A Fuzzy-Based Context-Aware Misbehavior Detecting Scheme for Detecting Rogue Nodes in Vehicular Ad Hoc Network
Abstract
:1. Introduction
- A fuzzy-based context-aware misbehavior detection model is proposed to effectively detect rogue nodes (misbehaving vehicles) that spread false context information in VANET. Vehicular context is represented by the quality and the reliability of the information created by a set of neighboring vehicles.
- Due to the high dynamicity of vehicular context, the decision about the maliciousness of vehicles is fuzzy. Thus, a fuzzy inference system is constructed to evaluate the maliciousness of vehicles according to the current context on time.
- Based on the output of the developed fuzzy inference system, a dynamic context reference is built online. Rogue nodes are the vehicles that significantly diverge from the context reference. This dynamic context reference is more flexible than solely depending on statistical evaluation due to the use of linguistic methods, which is similar to human reasoning.
- Extensive testing was performed to evaluate and validate the proposed FCA-MDS model. Results of the experiments show that the proposed model outperforms the state-of-the-art models. It attains 83.38% overall performance in terms of F-measure, which is 7.88% higher than the state-of-the-art model.
2. Related Works
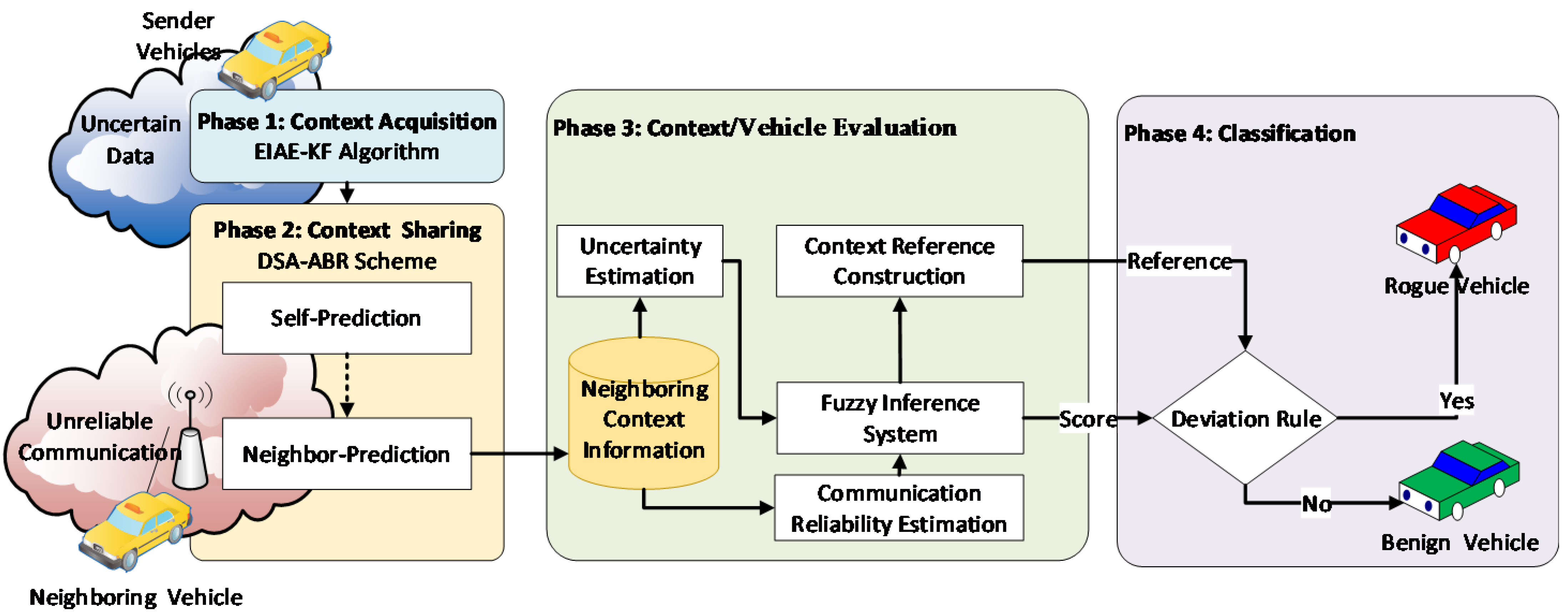
3. The Proposed Fuzzy-Based Context-Aware Approach
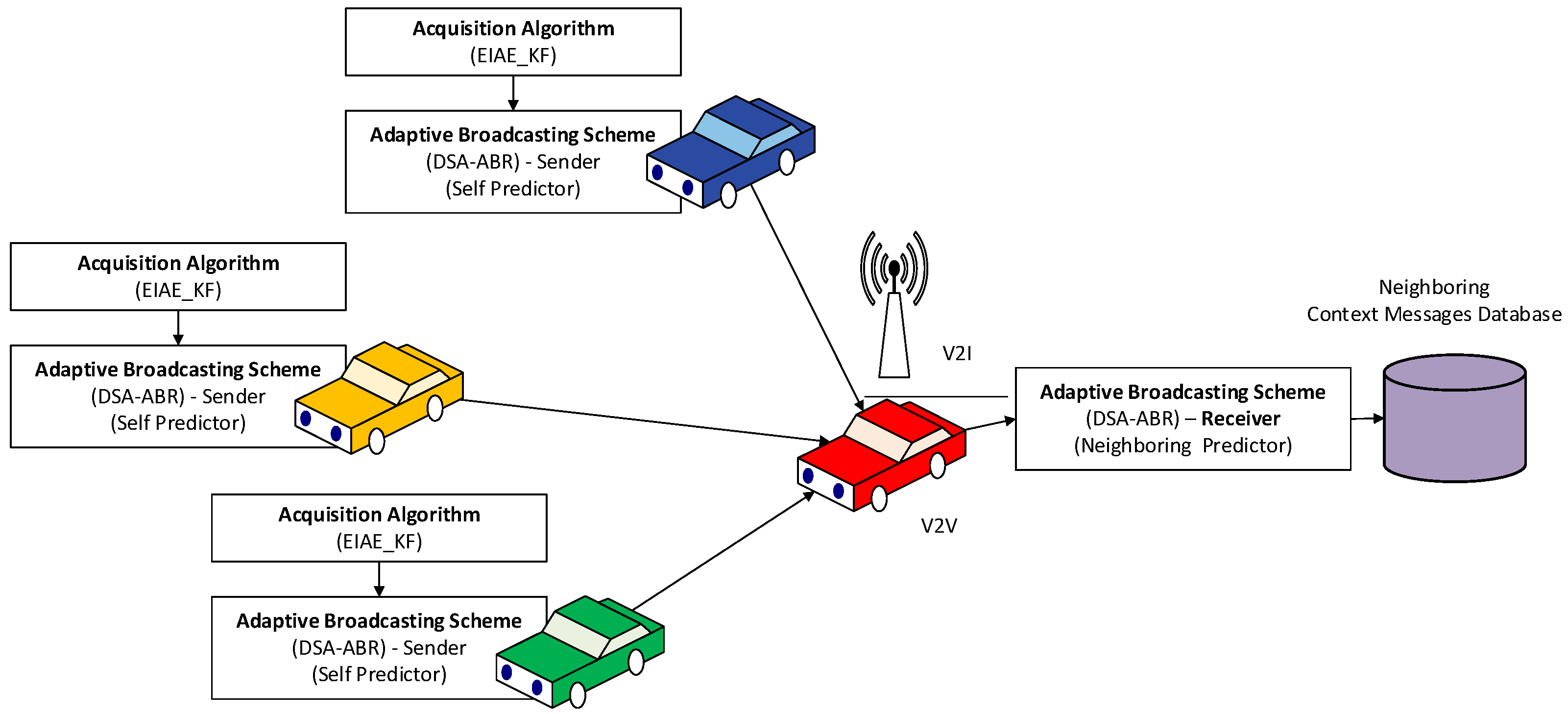
3.1. Phase 1: Context Acquisition Phase
3.2. Phase 2: Context Sharing Phase
3.3. Phase 3: Context/Vehicle Evaluation Phase
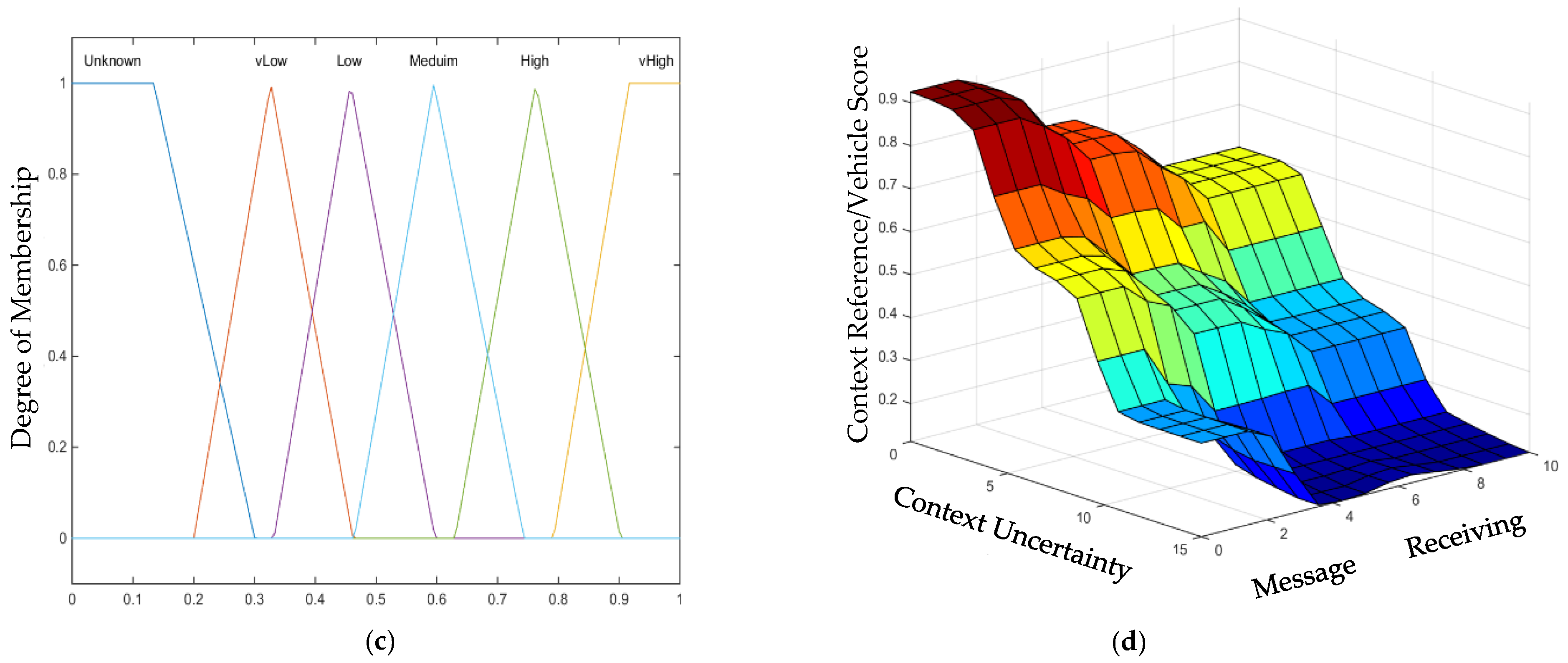
3.3.1. Uncertainty Estimation
| Algorithm 1: Estimate Data Uncertainty of Each vehicle |
| 1: Initialize,, H 2: FOR Each Time Epoch 3: 4: 5: 6: Compute the autocorrelation of the innovation sequence 7: IF THEN 8: //Estimation is not optimal 9: ELSE 10: 11: CONTINUE LOOP |
3.3.2. Communication Reliability Estimation
3.3.3. Fuzzy-Based Context Reference and Vehicle Scores
3.4. Phase 4: Classification Phase
4. Performance Evaluation
4.1. Datasets’ Source and Preprocessing
4.2. Simulation of Environmental Noises
4.3. Simulation of Communication Losses
4.4. Rogue Nodes Simulation
4.5. Expermintal Procedures
4.6. Performance Measures
4.7. Performance Comparison
5. Results and Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- WHO. 10 Facts on Global Road Safety. 2018. Available online: http://www.who.int/features/factfiles/roadsafety/en/ (accessed on 12 April 2021).
