1. Introduction
Wireless sensor networks are recognized as a vital component of IoT, representing an emerging technology with wide-ranging applications across various fields. With their implementation advancing rapidly, the importance of ensuring security becomes increasingly paramount. IoT has moved beyond its early stages and is actively reshaping our perception of the Internet from a static entity into a fully integrated and dynamic network of the future. ZigBee, Z-Wave, 6LoWPAN, and LoRa are among the communication technologies employed within the realm of IoT. The IoT industry has witnessed a significant increase in adoption, especially in ZigBee communication, which has attracted the attention of research communities to examine the security challenges faced by IoT [
1]. ZigBee technology is a wireless sensor network based on the IEEE 802.15.4 standard that provides low-rate, low-power, and low-cost connectivity for various applications, including industrial automation, intelligent control, and medical health. Despite its numerous advantages, ZigBee technology encounters various challenges, including restrictions on device computing, limited memory space, and constrained energy consumption. These limitations make it impractical to use traditional security mechanisms such as asymmetric cryptography. Hence, there is a need to conduct further research in this area and increase research efforts to develop alternative security solutions.
The cryptanalytic strength of a cipher against mathematical and algebraic attacks is closely related to the length of the key material. Selecting the appropriate key length is a delicate process that involves balancing security and performance requirements. Various recommendations are available for different cryptographic ciphers and operations [
2,
3,
4]. The National Institute of Standards and Technology (NIST) has published a report stating that all versions of the AES are expected to remain secure beyond 2030 [
5,
6]. In a previous report by the National Security Agency (NSA) in the IETF, symmetric ciphers with a key size of 256 bits or more were projected to remain secure until 2245 [
7]. Therefore, the current version of AES requires alternative solutions to strengthen its security.
The researchers proposed several hybrid encryption techniques, which incorporate encryption schemes of two symmetric keys or both symmetric and asymmetric encryption methods. These techniques offer superior security compared with single encryption models that use public or private keys. Although many techniques that combine cryptographic algorithms are available on the market and claim to enhance data security, they may not be suitable for the constraints of wireless sensor networks.
In addition to enhancing the encryption process of ZigBee, it is essential to implement authentication and authorization measures to secure the network infrastructure. Using one-way authentication cannot guarantee security for both parties in communication. Instead, mutual authentication, where both parties are authenticated before transmission, is an effective solution to this issue. Deploying and managing robust authentication mechanisms in IoT infrastructures is considerably more challenging because of restrictions on wireless sensor devices. The literature has presented various authentication schemes to create a secure and reliable communication infrastructure for ZigBee wireless sensor networks, such as [
8,
9,
10]. Although these mechanisms have resolved the security and privacy issues of resource-constrained networks such as ZigBee, some of these methods come with relatively higher costs of communication and computation. Additionally, several methods utilize the real identity of devices for communication, potentially establishing connections between previous and future transactions under the same identity. This compromises privacy and makes authentication more complex.
The motivation of this research lies in addressing the security weaknesses of ZigBee, improving cryptographic strength, and ensuring secure communication without the drawbacks of resource-intensive asymmetric cryptography and key management/authentication issues. The symmetric key block cipher AES currently used in ZigBee may become vulnerable in the future. Moreover, symmetric cryptosystems pose challenges related to key management and authentication. Most existing approaches involve hybrid schemes, combining symmetric and asymmetric cryptography, or using symmetric cryptography with additional costs. The proposed scheme is symmetric cryptography-based and introduces the use of secure one-way hash functions and bitwise exclusive OR operations during mutual authentication and encryption. This enables D2D via a TC to establish a shared session key and exchange a secure value, which is integrated with sensed data for regular AES encryption. The objective is to provide robust protection against cryptanalysis attacks, offer a mutual authentication solution with the unlinkability and untraceability of ZigBee devices’ communication, and maintain efficiency compared with other schemes.
To this end, in this paper, we propose a method for enhancing AES-based cryptography to address the aforementioned security challenges. Additionally, we present a mutual authentication and privacy scheme that enables each device in the ZigBee network to establish secure D2TC and D2D communication sessions. Our suggested approach achieves diverse security properties, such as anonymity and traceability, alongside the critical dual attributes of confidentiality and integrity.
