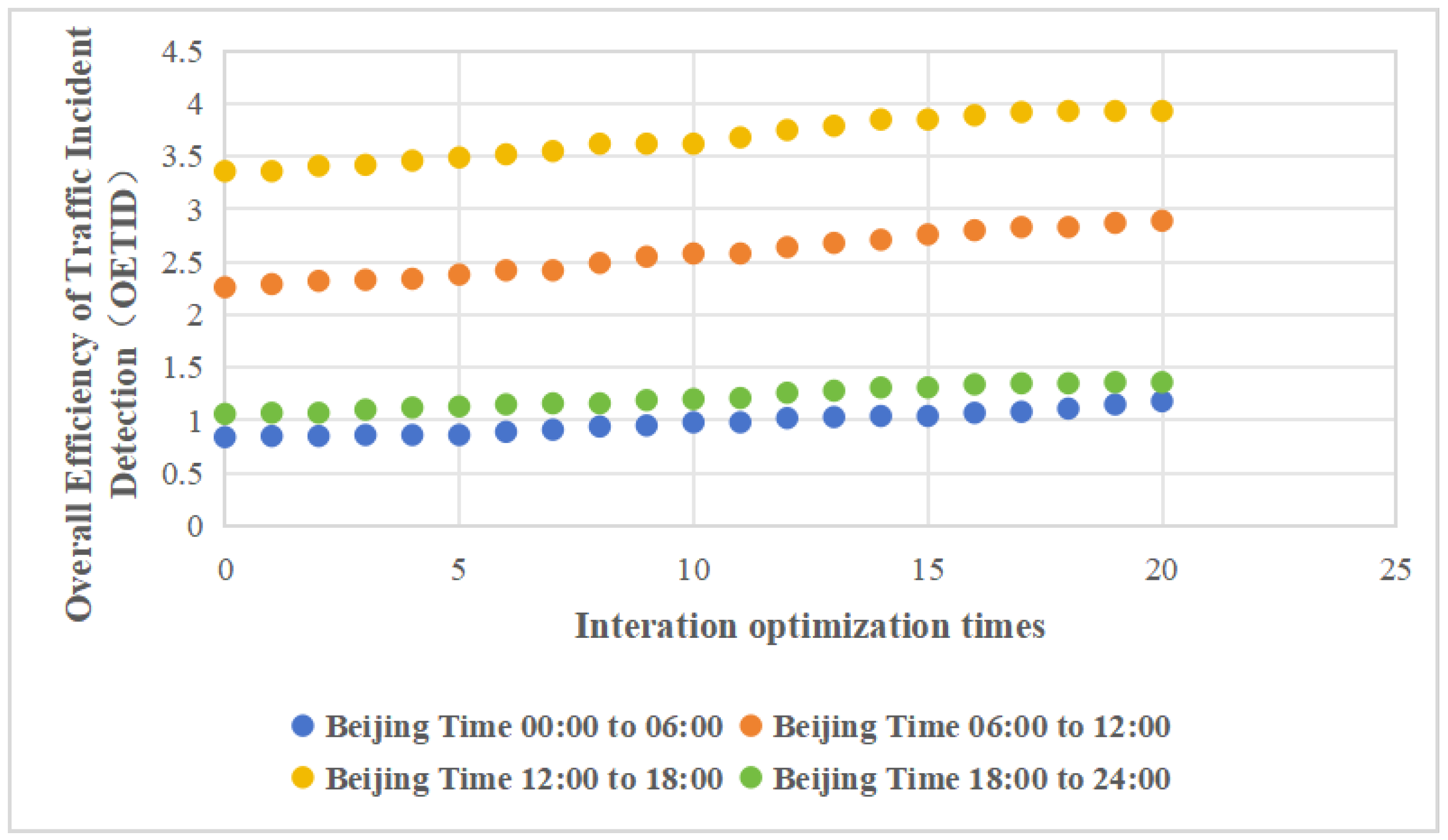
- With each successive iteration, the OETID within the four time windows demonstrated steady improvement. This indicates that continuous optimization iterations can enhance the identification of traffic incidents, even under the constraints of limited computational resources.
