A Deep Cryptographic Framework for Securing the Healthcare Network from Penetration
Abstract
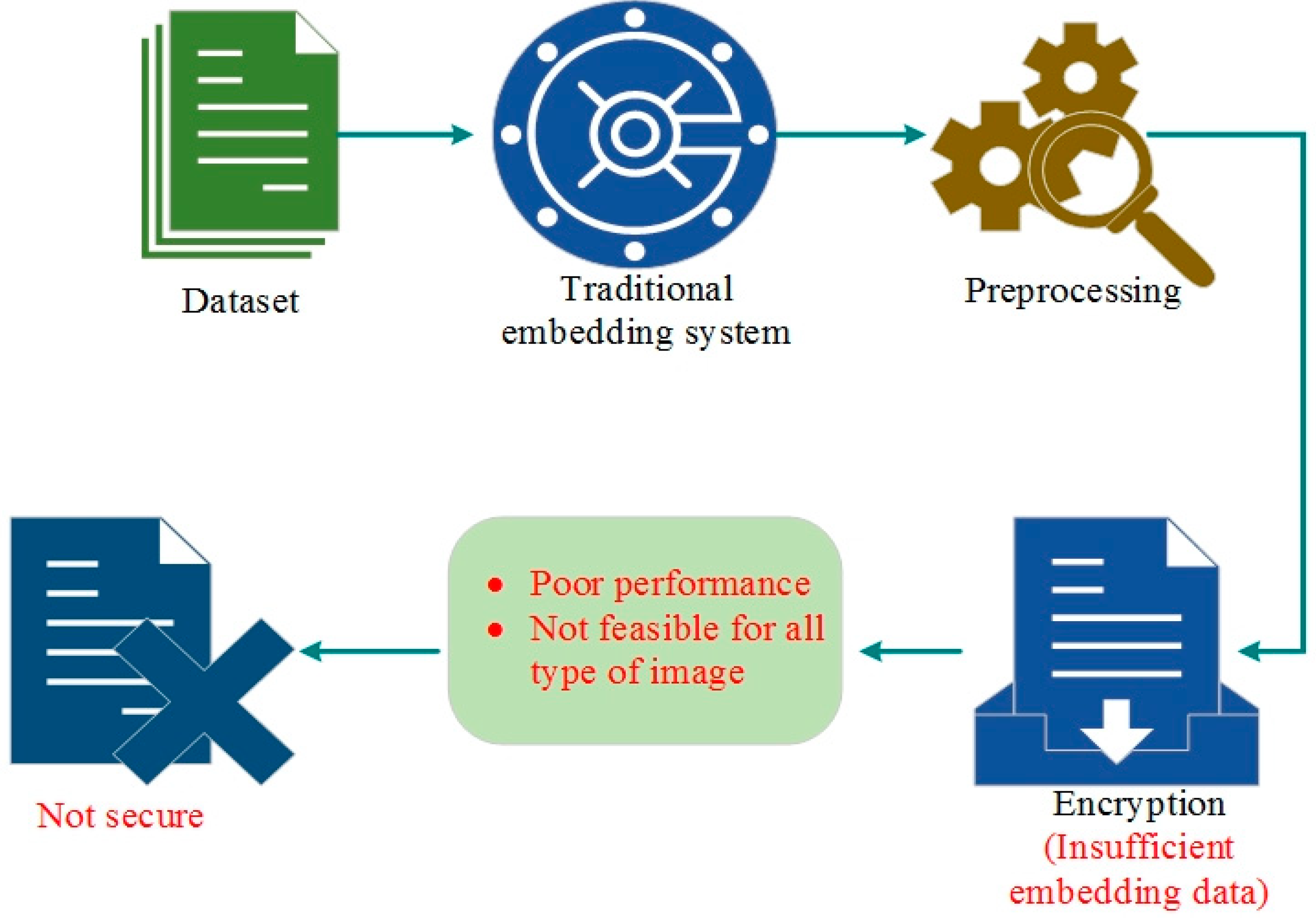
1. Introduction
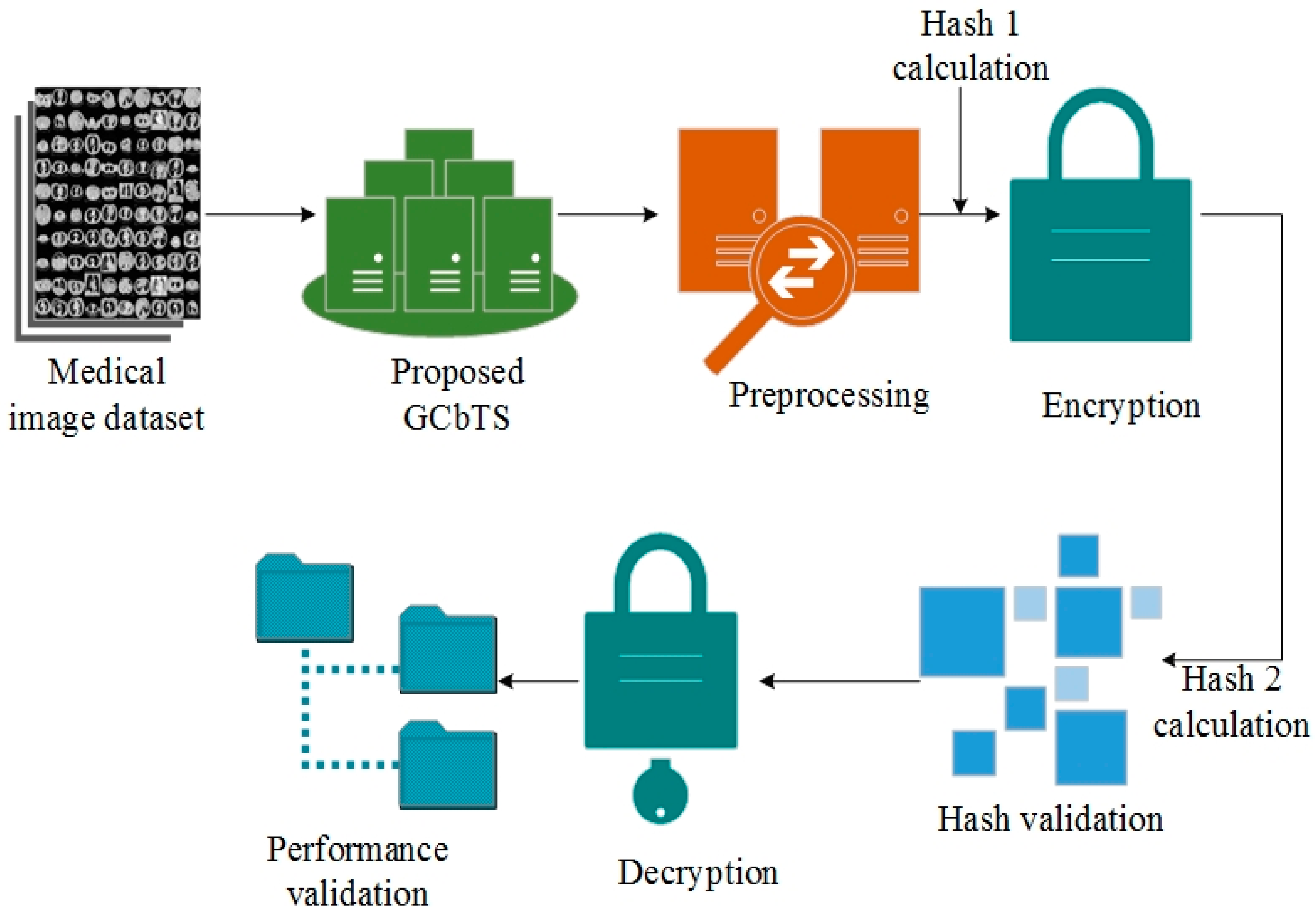
- Initially, medical image data were evaluated and trained according to the Python system;
- Consequently, a novel GCbTS is designed with the required crypto-security constraints;
- Henceforth, the hash 1 is found, and the data are encrypted and kept in an unreadable format;
- A hash 2 calculation is done to decrypt the data, verifying whether hash 1 is equal to hash 2;
- If hash 1 and hash 2 are equal, the secret key is shared for decryption;
- Finally, metrics like encryption and decryption time, PSNR, MSE, error rate, and computation time are compared with other models.
2. Related Work
3. System Model and Problem Statement
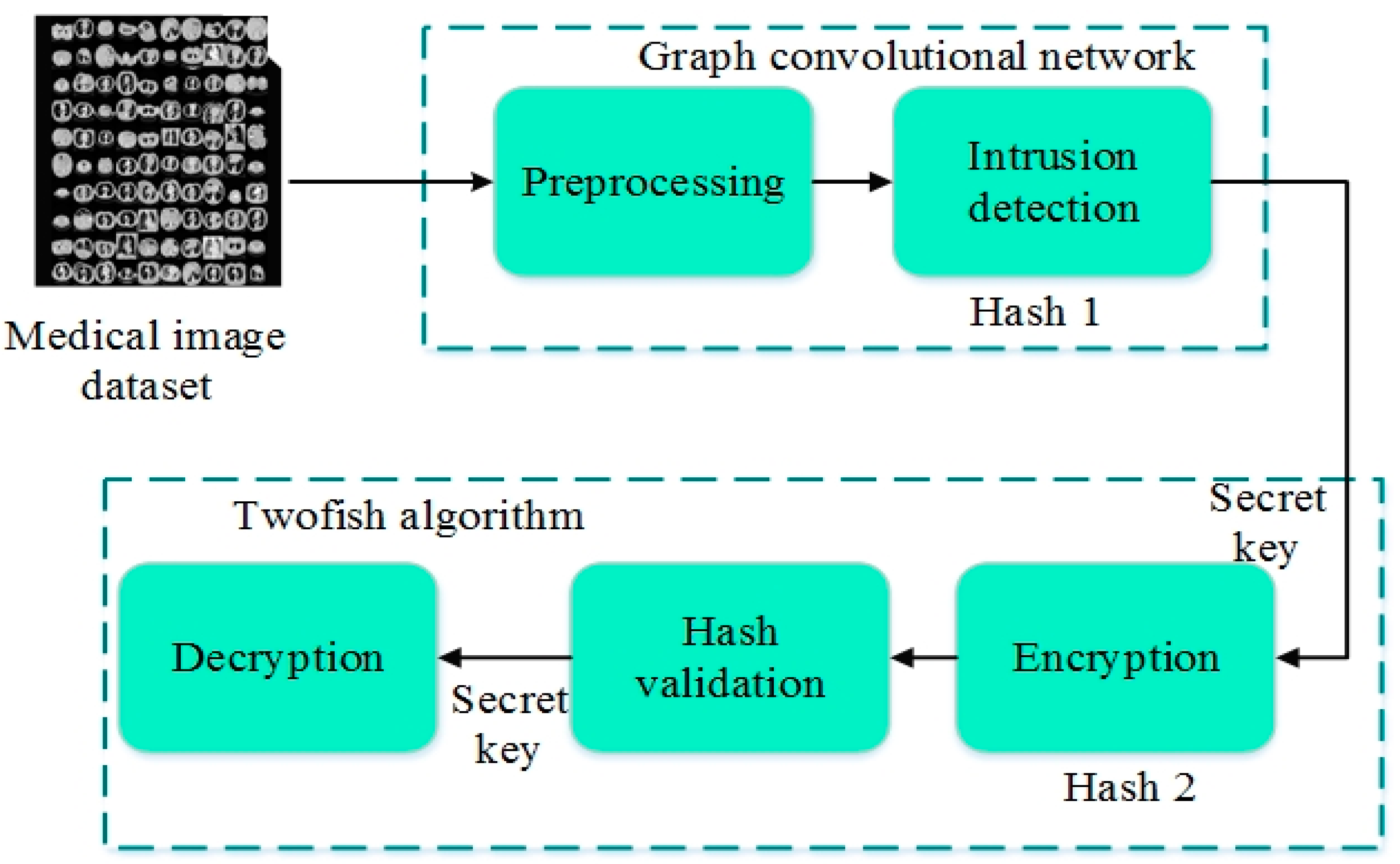
4. Proposed GCbTS to Secure the Healthcare Network Data
| Algorithm 1 Graph Convolutional-Based TwoFish Security (GCbTS) |
| Start |
| { |
| int |
| //initialization of input digital video dataset |
|
Preprocessing() { |
| int P,,, |
| //Preprocessing variables are initialized. |
| //Noises are removed. |
| Hash 1 calculation () |
| { |
| int , |
| // The hash 1 value is estimated and stored in the framework. |
| //Input videos are split into the types of frames. |