To summarize our contribution:
Key distribution in the original version of ZigBee has serious weaknesses since keys are transmitted over the air or preinstalled onto devices in an insecure manner. Additionally, all nodes share the same key, which puts the entire network at risk if a single node is compromised. Our solution addresses these shortcomings by utilizing a one-time-use session key and a secure adynamic array of bits to secure communication between two nodes, ensuring they cannot be used for future communications.
We introduce a novel mutual authentication approach for ZigBee wireless sensor networks.
This paper proposes a solution to strengthen the encryption between D2TC and D2D communication in ZigBee wireless sensor networks.
The proposed approach achieves protection against various attacks by relying on simple operations rather than computationally expensive cryptographic operations.
The paper is structured as follows:
Section 2 presents a brief literature review concerning schemes related to the proposed solution. Then, in
Section 3 we provide a breakdown of the fundamental components necessary for understanding the security framework of ZigBee and the network model.
Section 4 provides a detailed description of the proposed mutual authentication scheme and encryption process, including its phases and working mechanism, followed by an informal security analysis in the subsequent section.
Section 5 presents a detailed analysis of the results obtained by comparing the proposed mutual authentication scheme with existing schemes. Finally, the paper concludes with some closing remarks.
2. Related Works
The ZigBee protocol used in IoT networks presents significant security and privacy challenges. To address these issues, various authentication and cryptography mechanisms have been proposed in the literature, aiming to resolve these challenges without requiring changes to the current technological infrastructure. The following paragraphs present a concise overview of relevant approaches that closely align with the proposed scheme, without delving into the specific details of these schemes.
In study research, Lee et al. [
8] presented an IoT-specific lightweight mutual authentication protocol to enhance security. Instead of employing complex encryption schemes such as asymmetric encryption, the authors utilized symmetric encryption. As a result, this scheme is suitable for use with constrained IoT devices. While the paper offers a method for authenticating RFID tags with readers, it neglects the aspect of cryptography strength. Kulkarni et al. [
9] suggested a secure routing protocol for ZigBee networks, wherein aggregated MAC is utilized for authentication code. It offers authentication at every step of the path, along the entire route. While it allows for end-to-end authentication, the use of only two keys fails to guarantee communication secrecy. In addition, the paper does not provide an in-depth or comprehensive analysis of the security issues in the ZigBee protocol. It focuses solely on the MAC aspect, without considering other potential vulnerabilities or attack vectors.
An IoT mutual authentication scheme designed to enhance security in IoT systems was introduced by Zhao et al. [
10]. Through the implementation of dynamic password generation and the establishment of mutual authentication between devices and gateways, the scheme seeks to enhance the authentication process. The scheme underwent rigorous evaluation through mathematical analysis and simulation, demonstrating superior performance in terms of both security and efficiency compared with existing schemes. Nonetheless, it is worth noting that this scheme has several disadvantages as it fails to accommodate key properties such as anonymity, unlinkability, and untraceability. These shortcomings can undermine the privacy and security of the system, potentially exposing devices to risks such as identity disclosure, correlation of activities, and traceable transaction history. Chu et al. [
11] presented a scheme leveraging a smart card and a hash function to establish secure authentication and communication between IoT devices and the network. The scheme introduces a novel key-updating mechanism that enhances system security by regularly refreshing the authentication keys. Within this proposed framework, the generation of public and private key pairs relies on ECC. The initialization phase involved the configuration and computation of elliptic curve public parameters, which were specifically designed to be utilized during the authentication phase. Nevertheless, this scheme included limited safeguards for the aforementioned critical security properties.