- Throughout the iterative optimization process, the rankings of detection efficiency for the four time windows consistently remain in descending order: 12:00–18:00, 06:00–12:00, 18:00–24:00, and 00:00–06:00. The detection efficiency during the time window 12:00–18:00 is significantly higher, while the efficiency during time windows 18:00–24:00 and 00:00–06:00 are relatively similar. This indicates that the efficiency of traffic incident detection is greatly influenced by the time of day, underscoring the need for an optimization method tailored to different times.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Jiyang, B.; Zhang, X.; Sun, L. Traffic incident duration prediction grounded on Bayesian decision method-based tree algorithm. J. Tongji Univ. (Nat. Sci.) 2008, 36, 319. [Google Scholar]
- Wang, X.; Che, Z.; Jiang, B.; Xiao, N.; Yang, K.; Tang, J.; Ye, J.; Wang, J.; Qi, Q. Robust unsupervised video anomaly detection by multipath frame prediction. IEEE Trans. Neural Netw. Learn. Syst. 2021, 33, 2301–2312. [Google Scholar] [CrossRef]
- Shehata, M.S.; Cai, J.; Badawy, W.M.; Burr, T.W.; Pervez, M.S.; Johannesson, R.J.; Radmanesh, A. Video-based automatic incident detection for smart roads: The outdoor environmental challenges regarding false alarms. IEEE Trans. Intell. Transp. Syst. 2008, 9, 349–360. [Google Scholar] [CrossRef]
- Azfar, T.; Li, J.; Yu, H.; Cheu, R.L.; Lv, Y.; Ke, R. Deep learning-based computer vision methods for complex traffic environments perception: A review. Data Sci. Transp. 2024, 6, 1. [Google Scholar] [CrossRef]
- Maaloul, B.; Taleb-Ahmed, A.; Niar, S.; Harb, N.; Valderrama, C. Adaptive video-based algorithm for accident detection on highways. In Proceedings of the 2017 12th IEEE International Symposium on Industrial Embedded Systems, Toulouse, France, 14–16 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Karim, M.M.; Li, Y.; Qin, R. Toward explainable artificial intelligence for early anticipation of traffic accidents. Transp. Res. Rec. 2022, 2676, 743–755. [Google Scholar] [CrossRef]
- Adewopo, V.A.; Elsayed, N.; ElSayed, Z.; Ozer, M.; Wangia-Anderson, V.; Abdelgawad, A. AI on the Road: A Comprehensive Analysis of Traffic Accidents and Accident Detection System in Smart Cities. arXiv 2023, arXiv:2307.12128. [Google Scholar]
- Zhihang, X.; Xinpeng, Y.; Zhigang, X.; Xiaobo, Q. Review of Research on Road Traffic Detectors and Its Optimized Deployment Methods. J. South China Univ. Technol. (Nat. Sci. Ed.) 2023, 51, 68–88. [Google Scholar]
- Sun, X.; Bai, Z.; Lin, K.; Jiao, P.; Lu, H. Optimization model of traffic sensor layout considering traffic big data. J. Adv. Transp. 2020, 2020, 8845832. [Google Scholar] [CrossRef]
- Cao, X.; Zhang, Z.; Sun, Y.; Wang, P.; Xu, S.; Liu, F.; Wang, C.; Peng, F.; Mu, S.; Liu, Y. The review of image processing and edge computing for intelligent transportation system. J. Image Graph. 2022, 27, 1743–1767. [Google Scholar] [CrossRef]
- Wan, S.; Xu, X.; Wang, T.; Gu, Z. An intelligent video analysis method for abnormal event detection in intelligent transportation systems. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4487–4495. [Google Scholar] [CrossRef]
