Analyzing the Impact of Active Attack on the Performance of the AMCTD Protocol in Underwater Wireless Sensor Networks
Abstract
1. Introduction
2. Related Work
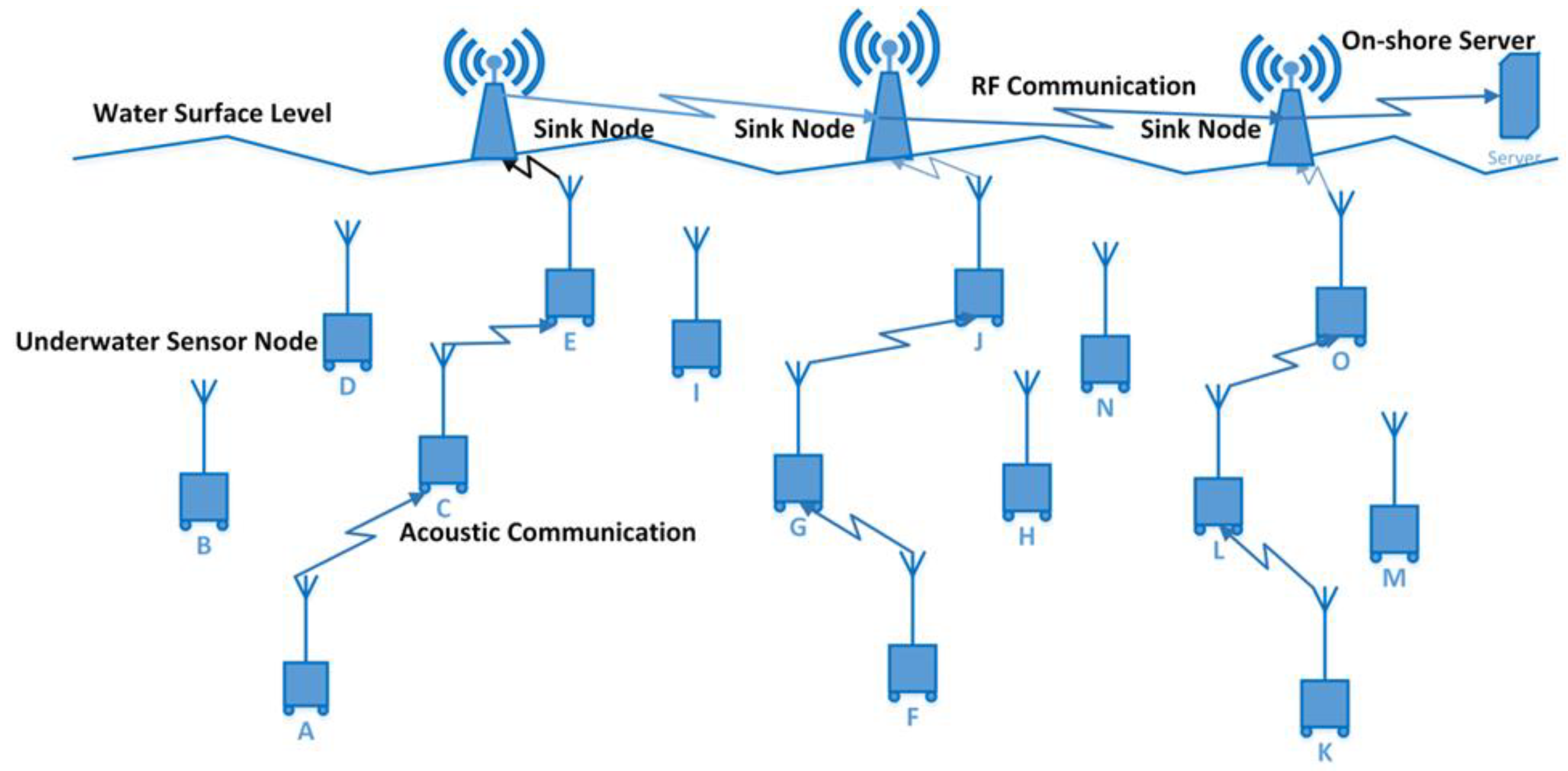
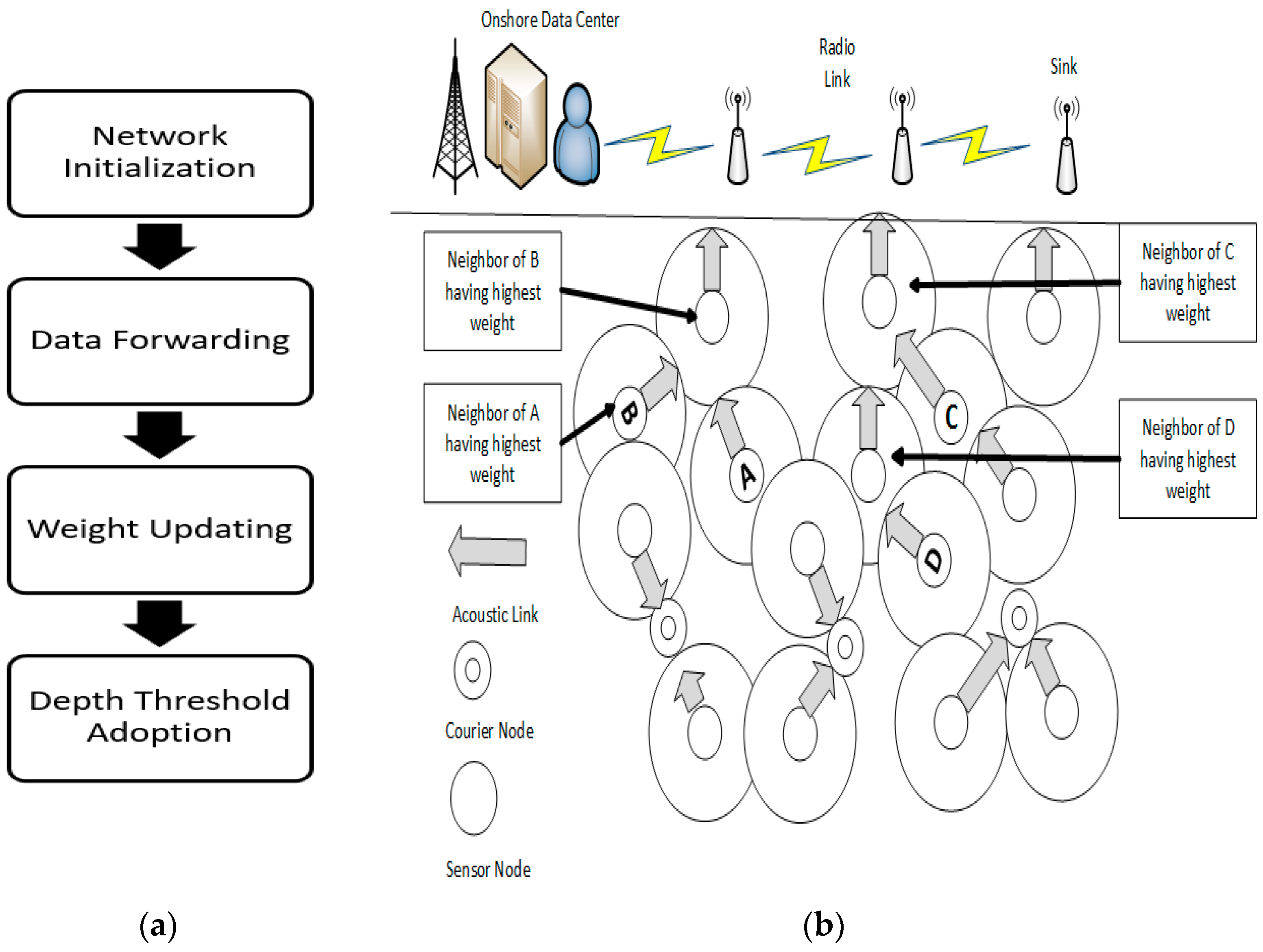