- Wahab, O.A.; Mourad, A.; Otrok, H.; Bentahar, J. CEAP: SVM-based intelligent detection model for clustered vehicular ad hoc networks. Expert Syst. Appl. 2016, 50, 40–54. [Google Scholar] [CrossRef]
- Sweet, M. Does traffic congestion slow the economy? J. Plan. Lit. 2011, 26, 391–404. [Google Scholar] [CrossRef]
- Williams, B.M.; Guin, A. Traffic Management Center Use of Incident Detection Algorithms: Findings of a Nationwide Survey. Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2007, 8, 351–358. [Google Scholar] [CrossRef]
- Vahdat-Nejad, H.; Ramazani, A.; Mohammadi, T.; Mansoor, W. A survey on context-aware vehicular network applications. Veh. Commun. 2016, 3, 43–57. [Google Scholar] [CrossRef]
- Firl, J.; Stubing, H.; Huss, S.A.; Stiller, C. MARV-X: Applying Maneuver Assessment for Reliable Verification of Car-to-X Mobility Data. IEEE Trans. Intell. Transp. Syst. 2013, 14, 1301–1312. [Google Scholar] [CrossRef]
- Petit, J.; Shladover, S.E. Potential Cyberattacks on Automated Vehicles. Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2015, 16, 546–556. [Google Scholar]
- Heijden, R.W.; Kargl, F. Open issues in differentiating misbehavior and anomalies for VANETs. In Proceedings of the 2nd GI/ITG KuVS Fachgespräch Inter-Vehicle Communication (FG-IVC 2014), Luxembourg, 20–21 February 2014. [Google Scholar]
- Santamaria, A.F.; Sottile, C.; De Rango, F.; Voznak, M. Road safety alerting system with radar and GPS cooperation in a VANET environment. In Proceedings of the Wireless Sensing, Localization, and Processing IX, Baltimore, MD, USA, 5–9 May 2014; Volume 9103. [Google Scholar]
- Uzcategui, R.; Acosta-Marum, G. Wave: A tutorial. IEEE Commun. Mag. 2009, 47, 126–133. [Google Scholar] [CrossRef]
- Hou, J.; Liu, J.; Han, L.; Zhao, J. Secure and Efficient Protocol for Position-based Routing in VANETs. In Proceedings of the 2012 IEEE International Conference on Intelligent Control, Automatic Detection and High-End Equipment (Icade), Beijing, China, 27–29 July 2012; pp. 142–148. [Google Scholar]
- Milanés, V.; Shladover, S.E.; Spring, J.; Nowakowski, C.; Kawazoe, H.; Nakamura, M. Cooperative Adaptive Cruise Control in Real Traffic Situations. IEEE Trans. Intell. Transp. Syst. 2014, 15, 296–305. [Google Scholar] [CrossRef] [Green Version]
- Dietzel, S.; Petit, J.; Heijenk, G.; Kargl, F. Graph-Based Metrics for Insider Attack Detection in VANET Multihop Data Dissemination Protocols. IEEE Trans. Veh. Technol. 2012, 62, 1505–1518. [Google Scholar] [CrossRef]
- Ghafoor, K.Z.; Lloret, J.; Abu Bakar, K.; Sadiq, A.S.; Ben Mussa, S.A. Beaconing Approaches in Vehicular Ad Hoc Networks: A Survey. Wirel. Pers. Commun. 2013, 73, 885–912. [Google Scholar] [CrossRef]
- Golestan, K.; Sattar, F.; Karray, F.; Kamel, M.; Seifzadeh, S. Localization in vehicular ad hoc networks using data fusion and V2V communication. Comput. Commun. 2015, 71, 61–72. [Google Scholar] [CrossRef]
- Liu, K.; Lim, H.B.; Frazzoli, E.; Ji, H.; Lee, C.S.V. Improving positioning accuracy using GPS pseudorange measurements for cooperative vehicular localization. IEEE Trans. Veh. Technol. 2014, 63, 2544–2556. [Google Scholar] [CrossRef]