- Ma, Y.; Wu, Z.; Xu, Z.; Zhong, L.; Xu, C. Optimization of task scheduling for computing reuse in computing power network. J. Commun. 2023, 44, 129–142. [Google Scholar]
- Jia, Q.; Ding, R.; Liu, H.; Zhang, C.; Xie, R. Survey on research progress for compute first networking. Chin. J. Netw. Inf. Secur. 2021, 7, 1–12. [Google Scholar]
- Mijuskovic, A.; Chiumento, A.; Bemthuis, R.; Aldea, A.; Havinga, P. Resource management techniques for cloud/fog and edge computing: An evaluation framework and classification. Sensors 2021, 21, 1832. [Google Scholar] [CrossRef]
- Micko, K.; Papcun, P.; Zolotova, I. Review of IoT sensor systems used for monitoring the road infrastructure. Sensors 2023, 23, 4469. [Google Scholar] [CrossRef]
- Xingyou, Q.; Zhihang, X.; Bin, T.; Jinchuan, W.; Lijuan, L.; Shibei, D. Research on optimal layout method of perceptive equipment on intelligent highway side. Electron. Des. Eng. 2023, 31, 11–15+20. [Google Scholar] [CrossRef]
- Li, Y.; Cheng, Z.; Yao, X.; Kong, Z.; Wang, Z.; Liu, M. Multi-Objective Optimal Deployment of Road Traffic Monitoring Cameras: A Case Study in Wujiang, China. Sustainability 2023, 15, 12011. [Google Scholar] [CrossRef]
- Qichun, B.; Bowen, G.; Ciyun, L.; Zhaosheng, Y. Traffic incident automatic detection algorithm for urban expressway. J. Cent. South Univ. (Sci. Technol.) 2017, 48, 1682–1687. [Google Scholar]
- Li, L.; Lin, Y.; Du, B.; Yang, F.; Ran, B. Real-time traffic incident detection based on a hybrid deep learning model. Transp. A Transp. Sci. 2022, 18, 78–98. [Google Scholar] [CrossRef]
- Yan, S.; Smith, J.S.; Lu, W.; Zhang, B. Abnormal event detection from videos using a two-stream recurrent variational autoencoder. IEEE Trans. Cogn. Dev. Syst. 2018, 12, 30–42. [Google Scholar] [CrossRef]
- Singh, D.; Mohan, C.K. Deep spatio-temporal representation for detection of road accidents using stacked autoencoder. IEEE Trans. Intell. Transp. Syst. 2018, 20, 879–887. [Google Scholar] [CrossRef]
- Yan, H.; Li, Y. A Survey of Generative AI for Intelligent Transportation Systems. arXiv 2023, arXiv:2312.08248. [Google Scholar]
- Qiu, L.; Zhang, D.; Tian, Y.; Al-Nabhan, N. Deep learning-based algorithm for vehicle detection in intelligent transportation systems. J. Supercomput. 2021, 77, 11083–11098. [Google Scholar] [CrossRef]
- Vishnu, S.; Ramanadhan, U.; Vasudevan, N.; Ramachandran, A. Vehicular collision avoidance using video processing and vehicle-to-infrastructure communication. In Proceedings of the 2015 International Conference on Connected Vehicles and Expo, Shenzhen, China, 19–23 October 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 387–388. [Google Scholar]
- Hasarinda, R.; Tharuminda, T.; Palitharathna, K.; Edirisinghe, S. Traffic Collision Avoidance with Vehicular Edge Computing. In Proceedings of the 2023 3rd International Conference on Advanced Research in Computing (ICARC), Belihuloya, Sri Lanka, 23–24 February 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 316–321. [Google Scholar]
- Lee, S.; Lee, S.; Noh, J.; Kim, J.; Jeong, H. Special traffic event detection: Framework, dataset generation, and deep neural network perspectives. Sensors 2023, 23, 8129. [Google Scholar] [CrossRef] [PubMed]