Gaikwad et al. [
12] focused on implementing a Kerberos-based authentication scheme with three levels of security for an IoT smart home system. The authors proposed the utilization of symmetric algorithms, precisely the hash algorithms and AES, to elevate the level of security within the system. However, it is important to note that the work did not encompass D2D interactions. The absence of secure communication and authentication among network devices poses a restriction, considering their vital role in ensuring the system’s overall security. Additionally, this approach does not adequately address important security properties such as transaction anonymity, lack of linkability, and absence of traceability. These properties are crucial for maintaining privacy and preventing the identification and tracking of users’ activities within the smart home system. Ashibani et al. [
13] introduced authentication frameworks for smart homes that incorporate context awareness. In their dynamic authentication scheme, the security of local and remote access to IoT smart home devices is enhanced by integrating traditional static credentials and a range of contextual information. However, their work primarily focuses on device-to-cloud interactions and lacks authentication for device-to-device interactions.
Mishra et al. [
14] presented a resilient authentication protocol that employs smart cards within a wireless sensor network based on the internet of things. In the proposed protocol, the establishment of authentication between the node acting as the gateway and the node serving as the sensor is accomplished through the utilization of password hash values and pre-shared keys. The authors emphasized the successful achievement of user anonymity and demonstrated the protocol’s resilience against various attacks. However, it is worth noting that this work does not address authentication in D2D interactions. Alshahrani and Traore [
15] developed a mutual authentication and automated access control scheme specifically for IoT smart homes, focusing on lightweight implementation, incorporating a cumulative keyed hash. The scheme employed the controller node for authenticating the nodes, enabling the establishment of a temporary session key in a manner that ensures anonymity and prevents linkability. The authors leveraged fog computing architecture, which was modified to prevent identity theft attacks. This adaptation of fog architecture played a crucial role in ensuring secure and trustworthy IoT device identities. However, the protocol did not take into account instances where the IoT node leaves a specific home network and joins a different network. It was stated that this concern will be addressed in future research, aligning with our own objectives.
Chang and Le [
16] introduced an authentication scheme tailored for ad hoc wireless sensor networks, focusing on achieving both security and efficiency. Their scheme provides provable security guarantees while maintaining an efficient authentication process. However, the scheme cannot guarantee the property of untraceability. This limitation arises from the fixed parameter in the login message, which remains the same for different sessions. Consequently, an adversary can readily deduce that both messages originate from the same user. Exploiting this vulnerability, the adversary can trace and monitor the user’s activities, compromising their privacy and anonymity.
Alalak et al. [
17] presented a solution to remove the vulnerabilities present in block cipher key encryption algorithms, incorporating support for multiple keys. This allows the system to encrypt each data block with a distinct key, ensuring no two blocks are encrypted using the same key. By implementing this method, the occurrence of two plaintexts being encrypted with the same cipher key is eliminated, thus reducing the opportunities for analysts to exploit the ciphertext. However, it is important to note that this approach requires additional storage space.
A three-factor authentication protocol for IoT environments was proposed by Mirsaraei et al. [
18]. The protocol incorporates blockchain technology, hashing functions, XOR operations, and the fuzzy extractor concept. By leveraging these cryptographic techniques, the protocol achieves a suitable level of security, safeguards data from tampering, and enhances the transparency of recorded information on smart cards. Through their research, the authors demonstrated the effectiveness of the proposed protocol in ensuring secure mutual authentication. To perform formal analysis, the authors employed BAN logic, the ROR model, and the Avispa tool. In future research, we also intend to employ these three tools for the formal analysis of our own protocol.
The low-power nature of sensor nodes and the intermittent wireless connections between them create vulnerabilities that can be exploited by low-rate denial of service (LDoS) attacks, causing nodes to become unavailable. In their work [
19], Gong et al. introduced a mutual identity authentication scheme for the IoT to defend against such attacks. Similar to our approach, the protocol proposed in their paper not only defends against common attacks but also ensures secure traceability while maintaining anonymity.
In their study, Amor et al. [
20] presented a novel approach aimed at creating a secure social industrial IoT (SIIoT) system. Their proposed system enables mutual authentication among social IoT devices. While our approach shares commonalities with theirs, utilizing symmetric cryptography, hash functions, and bitwise XOR operations, it is important to highlight that the strength of the employed cryptographic algorithm was not taken into account in their approach.