| } |
| Encryption() |
| { |
|
Int
,, |
| //By twofish algorithm, the images are encrypted and assembled. |
| } |
| Hash 2 calculation() |
| { |
| // The hash 1 value is computed for encrypted data. |
| } |
| Hash validation() |
| { |
| if |
| { |
|
//Verification is successful, and the system sends encrypted data along with key. |
| } |
| } |
| Decryption() |
| { |
| //Encrypted data are retrieved into their original form. |
| } |
| } |
| Stop |
4.1. Process of GCbTS Model
4.1.1. Data Initialization and Preprocessing
4.1.2. Encryption
4.1.3. Hash Verification
4.1.4. Decryption
5. Result and Discussion
5.1. Case Study
5.2. Performance Analysis
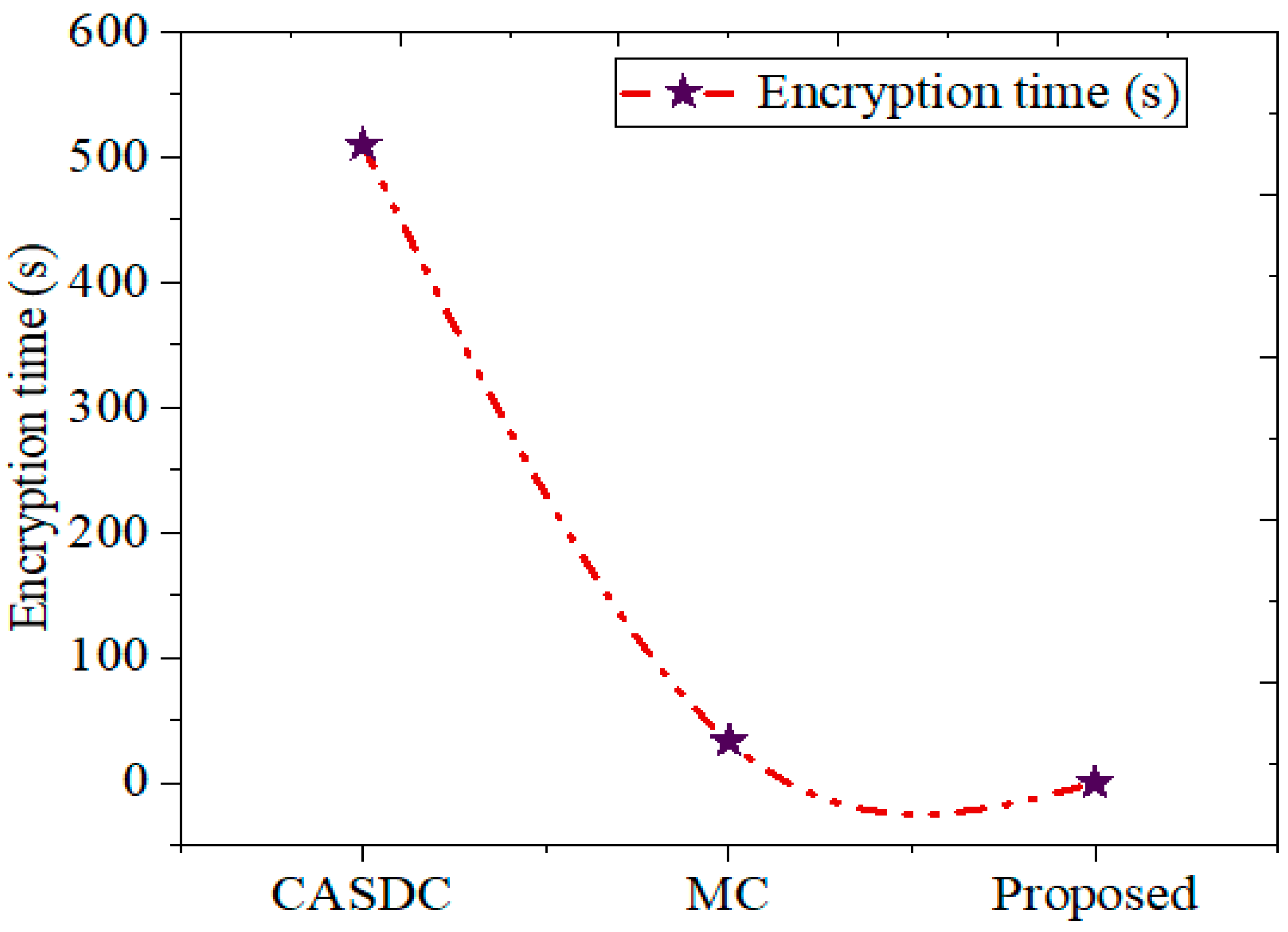
5.2.1. Encryption Time
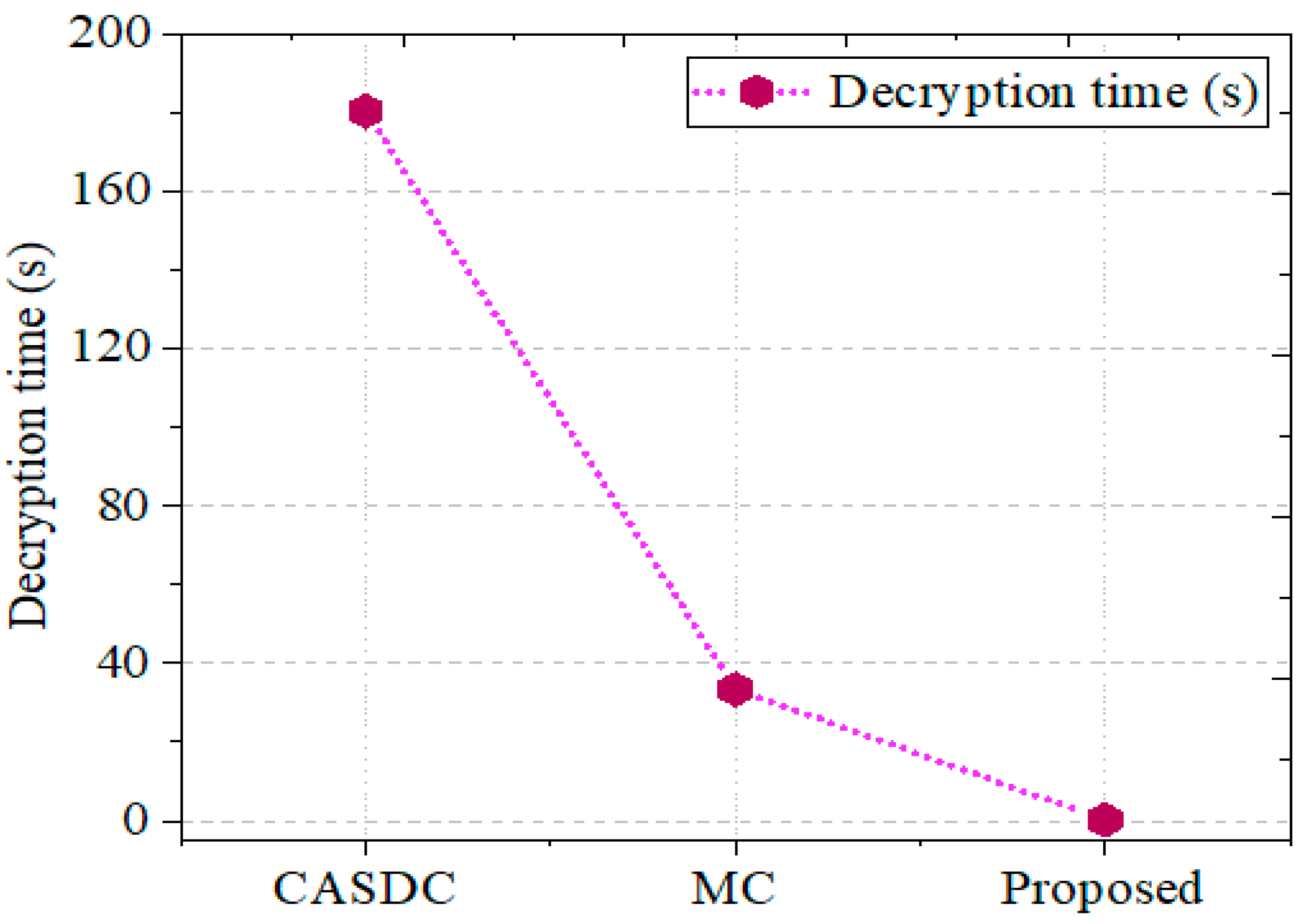
5.2.2. Decryption Time
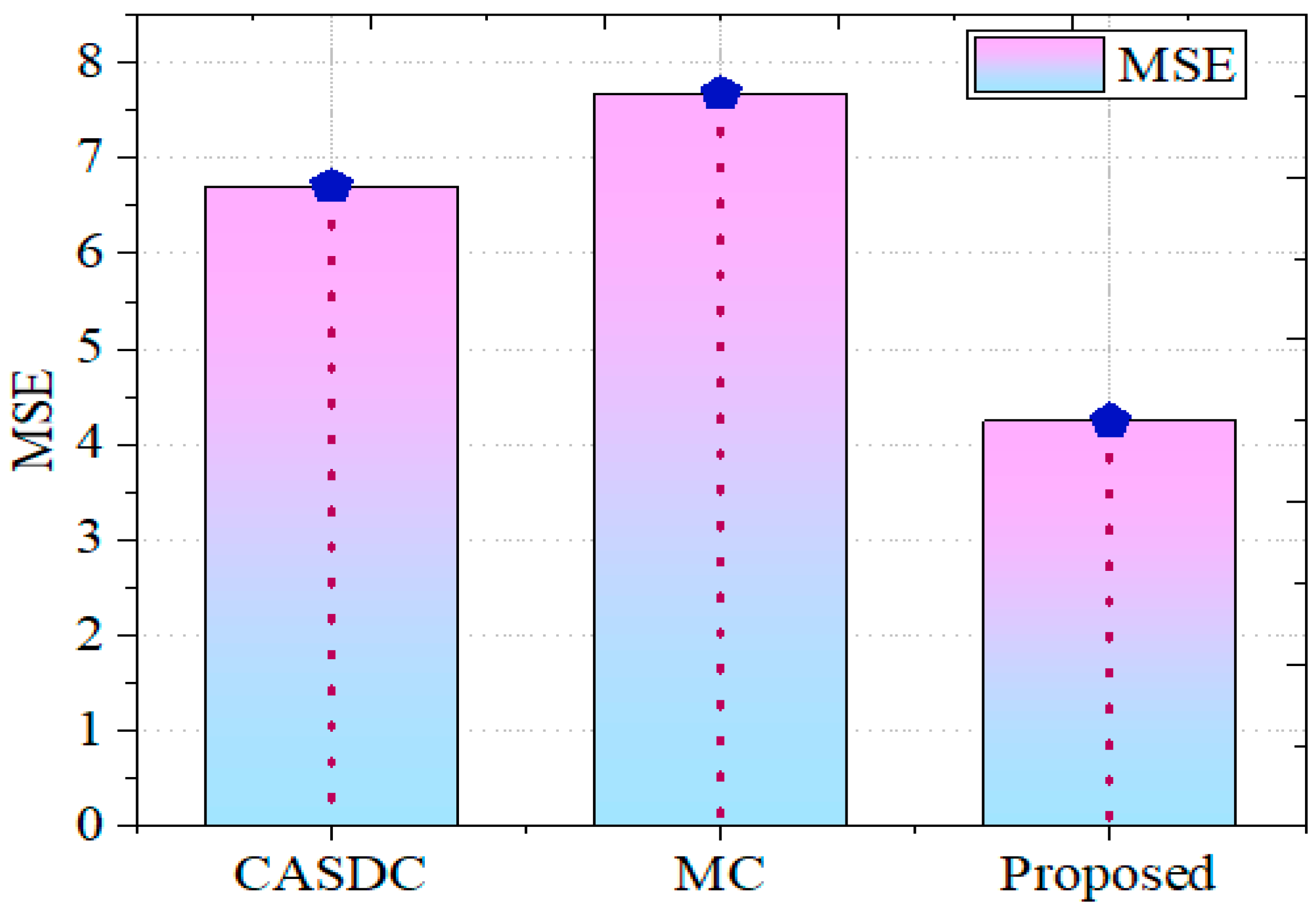
5.2.3. MSE
5.2.4. PSNR
5.2.5. Throughput
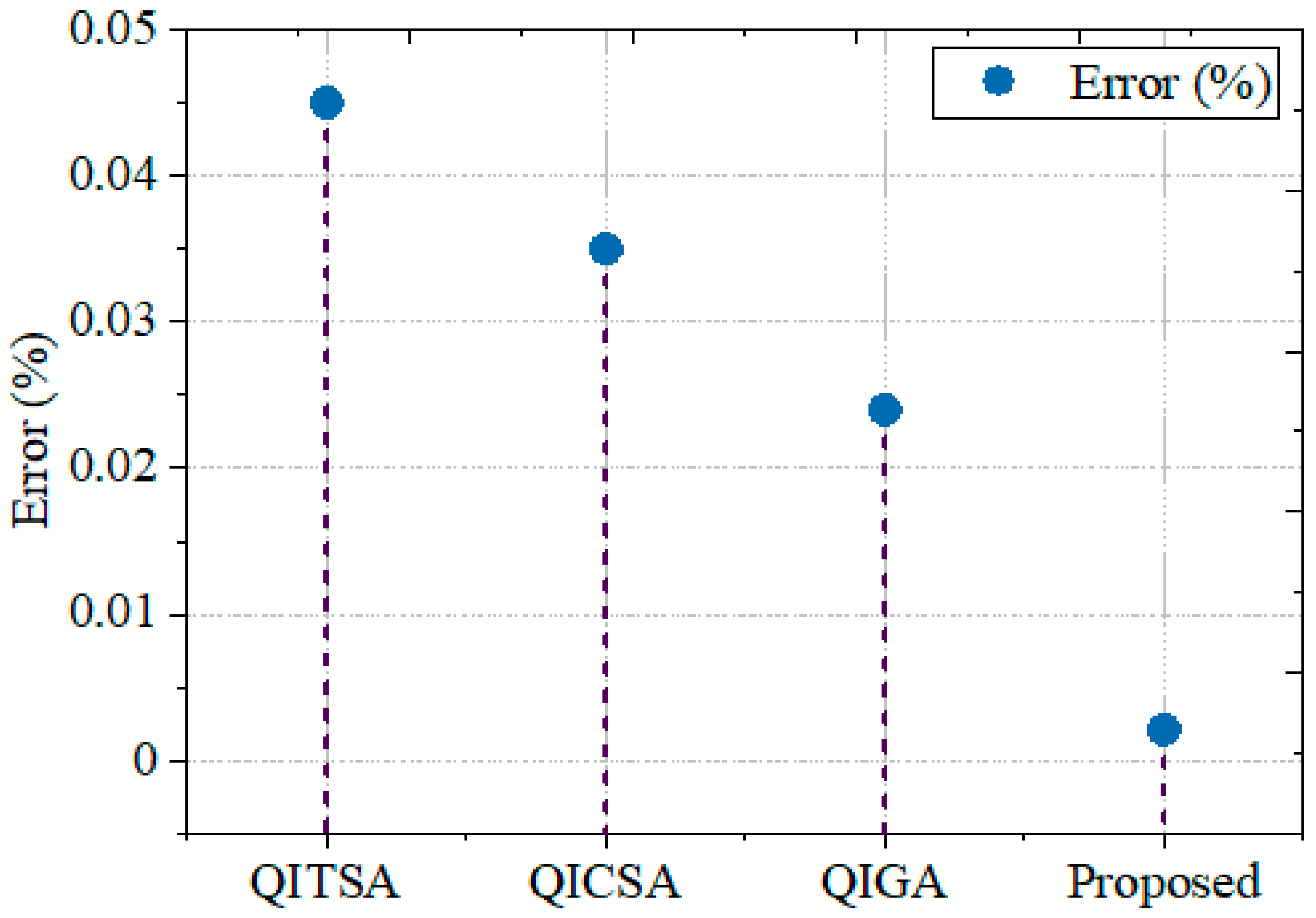
5.2.6. Error Rate
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Oosthoek, K.; Doerr, C. Cyber Security Threats to Bitcoin Exchanges: Adversary Exploitation and Laundering Techniques. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1616–1628. [Google Scholar] [CrossRef]
- Zhang, H.; Wang, J.; Wang, Y.; Li, M.; Song, J.; Liu, Z. ICVTest: A Practical Black-Box Penetration Testing Framework for Evaluating Cybersecurity of Intelligent Connected Vehicles. Appl. Sci. 2023, 14, 204. [Google Scholar] [CrossRef]