3. AMCTD Protocol
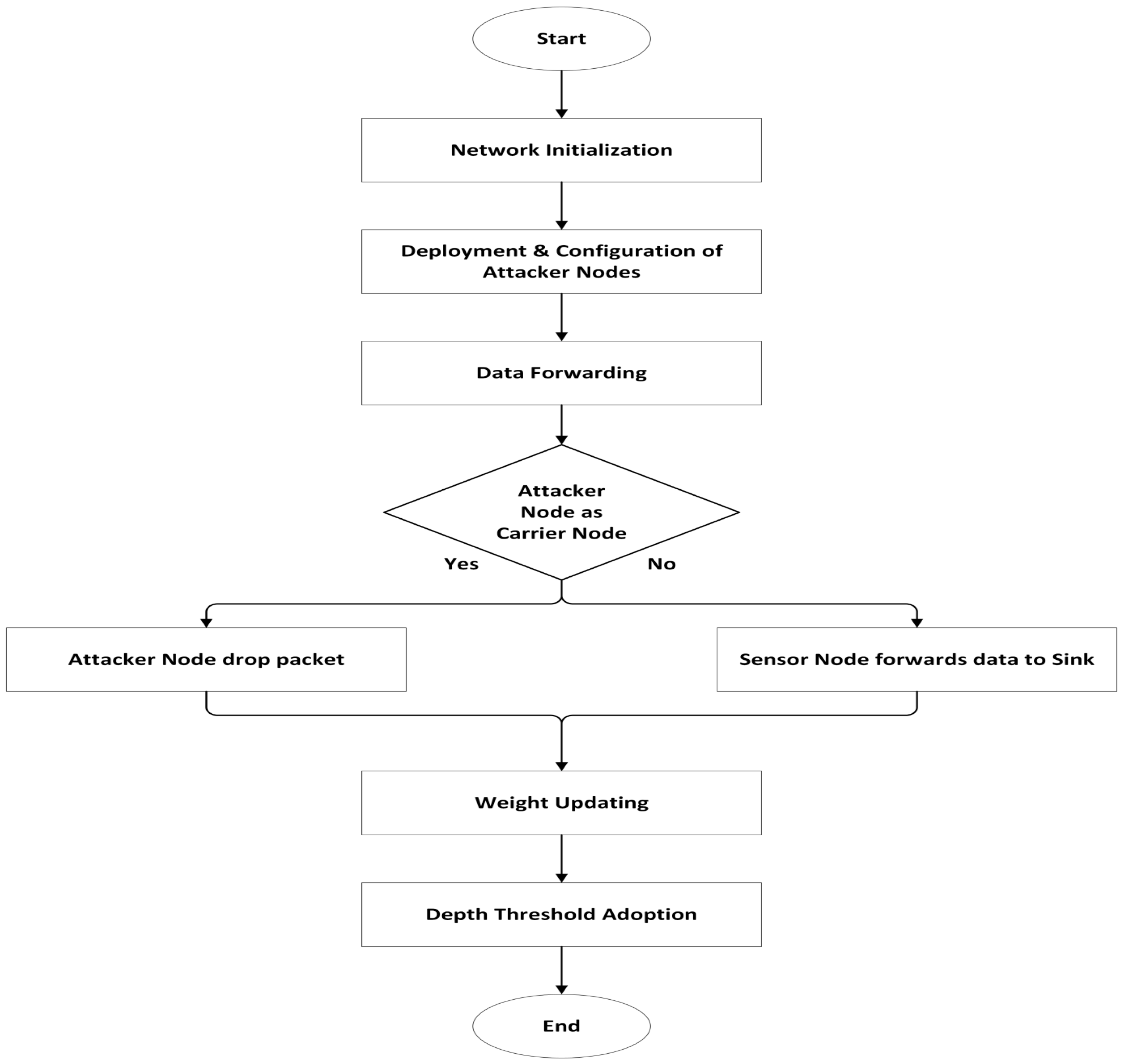
4. AMCTD Protocol and Active Attacks
5. Performance Evaluation and Implementation Parameters
6. Results and Discussion
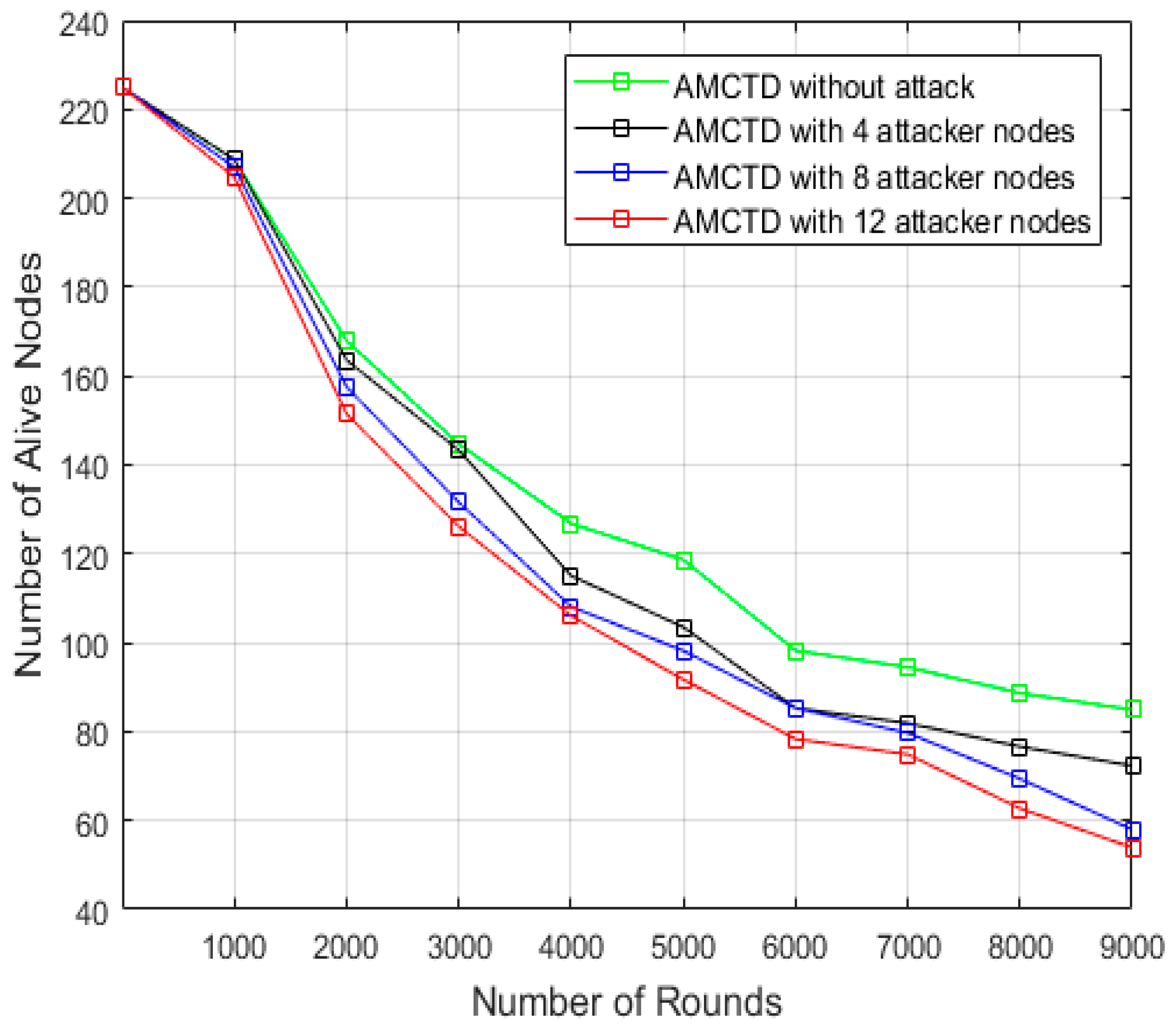
