Abstract
This paper investigates joint beamforming in a secure integrated sensing and communications (ISAC) system assisted by reconfigurable intelligent surfaces (RIS). The system communicates with legitimate downlink users, detecting a potential target, which is a potential eavesdropper attempting to intercept the downlink communication information from the base station (BS) to legitimate users. To enhance the physical-layer secrecy of the system, we design and introduce interference signals at the BS to disrupt eavesdroppers’ attempts to intercept legitimate communication information. The BS simultaneously transmits communication and interference signals, both utilized for communication and sensing to guarantee the sensing and communication quality. By jointly optimizing the BS active beamformer and the RIS passive beamforming matrix, we aim to maximize the achievable secrecy rate and radiation power of the system. We develop an effective scheme to find the active beamforming matrix through fractional programming (FP) and semi-definite programming (SDP) techniques and obtain the RIS phase shift matrix via a local search technique. Simulation results validate the effectiveness of the proposed methods in enhancing communication and sensing performance. Additionally, the results demonstrate the effectiveness of introducing the interference signals and RIS in enhancing the physical-layer secrecy of the ISAC system.
1. Introduction
With the explosive growth of wireless devices, spectrum and energy resources have become a valuable asset. The scarcity of these resources has promoted the development of more efficient technologies. Integrated sensing and communications (ISAC) is a promising technology to substantially enhance the spectral and energy efficiency of numerous next-generation wireless systems [1,2]. Due to their unique integration and coordination advantages, ISAC systems have attracted widespread interest in various fields [3], such as vehicle networks, unmanned aerial vehicle sensing, and communication and localization sensing, etc. In ISAC systems, many efforts have been devoted to designing ISAC waveforms to achieve the simultaneous support of target detection and communications through simultaneous sensing and communications [4,5,6,7]. A main focus has been on transmitting designs for enhancing the communication performances of legitimate users, with limited attention to the presence of potential eavesdroppers in the environment.
From the perspective of typical radar systems, the power of the sensing signal can be concentrated in the direction of targets of interest to ensure high detection performance. For the ISAC system, the transmitting signal encompasses not only sensing information but also communication information. Therefore, the communication information is susceptible to being intercepted by potential sensing targets, and these sensing targets are likely to be potential eavesdroppers, introducing potential security risks into the ISAC system. To tackle the security issues in the ISAC system, potential eavesdroppers can be regarded as radar targets [8]. While preventing eavesdropping on legitimate information, it is also essential to ensure the system maintains optimal sensing performance. However, the challenge lies in achieving a balance between suppressing eavesdropping and ensuring satisfactory sensing performance. The pursuit of robust sensing performance may inadvertently lead to sub-optimal communication performance for legitimate users in the ISAC system.
Various schemes have been proposed to address the security issue and maximize the communication security rate, such as artificial noise interference and multi-antenna beamforming [9,10,11,12,13,14,15], etc. In [12], the security of ISAC was investigated, aiming to maximize the signal-to-interference-plus-noise ratio (SINR) of the radar while ensuring the achievement of secure rates for legitimate users. The authors in [13] proposed an auxiliary method for Artificial Noise (AN) deployment in an ISAC system. This approach involves the base station (BS) providing communication services to legitimate users while concurrently detecting radar targets. In [14], pseudo-random interference signals were introduced during the transmission of communication signals. These signals are designed to disrupt eavesdroppers’ attempts to intercept useful signals and simultaneously act as signals for detecting targets. In [15], a multiple-user interference was leveraged to address security issues in the dual-functional radar and communication (DFRC) system. Constructive interference is employed to enhance the received signal at communication users, while destructive interference is utilized to degrade eavesdropping signals at radar targets. In the context of the ISAC system, it is crucial to enhance the communication secrecy rate for legitimate users while maintaining sensing performance. But, for the secure communications in the ISAC system, the performance is heavily constrained by the wireless propagation environment.
Recently, due to the introduction of RIS to beyond 5G communications, RIS-based ISAC has attracted extension attention. For instance, in [16], RIS is employed in an ISAC system to enhance downlink communications. This is achieved by maximizing SINR for radar applications and minimizing the multi-user interference (MUI) for communication purposes. In [17], RIS is employed to mitigate MUI under the Cramer–Rao bound (CRB) constraint for direction of arrival (DOA) estimation. In [18], a study on fair sensing–communication waveform design with RIS is conducted. In this study, the joint optimization of beamforming at the BS and RIS is performed. The optimization aims to maximize the sensing SINR and minimize the MUI for communication.
