Forgery Cyber-Attack Supported by LSTM Neural Network: An Experimental Case Study
Abstract
1. Introduction
1.1. Problem Definition: Cyber-Attacks
- introduction of an ill-natured (e.g., high frequency) control signal, which might increase the aging rate of the actuators, which would result in a larger overall loss due to the prolonged exposure, compared to more devastating but quicker to detect and fix attacks, e.g., denial of service;
- gaining knowledge about the process of control; as the operators are not aware of the subtle changes in the control signals, subtle responses visible in the measurements might be attributed to noise and disturbances, whereas the attacker might use this knowledge to understand the process and design more precise attacks;
- the prolonged presence of the attacker in the network might result in getting operators used to the new characteristics of the signals, thus lowering the operators’ caution.
1.2. State of the Art: LSTM Neural Networks
1.3. Article Contribution
1.4. Article Organization
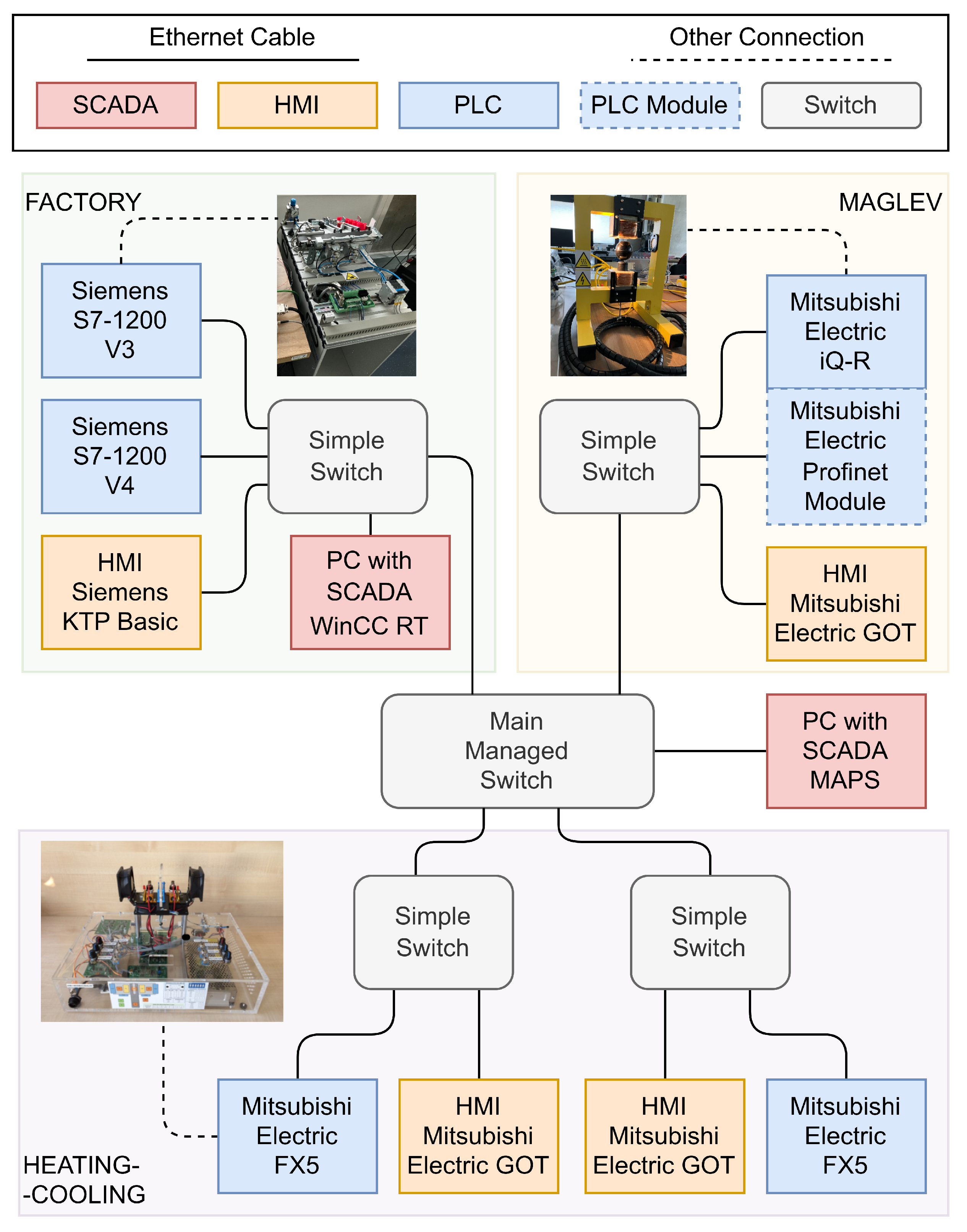
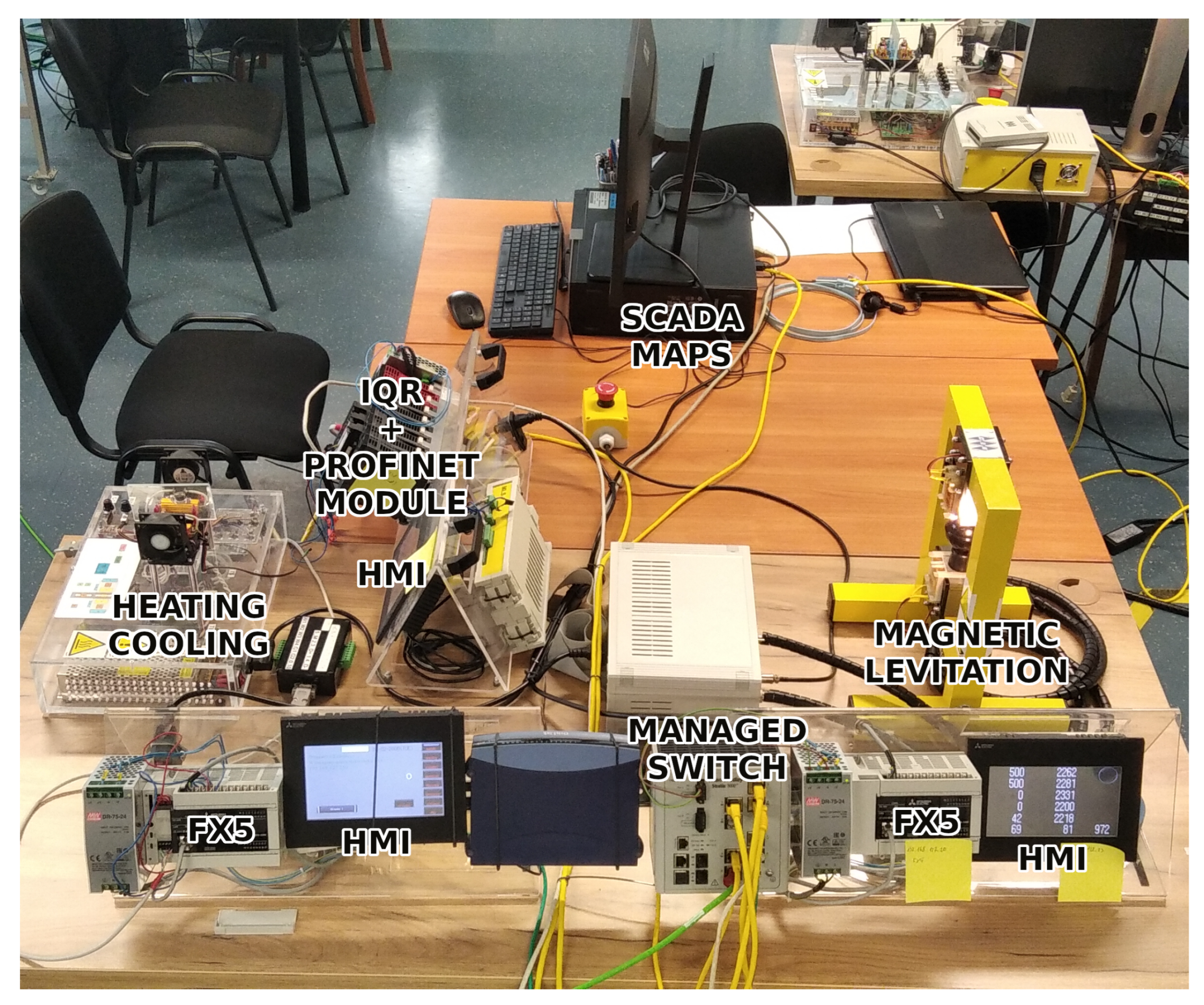
2. Laboratory Process Control Network
3. LSTM Neural Networks for SCADA System Operator Deception
3.1. Architecture of the LSTM Neural Network
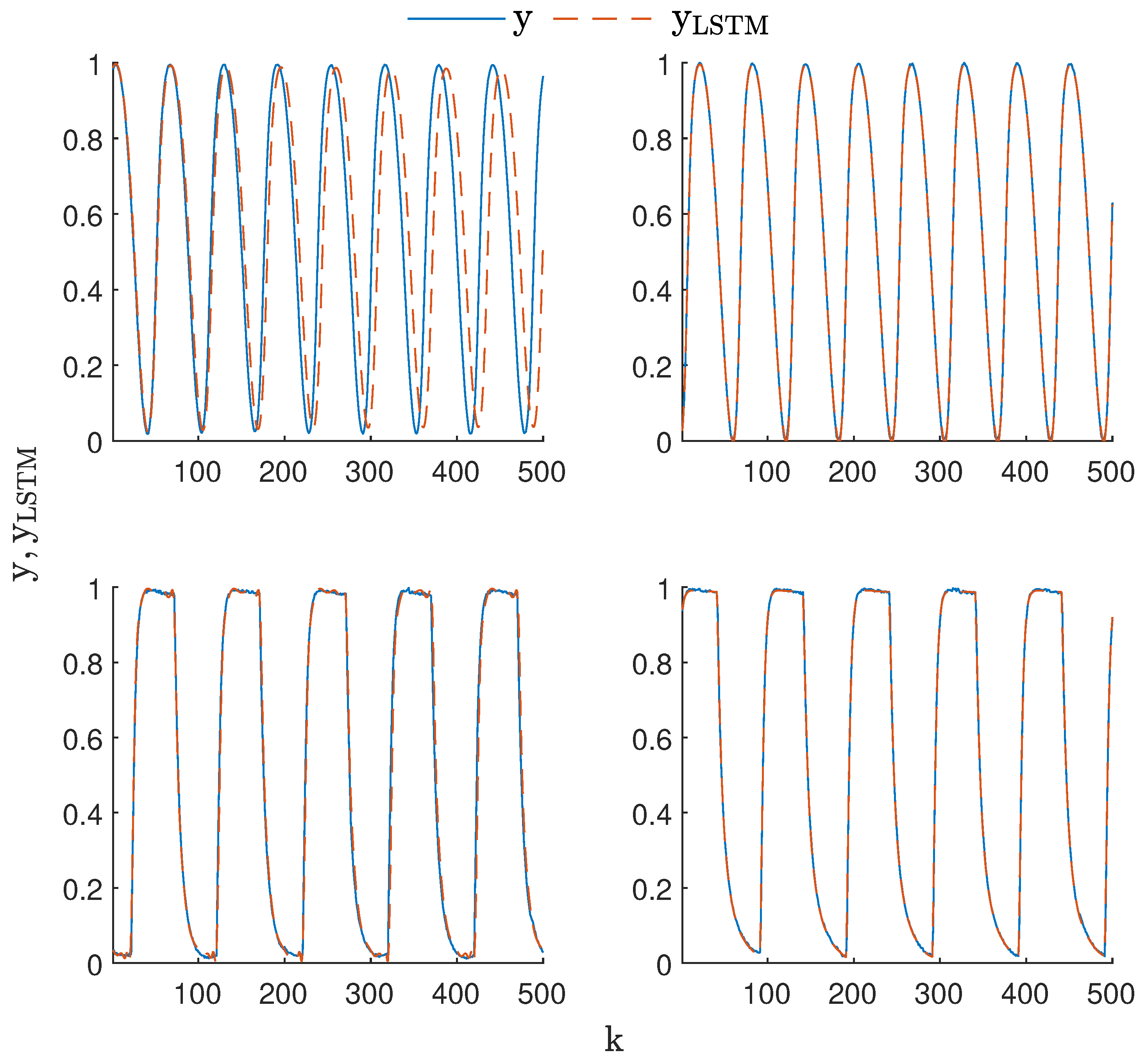
3.2. Data-Driven Training, Evaluation, and Structure Selection of the LSTM Neural Network
- 1.