- Tamburri, D.A. Design principles for the General Data Protection Regulation (GDPR): A formal concept analysis and its evaluation. Inf. Syst. 2020, 91, 101469. [Google Scholar] [CrossRef]
- Tudosi, A.-D.; Graur, A.; Balan, D.G.; Potorac, A.D. Research on Security Weakness Using Penetration Testing in a Distributed Firewall. Sensors 2023, 23, 2683. [Google Scholar] [CrossRef] [PubMed]
- Bella, G.; Biondi, P.; Bognanni, S.; Esposito, S. PETIoT: PEnetration Testing the Internet of Things. Internet Things 2023, 22, 100707. [Google Scholar] [CrossRef]
- Altulaihan, E.A.; Alismail, A.; Frikha, M. A Survey on Web Application Penetration Testing. Electronics 2023, 12, 1229. [Google Scholar] [CrossRef]
- Cirne, A.; Sousa, P.R.; Resende, J.S.; Antunes, L. IoT security certifications: Challenges and potential approaches. Comput. Secur. 2022, 116, 102669. [Google Scholar] [CrossRef]
- Iqbal, F.; Debbabi, M.; Fung, B.C.M.; Iqbal, F.; Debbabi, M.; Fung, B.C.M. Cybersecurity and Cybercrime Investigation. In Machine Learning for Authorship Attribution and Cyber Forensics; Springer: Cham, Switzerland, 2020; pp. 1–21. [Google Scholar] [CrossRef]