Given the potential of RIS in improving ISAC performances, RIS has also become popular in secure ISAC designs. In [19], the secrecy rate of legitimate users was enhanced through the introduction of RIS. In [20], RIS was used to sense and locate targets in wireless networks, where a special sensor is installed near the RIS to sense the direction of nearby targets through the RIS. In [21], RIS was used to assist the wireless communication system of a security classification to ensure the quality of service of ordinary users and the safe rate of confidential users while reducing the transmission power of the BS. In [22], RIS was employed to assist the ISAC system. This involves maximizing the output SINR of the radar while ensuring the quality of service (QoS) of communication. In [23], by jointly designing the radar’s received beamformer, active RIS reflection coefficient matrix, and transmit beamforming matrix, the maximum secrecy of the system was achieved under the conditions of the total power budget and the minimum signal-to-noise-ratio (SNR) of the radar. In [24], RIS was employed to assist the communication link between the BS and legitimate users while simultaneously aiding in the detection of obstructed sensing targets. The objective is to maximize the secrecy rate for legitimate users while ensuring a specified SINR for sensing. From these works, we see that RIS can provide additional communication links to improve the performance of communication networks, while increasing the SINR of legitimate users while suppressing the SINR of eavesdroppers. At the same time, RIS has expanded the ISAC system coverage range, not only ensuring communication performance, but also improving sensing performance. Inspired by the aforementioned efforts, we intend to leverage RIS to maximize both communication secrecy rate and radar radiation power towards a target.
In this paper, we leverage the potential of RIS to modify the wireless environment and design an ISAC transmitting waveform to improve the performance of the RIS-assisted secure ISAC system. We formulate an optimization problem to maximize the secrecy rate for legitimate users and the radar radiation power towards potential eavesdroppers. The main contributions are summarized as follows:
- In order to suppress the eavesdropper from intercepting legitimate users’ information, the BS is designed to simultaneously transmit communication signals and interference signals, which is to achieve both sensing and communication by introducing the designed interference signals into the system. To maximize the communication secrecy rate and radar radiation power, we jointly optimize the communication beamformer, interference signal beamformer, and the reflection coefficient matrix of the RIS. Specifically, under power and phase constraints, we maximize the secrecy rate in logarithmic form and maximize the detection power in quadratic form, rendering a highly non-convex problem that is challenging to solve.
- We reformulate the secrecy rate problem as a fractional programming (FP) problem. Together with maximizing the radiation power, we then cast the problem into a semi-definite programming (SDP) formulation. The combined use of FP and SDP addresses the challenges posed by the multi-ratio fractional and non-convex optimization aspects of the problem. This enables us to further apply the semi-definite relaxation (SDR) for solving the reformulated optimization problem. Subsequently, we employ an alternating optimization framework to optimize the active beamforming matrix and the reflection coefficient matrix to achieve the final solution.
The remainder of this paper is organized as follows. Section 2 introduces the system model of the considered RIS-assisted secure ISAC system. Section 3 introduces the problem formulation involved in the system, as well as develops the joint beamforming scheme. Section 4 presents and discusses the numerical and simulation results, and Section 5 concludes the paper.
Notations: Bold lowercase letters and bold uppercase letters denote column vectors and matrices, respectively. represents the set of complex numbers. denotes the Euclidean norm, and denotes the Frobenius-norm of its argument. denotes an N-dimensional diagonal matrix whose diagonal elements are . and and denote the transpose and conjugate transpose operation, respectively. represents the identity matrix. is the conjugate operation. is the expectation operation. is the real part of a complex number.
2. System Model
We consider a secure RIS-aided ISAC system that includes a dual-functional BS, a RIS, an eavesdropper that can be treated as a sensing target, and K single antenna users, as illustrated in Figure 1. The BS is equipped with a uniform linear array of M transmitting antennas, serving K users () while detecting the target. The RIS is with N reflecting elements, each of which has a discrete adjustable phase. Let be the diagonal reflecting phase matrix of the RIS, , and , where is the set of possible phase values for the n-th RIS element and b is the number of quantization bits. The users are uniformly distributed within a confined area, while the potential target is located in a different area.
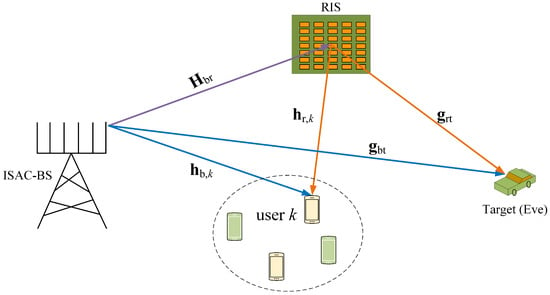
Figure 1.
A RIS-aided secure ISAC system.