- Models whose objective is to approximate the dynamics of the process when a sinusoidal set-point signal of the output is used; these models utilize previous values of the output signals to define the input vector of the LSTM network (Equation (1)), named hereafter ;
- 2.
- Models whose objective is to approximate the dynamics of the process when a square set-point signal of the output is used; these models utilize previous values of the output signals to define the input vector of the LSTM network (Equation (1)), named hereafter ;
- 3.
- Models whose objective is to approximate the dynamics of the process when a sinusoidal set-point signal of the output is used; these models utilize previous values of the output signals and the set-point signal to define the input vector of the LSTM network (Equation (2)), named hereafter ;
- 4.
- Models whose objective is to approximate the dynamics of the process when a square set-point signal of the output is used; these models utilize previous values of the output signals and the set-point signal to define the input vector of the LSTM network (Equation (2)), named hereafter ;
- 1.
- First, all the data collected from the network were transformed from hexadecimal to decimal format and normalized. We transformed all the signals to be in a range from 0 to 1, except the set-point for the square signal, which was transformed to 1 and −1;
- 2.
- Models with = 2 neurons and = 1 were trained. For each configuration of parameters, five models were trained;
- 3.
- The order of dynamics was increased to = 8 and = 3, and 10 new models were trained;
- 4.
- Steps 2 and 3 were repeated for models with equal to 12, 16, 24, 32, and 64.
4. Experimental Evaluation of LSTM Neural Networks in the SCADA System
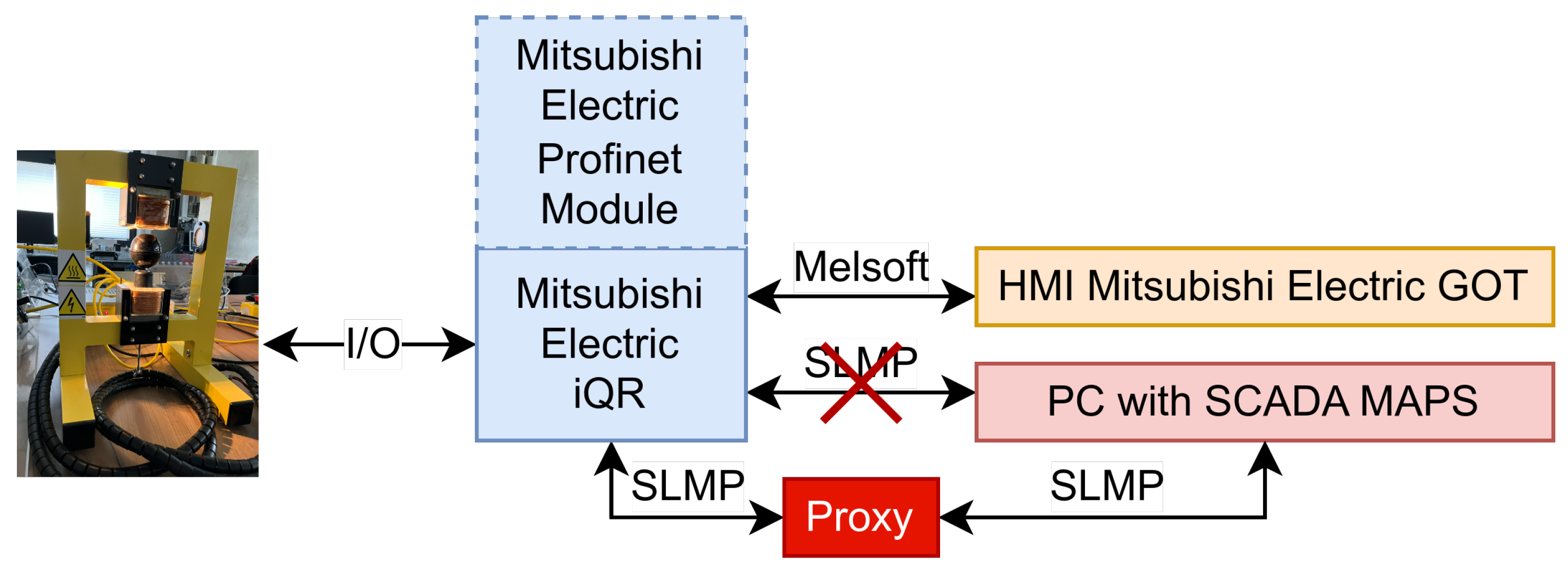
4.1. Cyber-Attack Description
4.2. Protection (Precautions) against Cyber-Attacks
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Toker, O.; Ozdemir, O. Physical-layer Cyberattack Resilient OFDM Automotive Radars. In Proceedings of the 2020 IEEE Vehicular Networking Conference (VNC), New York, NY, USA, 16–18 December 2020. [Google Scholar]
- Hou, B.; Zeng, S.; Xi, B.; Jia, S.; Guo, Q.; Xu, L.; Sun, H. Performance of Neighborhood-Watch-Based Resilient Distributed Energy Management Algorithm under Different Types of Cyberattacks. In Proceedings of the 2021 IEEE 4th International Electrical and Energy Conference (CIEEC), Wuhan, China, 28–30 May 2021; pp. 1–5. [Google Scholar]
- Zabetian-Hosseini, A.; Mehrizi-Sani, A.; Liu, C.C. Cyberattack to Cyber-Physical Model of Wind Farm SCADA. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 4929–4934. [Google Scholar]
- Colter, J.; Kinnison, M.; Henderson, A.; Schlager, S.M.; Bryan, S.; O’Grady, K.L.; Abballe, A.; Harbour, S. Testing the Resiliency of Consumer Off-the-Shelf Drones to a Variety of Cyberattack Methods. In Proceedings of the 2022 IEEE/AIAA 41st Digital Avionics Systems Conference (DASC), Portsmouth, VA, USA, 18–22 September 2022; pp. 1–5. [Google Scholar]
- Mu, L.; Zhao, E.; Wang, Y.; Zomaya, A.Y. Buoy Sensor Cyberattack Detection in Offshore Petroleum Cyber-Physical Systems. IEEE Trans. Serv. Comput. 2020, 13, 653–662. [Google Scholar] [CrossRef]