- Filiol, E.; Mercaldo, F.; Santone, A. A Method for Automatic Penetration Testing and Mitigation: A Red Hat Approach. Procedia Comput. Sci. 2021, 192, 2039–2046. [Google Scholar] [CrossRef]
- Alhamed, M.; Rahman, M.M.H. A Systematic Literature Review on Penetration Testing in Networks: Future Research Directions. Appl. Sci. 2023, 13, 6986. [Google Scholar] [CrossRef]
- Aslan, Ö.; Aktuğ, S.S.; Ozkan-Okay, M.; Yilmaz, A.A.; Akin, E. A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions. Electronics 2023, 12, 1333. [Google Scholar] [CrossRef]
- Yaacoub, J.-P.A.; Noura, H.N.; Salman, O.; Chehab, A. Ethical hacking for IoT: Security issues, challenges, solutions and recommendations. Internet Things Cyber-Physical Syst. 2023, 3, 280–308. [Google Scholar] [CrossRef]
- Rak, M.; Salzillo, G.; Granata, D. ESSecA: An automated expert system for threat modelling and penetration testing for IoT ecosystems. Comput. Electr. Eng. 2022, 99, 107721. [Google Scholar] [CrossRef]
- Zhang, J.; Pan, L.; Han, Q.-L.; Chen, C.; Wen, S.; Xiang, Y. Deep Learning Based Attack Detection for Cyber-Physical System Cybersecurity: A Survey. IEEE/CAA J. Autom. Sin. 2021, 9, 377–391. [Google Scholar] [CrossRef]
- Saheed, Y.K.; Abiodun, A.I.; Misra, S.; Holone, M.K.; Colomo-Palacios, R. A machine learning-based intrusion detection for detecting internet of things network attacks. Alex. Eng. J. 2022, 61, 9395–9409. [Google Scholar] [CrossRef]