This work focuses on designing the ISAC waveform for different stages of the physical-layer secrecy enhancement. First, we consider refining the target detection based on prior knowledge of the coarse direction of the target, ensuring communication quality of service for legitimate users in the meantime. In the second stage, we design ISAC waveforms to actively transmit interference signals towards eavesdroppers, enhancing the secrecy rate and further improving target detection. To achieve this goal, the BS is designed to simultaneously transmit two different signals, the communication signal and interference signal , and both signals can be used to detect the potential target. Assume that both and are simultaneously transmitted for communications and sensing by the shared antennas, where contains information required by legitimate users, and is used to interfere with the eavesdropper. We assume that the prior location information of the eavesdropper has been obtained. In the ISAC system, such information can be achieved by the sensing function and treating the eavesdropper as a sensing target [15,24]. Let represent the related communication beamformer and denote the corresponding interference beamformer. Let be the dual-function signal from the BS, and can be expressed as
where and . To avoid mutual interference between communication and interference signals, we assume that the communication and interference signals are statistically independent and uncorrelated [23], i.e., . This is a typical and legitimate assumption in the sense that both signals are noise-like in the time domain and generated independently. And the communication and interference signals satisfy and , where represents an X-order identity matrix. For convenience, we introduce and .
2.1. Communication Model
Let denote the channel information matrix from the BS to the RIS, denote the channel vector from the BS to user k, and denote the channel vector from the RIS to user k. Based on the symbols and channels modeled above, the signal received at user k can be written as
where is the additive white Gaussian noise (AWGN) with .
Denote as the composite communication channel from the BS to user k. Then, the received SINR at the k-th user can be written as
where represents the j-th column of , and denotes the noise power at the k-th user. According to (3), the achievable sum data rate of the legitimate users can be given by
2.2. Sensing Model
Let denote the direct channel from the BS to the target and denote the channel from the RIS to the target. and denote the path loss from the BS to the target and from the RIS to the target, respectively. and denote the target direction from BS and RIS, respectively; let and be the steering vectors from the BS to the target and from the RIS to the target, respectively. Then, the radiation power in the direction of the target can be given by
where in (5).
In the considered ISAC system, the target is a potential eavesdropper, who attempts to decode the information sent to the legitimate users. The received SINR at the target in terms of the k-th user can be given by
where denotes the noise power at the target.
Based on (6), the achievable rate of the communication information eavesdropped by the target can be given by
Then, the secrecy rate of the considered system can be computed by
3. Problem Formulation and Algorithm Design
In this paper, we jointly design the BS transmit beamformer and RIS phase shift matrix to maximize the secrecy rate of the system and the radiation power of the target.
3.1. Problem Formulation
The problem is formulated as
where is the regularization parameter, is the radiation power in the direction of the target (5), and P is the maximum transmission power of the BS. According to (3)–(6), the impact of and on the secrecy rate and radiation power optimization mainly depends on , , and .
Problem (9) is a non-convex optimization problem and is difficult to solve directly. Next, we will first transform the problem into two optimization problems with respect to and , respectively, and then employ FP [25] and SDP to develop a low complexity solution to the original problem.
3.2. Proposed Scheme
In this section, we solve Problem (9) in two steps: optimizing with a given RIS phase matrix and optimizing with a fixed BS beamforming matrix. The two steps alternate and iterate until convergence.
3.2.1. Step 1: Optimizing Active Beamforming Matrix at the BS
We solve the BS beamforming matrix by fixing the reflection coefficients matrix of the RIS, . Then, Problem (9) can be simplified as
Problem (10) is still non-convex, and we will transform it into a convex problem to find its solution. For the non-convex term involving the difference between two logarithmic functions in the first term, i.e., , we apply the FP method [25] to recast it to a convex problem. For the second term , we will reshape it to be convex, adopting a similar approach to that in [26]. By rephrasing the two terms, we rewrite the objective function with respect to the optimization variable into a convex form.
We start with recasting in the objective function of (10) as a convex form regarding . According to (4), in (8) can be expressed as
Applying the quadratic transformation [27], (11) can be expressed as a Lagrangian dual expression as
where is the auxiliary variable introduced. Note that there is still a fractional part on the right side of (12); hence, we apply the quadratic transformation again, leading to
where is the auxiliary variable introduced.
Note that and are auxiliary variables. With all other variables fixed, then and can be obtained by solving the equations of and equal to zero, respectively. With the details suppressed, and are obtained as
Define and , where refers to a permutation matrix. Further define and as
where . Based on (13)–(17), can be further written into
where .
Then, we recast in the objective function of (10) as a convex form regarding . Similarly, in (8) can be expressed as
Its polynomial form can be given by
where and are auxiliary variables and are given by
Note that in (21) and in (22) can again be obtained by solving the equations of and equal to zero.