- Khaw, Y.M.; Abiri Jahromi, A.; Arani, M.F.M.; Sanner, S.; Kundur, D.; Kassouf, M. A Deep Learning-Based Cyberattack Detection System for Transmission Protective Relays. IEEE Trans. Smart Grid 2021, 12, 2554–2565. [Google Scholar] [CrossRef]
- Pazouki, S.; K C, B.; Alkhwaildi, H.A.; Asrari, A. Modelling of Smart Homes Affected by Cyberattacks. In Proceedings of the 2020 52nd North American Power Symposium (NAPS), Tempe, AZ, USA, 11–13 April 2021; pp. 1–6. [Google Scholar]
- Zhang, Y.; Jiang, Y.; Xu, A.; Hong, C.; Chen, J. Method to Evaluate the Impact of Cyberattacks against Charging Piles on Distribution Network. In Proceedings of the 2020 12th IEEE PES Asia-Pacific Power and Energy Engineering Conference (APPEEC), Nanjing, China, 20–23 September 2020; pp. 1–5. [Google Scholar]
- Kbar, G.; Alazab, A. A Comprehensive Protection Method for Securing the Organization’s Network against Cyberattacks. In Proceedings of the 2019 Cybersecurity and Cyberforensics Conference (CCC), Melbourne, VIC, Australia, 8–9 May 2019; pp. 118–122. [Google Scholar]
- Sudar, K.; Deepalakshmi, P.; Nagaraj, P.; Muneeswaran, V. Analysis of Cyberattacks and its Detection Mechanisms. In Proceedings of the 2020 Fifth International Conference on Research in Computational Intelligence and Communication Networks (ICRCICN), Bangalore, India, 26–27 November 2020; pp. 12–16. [Google Scholar]
- Housh, M.; Kadosh, N.; Haddad, J. Detecting and Localizing Cyber-Physical Attacks in Water Distribution Systems without Records of Labeled Attacks. Sensors 2022, 22, 6035. [Google Scholar] [CrossRef] [PubMed]
- Gaggero, G.B.; Caviglia, R.; Armellin, A.; Rossi, M.; Girdinio, P.; Marchese, M. Detecting Cyberattacks on Electrical Storage Systems through Neural Network Based Anomaly Detection Algorithm. Sensors 2022, 22, 3933. [Google Scholar] [CrossRef]
- Jadidi, Z.; Pal, S.; Hussain, M.; Nguyen Thanh, K. Correlation-Based Anomaly Detection in Industrial Control Systems. Sensors 2023, 23, 1561. [Google Scholar] [CrossRef]
- Yin, X.C.; Liu, Z.G.; Nkenyereye, L.; Ndibanje, B. Toward an Applied Cyber Security Solution in IoT-Based Smart Grids: An Intrusion Detection System Approach. Sensors 2019, 19, 4952. [Google Scholar] [CrossRef]
- Chae, Y.; Katenka, N.; DiPippo, L. An Adaptive Threshold Method for Anomaly-based Intrusion Detection Systems. In Proceedings of the 2019 IEEE 18th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 26–28 September 2019; pp. 1–4. [Google Scholar]
- Villalba, D.A.M.; Varon, D.F.M.; Pórtela, F.G.; Triana, O.A.D. Intrusion Detection System (IDS) with anomaly-based detection and deep learning application. In Proceedings of the 2022 V Congreso Internacional en Inteligencia Ambiental, Ingeniería de Software y Salud Electrónica y Móvil (AmITIC), San Jose, Costa Rica, 14–16 September 2022; pp. 1–4. [Google Scholar]
- Wang, W.; Wang, Z.; Zhou, Z.; Deng, H.; Zhao, W.; Wang, C.; Guo, Y. Anomaly detection of industrial control systems based on transfer learning. Tsinghua Sci. Technol. 2021, 26, 821–832. [Google Scholar] [CrossRef]
- Kao, J.B.; Jiang, J.R. Anomaly Detection for Univariate Time Series with Statistics and Deep Learning. In Proceedings of the 2019 IEEE Eurasia Conference on IOT, Communication and Engineering (ECICE), Yunlin, Taiwan, 3–6 October 2019; pp. 404–407. [Google Scholar]