- Riggs, H.; Tufail, S.; Parvez, I.; Tariq, M.; Khan, M.A.; Amir, A.; Vuda, K.V.; Sarwat, A.I. Impact, Vulnerabilities, and Mitigation Strategies for Cyber-Secure Critical Infrastructure. Sensors 2023, 23, 4060. [Google Scholar] [CrossRef]
- Kure, H.I.; Islam, S.; Mouratidis, H. An integrated cyber security risk management framework and risk predication for the critical infrastructure protection. Neural Comput. Appl. 2022, 34, 15241–15271. [Google Scholar] [CrossRef]
- Cao, S.; Sun, X.; Bo, L.; Wei, Y.; Li, B. BGNN4VD: Constructing Bidirectional Graph Neural-Network for Vulnerability Detection. Inf. Softw. Technol. 2021, 136, 106576. [Google Scholar] [CrossRef]
- Wartschinski, L.; Noller, Y.; Vogel, T.; Kehrer, T.; Grunske, L. VUDENC: Vulnerability Detection with Deep Learning on a Natural Codebase for Python. Inf. Softw. Technol. 2022, 144, 106809. [Google Scholar] [CrossRef]
- Prabakaran, S.; Ramar, R.; Hussain, I.; Kavin, B.P.; Alshamrani, S.S.; AlGhamdi, A.S.; Alshehri, A. Predicting Attack Pattern via Machine Learning by Exploiting Stateful Firewall as Virtual Network Function in an SDN Network. Sensors 2022, 22, 709. [Google Scholar] [CrossRef]