Finally, we recast the last term in the objective function of (10) as a convex form regarding . To make the last term convex, we first reformulate (5) as follows
Note that is a positive semi-definite matrix [26]. Therefore, (27) is a convex function.
Substituting (26) and (27) into (10), Problem (10) can be reformulated as
Since and , according to the expressions in (16)–(24) and (27), it can be observed that (28) is a function of and . Note that when is fixed, Problem (28) is an SDP convex problem and can be efficiently solved by the CVX toolbox [28].
3.2.2. Step 2: Optimizing Passive Beamforming Matrix at the RIS
For given , Problem (9) can be simplified to
In (29), the available phase range of each reflective element depends on the bit of RIS. When is fixed and power constraints are removed, the objective function in (29) regarding still remains non-convex. Considering the complexity of the problem, here, we adopt a local search method [29] to solve it. For the optimization of the phase of the n-th RIS element, we first fix the phase values of the other N-1 RIS elements to their initial values (for those with already optimized phase values, these are fixed at their optimal values). We enumerate all possible values within the feasible region , identifying the value that maximizes the secrecy rate as the optimal phase value for the n-th element. Subsequently, we continue the search process until we obtain the optimal phase values for all RIS elements. The searching process will be executed times until all RIS elements obtain the optimal phase values.
3.2.3. Overall Optimization Framework
In Section 3.2.1 and Section 3.2.2, we have developed solutions to the problems of BS beamforming optimization and RIS phase shift optimization. In this section, we will describe the proposed overall alternate optimization scheme. Specifically, we execute Step 1 and Step 2 sequentially, and then alternatively iterate between these two steps to facilitate a RIS-assisted secure ISAC, as shown in Algorithm 1. In the algorithm, Line 1 is to optimize the variable settings for feasible initial values. Lines 3–11 involve alternately solving for and based on the convex problems transformed in (10) and (29). In this context, Lines 3–6 pertain to various auxiliary variables involved in the optimization process.
| Algorithm 1 Proposed joint beamforming scheme in RIS-assisted secure ISAC systems |
|
The computational complexity of Algorithm 1 is analyzed next. We can observe that the complexity of the algorithm is primarily concentrated in lines 7 and 8. Line 7 involves solving an SDP problem; its computational complexity for one iteration is . Line 8 is used to solve the optimization of discrete phase shift performs for Algorithm 1, with the respective computational complexity of . Therefore, the overall computational complexity of Algorithm 1 is in the order of , where denotes the iteration times. The convergence of Algorithm 1 will be demonstrated in the subsequent section.
4. Simulation Results
In this section, we present simulation results to validate the performance of the RIS-assisted secure ISAC system. We consider the RIS-assisted secure ISAC system depicted in Figure 1. Assume the direct link channel follows Rayleigh fading and the RIS-aided channels follow Rician fading. In the simulation, we set the number of antennas at the BS as , employing a ULA with half-wavelength spacing between adjacent antennas and the total power budget as dBm, dBm, dBm, and . The Rician factor is four, and the regularization parameter is 100. K single-antenna users are uniformly and randomly distributed within a circle centered at (200 m, −50 m) with a radius of 30 m. The BS and the RIS are located at (0 m, 0 m) and (200 m, 0 m), respectively. The target is positioned at an azimuth angle of and . The path loss models for direct and indirect links are dB, dB according to [30], where is the link distance.
Before showing the ISAC performance, we demonstrate the convergence of the proposed Algorithm 1. Figure 2 illustrates the convergence of the proposed algorithm with RIS, without RIS, and without the designed interference signal, where . As clearly shown, the average secrecy rate achieved by the proposed algorithm exhibits rapid growth with an increasing number of iterations, reaching convergence in less than 10 iterations. We also see that the introduction of RIS and the designed interference signals significantly enhance the security performance of the ISAC system.
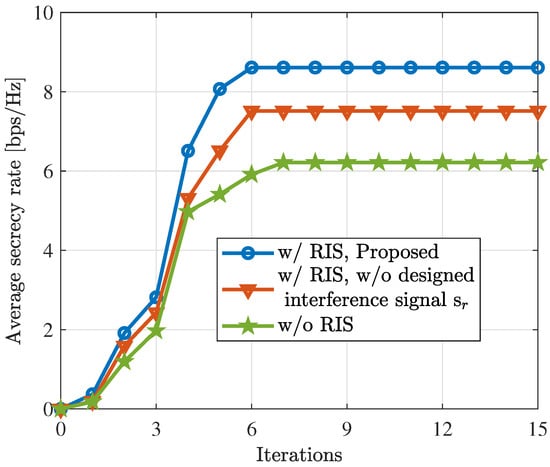
Figure 2.