- Wang, H.; Tang, M.; Park, Y.; Priebe, C.E. Locality Statistics for Anomaly Detection in Time Series of Graphs. IEEE Trans. Signal Process. 2014, 62, 703–717. [Google Scholar] [CrossRef]
- Heymann, S.; Latapy, M.; Magnien, C. Outskewer: Using Skewness to Spot Outliers in Samples and Time Series. In Proceedings of the 2012 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, Istanbul, Turkey, 26–29 August 2012; pp. 527–534. [Google Scholar]
- Abdallah, A.E.; Hamdan, M.; Gismalla, M.S.M.; Ibrahim, A.O.; Aljurayban, N.S.; Nagmeldin, W.; Khairi, M.H.H. Detection of Management-Frames-Based Denial-of-Service Attack in Wireless LAN Network Using Artificial Neural Network. Sensors 2023, 23, 2663. [Google Scholar] [CrossRef]
- Bhattasali, T.; Chaki, R.; Sanyal, S. Sleep Deprivation Attack Detection in Wireless Sensor Network. Int. J. Comput. Appl. 2012, 40, 19–25. [Google Scholar] [CrossRef]
- Alsaade, F.W.; Al-Adhaileh, M.H. Cyber Attack Detection for Self-Driving Vehicle Networks Using Deep Autoencoder Algorithms. Sensors 2023, 23, 4086. [Google Scholar] [CrossRef]
- Basan, E.; Basan, A.; Nekrasov, A.; Fidge, C.; Gamec, J.; Gamcová, M. A Self-Diagnosis Method for Detecting UAV Cyber Attacks Based on Analysis of Parameter Changes. Sensors 2021, 21, 509. [Google Scholar] [CrossRef]
- Alahmadi, A.N.; Rehman, S.U.; Alhazmi, H.S.; Glynn, D.G.; Shoaib, H.; Solé, P. Cyber-Security Threats and Side-Channel Attacks for Digital Agriculture. Sensors 2022, 22, 3520. [Google Scholar] [CrossRef]
- Mohamed, A.; Wang, F.; Butun, I.; Qadir, J.; Lagerström, R.; Gastaldo, P.; Caviglia, D.D. Enhancing Cyber Security of LoRaWAN Gateways under Adversarial Attacks. Sensors 2022, 22, 3498. [Google Scholar] [CrossRef] [PubMed]
- Kumar, V.; Kumar, R.; Khan, A.A.; Kumar, V.; Chen, Y.C.; Chang, C.C. RAFI: Robust Authentication Framework for IoT-Based RFID Infrastructure. Sensors 2022, 22, 3110. [Google Scholar] [CrossRef] [PubMed]
- Atilgan, E.; Ozcelik, I.; Yolacan, E.N. MQTT Security at a Glance. In Proceedings of the 2021 International Conference on Information Security and Cryptology (ISCTURKEY), Ankara, Turkey, 2–3 December 2021; pp. 138–142. [Google Scholar]
- Hadded, M.; Lauras, G.; Letailleur, J.; Petiot, Y.; Dubois, A. An Assessment Platform of Cybersecurity Attacks against the MQTT Protocol using SIEM. In Proceedings of the 2022 International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 22–24 September 2022; pp. 1–6. [Google Scholar]
- Sultan, A.B.M.; Mehmood, S.; Zahid, H. Man in the Middle Attack Detection for MQTT based IoT devices using different Machine Learning Algorithms. In Proceedings of the 2022 2nd International Conference on Artificial Intelligence (ICAI), Islamabad, Pakistan, 30–31 March 2022; pp. 118–121. [Google Scholar]
- Bassolillo, S.R.; D’Amato, E.; Notaro, I.; Blasi, L.; Mattei, M. Decentralized Mesh-Based Model Predictive Control for Swarms of UAVs. Sensors 2020, 20, 4324. [Google Scholar] [CrossRef] [PubMed]
- Ding, Z.; Sun, C.; Zhou, M.; Liu, Z.; Wu, C. Intersection Vehicle Turning Control for Fully Autonomous Driving Scenarios. Sensors 2021, 21, 3995. [Google Scholar] [CrossRef]
- Xiong, L.; Fu, Z.; Zeng, D.; Leng, B. An Optimized Trajectory Planner and Motion Controller Framework for Autonomous Driving in Unstructured Environments. Sensors 2021, 21, 4409. [Google Scholar] [CrossRef]