- Ghanem, M.C.; Chen, T.M.; Nepomuceno, E.G. Hierarchical reinforcement learning for efficient and effective automated penetration testing of large networks. J. Intell. Inf. Syst. 2022, 60, 281–303. [Google Scholar] [CrossRef]
- Preetha, A.D.; Kumar, T.S.P. Securing IoT-based healthcare systems from counterfeit medicine penetration using Blockchain. Appl. Nanosci. 2021, 13, 1263–1275. [Google Scholar] [CrossRef]
- Alabbad, M.; Mhaskar, N.; Khedri, R. Hardening of network segmentation using automated referential penetration testing. J. Netw. Comput. Appl. 2024, 224, 103851. [Google Scholar] [CrossRef]
- Hidayanto, B.C.; Akbar, I.A.; Putra, A.Z.D. Automated Web Security Testing Guide Mapping to Accelerate Process on Penetration Testing. Procedia Comput. Sci. 2024, 234, 1412–1419. [Google Scholar] [CrossRef]
- Manessi, F.; Rozza, A.; Manzo, M. Dynamic graph convolutional networks. Pattern Recognit. 2019, 97, 107000. [Google Scholar] [CrossRef]
- Haq, T.U.; Shah, T.; Siddiqui, G.F.; Iqbal, M.Z.; Hameed, I.A.; Jamil, H. Improved Twofish Algorithm: A Digital Image Enciphering Application. IEEE Access 2021, 9, 76518–76530. [Google Scholar] [CrossRef]
- Abu-Faraj, M.; Al-Hyari, A.; Al-Taharwa, I.; Al-Ahmad, B.; Alqadi, Z. CASDC: A Cryptographically Secure Data System Based on Two Private Key Images. IEEE Access 2022, 10, 126304–126314. [Google Scholar] [CrossRef]