Convergence of the proposed algorithm for scenarios with RIS, without RIS, and without the designed interference signal. ‘w/o’ and ‘w/ ’ stand for without and with, respectively.
Figure 3 illustrates the impact of the regularization factor introduced in Problem (9). It can be observed that the proposed method converges for different values of . However, due to the different weighting of the two physical quantities in (9) by , we can see that the performance achieved by the ISAC system varies with different regularization factors. Figure 3a and Figure 3b, respectively, depict the achieved communication secrecy rate, sum rate, and sensing radiation power under different values of . Across various regularization factors, the system’s achievable sum rate consistently surpasses the secrecy rate. This implies that maximizing the secrecy rate does not adversely affect the overall sum rate of the system. And from the simulation results, it can be seen that the performance achieved by the ISAC system varies with different regularization factors, which further proves the rationality of our proposed method.
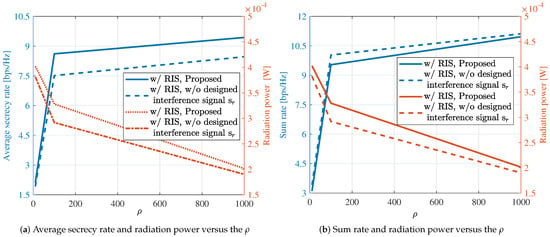
Figure 3.
Performance trade-off.
In Figure 4, we evaluate the secrecy rates and radar radiation power of the considered ISAC system under different network densities, as indicated by the numbers of legitimate users in a confined region. It can be observed that as the number of users increases, the two performance metrics slightly degrade. This is reasonable due to the increasing channel coherence. However, it is worth noting that the proposed approach actively transmitting interference signals achieves non-trivial performance improvements over the considered range of Ks. Specifically, when the number of legitimate users is six, the ISAC system with interference signals exhibits approximately a 13% improvement in the secrecy rate and an 11% increase in radiation power compared to the ISAC system without interference signals. This validates that introducing interference signals can effectively enhance the performance of the ISAC system. Moreover, our approach exhibits robust performance across different numbers of users, further confirming the robustness and applicability of the proposed method.
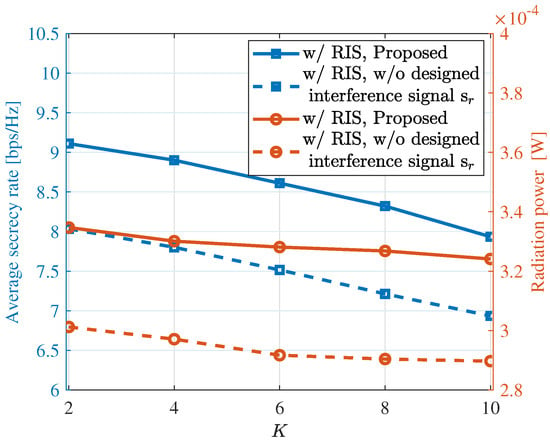
Figure 4.
The communication and sensing performance under different values of K (user number), where curves with circle markers use the right y-axis.
In Figure 5a, we compare the average secrecy rate with the number of RIS elements N. We can see that the performance of all schemes, except for the case without RIS, increases with the increment of N. Furthermore, compared to the method without the designed interference signals, the proposed approach achieves significant performance improvement. Specifically, when , the average secrecy rate of the system increases by 15%. Similarly, in Figure 5b, we compare the radiation power with the number of RIS elements N. It can be observed that the radiation power gradually increases with the increment of N. At , the system’s radiation power increases by 18%. Additionally, we find that the proposed approach exhibits a significant improvement in sensing performance. Combining the results from Figure 5a,b, the proposed algorithm significantly enhances the performance of the ISAC system. The introduction of RIS and interference signals has significantly enhanced the ISAC system’s performance.
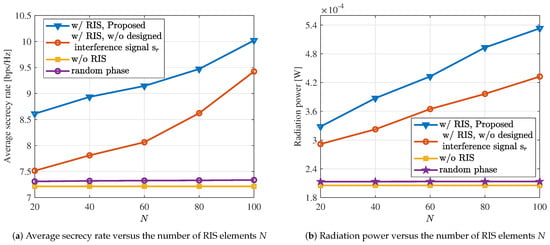
Figure 5.
The communication and sensing performance under different values of N.