Discussion
Several research studies have explored the potential of utilizing lightweight cryptographic functions, such as hash functions and bitwise XOR, for various purposes. However, these studies have overlooked the need for strong mutual authentication with minimal computational and communication cost, which is crucial for ZigBee devices. Consequently, the development of an efficient mutual authentication framework remains a significant challenge within the IoT ecosystem. Furthermore, it is important to note that a significant portion of these approaches prioritize strong mutual authentication without addressing the improvement of encryption or considering vital properties such as anonymity, linkability, and traceability. In contrast, our proposed approach not only considers a solution for D2TC and D2D authentication in ZigBee protocol, it also provides a solution to enhance encryption. Additionally, our approach effectively tackles crucial security properties, including transaction anonymity, absence of linkability, and lack of traceability.
4. Proposed Solution
Our proposed solution consists of two primary stages. The first stage is the device authentication and key agreement phase, which includes three sub-phases: (i) offline phase, (ii) authentication phase, and (iii) communication phase. The second stage involves strengthening the cryptography based on AES by utilizing a secure value exchanged in the first stage to enhance the cryptography of exchanged data in the ZigBee network. We provide a detailed description of both stages below, and we use the notations presented in
Table 1 to describe our solution throughout the paper.
4.1. Offline Phase
To establish secure D2TC and D2D communication in ZigBee networks, every device (Di) is required to register its master key and identity ID with the relevant TC during an offline phase to prevent unauthorized devices from gaining access. Only devices that have been registered in the offline phase are permitted to initiate a communication session.
4.2. Device Authentication Phase
In this section, D2TC authentication process is described. During the offline phase, if a device (Di) has participated, its ID address should be available in the authenticated devices list that is stored in the TC’s memory. If the ID matches one from the stored list, the requesting device (Di) will receive an encrypted message to begin the communication process. In our proposed solution, we prioritize the security and protection of ZigBee devices’ real identities (IDs) by ensuring that they are never transmitted in plain text. This is achieved by exclusively utilizing dynamic IDs during both the authentication and communication phases. The steps in this phase are explained below and summarized in
Figure 2.
Step1: Device to trust center
The device D1 generates three parameters, namely, KD1, CTRD1, and RAD1. KD1 is the key that will be used for encrypting the exchanged data with D1. The counter CTRD1 is incremented with each message. RAD1 is a random array of bytes equal to the block size used in AES. The device D1 creates a dynamic identity DIDD1 = h(IDD1, CTRD1) that changes for every session. This method ensures that the DIDD1 is unique in every session and can only be traced by the TC. Then D1 concatenates IDD1, KD1, CTRD1, and RAD1 and calculates the hash value, HD1 = h(CTRD1, (IDD1∥KD1∥CTRD1∥RAD1)). This ensures that HD1 is computed based on two dynamic values, enabling the detection of attacks even if one of the values is compromised. Finally, D1 encrypts (IDD1, KD1, CTRD1, RAD1) using the KTC and sends the message {IDTC, DIDD1, HD1, (IDD1, KD1, CTRD1, RAD1)_KTC } to the TC.
Step 2: Trust center to device
After receiving the message, the TC decrypts it using KTC, looks up IDD1, and subsequently carries out a validation process. Then, TC calculates the hash value of *HD1 and DIDD1 and proceeds to compare them against the received HD1 and DIDD1 for verification. The TC stores D1 information, KD1, CTRD1, DIDD1, and RAD1 in its database. Then, the TC increments CTRD1 by 1. Next, it concatenates the (DIDD1∥IDTC). After that, the TC computes the hash value, HTC1 = h(CTRD1, (DIDD1∥IDTC)). Then, the TC sends the message to D1. Finally, the TC increments CTRD1 again by 1 and computes for the upcoming session DIDD1 = h(IDD1, CTRD1). On the other side, D1 computes both the hash value and dynamic identity of D1. Then, it verifies whether these values match those received from the TC. When a match is identified, it signifies the accurate validation of the message’s integrity. Finally, D1 updates the CTRD1 value and the new dynamic identity for the upcoming session. At the end of this stage, as explained in steps 1 and 2, both D1 and the TC authenticate each other, and the parameters (IDD1, CTRD1, DIDD1, and RAD1) are securely sent between D1 and TC. The second stage describes the communication among devices. We assume that the ZigBee device D1 wants to communicate as a sender with the ZigBee device D2 as a receiver.