- Bhullar, R.K.; Pawar, L.; Kumar, V.; Anjali. A novel prime numbers based hashing technique for minimizing collisions. In Proceedings of the 2016 2nd International Conference on Next Generation Computing Technologies (NGCT), Dehradun, India, 14–16 October 2016. [Google Scholar] [CrossRef]
- Puteaux, P.; Puech, W. An Efficient MSB Prediction-Based Method for High-Capacity Reversible Data Hiding in Encrypted Images. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1670–1681. [Google Scholar] [CrossRef]
- Abu-Faraj, M.; Al-Hyari, A.; Aldebei, K.; Alqadi, Z.A.; Al-Ahmad, B. Rotation Left Digits to Enhance the Security Level of Message Blocks Cryptography. IEEE Access 2022, 10, 69388–69397. [Google Scholar] [CrossRef]
- Alhayani, B.A.; AlKawak, O.A.; Mahajan, H.B.; Ilhan, H.; Qasem, R.M. Design of Quantum Communication Protocols in Quantum Cryptography. Wirel. Pers. Commun. 2023, 1–18. [Google Scholar] [CrossRef]



| Implementation Parameters | |
|---|---|
| Parameter | Description |
| Programming platform | Python |
| Version | 3.7.14 |
| Operating system | Windows 10 |
| Dataset | Medical MNIST |
| Data format | Image |
| Dataset size | 6 GB |
| Processing power | 20 mW |
| Cryptographic algorithm | Twofish algorithm |
| Method | Encryption Time | Decryption Time | Throughput | MSE | PSNR | Confidentiality Score (%) |
|---|---|---|---|---|---|---|