In Figure 6, the achievable average secrecy rate and radiation power of the system are plotted against the increasing bit quantization number, ranging from 1 to 5. In Figure 6a, we can observe a clear advantage of the proposed approach in terms of secrecy rate. In the presence of interference signals, the average secrecy rate can be increased by up to 10%. Additionally, we observed that the bit quantization number increases from 1 to 4, and then from 4 to 5; the average secrecy rate remains relatively constant. This suggests that the system’s performance reaches a saturation point once the quantization bit number exceeds 4. Similarly, in Figure 6b, we can also observe a significant increase in radiation power with the addition of RIS and the introduction of interference signals. Likewise, as the quantization bit number varies, a phenomenon similar to Figure 6a is evident.
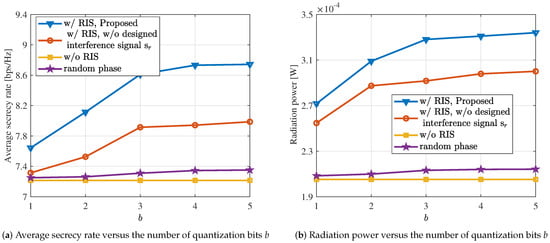
Figure 6.
The communication and sensing performance under different values of b.
Figure 7 illustrates the average secrecy rate of legitimate users when , while moving the RIS from (50 m, 0 m) to (250 m, 0 m). It can be observed that as the distance between RIS and BS increases, the ISAC system’s secrecy rate decreases and its security performance is weaker. Additionally, we also observe that under the same power constraints, introducing interference signals can provide a better secrecy rate.
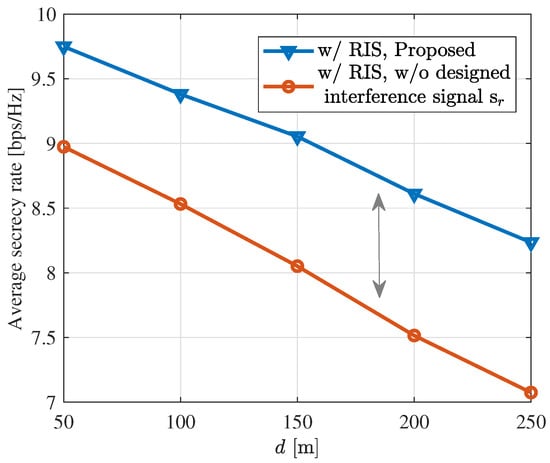
Figure 7.
Average secrecy rate versus the horizontal distance of the RIS from the BS d.
5. Conclusions
In this paper, we introduced the design of a secure ISAC system, proposing a joint optimization scheme on the transmit beamforming and the RIS coefficient matrix. Specifically, leveraging the potential of the RIS, we added the designed interference signals at the BS transmitter to confuse eavesdroppers attempting to intercept information from legitimate users. To ensure both the secrecy rate for legitimate users and the sensing performance of target detection, we formulated an optimization problem aiming to maximize the secrecy rate for legitimate users and the sensing radiation power. To overcome the non-convexity of the optimization problem, techniques such as FP and SDR were applied to convert the non-convex problem into a convex one. The problem was then solved using a low-complexity alternating optimization approach. Simulation results validated the effectiveness of the proposed method, demonstrating that the inclusion of RIS and interference signals can effectively enhance the ISAC system’s secrecy rate and sensing performance.
Though the optimization techniques applied in this work have achieved non-trivial performance enhancements in the considered secure ISAC system, it can be an interesting future work to further explore other optimization techniques, such as the popular majorization–minimization (MM) [24] and the manifold optimization [31]. In the future, we may consider exploring new methods to control nulls in the transmission waveform design to enhance the security rate and energy efficiency of the ISAC system [32]. And machine learning methods are showing promising results in addressing the issue of channel correlation between eavesdroppers and legitimate users [33], and in the future, we can further leverage machine learning techniques to enhance the security and efficiency of ISAC systems. Additionally, extending the proposed scheme to multi-RIS scenarios can be an interesting future work.