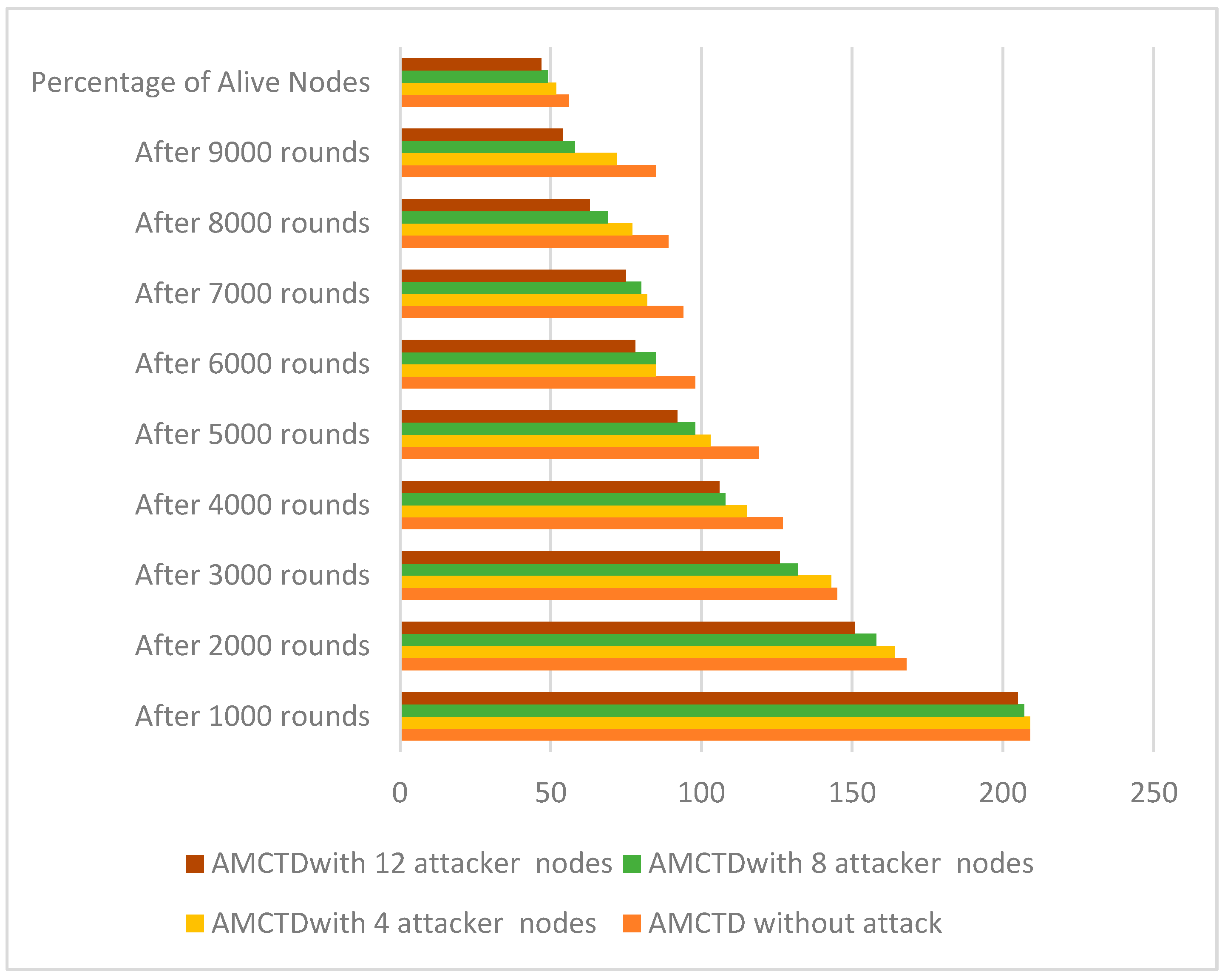
6.1. Evaluation of No. of Functioning/Alive Nodes
- 85 alive/functioning nodes without attack,
- 72 alive nodes with 4 attacker nodes,
- 58 alive nodes with 8 active nodes,
- 54 alive nodes with 12 active nodes.