4.3. D2D Communication Phase
In this section, we discuss the D2D communication phase, during which a device verifies the identity of one or more devices. Once verified, the devices establish a shared key and a secure array of bits that can be employed later to establish an encrypted communication channel. The following steps discuss the communication process in this phase.
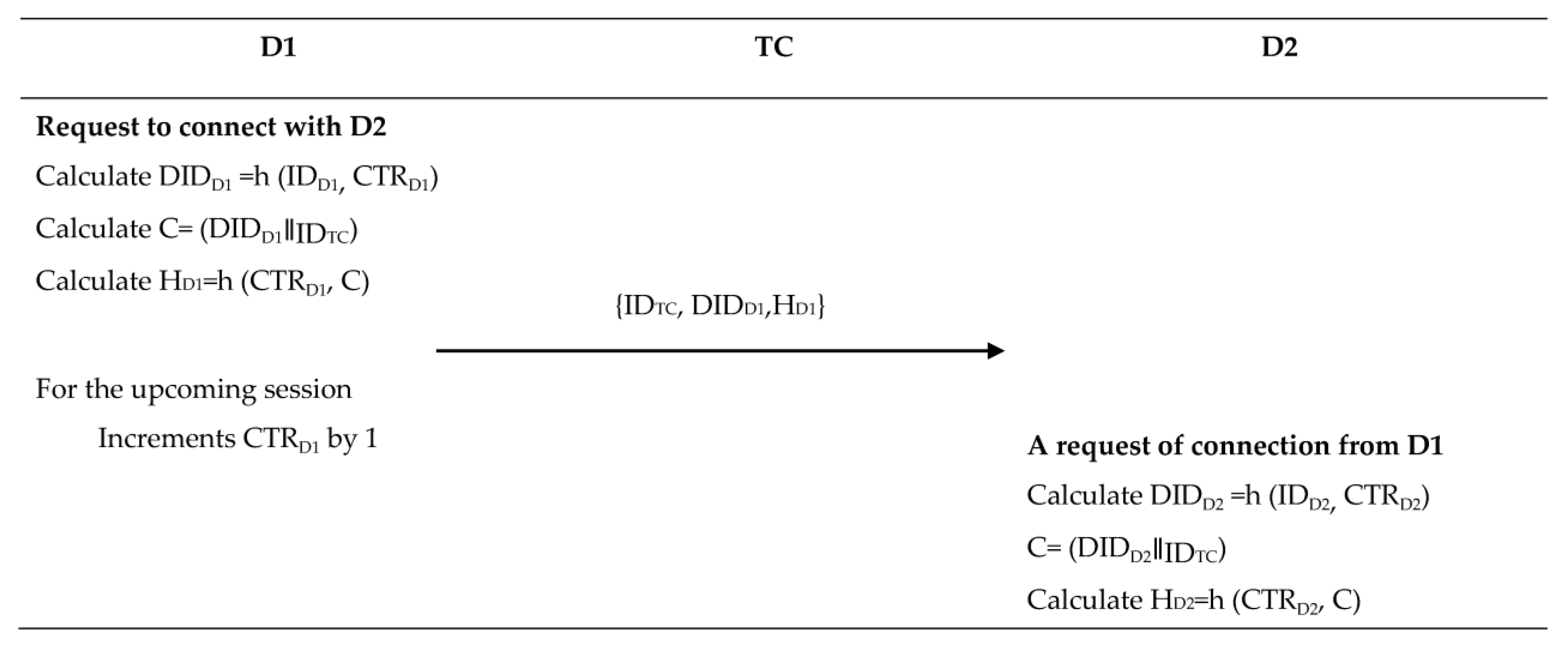
Step 1: Device (D1) to device (D2)
The device D1 sends a request to establish communication with an authenticated device D2. The message contains the device’s dynamic identity DIDD1, the identity of trust center IDTC, and the identity of the second device IDD2 encrypted using KD1. Then, the D1 computes the hash value of those parameters and CTRD1, HD1 = h (CTRD1, (IDTC∥DIDD1∥(IDD2)_kTC).