- Wymeersch, H.; Lien, J.; Win, M.Z. Cooperative Localization in Wireless Networks. Proc. IEEE 2009, 97, 427–450. [Google Scholar] [CrossRef]
- Zhang, J. A Survey on Trust Management for VANETs. In Proceedings of the 25th IEEE International Conference on Advanced Information Networking and Applications (Aina 2011), Biopolis, Singapore, 22–25 March 2011; pp. 105–112. [Google Scholar]
- Bissmeyer, N.; Michael, W.; Frank, K. Misbehavior Detection and Attacker Identification in Vehicular Ad-Hoc Networks. Ph.D. Thesis, Technische Universität Darmstadt, Darmstadt, Germany, 2014. [Google Scholar]
- Huang, C.L.; Fallah, Y.P.; Sengupta, R.; Krishnan, H. Information Dissemination Control for Cooperative Active Safety Applications in Vehicular Ad-Hoc Networks. In Proceedings of the Globecom 2009—2009 IEEE Global Telecommunications Conference, Honolulu, HI, USA, 30 November–4 December 2009; Volume 1–8, pp. 4085–4090. [Google Scholar]
- Park, Y.; Kim, H. Application-Level Frequency Control of Periodic Safety Messages in the IEEE WAVE. IEEE Trans. Veh. Technol. 2012, 61, 1854–1862. [Google Scholar] [CrossRef]
- Van der Heijden, R.W.; Dietzel, S.; Leinmüller, T.; Kargl, F. Survey on Misbehavior Detection in Cooperative Intelligent Transportation Systems. IEEE Commun. Surv. Tutor. 2018, 21, 779–811. [Google Scholar] [CrossRef] [Green Version]
- Engoulou, R.G.; Bellaïche, M.; Pierre, S.; Quintero, A. VANET security surveys. Comput. Commun. 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Zainal, A.; Rassam, M.A.; Abraham, A. Improved vehicle positioning algorithm using enhanced innovation-based adaptive Kalman filter. Pervasive Mob. Comput. 2017, 40, 139–155. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Zainal, A.; Rassam, M.A.; Saeed, F. Driving-situation-aware adaptive broadcasting rate scheme for vehicular ad hoc network. J. Intell. Fuzzy Syst. 2018, 35, 1–16. [Google Scholar] [CrossRef]
- U.S. Department of Transportation Federal Highway Administration. Next Generation Simulation (NGSIM) Vehicle Trajectories and Supporting Data. 2016. Available online: https://data.transportation.gov/Automobiles/Next-Generation-Simulation-NGSIM-Vehicle-Trajector/8ect-6jqj (accessed on 2 January 2022).
- Bissmeyer, N.; Schroder, K.H.; Petit, J.; Mauthofer, S.; Bayarou, K.M. Short paper: Experimental analysis of misbehavior detection and prevention in VANETs. In Proceedings of the Fifth IEEE Vehicular Networking Conference, Boston, MA, USA, 16–18 December 2013; pp. 198–201. [Google Scholar]
- Nikaein, N.; Datta, S.K.; Marecar, I.; Bonnet, C. Application Distribution Model and Related Security Attacks in VANET. In Proceedings of the International Conference on Graphic and Image Processing (ICGIP 2012), Singapore, 5–7 October 2012; p. 8768. [Google Scholar]
- Chen, Y.-M.; Wei, Y.-C. A beacon-based trust management system for enhancing user centric location privacy in VANETs. J. Commun. Netw. 2013, 15, 153–163. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Maarof, M.A.; Zainal, A.; Rassam, M.A.; Saeed, F.; Alsaedi, M. Context-aware data-centric misbehaviour detection scheme for vehicular ad hoc networks using sequential analysis of the temporal and spatial correlation of the consistency between the cooperative awareness messages. Veh. Commun. 2019, 20, 100186. [Google Scholar] [CrossRef] [Green Version]