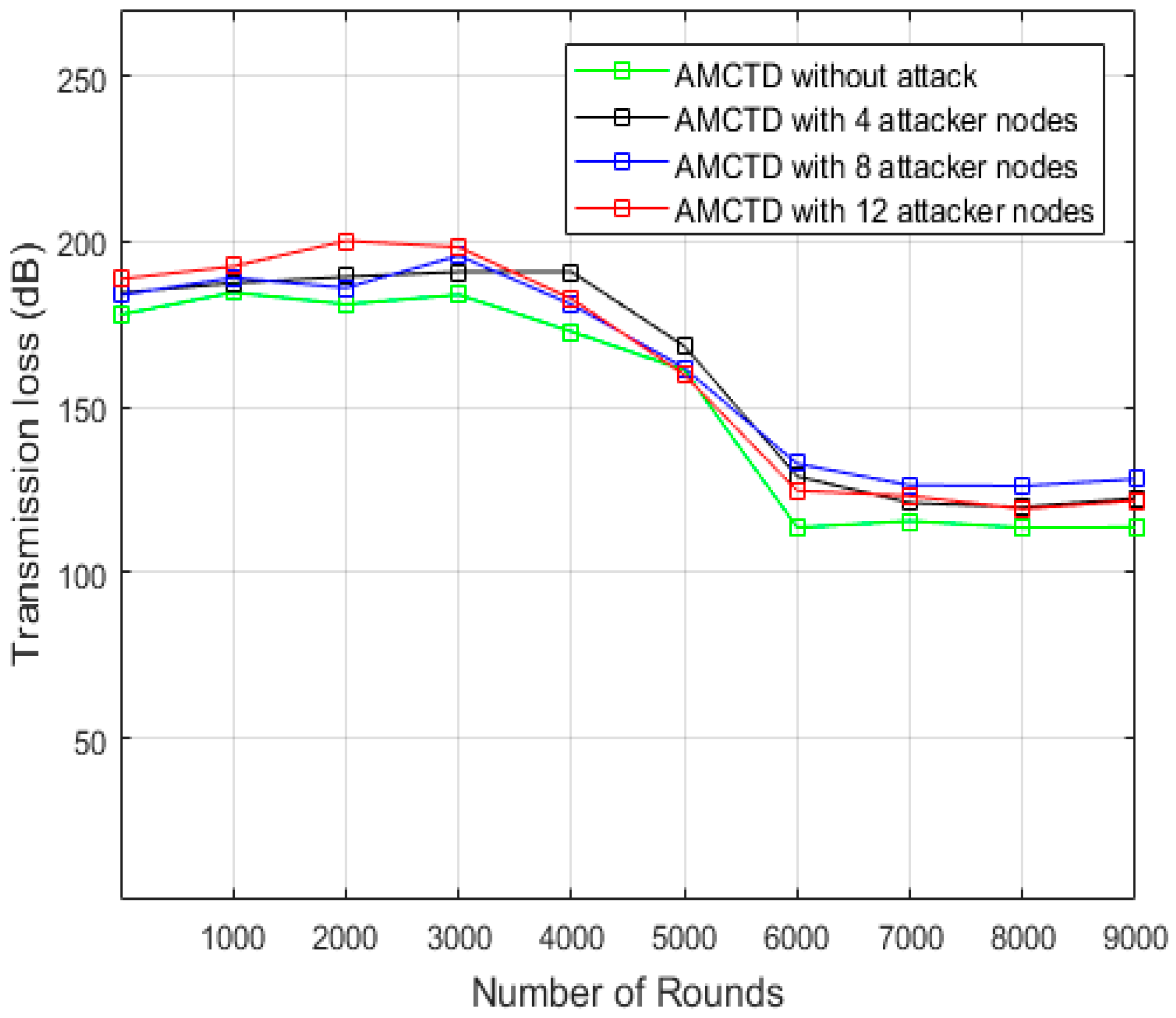
6.2. Analysis of Transmission Loss
- It has much lower transmission loss without attack.
- It has increased transmission loss with 4, 8, and 12 attacker nodes.
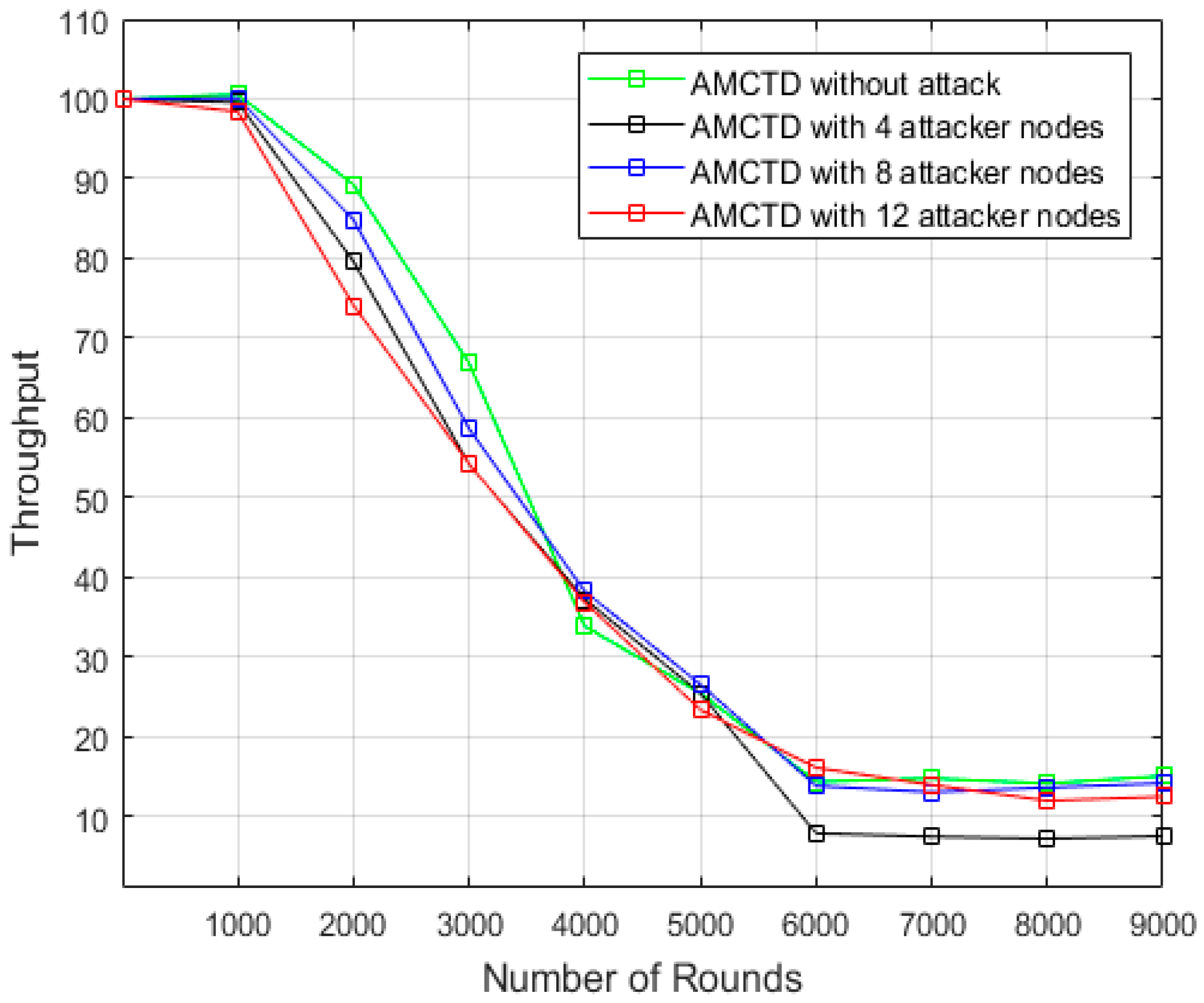
6.3. Analysis of Throughput
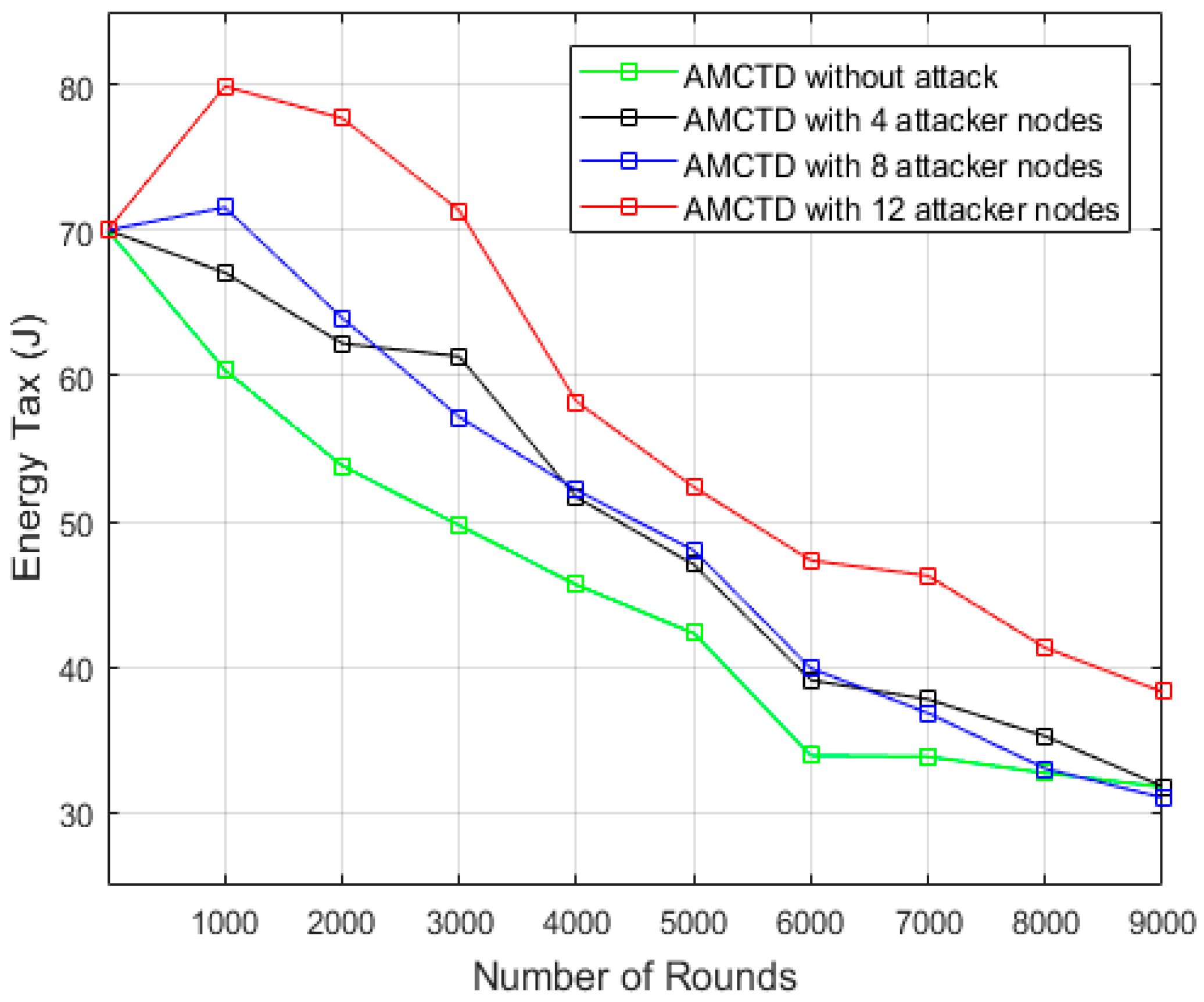
6.4. Analysis of Energy Tax
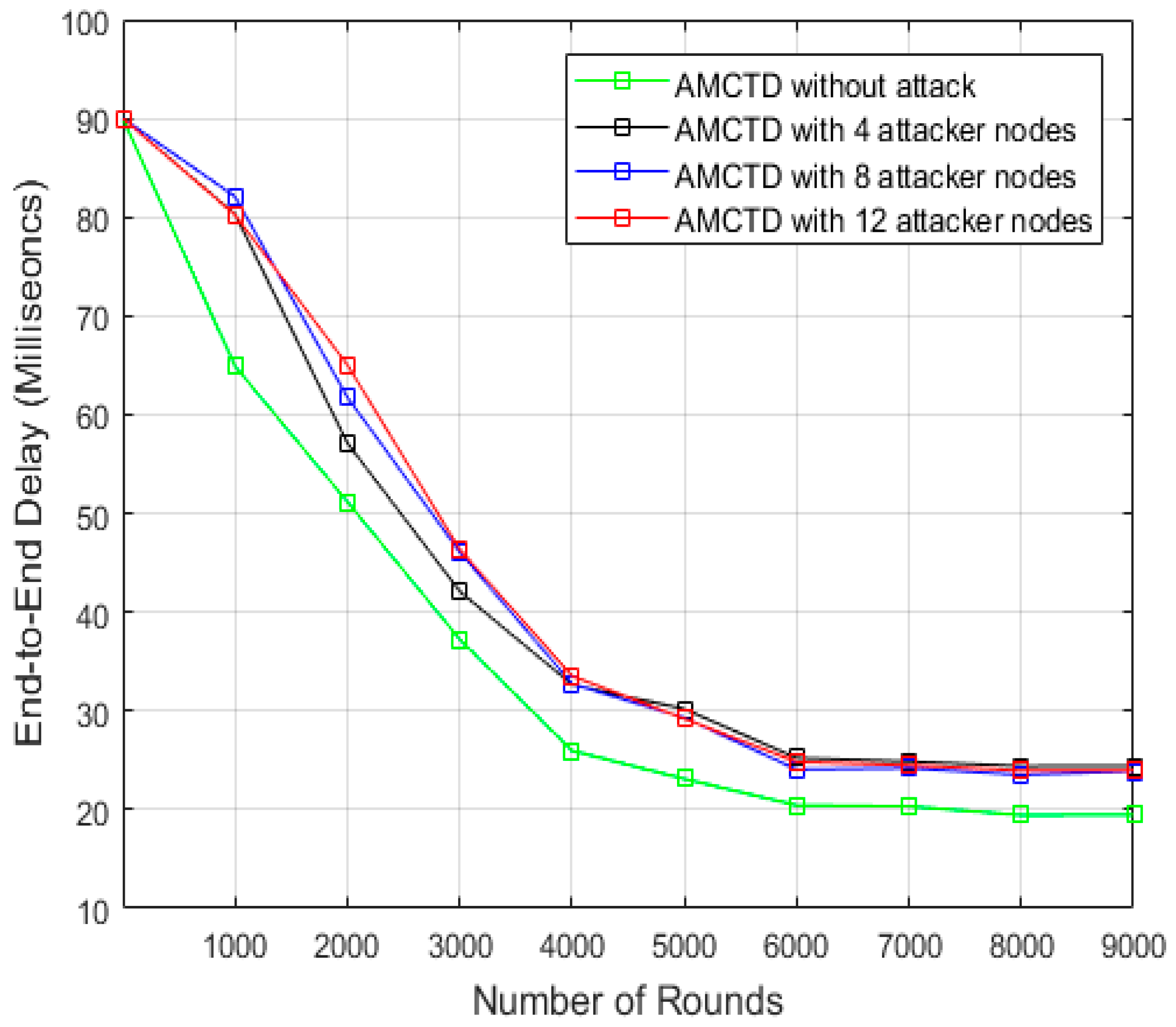
6.5. End-to-End Delay Analysis
7. Conclusions
- a reduction of up to 10% in the number of functioning nodes in the UWSNs environment;
- a decrease of up to 6% in throughput;
- an increase of up to 7% in transmission loss;
- a rise of up to 25% in energy cost; and
- an increase of up to 20% in end-to-end latency.
8. Future Directions and Challenges
- Trust: to establish the trust when the nodes are moving in the underwater environment, establishment of trust when the sensor nodes are sparsely deployed and they are far away from each other, considering block cipher algorithms such as ARIR and SEED for UWSNs environment, using the technology for underwater security with other network systems such as IEEE 802.15.3 (UWB), IEEE 802.11 (WLAN), IEEE 802.15.4 (ZigBee) [39,40,41,42,43].
- Intelligent sensor environments: to use AI models for reducing intelligent attacks in the network leading to robust systems. The transfer rate of packets in UWSNs environment can be reduced by utilizing intelligent sensor nodes that are self-localized; to address the DoS problem in UWSNs environment, secure UWSNs having intelligent sensor nodes and self-localization should be designed [35].
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Sun, N.; Wang, X.; Han, G.; Peng, Y.; Jiang, J. Collision-free and low delay MAC protocol based on multi-level quorum system in underwater wireless sensor networks. Comput. Commun. 2021, 173, 56–69. [Google Scholar] [CrossRef]
- Khan, H.; Hassan, S.A.; Jung, H. On underwater wireless sensor networks routing protocols: A review. IEEE Sens. J. 2020, 20, 10371–10386. [Google Scholar] [CrossRef]
- Ismail, A.S.; Wang, X.; Hawbani, A.; Alsamhi, S.; Abdel Aziz, S. Routing protocols classification for underwater wireless sensor networks based on localization and mobility. Wirel. Netw. 2022, 28, 797–826. [Google Scholar] [CrossRef]
- Gola, K.K.; Dhingra, M.; Gupta, B.; Rathore, R. An empirical study on underwater acoustic sensor networks based on localization and routing approaches. Adv. Eng. Softw. 2023, 175, 103319. [Google Scholar] [CrossRef]
- Cuzme-Rodríguez, F.; Velasco-Suárez, A.; Domínguez-Limaico, M.; Suárez-Zambrano, L.; Farinango-Endara, H.; Mediavilla-Valverde, M. Application for the Study of Underwater Wireless Sensor Networks: Case Study. Trends Artif. Intell. Comput. Eng. Proc. ICAETT 2023, 2022, 124–136. [Google Scholar]
- Sathish, K.; Ravikumar, C.V.; Rajesh, A.; Pau, G. Underwater wireless sensor network performance analysis using diverse routing protocols. J. Sens. Actuator Netw. 2022, 11, 64. [Google Scholar] [CrossRef]
- Khasawneh, A.M.; Kaiwartya, O.; Abualigah, L.M.; Lloret, J. Green computing in underwater wireless sensor networks pressure centric energy modeling. IEEE Syst. J. 2020, 14, 4735–4745. [Google Scholar] [CrossRef]