Step 2: Device (D2) to trust center
After constructing its message using the same method, device D2 forwards both the information it received from D1 and its own information to the trust center, requesting a temporary session key.
Step 3: Trust center authentication
The messages received by TC from D2 are validated by reconstructing HD1 and HD2 with KD1, KD2, CTRD1, and CTRD2 for the corresponding stored DIDD1 and DIDD2. The comparison of the hash value computed at TC, HTC for both D1 and D2, and matching with HD1 and HD2 confirms the message is authentic, as only D1 and D2 have access to KD1, KD2, CTRD1, and CTRD2. In addition, they have the ability to construct a valid message.
Step 4: Trust center to device (1) and trust center to device (D2)
TC creates the session key KSD12 and random array of bits RAD12, and subsequently sends them to D1 and D2 in an encrypted form using KD1 and KD2, respectively.
Step 5: Devices (D1 and D2) authentication
After receiving the encrypted information, D1 and D2 retrieve the secret session key using their respective private keys K
D1 and K
D2. The presence of CTR
D1 and CTR
D2 in the received message assures both devices that the message is new. At this stage, both devices can communicate securely utilizing the session key KS
D12.
Figure 2 provides a summary of the steps outlined in the preceding explanation.
Remark: We assume that the generated random array of bytes that will be used to strength the cryptography of AES will be used in the encryption process at the point that the devices need to send sensed data to the TC or other devices in the ZigBee network. The steps of this phase are explained below and are summarized in
Figure 3.
4.4. Encryption Based on AES
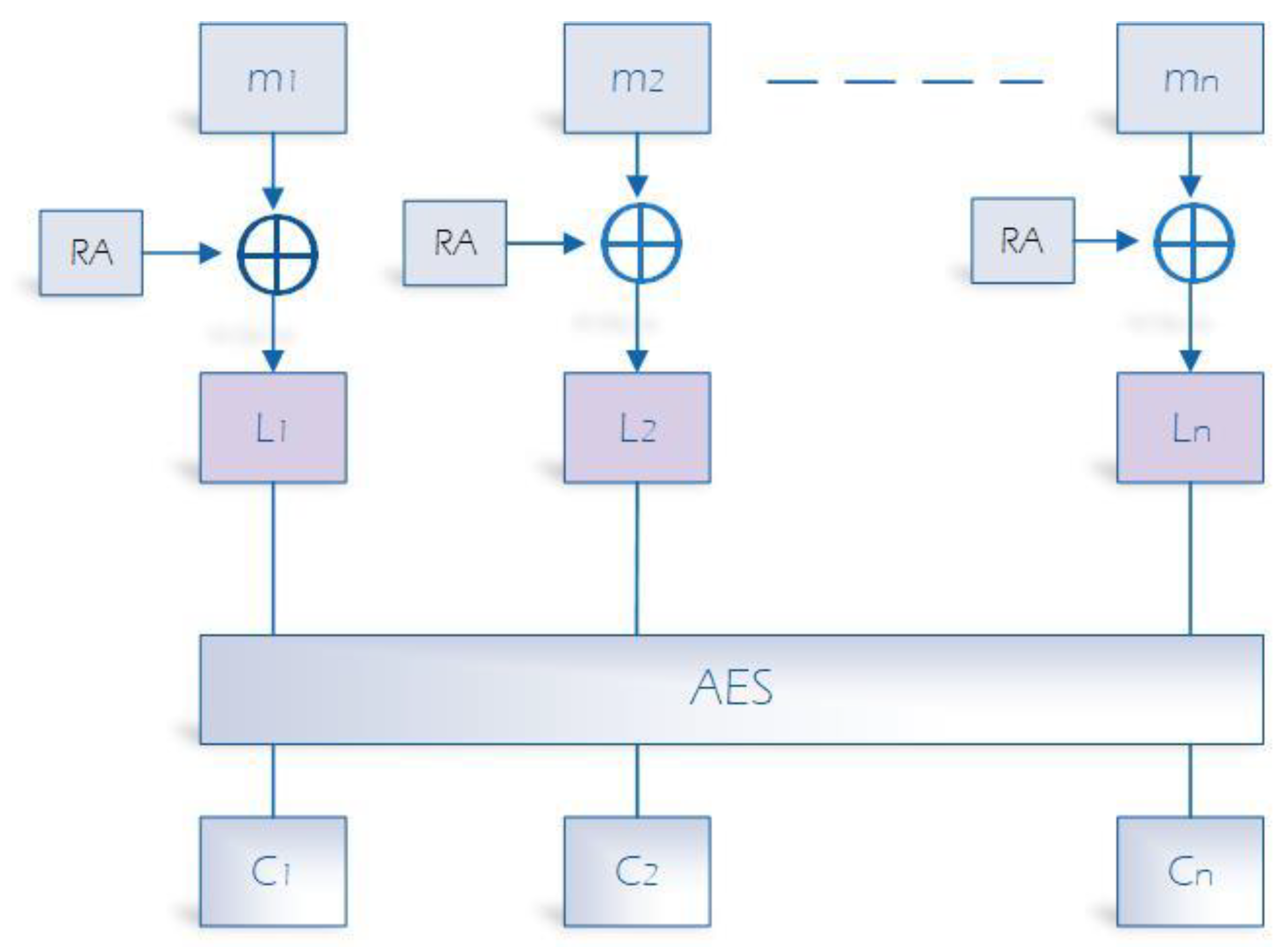
The main idea involves producing a random array of bits that matches the block size used in AES. This array will be combined with newly produced data by the ZigBee device, and the resulting output will serve as input for a standard AES. By doing so, the array will be refreshed with each message transmission between D2TC or D2D in the ZigBee network, ensuring that it remains unique for each session and can only be accessed by the two parties involved in the communication. The updated array, i.e., the previous array merged with the data generated by the ZigBee device, will be stored in both the device and the TC to be utilized