- Xu, Z.; Wang, X. A modified round-robin load-balancing algorithm for cluster-based web servers. In Proceedings of the 33rd Chinese Control Conference, Nanjing, China, 28–30 July 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 3580–3584. [Google Scholar]
- Kang, L.; Ting, X. Application of adaptive load balancing algorithm based on minimum traffic in cloud computing architecture. In Proceedings of the 2015 International Conference on Logistics, Informatics and Service Sciences (LISS), Barcelona, Spain, 27–29 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1–5. [Google Scholar]
- Ge, J.W.; Guo, Q.; Fang, Y.Q. A Multi-objective Optimization Algorithm for Cloud Computing Task Scheduling Based on Improved Ant Colony Algorithm. Microelectron. Comput. 2017, 34, 63–67. [Google Scholar]
- Han, H.; Liu, Y.; Hou, Y.; Qiao, J. Multi-modal multi-objective particle swarm optimization with self-adjusting strategy. Inf. Sci. 2023, 629, 580–598. [Google Scholar] [CrossRef]




| Incident Type | Pedestrians on Highways | Abnormal Parking | Traffic Congestion | Non-Motorized Vehicles on Highways |
|---|---|---|---|---|
| Weight | 0.42 | 0.24 | 0.15 | 0.19 |
| Camera Location | Pedestrians on Highways | Abnormal Parking | Traffic Congestion | Non-Motorized Vehicles on Highways | Detection Efficiency |
|---|---|---|---|---|---|
| 1 | 4 | 15 | 10 | 6 | 7.92 |
| 2 | 0 | 6 | 8 | 4 | 3.4 |
| 3 | 5 | 26 | 24 | 8 | 13.46 |
| 4 | 0 | 5 | 8 | 3 | 2.97 |
| 5 | 1 | 4 | 1 | 2 | 1.91 |
| … | … | … | … | … | … |
| Time Window | Before Optimization | After Optimization | Improvement |
|---|---|---|---|
| 00:00–06:00 | 0.84 | 1.18 | 40% |
| 06:00–12:00 | 2.26 | 2.89 | 28% |
| 12:00–18:00 | 3.36 | 3.93 | 17% |
| 18:00–24:00 | 1.06 | 1.36 | 28% |
| Time Window Interval | Overall Efficiency of Traffic Incident Detection (f) | Average Load Degree (U) | Load Balance Degree () | Computational Resource Utilization () |
|---|---|---|---|---|
| 00:00–06:00 | 1.18 | 3.45 | 7.44 | 97.50% |
| 06:00–12:00 | 2.89 | 8.11 | 14.57 | 98.17% |
| 12:00–18:00 | 3.93 | 11.68 | 35.73 | 94.83% |
| 18:00–24:00 | 1.36 | 4.29 | 21.40 | 97.33% |
| Method Name | Average Load Degree (U) | Load Balance Degree () | Computational Resource Utilization () |
|---|---|---|---|
| Static Round-Robin Scheduling | 4.25 | 37.43 | 77.22% |
| Weighted Round-Robin Scheduling | 5.78 | 25.32 | 89.67% |
| Priority Round-Robin Scheduling | 5.52 | 29.65 | 85.34% |
| Heuristic Adaptive Scheduling | 6.88 | 19.78 | 96.96% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, H.; Yang, J.; Yuan, M.-D.; Li, X. Heuristic Optimal Scheduling for Road Traffic Incident Detection Under Computational Constraints. Sensors 2024, 24, 7221. https://doi.org/10.3390/s24227221
Wu H, Yang J, Yuan M-D, Li X. Heuristic Optimal Scheduling for Road Traffic Incident Detection Under Computational Constraints. Sensors. 2024; 24(22):7221. https://doi.org/10.3390/s24227221
Chicago/Turabian StyleWu, Hao, Jiahao Yang, Ming-Dong Yuan, and Xin Li. 2024. "Heuristic Optimal Scheduling for Road Traffic Incident Detection Under Computational Constraints" Sensors 24, no. 22: 7221. https://doi.org/10.3390/s24227221
APA StyleWu, H., Yang, J., Yuan, M.-D., & Li, X. (2024). Heuristic Optimal Scheduling for Road Traffic Incident Detection Under Computational Constraints. Sensors, 24(22), 7221. https://doi.org/10.3390/s24227221