- Bhaskarwar, R.V.; Pete, D.J. Clustering with Compressive Sensing Technique for Network Lifetime Enhancement in Underwater Wireless Sensor Networks. In Proceedings of the International Conference on Communication and Computational Technologies: ICCCT 2022, Jaipur, India, 26–27 February 2022; pp. 479–491. [Google Scholar]
- Lu, Q.; Liu, F.; Zhang, Y.; Jiang, S. Routing protocols for underwater acoustic sensor networks: A survey from an application perspective. In Advances in Underwater Acoustics; Intech Open: Rijeka, Croatia, 2017; p. 23. [Google Scholar]
- Ahmed, S.; Javaid, N.; Khan, F.A.; Durrani, M.Y.; Ali, A.; Shaukat, A.; Sandhu, M.M.; Khan, Z.A.; Qasim, U. Co-UWSN: Cooperative energy-efficient protocol for underwater WSNs. Int. J. Distrib. Sens. Netw. 2015, 11, 891410. [Google Scholar] [CrossRef]
- Heidemann, J.; Ye, W.; Wills, J.; Syed, A.; Li, Y. Research challenges and applications for underwater sensor networking. In Proceedings of the IEEE Wireless Communications and Networking Conference, 2006, Las Vegas, NV, USA, 3–6 April 2006; Volume 1, pp. 228–235. [Google Scholar]
- Pompili, D.; Melodia, T. Three-dimensional routing in underwater acoustic sensor networks. In Proceedings of the 2nd ACM International Workshop on Performance Evaluation of Wireless Ad Hoc, Sensor, and Ubiquitous Networks, Montreal, QC, Canada, 10–13 October 2005; pp. 214–221. [Google Scholar]
- Venkateswara Rao, P.V.; Mohan Krishna Varma, N.; Sudhakar, R. A Systematic Survey on Software-Defined Networks, Routing Protocols and Security Infrastructure for Underwater Wireless Sensor Networks (UWSNs). In Emerging Research in Data Engineering Systems and Computer Communications; Springer: Singapore, 2020; pp. 551–559. [Google Scholar]
- Khan, Z.A.; Karim, O.A.; Abbas, S.; Javaid, N.; Zikria, Y.B.; Tariq, U. Q-learning based energy-efficient and void avoidance routing protocol for underwater acoustic sensor networks. Comput. Netw. 2021, 197, 108309. [Google Scholar] [CrossRef]
- Zhang, R.; Zhang, J.; Wang, Q.; Zhang, H. DOIDS: An Intrusion Detection Scheme Based on DBSCAN for Opportunistic Routing in Underwater Wireless Sensor Networks. Sensors 2023, 23, 2096. [Google Scholar] [CrossRef]
- Jodeh, H.; Mikkawi, A.; Awad, A.; Othman, O. Comparative analysis of routing protocols for under-water wireless sensor networks. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems, Amman, Jordan, 26–27 June 2018; pp. 1–7. [Google Scholar]
- Ahmad, B.; Jian, W.; Enam, R.N.; Abbas, A. Classification of DoS attacks in smart underwater wireless sensor network. Wirel. Pers. Commun. 2021, 116, 1055–1069. [Google Scholar] [CrossRef]
- Barati, A.; Dehghan, M.; Movaghar, A.; Barati, H. Improving fault tolerance in ad-hoc networks by using residue number system. J. Appl. Sci. 2008, 8, 3273–3278. [Google Scholar] [CrossRef]
- Javanmardi, S.; Barati, A.; Dastgheib, S.J.; Attarzadeh, I. A novel approach for faulty node detection with the aid of fuzzy theory and majority voting in wireless sensor networks. Int. J. Adv. Smart Sens. Netw. Syst. 2012, 2, 1–10. [Google Scholar] [CrossRef]