Author Contributions
Conceptualization, J.C. and K.W.; methodology, J.C.; software, J.C.; validation, J.C., K.W. and J.N.; formal analysis, K.W.; investigation, J.N.; resources, K.W.; data curation, J.C.; writing—original draft preparation, J.C.; writing—review and editing, J.C., K.W. and J.N.; visualization, J.C.; supervision, K.W., J.N. and Y.L.; project administration, J.C.; funding acquisition, J.N. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Natural Science Foundation of China (Grant No. 62072373, 61901372, 61972316), by the International Cooperation Foundation of Shaanxi Province (Grant No. 2019KW-012), by the Natural Science Research Program of Shaanxi Province (Grant No. 2020JQ-599), and by China Postdoctoral Science Foundation (Grant No. 2020M683541).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author. The data are not publicly available due to legal restrictions.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Liu, F.; Masouros, C.; Petropulu, A.P.; Griffiths, H.; Hanzo, L. Joint Radar and Communication Design: Applications, State-of-the-Art, and the Road Ahead. IEEE Trans. Commun. 2020, 68, 3834–3862. [Google Scholar] [CrossRef]
- Wu, K.; Zhang, J.A.; Guo, Y.J. Joint Communications and Sensing: From Fundamentals to Advanced Techniques; John Wiley & Sons: Hoboken, NJ, USA, 2022. [Google Scholar]
- Zhang, J.A.; Rahman, M.L.; Wu, K.; Huang, X.; Guo, Y.J.; Chen, S.; Yuan, J. Enabling Joint Communication and Radar Sensing in Mobile Networks—A Survey. IEEE Commun. Surv. Tutor. 2022, 24, 306–345. [Google Scholar] [CrossRef]
- Liu, F.; Zhou, L.; Masouros, C.; Li, A.; Luo, W.; Petropulu, A. Toward Dual-functional Radar-Communication Systems: Optimal Waveform Design. IEEE Trans. Signal Process. 2018, 66, 4264–4279. [Google Scholar] [CrossRef]
- Liu, F.; Masouros, C.; Li, A.; Sun, H.; Hanzo, L. MU-MIMO Communications with MIMO Radar: From Co-Existence to Joint Transmission. IEEE Trans. Wirel. Commun. 2018, 17, 2755–2770. [Google Scholar] [CrossRef]
- Sturm, C.; Wiesbeck, W. Waveform Design and Signal Processing Aspects for Fusion of Wireless Communications and Radar Sensing. Proc. IEEE 2011, 99, 1236–1259. [Google Scholar] [CrossRef]
- Liu, X.; Huang, T.; Shlezinger, N.; Liu, Y.; Zhou, J.; Eldar, Y.C. Joint Transmit Beamforming for Multiuser MIMO Communications and MIMO Radar. IEEE Trans. Signal Process. 2020, 68, 3929–3944. [Google Scholar] [CrossRef]
- Dong, L.; Han, Z.; Petropulu, A.P.; Poor, H.V. Improving Wireless Physical Layer Security via Cooperating Relays. IEEE Trans. Signal Process. 2010, 58, 1875–1888. [Google Scholar] [CrossRef]
- Wu, K.; Zhang, J.A.; Huang, X.; Guo, Y.J. Integrating Secure Communications Into Frequency Hopping MIMO Radar with Improved Data Rate. IEEE Trans. Wirel. Commun. 2022, 21, 5392–5405. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K.C. Secrecy Wireless Information and Power Transfer with MISO Beamforming. IEEE Trans. Signal Process. 2014, 62, 1850–1863. [Google Scholar] [CrossRef]
- Wu, K.; Ni, W.; Zhang, J.A.; Liu, R.P.; Guo, J. Secrecy Rate Analysis for Millimeter-Wave Lens Antenna Array Transmission. IEEE Commun. Lett. 2020, 24, 272–276. [Google Scholar] [CrossRef]
- Chalise, B.K.; Amin, M.G. Performance tradeoff in a unified system of communications and passive radar: A secrecy capacity approach. Digital Signal Process. 2018, 82, 282–293. [Google Scholar] [CrossRef]
- Su, N.; Liu, F.; Masouros, C. Secure Radar-Communication Systems with Malicious Targets: Integrating Radar, Communications and Jamming Functionalities. IEEE Trans. Wirel. Commun. 2021, 20, 83–95. [Google Scholar] [CrossRef]
- Deligiannis, A.; Daniyan, A.; Lambotharan, S.; Chambers, J.A. Secrecy Rate Optimizations for MIMO Communication Radar. IEEE Trans. Aerosp. Electron. Syst. 2018, 54, 2481–2492. [Google Scholar] [CrossRef]
- Su, N.; Liu, F.; Wei, Z.; Liu, Y.F.; Masouros, C. Secure Dual-Functional Radar-Communication Transmission: Exploiting Interference for Resilience against Target Eavesdropping. IEEE Trans. Wirel. Commun. 2022, 21, 7238–7252. [Google Scholar] [CrossRef]