- Ławryńczuk, M.; Nebeluk, R. Computationally Efficient Nonlinear Model Predictive Control Using the L1 Cost-Function. Sensors 2021, 21, 5835. [Google Scholar] [CrossRef]
- Schwedersky, B.B.; Flesch, R.C.C.; Dangui, H.A.S. Practical nonlinear model predictive control algorithm for long short-term memory networks. IFAC-PapersOnLine 2019, 52, 468–473. [Google Scholar] [CrossRef]
- Billings, S.A.; Jamaluddin, H.B.; Chen, S. Properties of neural networks with applications to modelling non-linear dynamical systems. Int. J. Control 1992, 55, 193–224. [Google Scholar] [CrossRef]
- Haykin, S. Neural Networks and Learning Machines; Pearson Education: Upper Saddle River, NJ, USA, 2009. [Google Scholar]
- Lysenko, S.; Bobrovnikova, K.; Shchuka, R.; Savenko, O. A Cyberattacks Detection Technique Based on Evolutionary Algorithms. In Proceedings of the 2020 IEEE 11th International Conference on Dependable Systems, Services and Technologies (DESSERT), Kyiv, Ukraine, 14–18 May 2020; pp. 127–132. [Google Scholar]
- Naik Sapavath, N.; Muhati, E.; Rawat, D.B. Prediction and Detection of Cyberattacks using AI Model in Virtualized Wireless Networks. In Proceedings of the 2021 8th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2021 7th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), Washington, DC, USA, 26–28 June 2021; pp. 97–102. [Google Scholar]
- Tang, Z.; Jiao, J.; Zhang, P.; Yue, M.; Chen, C.; Yan, J. Enabling Cyberattack-Resilient Load Forecasting through Adversarial Machine Learning. In Proceedings of the 2019 IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019; pp. 1–5. [Google Scholar]
- Pazouki, S.; Naderi, E.; Asrari, A. Interconnected Energy Hubs including DERs Targeted by FDI Cyberattacks. In Proceedings of the 2020 11th International Green and Sustainable Computing Workshops (IGSC), Pullman, WA, USA, 19–22 October 2020; pp. 1–6. [Google Scholar]
- Toker, O. Performance Bounds for Cyberattack Detectors Using Multiple Observations. In Proceedings of the SoutheastCon 2022, Mobile, AL, USA, 26 March–3 April 2022; pp. 104–109. [Google Scholar]
- Djenna, A.; Saidouni, D.E.; Abada, W. A Pragmatic Cybersecurity Strategies for Combating IoT-Cyberattacks. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; pp. 1–6. [Google Scholar]
- Nagy, L.; Márton, L. Cyberattack detection and compensation for distant-controlled mobile robots. In Proceedings of the 2020 IEEE 20th International Symposium on Computational Intelligence and Informatics (CINTI), Budapest, Hungary, 5–7 November 2020; pp. 39–44. [Google Scholar]
- Leng, M.; Sahoo, S.; Blaabjerg, F.; Molinas, M. Projections of Cyberattacks on Stability of DC Microgrids—Modeling Principles and Solution. IEEE Trans. Power Electron. 2022, 37, 11774–11786. [Google Scholar] [CrossRef]
- Hochreiter, S.; Schmidhuber, J. Long Short-term Memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef]
- Hochreiter, S. Untersuchungen zu Dynamischen Neuronalen Netzen. Master’s Thesis, Technical University Munich, Munich, Germany, 1991. [Google Scholar]
- Chen, W.; Zhao, Z.; Liu, J.; Chen, P.C.Y.; Wu, X. LSTM Network: A Deep Learning Approach for Short-Term Traffic Forecast. IET Intell. Transp. Syst. 2017, 11, 68–75. [Google Scholar]