- Khazaei, E.; Barati, A.; Movaghar, A. Improvement of fault detection in wireless sensor networks. In Proceedings of the 2009 ISECS International Colloquium on Computing, Communication, Control, and Management, Sanya, China, 8–9 August 2009; Volume 4, pp. 644–646. [Google Scholar]
- Barati, A.; Movaghar, A.; Sabaei, M. RDTP: Reliable data transport protocol in wireless sensor networks. Telecommun. Syst. 2016, 62, 611–623. [Google Scholar] [CrossRef]
- Akbari, M.R.; Barati, H.; Barati, A. An overlapping routing approach for sending data from things to the cloud inspired by fog technology in the large-scale IoT ecosystem. Wirel. Netw. 2022, 28, 521–538. [Google Scholar]
- Waite, A.D. Sonar for Practising Engineers; Wiley: Hoboken, NJ, USA, 2002. [Google Scholar]
- Ahmad, I.; Rahman, T.; Zeb, A.; Khan, I.; Ullah, I.; Hamam, H.; Cheikhrouhou, O. Analysis of security attacks and taxonomy in underwater wireless sensor networks. Wirel. Commun. Mob. Comput. 2021, 2021, 1444024. [Google Scholar] [CrossRef]
- Pranitha, B.; Anjaneyulu, L. Analysis of underwater acoustic communication system using equalization technique for ISI reduction. Procedia Comput. Sci. 2020, 167, 1128–1138. [Google Scholar] [CrossRef]
- Chen, K.; Zhou, Y.; He, J. A localization scheme for underwater wireless sensor networks. Int. J. Adv. Sci. Technol. 2009, 4, 9–16. [Google Scholar]
- Javaid, N.; Jafri, M.R.; Khan, Z.A.; Qasim, U.; Alghamdi, T.A.; Ali, M. IAMCTD: Improved adaptive mobility of courier nodes in threshold-optimized DBR protocol for underwater wireless sensor networks. Int. J. Distrib. Sens. Netw. 2014, 10, 213012. [Google Scholar] [CrossRef]
- Ahmed, S.; Javaid, N.; Ahmad, A.; Ahmed, I.; Durrani, M.Y.; Ali, A.; Haider, S.B.; Ilahi, M. SPARCO: Stochastic performance analysis with reliability and cooperation for underwater wireless sensor networks. J. Sens. 2016, 2016, 7604163. [Google Scholar] [CrossRef]
- Subramani, N.; Mohan, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. An efficient metaheuristic-based clustering with routing protocol for underwater wireless sensor networks. Sensors 2022, 22, 415. [Google Scholar] [CrossRef] [PubMed]
- Jafri, M.R.; Ahmed, S.; Javaid, N.; Ahmad, Z.; Qureshi, R.J. AMCTD: Adaptive mobility of courier nodes in threshold-optimized DBR protocol for underwater wireless sensor networks. In Proceedings of the 2013 Eighth International Conference on Broadband and Wireless Computing, Communication and Applications, Compiegne, France, 28–30 October 2013; pp. 93–99. [Google Scholar]
- Du, X.; Peng, C.; Li, K. A secure routing scheme for underwater acoustic networks. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717713643. [Google Scholar] [CrossRef]
- Dargahi, T.; Javadi, H.H.; Shafiei, H. Securing underwater sensor networks against routing attacks. Wirel. Pers. Commun. 2017, 96, 2585–2602. [Google Scholar] [CrossRef]