- Zhong, K.; Hu, J.; Pan, C.; Deng, M.; Fang, J. Joint Waveform and Beamforming Design for RIS-Aided ISAC Systems. IEEE Signal Process. Lett. 2023, 30, 165–169. [Google Scholar] [CrossRef]
- Wang, X.; Fei, Z.; Huang, J.; Yu, H. Joint Waveform and Discrete Phase Shift Design for RIS-Assisted Integrated Sensing and Communication System Under Cramer-Rao Bound Constraint. IEEE Trans. Veh. Technol. 2022, 71, 1004–1009. [Google Scholar] [CrossRef]
- An, D.; Hu, J.; Huang, C. Joint design of transmit waveform and passive beamforming for RIS-assisted ISAC system. Signal Process. 2023, 204, 108854. [Google Scholar] [CrossRef]
- Cui, M.; Zhang, G.; Zhang, R. Secure Wireless Communication via Intelligent Reflecting Surface. IEEE Wirel. Commun. Lett. 2019, 8, 1410–1414. [Google Scholar] [CrossRef]
- Shao, X.; You, C.; Ma, W.; Chen, X.; Zhang, R. Target Sensing with Intelligent Reflecting Surface: Architecture and Performance. IEEE J. Sel. Areas Commun. 2022, 40, 2070–2084. [Google Scholar] [CrossRef]
- Xing, J.; Lv, T.; Cao, Y.; Zeng, J.; Huang, P. Downlink Power Minimization in Intelligent Reflecting Surface Aided Security Classification Wireless Communications System. IEEE Syst. J. 2023, 17, 407–418. [Google Scholar] [CrossRef]
- Liu, R.; Li, M.; Liu, Y.; Wu, Q.; Liu, Q. Joint Transmit Waveform and Passive Beamforming Design for RIS-Aided DFRC Systems. IEEE J. Sel. Top. Signal Process. 2022, 16, 995–1010. [Google Scholar] [CrossRef]
- Salem, A.A.; Ismail, M.H.; Ibrahim, A.S. Active Reconfigurable Intelligent Surface-Assisted MISO Integrated Sensing and Communication Systems for Secure Operation. IEEE Trans. Veh. Technol. 2023, 72, 4919–4931. [Google Scholar] [CrossRef]
- Hua, M.; Wu, Q.; Chen, W.; Dobre, O.A.; Lee Swindlehurst, A. Secure Intelligent Reflecting Surface Aided Integrated Sensing and Communication. IEEE Trans. Wirel. Commun. 2023; early access. [Google Scholar] [CrossRef]
- Shen, K.; Yu, W. Fractional Programming for Communication Systems—Part II: Uplink Scheduling via Matching. IEEE Trans. Signal Process. 2018, 66, 2631–2644. [Google Scholar] [CrossRef]
- Xu, C.; Clerckx, B.; Zhang, J. Multi-Antenna Joint Radar and Communications: Precoder Optimization and Weighted Sum-Rate vs Probing Power Tradeoff. IEEE Access 2020, 8, 173974–173982. [Google Scholar] [CrossRef]
- Shen, K.; Yu, W. Fractional Programming for Communication Systems—Part I: Power Control and Beamforming. IEEE Trans. Signal Process. 2018, 66, 2616–2630. [Google Scholar] [CrossRef]
- Grant, M.; Boyd, S. CVX: Matlab Software for Disciplined Convex Programming, Version 2.1. Available online: http://cvxr.com/cvx (accessed on 1 March 2014).
- Chen, Y.; Ai, B.; Zhang, H.; Niu, Y.; Song, L.; Han, Z.; Vincent Poor, H. Reconfigurable Intelligent Surface Assisted Device-to-Device Communications. IEEE Trans. Wirel. Commun. 2021, 20, 2792–2804. [Google Scholar] [CrossRef]
- Guo, H.; Liang, Y.C.; Chen, J.; Larsson, E.G. Weighted Sum-Rate Maximization for Reconfigurable Intelligent Surface Aided Wireless Networks. IEEE Trans. Wirel. Commun. 2020, 19, 3064–3076. [Google Scholar] [CrossRef]
- Yu, X.; Xu, D.; Schober, R. MISO Wireless Communication Systems via Intelligent Reflecting Surfaces: (Invited Paper). In Proceedings of the IEEE/CIC International Conference on Communications in China (ICCC), Changchun, China, 11–13 August 2019; pp. 735–740. [Google Scholar] [CrossRef]
- Madani, S.; Jog, S.; Lacruz, J.O.; Widmer, J.; Hassanieh, H. Practical null steering in millimeter wave networks. In Proceedings of the USENIX Symposium on Networked Systems Design and Implementation (NSDI), Virtual, 12–14 April 2021; pp. 903–921. [Google Scholar]
- Rawat, D.B. Deep Transfer Learning for Physical Layer Security in Wireless Communication Systems. In Proceedings of the IEEE International Conference on Trust, Privacy and Security in Intelligent Systems, and Applications (TPS-ISA), Virtual, 13–15 December 2021; pp. 289–296. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).