- Gallardo-Antolín, A.; Montero, J.M. Detecting deception from gaze and speech using a multimodal attention LSTM-based framework. Appl. Sci. 2021, 11, 6393. [Google Scholar] [CrossRef]
- Capes, T.; Coles, P.; Conkie, A.; Golipour, L.; Hadjitarkhani, A.; Hu, Q.; Huddleston, N.; Hunt, M.; Li, J.; Neeracher, M.; et al. Siri on-device deep learning-guided unit selection text-to-speech system. In Proceedings of the Interspeech 2017, Stockholm, Sweden, 20–24 August 2017; pp. 4011–4015. [Google Scholar]
- Graves, A.; Schmidhuber, J. Offline handwriting recognition with multidimensional recurrent neural networks. Adv. Neural Inf. Process. Syst. 2009, 21, 1–8. [Google Scholar]
- Zarzycki, K.; Ławryńczuk, M. LSTM and GRU Neural Networks as Models of Dynamical Processes Used in Predictive Control: A Comparison for Two Chemical Reactors. Sensors 2021, 21, 5625. [Google Scholar] [CrossRef]
- Zarzycki, K.; Ławryńczuk, M. Advanced predictive control for GRU and LSTM networks. Inf. Sci. 2022, 616, 229–254. [Google Scholar] [CrossRef]
- Jeon, B.K.; Kim, E.J. LSTM-based model predictive control for optimal temperature set-point planning. Sustainability 2021, 13, 894. [Google Scholar] [CrossRef]
- Li, Y.; Zhu, Z.; Kong, D.; Han, H.; Zhao, Y. EA-LSTM: Evolutionary attention-based LSTM for time series prediction. Knowl.-Based Syst. 2019, 181, 104785. [Google Scholar] [CrossRef]
- Cao, J.; Li, Z.; Li, J. Financial time series forecasting model based on CEEMDAN and LSTM. Phys. A Stat. Mech. Its Appl. 2019, 519, 127–139. [Google Scholar] [CrossRef]
- Karim, F.; Majumdar, S.; Darabi, H.; Harford, S. Multivariate LSTM-FCNs for time series classification. Neural Netw. 2019, 116, 237–245. [Google Scholar] [CrossRef] [PubMed]
- Wojtulewicz, A.; Chaber, P.; Ławryńczuk, M. Multiple-input multiple-output laboratory stand for process control education. In Proceedings of the 2016 21st International Conference on Methods and Models in Automation and Robotics (MMAR), Miedzyzdroje, Poland, 29 August–1 September 2016; pp. 466–471. [Google Scholar]
- Herarsi, N.E.H.; Mkedder, M.E.A.; Hassam, A.; Meliani, S.M. Development of a supervisory and control Interface for the distribution station of the FESTO MPS 500 system using WinCC software. In Proceedings of the 2021 1st International Conference on Cyber Management and Engineering (CyMaEn), Hammamet, Tunisia, 26-28 May 2021; pp. 1–4. [Google Scholar]
- Giusti, F.; Bevilacqua, M.; Tedeschi, S.; Emmanouilidis, C. Data analytics and production efficiency evaluation on a flexible manufacturing cell. In Proceedings of the 2018 IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Houston, TX, USA, 14–17 May 2018; pp. 1–6. [Google Scholar]
- Garcia, C.A.; Castellanos, E.X.; Rosero, C.; Sanchez, C.; Garcia, M.V. Designing Automation Distributed Systems Based on IEC-61499 and UML. In Proceedings of the 2017 5th International Conference in Software Engineering Research and Innovation (CONISOFT), Merida, Mexico, 25–27 October 2017; pp. 61–68. [Google Scholar]
- Hedrea, E.L.; Precup, R.E.; Bojan-Dragos, C.A. Results on Tensor Product-based Model Transformation of Magnetic Levitation Systems. Acta Polytech. Hung. 2019, 16, 93–111. [Google Scholar] [CrossRef]
- Bauer, W.; Baranowski, J. Fractional PIλD Controller Design for a Magnetic Levitation System. Electronics 2020, 9, 2135. [Google Scholar] [CrossRef]