- Ghaleb, F.A.; Zainal, A.; Rassam, M.A.; Mohammed, F. An effective misbehavior detection model using artificial neural network for vehicular ad hoc network applications. In Proceedings of the 2017 IEEE Conference on Application, Information and Network Security (AINS), Miri, Malaysia, 13–14 November 2017; pp. 13–18. [Google Scholar]
- Ghaleb, F.A.; Saeed, F.; Al-Sarem, M.; Ali Saleh Al-rimy, B.; Boulila, W.; Eljialy, A.E.M.; Aloufi, K.; Alazab, M. Misbehavior-aware on-demand collaborative intrusion detection system using distributed ensemble learning for VANET. Electronics 2020, 9, 1411. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Maarof, M.A.; Zainal, A.; Al-Rimy BA, S.; Saeed, F.; Al-Hadhrami, T. Hybrid and multifaceted context-aware misbehavior detection model for vehicular ad hoc network. IEEE Access 2019, 7, 159119–159140. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Maarof, M.A.; Zainal, A.; Al-rimy BA, S.; Alsaeedi, A.; Boulila, W. Ensemble-based hybrid context-aware misbehavior detection model for vehicular ad hoc network. Remote Sens. 2019, 11, 2852. [Google Scholar] [CrossRef] [Green Version]
- Wan, J.; Zhang, D.; Zhao, S.; Yang, L.Y.; Lloret, J. Context-aware vehicular cyber-physical systems with cloud support: Architecture, challenges, and solutions. IEEE Commun. Mag 2014, 52, 106–113. [Google Scholar]
- Zhang, C.; Chen, K.; Zeng, X.; Xue, X. Misbehavior Detection Based on Support Vector Machine and Dempster-Shafer Theory of Evidence in VANETs. IEEE Access 2018, 6, 59860–59870. [Google Scholar] [CrossRef]
- Ercan, S.; Ayaida, M.; Messai, N. Misbehavior Detection for Position Falsification Attacks in VANETs Using Machine Learning. IEEE Access 2022, 10, 1893–1904. [Google Scholar] [CrossRef]
- Jaeger, A.; Bißmeyer, N.; Stübing, H.; Huss, S.A. A Novel Framework for Efficient Mobility Data Verification in Vehicular Ad-hoc Networks. Int. J. Intell. Transp. Syst. Res. 2012, 10, 11–21. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Zainal, A.; Maroof, M.A.; Rassam, M.A.; Saeed, F. Detecting Bogus Information Attack in Vehicular Ad Hoc Network: A Context-Aware Approach. Procedia Comput. Sci. 2019, 163, 180–189. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Al-Rimy, B.A.S.; Almalawi, A.; Ali, A.M.; Zainal, A.; Rassam, M.A.; Shaid, S.Z.M.; Maarof, M.A. Deep Kalman Neuro Fuzzy-Based Adaptive Broadcasting Scheme for Vehicular Ad Hoc Network: A Context-Aware Approach. IEEE Access 2020, 8, 217744–217761. [Google Scholar] [CrossRef]
- Ross, T.J. Fuzzy Logic with Engineering Applications; John Wiley & Sons: Chichester, UK, 2005. [Google Scholar]
- Thiemann, C.; Treiber, M.; Kesting, A. Estimating acceleration and lane-changing dynamics from next generation simulation trajectory data. Transp. Res. Rec. 2008, 2088, 90–101. [Google Scholar] [CrossRef] [Green Version]
- Ma, X.; Zhang, J.; Yin, X.; Trivedi, K.S. Design and Analysis of a Robust Broadcast Scheme for VANET Safety-Related Services. IEEE Trans. Veh. Technol. 2011, 61, 46–61. [Google Scholar] [CrossRef]