- Zhang, R.; Zhang, Y. Wormhole-resilient secure neighbor discovery in underwater acoustic networks. In Proceedings of the 2010 Proceedings IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Dini, G.; Duca, A.L. A secure communication suite for underwater acoustic sensor networks. Sensors 2012, 12, 15133–15158. [Google Scholar] [CrossRef]
- Das, A.P.; Thampi, S.M. Secure communication in mobile underwater wireless sensor networks. In Proceedings of the 2015 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Kochi, India, 10–13 August 2015; pp. 2164–2173. [Google Scholar]
- Ali, M.; Shah, S.; Khan, M.; Ali, I.; Alroobaea, R.; Baqasah, A.M.; Ahmad, M. MuLSi-Co: Multilayer Sinks and Cooperation-Based Data Routing Techniques for Underwater Acoustic Wireless Sensor Networks (UA-WSNs). Wirel. Commun. Mob. Comput. 2022, 2022, 4840481. [Google Scholar] [CrossRef]
- Ullah, I.; Chen, J.; Su, X.; Esposito, C.; Choi, C. Localization and detection of targets in underwater wireless sensor using distance and angle-based algorithms. IEEE Access 2019, 7, 45693–45704. [Google Scholar] [CrossRef]
- Peng, C.; Du, X.; Li, K.; Li, M. An Ultra-Lightweight Encryption Scheme in Underwater Acoustic Networks. J. Sens. 2016, 2016, 8763528. [Google Scholar] [CrossRef]
- Jiang, J.; Han, G.; Zhu, C.; Chan, S.; Rodrigues, J.J. A Trust Cloud Model for Underwater Wireless Sensor Networks. IEEE Commun. Mag. 2017, 55, 110–116. [Google Scholar] [CrossRef]
- Ibragimov, M.; Lee, J.-H.; Kalyani, M.; Namgung, J.; Park, S.-H.; Yi, O.; Kim, C.H.; Lim, Y.-K. CCM-UW Security Modes for Low-Band Underwater Acoustic Sensor Networks. Wirel. Pers. Commun. 2016, 89, 479–499. [Google Scholar] [CrossRef]
- Xu, M.; Liu, G.; Guan, J. Towards a Secure Medium Access Control Protocol for Cluster-Based Underwater Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2015, 11, 325474. [Google Scholar] [CrossRef]
- Siddiqa, A.; Shah, M.A.; Khattak, H.A.; Akhunzada, A.; Ali, I.; Razak, Z.B.; Gani, A. Social Internet of Vehicles: Complexity, Adaptivity, Issues and Beyond. IEEE Access 2018, 6, 62089–62106. [Google Scholar] [CrossRef]
- Khan, M.N.R.; Shahin, F.B.; Sunny, F.I.; Khan, M.R.; Mashuk, A.E.H.; Al Mamun, K.A. An Innovative and Augmentative Android Application for Enhancing Mediated Communication of Verbally Disabled People. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kanpur, India, 6–8 July 2019; pp. 1–5. [Google Scholar]




| Technique | Contribution | Tool Used |
|---|---|---|
| IDS for Opportunistic Routing in UWSNs [15] | Proposed an Intrusion Detection System (IDS) for reducing the bad influence of malicious nodes on the transmission of data. The mechanism of location monitoring is adopted in the proposed DOIDS. The malicious nodes are detected through the clustering algorithms DBSCAN. The obtained results show that proposed algorithm significantly improved the accuracy rate of detection from 3% to 15% in different scenarios. | Not mentioned |
| Secure routing scheme for UASNs [31] | Recommended secure routing for UASNs. Signature algorithm is proposed for authentication between source and destination node. A trap-door scheme is used in order to achieve anonymity of the nodes. | NS2 with AquaSim |