in the encryption process of the subsequent message exchange between the two parties. This technique makes it difficult to perform cryptanalysis on the encrypted messages. The randomly generated array, which is updated with each sensed data, can offer protection against cryptanalysis attacks, even if the symmetric key is breached. The following figure summarizes our encryption solution (
Figure 4).
In our solution, the sensed data of the ZigBee device will be divided into blocks of size 128 bits. Then, the random generated array will be merged with each block and the output of this step will be used as input to the regular AES 128/CCM algorithm. Since the data are encrypted, the device will send the message to the receiver device in the ZigBee network and update the array as follows: RA = Ln. On the other side, the receiver device will decrypt the message based on the pre-shared symmetric key and RA, then recalculate RA and store it in its database for the upcoming session. In the following section, we explain how the session symmetric key and RA are exchanged and updated, in addition to the process of device authentication and communication.
6. Conclusions
In this paper, we propose a mutual authentication and key agreement approach for ZigBee wireless sensor networks. ZigBee devices are known for their low-power, low-cost, and lightweight characteristics. To optimize energy efficiency, we have exclusively employed hash functions for mutual authentication between D2TC and D2D, along with bitwise exclusive OR operations to enhance cryptography. Moreover, our approach uses the dynamic identity of the devices to preserve anonymity, while providing confidentiality, integrity, and untraceability properties. Through an informal security analysis, we have verified the resilience of our approach against commonly encountered attacks. Additionally, our approach’s efficiency was evaluated through a comparative analysis, comparing it with other relevant solutions.
In our future work, we aim to extend the protocol to handle cases where a ZigBee device switches from one network to another. Furthermore, we intend to investigate scenarios where multiple ZigBee TCs exist within the network. We aim to experimentally investigate and evaluate the performance overhead for those cases and conduct a formal security analysis using BAN logic, the ROR model, and the AVISPA tool [
18].