- Langbein, J.; Johnson, H. Correlated errors in geodetic time series: Implications for time-dependent deformation. J. Geophys. Res. Earth Surf. 1997, 102, 591–603. [Google Scholar] [CrossRef]
- Ghandour, A.J.; Di Felice, M.; Artail, H.; Bononi, L. Dissemination of safety messages in IEEE 802.11 p/WAVE vehicular network: Analytical study and protocol enhancements. Pervasive Mob. Comput. 2014, 11, 3–18. [Google Scholar] [CrossRef]
- Qiu, H.J.; Ho IW, H.; Chi, K.T.; Xie, Y. A methodology for studying 802.11 p VANET broadcasting performance with practical vehicle distribution. IEEE Trans. Veh. Technol. 2014, 64, 4756–4769. [Google Scholar] [CrossRef]
- Lyamin, N.; Vinel, A.; Jonsson, M.; Bellalta, B. Cooperative awareness in VANETs: On ETSI EN 302 637-2 performance. IEEE Trans. Veh. Technol. 2017, 67, 17–28. [Google Scholar] [CrossRef]





| Noise Type | Noise Model | Description |
|---|---|---|
| Static Gaussian Noise | ) | |
| Dynamic Gaussian Noise | ) | |
| Dynamic Correlated Noise | is white noise to represent the harsh environment. |
| Simulation Parameter | Configured Value |
|---|---|
| Communication Protocol | IEEE 802.11p/WAVE |
| Communication Range | 1000 m |
| Message Generation Rate | 10 Hz |
| Max Broadcasting Rate | 10 messages/second |
| Data Payload | 500 Byte |
| Data Rate | 3 Mbps |
| Propagation Model | Two-ray path-loss |
| Message arrival probabilities | 1 to 0.01 |
| Contention Mechanism | CSMA/CA |
| Number of Vehicles | 1725 |
| Vehicle Speeds | 40–100 km/h |
| Simulation Time | 15 min |
| Model | Accuracy% | FPR% | FNR% | DR% | Precession% | F-Measure% | |
|---|---|---|---|---|---|---|---|
| FCA-EC-MDS (the proposed) | Average | 92.88 | 4.27 | 4.27 | 82.65 | 84.18 | 83.38 |
| Deviation | 0.98 | 0.94 | 0.56 | 2.26 | 4.45 | 3.17 | |
| CA-EC-MDS [32] | Average | 90.98 | 2.33 | 9.15 | 66.18 | 88.18 | 75.50 |
| Deviation | 1.05 | 0.78 | 5.03 | 4.77 | 4.03 | 1.05 | |
| ECT-MDS [6] | Average | 74.79 | 2.98 | 33.49 | 30.65 | 83.83 | 44.49 |
| Deviation | 2.71 | 1.49 | 3.62 | 2.32 | 6.56 | 3.32 | |
| Baseline [43] | Average | 87.037 | 4.79 | 11.88 | 62.25 | 87.25 | 71.6 |
| Deviation | 5.94 | 8.29 | 0.91 | 3.0 | 0.18 | 7.21 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ghaleb, F.A.; Saeed, F.; Alkhammash, E.H.; Alghamdi, N.S.; Al-rimy, B.A.S. A Fuzzy-Based Context-Aware Misbehavior Detecting Scheme for Detecting Rogue Nodes in Vehicular Ad Hoc Network. Sensors 2022, 22, 2810. https://doi.org/10.3390/s22072810
Ghaleb FA, Saeed F, Alkhammash EH, Alghamdi NS, Al-rimy BAS. A Fuzzy-Based Context-Aware Misbehavior Detecting Scheme for Detecting Rogue Nodes in Vehicular Ad Hoc Network. Sensors. 2022; 22(7):2810. https://doi.org/10.3390/s22072810
Chicago/Turabian StyleGhaleb, Fuad A., Faisal Saeed, Eman H. Alkhammash, Norah Saleh Alghamdi, and Bander Ali Saleh Al-rimy. 2022. "A Fuzzy-Based Context-Aware Misbehavior Detecting Scheme for Detecting Rogue Nodes in Vehicular Ad Hoc Network" Sensors 22, no. 7: 2810. https://doi.org/10.3390/s22072810
APA StyleGhaleb, F. A., Saeed, F., Alkhammash, E. H., Alghamdi, N. S., & Al-rimy, B. A. S. (2022). A Fuzzy-Based Context-Aware Misbehavior Detecting Scheme for Detecting Rogue Nodes in Vehicular Ad Hoc Network. Sensors, 22(7), 2810. https://doi.org/10.3390/s22072810