| Securing network from routing attacks [32] | Proposed distributed approach for detecting and mitigating the routing attacks in UWSNs. An analytical model is proposed for the said purpose. | Castalia simulator |
| Secure discovery of neighbor in UASNs [33] | Proposed protocols suite for secure neighbor discovery in UASNs. The proposed protocols are based on the Direction of Arrival (DoA) signals approach. | C++ |
| Secure communication suite for UASNs [34] | Proposed scheme includes secure routing protocol and cryptographic primitives. Proposed protocols suite has limited power consumption and overhead; that is why it is suitable for UASNs. | Real data used |
| Secure communication in mobile UWSNs [35] | Flooding attack in UWSNs is simulated, and its impact is analyzed on the performance of UWSNs. It has been concluded that techniques suitable for the WSN environment are not suitable for UWSNs environment. | Aqua-Sim |
| MuLSi-Co routing technique for UASNs [36] | Proposed two algorithms: multilayer sink (MuLSi) and MuLSi-Co. MuLSi-Co uses cooperation technique, and it is the reliable version of MulSi. The schemes proposed are better in terms of reliable data exchange and energy cost and have a smaller number of dead nodes. | MATLAB |
| Presented better localization for UWSNs [37] | The authors first presented algorithms of general localization. Then two more algorithms were presented: angle-based and distance-based localization algorithms. The simulation results reveal that the proposed algorithms are able to achieve better accuracy of localization. | Not mentioned |
| Parameter | Value |
|---|---|
| No. of Nodes | 225 |
| No. of Sinks | 10 |
| Routing Protocol | AMCTD |
| Attack type | Active Attack |
| No. of Attacker nodes | 4, 8, 12 |
| No. of rounds | 9000 |
| Simulation volume | 500 m × 500 m × 500 m |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saeed, K.; Khalil, W.; Al-Shamayleh, A.S.; Ahmad, I.; Akhunzada, A.; ALharethi, S.Z.; Gani, A. Analyzing the Impact of Active Attack on the Performance of the AMCTD Protocol in Underwater Wireless Sensor Networks. Sensors 2023, 23, 3044. https://doi.org/10.3390/s23063044
Saeed K, Khalil W, Al-Shamayleh AS, Ahmad I, Akhunzada A, ALharethi SZ, Gani A. Analyzing the Impact of Active Attack on the Performance of the AMCTD Protocol in Underwater Wireless Sensor Networks. Sensors. 2023; 23(6):3044. https://doi.org/10.3390/s23063044
Chicago/Turabian StyleSaeed, Khalid, Wajeeha Khalil, Ahmad Sami Al-Shamayleh, Iftikhar Ahmad, Adnan Akhunzada, Salman Z. ALharethi, and Abdullah Gani. 2023. "Analyzing the Impact of Active Attack on the Performance of the AMCTD Protocol in Underwater Wireless Sensor Networks" Sensors 23, no. 6: 3044. https://doi.org/10.3390/s23063044
APA StyleSaeed, K., Khalil, W., Al-Shamayleh, A. S., Ahmad, I., Akhunzada, A., ALharethi, S. Z., & Gani, A. (2023). Analyzing the Impact of Active Attack on the Performance of the AMCTD Protocol in Underwater Wireless Sensor Networks. Sensors, 23(6), 3044. https://doi.org/10.3390/s23063044