| CASDC | 509.66 s | 1802 s | 3237.2 | 6.7064 | 22.7171 | 77% |
| MC | 0.3340 s | 0.3340 s | 5279.7 | 7.6702 | 21.2168 | 72% |
| Proposed | 0.225 s | 0.231 s | 71.225 | 4.245 | 24.721 | 98% |
| Metrics | Performance |
|---|---|
| Encryption time | 0.225 s |
| Decryption time | 0.231 s |
| MSE | 4.245 |
| PSNR | 24.721 |
| Confidentiality score | 98% |
| Throughput | 71.225% |
| Error | 0.0021% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Singh, A.; Sharma, V.S.; Basheer, S.; Chowdhary, C.L. A Deep Cryptographic Framework for Securing the Healthcare Network from Penetration. Sensors 2024, 24, 7089. https://doi.org/10.3390/s24217089
Singh A, Sharma VS, Basheer S, Chowdhary CL. A Deep Cryptographic Framework for Securing the Healthcare Network from Penetration. Sensors. 2024; 24(21):7089. https://doi.org/10.3390/s24217089
Chicago/Turabian StyleSingh, Arjun, Vijay Shankar Sharma, Shakila Basheer, and Chiranji Lal Chowdhary. 2024. "A Deep Cryptographic Framework for Securing the Healthcare Network from Penetration" Sensors 24, no. 21: 7089. https://doi.org/10.3390/s24217089
APA StyleSingh, A., Sharma, V. S., Basheer, S., & Chowdhary, C. L. (2024). A Deep Cryptographic Framework for Securing the Healthcare Network from Penetration. Sensors, 24(21), 7089. https://doi.org/10.3390/s24217089