- Gao, J.; Gan, L.; Buschendorf, F.; Zhang, L.; Liu, H.; Li, P.; Dong, X.; Lu, T. LSTM for SCADA Intrusion Detection. In Proceedings of the 2019 IEEE Pacific Rim Conference on Communications, Computers and Signal Processing (PACRIM), Victoria, BC, Canada, 21–23 August 2019; pp. 1–5. [Google Scholar]
- Kotenko, I.; Lauta, O.; Kribel, K.; Saenko, I. LSTM Neural Networks for Detecting Anomalies Caused by Web Application Cyber Attacks. In Frontiers in Artificial Intelligence and Applications, New Trends in Intelligent Software Methodologies, Tools and Techniques; IOS Press: Amsterdam, The Netherlands, 2021; pp. 127–140. [Google Scholar]
- Wilson, M.; Mahmood, H.; Giordano, J. Detection and Mitigation of Cyberattacks against Power Measurement Channels Using LSTM Neural Networks. In Proceedings of the 2021 IEEE Energy Conversion Congress and Exposition (ECCE), Vancouver, BC, Canada, 10–14 October 2021; pp. 1419–1426. [Google Scholar]


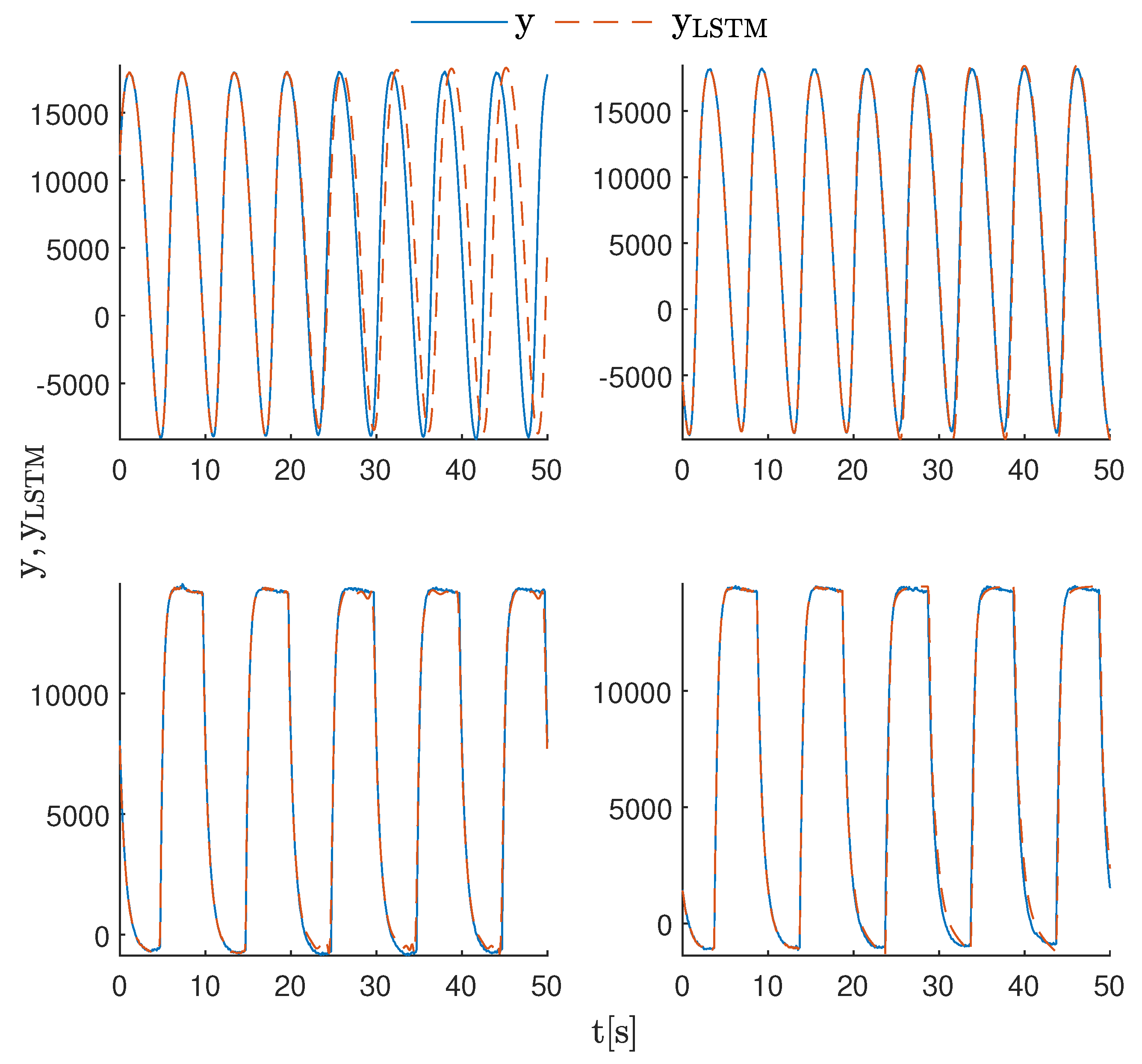
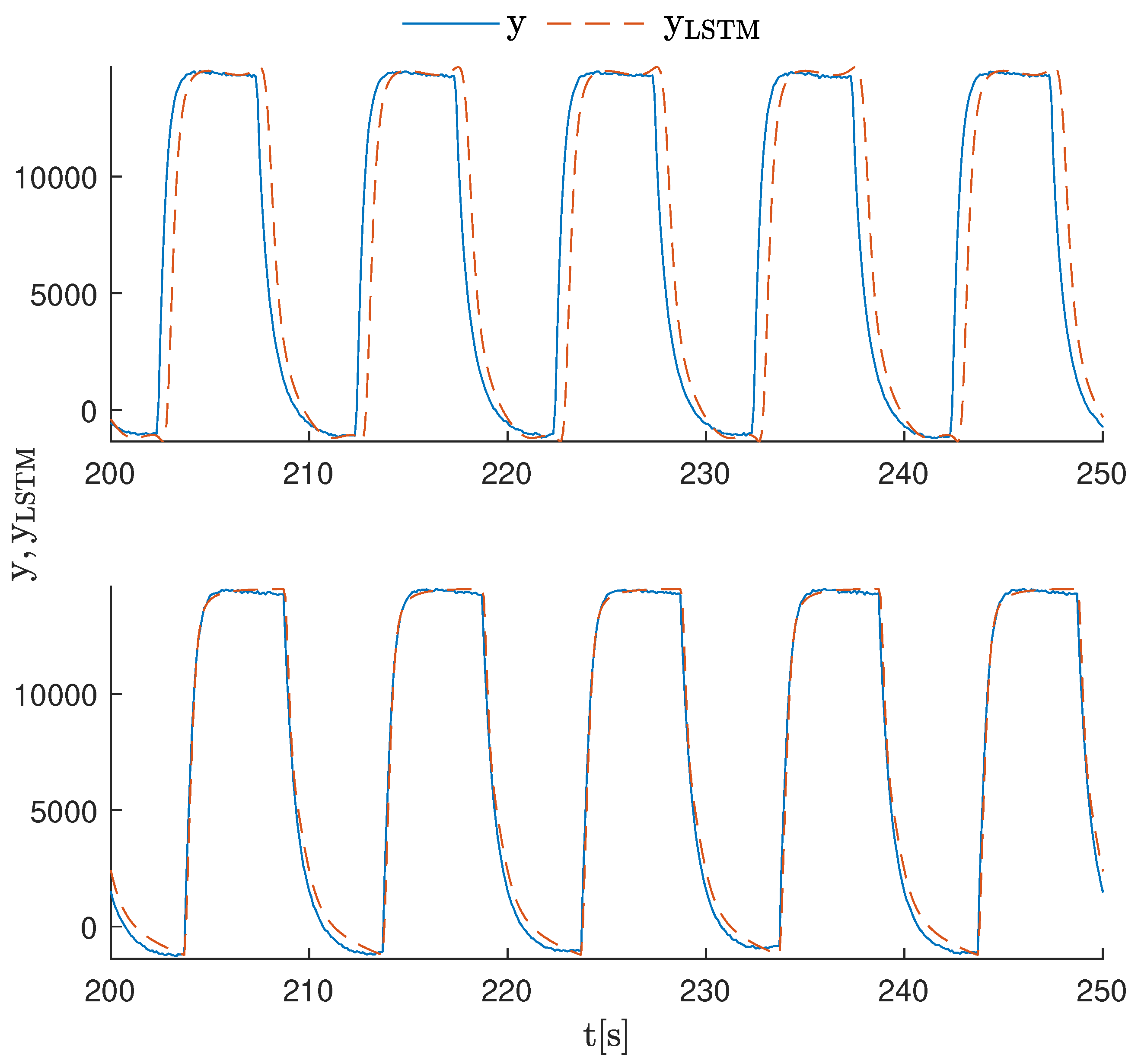
| 8 | 2.1 × 10 −1 | 8.5 × 10 −3 | 6.3 × 10 −4 | 4.6 × 10 −4 | 8.5 × 10 −4 | 2.5 × 10 −4 | |
| 12 | 1.0 × 10 −3 | 5.1 × 10 −4 | 2.3 × 10 −1 | 4.7 × 10 −4 | 7.5 × 10 −4 | 1.9 × 10 −4 | |
| 16 | 6.5 × 10 −4 | 1.6 × 10 −3 | 7.6 × 10 −4 | 4.7 × 10 −4 | 2.9 × 10 −4 | 2.0 × 10 −4 | |
| 24 | 1.1 × 10 −2 | 5.8 × 10 −3 | 5.9 × 10 −4 | 3.8 × 10 −4 | 1.7 × 10 −4 | 2.3 × 10 −4 | |
| 32 | 6.2 × 10 −4 | 5.6 × 10 −4 | 1.1 × 10 −2 | 2.4 × 10 −4 | 2.0 × 10 −4 | 1.8 × 10 −4 | |
| 64 | 0.00047 | 1.6 × 10 −3 | 2.1 × 10 −1 | 2.7 × 10 −4 | 1.7 × 10 −4 | 0.00013 | |
| 8 | 2.5 × 10 −1 | 2.8 × 10 −1 | 1.6 × 10 −1 | 1.0 × 10 −3 | 9.4 × 10 −4 | 0.00053 | |
| 12 | 3.3 × 10 −1 | 2.3 × 10 −1 | 2.2 × 10 −1 | 5.9 × 10 −4 | 8.2 × 10 −4 | 9.5 × 10 −4 | |
| 16 | 3.4 × 10 −1 | 1.4 × 10 −1 | 3.0 × 10 −1 | 6.5 × 10 −4 | 6.9 × 10 −4 | 6.4 × 10 −4 | |
| 24 | 6.7 × 10 −2 | 6.2 × 10 −2 | 2.5 × 10 −2 | 6.3 × 10 −4 | 7.6 × 10 −4 | 7.3 × 10 −4 | |
| 32 | 1.1 × 10 −1 | 5.1 × 10 −2 | 7.8 × 10 −2 | 6.3 × 10 −4 | 6.6 × 10 −4 | 7.2 × 10 −4 | |
| 64 | 7.8 × 10 −2 | 6.3 × 10 −2 | 0.023 | 6.9 × 10 −4 | 6.2 × 10 −4 | 6.0 × 10 −4 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zarzycki, K.; Chaber, P.; Cabaj, K.; Ławryńczuk, M.; Marusak, P.; Nebeluk, R.; Plamowski, S.; Wojtulewicz, A. Forgery Cyber-Attack Supported by LSTM Neural Network: An Experimental Case Study. Sensors 2023, 23, 6778. https://doi.org/10.3390/s23156778
Zarzycki K, Chaber P, Cabaj K, Ławryńczuk M, Marusak P, Nebeluk R, Plamowski S, Wojtulewicz A. Forgery Cyber-Attack Supported by LSTM Neural Network: An Experimental Case Study. Sensors. 2023; 23(15):6778. https://doi.org/10.3390/s23156778
Chicago/Turabian StyleZarzycki, Krzysztof, Patryk Chaber, Krzysztof Cabaj, Maciej Ławryńczuk, Piotr Marusak, Robert Nebeluk, Sebastian Plamowski, and Andrzej Wojtulewicz. 2023. "Forgery Cyber-Attack Supported by LSTM Neural Network: An Experimental Case Study" Sensors 23, no. 15: 6778. https://doi.org/10.3390/s23156778
APA StyleZarzycki, K., Chaber, P., Cabaj, K., Ławryńczuk, M., Marusak, P., Nebeluk, R., Plamowski, S., & Wojtulewicz, A. (2023). Forgery Cyber-Attack Supported by LSTM Neural Network: An Experimental Case Study. Sensors, 23(15), 6778. https://doi.org/10.3390/s23156778






